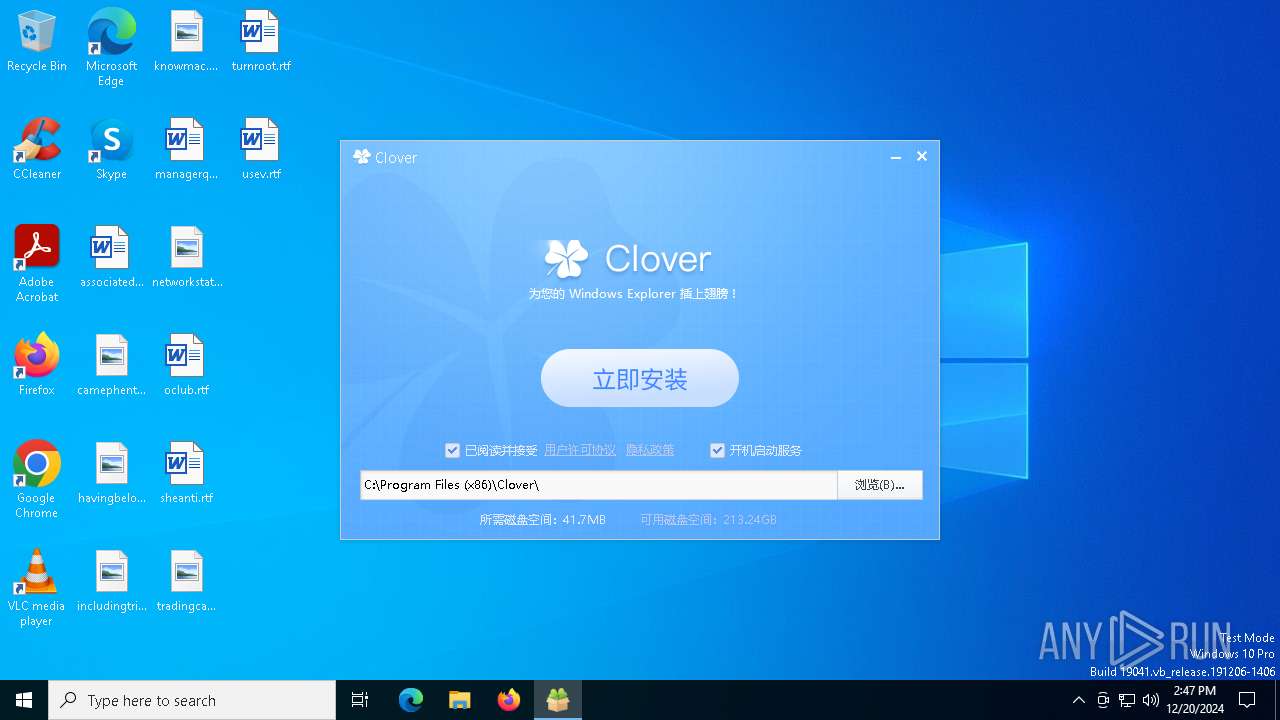
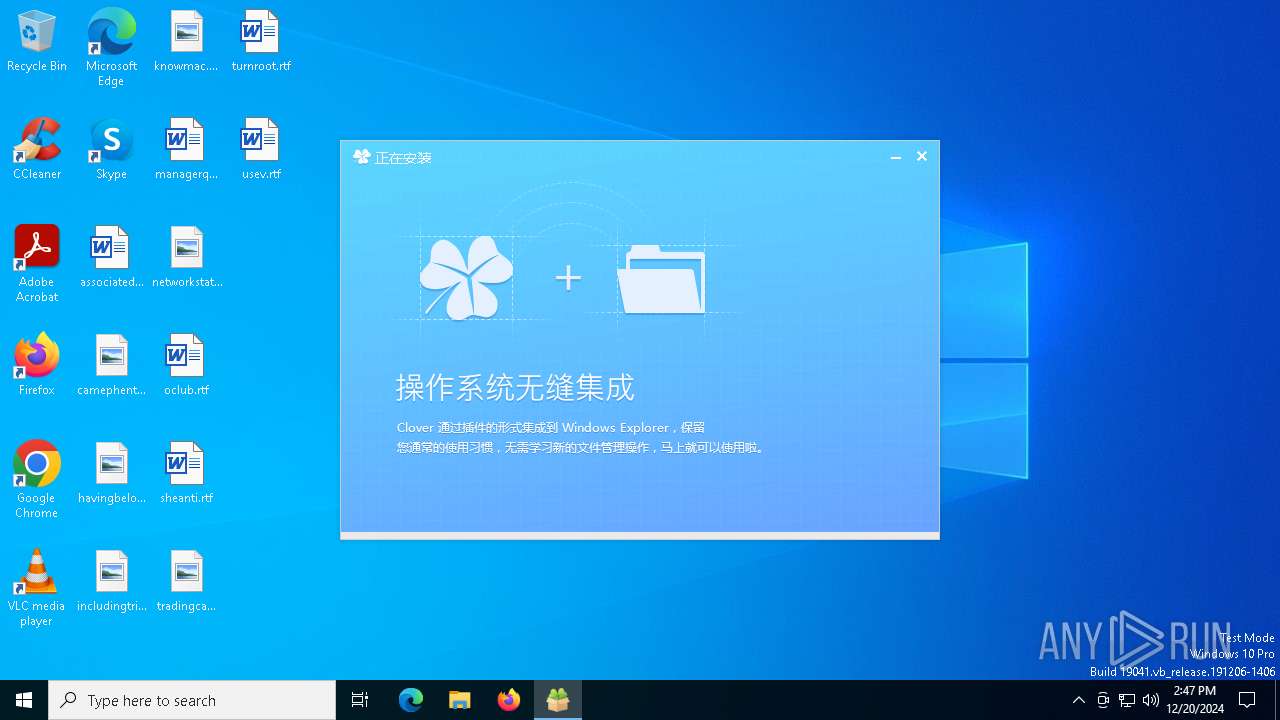
| File name: | setup_clover@3.5.4.exe |
| Full analysis: | https://app.any.run/tasks/35f6b4f0-edb1-4160-8c73-743517527690 |
| Verdict: | Malicious activity |
| Analysis date: | December 20, 2024, 14:47:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 12A57F152E0FC65517B1C22629F87430 |
| SHA1: | F5CF35BF021675B02C8299CFF95E53DC6DB95890 |
| SHA256: | 9847281C4CACA7B50D73839B8D1A8426A16D55C551EBD55C5854F29BCF517910 |
| SSDEEP: | 196608:fgJIqr+XnTHTDwTnH01T6yzGAKV+WRjgtgEYcK7yEbDj0Hm+9/3OeuWLKCgOEFaV:2Iqr+XT601T62CUgEYcgyC0H39Bl5gbQ |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- ClvUtility.exe (PID: 3696)
SUSPICIOUS
Executable content was dropped or overwritten
- setup_clover@3.5.4.exe (PID: 6752)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 556)
- regsvr32.exe (PID: 3792)
Reads security settings of Internet Explorer
- ClvUtility.exe (PID: 3696)
- SoftUpd.exe (PID: 5032)
Creates a software uninstall entry
- ClvUtility.exe (PID: 3696)
Application launched itself
- ClvUtility.exe (PID: 3696)
Creates or modifies Windows services
- ClvUtility.exe (PID: 3560)
Searches for installed software
- ClvUtility.exe (PID: 3696)
INFO
The sample compiled with chinese language support
- setup_clover@3.5.4.exe (PID: 6752)
Create files in a temporary directory
- setup_clover@3.5.4.exe (PID: 6752)
- SoftUpd.exe (PID: 5032)
Reads the computer name
- setup_clover@3.5.4.exe (PID: 6752)
- ClvUtility.exe (PID: 3696)
- ClvUtility.exe (PID: 6288)
- ClvUtility.exe (PID: 4516)
- ClvUtility.exe (PID: 3560)
- Clover.exe (PID: 4320)
- SoftUpd.exe (PID: 5032)
- Clover.exe (PID: 7096)
- ClvUtility.exe (PID: 3568)
- ClvUtility.exe (PID: 6852)
Creates files in the program directory
- setup_clover@3.5.4.exe (PID: 6752)
- Clover.exe (PID: 4320)
- ClvUtility.exe (PID: 4516)
Creates files or folders in the user directory
- setup_clover@3.5.4.exe (PID: 6752)
- ClvUtility.exe (PID: 4516)
- SoftUpd.exe (PID: 5032)
The sample compiled with english language support
- setup_clover@3.5.4.exe (PID: 6752)
Checks supported languages
- setup_clover@3.5.4.exe (PID: 6752)
- ClvUtility.exe (PID: 3696)
- ClvUtility.exe (PID: 6288)
- ClvUtility.exe (PID: 4516)
- Clover.exe (PID: 4320)
- SoftUpd.exe (PID: 5032)
- ClvUtility.exe (PID: 3560)
- Clover.exe (PID: 7096)
- ClvUtility.exe (PID: 3568)
- ClvUtility.exe (PID: 6852)
Process checks computer location settings
- ClvUtility.exe (PID: 3696)
The process uses the downloaded file
- ClvUtility.exe (PID: 3696)
Sends debugging messages
- Clover.exe (PID: 4320)
Checks proxy server information
- SoftUpd.exe (PID: 5032)
Manual execution by a user
- Clover.exe (PID: 7096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (46.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (41) |
| .exe | | | Win32 Executable (generic) (6.6) |
| .exe | | | Generic Win/DOS Executable (2.9) |
| .exe | | | DOS Executable Generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:04:22 11:23:06+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 819200 |
| InitializedDataSize: | 11587584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x45ae8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.4.20416 |
| ProductVersionNumber: | 3.5.4.20416 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Windows, Chinese (Simplified) |
| Comments: | Clover 安装程序 |
| CompanyName: | ejie.me |
| FileDescription: | Clover 安装程序 |
| FileVersion: | 3.5.4.20416 |
| InternalName: | Clover |
| LegalCopyright: | Copyright (C) 2020 |
| OriginalFileName: | Clover.exe |
| ProductName: | Clover |
| ProductVersion: | 3.5.4.20416 |
Total processes
146
Monitored processes
18
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | regsvr32 /s /u "C:\Program Files (x86)\Clover\\TabHelper32.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | ClvUtility.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | regsvr32 /s "C:\Program Files (x86)\Clover\\TabHelper32.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | ClvUtility.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3560 | "C:\Program Files (x86)\Clover\ClvUtility.exe" InstallService | C:\Program Files (x86)\Clover\ClvUtility.exe | — | setup_clover@3.5.4.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Clover 辅助程序 Exit code: 0 Version: 1,0,1,0 Modules
| |||||||||||||||
| 3568 | "C:\Program Files (x86)\Clover\ClvUtility.exe" SetSpreader --qid clover241241220 --time 1734706186 | C:\Program Files (x86)\Clover\ClvUtility.exe | ClvUtility.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Clover 辅助程序 Exit code: 0 Version: 1,0,1,0 Modules
| |||||||||||||||
| 3696 | "C:\Program Files (x86)\Clover\\ClvUtility.exe" InstallSpreadOperate clover241220,,0 | C:\Program Files (x86)\Clover\ClvUtility.exe | setup_clover@3.5.4.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Clover 辅助程序 Exit code: 0 Version: 1,0,1,0 Modules
| |||||||||||||||
| 3792 | /s "C:\Program Files (x86)\Clover\\TabHelper64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4320 | "C:\Program Files (x86)\Clover\Clover.exe" | C:\Program Files (x86)\Clover\Clover.exe | setup_clover@3.5.4.exe | ||||||||||||
User: admin Company: www.ejie.me Integrity Level: MEDIUM Description: Clover Exit code: 0 Version: 3.5.4.20416 Modules
| |||||||||||||||
| 4516 | "C:\Program Files (x86)\Clover\\ClvUtility.exe" CreateStartMenu 1 | C:\Program Files (x86)\Clover\ClvUtility.exe | — | setup_clover@3.5.4.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Clover 辅助程序 Exit code: 0 Version: 1,0,1,0 Modules
| |||||||||||||||
| 5032 | "C:\Program Files (x86)\Clover\SoftUpd.exe" RunAuto | C:\Program Files (x86)\Clover\SoftUpd.exe | Clover.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3.5.4.20416 Modules
| |||||||||||||||
| 5464 | regsvr32 /s /u "C:\Program Files (x86)\Clover\\TabHelper64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | ClvUtility.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 797
Read events
4 751
Write events
46
Delete events
0
Modification events
| (PID) Process: | (6752) setup_clover@3.5.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Clover |
| Operation: | write | Name: | LastInstallTime |
Value: 0 | |||
| (PID) Process: | (6752) setup_clover@3.5.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Clover |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files (x86)\Clover\ | |||
| (PID) Process: | (6752) setup_clover@3.5.4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Clover |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files (x86)\Clover\ | |||
| (PID) Process: | (3792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\TabHelper.DLL |
| Operation: | write | Name: | AppID |
Value: {3D8758D6-6EEF-453D-B910-391ABFFFD326} | |||
| (PID) Process: | (3792) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F8A6CAA2-533D-4AED-9E05-8EB19A4021AB}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (3696) ClvUtility.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Clover |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files (x86)\Clover\ | |||
| (PID) Process: | (3696) ClvUtility.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Clover |
| Operation: | write | Name: | DisplayName |
Value: Clover V3.5 | |||
| (PID) Process: | (3696) ClvUtility.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Clover |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Clover\Uninst.exe | |||
| (PID) Process: | (3696) ClvUtility.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Clover |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Clover\Clover.exe | |||
| (PID) Process: | (3696) ClvUtility.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Clover |
| Operation: | write | Name: | DisplayVersion |
Value: 3.5.4.20416 | |||
Executable files
29
Suspicious files
14
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6752 | setup_clover@3.5.4.exe | C:\Users\admin\AppData\Local\Temp\my7zData.7z | — | |
MD5:— | SHA256:— | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\CloverInfo.ini | text | |
MD5:EFA85F0CED4BE6AF19136214B95361F0 | SHA256:4BAA03530BA8DC5A4809190B9E1752E0A6B872514B474107AC6423452E855B64 | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\data\____.dat | image | |
MD5:064F3B680CC5E020F6A8E0C5E005B787 | SHA256:5B5937A7AB24C2C7ADE09B04C807B4B4290A22FA2F110A84CF1614BEE0C52CE4 | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\ico\taobao.png | image | |
MD5:733F9F84C062D33C14D8DC16157AF9F8 | SHA256:DB5703CB584F8175D9F5282D4F74A1263EBB17285D3C1112AAE883EB7D3FE64C | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\lang\lang_index.xml | xml | |
MD5:927C5543CBEE0F8A06F2589B84D75781 | SHA256:B2165610C2519DE6580E80A208D4126976314CFEC60AB08918CC335B937D7E65 | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\appconfig.dat | binary | |
MD5:1FF0200124BCC8EA6316732FDC754828 | SHA256:36AE2957E42498E8FFF9D258FEB0121D3F085B6F79CE013B4CE3B0F176A2E01E | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\CloverAss.exe | executable | |
MD5:50FF7918A774A05589D83A9FDD763100 | SHA256:A8843FFA531DED6910ABEE426F95ADDFBCCFB8E5D3548F46710453C58F5E078D | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Common Files\Clover\Clover.ini | text | |
MD5:7AE7390B4FD7F79667F40101E174E7E0 | SHA256:4EE0E8B8789E61C80CC151D54CB8C6ACE2A6B744703A46CAF3D63C8CD85AED73 | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\default.dat | text | |
MD5:1EBB800AFDCB061B06B36960F51A19D7 | SHA256:ED186334888F04D48B5F400ED63845A6FDF99DB8930E2002E069883217F4F437 | |||
| 6752 | setup_clover@3.5.4.exe | C:\Program Files (x86)\Clover\data\__.dat | image | |
MD5:F01765E7A55B8BC53CA72BFEFBD8542E | SHA256:3B2AEEDC35262E3D8188B70F307217FEE3DA19518F4CBE3F97D516DA79308249 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
67
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3220 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3220 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6752 | setup_clover@3.5.4.exe | GET | 404 | 47.89.39.18:80 | http://config.ejie.me/install/clover/3.5.4.20416.dat | unknown | — | — | whitelisted |
5432 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5432 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4704 | SoftUpd.exe | GET | 200 | 47.89.39.18:80 | http://updatecn.ejie.me/update.dat?19426 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3220 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3220 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.209.154:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
tjv1.ejie.me |
| whitelisted |
config.ejie.me |
| whitelisted |
Threats
Process | Message |
|---|---|
Clover.exe | CreateProcessAsUser ok!
|
Clover.exe | CreateProcessAsUser ok!
|