| File name: | trustedinstaller.bat |
| Full analysis: | https://app.any.run/tasks/b0abf7a5-c346-4e8a-bfd1-5e10a07aab6b |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2024, 19:42:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | A342C02D8B85D351AF8871776FC67DD7 |
| SHA1: | 4B7C7E5697CEE05354F0902A3C40D35C7C892A7D |
| SHA256: | 9802EDA5439017E0B2FE42D53BBEAC75176C52B4383E33D1A4CB445A00B16B8B |
| SSDEEP: | 48:pEQfN2qQUWzp3SjBc8sVsFMsjD7RBW0e1iMhKTCID2wg+7C5:pxIqCR/VsFMsfNEKCID2wRI |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4052)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 5664)
Probably download files using WebClient
- cmd.exe (PID: 4052)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 5664)
- cmd.exe (PID: 1800)
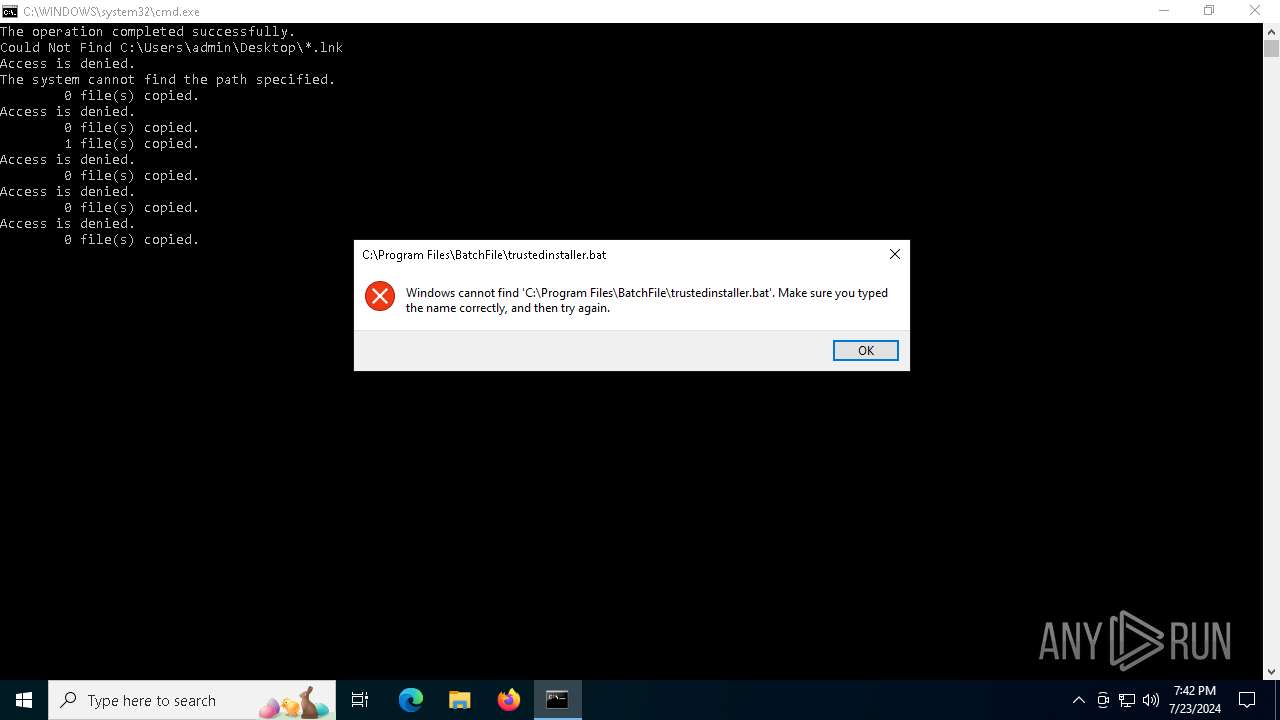
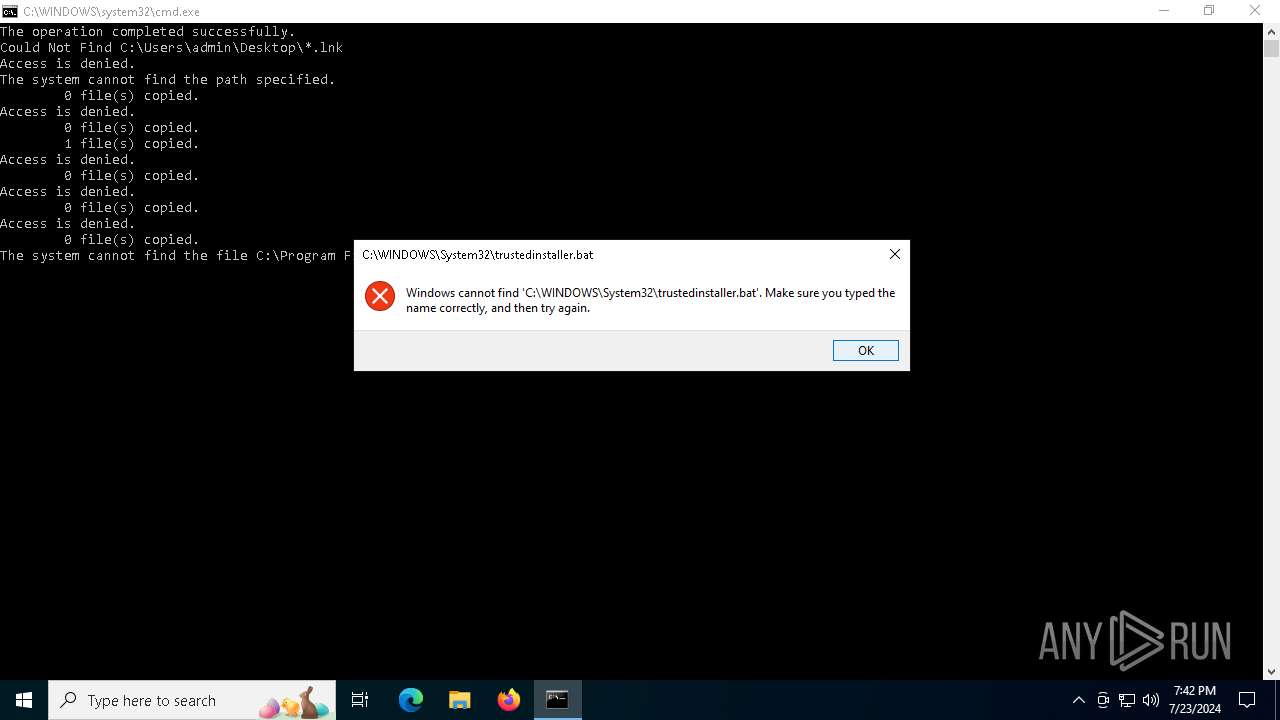
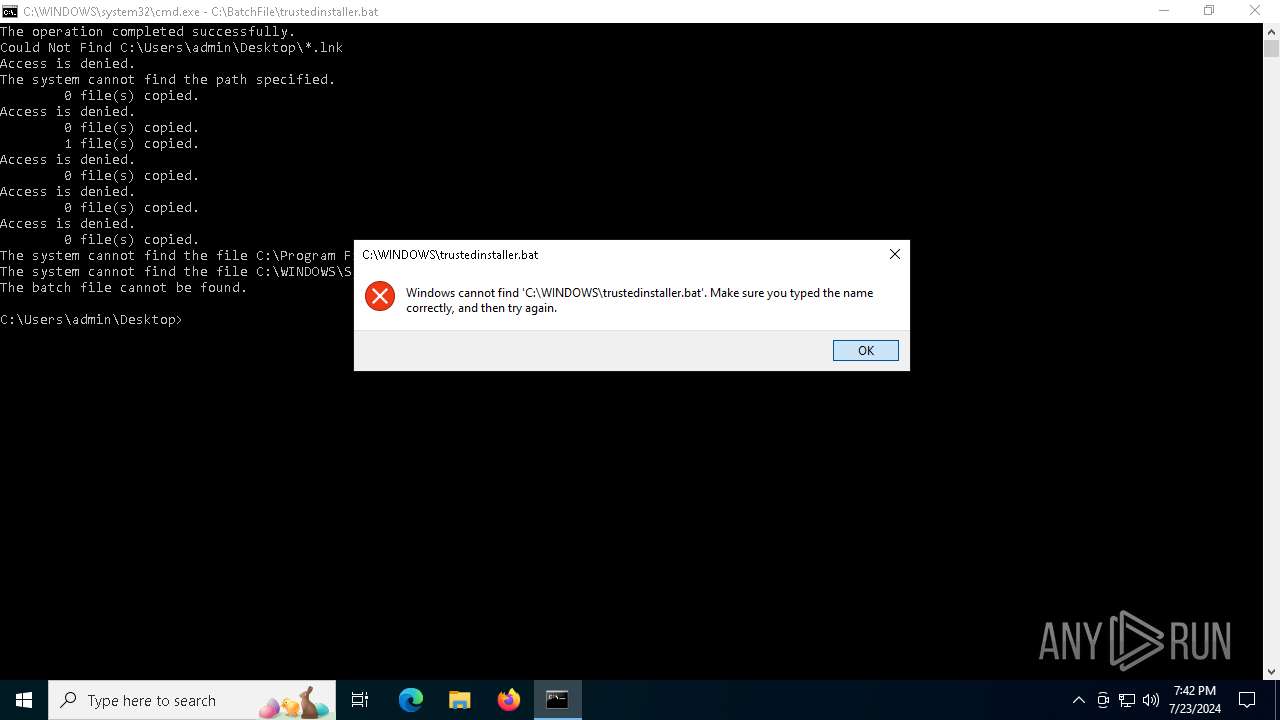
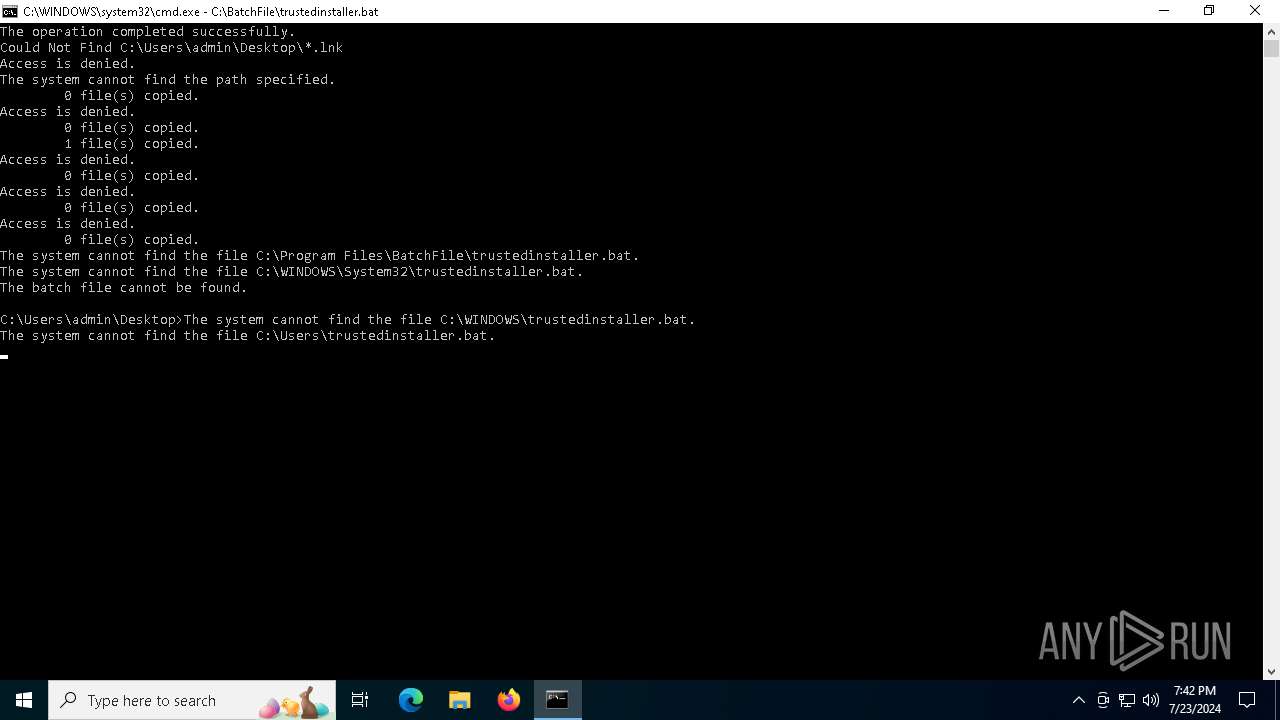
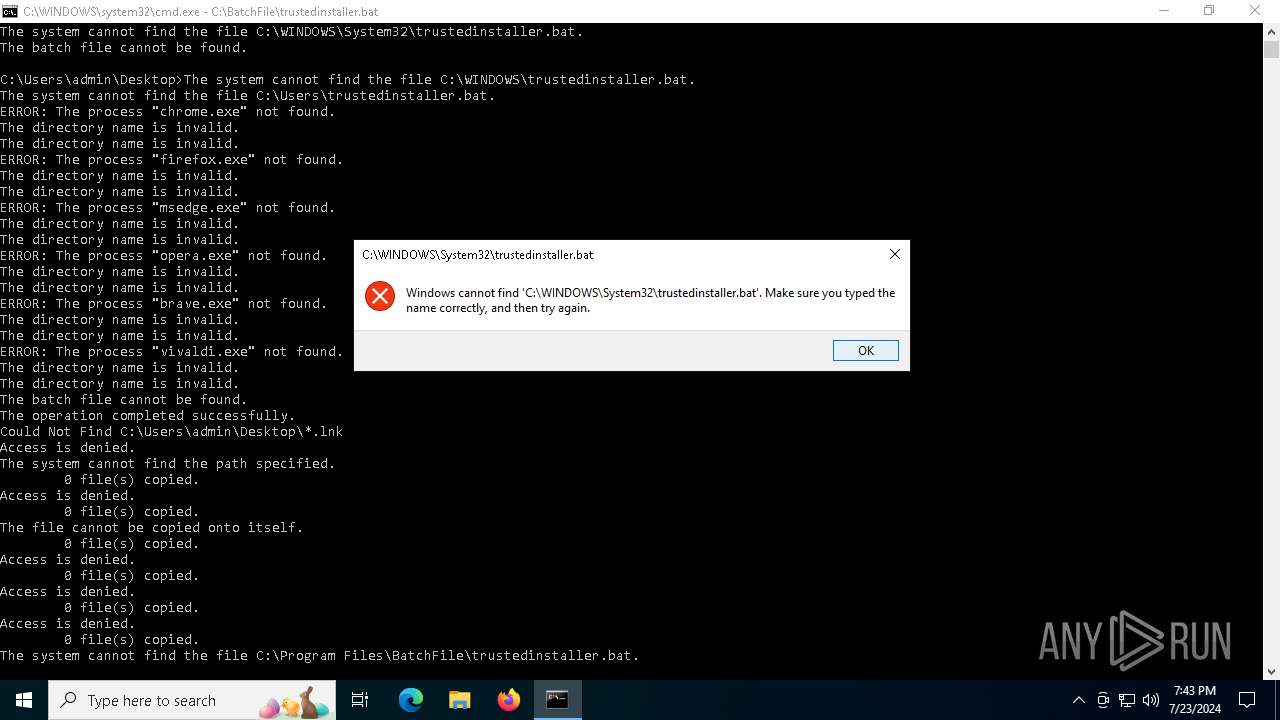
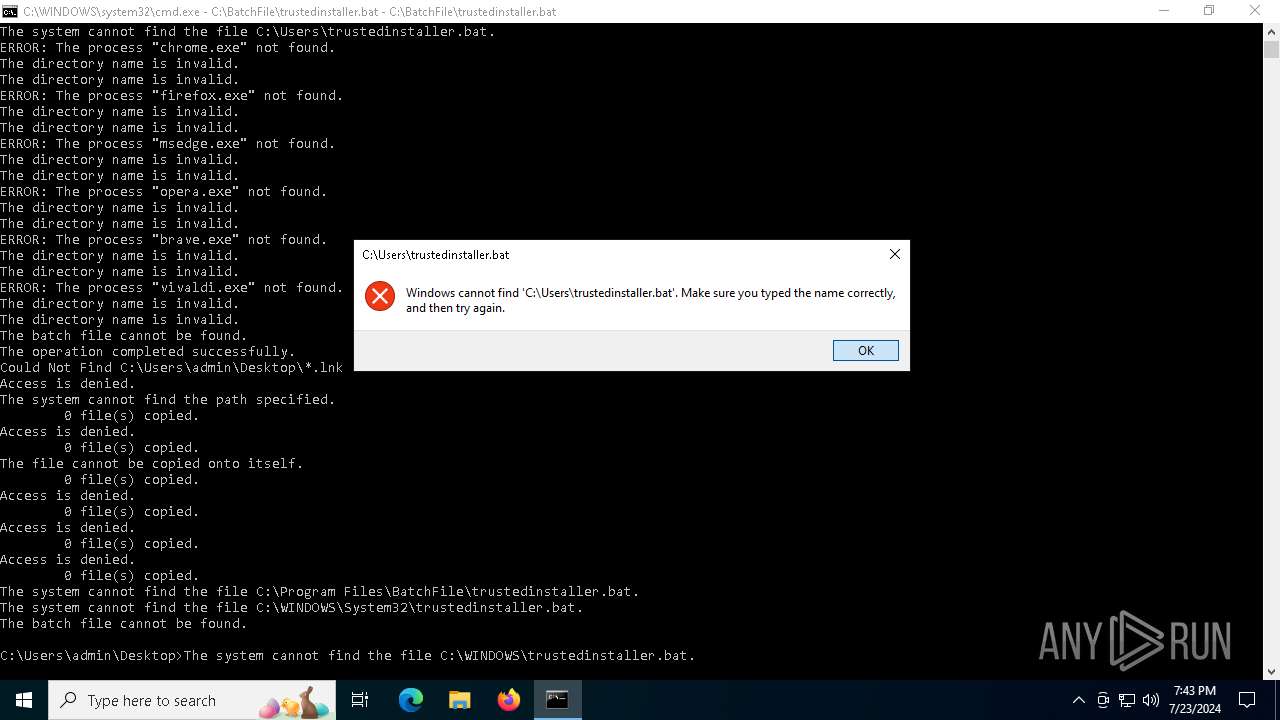
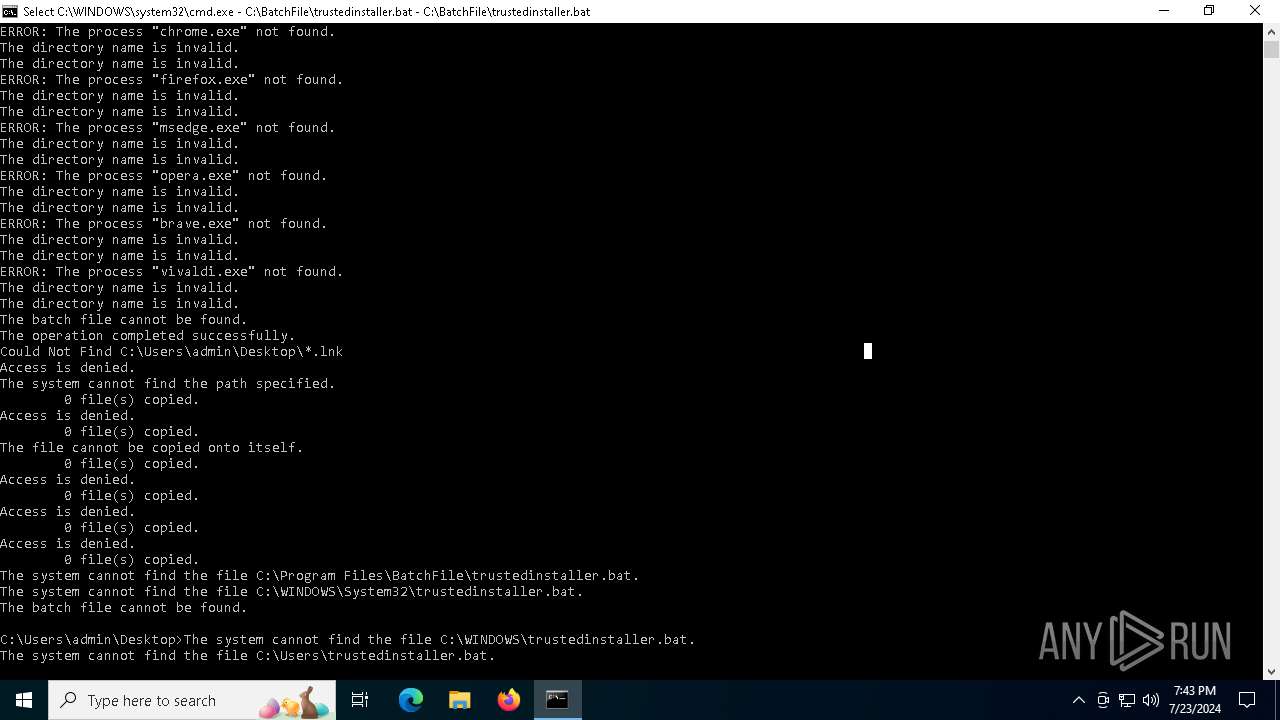
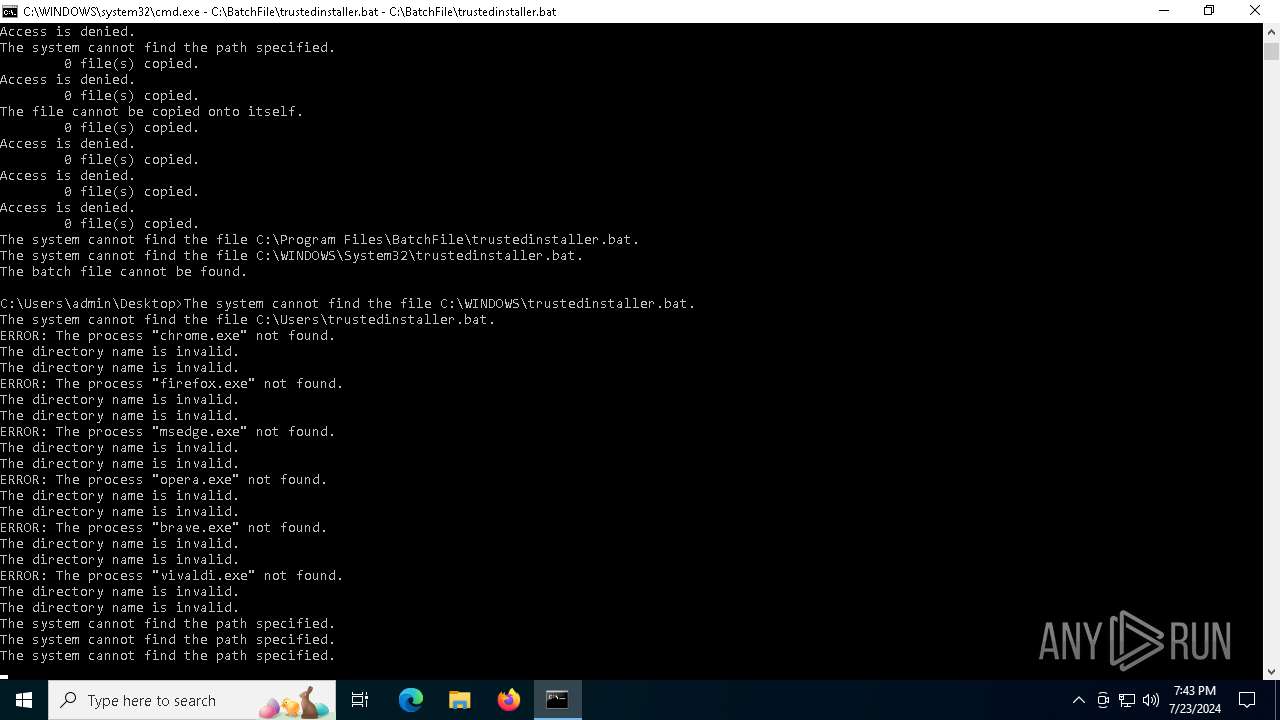
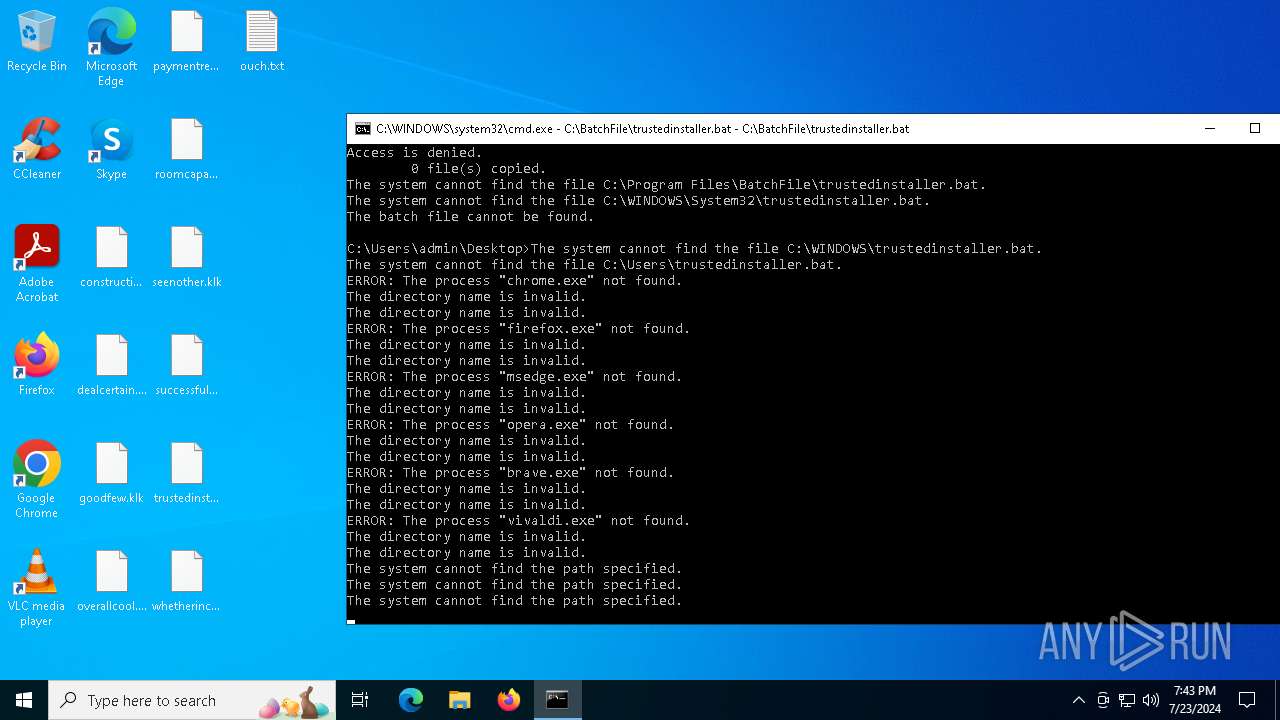
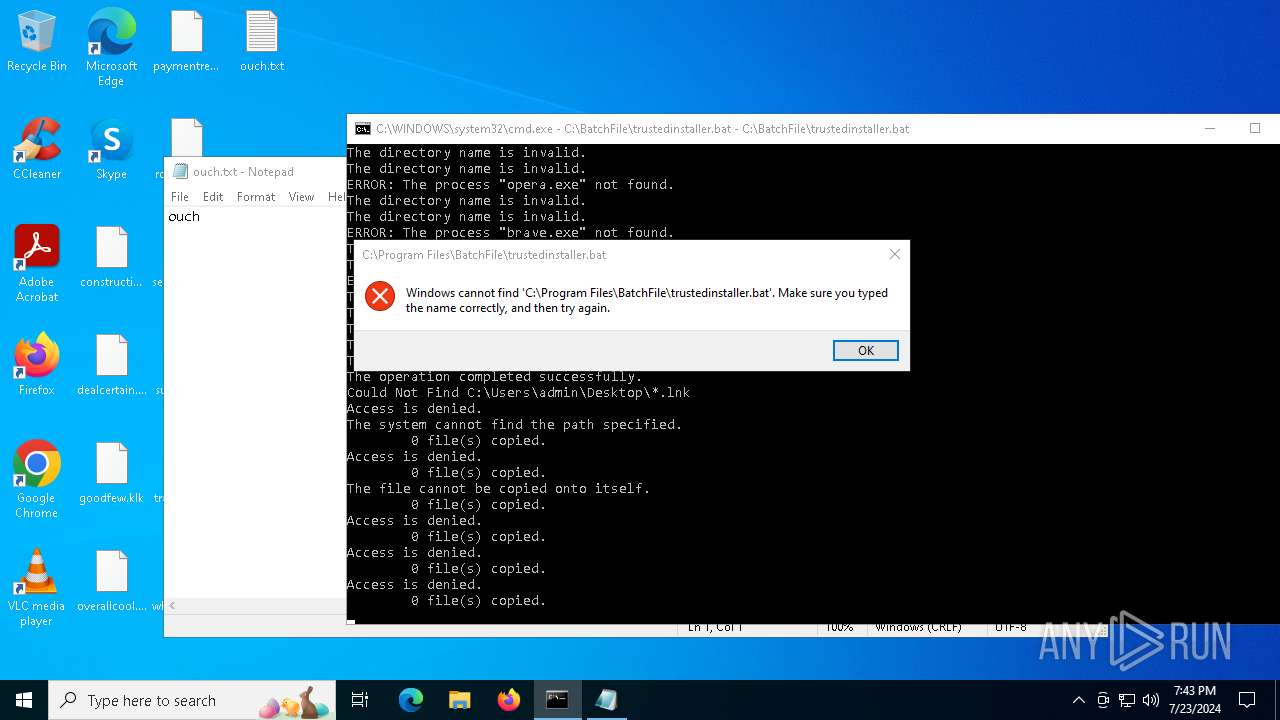
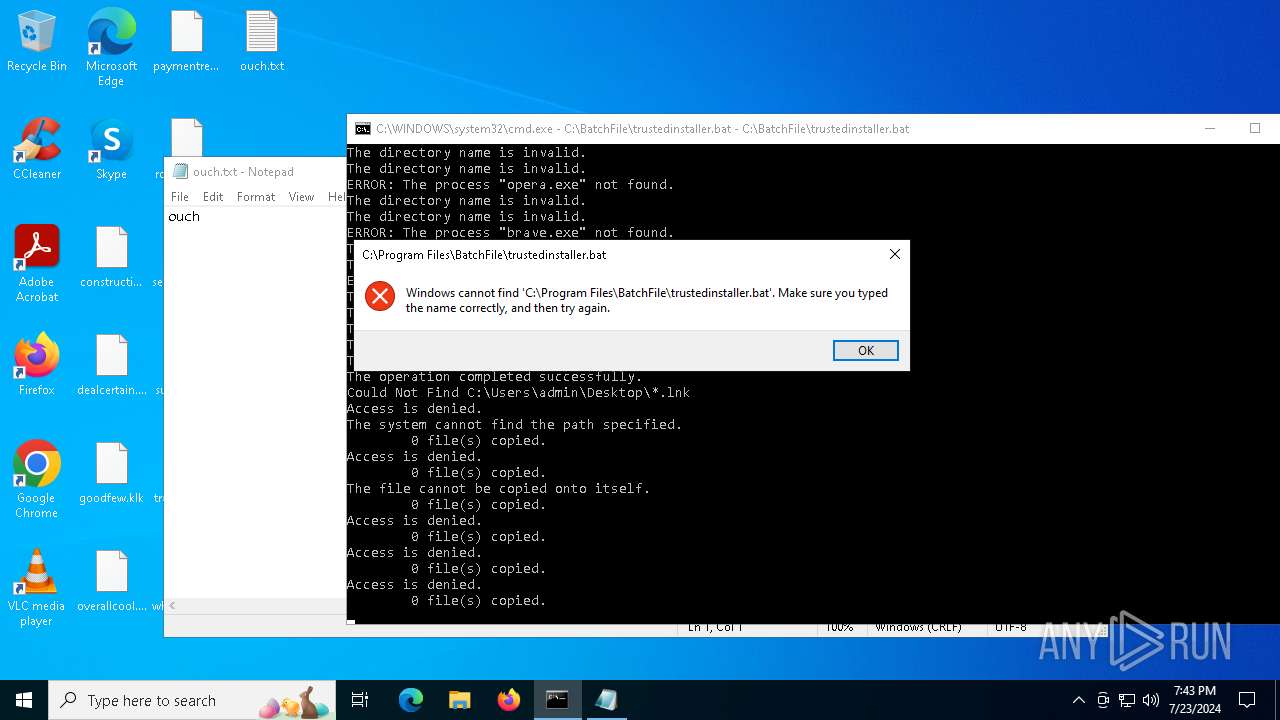
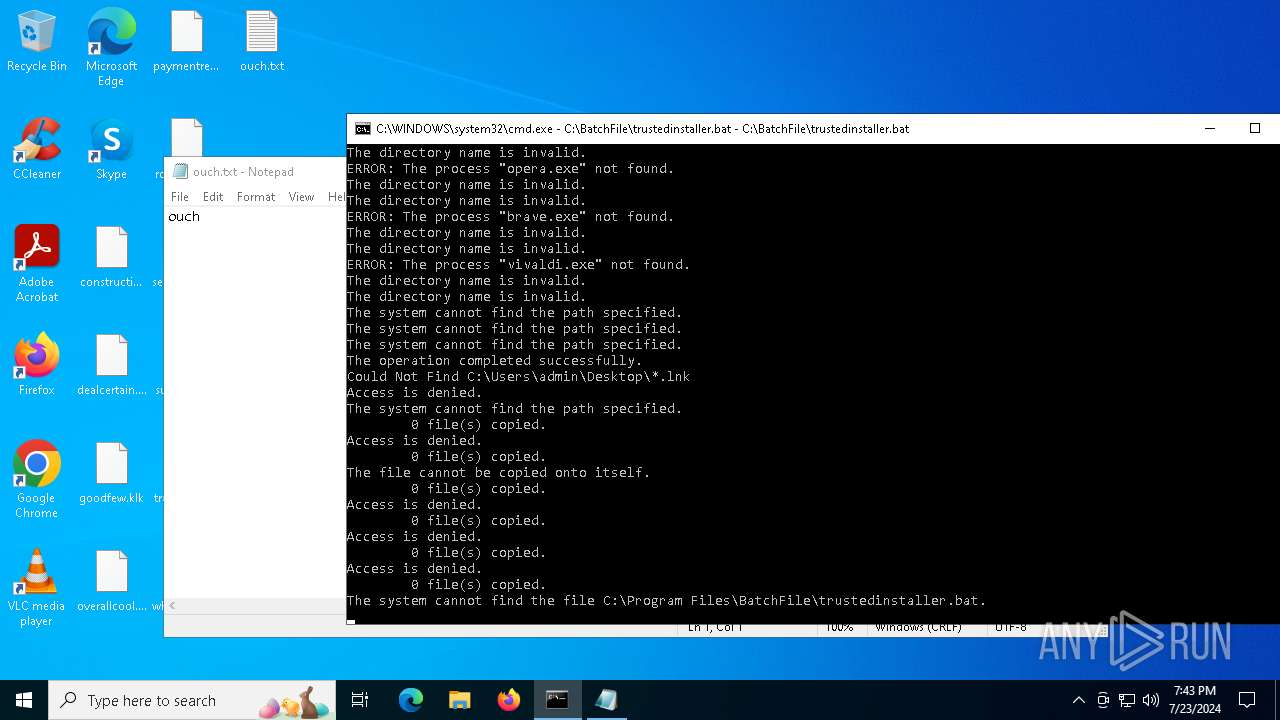
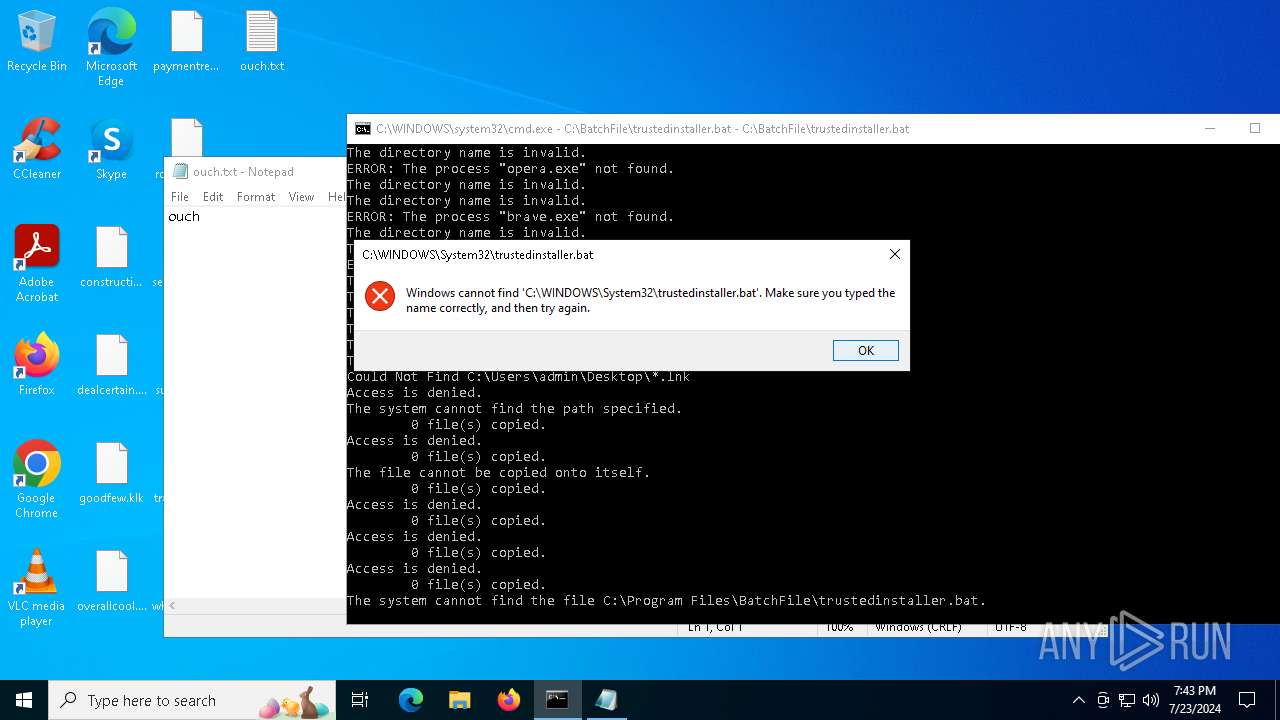
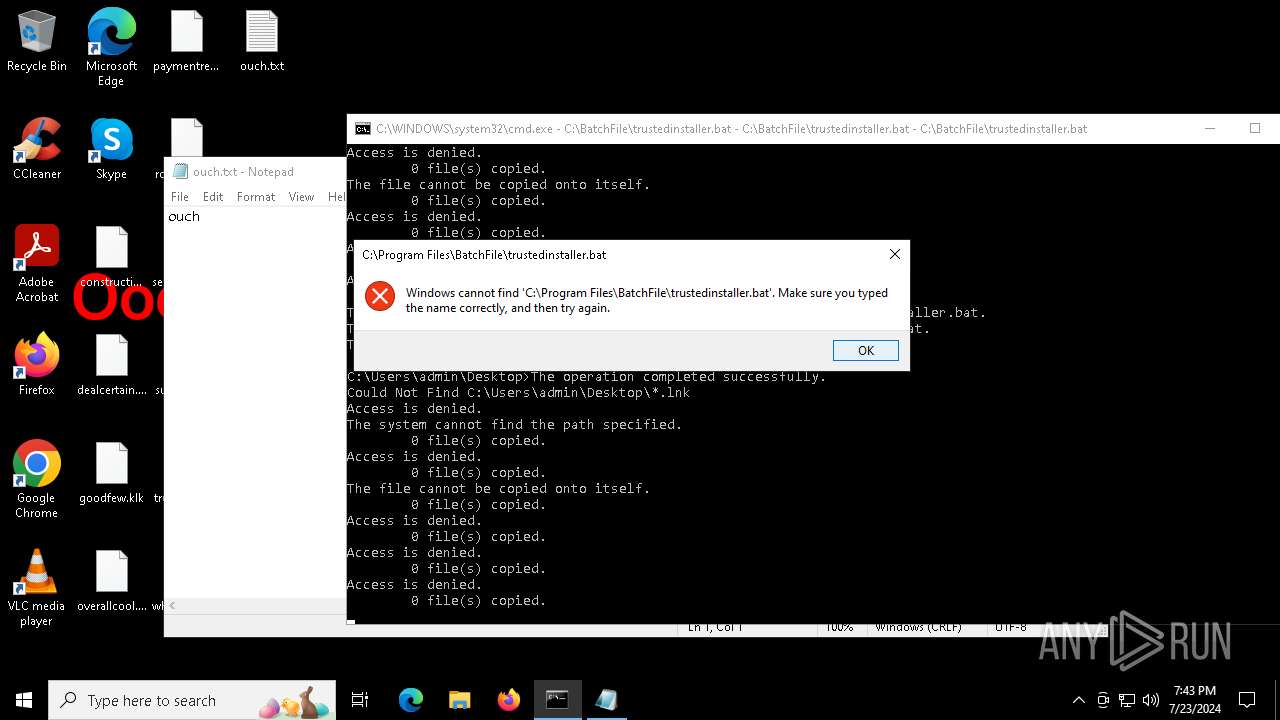
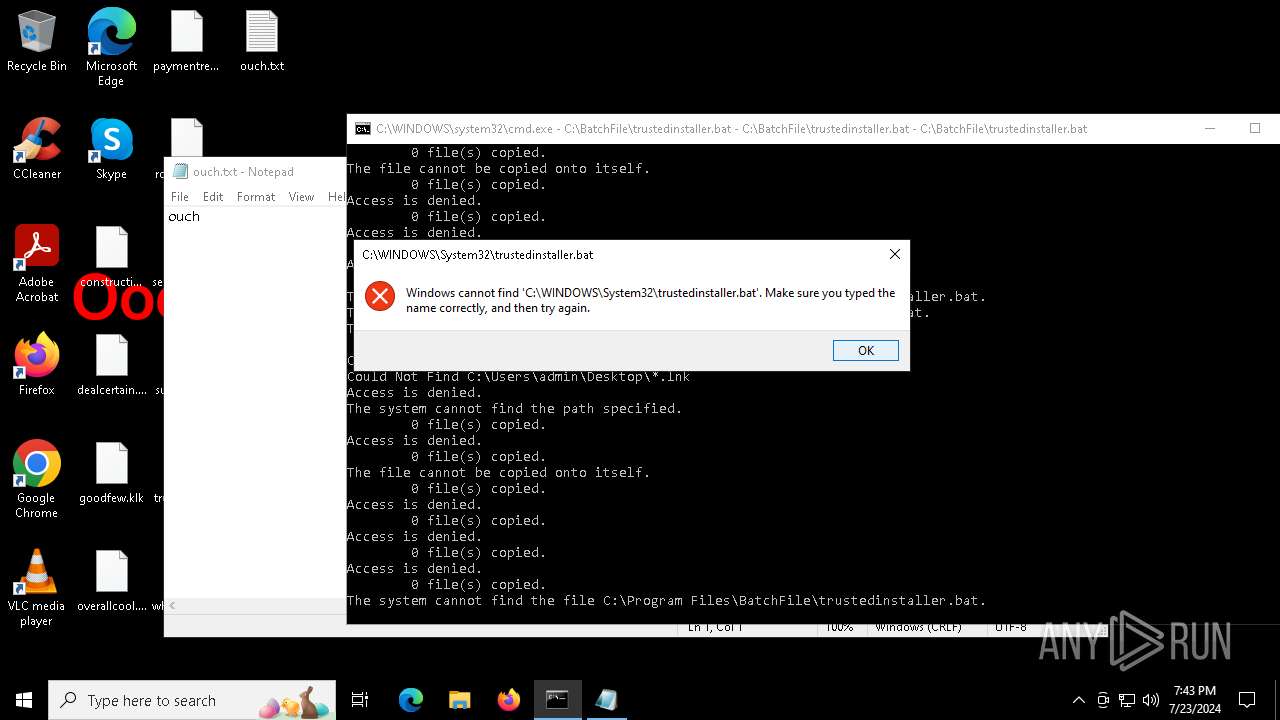
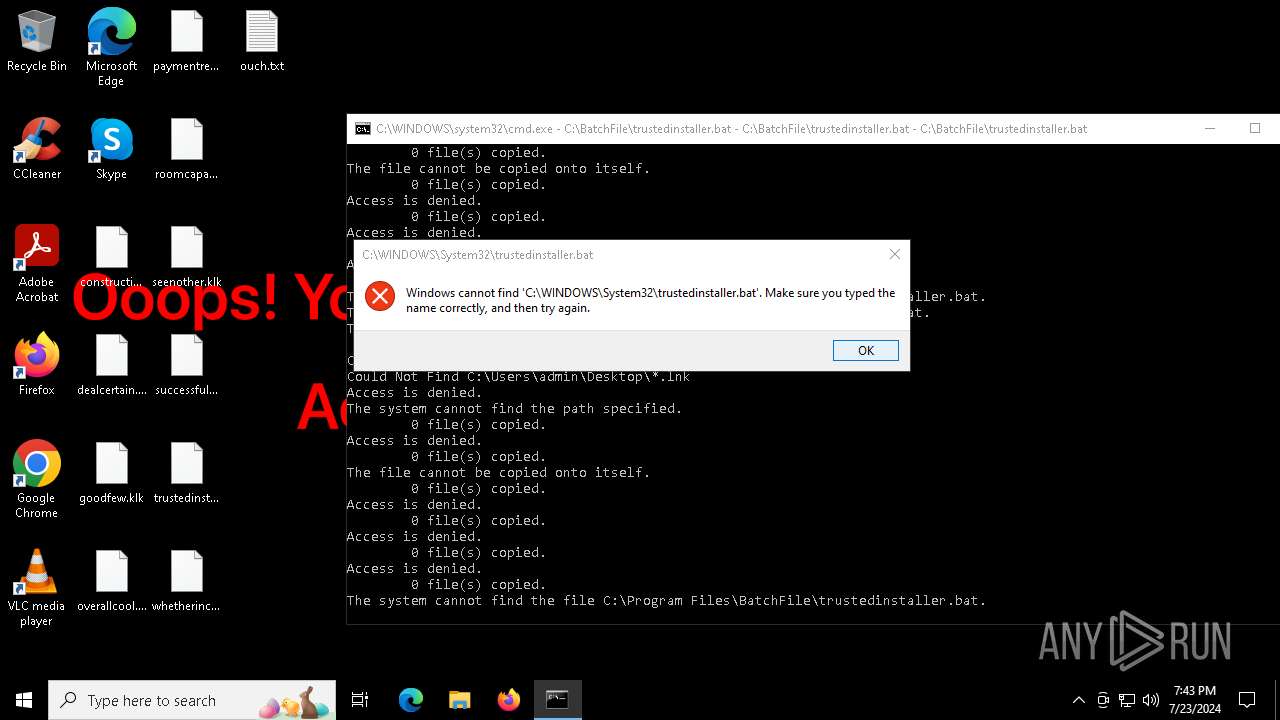
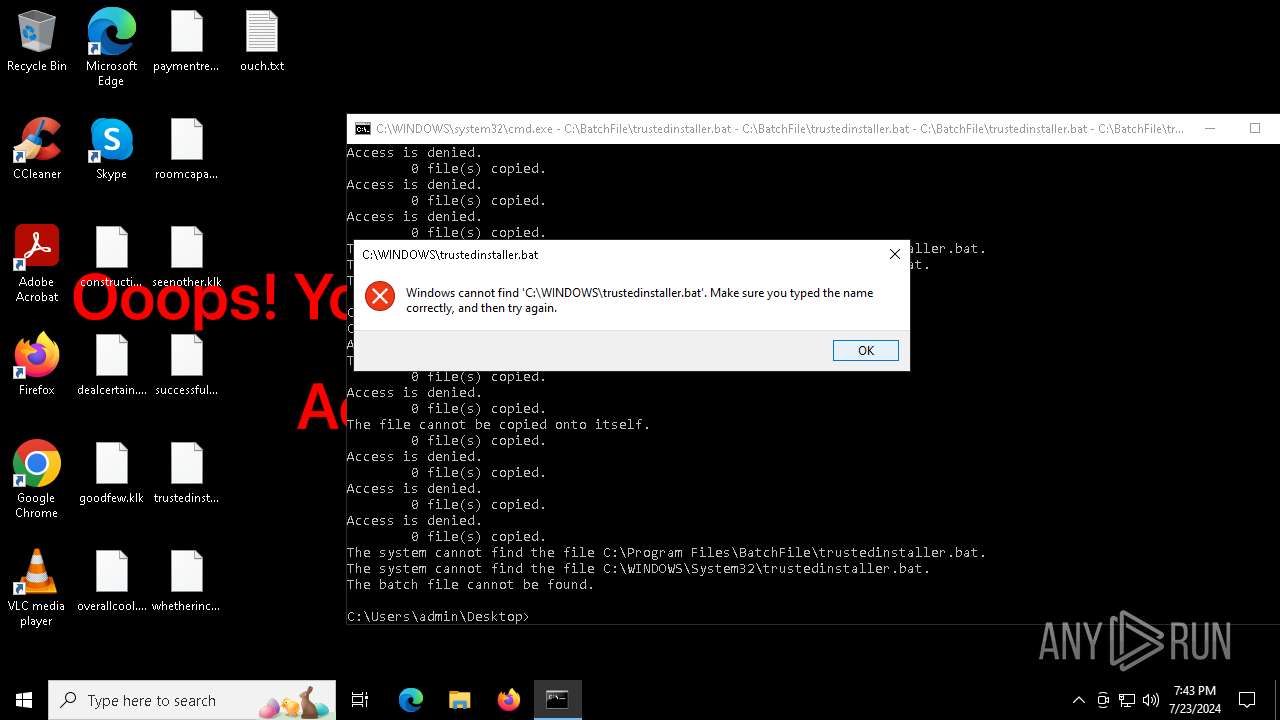
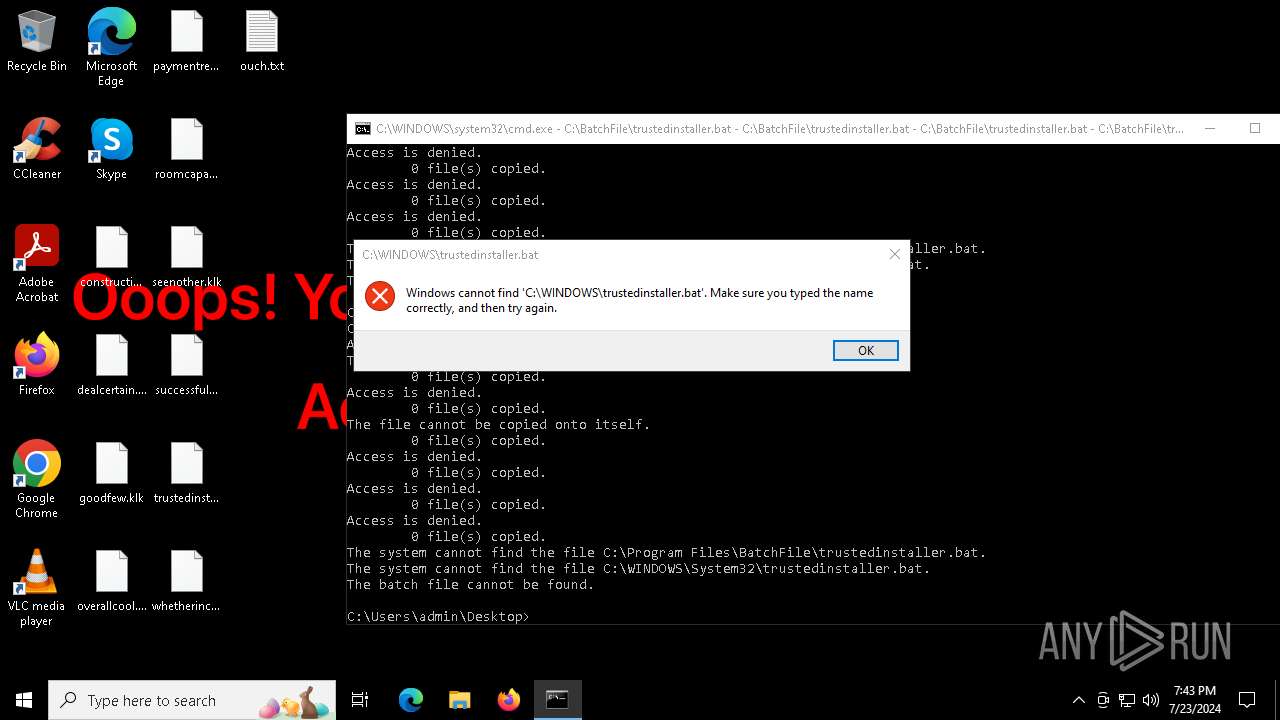
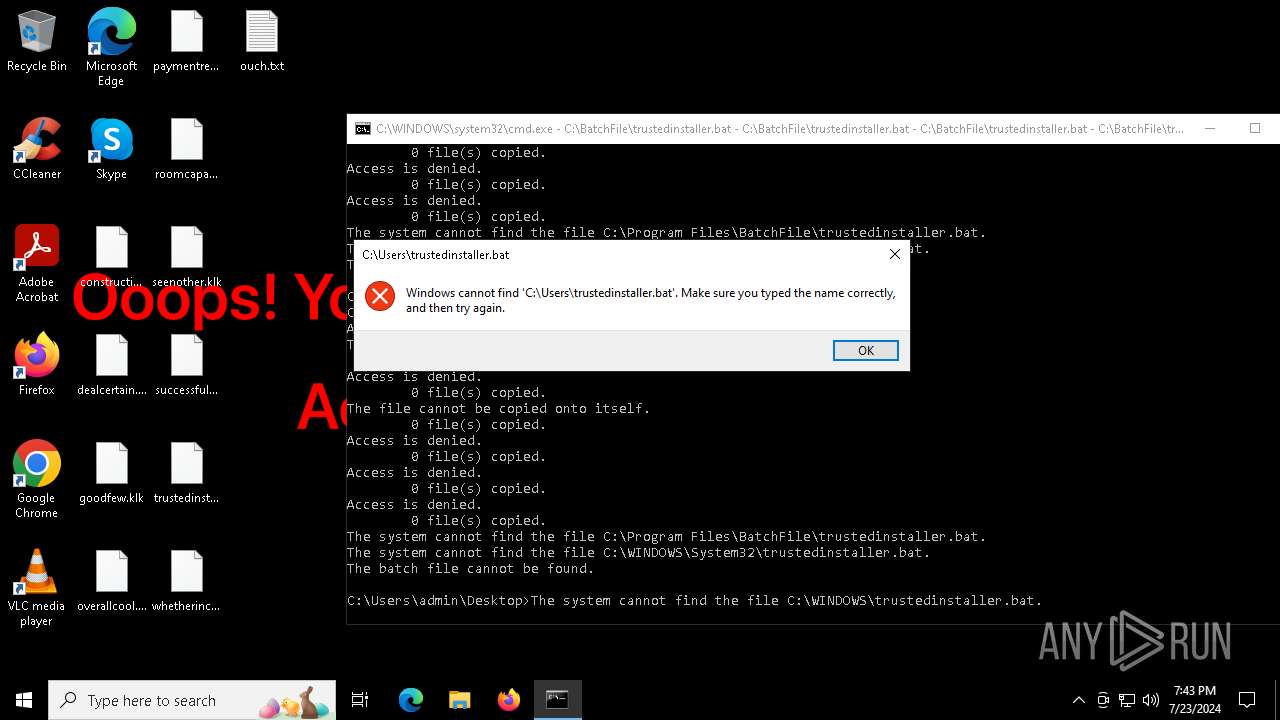
Executing commands from a ".bat" file
- cmd.exe (PID: 4052)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 6636)
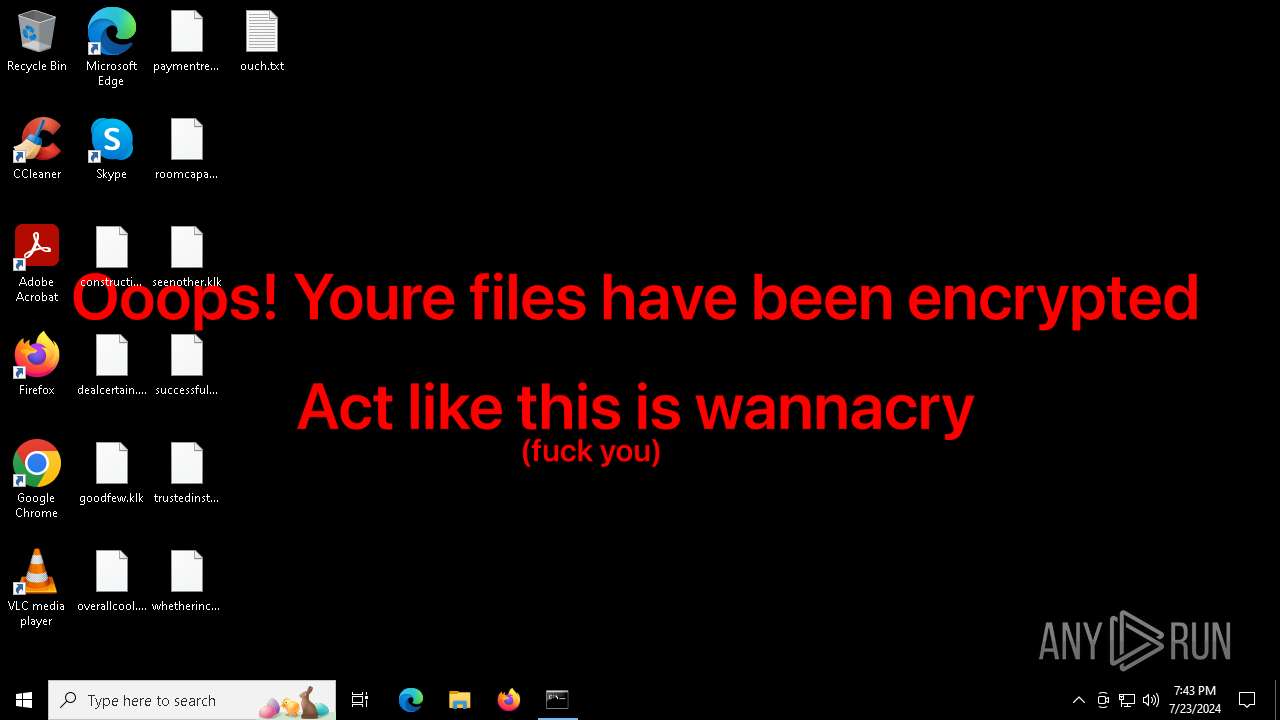
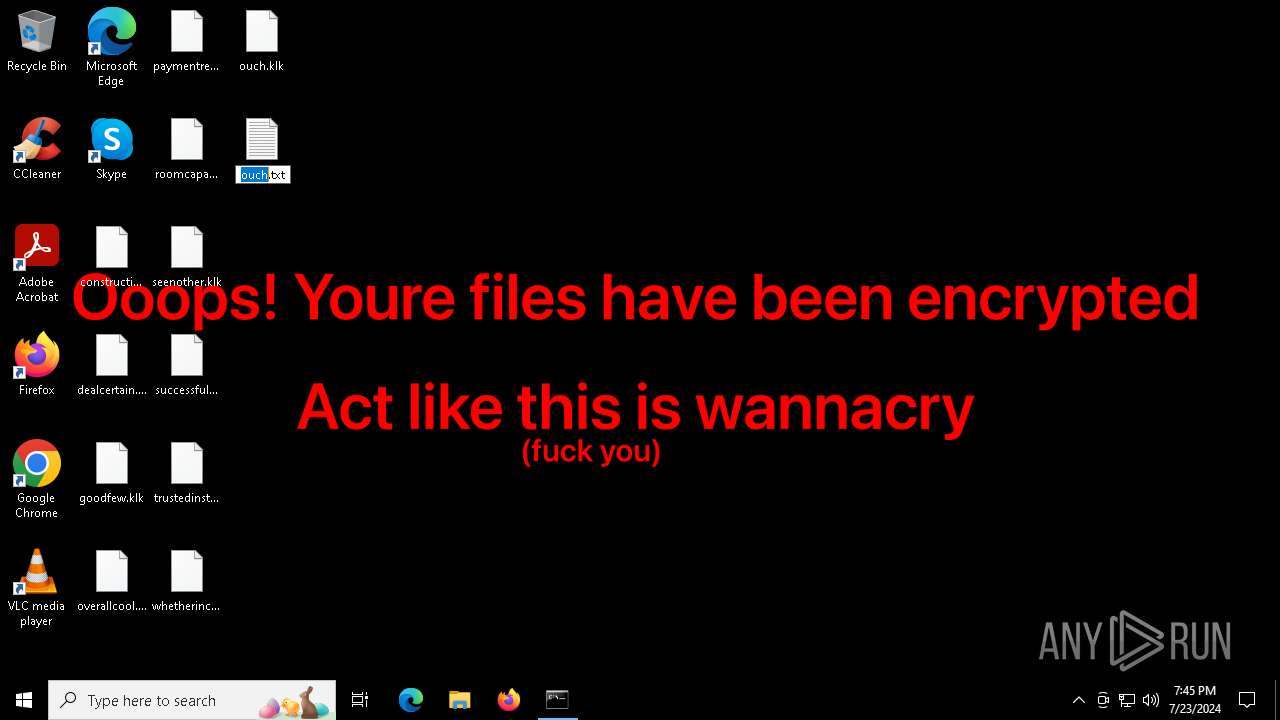
Changes the desktop background image
- reg.exe (PID: 6680)
- reg.exe (PID: 2192)
- reg.exe (PID: 2348)
- reg.exe (PID: 6880)
Discord domain found in command line (probably downloading payload)
- powershell.exe (PID: 1432)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 4512)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7160)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 4052)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 6636)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4052)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 6636)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3924)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 6636)
Application launched itself
- cmd.exe (PID: 4052)
- cmd.exe (PID: 1800)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 3924)
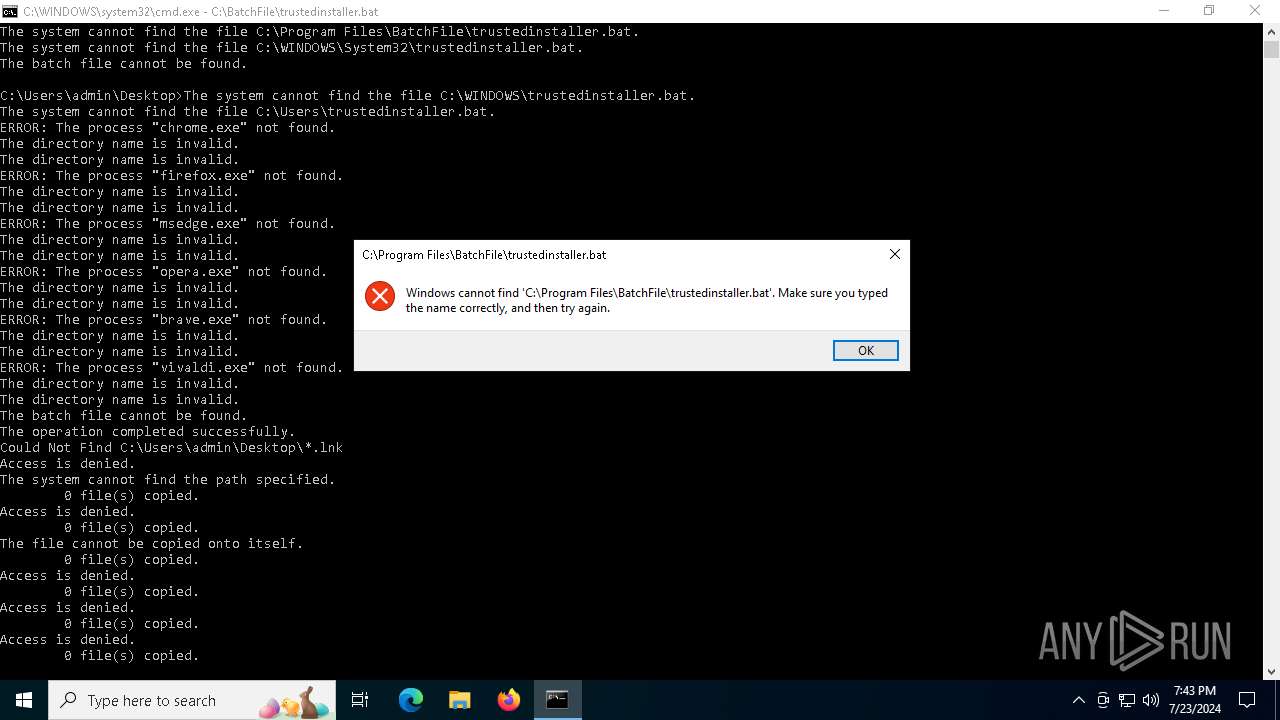
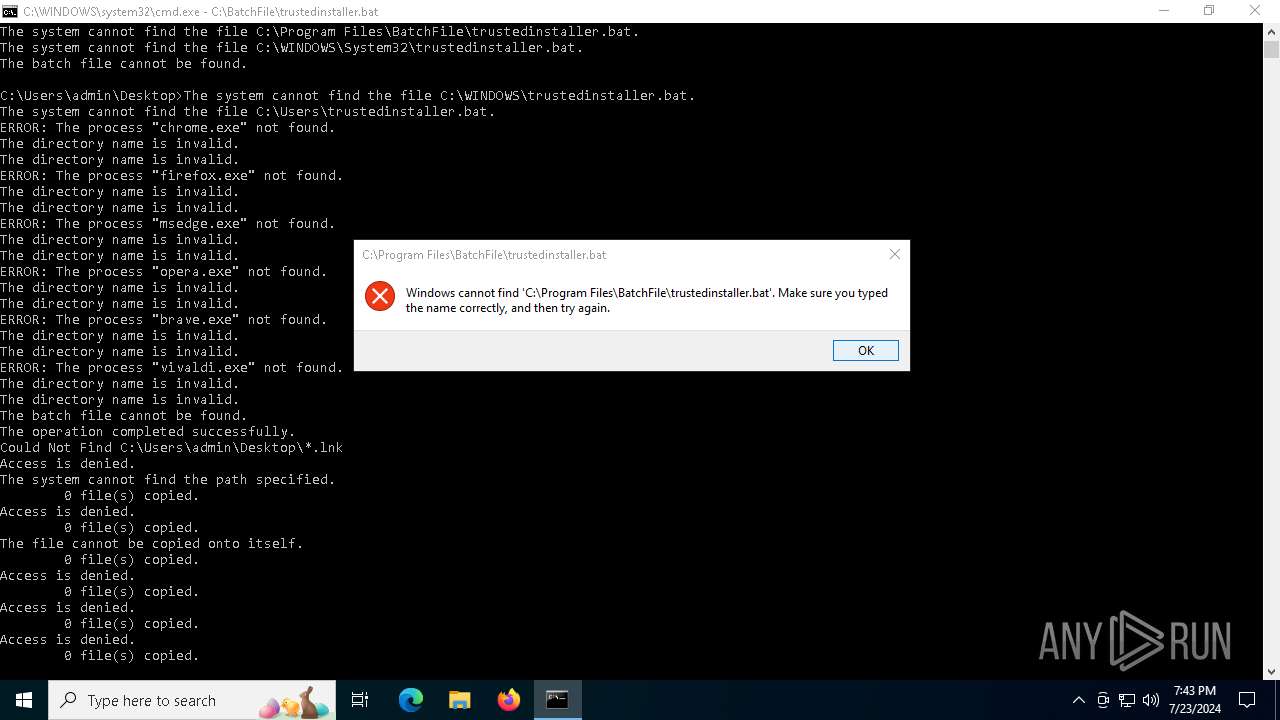
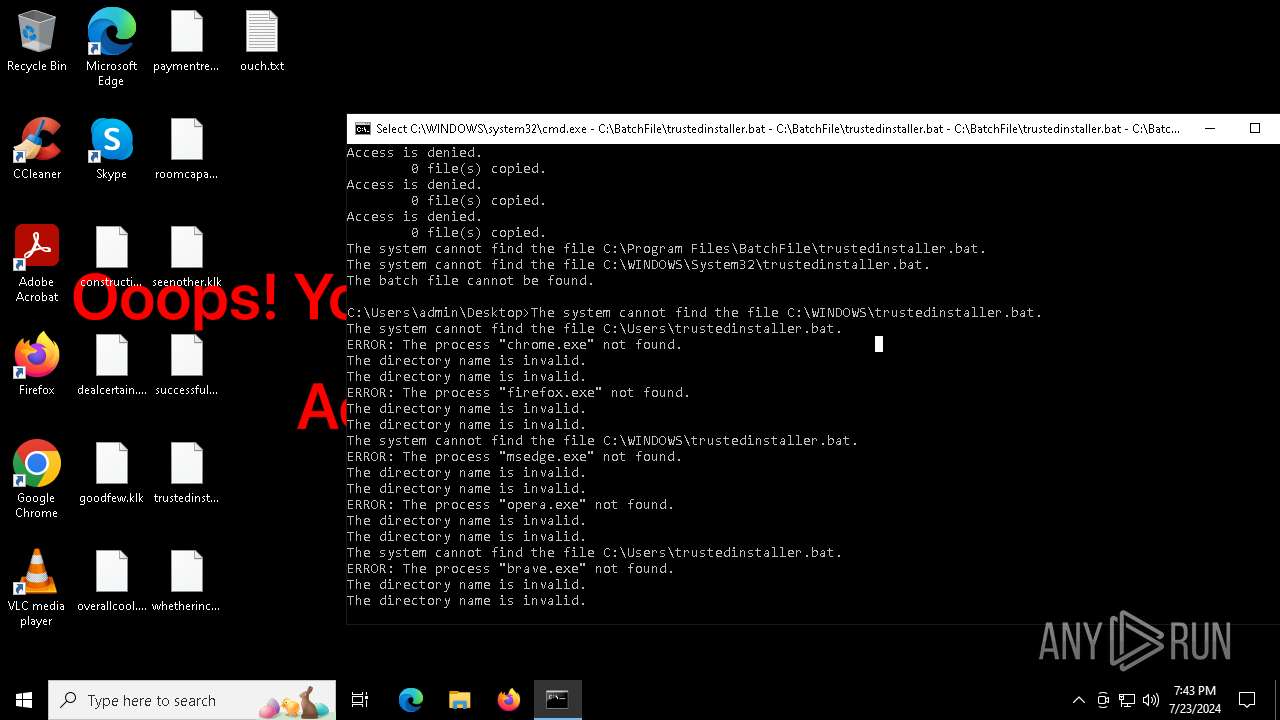
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4052)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 1800)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3924)
INFO
Disables trace logs
- powershell.exe (PID: 1432)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 4512)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7160)
Checks proxy server information
- powershell.exe (PID: 1432)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 4512)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7160)
- slui.exe (PID: 6644)
Attempting to use instant messaging service
- powershell.exe (PID: 1432)
- powershell.exe (PID: 6884)
- powershell.exe (PID: 4512)
- powershell.exe (PID: 6956)
- powershell.exe (PID: 7160)
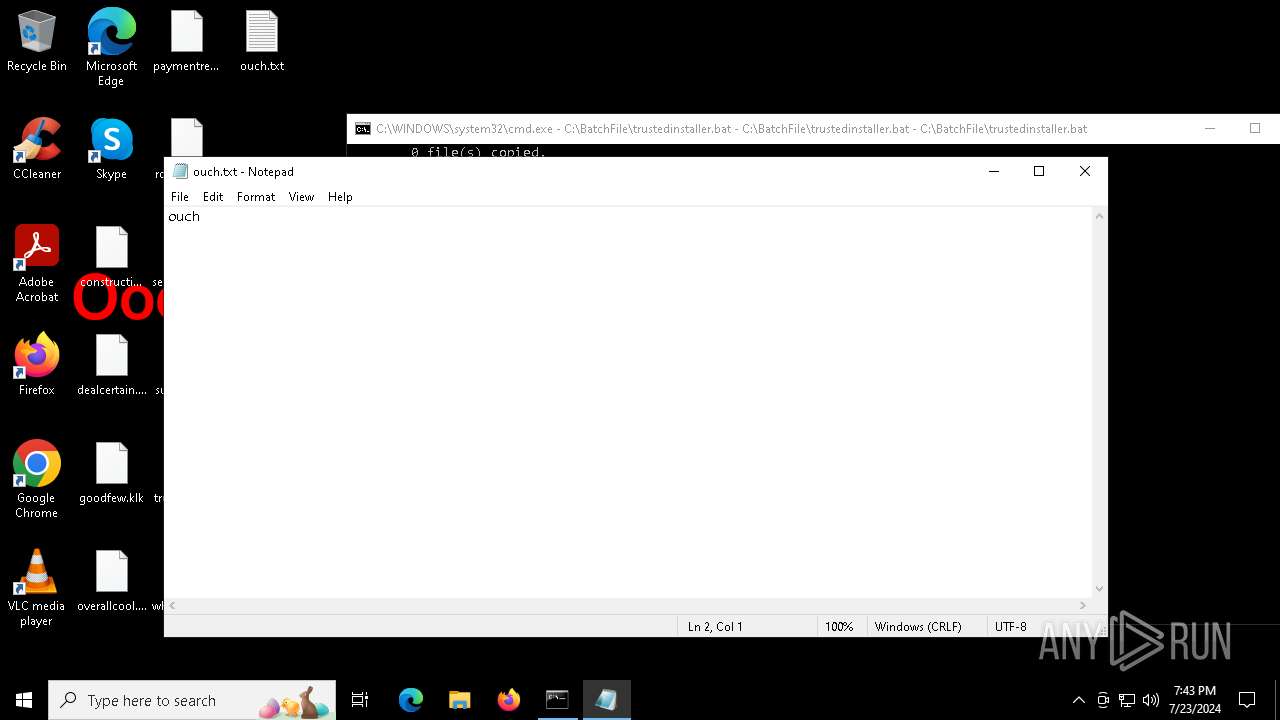
Manual execution by a user
- notepad.exe (PID: 5576)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5576)
Reads the software policy settings
- slui.exe (PID: 6644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
165
Monitored processes
45
Malicious processes
4
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | taskkill /f /im "firefox.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | taskkill /f /im "vivaldi.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1320 | taskkill /f /im "brave.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | taskkill /f /im "msedge.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | powershell -Command "(New-Object Net.WebClient).DownloadFile('https://cdn.discordapp.com/attachments/1210857012976680982/1265375003356958820/Untitled11_20240723222812.png?ex=66a147ce&is=669ff64e&hm=a5ecf1bc511891fb8e579dce5e1c76df281f970a2c4b3e920c861ca27b0b0ef7&', 'C:\Users\admin\AppData\Local\Temp\wallpaper.png')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1696 | C:\WINDOWS\system32\cmd.exe /K "C:\PerfLogs\trustedinstaller.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1800 | C:\WINDOWS\system32\cmd.exe /K "C:\BatchFile\trustedinstaller.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | taskkill /f /im "chrome.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | C:\WINDOWS\system32\cmd.exe /K "C:\PerfLogs\trustedinstaller.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
34 297
Read events
34 278
Write events
19
Delete events
0
Modification events
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1432) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
45
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rbche2yr.1ny.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4052 | cmd.exe | C:\Users\admin\Desktop\constructionpressure.klk | image | |
MD5:6E94A09B15D3D42CB6BAEA5312BEC6E7 | SHA256:ABA960160D1ACC29D0493ECBE94098EC3FF29E66B1F8AF7B1A8C86EA8FB0EC90 | |||
| 6884 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zhckueyu.eud.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4052 | cmd.exe | C:\Users\admin\Desktop\successfulcouple.klk | image | |
MD5:B5D65730B09BEDE1E5D7E9C263B9EABC | SHA256:2E2FFB4408CA729853D5661AA83D81A7F09D3A91EC20EB94A734BF6EBB970905 | |||
| 4052 | cmd.exe | C:\Users\admin\Desktop\roomcapacity.klk | image | |
MD5:89DF59A805E78F01F73878F9A382607D | SHA256:D3DA8855FA3535165E3DF2F1B9E2BD25771CB12BEA6DED6583DDCCBD7627643B | |||
| 4052 | cmd.exe | C:\Users\admin\Desktop\paymentresort.klk | image | |
MD5:6F951962BB5801C44252FFAEF82E6E8B | SHA256:6DB348DD75278ED9AB432454E8A6F81276199C69C1FBEF4C18891E81FB56C960 | |||
| 1432 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:54C8576BD62F881F2A58013BBB36EEAE | SHA256:91BCF38AC77519F079552758B97D1FA95FD983A9BBC8EEEF5AF15814BC5DAF60 | |||
| 4052 | cmd.exe | C:\Users\admin\Desktop\goodfew.klk | text | |
MD5:D6EAB361147F20198A67249EA46FE046 | SHA256:24176F69B9BF468769C6E0397FA624B7502DA76054035DD77ED69184C3CD56DA | |||
| 4052 | cmd.exe | C:\Users\admin\Desktop\dealcertain.klk | image | |
MD5:1237F7B4DF8B5913824082F9A0681F1E | SHA256:D373AF445A51B3E08DBC9CD12CF9A27DF490BCFE69710D188E39103244AB7E88 | |||
| 4052 | cmd.exe | C:\Users\admin\Downloads\agreementcompleted.klk | image | |
MD5:B0C2FB747AA74E88CF39F354979DAC4B | SHA256:A8090512E4204F8FD572261E7C70F9A0DEBAA504D8ECC26A937B1B87EF5862FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
21
DNS requests
5
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
— | — | POST | 401 | 4.208.221.206:443 | https://licensing.mp.microsoft.com/v7.0/licenses/content | unknown | binary | 340 b | unknown |
— | — | GET | 200 | 162.159.129.233:443 | https://cdn.discordapp.com/attachments/1210857012976680982/1265375003356958820/Untitled11_20240723222812.png?ex=66a147ce&is=669ff64e&hm=a5ecf1bc511891fb8e579dce5e1c76df281f970a2c4b3e920c861ca27b0b0ef7& | unknown | image | 96.0 Kb | unknown |
— | — | GET | 200 | 162.159.135.233:443 | https://cdn.discordapp.com/attachments/1210857012976680982/1265375003356958820/Untitled11_20240723222812.png?ex=66a147ce&is=669ff64e&hm=a5ecf1bc511891fb8e579dce5e1c76df281f970a2c4b3e920c861ca27b0b0ef7& | unknown | image | 96.0 Kb | unknown |
— | — | GET | 200 | 162.159.133.233:443 | https://cdn.discordapp.com/attachments/1210857012976680982/1265375003356958820/Untitled11_20240723222812.png?ex=66a147ce&is=669ff64e&hm=a5ecf1bc511891fb8e579dce5e1c76df281f970a2c4b3e920c861ca27b0b0ef7& | unknown | image | 96.0 Kb | unknown |
— | — | POST | 200 | 20.42.73.25:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | GET | 200 | 162.159.130.233:443 | https://cdn.discordapp.com/attachments/1210857012976680982/1265375003356958820/Untitled11_20240723222812.png?ex=66a147ce&is=669ff64e&hm=a5ecf1bc511891fb8e579dce5e1c76df281f970a2c4b3e920c861ca27b0b0ef7& | unknown | image | 96.0 Kb | unknown |
— | — | GET | 200 | 162.159.134.233:443 | https://cdn.discordapp.com/attachments/1210857012976680982/1265375003356958820/Untitled11_20240723222812.png?ex=66a147ce&is=669ff64e&hm=a5ecf1bc511891fb8e579dce5e1c76df281f970a2c4b3e920c861ca27b0b0ef7& | unknown | image | 96.0 Kb | unknown |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3108 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3204 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4204 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1432 | powershell.exe | 162.159.133.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
7124 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6884 | powershell.exe | 162.159.133.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cdn.discordapp.com |
| shared |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1432 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2284 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
6884 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
4512 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
6956 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
7160 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
5 ETPRO signatures available at the full report