| File name: | stubInf.exe |
| Full analysis: | https://app.any.run/tasks/9da9e0ab-3972-4a4e-bd0e-7b1341be4582 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2024, 19:52:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | EA23C02FE4B5AE3DA838A07023C532DD |
| SHA1: | B31E144D30F77F77C03347319B4E2909C8E9036F |
| SHA256: | 9800FC9D430775D5D589DCA968CF9973A6386CD48E393F14891E611C4872F132 |
| SSDEEP: | 24576:luhM0wq9ZKk6k/p1U4cebHtVCkf9JZ7usxkr/kK:KM0wq9ZV6kMjebHtVCkf9JZ7u+krcK |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 1436)
Application was injected by another process
- svchost.exe (PID: 4332)
- explorer.exe (PID: 4552)
- svchost.exe (PID: 3340)
- svchost.exe (PID: 4324)
- svchost.exe (PID: 5116)
- svchost.exe (PID: 2160)
- svchost.exe (PID: 2496)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 2344)
- svchost.exe (PID: 1508)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 2520)
- svchost.exe (PID: 3304)
- svchost.exe (PID: 1328)
- svchost.exe (PID: 2000)
- svchost.exe (PID: 2312)
- svchost.exe (PID: 3496)
- svchost.exe (PID: 2692)
- svchost.exe (PID: 2304)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 4300)
- svchost.exe (PID: 5036)
- svchost.exe (PID: 2664)
- svchost.exe (PID: 896)
- svchost.exe (PID: 2072)
- svchost.exe (PID: 5416)
- svchost.exe (PID: 1472)
- svchost.exe (PID: 1872)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 3260)
- svchost.exe (PID: 1864)
- svchost.exe (PID: 1272)
- svchost.exe (PID: 6980)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 4808)
- svchost.exe (PID: 1456)
- svchost.exe (PID: 476)
- svchost.exe (PID: 2436)
- svchost.exe (PID: 3036)
- svchost.exe (PID: 3012)
- svchost.exe (PID: 3408)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 5236)
- svchost.exe (PID: 5256)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 3888)
- svchost.exe (PID: 1628)
- svchost.exe (PID: 1036)
- svchost.exe (PID: 3020)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 1816)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 3200)
- svchost.exe (PID: 1824)
- svchost.exe (PID: 6196)
- svchost.exe (PID: 1012)
- svchost.exe (PID: 1408)
- svchost.exe (PID: 2788)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 1200)
- svchost.exe (PID: 1796)
- svchost.exe (PID: 1588)
- svchost.exe (PID: 2184)
- svchost.exe (PID: 4140)
- svchost.exe (PID: 3548)
- svchost.exe (PID: 4532)
- svchost.exe (PID: 2968)
- svchost.exe (PID: 1192)
Runs injected code in another process
- powershell.exe (PID: 1436)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 1436)
SUSPICIOUS
Executing commands from a ".bat" file
- stubInf.exe (PID: 5240)
- cmd.exe (PID: 3296)
Starts CMD.EXE for commands execution
- stubInf.exe (PID: 5240)
- cmd.exe (PID: 3296)
Application launched itself
- cmd.exe (PID: 3296)
Cryptography encrypted command line is found
- cmd.exe (PID: 1884)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3296)
Process requests binary or script from the Internet
- powershell.exe (PID: 1436)
Process drops legitimate windows executable
- powershell.exe (PID: 1436)
Executable content was dropped or overwritten
- powershell.exe (PID: 1436)
INFO
The process uses the downloaded file
- explorer.exe (PID: 4552)
Reads the time zone
- svchost.exe (PID: 2692)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 157184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32ee0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
78
Malicious processes
4
Suspicious processes
70
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 476 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\system32\svchost.exe -k RPCSS -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNoNetwork -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s NcbService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s TimeBrokerSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNetworkRestricted -p -s EventLog | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1316 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Schedule | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wlidsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 389
Read events
20 569
Write events
463
Delete events
357
Modification events
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Orchestrator |
| Operation: | write | Name: | Preshutdown |
Value: 0 | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | ScheduledRebootTime |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | RebootScheduledByUser |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | RebootConfirmedByUser |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | RebootScheduledBySmartScheduler |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | AutoAcceptShownToUser |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | LastAttemptedRebootTime |
Value: 㱰躎�ǚ | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | AutoScheduledRebootFailed |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | ScheduledRebootFailed |
Value: | |||
| (PID) Process: | (4324) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsUpdate\UX\StateVariables |
| Operation: | delete value | Name: | RebootDeferredReason |
Value: | |||
Executable files
1
Suspicious files
32
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1316 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Maintenance Work | xml | |
MD5:4838EE953DAB2C7A1BF57E0C6620A79D | SHA256:22C798E00C4793749EAC39CFB6EA3DD75112FD4453A3706E839038A64504D45D | |||
| 3036 | svchost.exe | C:\ProgramData\Microsoft\Network\Downloader\qmgr.db | edb | |
MD5:CCA969D3215B903D152EEEBAD3E19447 | SHA256:D25783E67F288BDA56A4531373680B73F5359AE5FD49DDF11029E98279C94DD8 | |||
| 1316 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Work | xml | |
MD5:5FADF13CCFBDCC5DD728380F7A615B28 | SHA256:FF1F73395F6B5B22D5FDA367521FE0DCC31FF252849B7FA85FA346B953A40451 | |||
| 1316 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Wake To Work | xml | |
MD5:C6086D02F8CE044F5FA07A98303DC7EB | SHA256:8901D9C9AEA465DA4EA7AA874610A90B8CF0A71EBA0E321CF9675FCEEE0B54A0 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-61541290.pf | binary | |
MD5:E4404487AE7FE32445CE9C31A1572029 | SHA256:2AED9F2D2891E472BCD515C441683064C0449F01F5DAB76CEBEAE16A8B0A7E10 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-D1174AA4.pf | binary | |
MD5:486EF1C3B7E71C63E789E5EB541B496C | SHA256:DD71C954EAAD035E81F1B9B478C1B9A62F512E236489EA3E21A6C8B0512E703F | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\CONSENT.EXE-531BD9EA.pf | binary | |
MD5:5808009373D31D60DE013AD9CADC33B9 | SHA256:9D10B7ED3C8AA42DDEA06F4B2F70888558004F43AB370261B6A7A2EF2C1835C0 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-98090C0A.pf | binary | |
MD5:487837169DAFB69B94BFA8208D36532C | SHA256:8A2C81C767BB8592034B026E2583112B2E7C6ABBF382EBEC6D7537BF82B4E7A6 | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 5240 | stubInf.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\stub.bat | text | |
MD5:C2F3BB55AEC3837347D4AB1D51FE3DC5 | SHA256:21020A9C775BF2606518B109B3EB3464C7B528B1738BB31D5D8E89FC25DC580D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
45
DNS requests
16
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1328 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
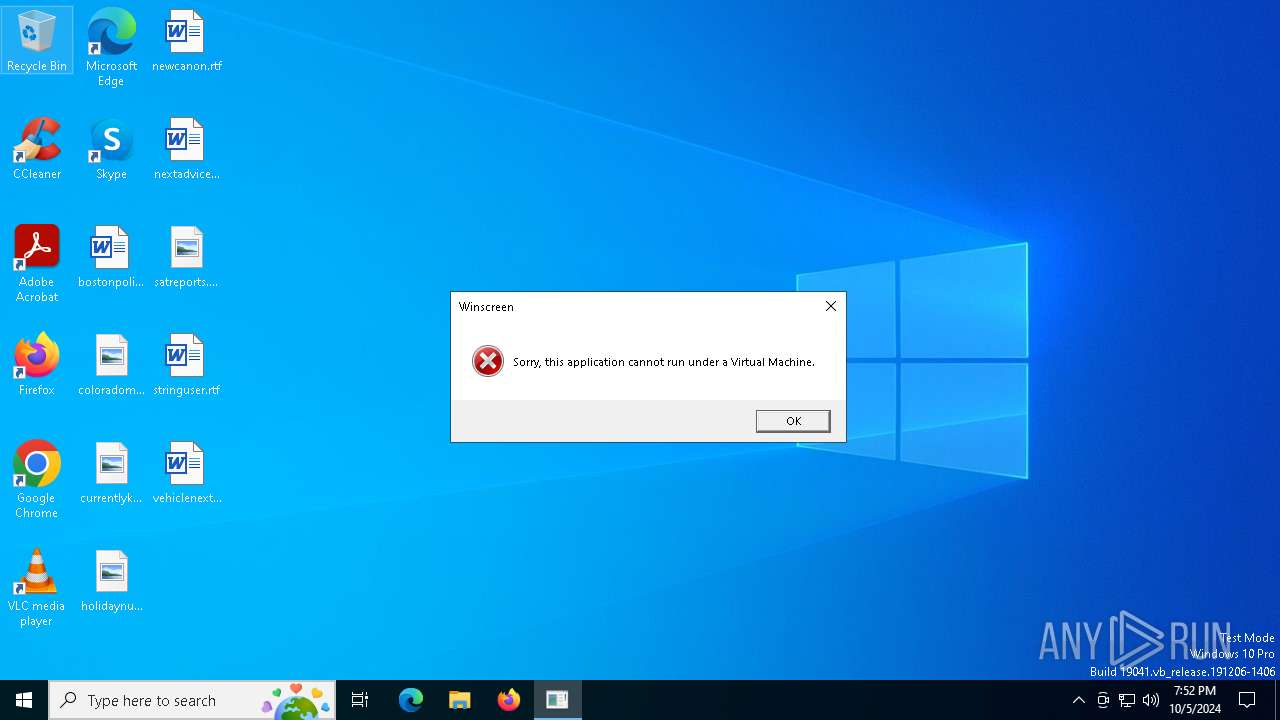
1436 | powershell.exe | GET | 301 | 140.82.121.3:80 | http://github.com/darkZeusWeb/loadersoft/raw/refs/heads/main/Winscreen.exe | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5924 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6564 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1328 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1328 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.com |
| shared |
go.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |