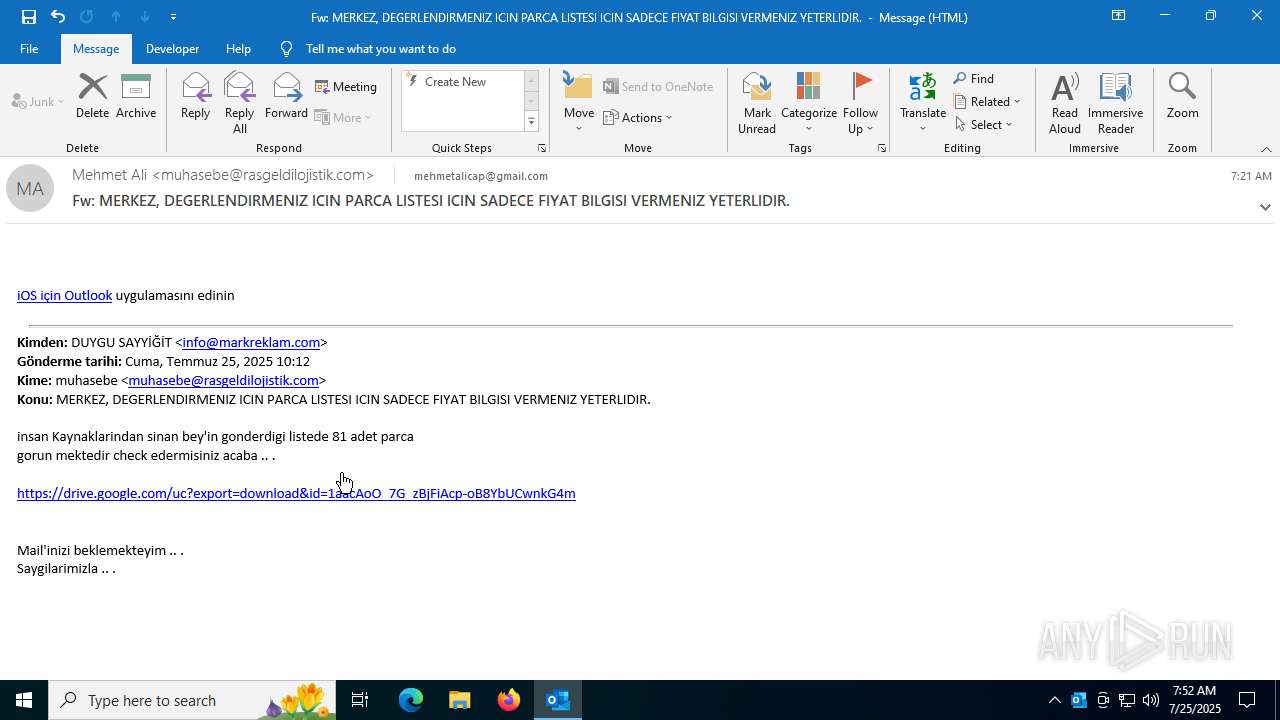
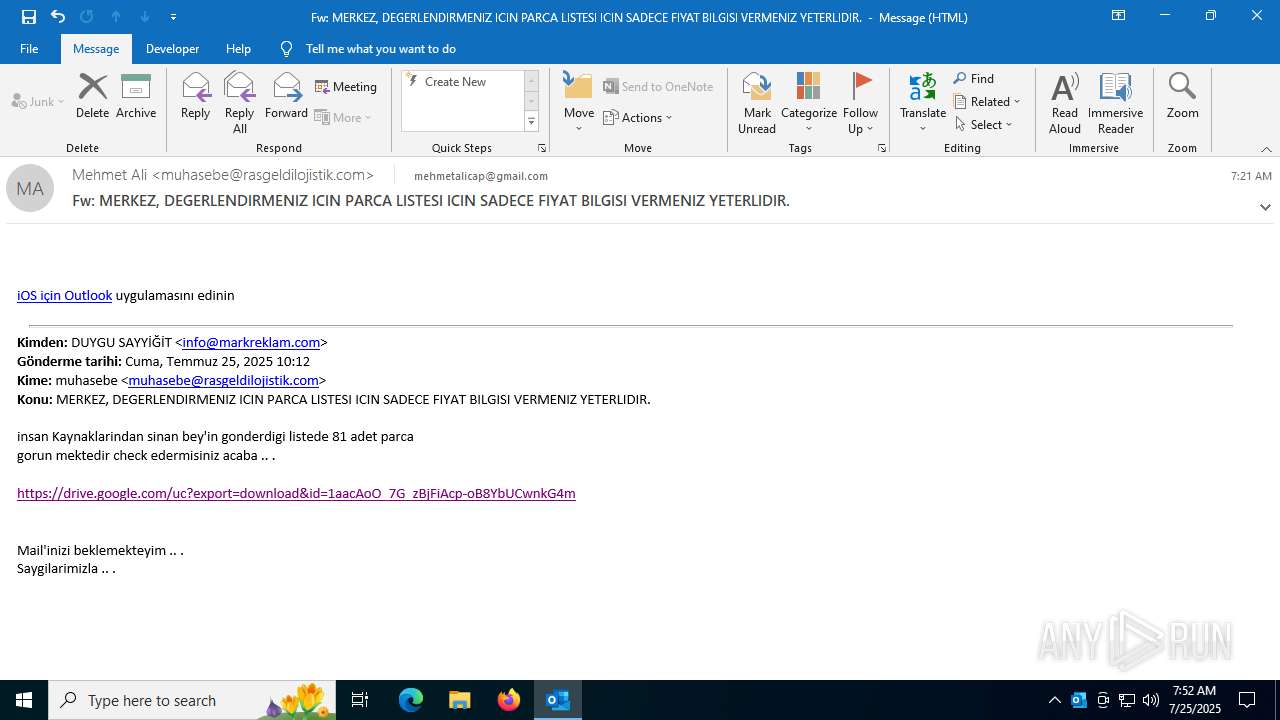
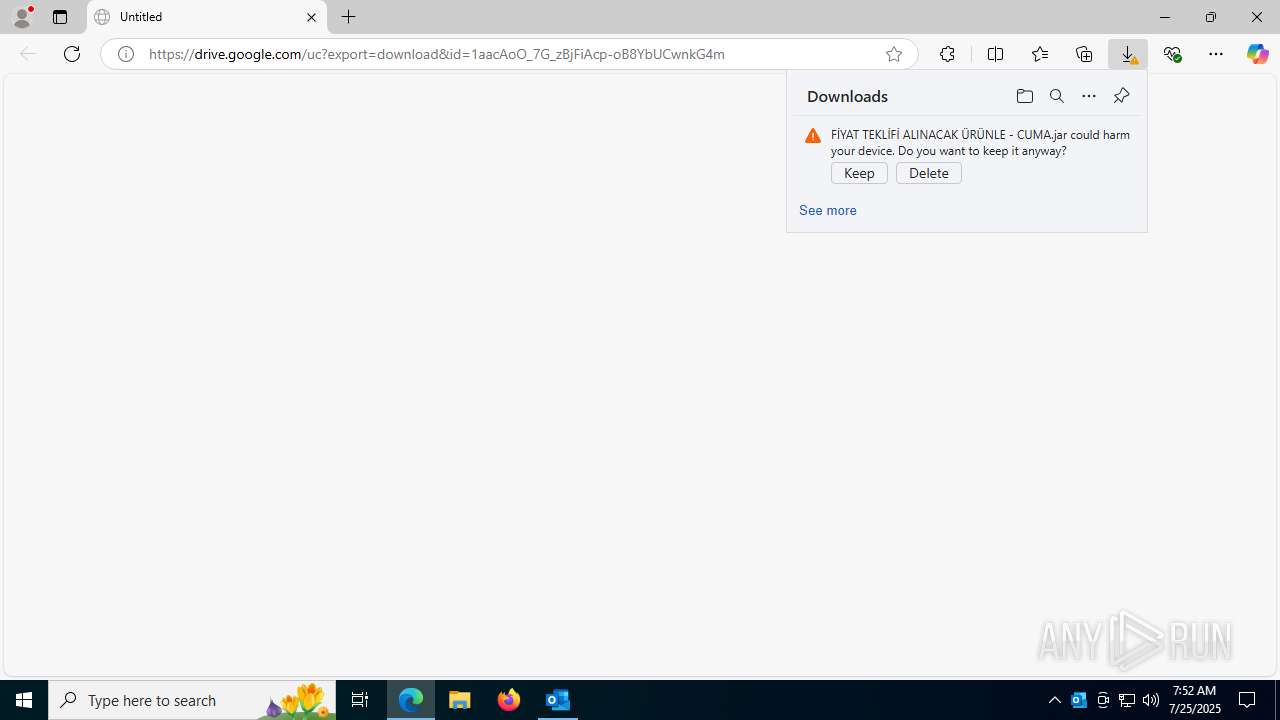
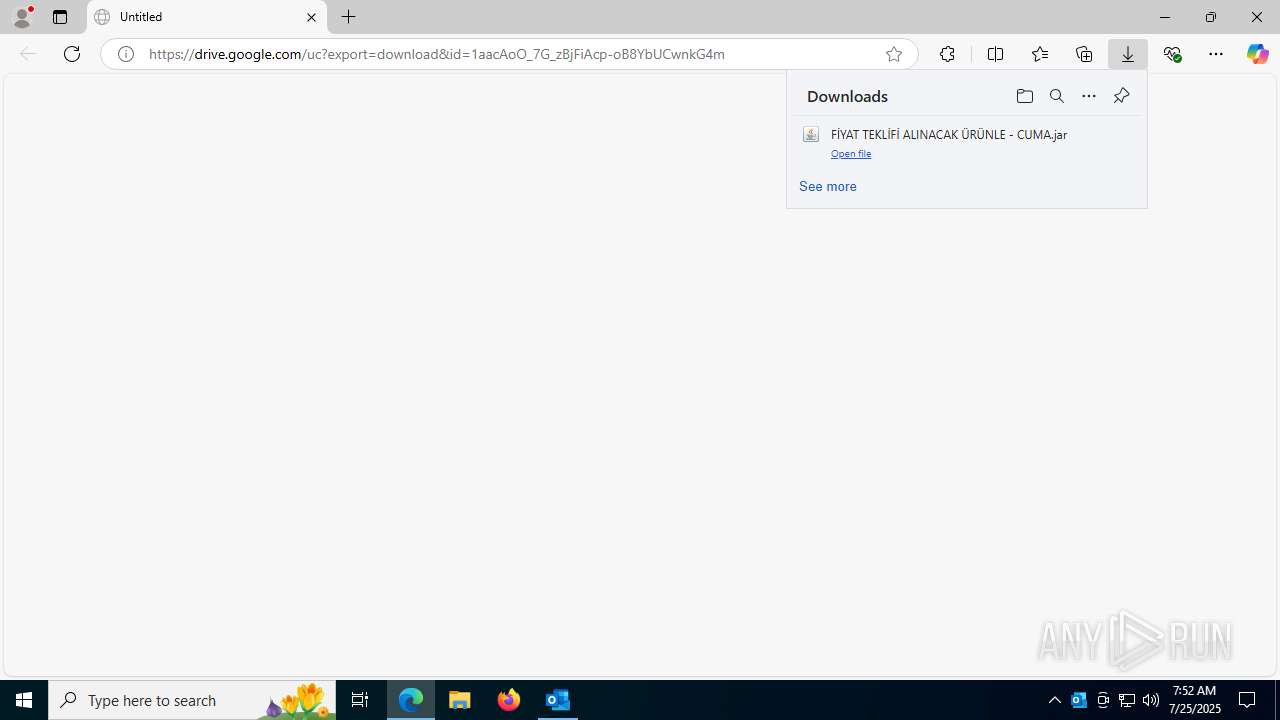
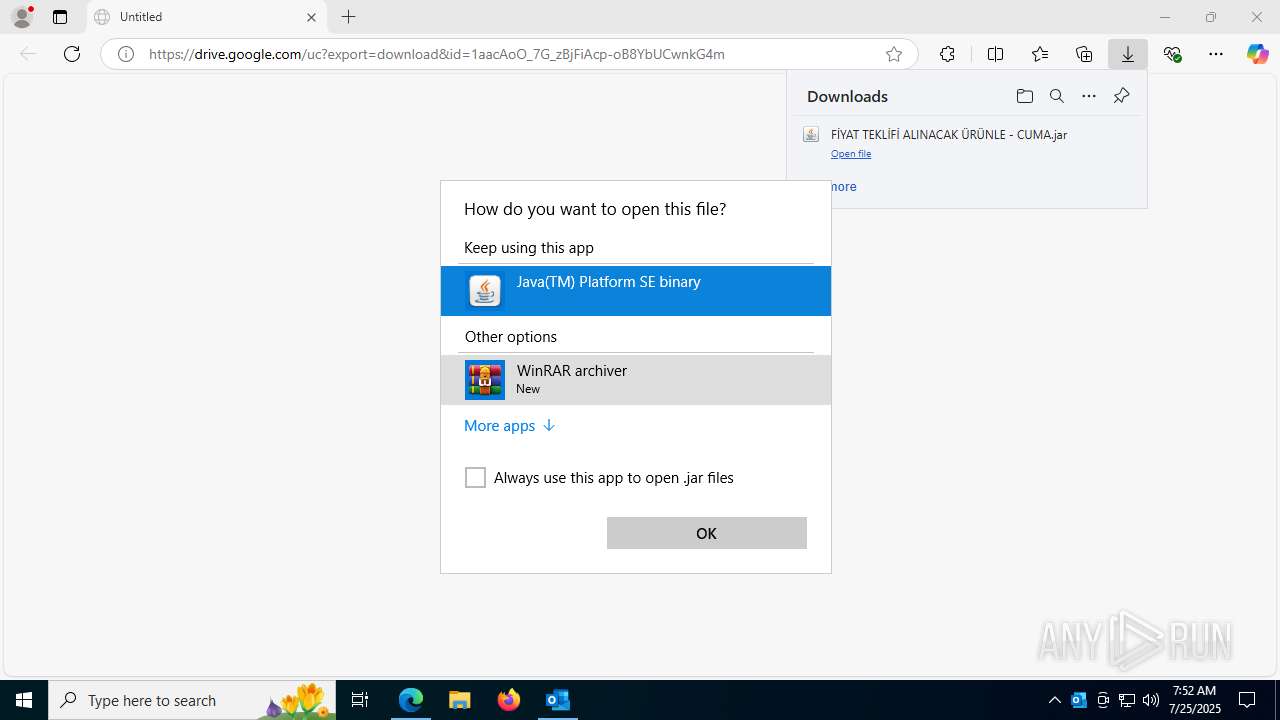
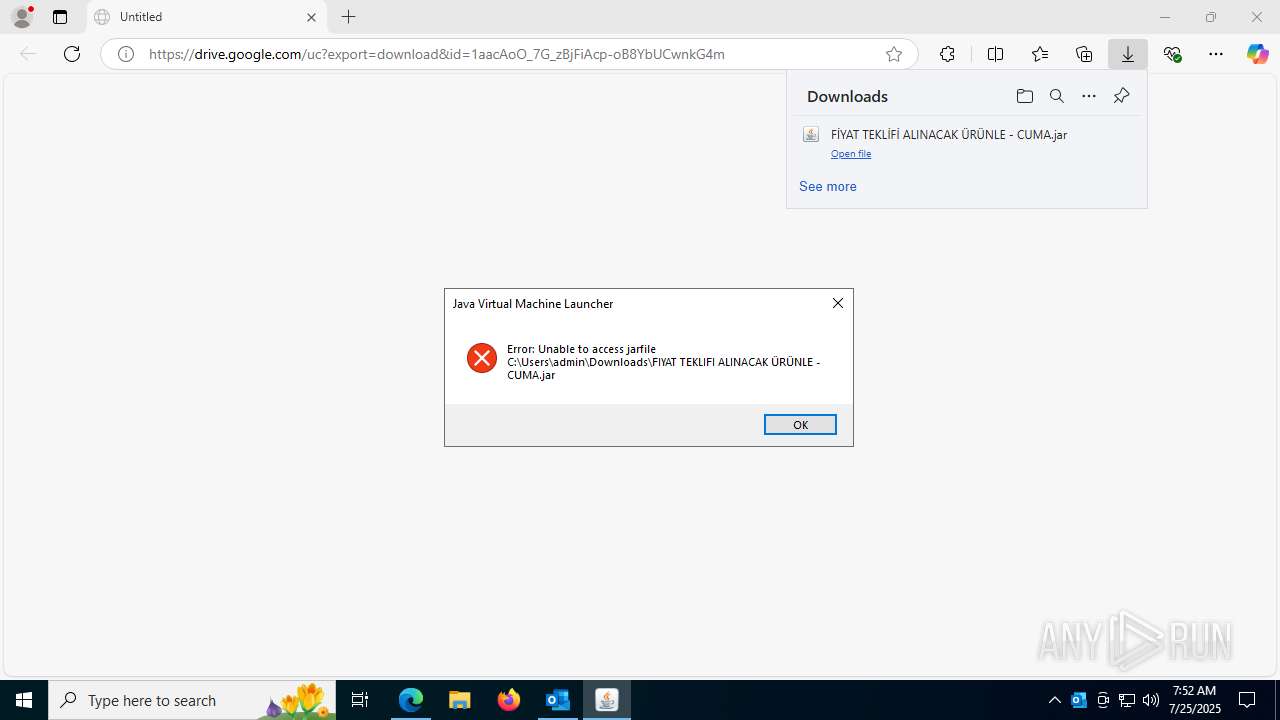
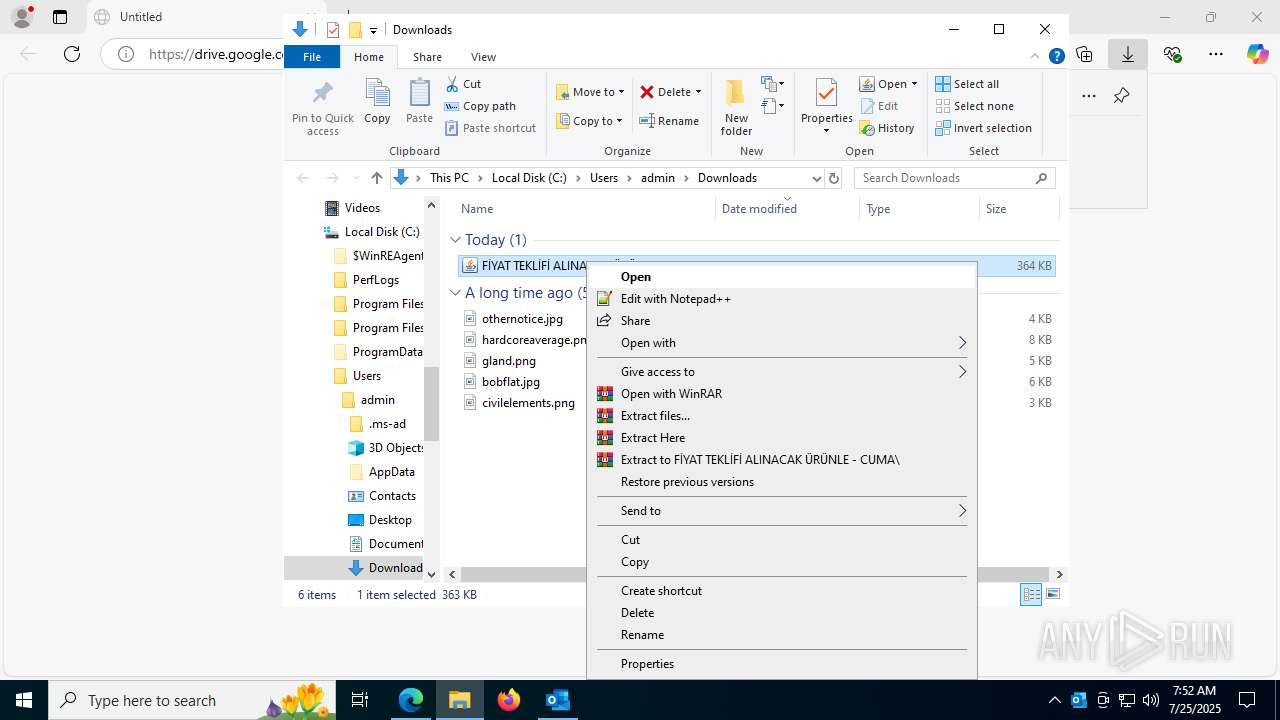
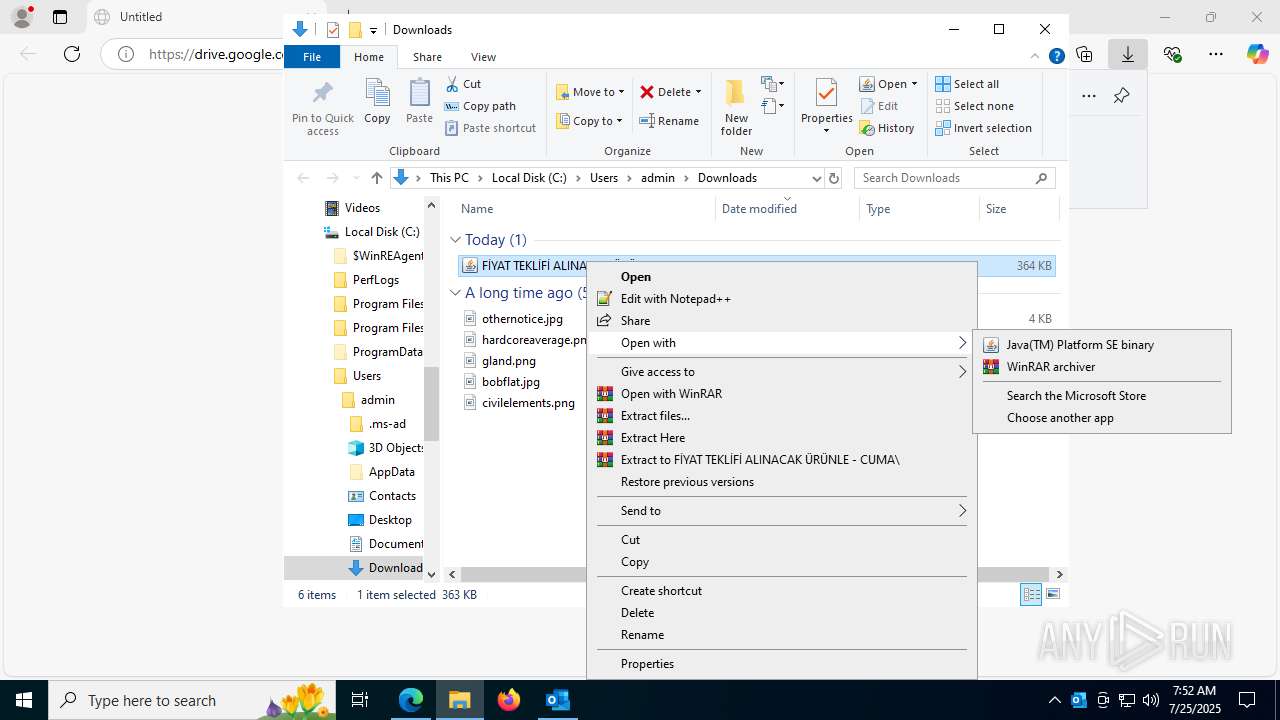
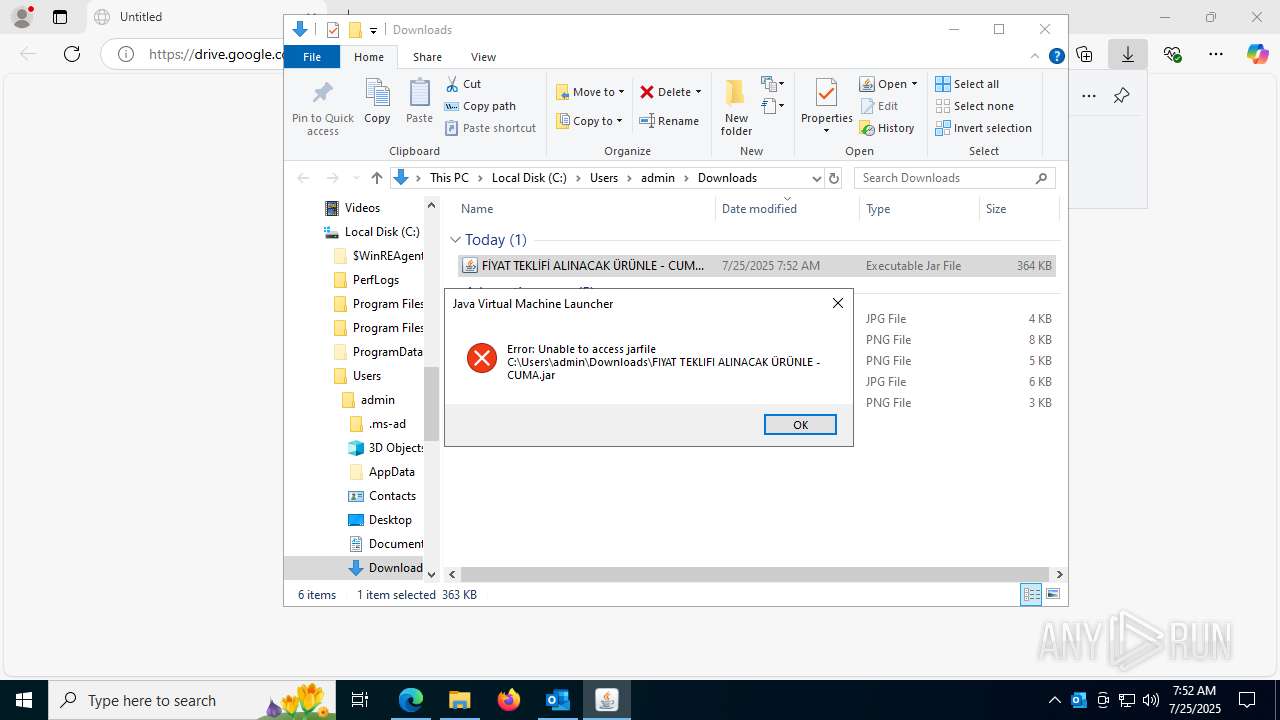
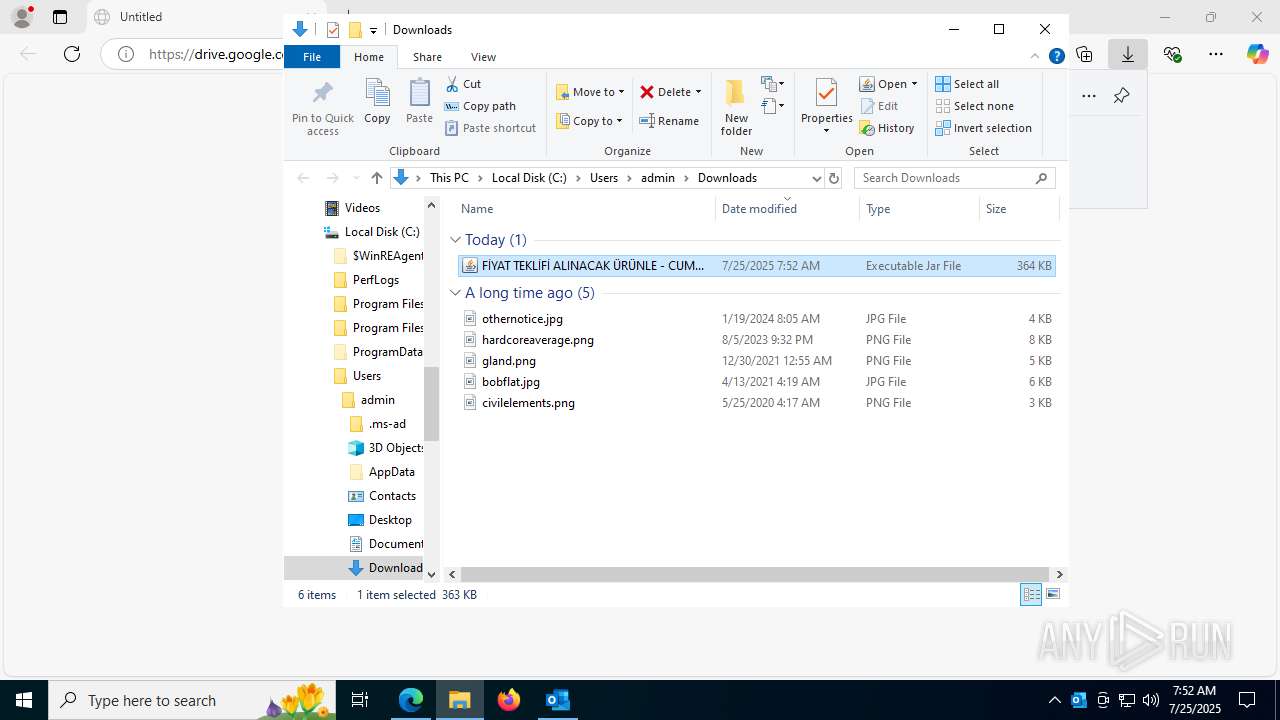
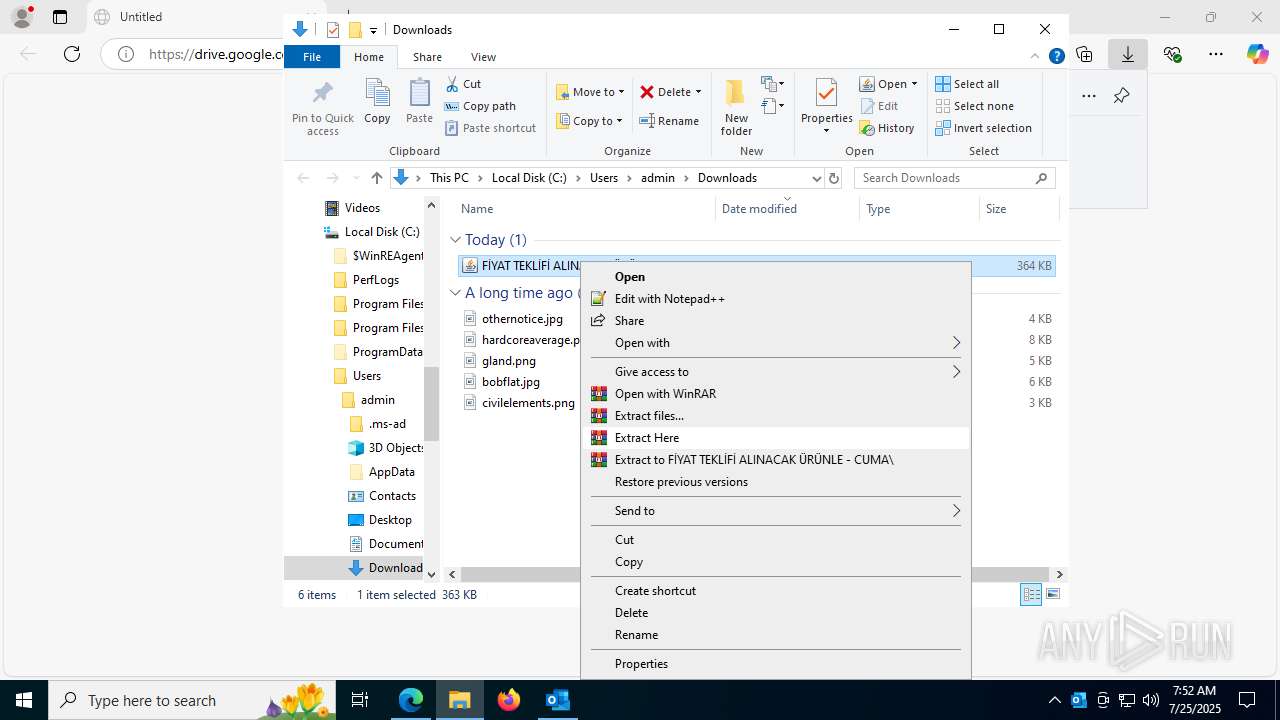
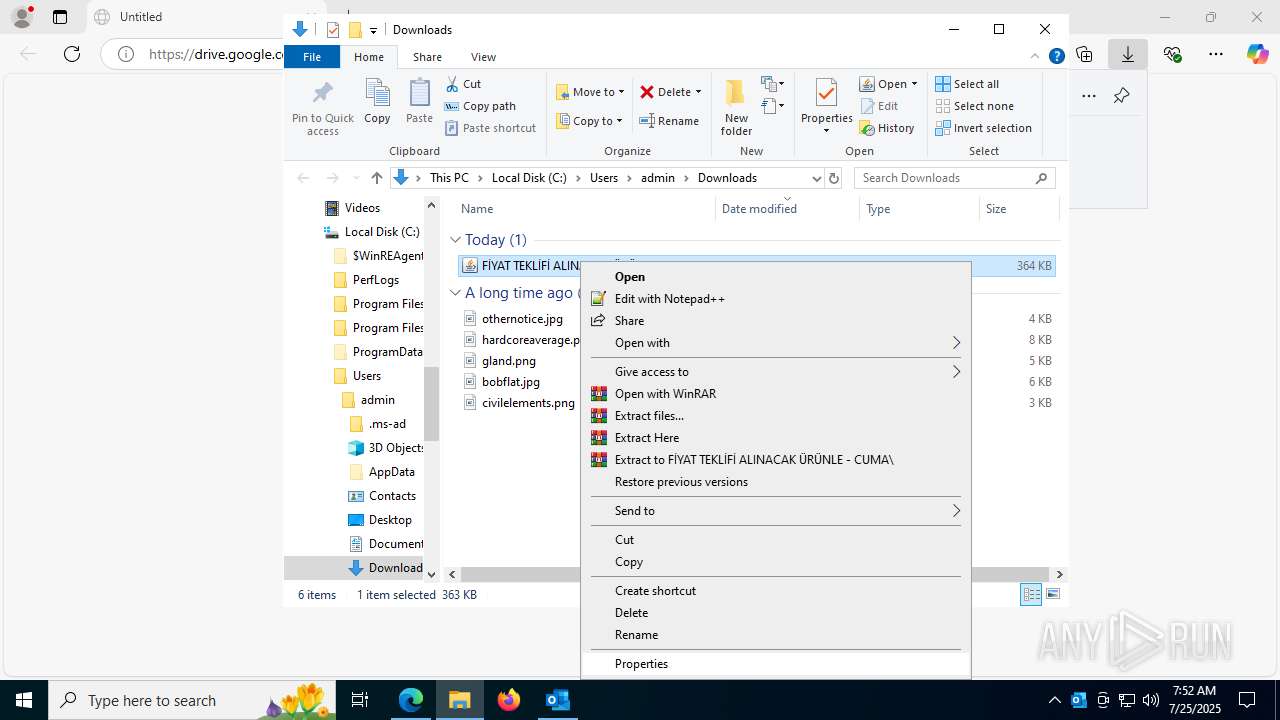
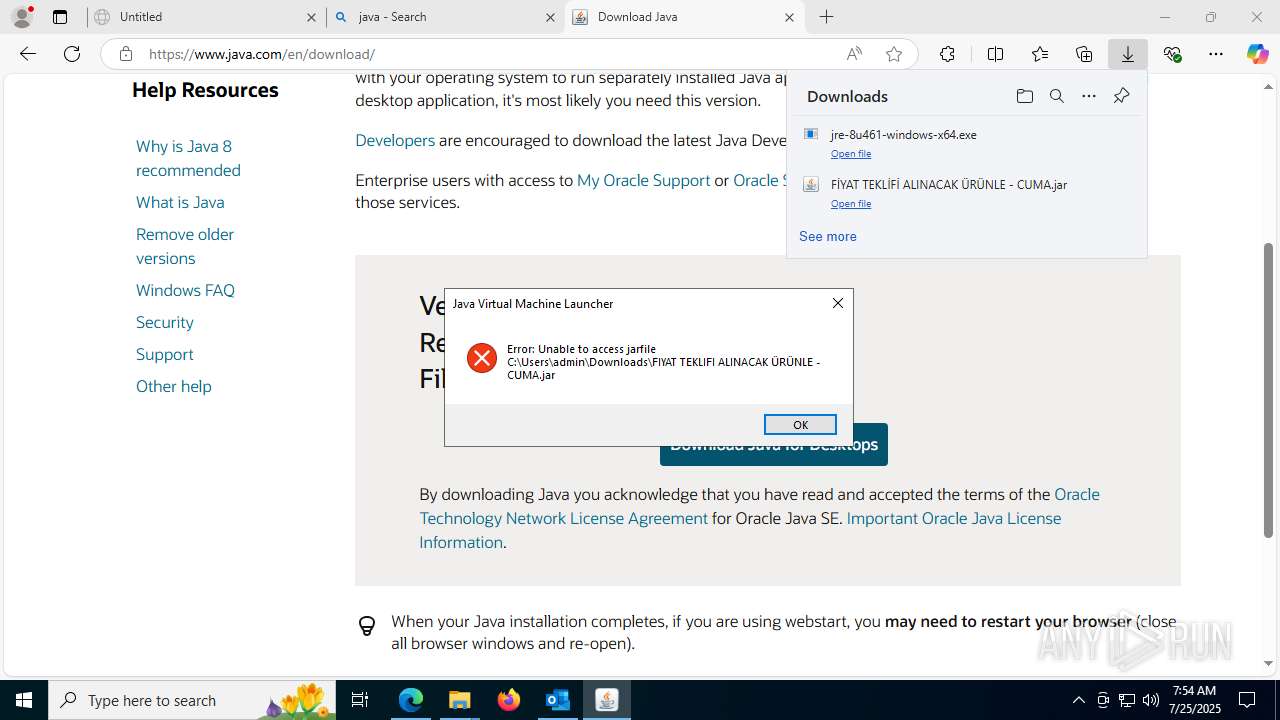
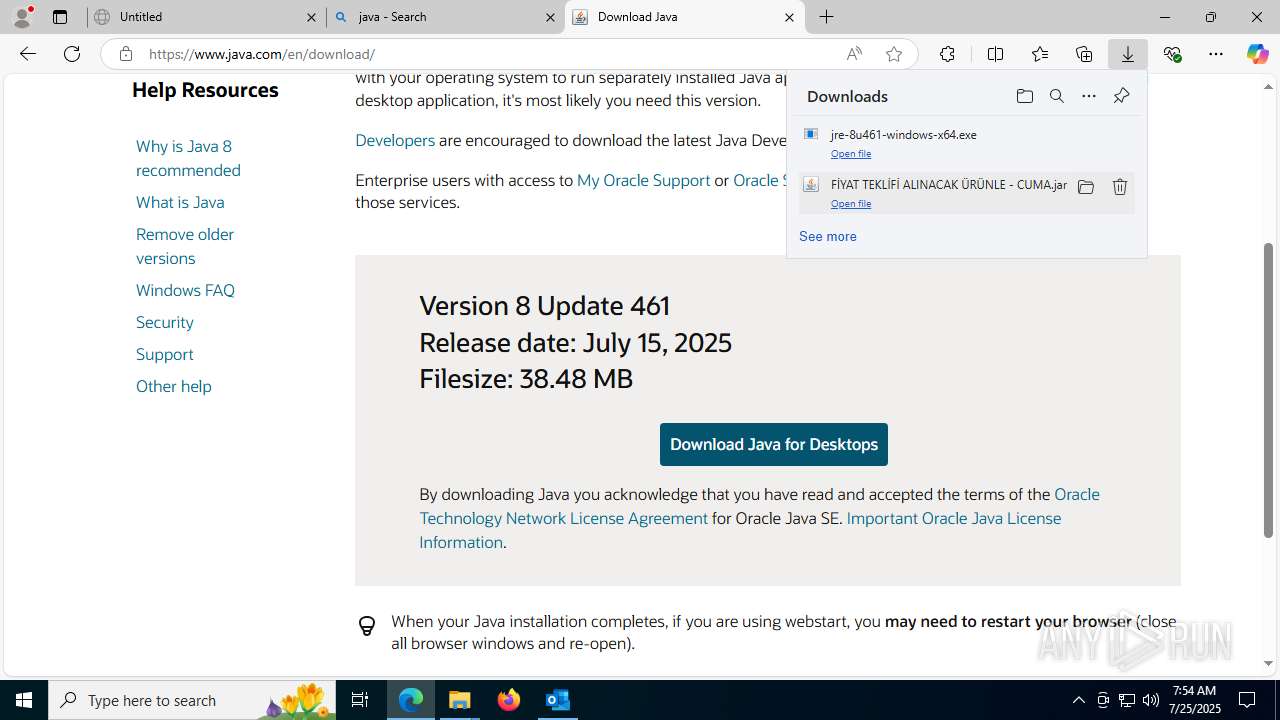
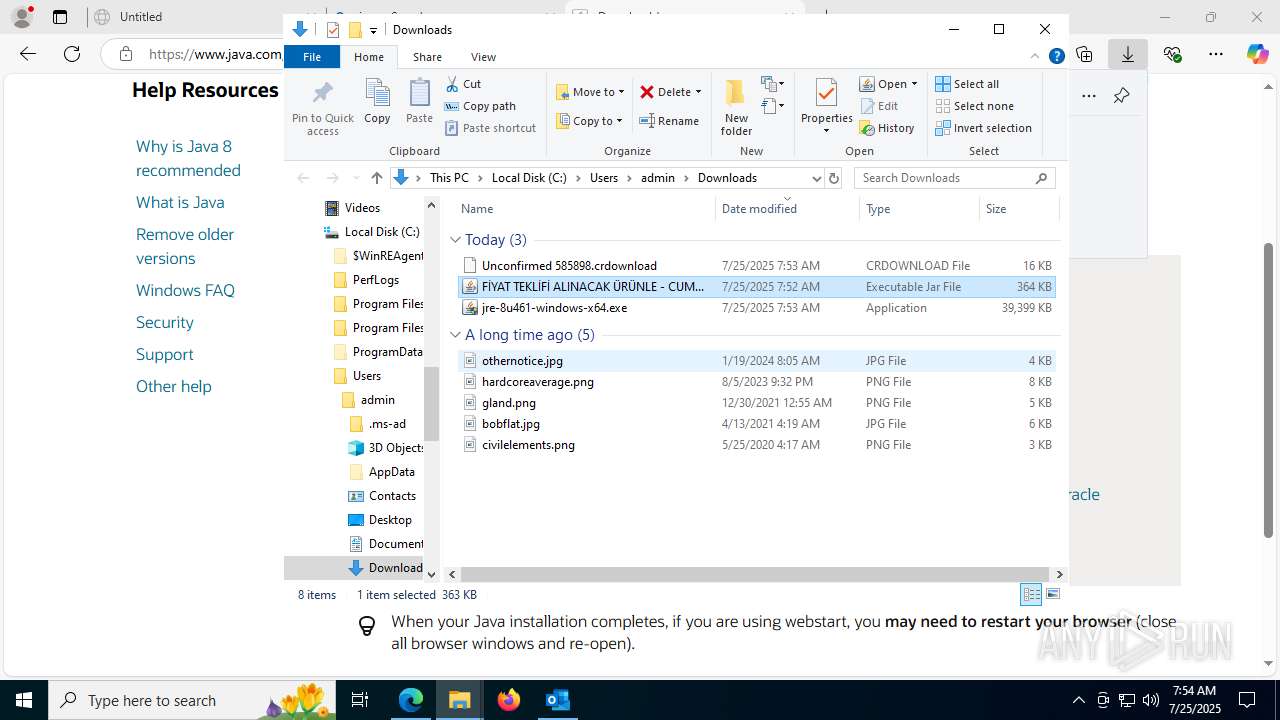
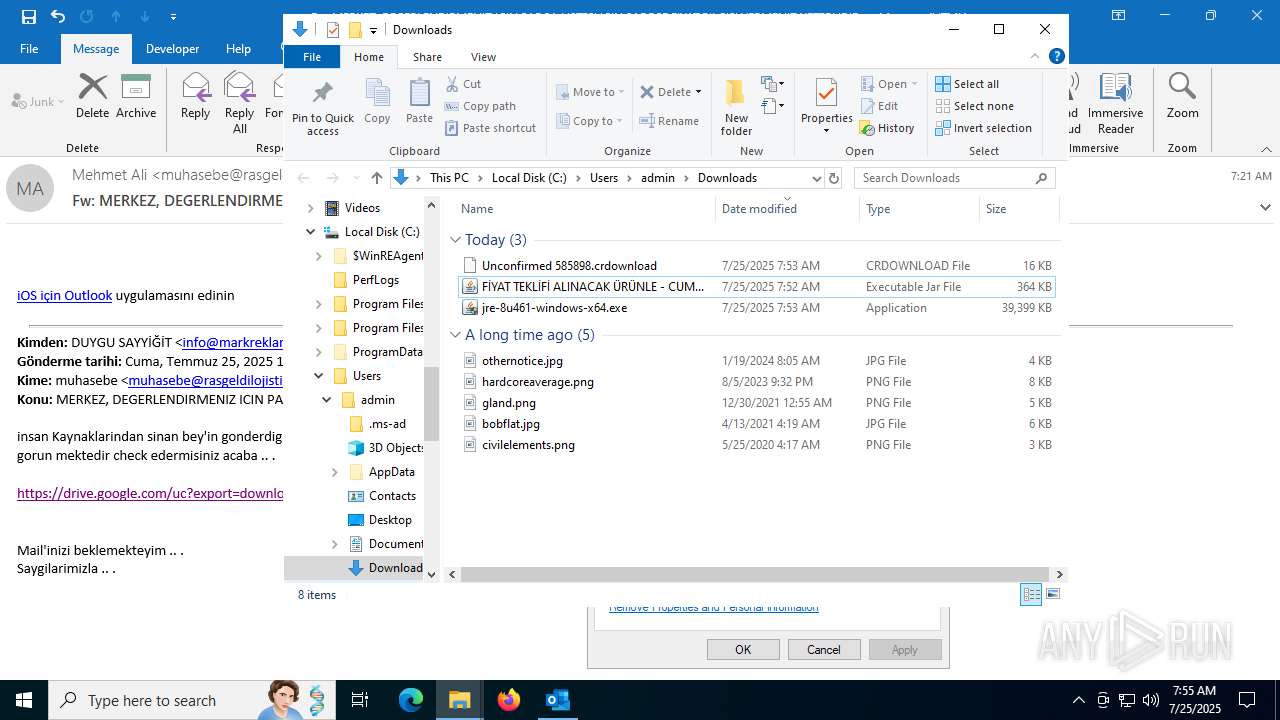
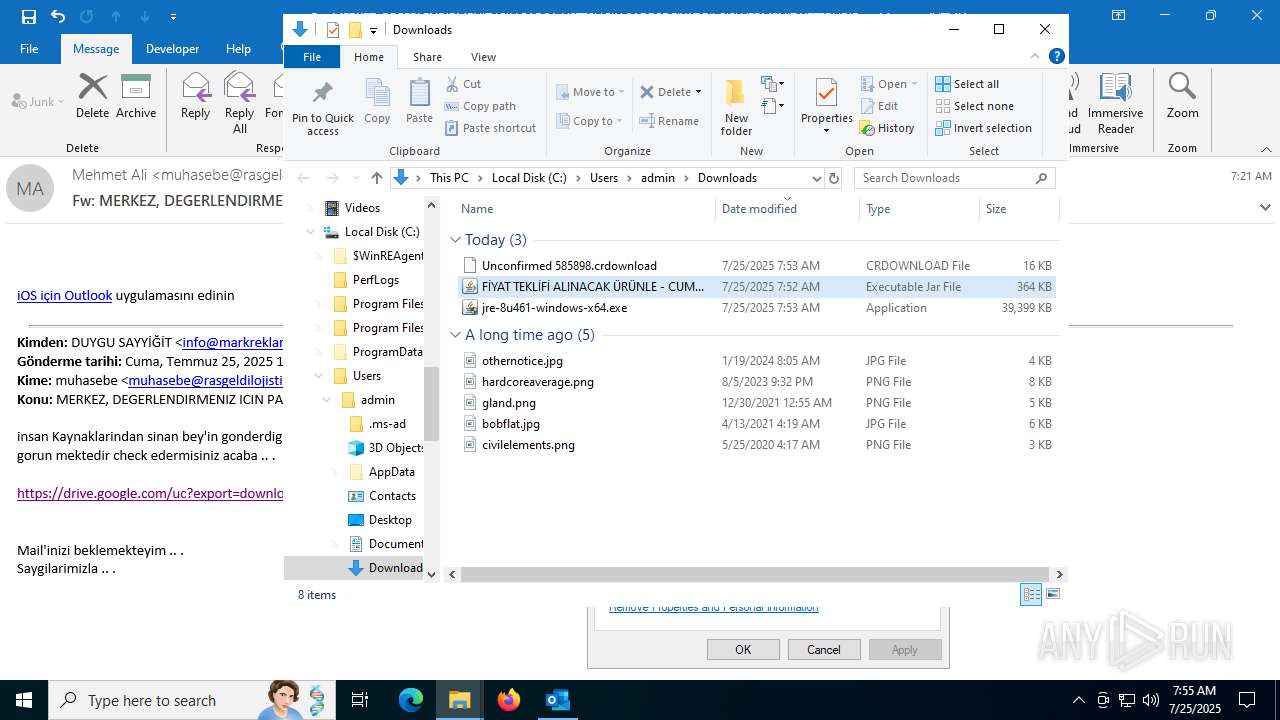
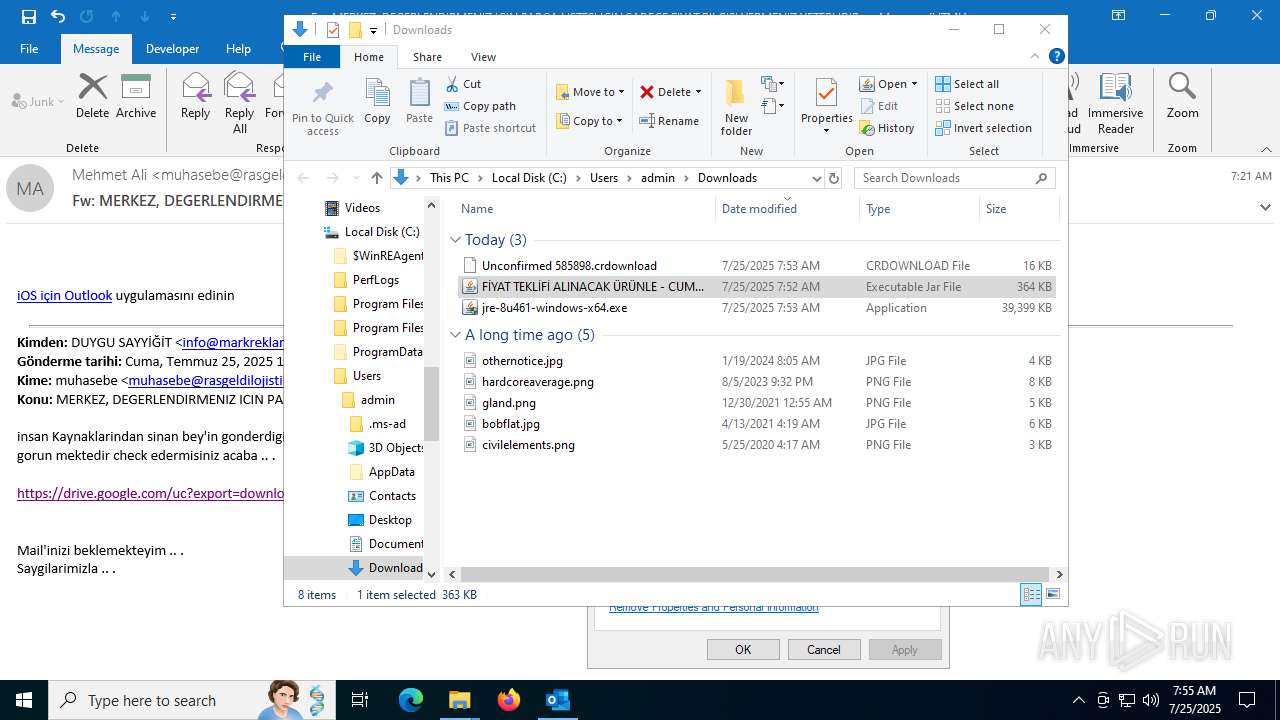
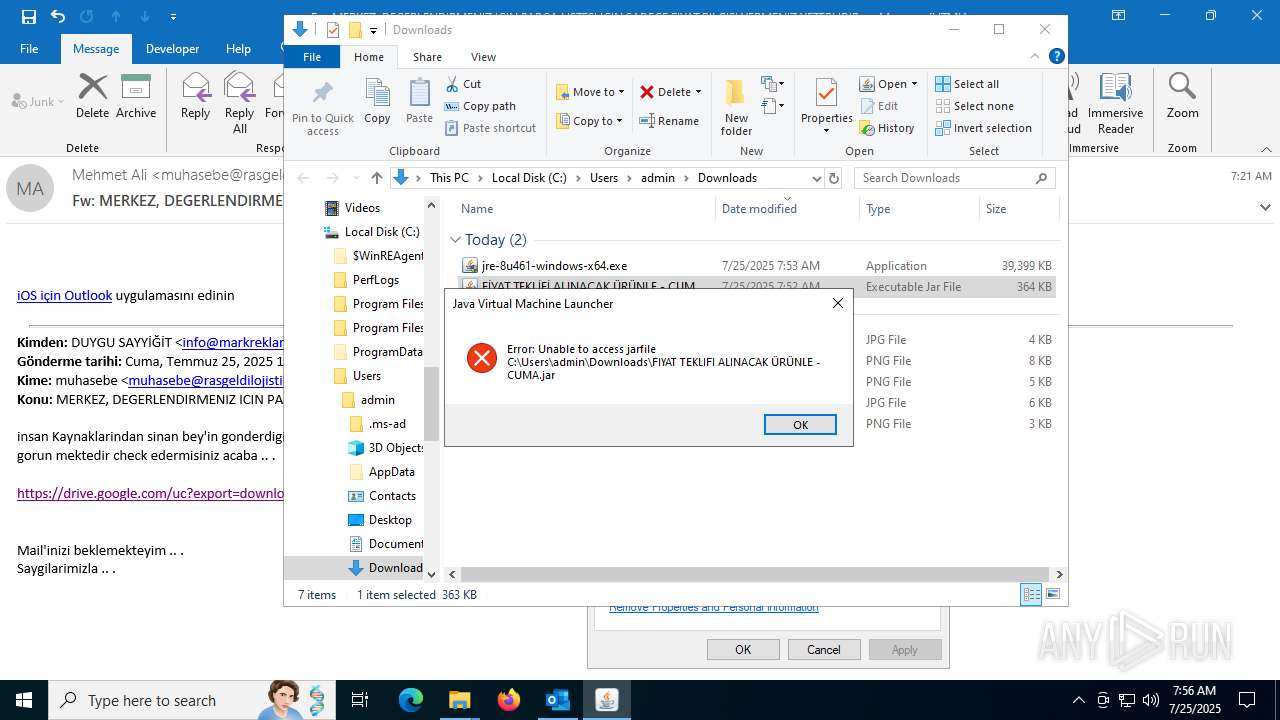
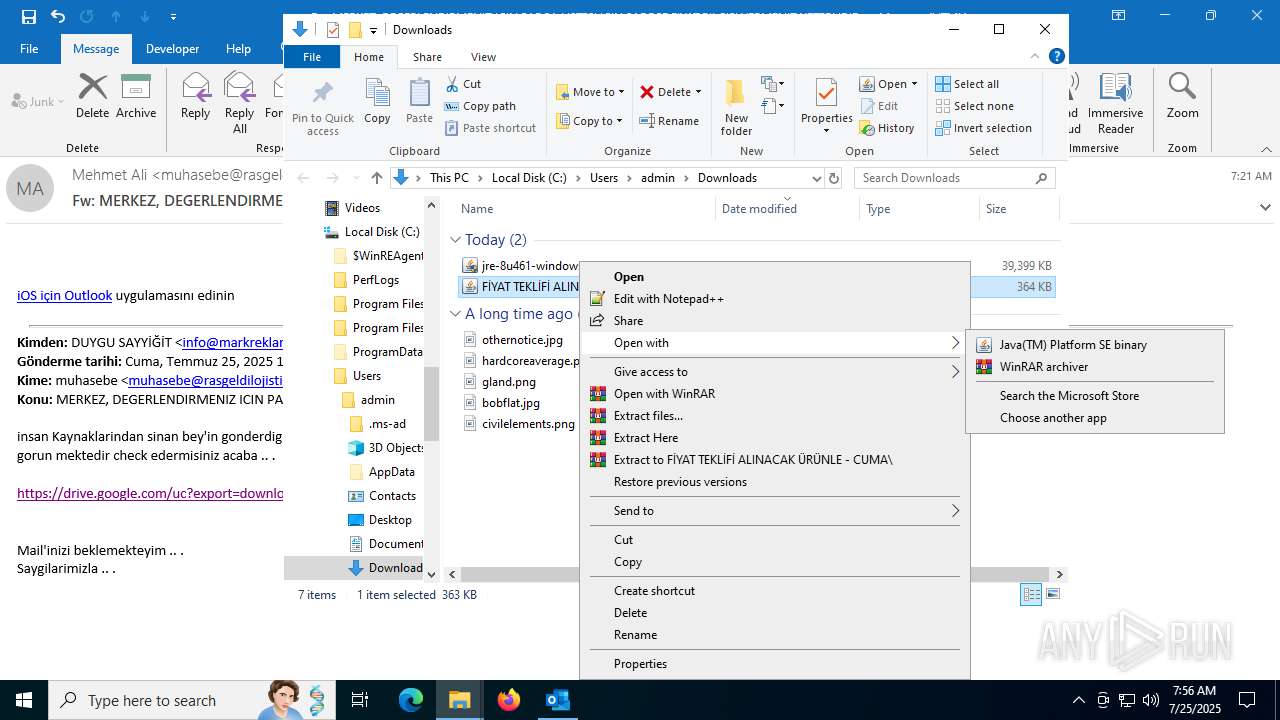
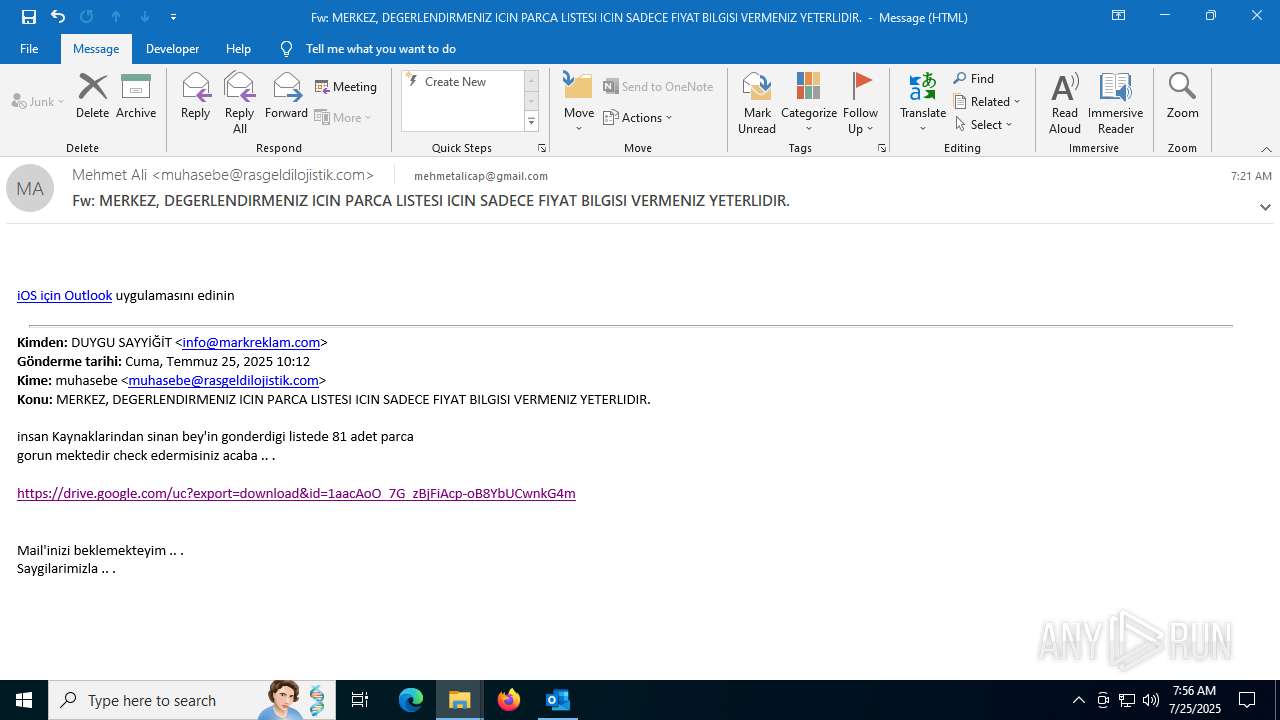
| File name: | Fw_ MERKEZ, DEGERLENDIRMENIZ ICIN PARCA LISTESI ICIN SADECE FIYAT BILGISI VERMENIZ YETERLIDIR..eml |
| Full analysis: | https://app.any.run/tasks/8972387e-bd8b-4b66-ae6a-e9f0b70174be |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2025, 07:52:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 04E4FAAA0A82835175CA741FEC644123 |
| SHA1: | F5E0FDDD031E04E26BF169EE8DEAA39B6E988970 |
| SHA256: | 97D736116BCC26E6BE249D2C0881F2867BEC35ACF9795C60B825F3E43A99FDE1 |
| SSDEEP: | 96:26KET5Qa6wguB0CFGeCM6OFZQ6F4QI8s8ZSqPswhBjF2ryOnZzIUKtrna:29I50wguB0XedZQ6NI8s8ZDPsmYryOZJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
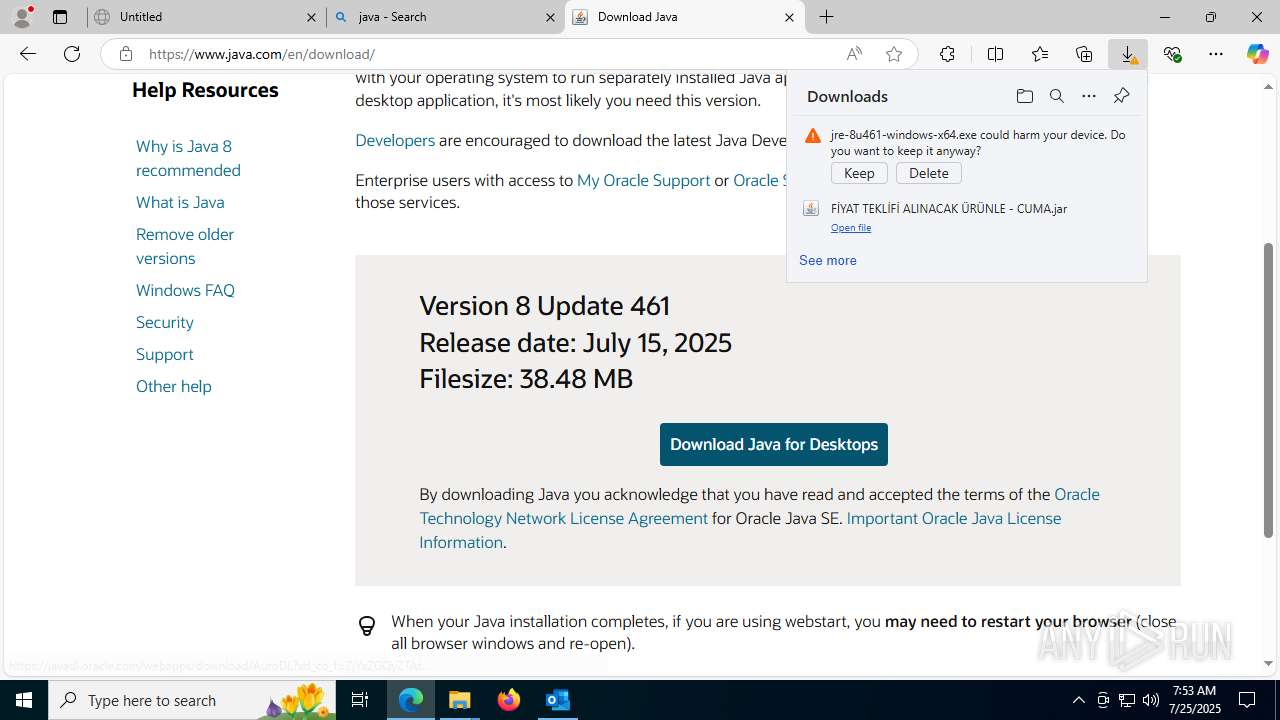
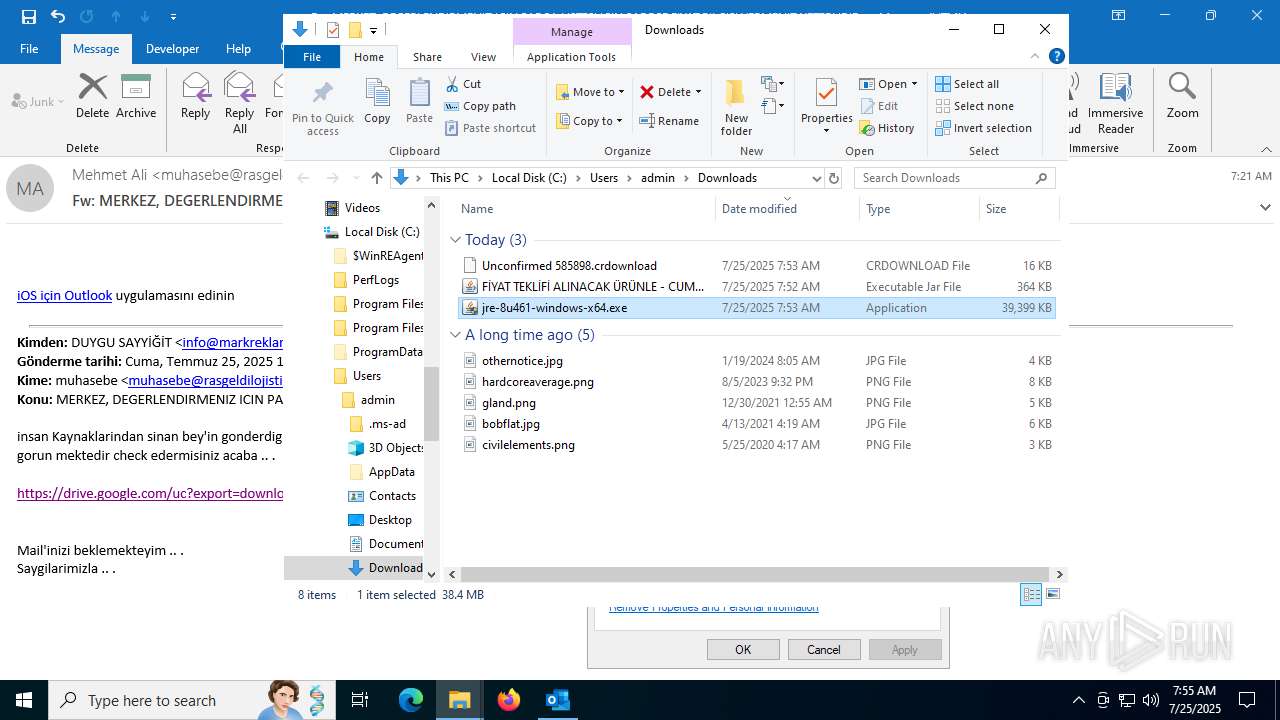
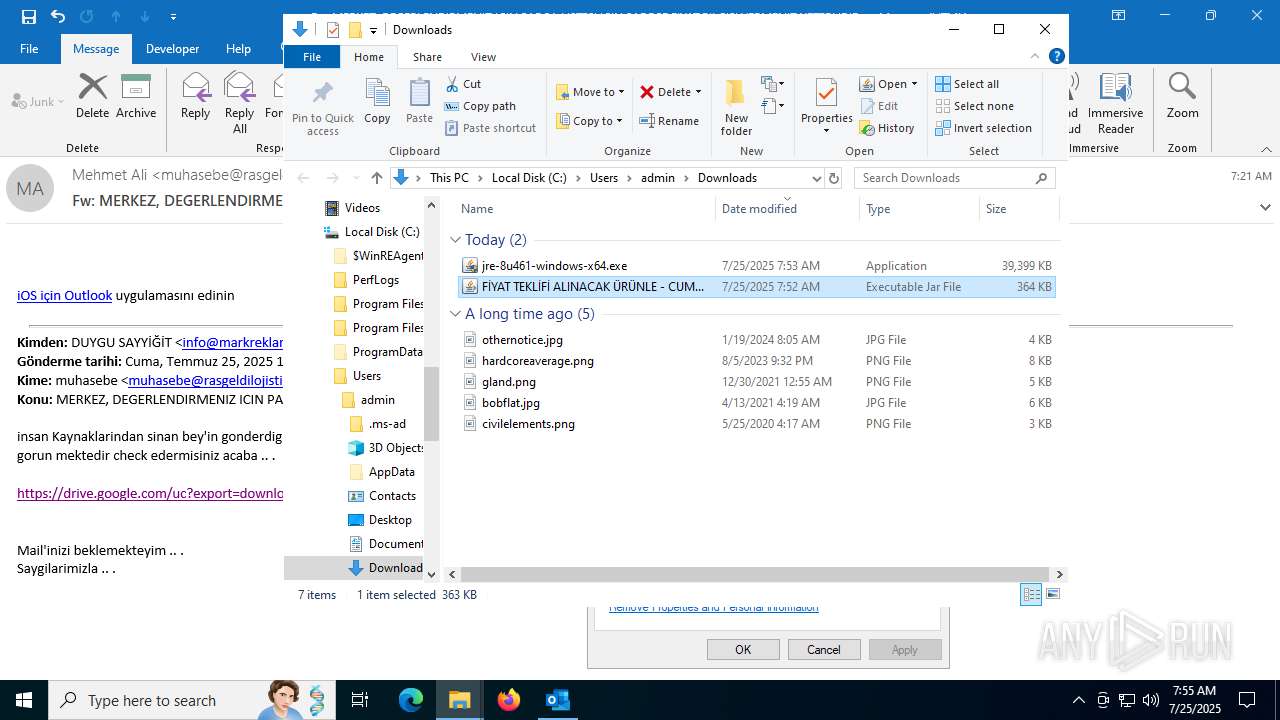
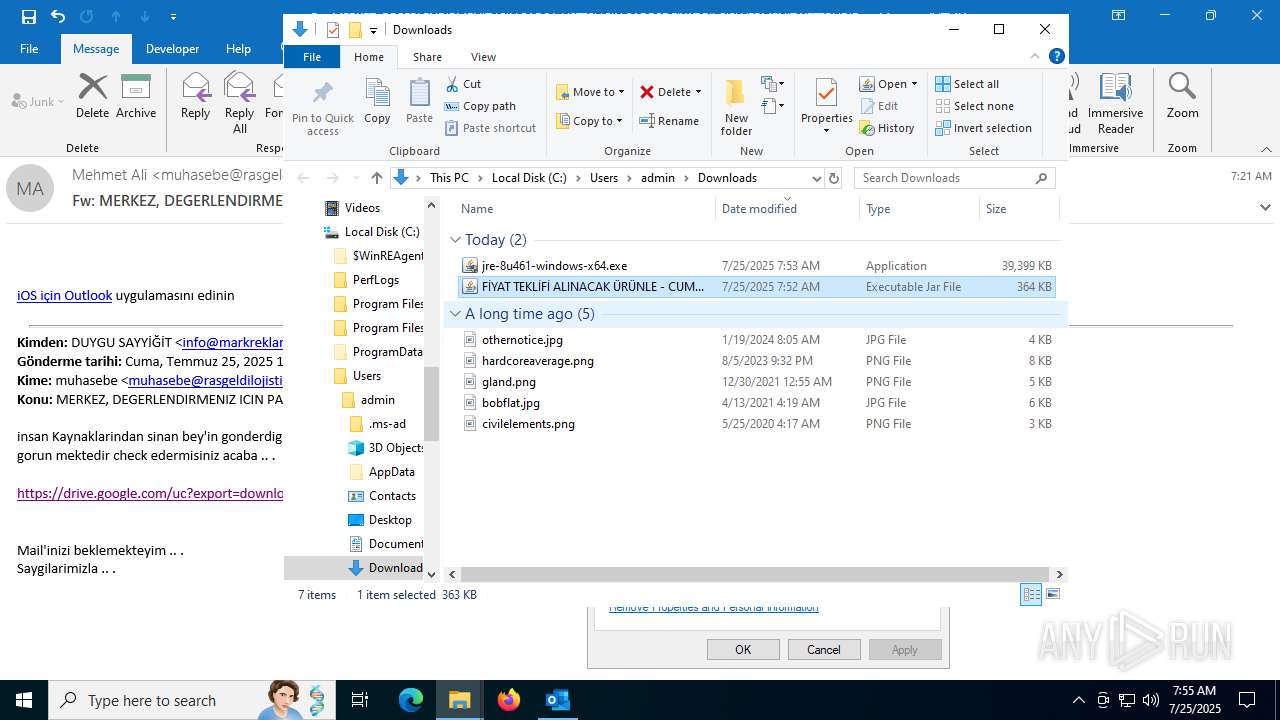
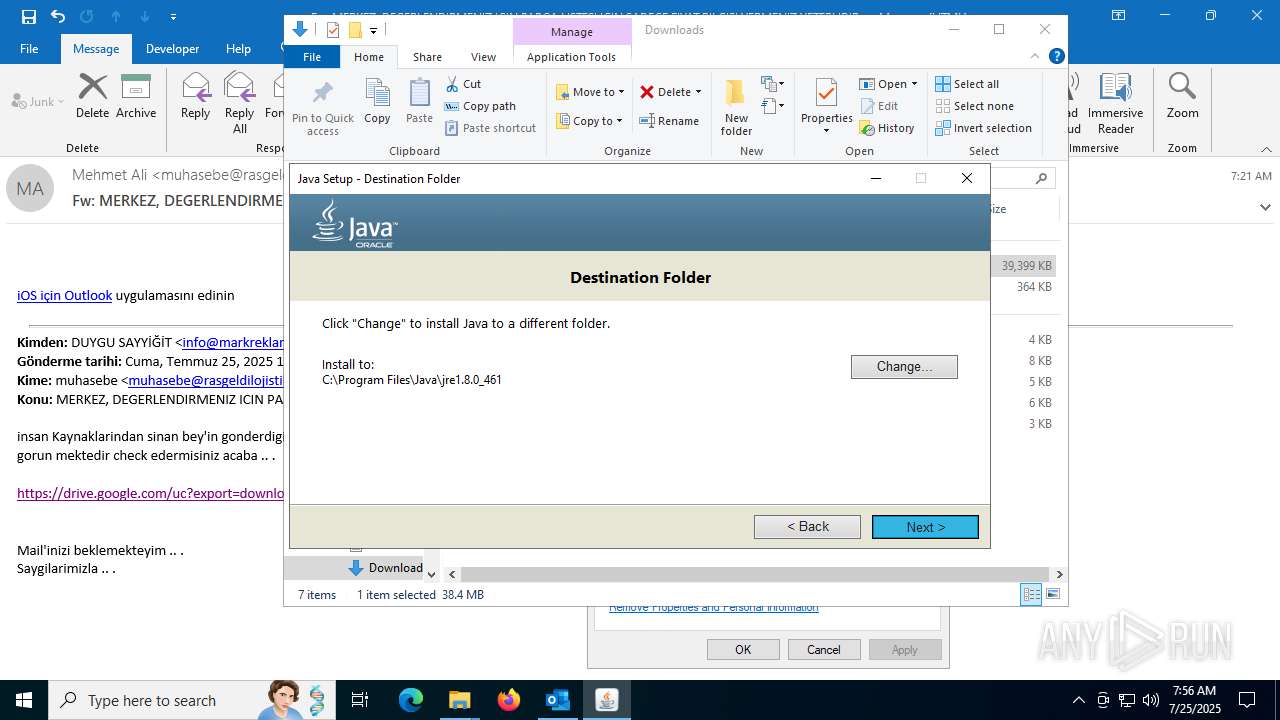
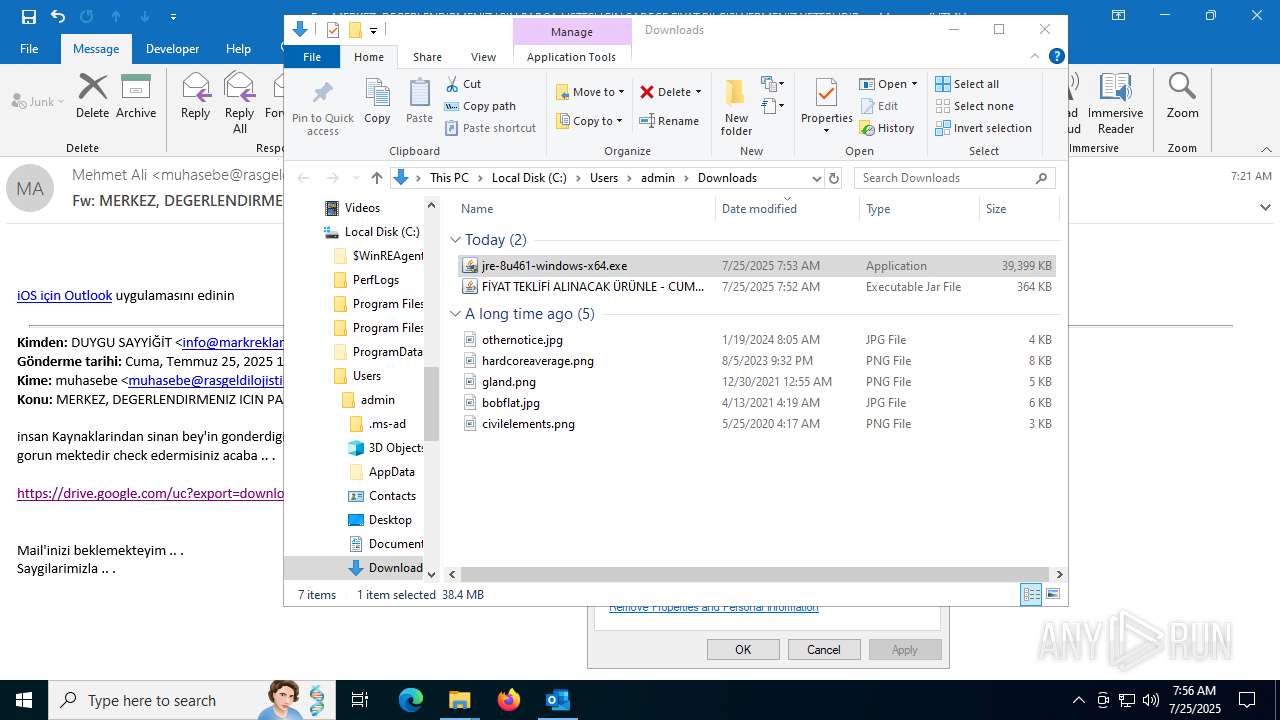
- jre-8u461-windows-x64.exe (PID: 5884)
- jre-8u461-windows-x64.exe (PID: 7364)
Reads Internet Explorer settings
- jre-8u461-windows-x64.exe (PID: 5884)
- jre-8u461-windows-x64.exe (PID: 7364)
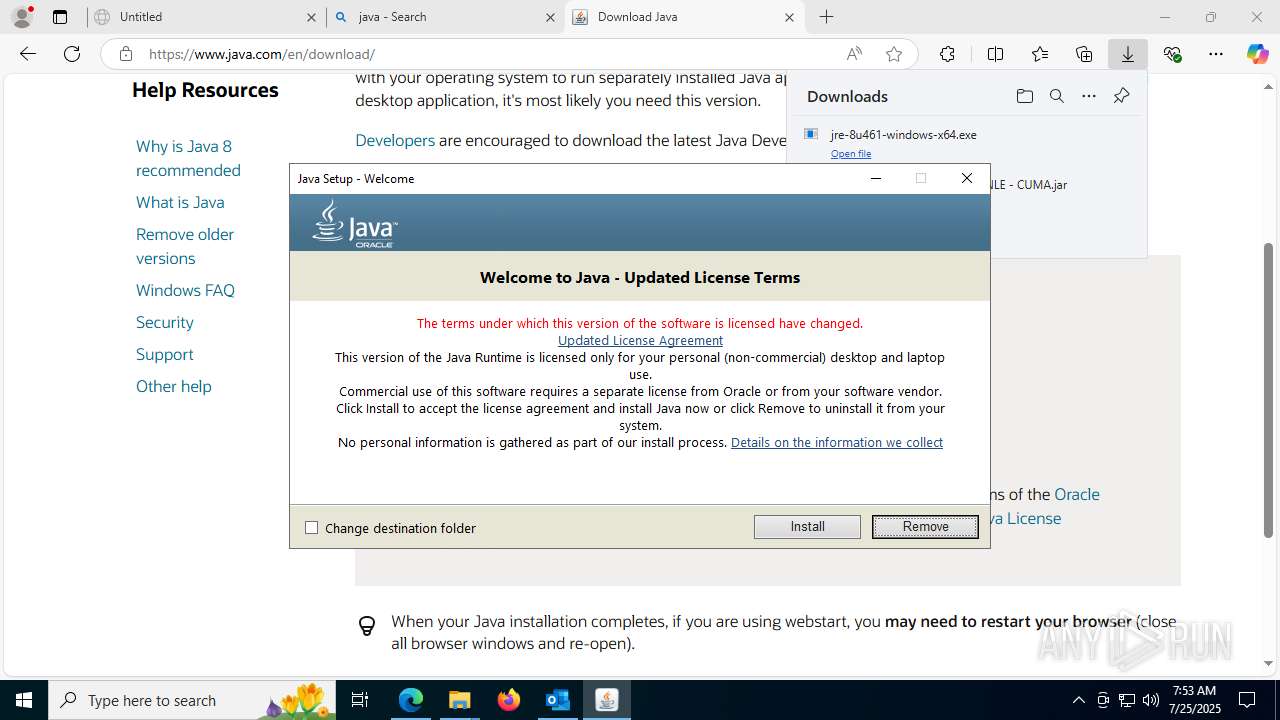
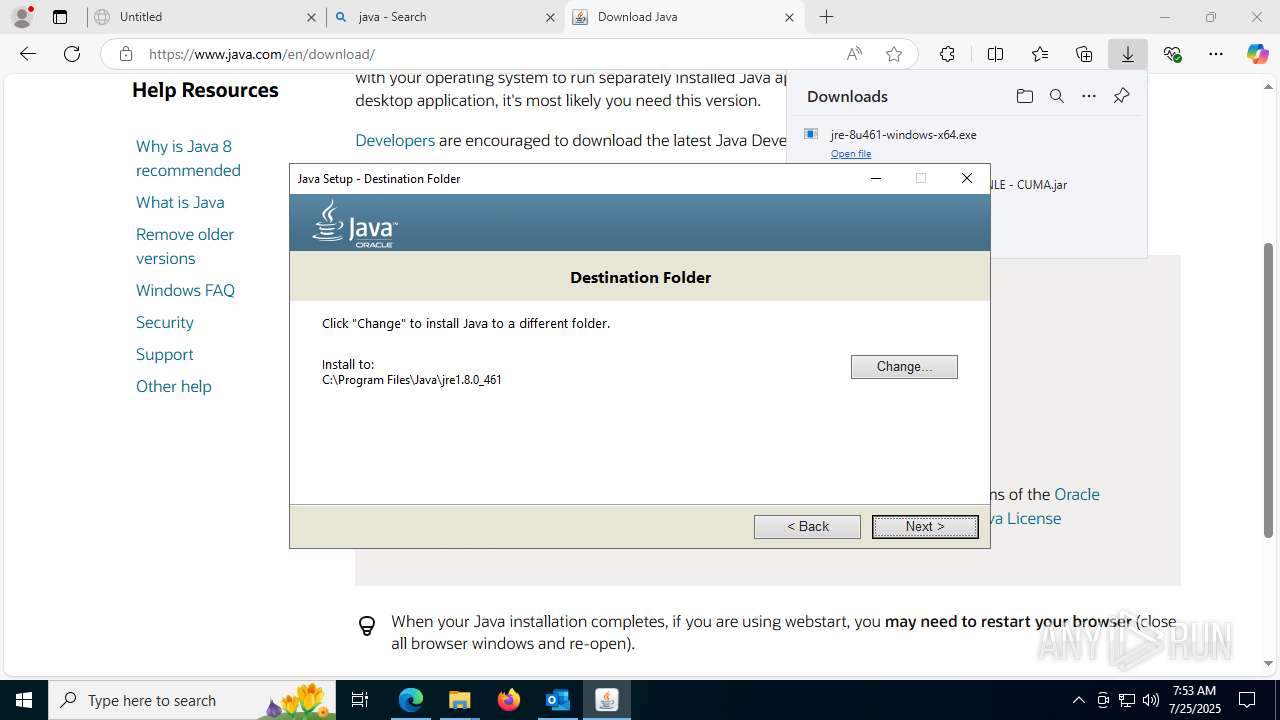
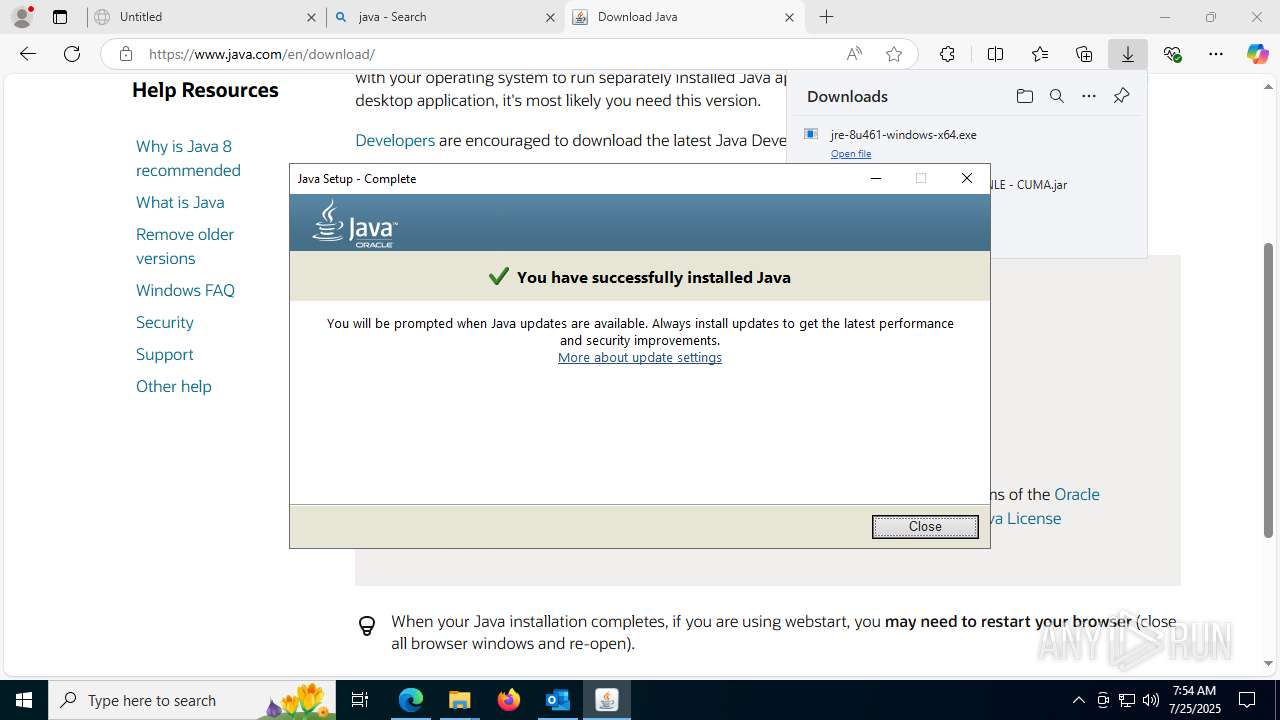
Checks for Java to be installed
- jre-8u461-windows-x64.exe (PID: 5884)
- msiexec.exe (PID: 1324)
- msiexec.exe (PID: 8004)
- installer.exe (PID: 1668)
- jp2launcher.exe (PID: 2632)
- ssvagent.exe (PID: 7860)
- msiexec.exe (PID: 3052)
- jp2launcher.exe (PID: 7328)
- javaw.exe (PID: 236)
- jucheck.exe (PID: 7368)
- javaw.exe (PID: 4084)
- jre-8u461-windows-x64.exe (PID: 7364)
- msiexec.exe (PID: 4512)
- ssvagent.exe (PID: 3580)
- installer.exe (PID: 3540)
- jp2launcher.exe (PID: 7340)
- msiexec.exe (PID: 4056)
- jp2launcher.exe (PID: 7420)
- javaw.exe (PID: 7616)
Reads security settings of Internet Explorer
- jre-8u461-windows-x64.exe (PID: 5884)
- installer.exe (PID: 1668)
- jp2launcher.exe (PID: 2632)
- jp2launcher.exe (PID: 7328)
- jre-8u461-windows-x64.exe (PID: 7364)
- installer.exe (PID: 3540)
- jp2launcher.exe (PID: 7340)
- jp2launcher.exe (PID: 7420)
Application launched itself
- msiexec.exe (PID: 1324)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1324)
The process drops C-runtime libraries
- msiexec.exe (PID: 1324)
Reads Mozilla Firefox installation path
- MSI6A70.tmp (PID: 7288)
- installer.exe (PID: 1668)
- javaw.exe (PID: 4084)
- MSIF8C2.tmp (PID: 7560)
- installer.exe (PID: 3540)
Process drops legitimate windows executable
- msiexec.exe (PID: 1324)
There is functionality for taking screenshot (YARA)
- jre-8u461-windows-x64.exe (PID: 5884)
Creates/Modifies COM task schedule object
- installer.exe (PID: 1668)
- ssvagent.exe (PID: 7860)
- installer.exe (PID: 3540)
- ssvagent.exe (PID: 3580)
Executable content was dropped or overwritten
- installer.exe (PID: 1668)
- jre-8u461-windows-x64.exe (PID: 5884)
- installer.exe (PID: 3540)
- jre-8u461-windows-x64.exe (PID: 7364)
Creates file in the systems drive root
- OpenWith.exe (PID: 4444)
INFO
Reads the computer name
- identity_helper.exe (PID: 7768)
- javaw.exe (PID: 8132)
- javaw.exe (PID: 8064)
- msiexec.exe (PID: 1324)
- jre-8u461-windows-x64.exe (PID: 8152)
- jre-8u461-windows-x64.exe (PID: 5884)
- msiexec.exe (PID: 8004)
- installer.exe (PID: 1668)
- MSI6A70.tmp (PID: 7288)
- javaws.exe (PID: 6068)
- jp2launcher.exe (PID: 2632)
- javaws.exe (PID: 8168)
- jp2launcher.exe (PID: 7328)
- msiexec.exe (PID: 3052)
- msiexec.exe (PID: 7900)
- javaw.exe (PID: 236)
- javaw.exe (PID: 7308)
- msiexec.exe (PID: 620)
- javaw.exe (PID: 5140)
- javaw.exe (PID: 7328)
- msiexec.exe (PID: 436)
- jucheck.exe (PID: 7368)
- identity_helper.exe (PID: 7004)
- javaw.exe (PID: 4084)
- jre-8u461-windows-x64.exe (PID: 4120)
- jre-8u461-windows-x64.exe (PID: 7364)
- MSIF8C2.tmp (PID: 7560)
- msiexec.exe (PID: 2760)
- msiexec.exe (PID: 4512)
- msiexec.exe (PID: 7216)
- installer.exe (PID: 3540)
- msiexec.exe (PID: 1740)
- javaws.exe (PID: 8072)
- jp2launcher.exe (PID: 7340)
- msiexec.exe (PID: 4056)
- jp2launcher.exe (PID: 7420)
- javaws.exe (PID: 6364)
- javaw.exe (PID: 7616)
- javaw.exe (PID: 7712)
- javaw.exe (PID: 4196)
- msiexec.exe (PID: 1136)
- msiexec.exe (PID: 1056)
- javaw.exe (PID: 8136)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4748)
- OpenWith.exe (PID: 7932)
- OpenWith.exe (PID: 4444)
Checks supported languages
- identity_helper.exe (PID: 7768)
- javaw.exe (PID: 8132)
- javaw.exe (PID: 8064)
- jre-8u461-windows-x64.exe (PID: 8152)
- jre-8u461-windows-x64.exe (PID: 5884)
- MSI6A70.tmp (PID: 7288)
- msiexec.exe (PID: 1324)
- msiexec.exe (PID: 8004)
- installer.exe (PID: 1668)
- jaureg.exe (PID: 516)
- javaw.exe (PID: 7792)
- javaws.exe (PID: 6068)
- jp2launcher.exe (PID: 2632)
- javaws.exe (PID: 8168)
- jp2launcher.exe (PID: 7328)
- ssvagent.exe (PID: 7860)
- msiexec.exe (PID: 3052)
- msiexec.exe (PID: 7900)
- javaw.exe (PID: 236)
- javaw.exe (PID: 5140)
- javacpl.exe (PID: 236)
- javaw.exe (PID: 7308)
- msiexec.exe (PID: 436)
- msiexec.exe (PID: 620)
- javaw.exe (PID: 7328)
- javaw.exe (PID: 4084)
- jucheck.exe (PID: 7368)
- identity_helper.exe (PID: 7004)
- jre-8u461-windows-x64.exe (PID: 7364)
- MSIF8C2.tmp (PID: 7560)
- msiexec.exe (PID: 2760)
- jaureg.exe (PID: 8020)
- jre-8u461-windows-x64.exe (PID: 4120)
- msiexec.exe (PID: 4512)
- msiexec.exe (PID: 7216)
- msiexec.exe (PID: 1740)
- javaws.exe (PID: 8072)
- jp2launcher.exe (PID: 7420)
- installer.exe (PID: 3540)
- javaw.exe (PID: 7320)
- ssvagent.exe (PID: 3580)
- javaws.exe (PID: 6364)
- jp2launcher.exe (PID: 7340)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 1136)
- javaw.exe (PID: 4196)
- msiexec.exe (PID: 1056)
- javaw.exe (PID: 8136)
- javaw.exe (PID: 7616)
- javaw.exe (PID: 7712)
Reads Environment values
- identity_helper.exe (PID: 7768)
- jre-8u461-windows-x64.exe (PID: 5884)
- identity_helper.exe (PID: 7004)
- jre-8u461-windows-x64.exe (PID: 7364)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 7932)
- OpenWith.exe (PID: 4444)
Application launched itself
- msedge.exe (PID: 4748)
- msedge.exe (PID: 4864)
Application based on Java
- javaw.exe (PID: 8132)
- javaw.exe (PID: 8064)
- javaw.exe (PID: 5140)
- javaw.exe (PID: 4196)
Manual execution by a user
- javaw.exe (PID: 8064)
- javacpl.exe (PID: 236)
- jre-8u461-windows-x64.exe (PID: 2692)
- jre-8u461-windows-x64.exe (PID: 4120)
- javaw.exe (PID: 4196)
Create files in a temporary directory
- jre-8u461-windows-x64.exe (PID: 8152)
- javaw.exe (PID: 7792)
- MSI6A70.tmp (PID: 7288)
- jp2launcher.exe (PID: 2632)
- jp2launcher.exe (PID: 7328)
- javaw.exe (PID: 7308)
- javaw.exe (PID: 4084)
- jre-8u461-windows-x64.exe (PID: 4120)
- javaw.exe (PID: 7320)
- jp2launcher.exe (PID: 7340)
- jp2launcher.exe (PID: 7420)
- javaw.exe (PID: 8136)
Executable content was dropped or overwritten
- msedge.exe (PID: 4748)
- msiexec.exe (PID: 1324)
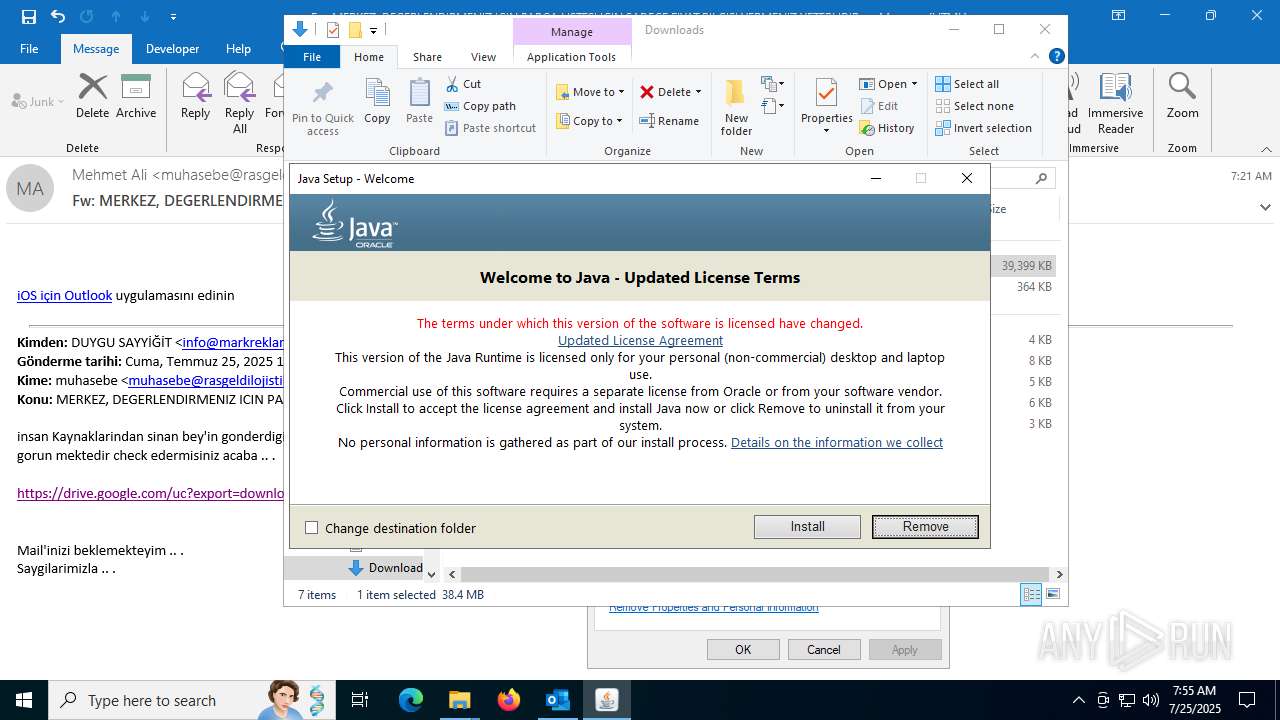
Java executable
- jre-8u461-windows-x64.exe (PID: 8152)
- jre-8u461-windows-x64.exe (PID: 5968)
- jre-8u461-windows-x64.exe (PID: 5884)
- MSI6A70.tmp (PID: 7288)
- installer.exe (PID: 1668)
- jre-8u461-windows-x64.exe (PID: 2692)
- jre-8u461-windows-x64.exe (PID: 7364)
- MSIF8C2.tmp (PID: 7560)
- jre-8u461-windows-x64.exe (PID: 4120)
- installer.exe (PID: 3540)
Checks proxy server information
- jre-8u461-windows-x64.exe (PID: 5884)
- slui.exe (PID: 7856)
- jp2launcher.exe (PID: 2632)
- jp2launcher.exe (PID: 7328)
- jre-8u461-windows-x64.exe (PID: 7364)
- jp2launcher.exe (PID: 7420)
- jp2launcher.exe (PID: 7340)
Reads the machine GUID from the registry
- jre-8u461-windows-x64.exe (PID: 5884)
- msiexec.exe (PID: 1324)
- javaw.exe (PID: 4084)
- jre-8u461-windows-x64.exe (PID: 7364)
Creates files or folders in the user directory
- jre-8u461-windows-x64.exe (PID: 5884)
- msiexec.exe (PID: 1324)
- javaw.exe (PID: 4084)
- jre-8u461-windows-x64.exe (PID: 7364)
Reads the software policy settings
- jre-8u461-windows-x64.exe (PID: 5884)
- msiexec.exe (PID: 1324)
- slui.exe (PID: 7856)
- jre-8u461-windows-x64.exe (PID: 7364)
The sample compiled with english language support
- msiexec.exe (PID: 1324)
- installer.exe (PID: 1668)
- jre-8u461-windows-x64.exe (PID: 5884)
- installer.exe (PID: 3540)
- jre-8u461-windows-x64.exe (PID: 7364)
Reads CPU info
- msiexec.exe (PID: 1324)
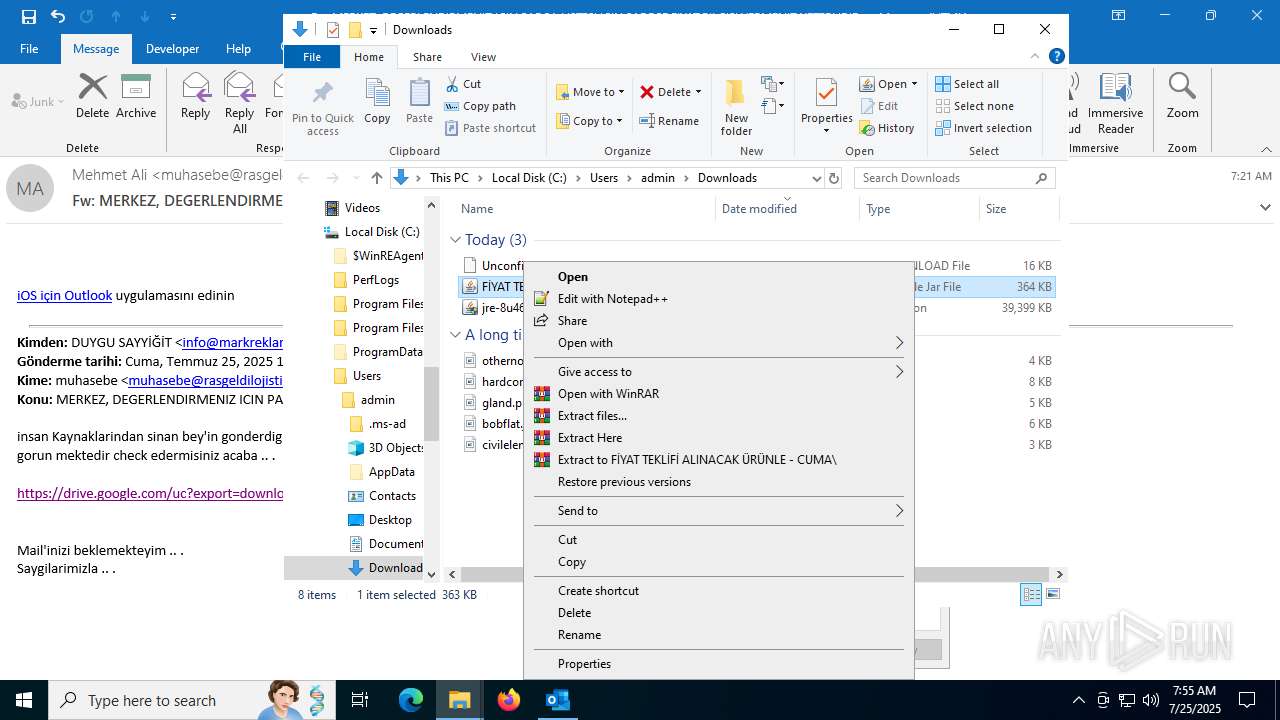
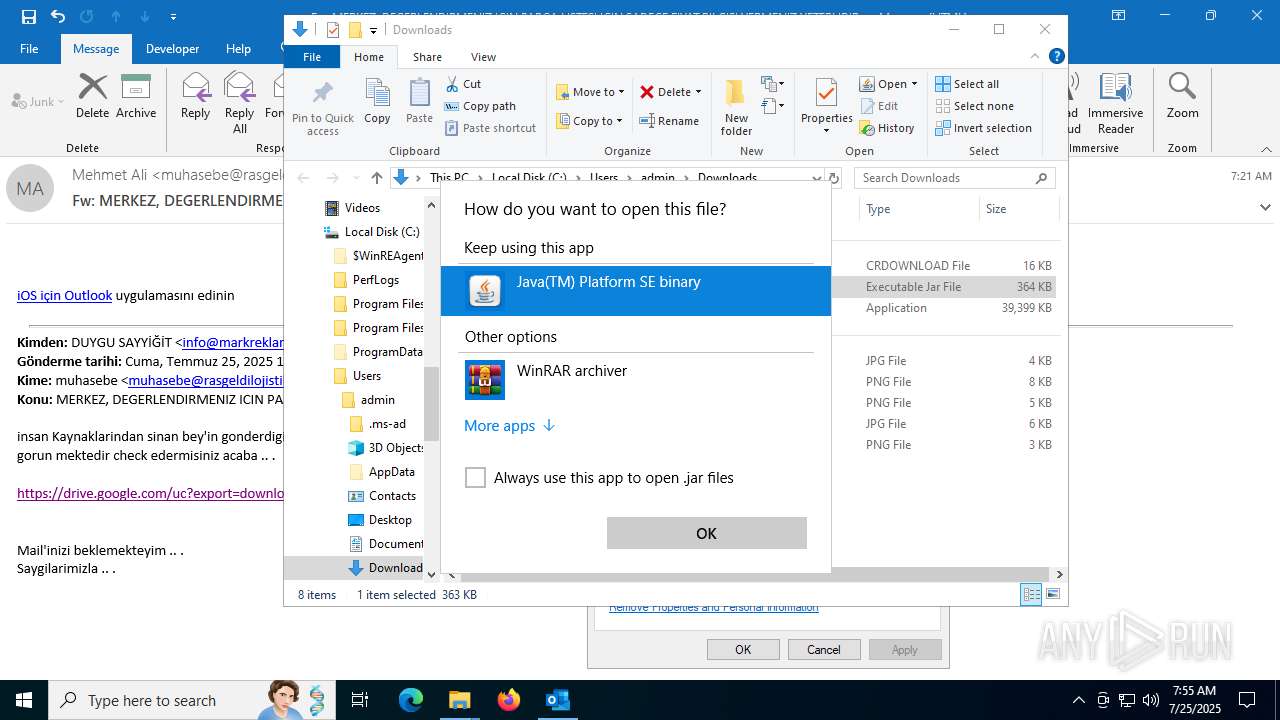
Starts application with an unusual extension
- msiexec.exe (PID: 1324)
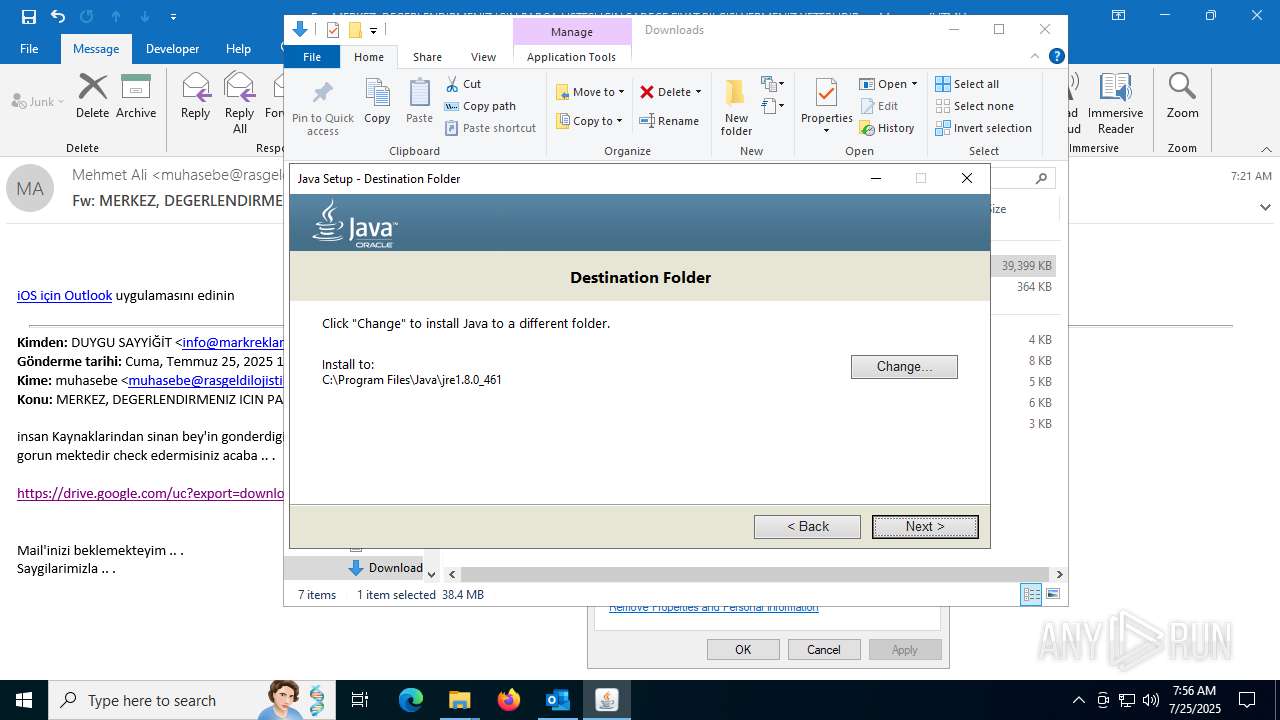
Creates files in the program directory
- installer.exe (PID: 1668)
- javaw.exe (PID: 7792)
- installer.exe (PID: 3540)
- javaw.exe (PID: 7320)
Creates a software uninstall entry
- msiexec.exe (PID: 1324)
JAVA mutex has been found
- jp2launcher.exe (PID: 2632)
- jp2launcher.exe (PID: 7328)
- msiexec.exe (PID: 7900)
- msiexec.exe (PID: 436)
- msiexec.exe (PID: 4512)
- jp2launcher.exe (PID: 7340)
- jp2launcher.exe (PID: 7420)
- msiexec.exe (PID: 1136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 7) (100) |
|---|
Total processes
281
Monitored processes
120
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=8272,i,320755309266016854,5323904308623688703,262144 --variations-seed-version --mojo-platform-channel-handle=8180 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 236 | -Djdk.disableLastUsageTracking -cp "C:\Program Files\Java\jre1.8.0_461\bin\..\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -getUserWebJavaStatus | C:\Program Files\Java\jre1.8.0_461\bin\javaw.exe | — | jre-8u461-windows-x64.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.4610.11 Modules
| |||||||||||||||
| 236 | "C:\Program Files\Java\jre1.8.0_461\bin\javacpl.exe" | C:\Program Files\Java\jre1.8.0_461\bin\javacpl.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Control Panel Exit code: 0 Version: 11.461.0.11 Modules
| |||||||||||||||
| 436 | C:\Windows\syswow64\MsiExec.exe -Embedding D35FDD997481C10297B1ABA1FBF09A5D | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Program Files (x86)\Common Files\Java\Java Update\jaureg.exe" -u auto-update | C:\Program Files (x86)\Common Files\Java\Java Update\jaureg.exe | MSI6A70.tmp | ||||||||||||
User: SYSTEM Company: Oracle Corporation Integrity Level: SYSTEM Description: Java Update Registration Exit code: 0 Version: 2.8.271.9 Modules
| |||||||||||||||
| 536 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2220,i,320755309266016854,5323904308623688703,262144 --variations-seed-version --mojo-platform-channel-handle=2548 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 620 | C:\Windows\syswow64\MsiExec.exe -Embedding AD10131299DA6FB875DE3752B7C50D3E E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "3603A16C-B76C-49B7-88AC-38DA2D03486B" "702D1FAB-E29E-459D-855D-9C034B2A0BD9" "3576" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1056 | C:\Windows\syswow64\MsiExec.exe -Embedding E2D76156C261CA3BE9C03B868A1C44AF E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | C:\Windows\syswow64\MsiExec.exe -Embedding 52171A86F2F24E7D82B650B44A3ECB71 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
120 647
Read events
52 539
Write events
26 903
Delete events
41 205
Modification events
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | SessionId |
Value: D3237F99-F829-44AC-8848-F16680E0A16E | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Preferences |
| Operation: | delete value | Name: | ChangeProfileOnRestart |
Value: | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 09000000 | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030397 |
Value: 60000000 | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Experiment\outlook |
| Operation: | write | Name: | BuildNumber |
Value: 16.0.16026 | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs |
| Operation: | write | Name: | CountryCode |
Value: std::wstring|NO | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs\outlook |
| Operation: | write | Name: | Expires |
Value: int64_t|0 | |||
| (PID) Process: | (3576) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs\outlook |
| Operation: | delete value | Name: | ConfigIds |
Value: | |||
Executable files
533
Suspicious files
882
Text files
504
Unknown types
177
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3576 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:B0A9EBC58900231AE6E968B1FD35189E | SHA256:9B58C142595FC9EF3F835A26E922D269C4D354A84395CC13B8EC0A6BC2429393 | |||
| 3576 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | der | |
MD5:2E2F6B31BBDE1EA4D6800CB96408F17B | SHA256:9DDA126A92124DD6792842A207E7FD31BC8F1B420E1FAC8E06736AD0E93493BA | |||
| 4748 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF18fc6c.TMP | — | |
MD5:— | SHA256:— | |||
| 4748 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3576 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:E4F02EFA52177909EC0E705B089A5F07 | SHA256:B2C32B6596679A76C9F5D276A9954723D5C3E3D85B60D894865828929F366832 | |||
| 3576 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:928A441F6547156C9631B7A690F20631 | SHA256:B25EC8C608E7353FCE06BF36F7C3D3B0DB6A1916D0B474C34DE49135C39C8DD0 | |||
| 3576 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:7973B6AE8C8910AC1D78D000786A9C64 | SHA256:A8C197085DFE4E76FF170D4E322C7CEDD519A528687AE4BEC0191E5DD15A45EA | |||
| 4748 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18fc8b.TMP | — | |
MD5:— | SHA256:— | |||
| 4748 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18fc8b.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
188
DNS requests
222
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3576 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2064 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3576 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
536 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:eQm-YXND97OXdddZTNVFwm06goBA92z93iOAOyiUhwQ&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8092 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8092 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7416 | svchost.exe | HEAD | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1753781641&P2=404&P3=2&P4=H9054zEnMcYXvCIkJ8ldzYwy4DuYqsg655%2fgqUeKXCqKybG5dNU3tHiUQONgJ9tN2L6545Nl2Hw%2bKQNyYJYGPg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5724 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3576 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3576 | OUTLOOK.EXE | 52.109.28.47:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
3576 | OUTLOOK.EXE | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3576 | OUTLOOK.EXE | 23.48.23.11:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
3576 | OUTLOOK.EXE | 52.111.229.36:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
login.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |