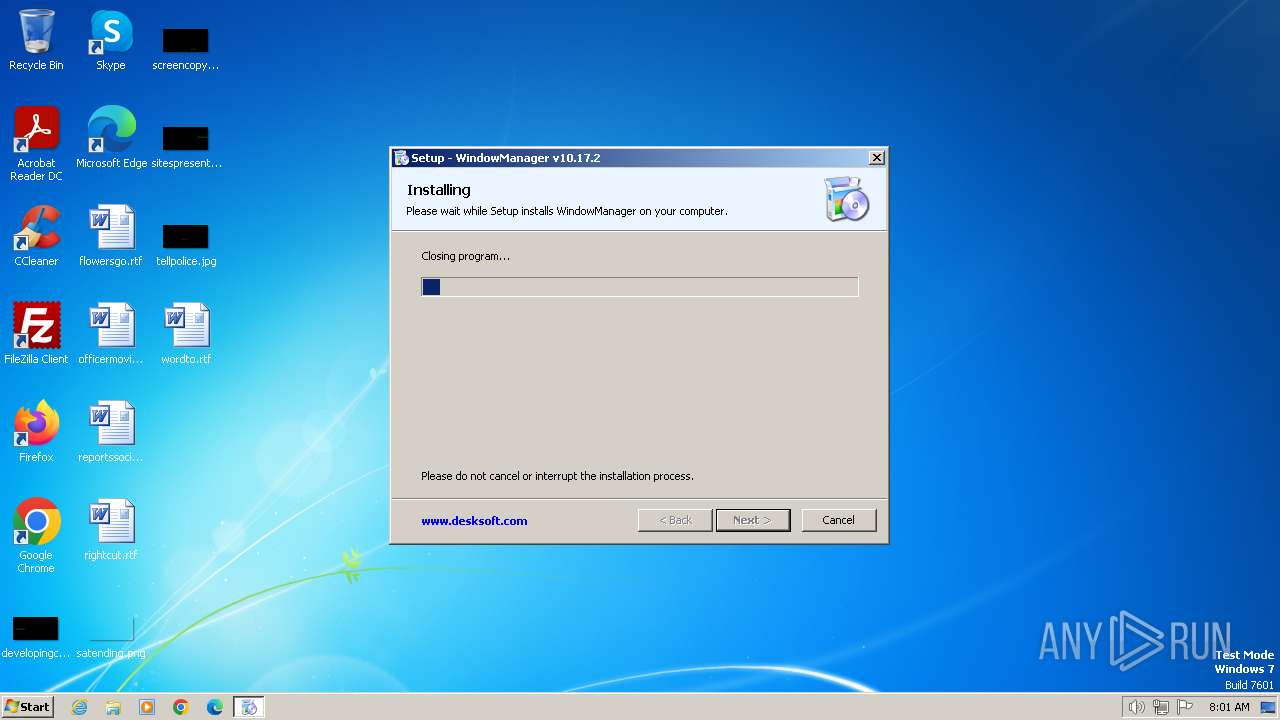
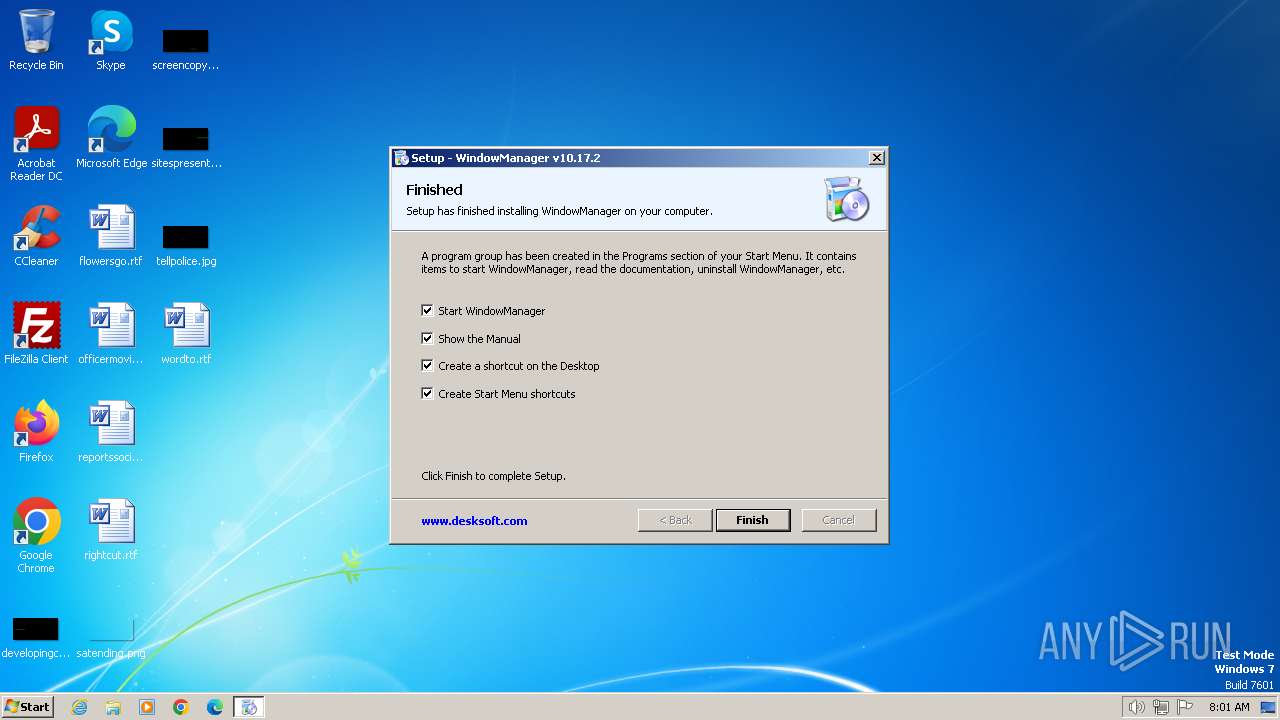
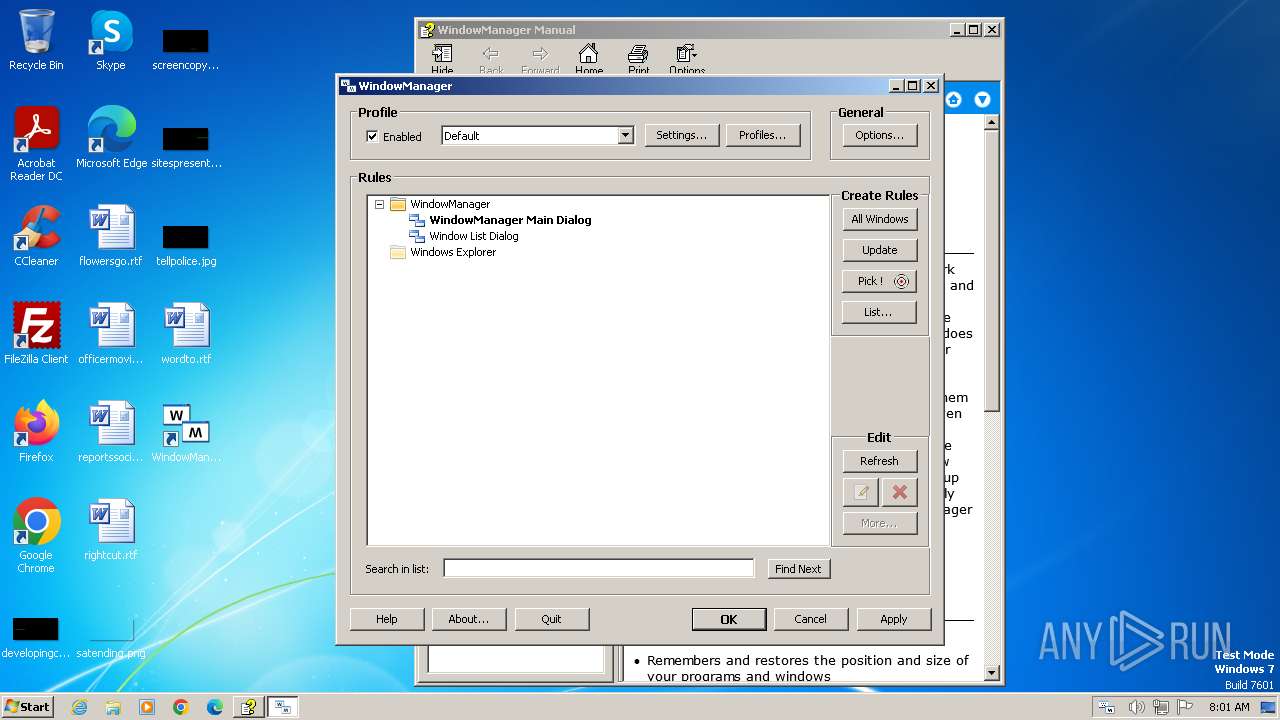
| File name: | WMSetup.exe |
| Full analysis: | https://app.any.run/tasks/960b80de-cfd5-4de8-8a33-f2418a66cca5 |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2024, 07:00:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 32F7AFAC4BC7AADECF65E0C7F14E1DCC |
| SHA1: | 3710B3713142679C8A23D117B289BD14EFBFBD55 |
| SHA256: | 97C0F47C4713562060C16141BA96D1A157C2D4E29BE8E635DDA5EC9092FF98DA |
| SSDEEP: | 49152:oPbcq8efxg8KZzNhpmzPFZ1/Mp01/waF0QEpRWhCcWK5TgVJ3D+zxNCEsZQGfnCr:oPYGJKZJhpmJZpQre0Q6RGfWK1oZ4bF5 |
MALICIOUS
Drops the executable file immediately after the start
- WMSetup.exe (PID: 3344)
SUSPICIOUS
Creates a software uninstall entry
- WMSetup.exe (PID: 3344)
Reads security settings of Internet Explorer
- WMSetup.exe (PID: 3344)
Executable content was dropped or overwritten
- WMSetup.exe (PID: 3344)
Reads the Internet Settings
- WMSetup.exe (PID: 3344)
- hh.exe (PID: 2556)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2556)
Reads Internet Explorer settings
- hh.exe (PID: 2556)
INFO
Creates files in the program directory
- WMSetup.exe (PID: 3344)
- WindowManager.exe (PID: 1028)
- hh.exe (PID: 2556)
- WindowManager.exe (PID: 2904)
Reads the computer name
- WMSetup.exe (PID: 3344)
- WindowManager.exe (PID: 1028)
- WindowManager.exe (PID: 2904)
Checks supported languages
- WMSetup.exe (PID: 3344)
- WindowManager.exe (PID: 1028)
- WindowManager.exe (PID: 2904)
Create files in a temporary directory
- WMSetup.exe (PID: 3344)
- hh.exe (PID: 2556)
Creates files or folders in the user directory
- WindowManager.exe (PID: 1028)
- hh.exe (PID: 2556)
- WindowManager.exe (PID: 2904)
Reads the machine GUID from the registry
- hh.exe (PID: 2556)
- WindowManager.exe (PID: 1028)
Reads security settings of Internet Explorer
- hh.exe (PID: 2556)
Manual execution by a user
- WindowManager.exe (PID: 2904)
- explorer.exe (PID: 1236)
Checks proxy server information
- hh.exe (PID: 2556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:03:30 15:05:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.35 |
| CodeSize: | 150016 |
| InitializedDataSize: | 1105408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe02c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
46
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
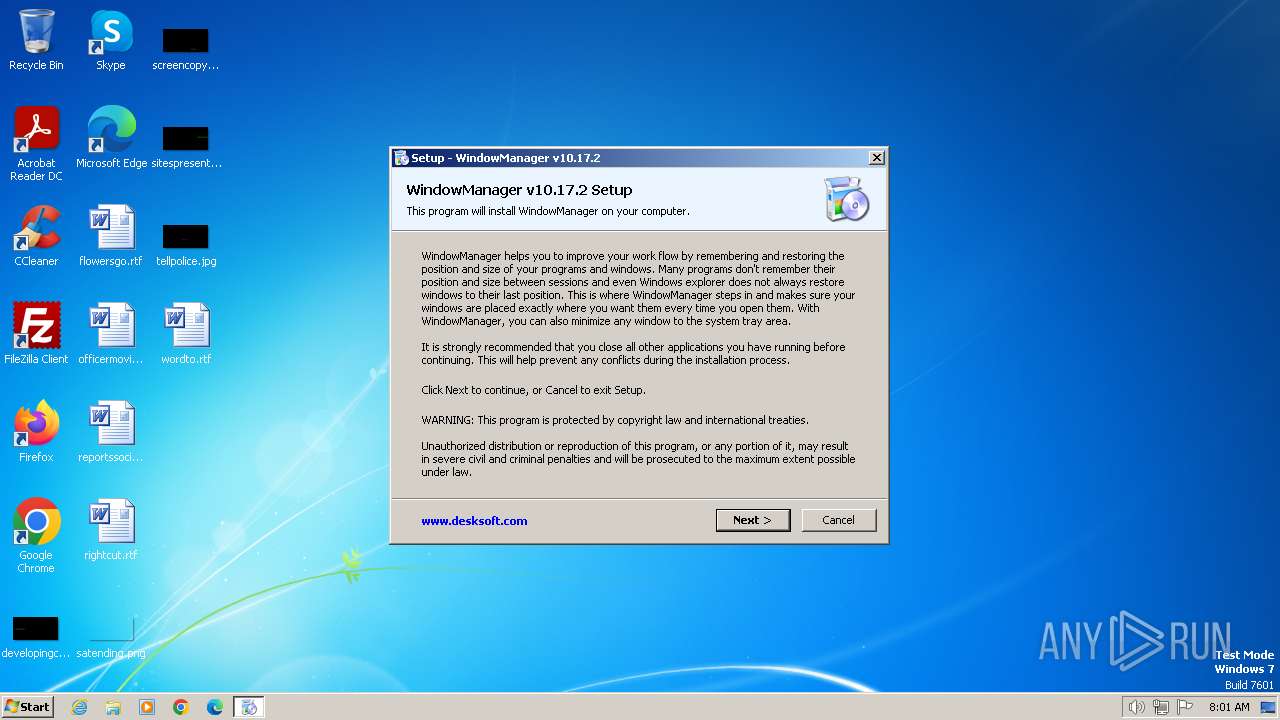
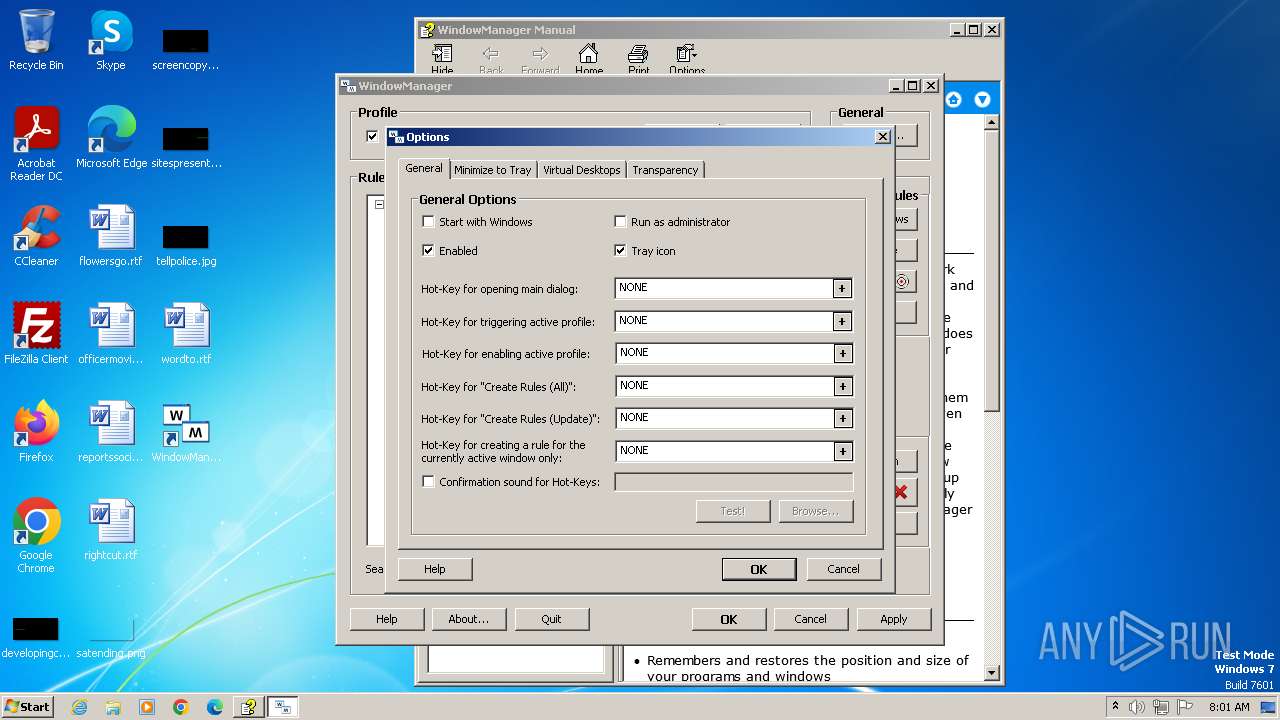
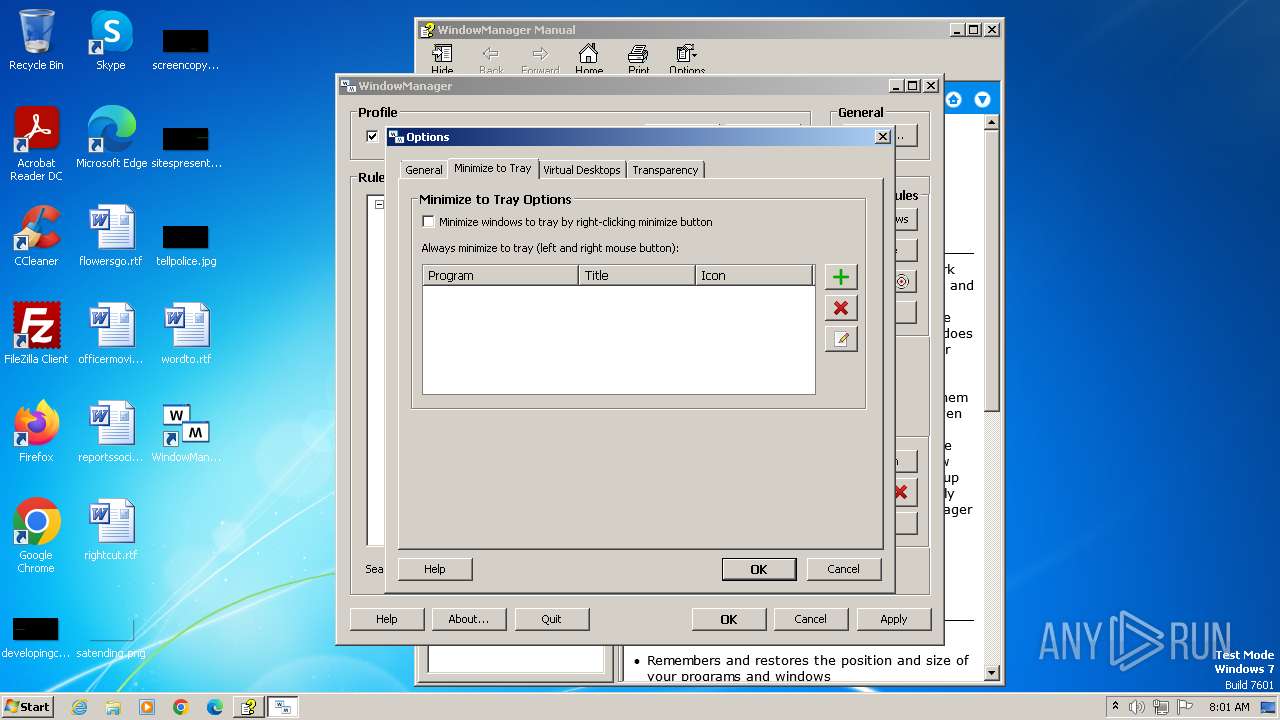
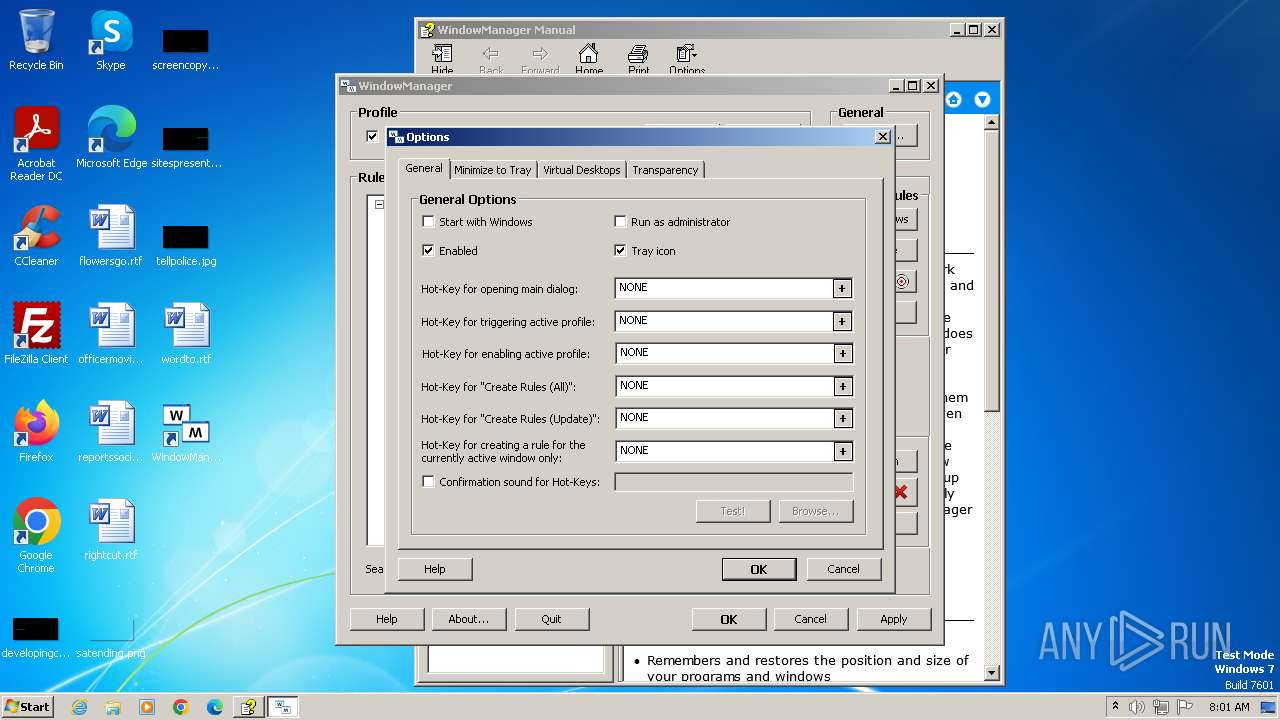
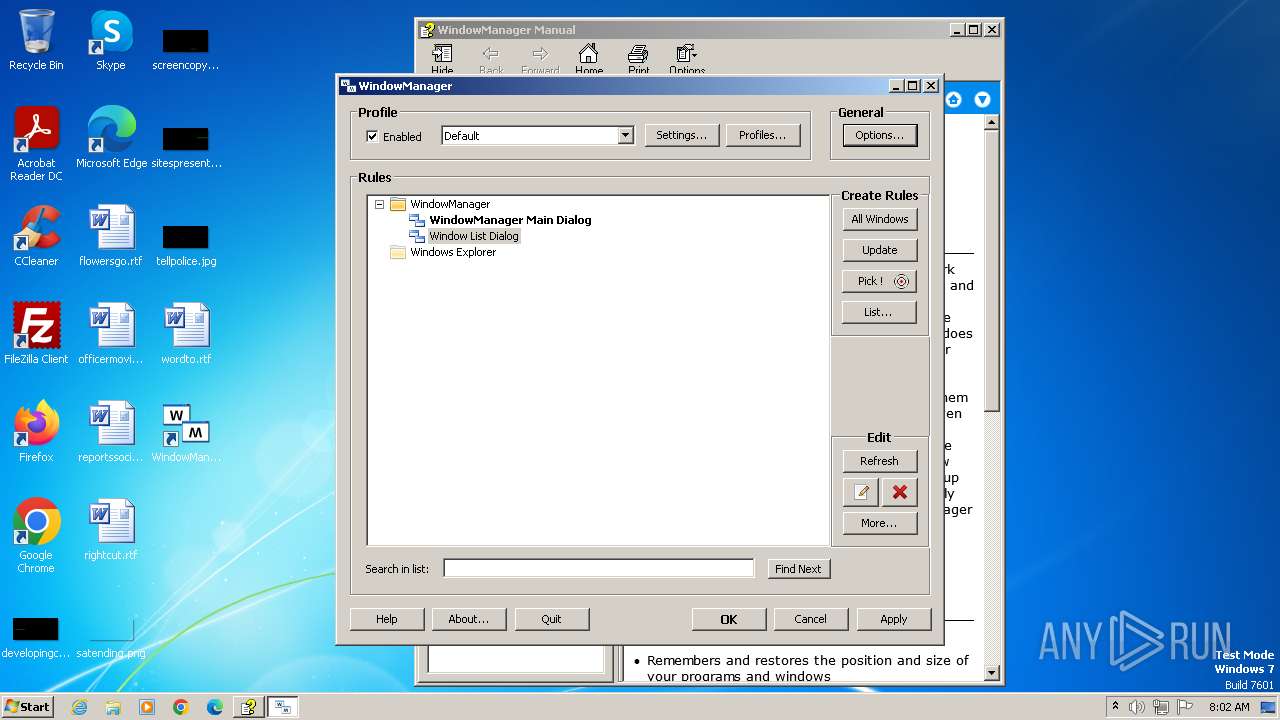
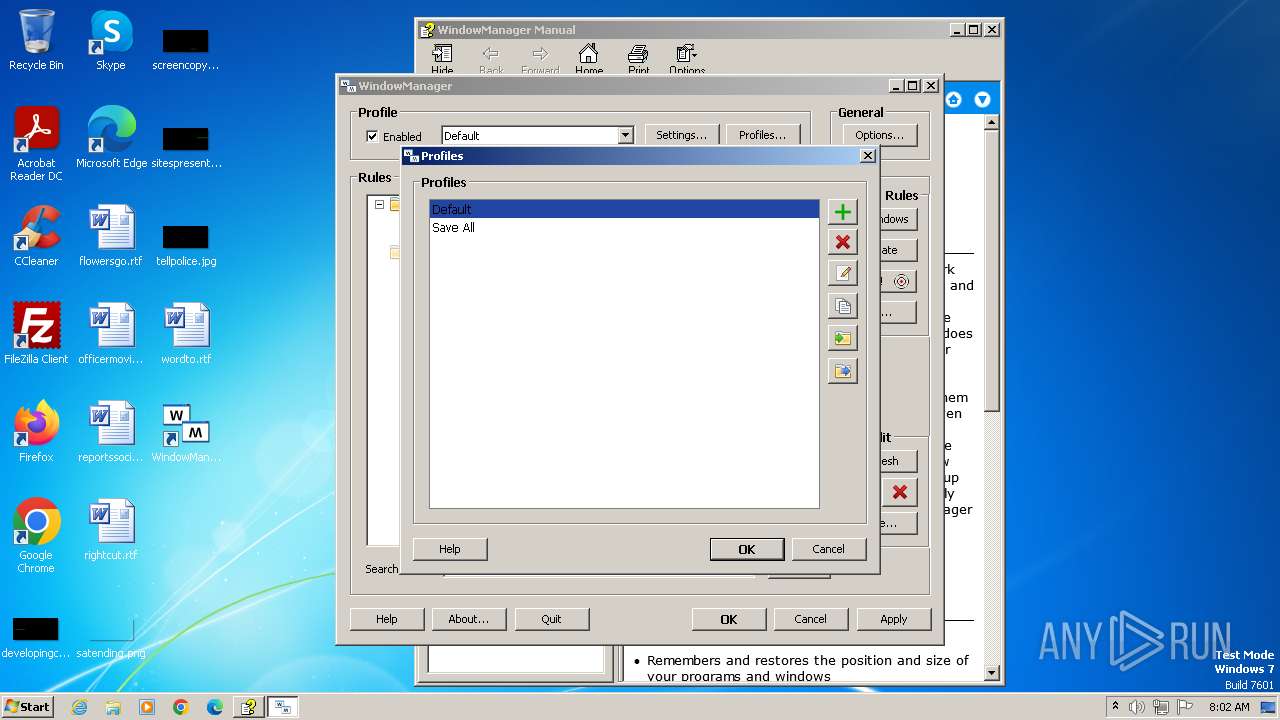
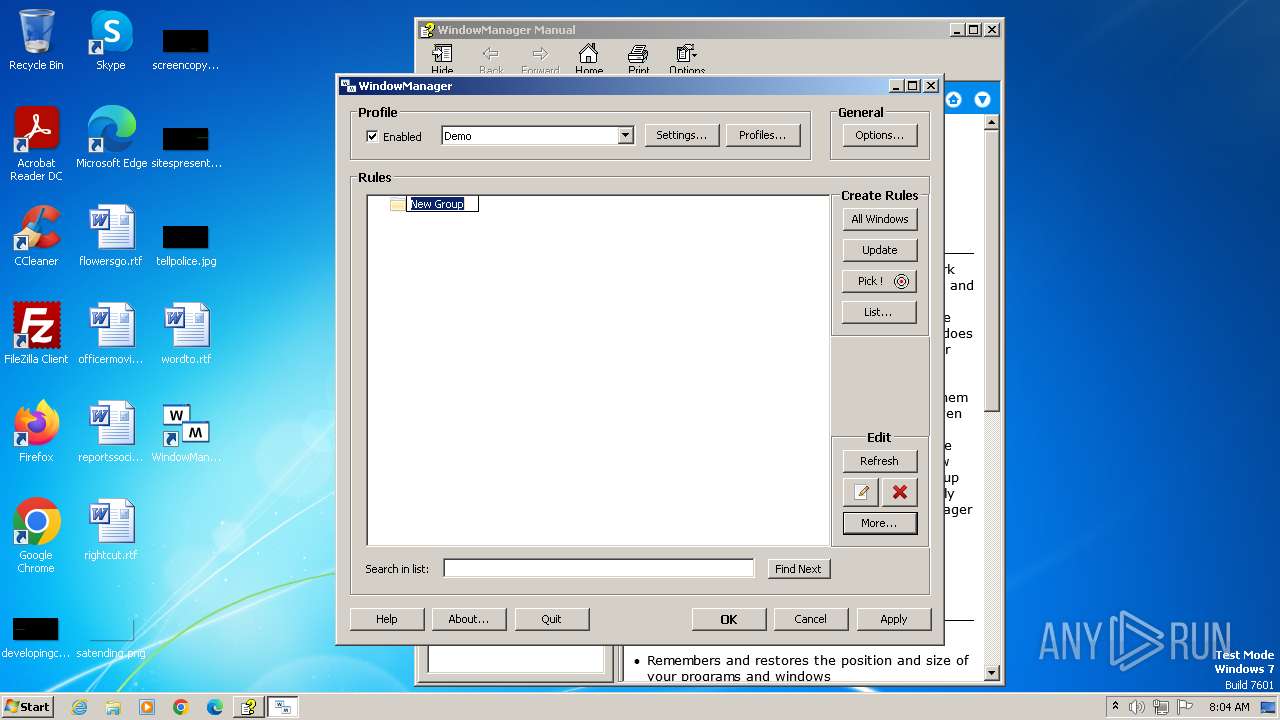
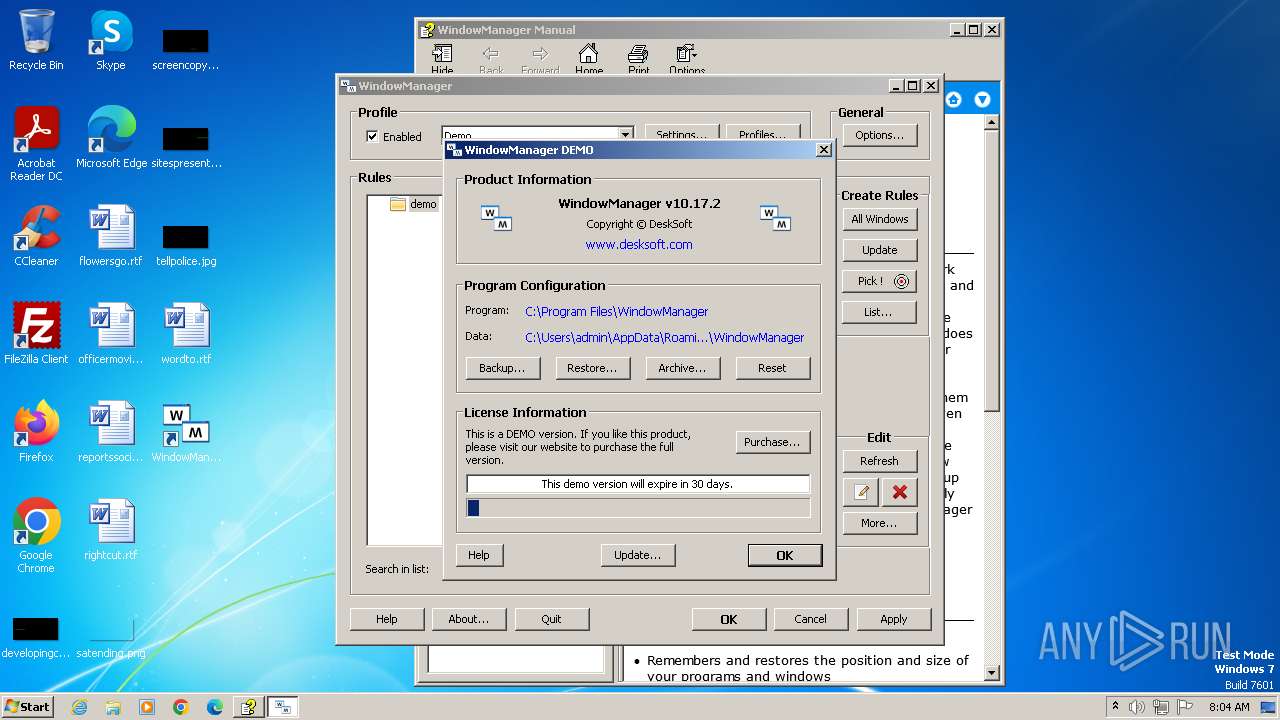
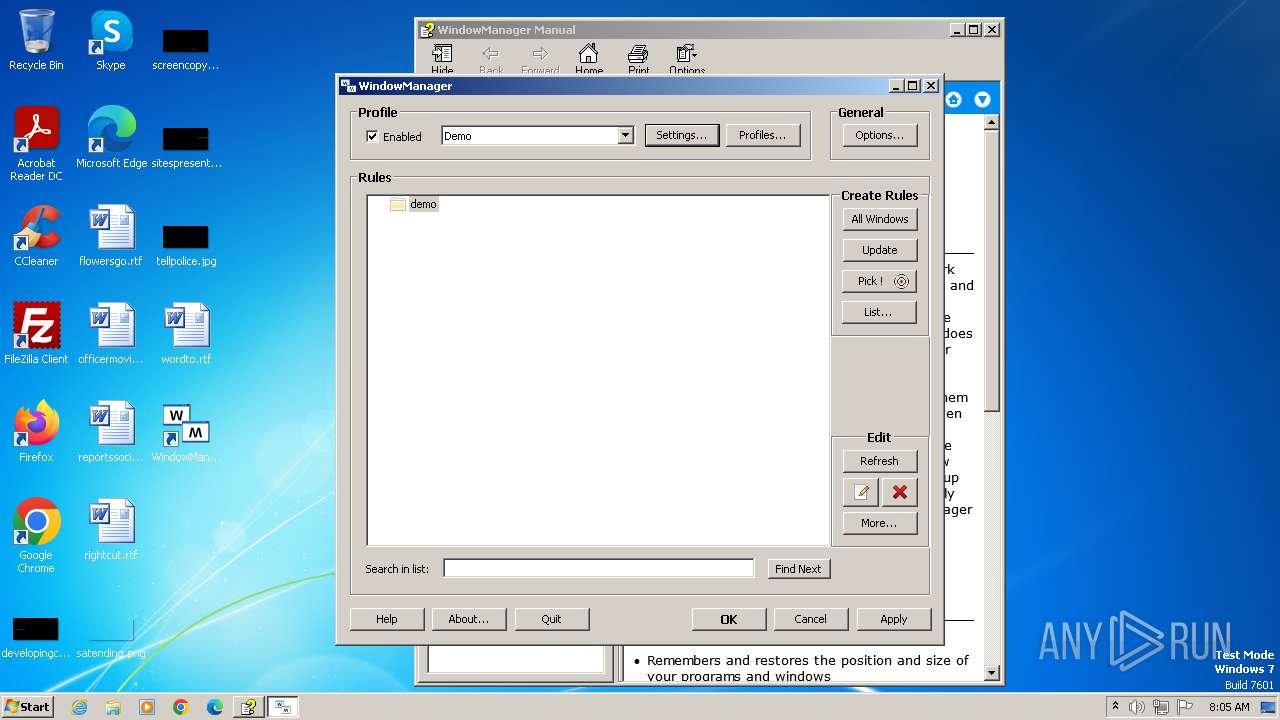
| 1028 | "C:\Program Files\WindowManager\WindowManager.exe" | C:\Program Files\WindowManager\WindowManager.exe | WMSetup.exe | ||||||||||||
User: admin Company: DeskSoft Integrity Level: HIGH Description: WindowManager Application Version: 10.17.2 Modules
| |||||||||||||||
| 1236 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
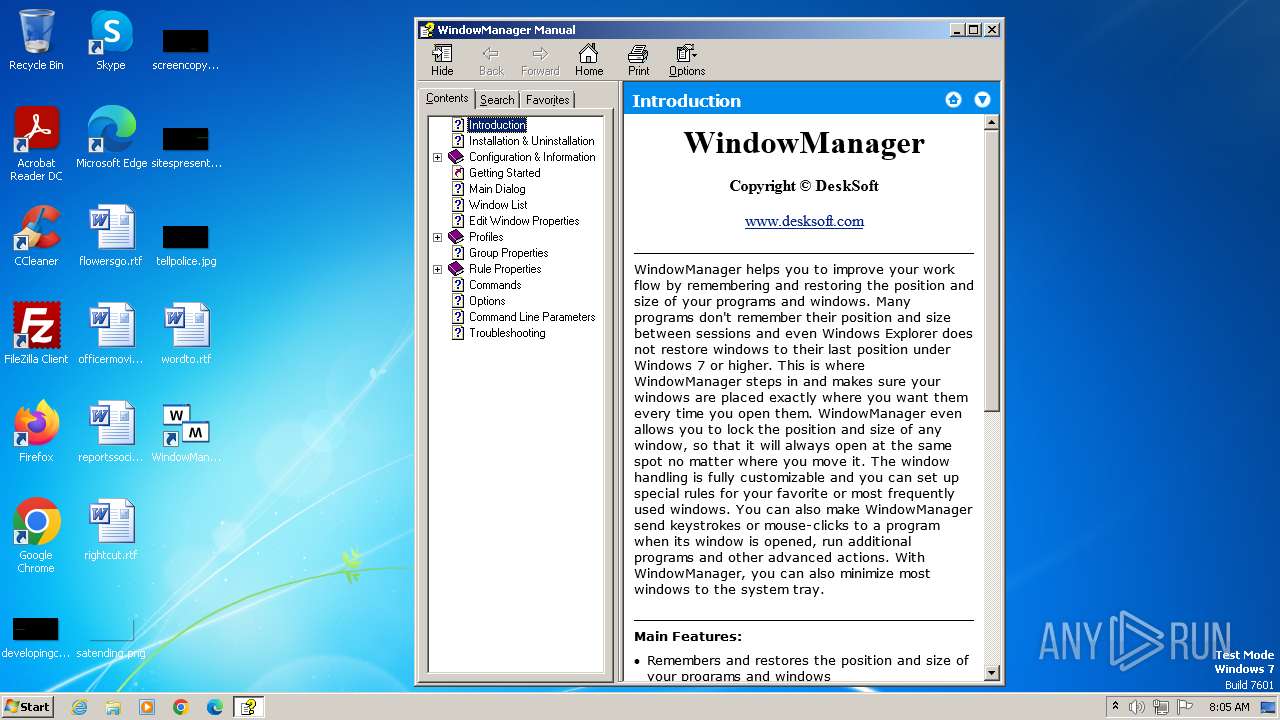
| 2556 | "C:\Windows\hh.exe" C:\Program Files\WindowManager\WindowManager.chm | C:\Windows\hh.exe | — | WMSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2904 | "C:\Program Files\WindowManager\WindowManager.exe" | C:\Program Files\WindowManager\WindowManager.exe | — | explorer.exe | |||||||||||
User: admin Company: DeskSoft Integrity Level: MEDIUM Description: WindowManager Application Exit code: 0 Version: 10.17.2 Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\AppData\Local\Temp\WMSetup.exe" | C:\Users\admin\AppData\Local\Temp\WMSetup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3344 | "C:\Users\admin\AppData\Local\Temp\WMSetup.exe" | C:\Users\admin\AppData\Local\Temp\WMSetup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 219
Read events
4 176
Write events
37
Delete events
6
Modification events
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MHDSYS32 |
| Operation: | write | Name: | 99622DA110 |
Value: | |||
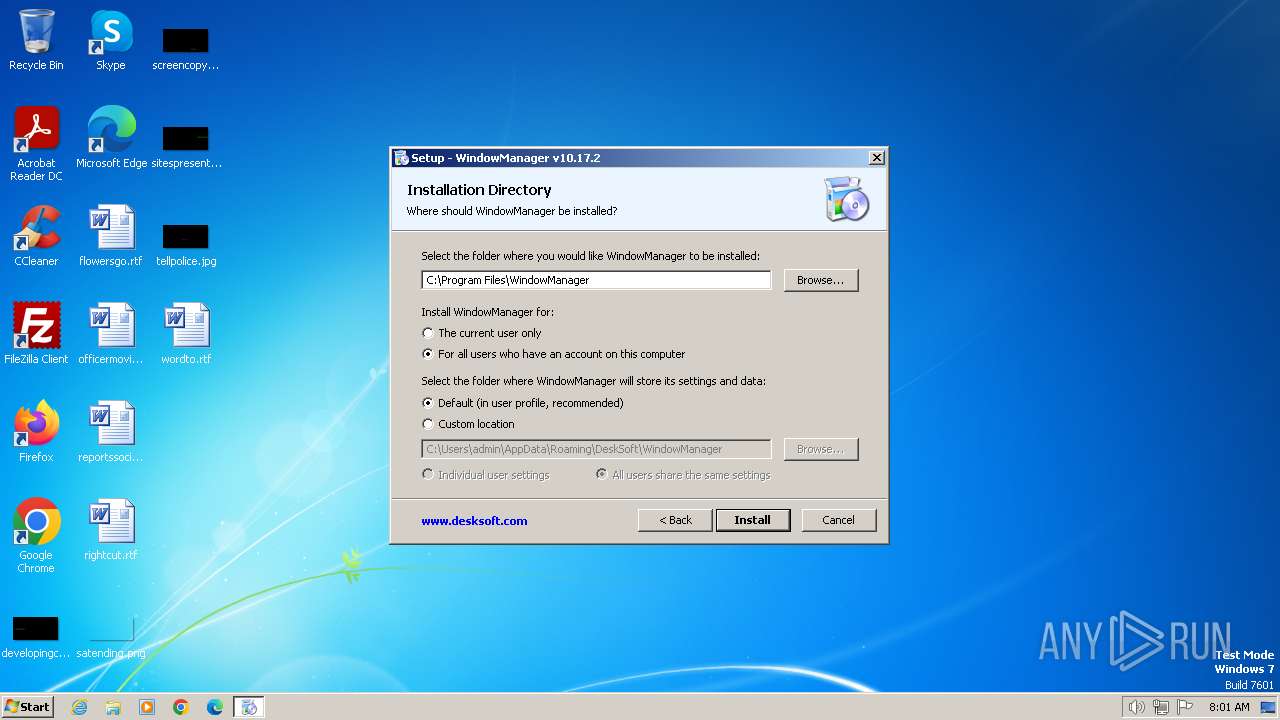
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DeskSoft |
| Operation: | write | Name: | WindowManager |
Value: 0100ECF1725AA12D62990A001100010000000000433A5C50726F6772616D2046696C65735C57696E646F774D616E616765720000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000433A5C55736572735C61646D696E5C417070446174615C526F616D696E675C4465736B536F66745C57696E646F774D616E61676572000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000687474703A2F2F7777772E6465736B736F66742E636F6D2F57696E646F774D616E616765725F50757263686173652E68746D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000687474703A2F2F7777772E6465736B736F66742E636F6D2F5041442F574D5F5645522E545854000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000687474703A2F2F7777772E6465736B736F66742E636F6D2F57696E646F774D616E616765725F446F776E6C6F61642E68746D0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 116 | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | DisplayName |
Value: WindowManager | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\WindowManager\WindowManager.exe,0 | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | DisplayVersion |
Value: 10.17.2 | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | Publisher |
Value: DeskSoft | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | HelpLink |
Value: http://www.desksoft.com | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.desksoft.com | |||
| (PID) Process: | (3344) WMSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\WindowManager |
| Operation: | write | Name: | URLUpdateInfo |
Value: http://www.desksoft.com | |||
Executable files
2
Suspicious files
16
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3344 | WMSetup.exe | C:\Users\admin\AppData\Local\Temp\Temp.lnk | — | |
MD5:— | SHA256:— | |||
| 3344 | WMSetup.exe | C:\Users\Public\Desktop\WindowManager.lnk | — | |
MD5:— | SHA256:— | |||
| 3344 | WMSetup.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\WindowManager\WindowManager Manual.lnk | — | |
MD5:— | SHA256:— | |||
| 1028 | WindowManager.exe | C:\Users\admin\AppData\Roaming\DeskSoft\WindowManager\PinList.dcf_tmp | — | |
MD5:— | SHA256:— | |||
| 1028 | WindowManager.exe | C:\Users\admin\AppData\Roaming\DeskSoft\WindowManager\PinList.dcf | — | |
MD5:— | SHA256:— | |||
| 1028 | WindowManager.exe | C:\Users\admin\AppData\Roaming\DeskSoft\WindowManager\MinList.dcf_tmp | — | |
MD5:— | SHA256:— | |||
| 1028 | WindowManager.exe | C:\Users\admin\AppData\Roaming\DeskSoft\WindowManager\MinList.dcf | — | |
MD5:— | SHA256:— | |||
| 3344 | WMSetup.exe | C:\Program Files\WindowManager\WindowManager.chm | chm | |
MD5:EA79B0E6750A9310CF995CE0CFD8ABE4 | SHA256:4144A894FC45DFF6E7C32717AB6B752032C3A620CE14871F275DAD963721BE37 | |||
| 3344 | WMSetup.exe | C:\Program Files\WindowManager\Uninstall.exe | executable | |
MD5:AA17AF7706986C81CF4E2A43DED340E3 | SHA256:7523A477039225E020321E8CA48B92BD7228F72A85EF1E9BFC39808E1D5D2E43 | |||
| 3344 | WMSetup.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\WindowManager\WindowManager.lnk | lnk | |
MD5:CAFE342A020BFC507A92322C7BE87E30 | SHA256:66B2C0CC18585C6DD7644E1EFA2821097FD2D868706D8D284639DE97627BC63A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1028 | WindowManager.exe | GET | 301 | 188.68.47.244:80 | http://www.desksoft.com/PAD/WM_VER.TXT | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1028 | WindowManager.exe | 188.68.47.244:80 | www.desksoft.com | netcup GmbH | DE | unknown |
1028 | WindowManager.exe | 188.68.47.244:443 | www.desksoft.com | netcup GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.desksoft.com |
| unknown |