| File name: | sample.exe |
| Full analysis: | https://app.any.run/tasks/7e9abee7-2be7-4246-9232-fab2cf04b04e |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2019, 12:54:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EFECA44E62236AFFE49B5B66049E385A |
| SHA1: | 9CA715B5E3591BC04C582ACA4BD27A1524F42132 |
| SHA256: | 97E5770485780B365DB1BF8B3A101C1D1D88154BF62AB6D96A83024EBD845A4B |
| SSDEEP: | 196608:kJotydtkPm9FHDG2kOYlB62INLRCa81COSzHeo3WS6:kJaPE02W9IKrsOSbeoM |
MALICIOUS
Application was dropped or rewritten from another process
- Wordle.exe (PID: 3752)
Loads dropped or rewritten executable
- Wordle.exe (PID: 3752)
SUSPICIOUS
Creates files in the program directory
- sample.exe (PID: 2820)
Creates files in the user directory
- sample.exe (PID: 3256)
Application launched itself
- sample.exe (PID: 3256)
Creates a software uninstall entry
- sample.exe (PID: 2820)
Executable content was dropped or overwritten
- sample.exe (PID: 2820)
INFO
Dropped object may contain Bitcoin addresses
- sample.exe (PID: 2820)
Manual execution by user
- Wordle.exe (PID: 3752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:07 11:47:38+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 232448 |
| InitializedDataSize: | 216576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25cc0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.2.0.0 |
| ProductVersionNumber: | 0.2.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | Wordle |
| FileVersion: | 0.2 |
| LegalCopyright: | - |
| ProductName: | Wordle |
| ProductVersion: | 0.2 |
| OriginalFileName: | wordle_windows_0_2.exe |
| InternalName: | wordle |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 07-Dec-2018 10:47:38 |
| Detected languages: |
|
| CompanyName: | - |
| FileDescription: | Wordle |
| FileVersion: | 0.2 |
| LegalCopyright: | - |
| ProductName: | Wordle |
| ProductVersion: | 0.2 |
| OriginalFilename: | wordle_windows_0_2.exe |
| InternalName: | wordle |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 07-Dec-2018 10:47:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00038A85 | 0x00038C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.67683 |
.rdata | 0x0003A000 | 0x00019386 | 0x00019400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.32397 |
.data | 0x00054000 | 0x00012EE4 | 0x00001E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.10263 |
.rsrc | 0x00067000 | 0x00004E00 | 0x00004E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.56041 |
.reloc | 0x0006C000 | 0x00003BCC | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.6709 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.17909 | 1244 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.03916 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 4.93195 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 7.91261 | 8327 | UNKNOWN | UNKNOWN | RT_ICON |
101 | 3.19761 | 302 | UNKNOWN | English - United States | RT_DIALOG |
103 | 3.05366 | 286 | UNKNOWN | English - United States | RT_DIALOG |
104 | 2.62517 | 226 | UNKNOWN | English - United States | RT_DIALOG |
1001 | 2.52704 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
USER32.dll |
ole32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
_Java_com_install4j_runtime_installer_platform_win32_ACLHandling_addACE@40 | 1 | 0x00017583 |
_Java_com_install4j_runtime_installer_platform_win32_FileVersion_compare0@16 | 2 | 0x00017EE0 |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getDriveType0@12 | 3 | 0x00018319 |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getPathFromRegistry0@12 | 4 | 0x0001816B |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getShortPathName0@12 | 5 | 0x00018378 |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getSpecialFolder0@16 | 6 | 0x00018131 |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getSystemDirectory0@8 | 7 | 0x000182B7 |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getUniversalPathName0@12 | 8 | 0x000183FF |
_Java_com_install4j_runtime_installer_platform_win32_FolderInfo_getWindowsDirectory0@8 | 9 | 0x00018227 |
_Java_com_install4j_runtime_installer_platform_win32_Misc_broadcastSettingChange0@8 | 10 | 0x000192BB |
Total processes
41
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | c:\PROGRA~1\java\JRE18~1.0_9\bin\java.exe -version | c:\PROGRA~1\java\JRE18~1.0_9\bin\java.exe | — | sample.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
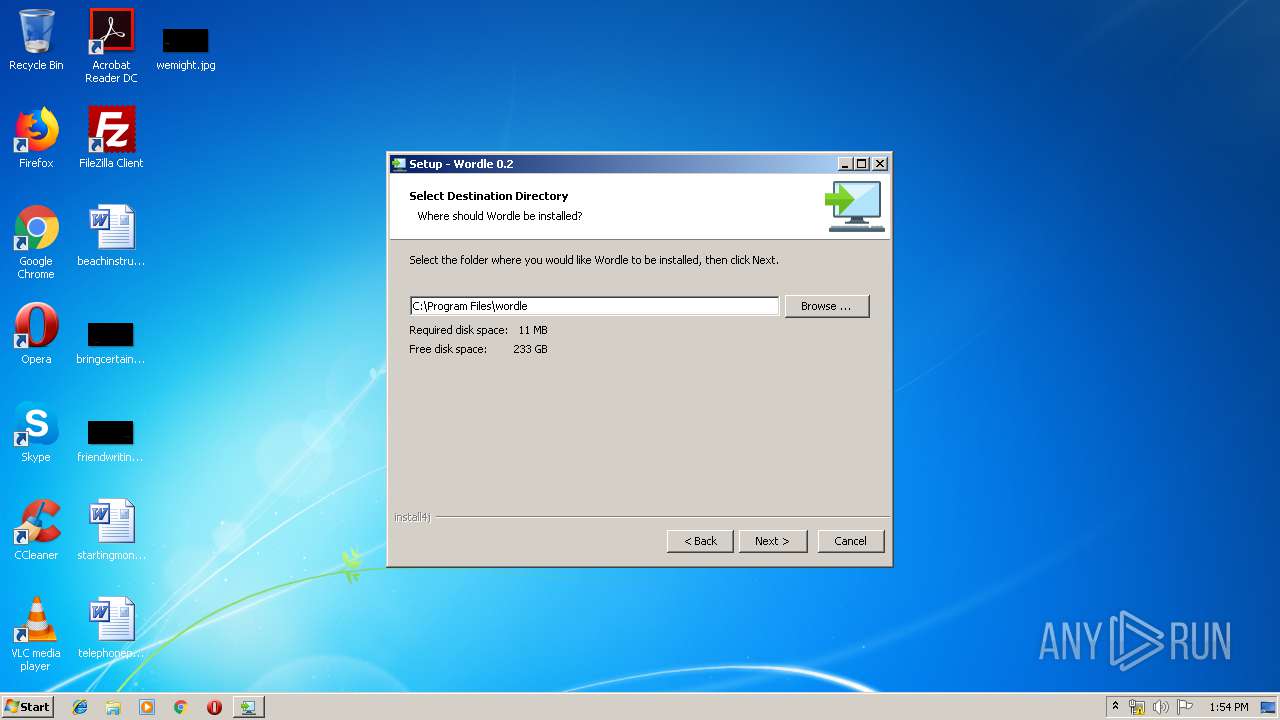
| 2820 | "C:\Users\admin\AppData\Local\Temp\sample.exe" __i4j_lang_restart -J-Xmx128m -J-Dinstall4j.commIdentifier=\\.\pipe\i4jcomm0 -J-Dinstall4j.helperAppId=installer -J-Duser.language=en -J-Dinstall4j.language=en -J-Dinstall4j.systemLanguage=en -J-Dexe4j.unextractedPositionRestart=2597793 -J-Dinstall4j.commIdentifier=\\.\pipe\i4jcomm0 -J-Dinstall4j.helperLog=false -J-Dinstall4j.dontUninstallServices=false "-J-Dexe4j.semaphoreName=Local\c:_users_admin_appdata_local_temp_sample.exe" | C:\Users\admin\AppData\Local\Temp\sample.exe | sample.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Wordle Exit code: 0 Version: 0.2 Modules
| |||||||||||||||
| 3256 | "C:\Users\admin\AppData\Local\Temp\sample.exe" | C:\Users\admin\AppData\Local\Temp\sample.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Wordle Exit code: 0 Version: 0.2 Modules
| |||||||||||||||
| 3752 | "C:\Program Files\wordle\Wordle.exe" | C:\Program Files\wordle\Wordle.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3984 | "C:\Users\admin\AppData\Local\Temp\sample.exe" __i4j_windel C:\Users\admin\AppData\Local\Temp\i4j8029920515607044211.tmp | C:\Users\admin\AppData\Local\Temp\sample.exe | — | sample.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Wordle Exit code: 0 Version: 0.2 Modules
| |||||||||||||||
Total events
615
Read events
571
Write events
42
Delete events
2
Modification events
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j\pids |
| Operation: | write | Name: | c:\users\admin\appdata\local\temp\sample.exe |
Value: 3256 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j |
| Operation: | write | Name: | InstallStarted_3256 |
Value: 1 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j |
| Operation: | write | Name: | InstallStarted |
Value: 1 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j\jvms\c:/program files/java/jre1.8.0_92/bin/java.exe |
| Operation: | write | Name: | LastWriteTime |
Value: 40942D4BC73ED401 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j\jvms\c:/program files/java/jre1.8.0_92/bin/java.exe |
| Operation: | write | Name: | Version |
Value: 1.8.0_92 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j |
| Operation: | write | Name: | InstallStarted_3256 |
Value: 0 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j |
| Operation: | write | Name: | InstallStarted |
Value: 0 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3256) sample.exe | Key: | HKEY_CURRENT_USER\Software\ej-technologies\exe4j |
| Operation: | delete value | Name: | InstallStarted_3256 |
Value: 0 | |||
Executable files
5
Suspicious files
5
Text files
200
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\e4jF089.tmp | — | |
MD5:— | SHA256:— | |||
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\i4j_nlog_1.log | text | |
MD5:— | SHA256:— | |||
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\e4jF05A.tmp_dir1559048087\i4jruntime.jar | compressed | |
MD5:BFBC7DD645E3CE681B6DC75C7E75437B | SHA256:3DE34B00BB36B8CD8CBBBC17E065EF8B9215006BC5AEC9888DDB0389BBA77325 | |||
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\e4jF05A.tmp_dir1559048087\i4j_extf_7_1xg8ule_18gg8kx.png | image | |
MD5:05658E9BE759D303893D0AF89025FD05 | SHA256:CB52AEBF64334395C1EFF412DEF789EC55A18630953A1F69015B501E0DBF87CA | |||
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\e4jF05A.tmp_dir1559048087\i4j_extf_6_1xg8ule_259ij1.png | image | |
MD5:3DF21A5C9E9ED0749F00BA1A4EBC2B21 | SHA256:CB78EB088384FA5B98F08879D914AB5388E54707ED267A569E5FDEA16588913A | |||
| 2820 | sample.exe | C:\Program Files\wordle\.install4j\i4j5793584864614995458.tmp | — | |
MD5:— | SHA256:— | |||
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\e4jF05A.tmp_dir1559048087\i4j_extf_2_1xg8ule_x7nby6.png | image | |
MD5:F6DFE7474B27F1D3EADF2E2FBC22C255 | SHA256:AD32F1717727377B4BB48BC8320E8E1BF87FF493FAAC1D17C554299A7D128C08 | |||
| 2820 | sample.exe | C:\Program Files\wordle\.install4j\i4j88981009629263144.tmp | — | |
MD5:— | SHA256:— | |||
| 3256 | sample.exe | C:\Users\admin\AppData\Local\Temp\e4jF05A.tmp_dir1559048087\stats.properties | text | |
MD5:EFD532407CDBD986509BB9F3447A4493 | SHA256:7079216DB15EE41A10C0F62028272AEA323E2D97F707A9A788B308DBFFAF81BB | |||
| 2820 | sample.exe | C:\Program Files\wordle\.install4j\i4j8972715214782187380.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report