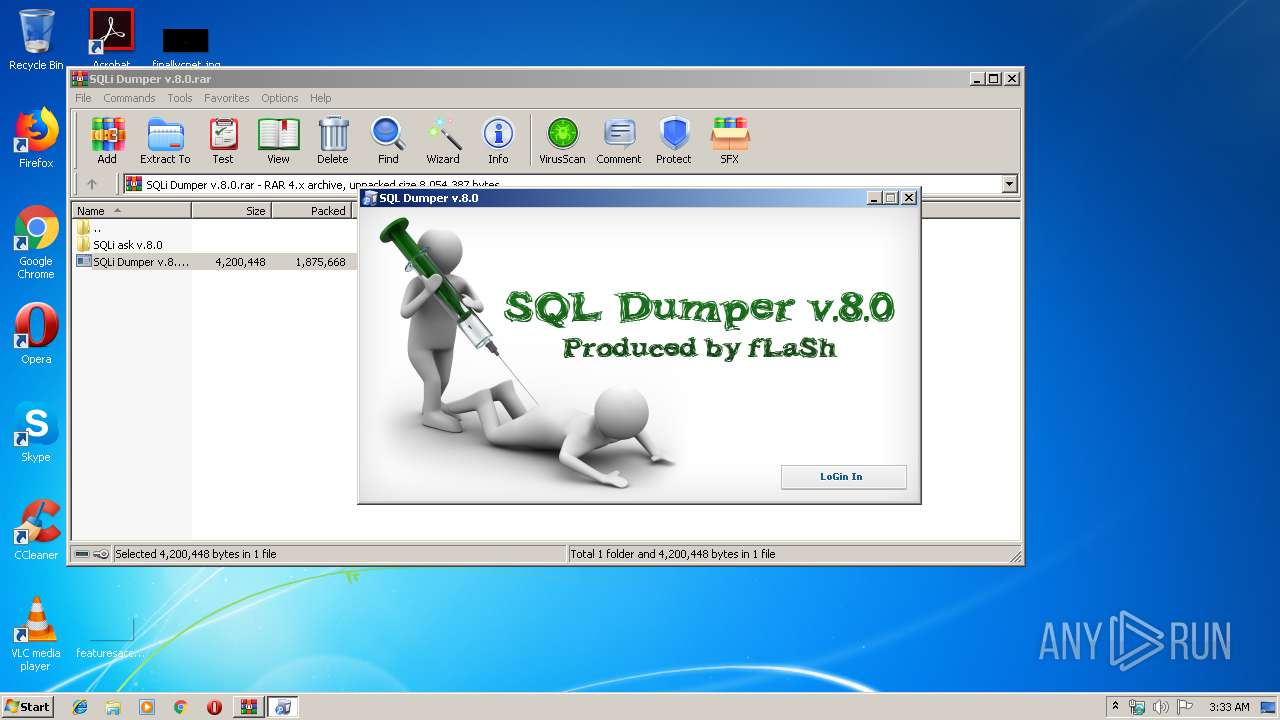
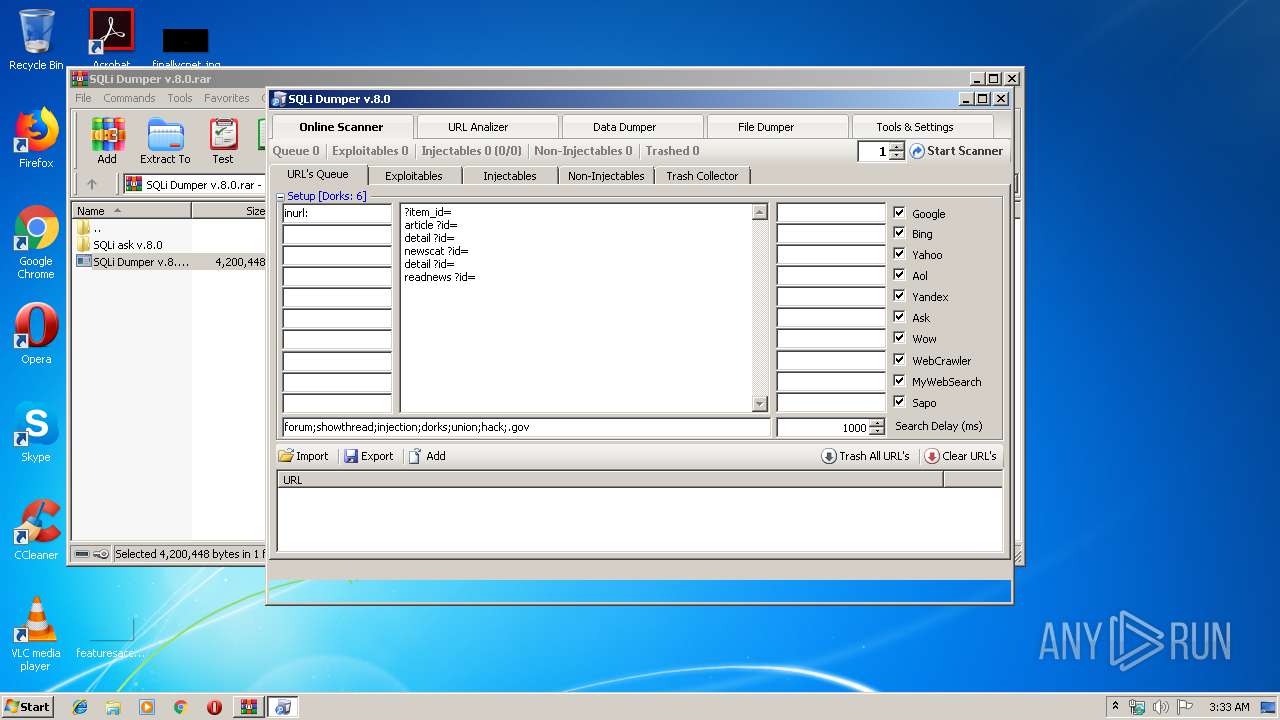
| File name: | SQLi Dumper v.8.0.rar |
| Full analysis: | https://app.any.run/tasks/c6e243e0-8dab-491d-b297-4ca8298f0bdd |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 02:32:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | A248BED1A043BE09D6A39C2429DEEDD4 |
| SHA1: | 41F83A7D85D1BDC1E5A42B9F50D6D1D309D86CD1 |
| SHA256: | 97A35FE7953EC05C1AE408F6F3CE19286987D9887FFCE114A8E33AEB82471ED6 |
| SSDEEP: | 98304:/uYeOJic6BUfmfZaRqv1Eod8+N6jqnrmjyJH7vIdYWSJG:/uJK6BQmagEP+NmWXxs |
MALICIOUS
Application was dropped or rewritten from another process
- SQLi Dumper v.8.0.exe (PID: 1628)
- SQLi Dumper v.8.0.exe (PID: 3156)
- SQLi ask v.8.0.exe (PID: 3804)
Changes the autorun value in the registry
- SQLi Dumper v.8.0.exe (PID: 3156)
Changes settings of System certificates
- SQLi ask v.8.0.exe (PID: 3804)
SUSPICIOUS
Executable content was dropped or overwritten
- SQLi Dumper v.8.0.exe (PID: 3156)
- WinRAR.exe (PID: 3024)
Reads internet explorer settings
- SQLi ask v.8.0.exe (PID: 3804)
Creates files in the program directory
- SQLi Dumper v.8.0.exe (PID: 3156)
Adds / modifies Windows certificates
- SQLi ask v.8.0.exe (PID: 3804)
INFO
Reads settings of System Certificates
- SQLi ask v.8.0.exe (PID: 3804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1875715 |
|---|---|
| UncompressedSize: | 4200448 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2015:04:18 00:08:19 |
| PackingMethod: | Normal |
| ArchivedFileName: | SQLi Dumper v.8.0.exe |
Total processes
38
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1628 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi Dumper v.8.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi Dumper v.8.0.exe | — | WinRAR.exe | |||||||||||
User: admin Company: SQLi Dumper v.8.0 Integrity Level: MEDIUM Description: SQLi Dumper v.8.0 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3024 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SQLi Dumper v.8.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3156 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi Dumper v.8.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi Dumper v.8.0.exe | WinRAR.exe | ||||||||||||
User: admin Company: SQLi Dumper v.8.0 Integrity Level: HIGH Description: SQLi Dumper v.8.0 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3804 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\SQLi ask v.8.0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\SQLi ask v.8.0.exe | SQLi Dumper v.8.0.exe | ||||||||||||
User: admin Company: c4rl0s@jabber.ru Integrity Level: HIGH Description: SQLi Dumper Exit code: 0 Version: 7.0.0.0 Modules
| |||||||||||||||
Total events
966
Read events
918
Write events
48
Delete events
0
Modification events
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SQLi Dumper v.8.0.rar | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
2
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi Dumper v.8.0.exe | executable | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\Settings | xml | |
MD5:— | SHA256:— | |||
| 3156 | SQLi Dumper v.8.0.exe | C:\Program Files\Google\Chrome\Application\Ask Toolbar Chrome.exe | executable | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\Settings.xml | xml | |
MD5:— | SHA256:— | |||
| 3156 | SQLi Dumper v.8.0.exe | C:\Program Files\Mozilla Firefox\Ask Toolbar Firefox.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3156 | SQLi Dumper v.8.0.exe | C:\Program Files\Google\Chrome\Application\Ask Toolbar Chrome.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\ErrLog.txt | text | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\DIC\dic_file_dump.txt | text | |
MD5:351CACFFC2884FCD4E69BB1FB04DDEB5 | SHA256:C67BCC0B4ED5E5EF72AA1134C0838D9201A97C2BF462FDFF0AC9052A53B286A2 | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\DIC\dic_admin.txt | text | |
MD5:A0E54634DDD435DF5B82E20EA20C7EFE | SHA256:963E3A1E46D5F4C35B85464DB61B7C346C5C44669E64A5C016192DDE078F997A | |||
| 3024 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3024.8675\SQLi ask v.8.0\SQLi ask v.8.0.exe | executable | |
MD5:BE1088E8AAE934834BE0CA831E609055 | SHA256:6BDDCA0DE3CC4C39EBF9411A020D7A465915707DDF63A45161CF57537D414C52 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
109
TCP/UDP connections
60
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3804 | SQLi ask v.8.0.exe | GET | 200 | 213.13.145.10:80 | http://pesquisa.sapo.pt/?q=%3fitem_id%3d | PT | xml | 17.8 Kb | malicious |
3804 | SQLi ask v.8.0.exe | GET | 504 | 52.17.173.115:80 | http://www.webcrawler.com/search/web?q=%3fitem_id%3d | IE | — | — | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | — | 212.82.100.137:80 | http://www.wow.com/search?q=%3fitem_id%3d | CH | — | — | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | — | 151.101.2.114:80 | http://www.ask.com/web?q=%3fitem_id%3d | US | — | — | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=%3fitem_id%3d&count=50 | US | html | 110 Kb | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | 302 | 213.180.204.62:80 | http://www.yandex.com/yandsearch?text=article+%3fid%3d | RU | html | 111 Kb | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | 200 | 213.180.204.62:80 | http://www.yandex.com/yandsearch?text=%3fitem_id%3d | RU | html | 111 Kb | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=%3fitem_id%3d&first=50&count=50 | US | html | 110 Kb | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | 302 | 2.18.232.251:80 | http://search.mywebsearch.com/mywebsearch/GGmain.jhtml?searchfor=%3fitem_id%3d | unknown | html | 550 b | whitelisted |
3804 | SQLi ask v.8.0.exe | GET | 200 | 213.180.204.62:80 | http://www.yandex.com/showcaptcha?cc=1&retpath=http%3A//www.yandex.com/yandsearch%3Ftext%3Darticle%2B%253fid%253d_bafab230d87f794ce18359f6665d2099&t=0/1555295622/fa08dbcebc25147c4138abb5512556de&s=51d07f4fe65eaf24a8ae155a388466d6 | RU | html | 14.6 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3804 | SQLi ask v.8.0.exe | 212.82.100.137:80 | www.wow.com | Yahoo! UK Services Limited | CH | shared |
3804 | SQLi ask v.8.0.exe | 52.17.173.115:80 | www.webcrawler.com | Amazon.com, Inc. | IE | unknown |
3804 | SQLi ask v.8.0.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3804 | SQLi ask v.8.0.exe | 151.101.2.114:443 | www.ask.com | Fastly | US | suspicious |
3804 | SQLi ask v.8.0.exe | 213.13.145.10:80 | pesquisa.sapo.pt | Servicos De Comunicacoes E Multimedia S.A. | PT | malicious |
3804 | SQLi ask v.8.0.exe | 151.101.2.114:80 | www.ask.com | Fastly | US | suspicious |
3804 | SQLi ask v.8.0.exe | 2.18.232.251:80 | search.mywebsearch.com | Akamai International B.V. | — | whitelisted |
— | — | 212.82.100.137:80 | www.wow.com | Yahoo! UK Services Limited | CH | shared |
3804 | SQLi ask v.8.0.exe | 213.180.204.62:80 | www.yandex.com | YANDEX LLC | RU | whitelisted |
3804 | SQLi ask v.8.0.exe | 216.58.205.228:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
search.mywebsearch.com |
| whitelisted |
www.google.com |
| malicious |
www.yandex.com |
| whitelisted |
www.wow.com |
| whitelisted |
pesquisa.sapo.pt |
| malicious |
search.aol.com |
| whitelisted |
www.webcrawler.com |
| whitelisted |
www.ask.com |
| whitelisted |
search.yahoo.com |
| whitelisted |