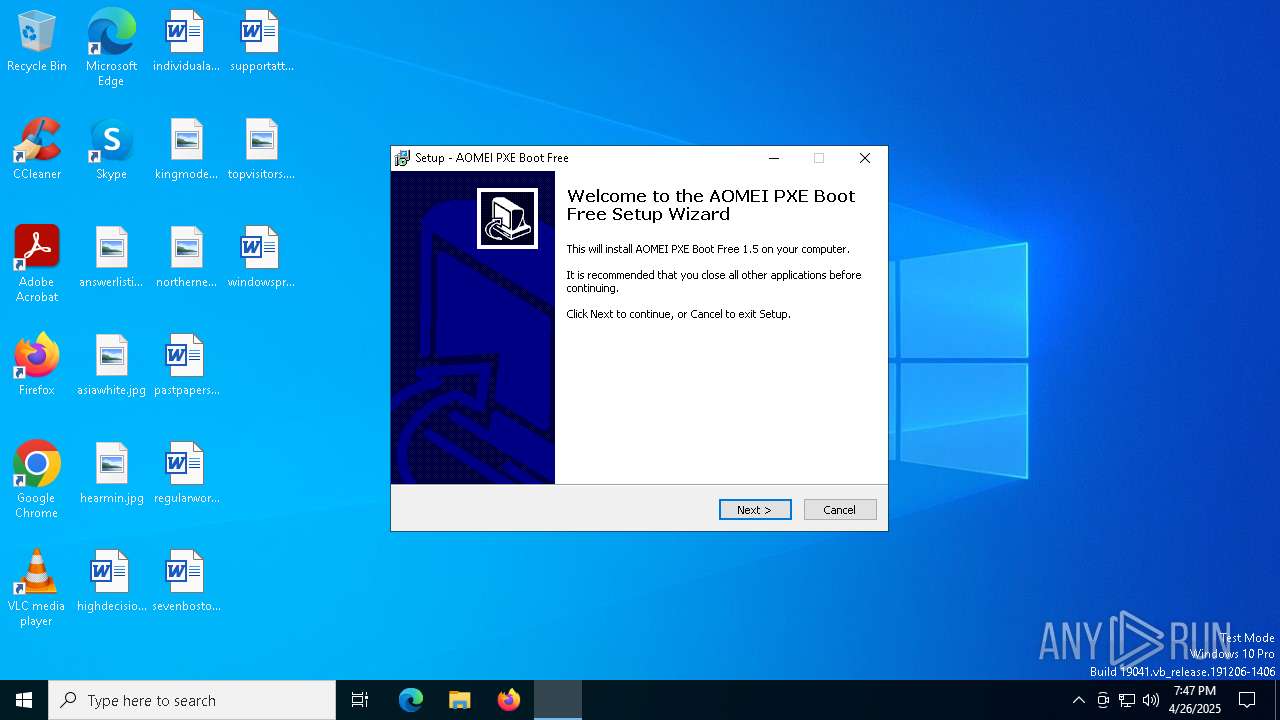
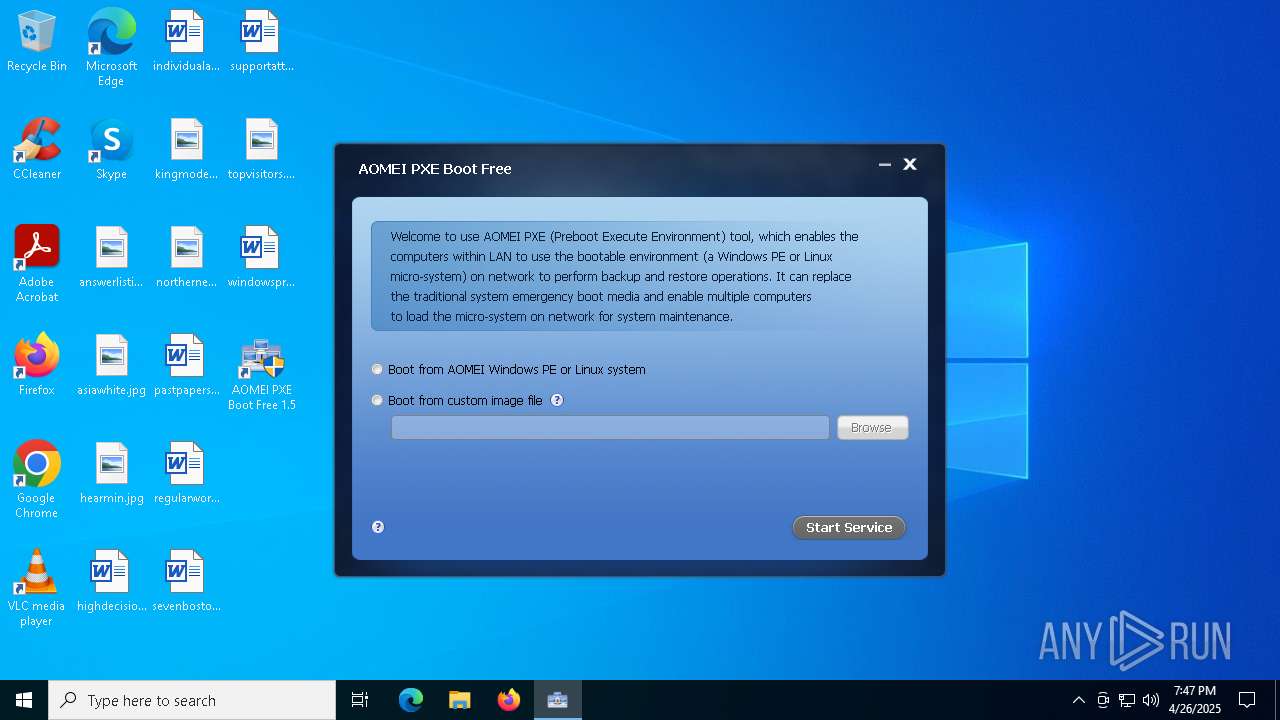
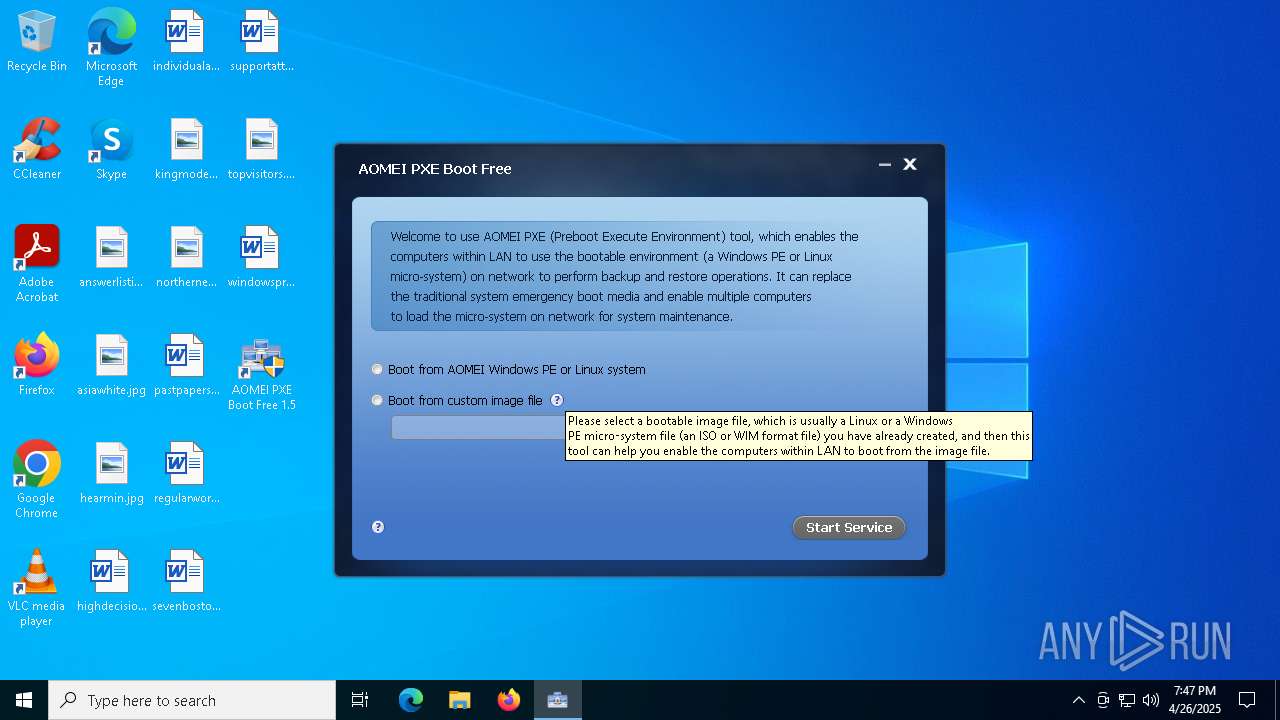
| File name: | PXEBoot.exe |
| Full analysis: | https://app.any.run/tasks/6b6009a7-6cc8-48b4-af21-504be971382d |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2025, 19:47:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 3256DBF718362D0C99963C0B39894A81 |
| SHA1: | 95286AC18E9B81C2A68412C406B791DFE8B91400 |
| SHA256: | 982BB7FDF2AA85A0E233462B9B47F368AD7B4FD8ACACF8185C0B5C3B96286796 |
| SSDEEP: | 393216:ZlC1Px/Q6XT3XuqqIFMtWs/+Gh+hC0/tew3:Zlsx//TVFMtWsGGYC0Mw3 |
MALICIOUS
Executing a file with an untrusted certificate
- PXEBoot.exe (PID: 4892)
- PXEBoot.exe (PID: 6728)
- PXEBoot.exe (PID: 5548)
- PXEBoot.exe (PID: 4244)
SUSPICIOUS
Executable content was dropped or overwritten
- PXEBoot.exe (PID: 4892)
- PXEBoot.tmp (PID: 4040)
Uses NETSH.EXE to add a firewall rule or allowed programs
- PXEBoot.exe (PID: 4244)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- PXEBoot.exe (PID: 4244)
Process drops legitimate windows executable
- PXEBoot.tmp (PID: 4040)
Reads the Windows owner or organization settings
- PXEBoot.tmp (PID: 4040)
The process drops C-runtime libraries
- PXEBoot.tmp (PID: 4040)
INFO
Create files in a temporary directory
- PXEBoot.exe (PID: 4892)
- PXEBoot.tmp (PID: 4040)
Reads the computer name
- PXEBoot.tmp (PID: 4040)
- PXEBoot.exe (PID: 4244)
Checks supported languages
- PXEBoot.exe (PID: 4892)
- PXEBoot.tmp (PID: 4040)
- PXEBoot.exe (PID: 4244)
Creates files or folders in the user directory
- PXEBoot.tmp (PID: 4040)
Manual execution by a user
- PXEBoot.exe (PID: 5548)
- PXEBoot.exe (PID: 4244)
Detects InnoSetup installer (YARA)
- PXEBoot.exe (PID: 4892)
Compiled with Borland Delphi (YARA)
- PXEBoot.exe (PID: 4892)
Creates files in the program directory
- PXEBoot.tmp (PID: 4040)
The sample compiled with english language support
- PXEBoot.tmp (PID: 4040)
Creates a software uninstall entry
- PXEBoot.tmp (PID: 4040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:12:20 14:16:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 86016 |
| InitializedDataSize: | 53760 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16478 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.0.0 |
| ProductVersionNumber: | 1.5.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
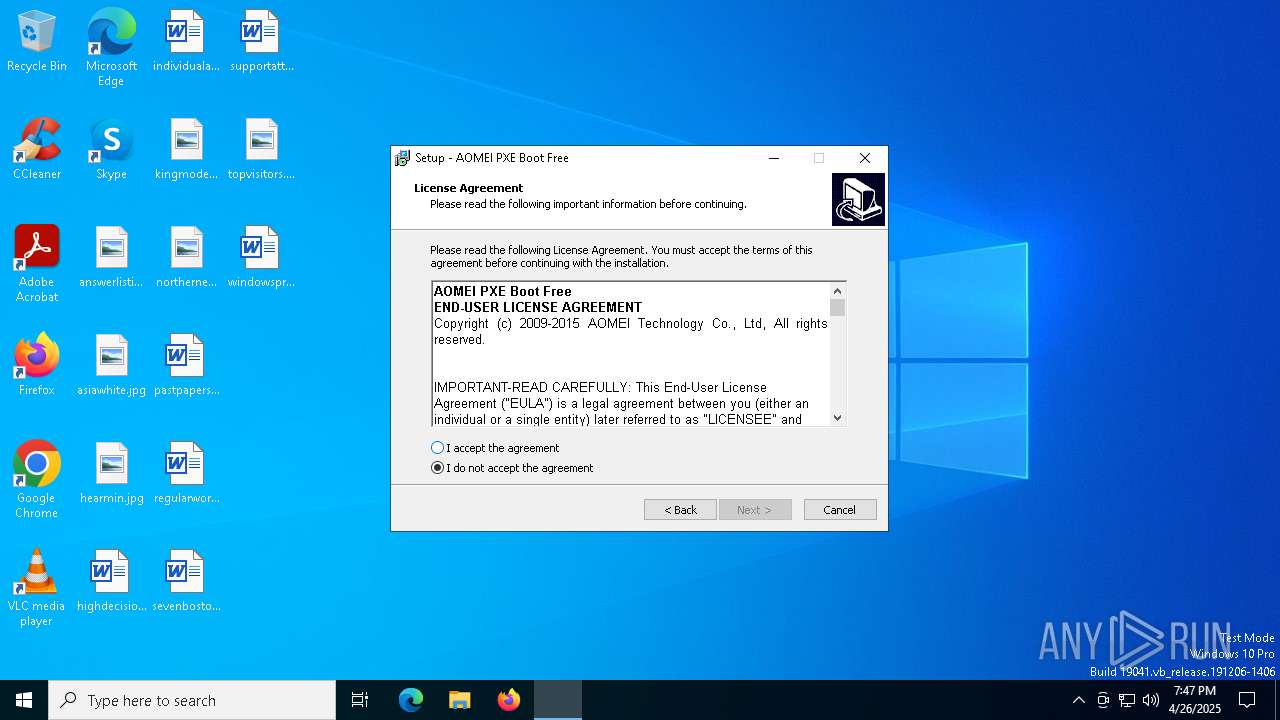
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | AOMEI Technology Co., Ltd. |
| FileDescription: | |
| FileVersion: | 1.5 |
| LegalCopyright: | |
| ProductName: | |
| ProductVersion: | 1.5 |
Total processes
141
Monitored processes
9
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | C:\WINDOWS\system32\netsh.exe advfirewall firewall add rule name = "ampxe" dir=in program = "C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\PXEBoot.exe" action="allow" | C:\Windows\SysWOW64\netsh.exe | — | PXEBoot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | "C:\Users\admin\AppData\Local\Temp\is-FDVBS.tmp\PXEBoot.tmp" /SL5="$802C6,12730523,140800,C:\Users\admin\AppData\Local\Temp\PXEBoot.exe" | C:\Users\admin\AppData\Local\Temp\is-FDVBS.tmp\PXEBoot.tmp | PXEBoot.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4120 | C:\WINDOWS\system32\netsh.exe advfirewall firewall delete rule name = "ampxe" | C:\Windows\SysWOW64\netsh.exe | — | PXEBoot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\PXEBoot.exe" | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\PXEBoot.exe | explorer.exe | ||||||||||||
User: admin Company: AOMEI Tech Co., Ltd. Integrity Level: HIGH Description: AOMEI PXE Boot Free Version: 1, 5, 0, 0 Modules
| |||||||||||||||
| 4892 | "C:\Users\admin\AppData\Local\Temp\PXEBoot.exe" | C:\Users\admin\AppData\Local\Temp\PXEBoot.exe | explorer.exe | ||||||||||||
User: admin Company: AOMEI Technology Co., Ltd. Integrity Level: HIGH Description: Exit code: 0 Version: 1.5 Modules
| |||||||||||||||
| 5548 | "C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\PXEBoot.exe" | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\PXEBoot.exe | — | explorer.exe | |||||||||||
User: admin Company: AOMEI Tech Co., Ltd. Integrity Level: MEDIUM Description: AOMEI PXE Boot Free Exit code: 3221226540 Version: 1, 5, 0, 0 Modules
| |||||||||||||||
| 5868 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6728 | "C:\Users\admin\AppData\Local\Temp\PXEBoot.exe" | C:\Users\admin\AppData\Local\Temp\PXEBoot.exe | — | explorer.exe | |||||||||||
User: admin Company: AOMEI Technology Co., Ltd. Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 1.5 Modules
| |||||||||||||||
Total events
833
Read events
810
Write events
23
Delete events
0
Modification events
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AOMEI PXE Boot Free |
| Operation: | write | Name: | AOMEI PXE Boot Free |
Value: 1.0 | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AOMEI PXE Boot Free |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\unins000.exe | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.4.3 (u) | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
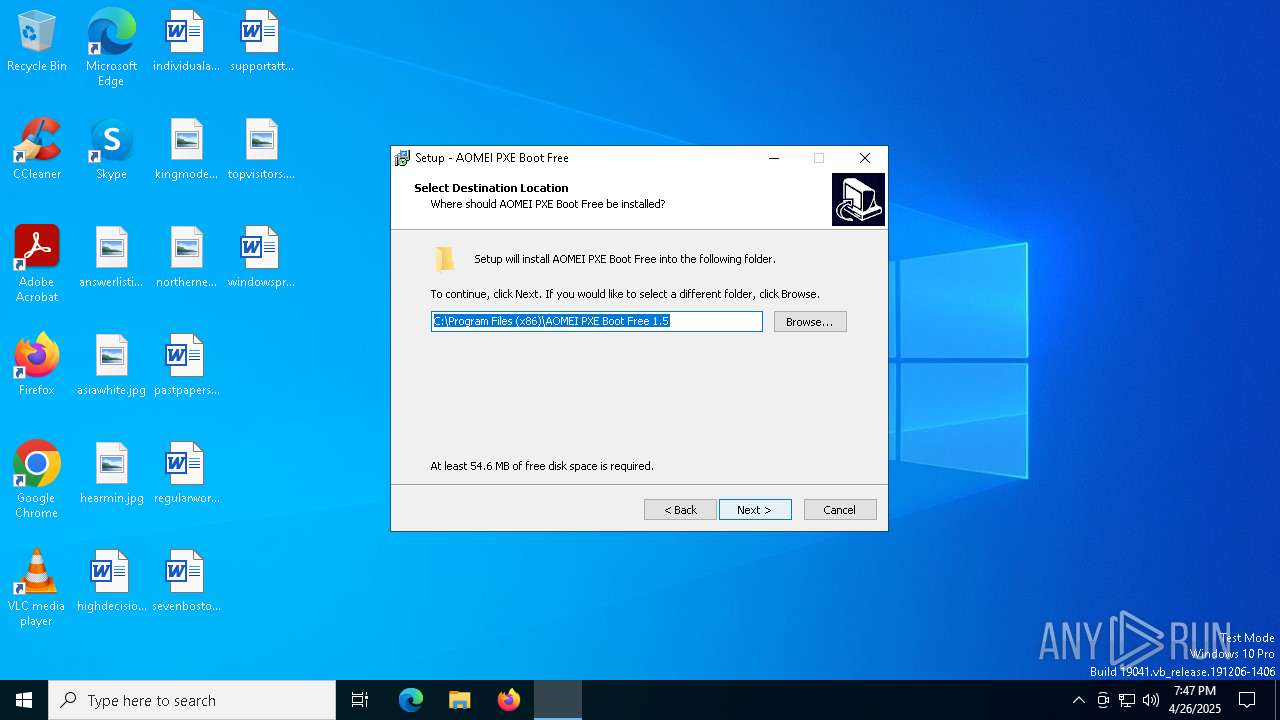
Value: C:\Program Files (x86)\AOMEI PXE Boot Free 1.5 | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\ | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: AOMEI PXE Boot Free 1.5 | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: desktopicon,quicklaunchicon | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: | |||
| (PID) Process: | (4040) PXEBoot.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{A83692F5-3E9B-4E95-9E7E-B5DF5566009D}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: en | |||
Executable files
49
Suspicious files
50
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\is-HKRPI.tmp | executable | |
MD5:0DF42DBD2137C225B14395F1F410AB6D | SHA256:E5474591299AE03DF404A005EBF03C394B92EEFD2DC747B9546E38F359E1E2D9 | |||
| 4892 | PXEBoot.exe | C:\Users\admin\AppData\Local\Temp\is-FDVBS.tmp\PXEBoot.tmp | executable | |
MD5:B277E6AC242FCBC37F4D03E1528949C1 | SHA256:9461AE8A13A57C0D8490916DC1E1BB20CB0C171B9852D0846A03C4C4D212F204 | |||
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\is-J4JAU.tmp | executable | |
MD5:689D2164F44644B467B9784125641844 | SHA256:08D7E0222B15B712A7BD26486928229436C329494FDC61AAA0D4FE92EA538708 | |||
| 4040 | PXEBoot.tmp | C:\Users\admin\AppData\Local\Temp\is-A3AGH.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\unins000.exe | executable | |
MD5:0DF42DBD2137C225B14395F1F410AB6D | SHA256:E5474591299AE03DF404A005EBF03C394B92EEFD2DC747B9546E38F359E1E2D9 | |||
| 4040 | PXEBoot.tmp | C:\Users\admin\AppData\Local\Temp\is-A3AGH.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\PXEBoot.exe | executable | |
MD5:689D2164F44644B467B9784125641844 | SHA256:08D7E0222B15B712A7BD26486928229436C329494FDC61AAA0D4FE92EA538708 | |||
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\mfc80u.dll | executable | |
MD5:CCC2E312486AE6B80970211DA472268B | SHA256:18BE5D3C656236B7E3CD6D619D62496FE3E7F66BF2859E460F8AC3D1A6BDAA9A | |||
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\is-RG6A1.tmp | executable | |
MD5:033978C19E56E970C32733EA725969EF | SHA256:3058E1C4C7E63A376072CE5D8C2B165AA12DE787799731C50EC1431E0744B03F | |||
| 4040 | PXEBoot.tmp | C:\Program Files (x86)\AOMEI PXE Boot Free 1.5\ssleay32.dll | executable | |
MD5:033978C19E56E970C32733EA725969EF | SHA256:3058E1C4C7E63A376072CE5D8C2B165AA12DE787799731C50EC1431E0744B03F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.170:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.170:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6148 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |