| File name: | Untitled 1.odt |
| Full analysis: | https://app.any.run/tasks/1eb540d8-7202-498d-a2a2-7f8a97282245 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 18:41:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.oasis.opendocument.text |
| File info: | OpenDocument Text |
| MD5: | C7423BE9CC5E034E91FBD667B5DB3505 |
| SHA1: | 3B74DCE177EB0B4A4190BDEF5CF9CF6C60F200E0 |
| SHA256: | 97FAC7D3875C206823221FA76A223C88B104A61037727D8E48C7278CEACE1F0D |
| SSDEEP: | 96:ot69/ehAz2kj422kXwYFaUOb2E3zn8PjlxXOpnKehV0Pcz0/8ybDNrUV04MYdvcK:j9DjNTXnyzn8PjCfSm0/2V0X2SFlR0FV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3272)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2680)
Creates files in the user directory
- WINWORD.EXE (PID: 2680)
Application launched itself
- chrome.exe (PID: 3272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .odt | | | OpenDocument Text document (54.1) |
|---|---|---|
| .xmind | | | XMind Workbook (37.6) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
XMP
| Creation-date: | 2019:04:24 00:11:26.042642495 |
|---|---|
| Date: | 2019:04:24 00:11:32.112038230 |
| Editing-duration: | PT6S |
| Editing-cycles: | 1 |
| Document-statisticTable-count: | - |
| Document-statisticImage-count: | - |
| Document-statisticObject-count: | - |
| Document-statisticPage-count: | 1 |
| Document-statisticParagraph-count: | 1 |
| Document-statisticWord-count: | 1 |
| Document-statisticCharacter-count: | 51 |
| Document-statisticNon-whitespace-character-count: | 51 |
| Generator: | LibreOffice/5.3.6.1$Linux_X86_64 LibreOffice_project/30$Build-1 |
Total processes
57
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6724570942806312781 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6724570942806312781 --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=464 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9407660998595355868 --mojo-platform-channel-handle=3608 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12915020945459609322 --mojo-platform-channel-handle=1232 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9434930960321745584 --mojo-platform-channel-handle=4068 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5435381197728993638 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5435381197728993638 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3988 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=11229269033268112947 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11229269033268112947 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3588 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=ppapi-broker --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --ppapi-antialiased-text-enabled=0 --ppapi-subpixel-rendering-setting=0 --service-request-channel-token=11050092005986623449 --mojo-platform-channel-handle=3964 /prefetch:4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --service-pipe-token=8662315743498097627 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8662315743498097627 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1972 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17217339053088355222 --mojo-platform-channel-handle=1212 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,5198793074222624193,11641233285489817956,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=3470580981884832495 --mojo-platform-channel-handle=972 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 963
Read events
1 259
Write events
694
Delete events
10
Modification events
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | "0: |
Value: 22303A00780A0000010000000000000000000000 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1318518814 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318518928 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318518929 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 780A000018BCB43D04FAD40100000000 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | <1: |
Value: 3C313A00780A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | <1: |
Value: 3C313A00780A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2680) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318518930 | |||
Executable files
0
Suspicious files
37
Text files
142
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2680 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6812.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2680 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\mso9E85.tmp | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\6f9c2f9d-7e0d-498b-8f2a-d2c6671e0174.tmp | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
46
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3272 | chrome.exe | GET | 200 | 2.16.186.49:80 | http://pxlgnpgecom-a.akamaihd.net/javascripts/browserfp.min.js?templateId=10 | unknown | text | 250 b | whitelisted |
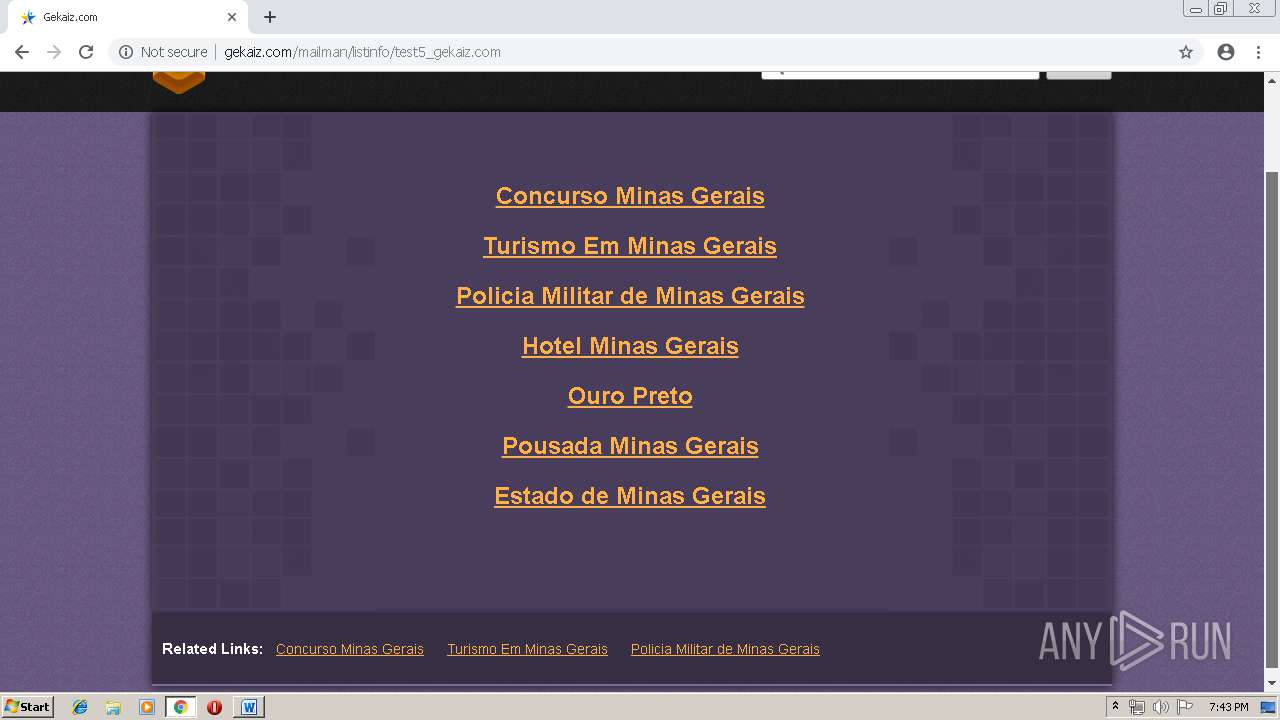
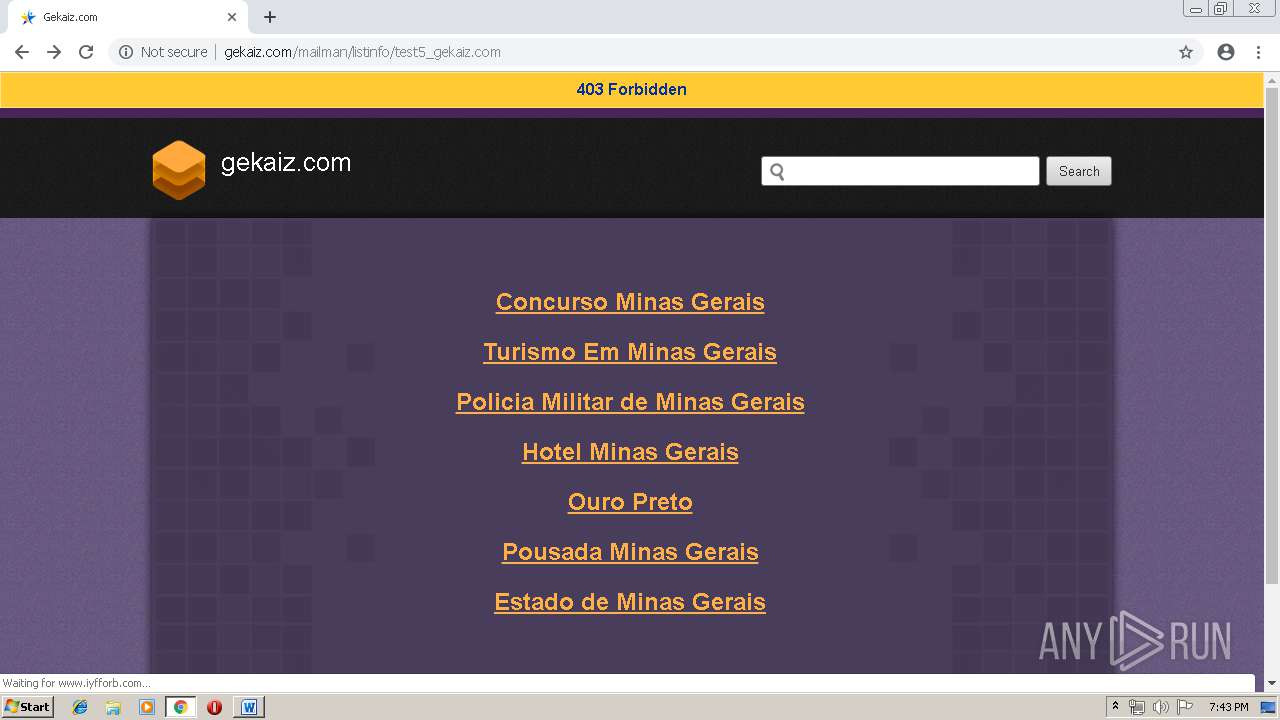
3272 | chrome.exe | GET | 200 | 162.241.148.160:80 | http://gekaiz.com/favicon.ico | US | image | 1.12 Kb | suspicious |
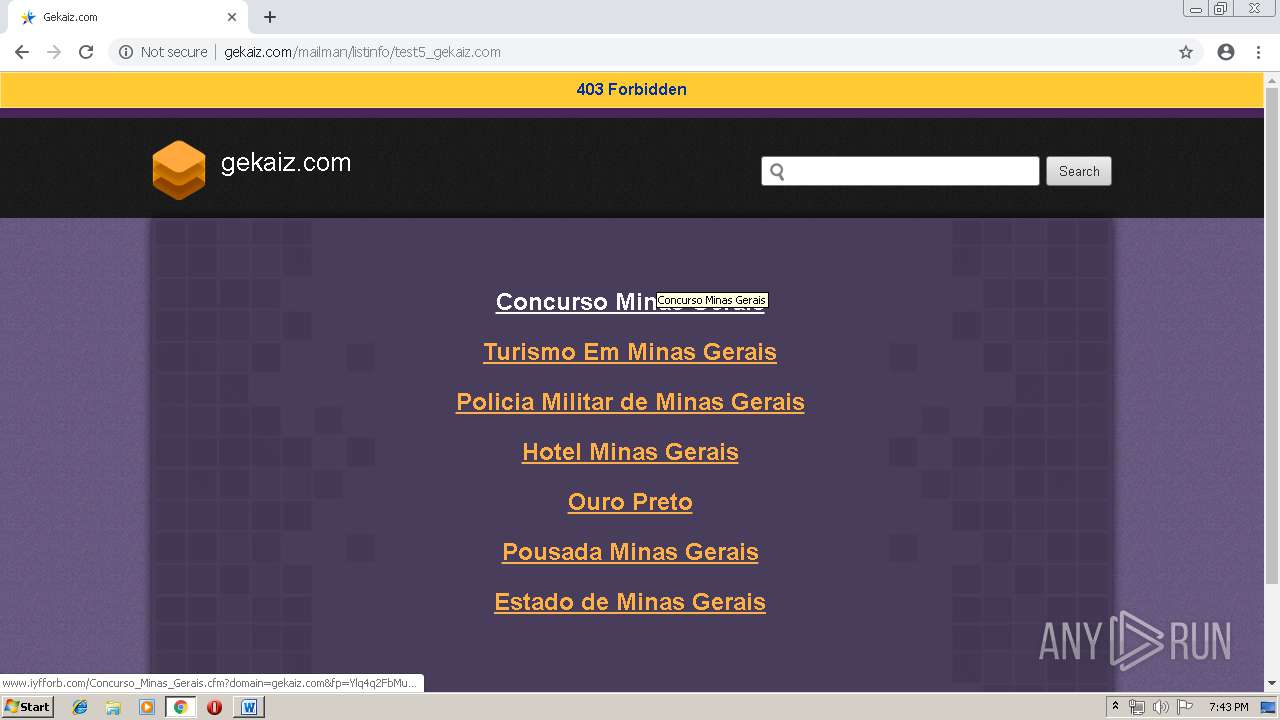
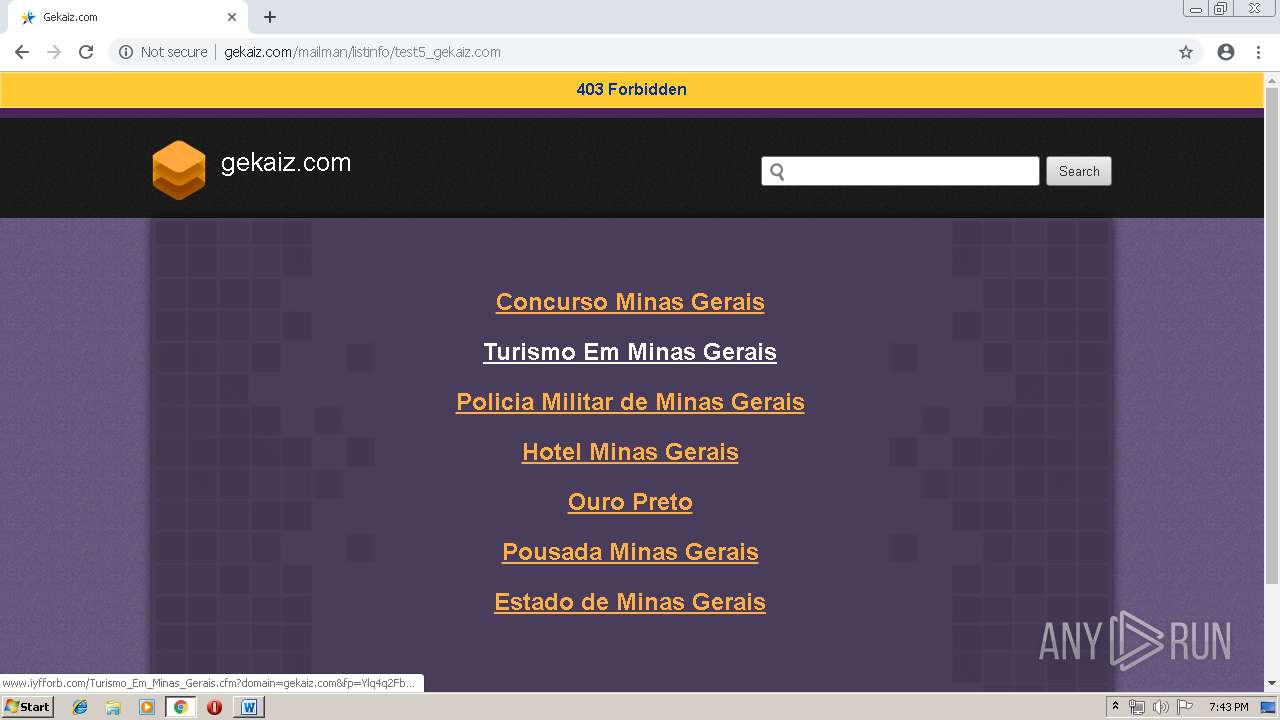
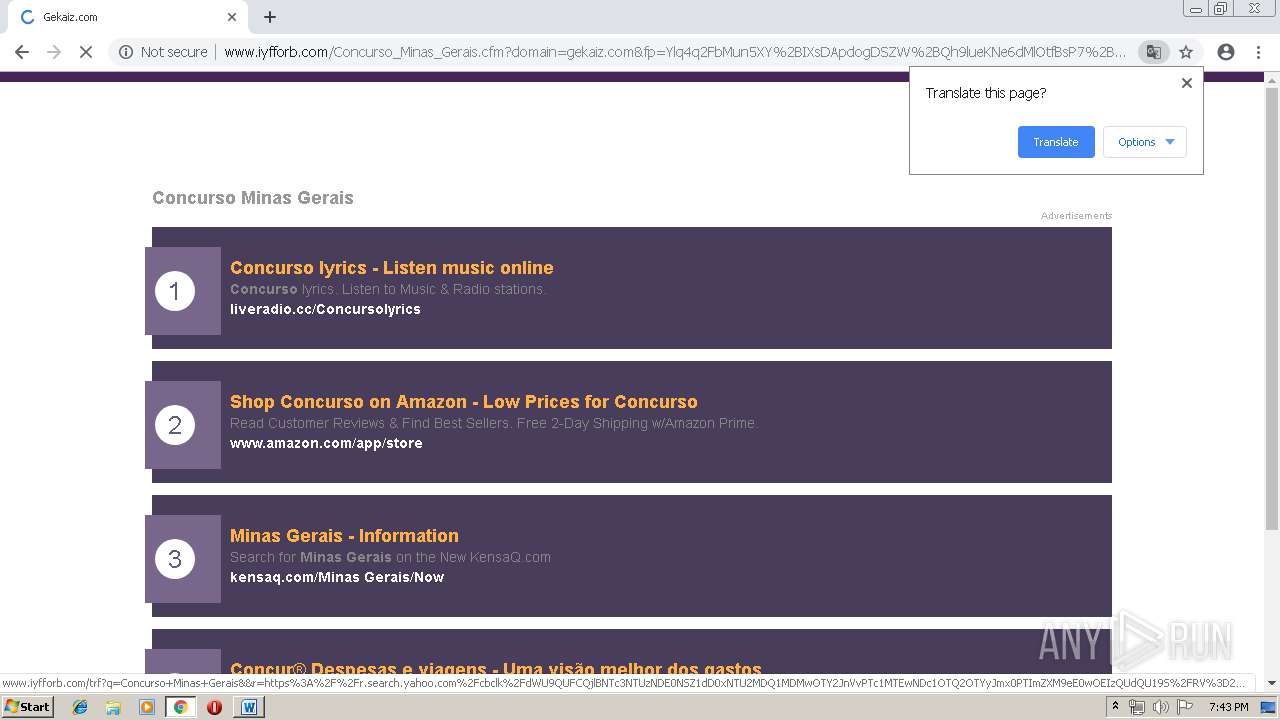
3272 | chrome.exe | GET | 200 | 208.91.196.46:80 | http://www.iyfforb.com/Concurso_Minas_Gerais.cfm?domain=gekaiz.com&fp=Ylq4q2FbMun5XY%2BIXsDApdogDSZW%2BQh9lueKNe6dMlOtfBsP7%2B2NrEUtXfNA0EhxWpN1rziRYfDkKyKkLK12HAJBuRoUA1HUuuE%2BcoidX%2BTobomSMubhu7EeO9q4CooDMrd4LN6k8uyaKH%2BWamrApe8F3MhuPyZpH%2FPypZXK3%2Fk%2FLg8bM4URNdPnuDRN8wiCfIqKaV7EQpuLEeC4QIVIhw%3D%3D&yep=KE1OgimxemwG0ijmS1ta5Pd7qSNA7C9bsaQ2Omk5xezo7B20JpPw%2BGFHkk8JIH0YtXv%2BBEsD7OlOX4ePGjtw5HW11SEzzemPqKs199kkb7QixHj76DGhMXpZ0NxxzW78HAWpjfaBZbxOa6udrN8oc2mUQ%2Bz6B7xZnFRE6s0tBJD2epzbltegF0Je61XzLDG0dv5O6JvfG%2Bg2xVCETaP4e6mx1vVyl4JwS4VMQgC4wTGw0dlZQLp8CEAOSHwFmLeaXPW6a8jWNd6E4MCmw51%2Fs3B1ACGD2qov2A8F4EfZbXTQq1LLILpSN79XY3zvKJl873RhUogN8QYKC6JK2apB8pBmfJsHCatfMZZFa%2FrT6fn8nPSTFmAuqVGF6aXTDa1fmO2JVKys6G%2FmMqWJ8cg9LjnmOLW%2BnkkZ2IQMjbDvMVtYxQL5ZUt4uLi3XSJuROQUWtH1%2Fj26IvSIKVPqg8HBkXQxlR%2FLdJE7L%2BfGOHpMv86WjxS884%2BNapAHWOZLxeaWfa7rEeD6qYKAJv%2FKWqCUxPXna3AN8qqcAV7hOGXfy3mRMYSH1qiWTDxRRwY19hVbeZtKCU8NXr7%2FvpQ1iZk7AQ%3D%3D>np=0>pp=0&kld=1061&yprpnd=jCZHp8Pr7RiJkuSemIcOD05IyxIuTc99vOgwjJnTBJ4%3D&prvtof=odKOkapAQicXj6uqidiBong0ApQ3wxuiaj3DddQkf1s%3D&>np=0>pp=0&kt=362&&kbc=gerais&ki=64687623&ktd=256&kld=1061&kp=1&bd=1%23720%231280%231%230%23668%23241 | VG | html | 10.0 Kb | malicious |
3272 | chrome.exe | GET | 200 | 87.245.198.13:80 | http://r2---sn-gxuog0-axqe.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=91.221.66.140&mm=28&mn=sn-gxuog0-axqe&ms=nvh&mt=1556044896&mv=m&pl=23&shardbypass=yes | RU | crx | 842 Kb | whitelisted |
3272 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 510 b | whitelisted |
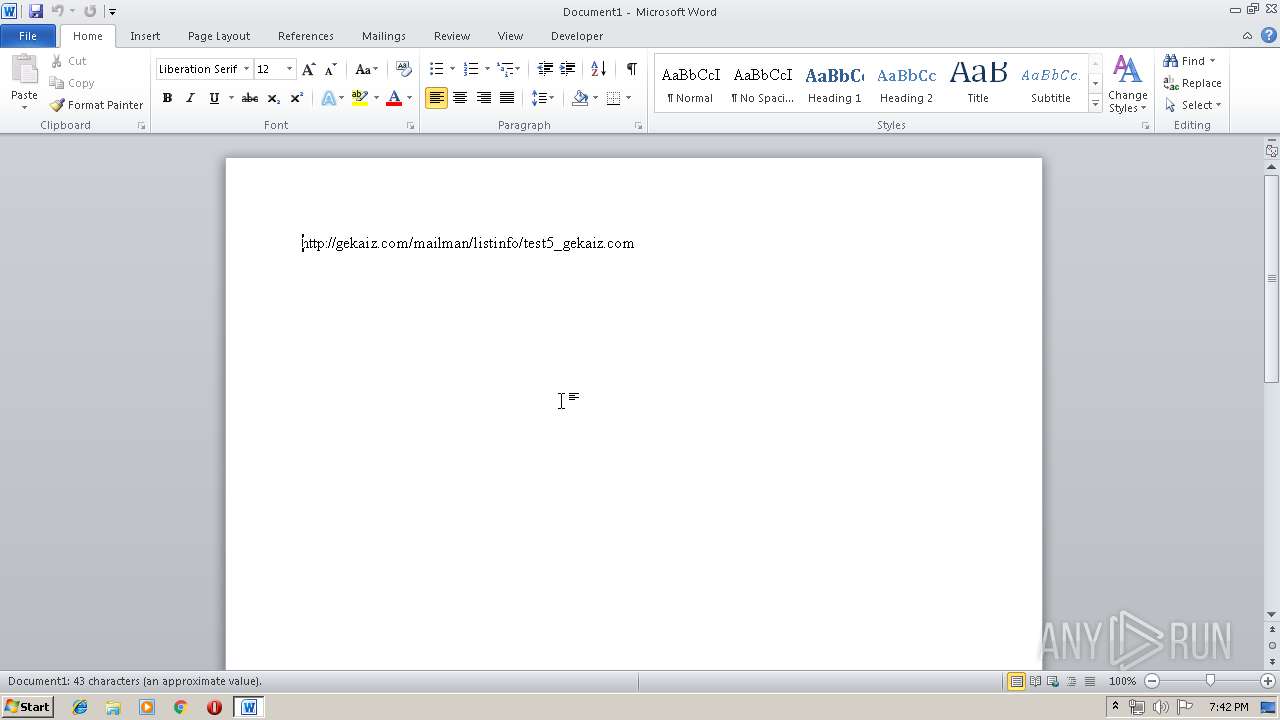
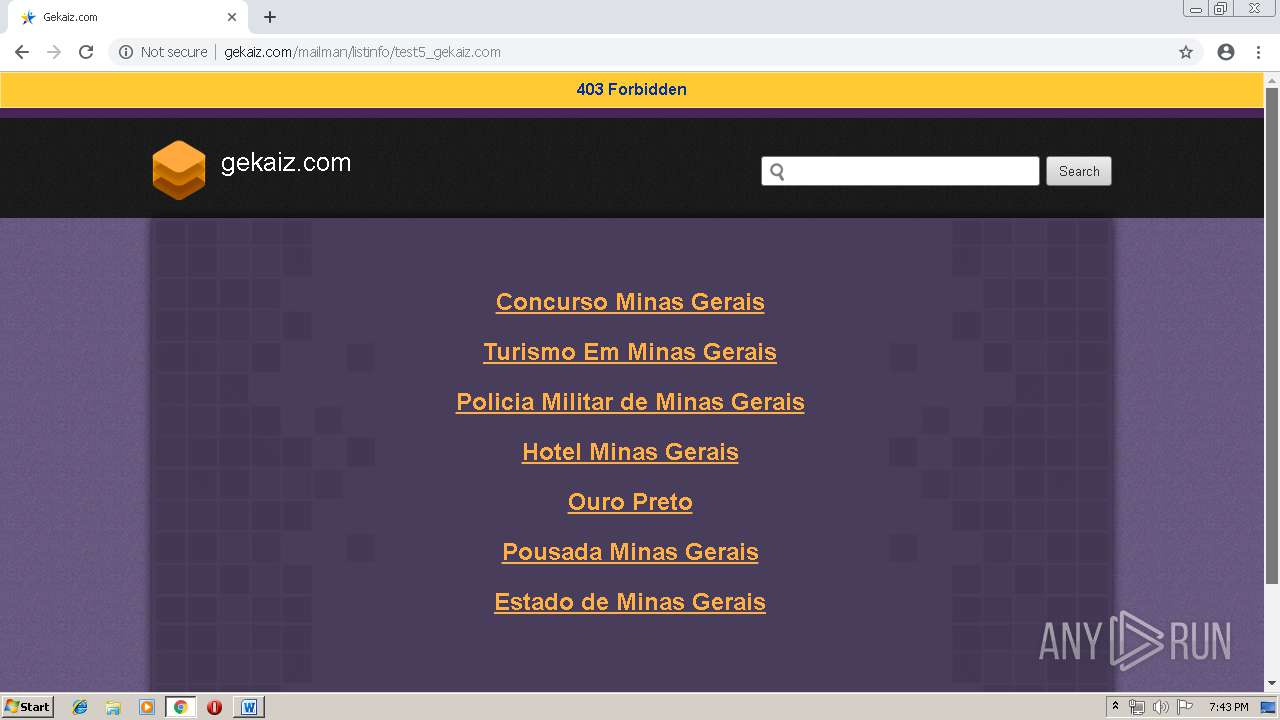
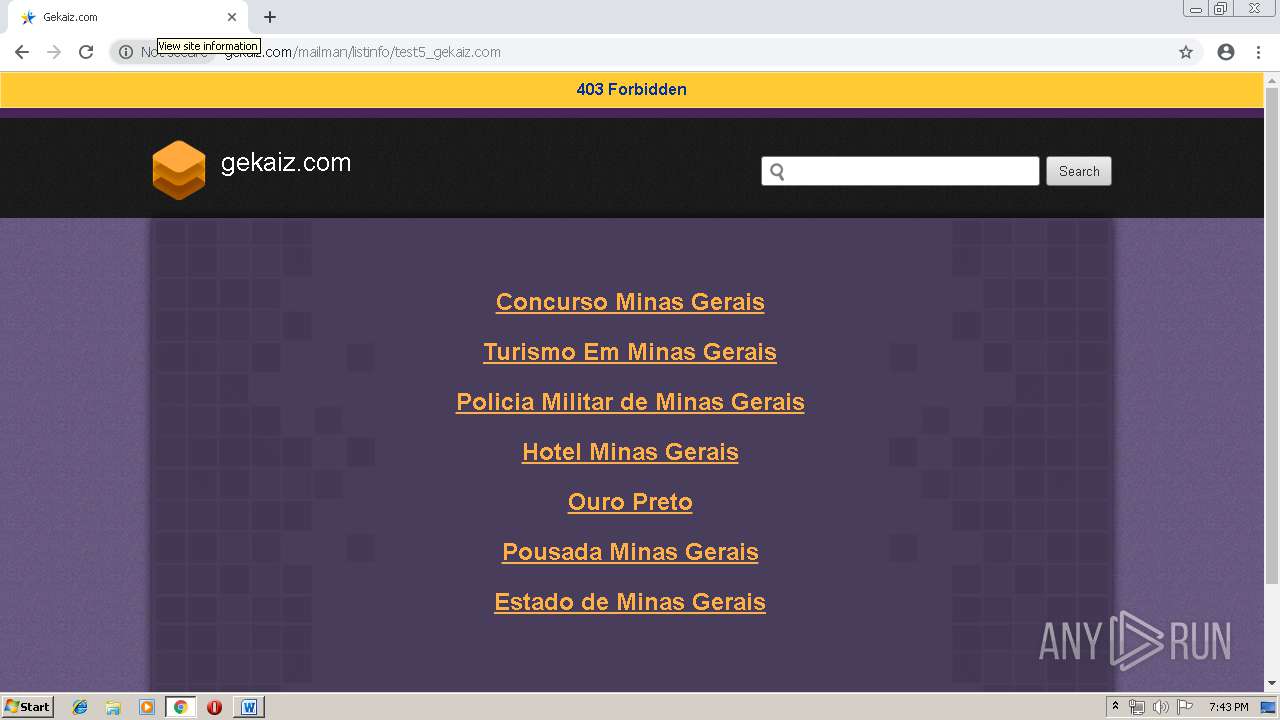
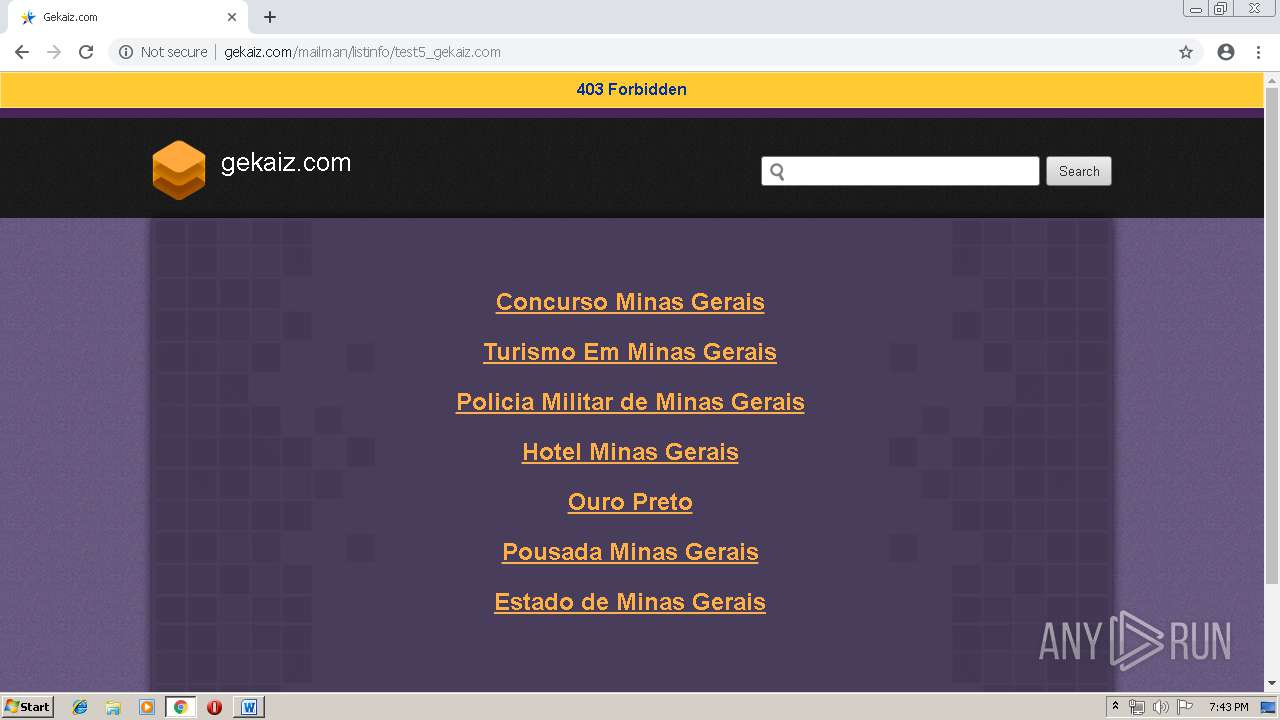
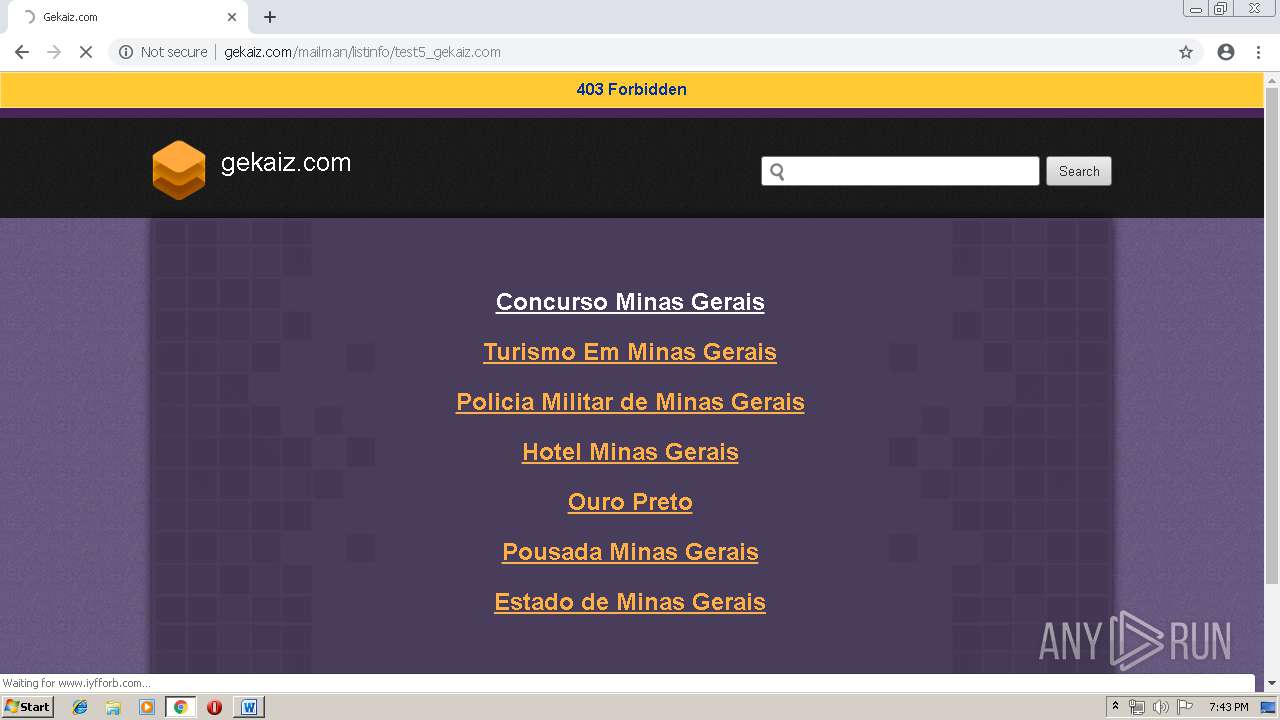
3272 | chrome.exe | GET | 403 | 162.241.148.160:80 | http://gekaiz.com/mailman/listinfo/test5_gekaiz.com | US | html | 28.3 Kb | suspicious |
3272 | chrome.exe | GET | 200 | 2.16.186.106:80 | http://i3.cdn-image.com/__media__/js/min.js?v2.2 | unknown | text | 2.97 Kb | whitelisted |
3272 | chrome.exe | GET | 200 | 208.91.196.46:80 | http://www.iyfforb.com/sk-logabpstatus.php?a=MXVSallSODlzS2hHQ0YzdG1CWWZVTmdLY0xzc29ZeFV6RG9vSldWUE85SlhLK0E1UHRUcUFoZGtUWlBJWmZaelY3R2xFdFhJbG5rek9FNmhTb2UzL1J6b1FSejQwNEhocjVXT0grNlpkNE96RnpIL2FJejVxekFOeDVqTFRjS1o=&b=false | VG | compressed | 10.0 Kb | malicious |
3272 | chrome.exe | GET | 200 | 2.16.186.64:80 | http://i4.cdn-image.com/__media__/pics/7867/srch-bg.gif | unknown | image | 1.62 Kb | whitelisted |
3272 | chrome.exe | GET | 200 | 2.16.186.106:80 | http://i3.cdn-image.com/__media__/pics/8243/h_bg.gif | unknown | image | 2.17 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 216.58.207.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.22.67:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 216.58.206.14:443 | clients1.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.18.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 216.58.207.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3272 | chrome.exe | 162.241.148.160:80 | gekaiz.com | CyrusOne LLC | US | suspicious |
3272 | chrome.exe | 172.217.16.206:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
gekaiz.com |
| suspicious |
redirector.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3272 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3272 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |