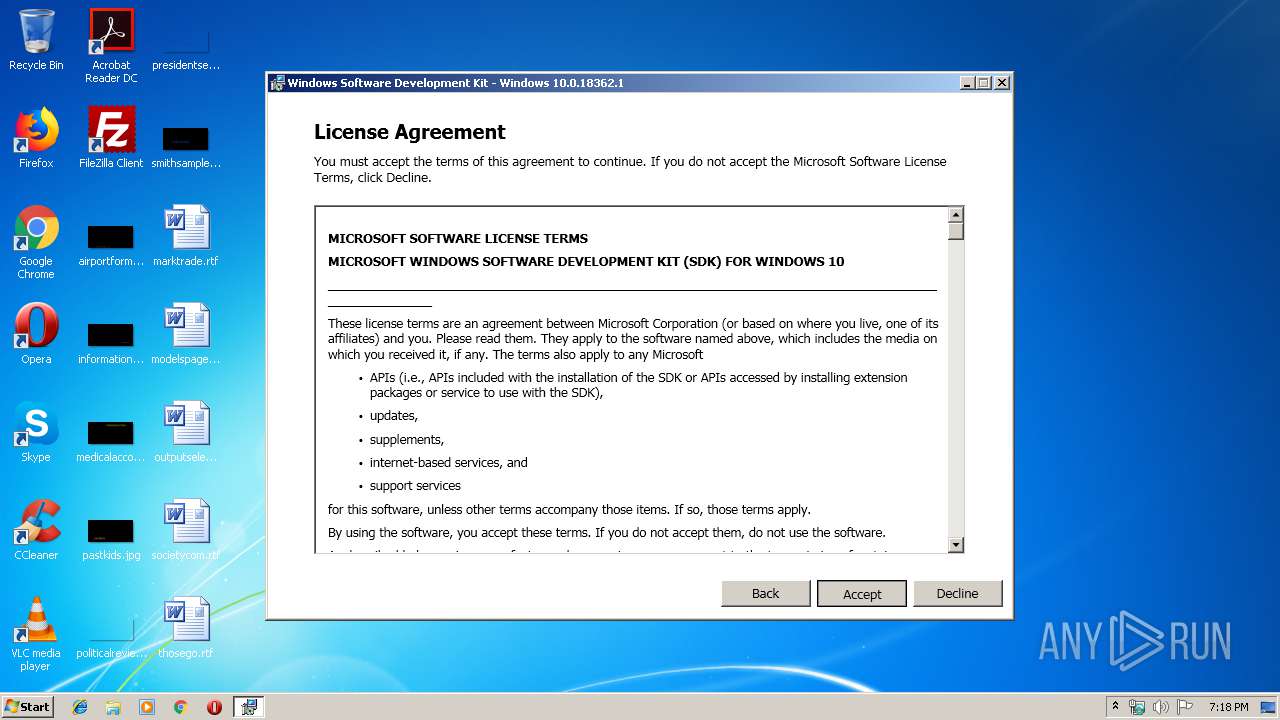
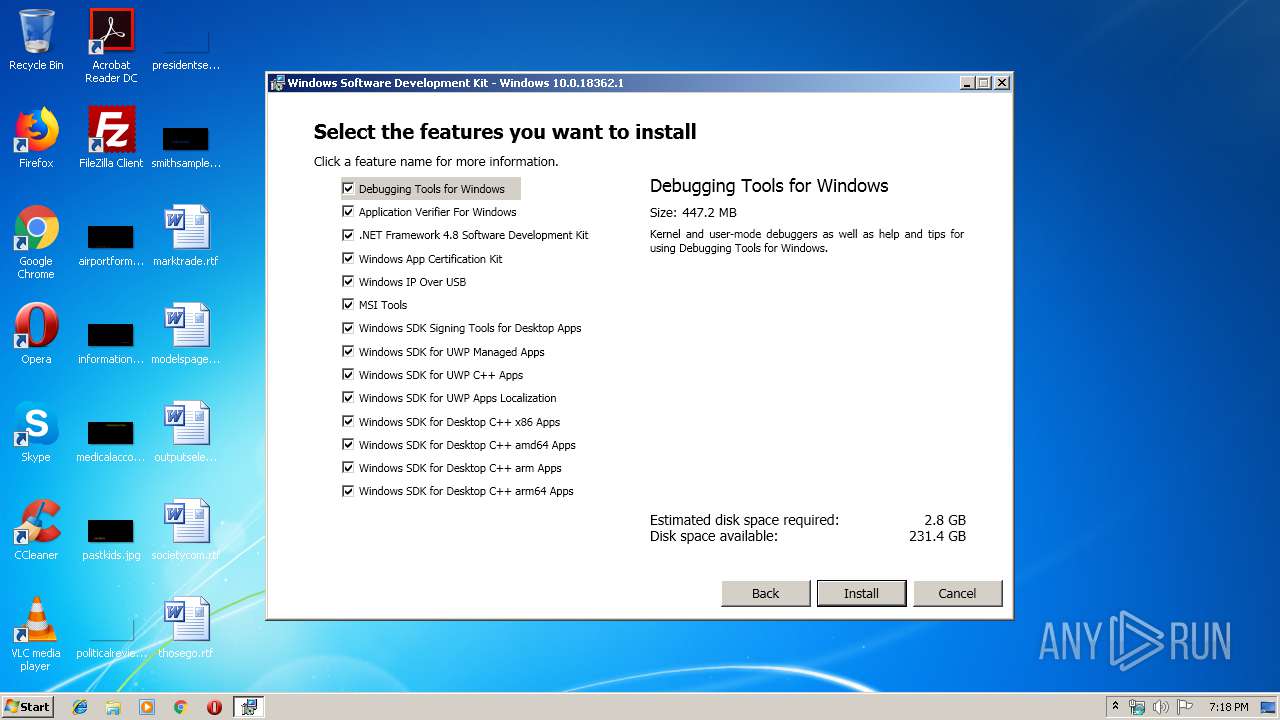
| File name: | fuck_spheres.exe |
| Full analysis: | https://app.any.run/tasks/e5ab6600-6459-487a-9b56-a582f5fd045b |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 18:18:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | EB08CF518184DEB024CADC8097B80026 |
| SHA1: | E28524C60A4D17CEE7A95759F01E768F414DB8EE |
| SHA256: | 978FCAEF114B868A1FD879E1B0135ABF7CB5CF6AC203BCA205F798256E536EC6 |
| SSDEEP: | 98304:wSmAvJGSqp7Ju1G64ESktXr/ZLeL7X70hz+iCD9mPpMG+B4N4kK4dRnF5rQZFJwe:wVAxGllUBFXr/kn7gz+txmbukF5rOFOe |
MALICIOUS
Application was dropped or rewritten from another process
- winsdksetup.exe (PID: 2972)
- winsdksetup.exe (PID: 552)
- crypto.exe (PID: 2844)
- hdd.exe (PID: 1696)
- crypto.exe (PID: 2520)
- winsdksetup.exe (PID: 3052)
Loads dropped or rewritten executable
- winsdksetup.exe (PID: 552)
- crypto.exe (PID: 2520)
Changes settings of System certificates
- winsdksetup.exe (PID: 552)
Changes the autorun value in the registry
- winsdksetup.exe (PID: 3052)
Actions looks like stealing of personal data
- crypto.exe (PID: 2520)
SUSPICIOUS
Creates files in the Windows directory
- winsdksetup.exe (PID: 2972)
- winsdksetup.exe (PID: 552)
Executable content was dropped or overwritten
- winsdksetup.exe (PID: 2972)
- fuck_spheres.exe (PID: 3364)
- winsdksetup.exe (PID: 552)
- crypto.exe (PID: 2844)
- winsdksetup.exe (PID: 3052)
Creates files in the program directory
- winsdksetup.exe (PID: 552)
- winsdksetup.exe (PID: 3052)
Application launched itself
- crypto.exe (PID: 2844)
Starts itself from another location
- winsdksetup.exe (PID: 552)
Executed as Windows Service
- vssvc.exe (PID: 2124)
Searches for installed software
- winsdksetup.exe (PID: 3052)
Executed via COM
- DrvInst.exe (PID: 2128)
Loads Python modules
- crypto.exe (PID: 2520)
Creates a software uninstall entry
- winsdksetup.exe (PID: 3052)
Reads Internet Cache Settings
- winsdksetup.exe (PID: 552)
Adds / modifies Windows certificates
- winsdksetup.exe (PID: 552)
Removes files from Windows directory
- winsdksetup.exe (PID: 552)
INFO
Dropped object may contain Bitcoin addresses
- winsdksetup.exe (PID: 552)
Low-level read access rights to disk partition
- vssvc.exe (PID: 2124)
Reads settings of System Certificates
- winsdksetup.exe (PID: 552)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:09 15:50:58+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 5633536 |
| InitializedDataSize: | 2560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x56154e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.1.18362.1 |
| ProductVersionNumber: | 10.1.18362.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
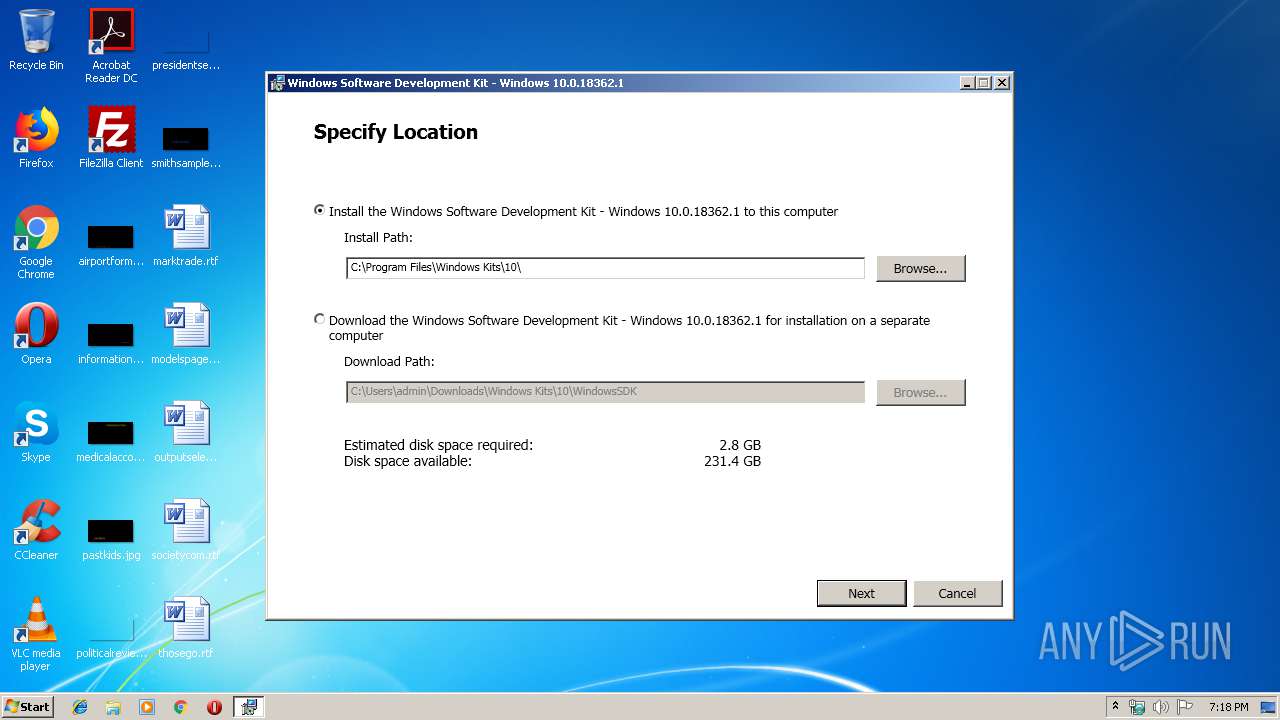
| FileDescription: | Windows Software Development Kit - Windows 10.0.18362.1 |
| FileVersion: | 10.1.18362.1 |
| InternalName: | winsdksetupEVIL.exe |
| LegalCopyright: | Copyright (c) Microsoft Corporation. All rights reserved. |
| OriginalFileName: | winsdksetupEVIL.exe |
| ProductName: | Windows Software Development Kit - Windows 10.0.18362.1 |
| ProductVersion: | 10.1.18362.1 |
| AssemblyVersion: | 10.1.18362.1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Oct-2019 13:50:58 |
| FileDescription: | Windows Software Development Kit - Windows 10.0.18362.1 |
| FileVersion: | 10.1.18362.1 |
| InternalName: | winsdksetupEVIL.exe |
| LegalCopyright: | Copyright (c) Microsoft Corporation. All rights reserved. |
| OriginalFilename: | winsdksetupEVIL.exe |
| ProductName: | Windows Software Development Kit - Windows 10.0.18362.1 |
| ProductVersion: | 10.1.18362.1 |
| Assembly Version: | 10.1.18362.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 09-Oct-2019 13:50:58 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x0055F554 | 0x0055F600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.99901 |
.rsrc | 0x00562000 | 0x00000790 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.33019 |
.reloc | 0x00564000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.0831 | 756 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
45
Monitored processes
10
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Windows\Temp\{EF33738E-EB02-4BF4-93AD-A68CDA5BB433}\.cr\winsdksetup.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\winsdksetup.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 | C:\Windows\Temp\{EF33738E-EB02-4BF4-93AD-A68CDA5BB433}\.cr\winsdksetup.exe | winsdksetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Software Development Kit - Windows 10.0.18362.1 Exit code: 0 Version: 10.1.18362.1 Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\AppData\Local\Temp\hdd.exe" | C:\Users\admin\AppData\Local\Temp\hdd.exe | — | fuck_spheres.exe | |||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: ApacheBench command line utility Exit code: 0 Version: 2.2.14 Modules
| |||||||||||||||
| 2124 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot22" "" "" "695c3f483" "00000000" "00000534" "00000394" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | "C:\Users\admin\Documents\crypto.exe" | C:\Users\admin\Documents\crypto.exe | crypto.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\Documents\crypto.exe" | C:\Users\admin\Documents\crypto.exe | fuck_spheres.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2972 | "C:\Users\admin\AppData\Local\Temp\winsdksetup.exe" | C:\Users\admin\AppData\Local\Temp\winsdksetup.exe | fuck_spheres.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Software Development Kit - Windows 10.0.18362.1 Exit code: 0 Version: 10.1.18362.1 Modules
| |||||||||||||||
| 3052 | "C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.be\winsdksetup.exe" -q -burn.elevated BurnPipe.{5235E579-47C3-4ED5-B253-A8084F156FC4} {C867AF44-D30A-448E-BB91-59371DC06513} 552 | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.be\winsdksetup.exe | winsdksetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Software Development Kit - Windows 10.0.18362.1 Exit code: 0 Version: 10.1.18362.1 Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\AppData\Local\Temp\fuck_spheres.exe" | C:\Users\admin\AppData\Local\Temp\fuck_spheres.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Windows Software Development Kit - Windows 10.0.18362.1 Exit code: 3221226540 Version: 10.1.18362.1 Modules
| |||||||||||||||
| 3364 | "C:\Users\admin\AppData\Local\Temp\fuck_spheres.exe" | C:\Users\admin\AppData\Local\Temp\fuck_spheres.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Windows Software Development Kit - Windows 10.0.18362.1 Exit code: 0 Version: 10.1.18362.1 Modules
| |||||||||||||||
Total events
1 069
Read events
747
Write events
322
Delete events
0
Modification events
| (PID) Process: | (3364) fuck_spheres.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3364) fuck_spheres.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3364) fuck_spheres.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (552) winsdksetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: winsdksetup.exe | |||
| (PID) Process: | (552) winsdksetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (552) winsdksetup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3052) winsdksetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000090C20EF8CD7ED501EC0B0000640A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3052) winsdksetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000090C20EF8CD7ED501EC0B0000640A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3052) winsdksetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 24 | |||
| (PID) Process: | (3052) winsdksetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000389764F8CD7ED501EC0B0000640A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
35
Suspicious files
7
Text files
41
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3364 | fuck_spheres.exe | C:\Users\admin\Documents\crypto.exe | executable | |
MD5:— | SHA256:— | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\BootstrapperCore.config | xml | |
MD5:57AA0F7B5F6F076454F075A88BCC0CC9 | SHA256:361079F9F118E11EA3F05D75FD3874664C94334F453177242C8E32F0881A3527 | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\mbapreq.png | image | |
MD5:A356956FD269567B8F4612A33802637B | SHA256:A401A225ADDAF89110B4B0F6E8CF94779E7C0640BCDD2D670FFCF05AAB0DAD03 | |||
| 3364 | fuck_spheres.exe | C:\Users\admin\AppData\Local\Temp\winsdksetup.exe | executable | |
MD5:31BBF735442CC6BDBE416274256B0210 | SHA256:2E28117E82B4D02FE30D564B835ACE9976612609271265872F20F2256A9C506B | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\BootstrapperCore.dll | executable | |
MD5:789476090439024462CF3694B8090B7D | SHA256:9C900B865AAAB23622C23E6F2EB22DFC881109351FE06F07CD7CC69C80CB55D2 | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\license.rtf | text | |
MD5:1C2304FD72C13D32E690924A5CB0F150 | SHA256:863A7B97EBD8FC2BA102FD7F12183CC75E281C5637F9A6CCB341CD0A2CFED297 | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\mbapreq.thm | xml | |
MD5:9F63155A23573D3E522CD28E982658B1 | SHA256:DF05AC2A44327303B718B9FC05D306047EC387EE551664B8EB9B3E48DF24B5F9 | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\Microsoft.Bootstrapper.dll | executable | |
MD5:2FE33C4EEC81898D68C1B1ABF186CCEC | SHA256:FD48FC4D1E5DDB6F0B9C7E098E58A095B13726CE69EA1A98996B2A68BDC5F114 | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\sqmapi.dll | executable | |
MD5:FC6889924C0FBDDF99B7DA588C97172D | SHA256:968D74F496162DAC8D6906E69A5DDFC13498BE4A380AFB814CB7EB19A0B167EB | |||
| 552 | winsdksetup.exe | C:\Windows\Temp\{8138BF5E-4579-4E6D-B9A6-6296A927979D}\.ba\Microsoft.Bootstrapper.Presentation.dll | executable | |
MD5:28A709345DC0BD3E55C0C7A0B4C68BEE | SHA256:10DD4F2220903EBD9D4842126FA457835EAC0E0495F129B6CD36905F3DC6B779 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
552 | winsdksetup.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?prd=11966&pver=1.0&plcid=0x409&clcid=0x409&ar=Windows10&sar=SDK&o1=10.0.18362.1 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
552 | winsdksetup.exe | 2.19.38.59:80 | go.microsoft.com | Akamai International B.V. | — | whitelisted |
552 | winsdksetup.exe | 2.18.233.19:443 | download.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |