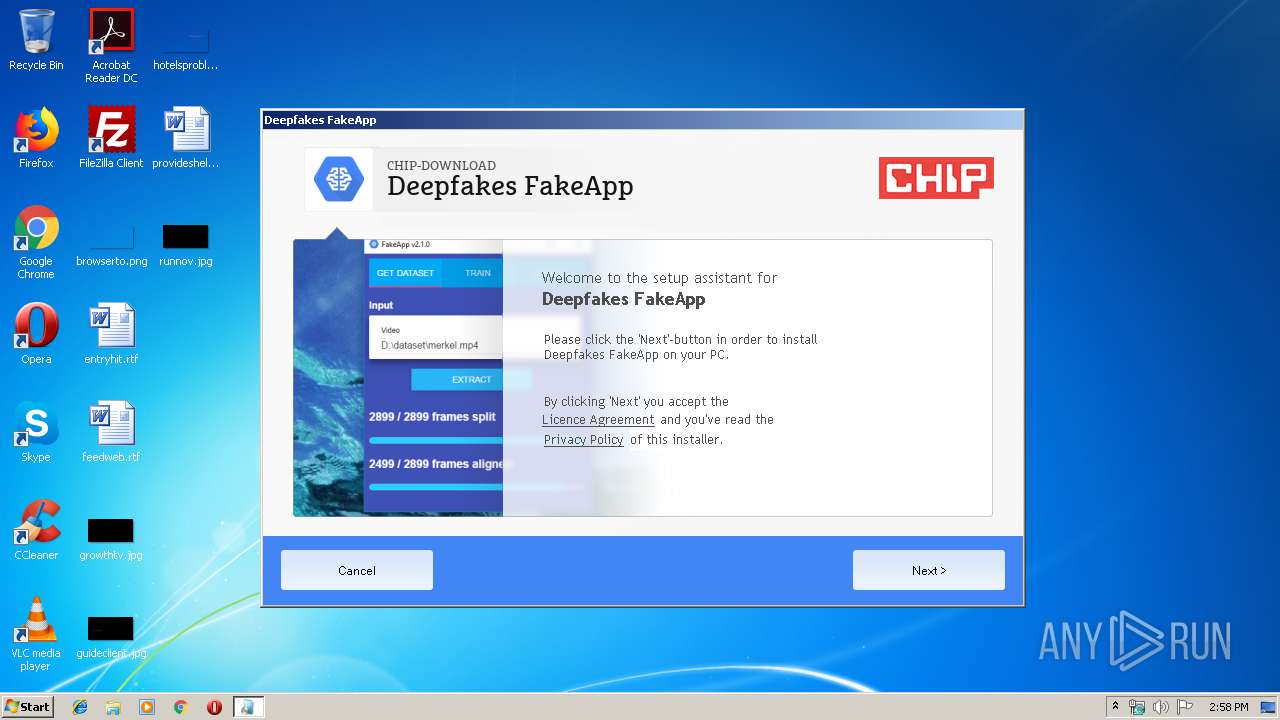
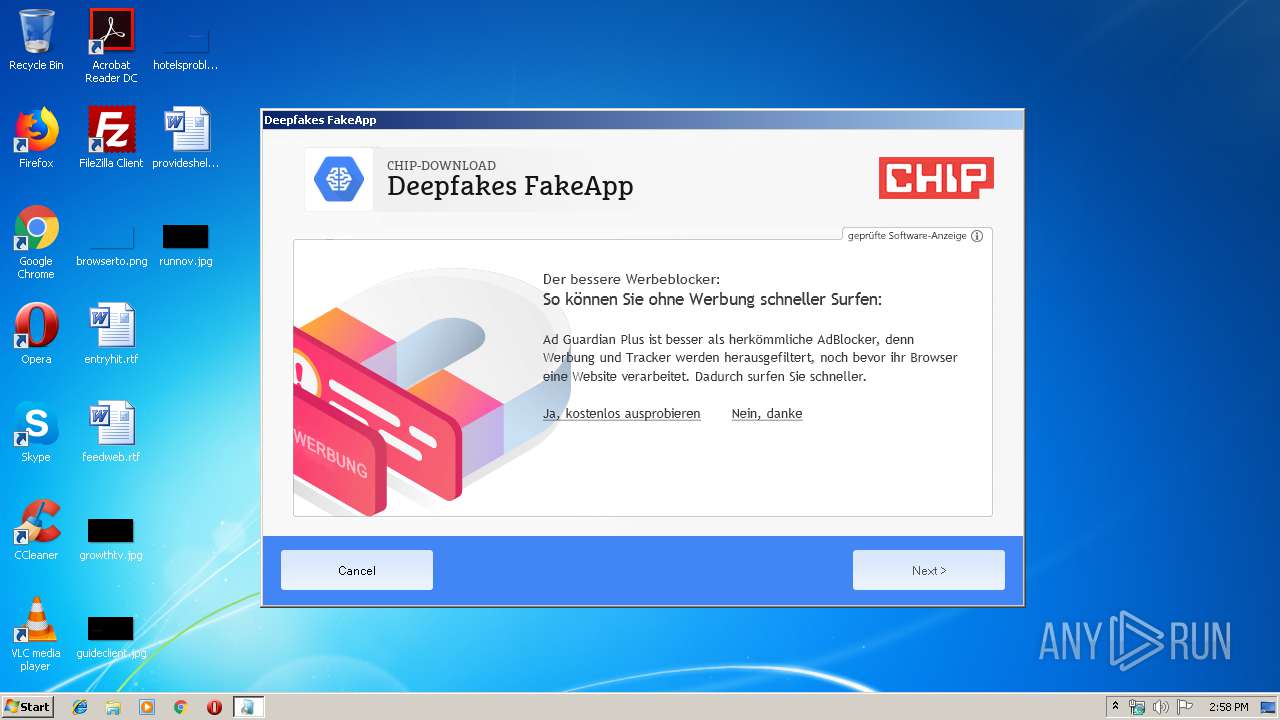
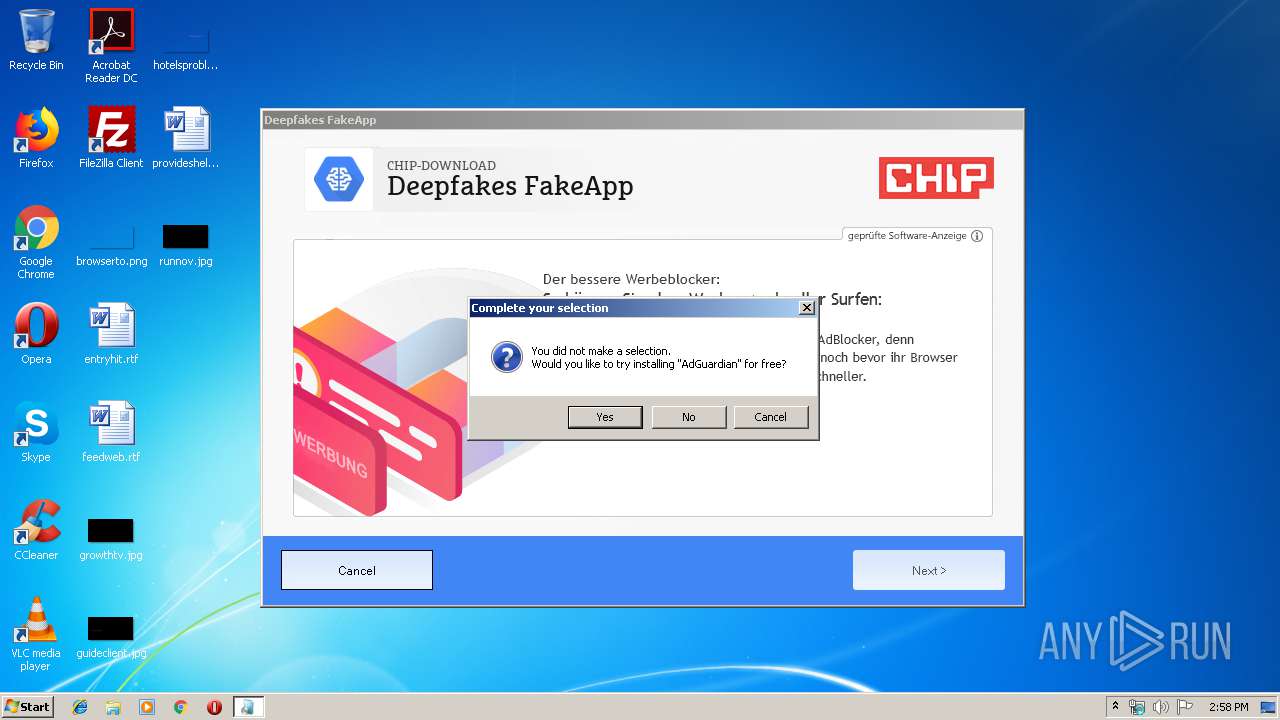
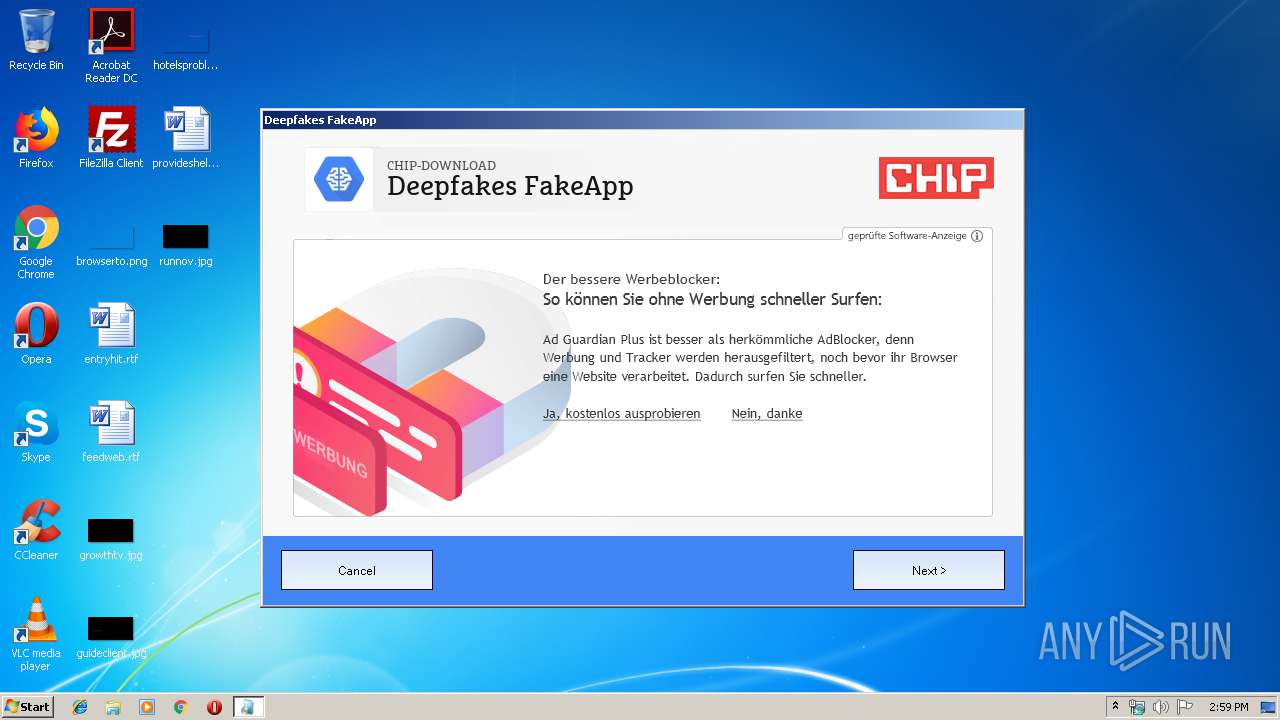
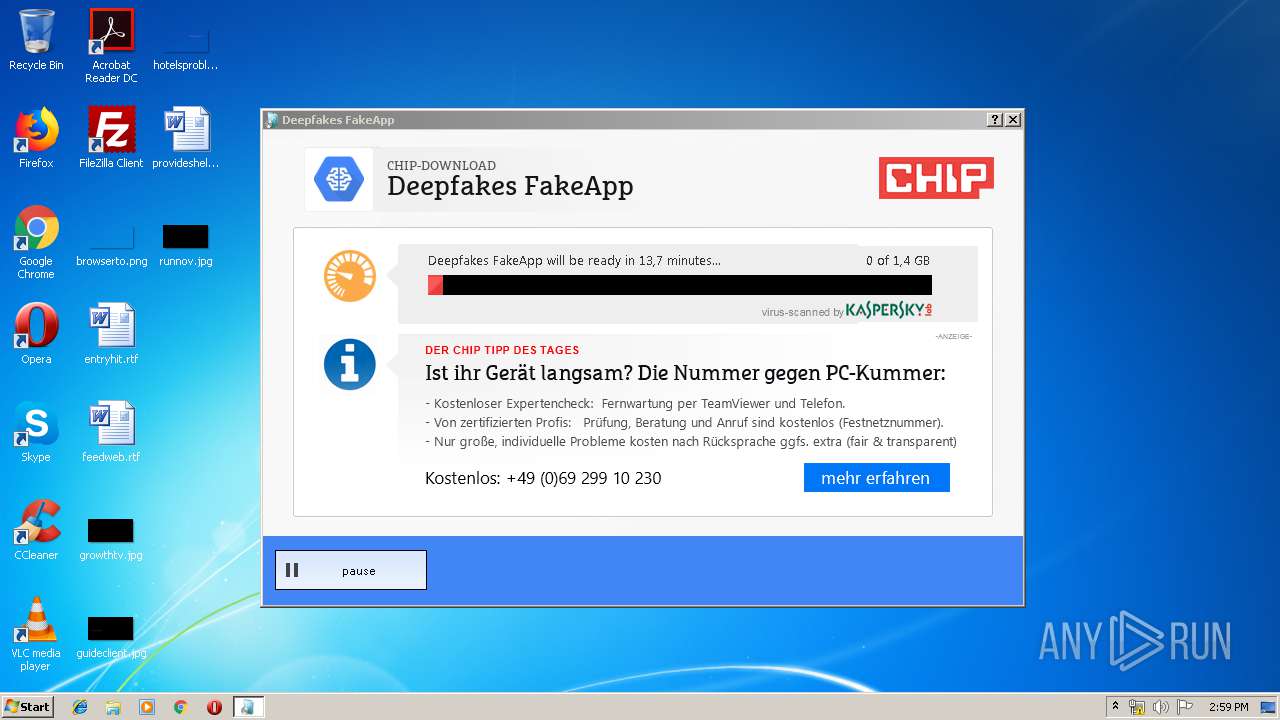
| File name: | Deepfakes FakeApp - CHIP-Installer.exe |
| Full analysis: | https://app.any.run/tasks/85aacb54-a6f3-467a-934b-d3f8696920eb |
| Verdict: | Malicious activity |
| Analysis date: | September 02, 2019, 13:58:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | BE50D9B2E91E6C9B6BE19AEAA5DD83C3 |
| SHA1: | 7A742F89099D56AB5F11342092CA7183F19ECFD4 |
| SHA256: | 97BCC08E4B4CE7C1314F6F7567F173661ACA3A3D9CB1AB21CBFDC601D28D0019 |
| SSDEEP: | 24576:eq5TfcdHj4fmbpO2qSjzPxFnieBrAhfFznMkrV7rAMMB:eUTsamYxKZrAd5rAb |
MALICIOUS
Application was dropped or rewritten from another process
- dmr_72.exe (PID: 3916)
SUSPICIOUS
Executable content was dropped or overwritten
- Deepfakes FakeApp - CHIP-Installer.exe (PID: 2540)
Reads Internet Cache Settings
- dmr_72.exe (PID: 3916)
Reads internet explorer settings
- dmr_72.exe (PID: 3916)
Creates files in the user directory
- dmr_72.exe (PID: 3916)
Searches for installed software
- dmr_72.exe (PID: 3916)
INFO
Reads settings of System Certificates
- dmr_72.exe (PID: 3916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (30.7) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (30.1) |
| .exe | | | Win32 EXE Yoda's Crypter (29.5) |
| .exe | | | Win32 Executable (generic) (5) |
| .exe | | | Generic Win/DOS Executable (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:08:26 13:47:42+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 344064 |
| InitializedDataSize: | 1007616 |
| UninitializedDataSize: | 1536000 |
| EntryPoint: | 0x1cb8d0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.10.0.1 |
| ProductVersionNumber: | 2.10.0.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | German |
| CharacterSet: | Unicode |
| FileVersion: | 2.10.0.1 |
| Comments: | CHIP Secured Installer |
| FileDescription: | CHIP Secured Installer |
| ProductVersion: | 2.10.0.1 |
| LegalCopyright: | Copyright © 2019 Chip Digital GmbH |
| CompanyName: | CHIP Digital GmbH |
| InternalName: | CHIP Secured Installer |
| ProductName: | CHIP Secured Installer |
| OriginalFileName: | CHIP Secured Installer |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Aug-2019 11:47:42 |
| Detected languages: |
|
| FileVersion: | 2.10.0.1 |
| Comments: | CHIP Secured Installer |
| FileDescription: | CHIP Secured Installer |
| ProductVersion: | 2.10.0.1 |
| LegalCopyright: | Copyright © 2019 Chip Digital GmbH |
| CompanyName: | CHIP Digital GmbH |
| InternalName: | CHIP Secured Installer |
| ProductName: | CHIP Secured Installer |
| OriginalFilename: | CHIP Secured Installer |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 26-Aug-2019 11:47:42 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00177000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00178000 | 0x00054000 | 0x00053C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.93599 |
.rsrc | 0x001CC000 | 0x000F6000 | 0x000F5800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.38312 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.32366 | 1444 | Latin 1 / Western European | German - Germany | RT_MANIFEST |
4 | 3.75291 | 9640 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
7 | 3.34702 | 1428 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
8 | 3.2817 | 1674 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
9 | 3.28849 | 1168 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
10 | 3.28373 | 1532 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
11 | 3.26322 | 1628 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
12 | 3.25812 | 1126 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
99 | 2.0815 | 20 | Latin 1 / Western European | English - United Kingdom | RT_GROUP_ICON |
166 | 2.68292 | 80 | Latin 1 / Western European | English - United Kingdom | RT_MENU |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IPHLPAPI.DLL |
KERNEL32.DLL |
MPR.dll |
OLEAUT32.dll |
PSAPI.DLL |
SHELL32.dll |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2540 | "C:\Users\admin\AppData\Local\Temp\Deepfakes FakeApp - CHIP-Installer.exe" | C:\Users\admin\AppData\Local\Temp\Deepfakes FakeApp - CHIP-Installer.exe | explorer.exe | ||||||||||||
User: admin Company: CHIP Digital GmbH Integrity Level: HIGH Description: CHIP Secured Installer Exit code: 0 Version: 2.10.0.1 Modules
| |||||||||||||||
| 2984 | "C:\Users\admin\AppData\Local\Temp\Deepfakes FakeApp - CHIP-Installer.exe" | C:\Users\admin\AppData\Local\Temp\Deepfakes FakeApp - CHIP-Installer.exe | — | explorer.exe | |||||||||||
User: admin Company: CHIP Digital GmbH Integrity Level: MEDIUM Description: CHIP Secured Installer Exit code: 3221226540 Version: 2.10.0.1 Modules
| |||||||||||||||
| 3916 | "C:\Users\admin\AppData\Local\Temp\DMR\dmr_72.exe" -install -133452281 -chipderedesign -b6b3ec095b4244b0805725cfdd14dd0a - -BLUB2 -ukfvwhriwetgepdd -2540 | C:\Users\admin\AppData\Local\Temp\DMR\dmr_72.exe | Deepfakes FakeApp - CHIP-Installer.exe | ||||||||||||
User: admin Company: Chip Digital GmbH Integrity Level: HIGH Description: CHIP Secured Installer Exit code: 0 Version: 2.10.0.1 Modules
| |||||||||||||||
Total events
3 276
Read events
3 233
Write events
42
Delete events
1
Modification events
| (PID) Process: | (2540) Deepfakes FakeApp - CHIP-Installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2540) Deepfakes FakeApp - CHIP-Installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_CURRENT_USER\Software\OCS |
| Operation: | write | Name: | CID |
Value: c0ac5b5d-00ce-4920-b62b-a2203c273e85 | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_CURRENT_USER\Software\OCS |
| Operation: | write | Name: | PID |
Value: chipderedesign | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_CURRENT_USER\Software\OCS |
| Operation: | write | Name: | lastPID |
Value: chipderedesign | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3916) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
1
Suspicious files
0
Text files
15
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\main[1].js | text | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\main[1].css | text | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\MarselisSlabWeb[1].eot | eot | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\jquery[1].js | text | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\progress[1].php | htm | |
MD5:— | SHA256:— | |||
| 2540 | Deepfakes FakeApp - CHIP-Installer.exe | C:\Users\admin\AppData\Local\Temp\DMR\dmr_72.exe | executable | |
MD5:4D3D9F8FB3DB913A559CEB5BD56141C7 | SHA256:3BF6EDCA9052E57FBA87AE8D81FB00CB7CEC0556C1C0F084FBE659D20ECA54B3 | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\bg-icon-speedometer[1].png | image | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\kasper-progresspg-ongrey-en[1].gif | image | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\bg-top[1].gif | image | |
MD5:— | SHA256:— | |||
| 3916 | dmr_72.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\background%20progressad[1].gif | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
13
DNS requests
6
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/img/speedometer_sprites.gif | DE | image | 288 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/track/uac.php?clientid=c0ac5b5d-00ce-4920-b62b-a2203c273e85&cid=133452281&pid=chipderedesign&source=BLUB2&setupid=b6b3ec095b4244b0805725cfdd14dd0a&langcountry=en-US&state=WithoutUAC | DE | binary | 146 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/newbrandmachine/chipderedesign?cid=133452281&scid=&headline1=4465657066616B65732046616B65417070&headline2=434849502D444F574E4C4F4144&euid=323539386566386632626439323036383038353533343436&icon=68747470733A2F2F7777772E636869702E64652F69692F382F322F372F332F392F342F382F302F333134333263386365316262333734332E6A7067&screenshot=68747470733A2F2F7777772E636869702E64652F69692F382F322F372F332F392F342F382F302F333161353661646439353764303564662E6A7067&MetaRating=34&lang=en | DE | binary | 146 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/progress.php?pid=chipderedesign&cid=133452281&sid=b6b3ec095b4244b0805725cfdd14dd0a&appname=4465657066616B65732046616B65417070&uid=c0ac5b5d-00ce-4920-b62b-a2203c273e85&scid=&source=BLUB2&language=en-nl&piddata=&uaexe=6F706572612E657865&Camplist=63346434316239326366383633353664303639386466623737383336343835653B64386635313338383638323336356261393562616434326463323933303838663B61316363303330363632343534346235306161666131633930383766343364643B3131313163623065623138653362623862373635636266366462323765613233 | DE | htm | 2.11 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/jquery.js | DE | text | 91.1 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/main.css?v=1461939270 | DE | text | 6.27 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/main.js?v=12 | DE | text | 8.33 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/img/bg-top.gif | DE | image | 213 b | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/MarselisSlabWeb.eot?&1440165143 | DE | eot | 61.7 Kb | malicious |
3916 | dmr_72.exe | GET | 200 | 148.251.213.132:80 | http://api2.chip-secured-download.de/downloaderContent/img/bg-progressbar.gif | DE | image | 7.94 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | dmr_72.exe | 148.251.213.132:80 | api2.chip-secured-download.de | Hetzner Online GmbH | DE | malicious |
3916 | dmr_72.exe | 5.9.175.19:80 | ocs1.chdi-server.de | Hetzner Online GmbH | DE | malicious |
3916 | dmr_72.exe | 5.9.175.19:443 | ocs1.chdi-server.de | Hetzner Online GmbH | DE | malicious |
3916 | dmr_72.exe | 5.9.198.84:80 | static.chip-secured-download.de | Hetzner Online GmbH | DE | suspicious |
3916 | dmr_72.exe | 172.217.22.6:443 | ad.doubleclick.net | Google Inc. | US | whitelisted |
3916 | dmr_72.exe | 2.16.186.130:443 | downloaderapi.chip.de | Akamai International B.V. | — | whitelisted |
3916 | dmr_72.exe | 2.16.186.130:80 | downloaderapi.chip.de | Akamai International B.V. | — | whitelisted |
3916 | dmr_72.exe | 2.16.186.16:80 | dl.cdn.chip.de | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api2.chip-secured-download.de |
| unknown |
ocs1.chdi-server.de |
| unknown |
static.chip-secured-download.de |
| suspicious |
ad.doubleclick.net |
| whitelisted |
downloaderapi.chip.de |
| whitelisted |
dl.cdn.chip.de |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3916 | dmr_72.exe | A Network Trojan was detected | MALWARE [PTsecurity] DownloadSponsor inbound artifact m1 |
3916 | dmr_72.exe | A Network Trojan was detected | MALWARE [PTsecurity] DownloadSponsor inbound artifact m1 |
3916 | dmr_72.exe | A Network Trojan was detected | MALWARE [PTsecurity] DownloadSponsor img_welcome PNG artifact |
3916 | dmr_72.exe | A Network Trojan was detected | MALWARE [PTsecurity] DownloadSponsor inbound artifact m1 |
1 ETPRO signatures available at the full report