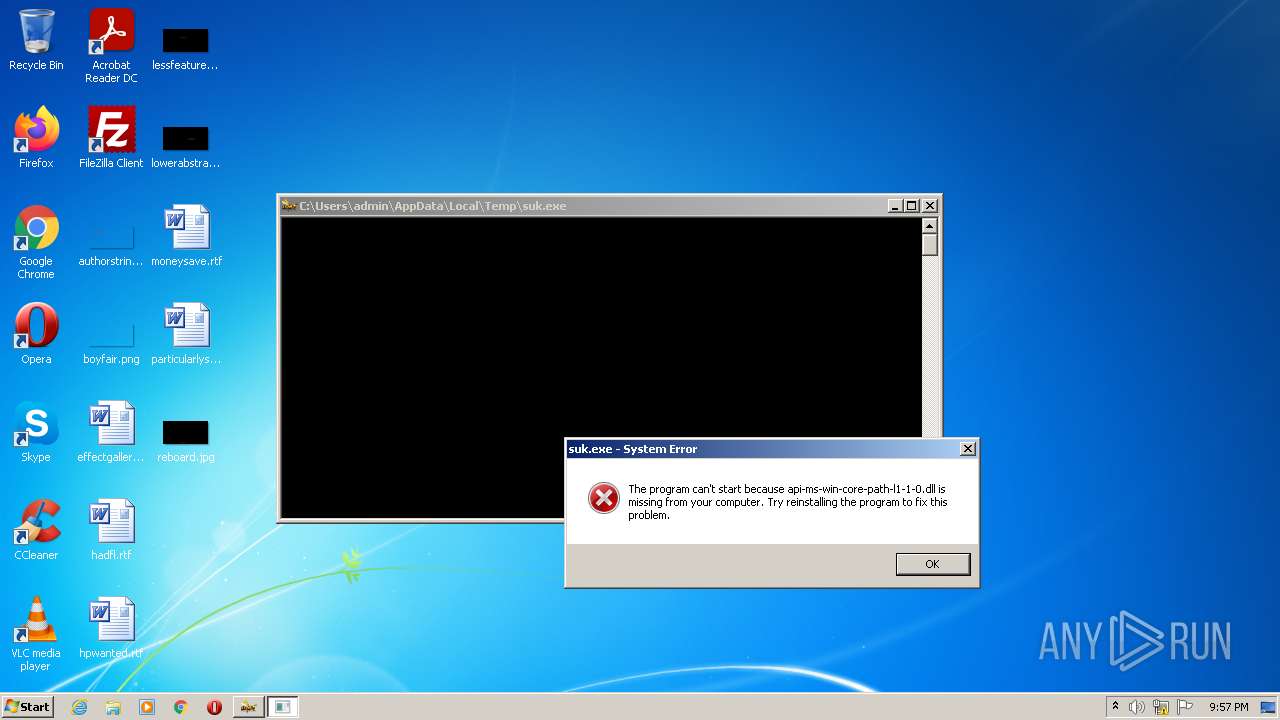
| download: | suk.exe |
| Full analysis: | https://app.any.run/tasks/23fed483-c0ca-4cdd-8d18-13cd3ea31caf |
| Verdict: | Malicious activity |
| Analysis date: | September 29, 2022, 20:56:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 29C5707B4F3626606777FB4D66F55FB0 |
| SHA1: | 1B5B269DD23A72C5CB6EC6F80B0D6210F552D87B |
| SHA256: | 983822688D74EF6341F33A8A6B7FF476094678E373E9934D8B749ED3ED61BFBC |
| SSDEEP: | 393216:NbtwR5J3e3/TehYYfkP1UricCyCdN7mUh/CiIi02czJo:r0TeLyYYfE1UricCyCdN7mECiz02Y |
MALICIOUS
Drops executable file immediately after starts
- suk.exe (PID: 1844)
Loads dropped or rewritten executable
- suk.exe (PID: 4028)
SUSPICIOUS
Checks supported languages
- suk.exe (PID: 1844)
- suk.exe (PID: 4028)
Reads the computer name
- suk.exe (PID: 1844)
Drops a file with a compile date too recent
- suk.exe (PID: 1844)
Application launched itself
- suk.exe (PID: 1844)
Executable content was dropped or overwritten
- suk.exe (PID: 1844)
INFO
Dropped object may contain Bitcoin addresses
- suk.exe (PID: 1844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 2022-Sep-29 18:20:09 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 248 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2022-Sep-29 18:20:09 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 135672 | 135680 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65066 |
.rdata | 143360 | 52240 | 52736 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.97303 |
.data | 196608 | 63596 | 3072 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.67312 |
.rsrc | 262144 | 163840 | 163840 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.41559 |
.reloc | 425984 | 6828 | 7168 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.5413 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
0 | 3.06388 | 118 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
1 | 2.11443 | 67624 | Latin 1 / Western European | UNKNOWN | RT_ICON |
2 | 2.37569 | 38056 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 2.47663 | 21640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 2.37972 | 16936 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 2.56973 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 2.7517 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 2.99211 | 2440 | Latin 1 / Western European | UNKNOWN | RT_ICON |
8 | 4.37821 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
1 (#2) | 5.29005 | 1422 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
Imports
ADVAPI32.dll |
KERNEL32.dll |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1844 | "C:\Users\admin\AppData\Local\Temp\suk.exe" | C:\Users\admin\AppData\Local\Temp\suk.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 4028 | "C:\Users\admin\AppData\Local\Temp\suk.exe" | C:\Users\admin\AppData\Local\Temp\suk.exe | — | suk.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
15
Read events
15
Write events
0
Delete events
0
Modification events
Executable files
74
Suspicious files
2
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_Salsa20.pyd | executable | |
MD5:E372119201D5E3D9DEE6C0F92C45528C | SHA256:5CF3325E5389E8AE3EF8B5624091FF52681FC19470A8DE46123A13B5911B712B | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_cbc.pyd | executable | |
MD5:48AD84C24A5C163660054E2F560EACDE | SHA256:6106E21A69E5FD53C1897192DECF771D1B679A6588BC7E1A35E915B47D269F03 | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_arc2.pyd | executable | |
MD5:44D2C7A178D403E771D944950374D865 | SHA256:6379C58CC3C7017DB249B14D8708678420872D165040278ACEC947C4713E598F | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_des.pyd | executable | |
MD5:8366789AD581FB576CEFCC38960D3DA2 | SHA256:A83576B92A9078DEEEF3EFEC67BD6C6EC52C3B067879FA6220F20585A766E23F | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_des3.pyd | executable | |
MD5:9E0A316249417889E9BBBD73806A2E26 | SHA256:03CFEDF500026479E1AFF3B2C1FAE56FF39BFC0BDE17A97687EB69D6BBDD35C6 | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_ctr.pyd | executable | |
MD5:395F8173A0828691C137E03D4C0B751E | SHA256:0CA8E51B9A5F677CF273F34691D5B81EF40DA0F28C6367926CF7D07469B9ECFE | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_ocb.pyd | executable | |
MD5:79C173339C095B33CCDDBC0F68A6C522 | SHA256:8D8087231FA634389ECE18BA2CA8D64645859BB9ADF0BC2EDD5736C339142E86 | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_cfb.pyd | executable | |
MD5:496DD306BE58A199CD62D9037CE8F60A | SHA256:172C713C4837D88FCA5BDFCBB9CBE1BB827CA537D2C17214D0FB6DDA407ED04A | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_blowfish.pyd | executable | |
MD5:719A46CA7041302B3F8A7CE8CE8DC619 | SHA256:4A4EE02533B1FF51B6F13781D57FB7FF0FA11B2A219AF601EF5BE6B4E01D9F7D | |||
| 1844 | suk.exe | C:\Users\admin\AppData\Local\Temp\_MEI18442\Crypto\Cipher\_raw_ecb.pyd | executable | |
MD5:2B487A27439563DBFCC765A459CF080C | SHA256:A90DC0677A75B60659A562AA3797A0639EBE91BEBC5943B8C90FC69F8CF0F69A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report