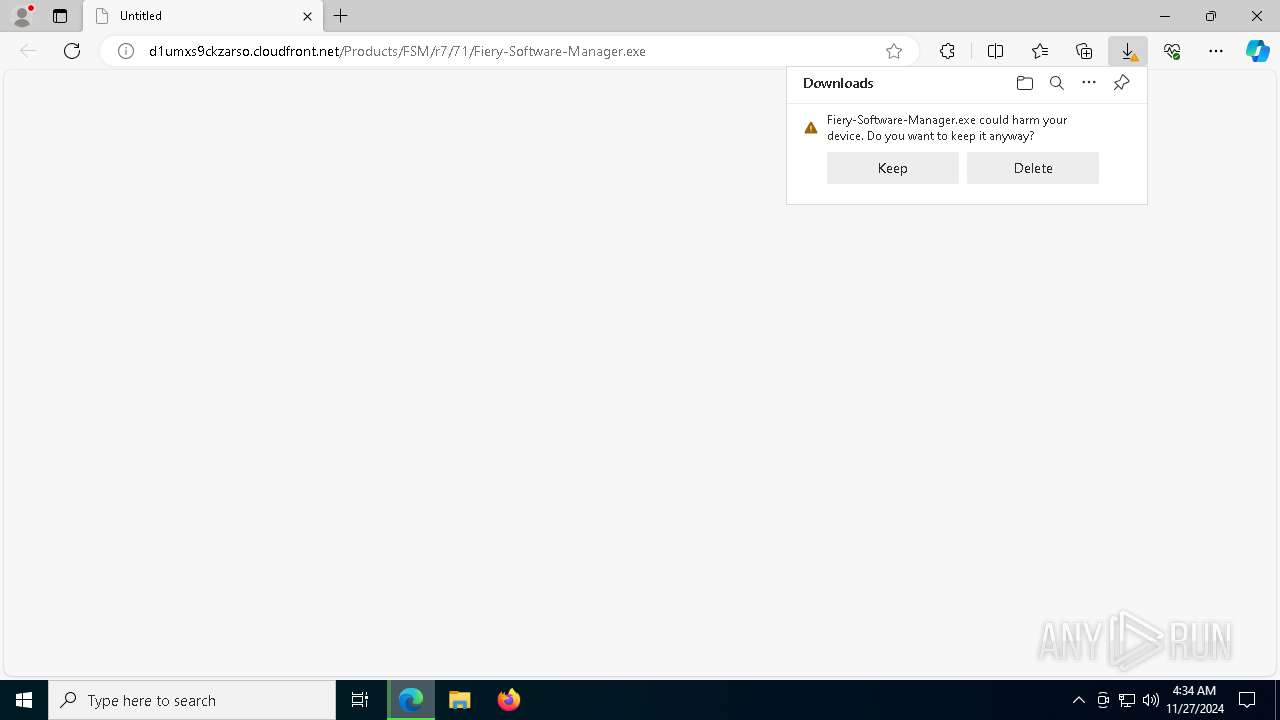
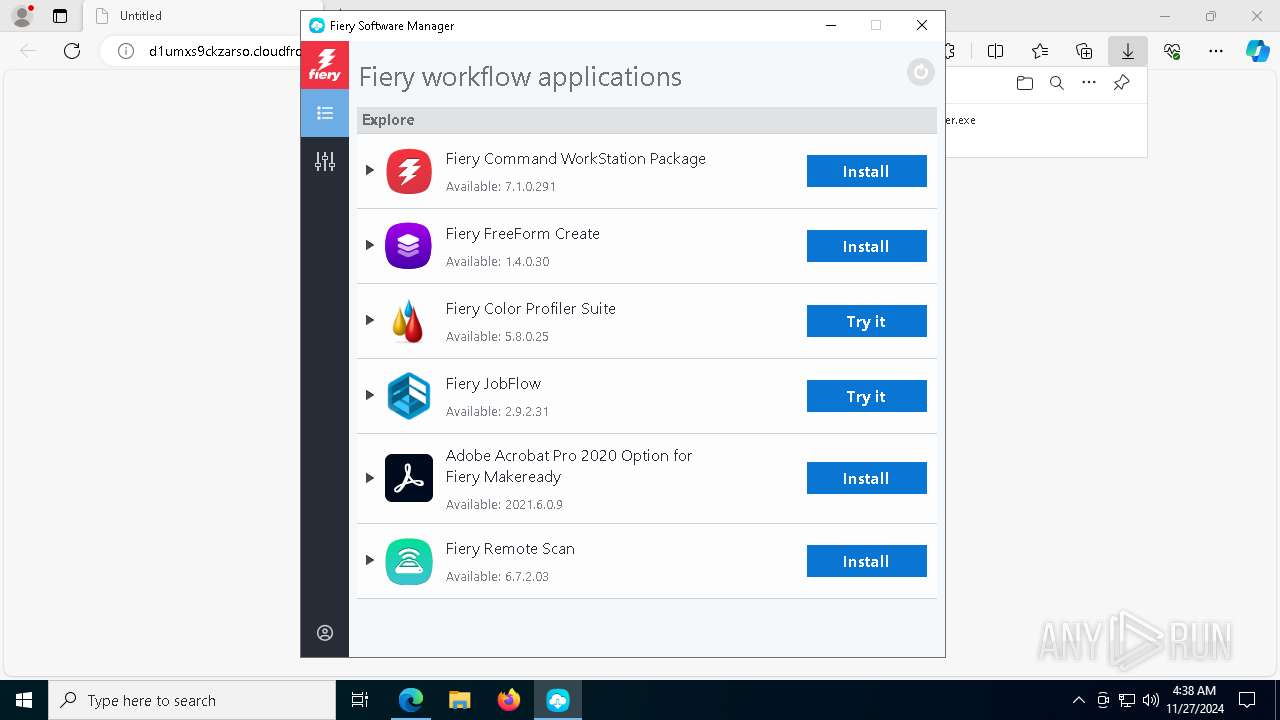
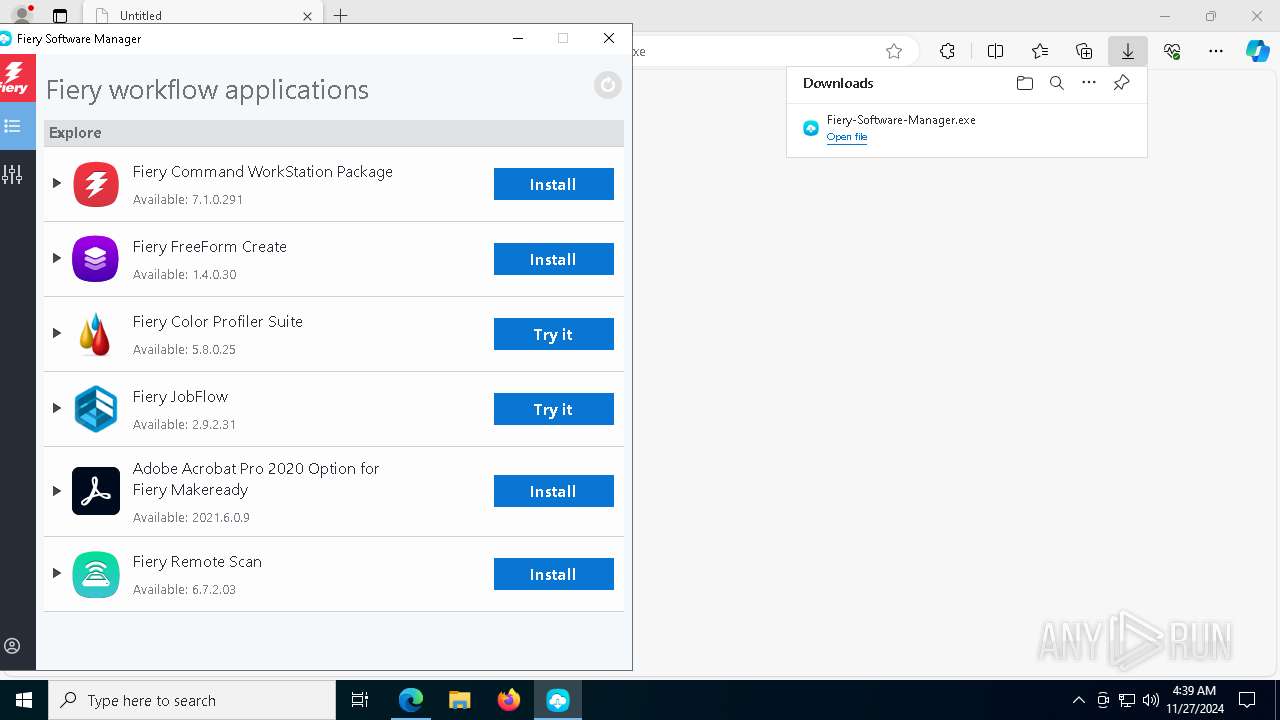
| URL: | d1umxs9ckzarso.cloudfront.net/Products/FSM/r7/71/Fiery-Software-Manager.exe |
| Full analysis: | https://app.any.run/tasks/0ca73ef2-890c-43c8-8f66-f2eb9dd7c2d1 |
| Verdict: | Malicious activity |
| Analysis date: | November 27, 2024, 04:34:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | A3A46377360D026EDCD410A698E36CBA |
| SHA1: | BB221E59F5AA0A314375F28FF632086BE62B1157 |
| SHA256: | 978CFECFD40595EF8B647405A136F8F1DBAD103FCB6DECB4C63CE7C6E1A1577B |
| SSDEEP: | 3:kd2I5Il/0uKQB7oGSvMAt3YCY:JIvBU7oFvMsYF |
MALICIOUS
Uses Task Scheduler to run other applications
- msiexec.exe (PID: 7432)
The DLL Hijacking
- msedgewebview2.exe (PID: 3864)
SUSPICIOUS
Executable content was dropped or overwritten
- Fiery-Software-Manager.exe (PID: 2452)
- WebView2-Installer.exe (PID: 8136)
- expand.exe (PID: 1752)
- curl.exe (PID: 6184)
- FACConnector.exe (PID: 3524)
- FACConnector.exe (PID: 7892)
Process drops legitimate windows executable
- Fiery-Software-Manager.exe (PID: 2452)
- expand.exe (PID: 1752)
- msiexec.exe (PID: 4944)
The process creates files with name similar to system file names
- Fiery-Software-Manager.exe (PID: 2452)
The process drops C-runtime libraries
- Fiery-Software-Manager.exe (PID: 2452)
- expand.exe (PID: 1752)
- msiexec.exe (PID: 4944)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- Fiery Software Manager.exe (PID: 7548)
Reads security settings of Internet Explorer
- Fiery-Software-Manager.exe (PID: 2452)
- Fiery Software Manager.exe (PID: 7548)
- msiexec.exe (PID: 7900)
- msiexec.exe (PID: 7432)
- msedgewebview2.exe (PID: 6408)
Reads the date of Windows installation
- Fiery-Software-Manager.exe (PID: 2452)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Fiery Software Manager.exe (PID: 7548)
- cmd.exe (PID: 3808)
Process uses powershell cmdlet to discover network configuration
- Fiery Software Manager.exe (PID: 7548)
Starts POWERSHELL.EXE for commands execution
- Fiery Software Manager.exe (PID: 7548)
Uses WMIC.EXE to obtain CPU information
- Fiery Software Manager.exe (PID: 7548)
Starts itself from another location
- WebView2-Installer.exe (PID: 6440)
- FACConnector.exe (PID: 3524)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4944)
Checks Windows Trust Settings
- msiexec.exe (PID: 4944)
- msiexec.exe (PID: 7900)
- msiexec.exe (PID: 7432)
Executing commands from a ".bat" file
- msiexec.exe (PID: 7900)
Unpacks CAB file
- expand.exe (PID: 1752)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 7900)
- WebView2-Installer.exe (PID: 8136)
- msiexec.exe (PID: 7432)
- FACConnector.exe (PID: 7892)
The process deletes folder without confirmation
- WebView2-Installer.exe (PID: 8136)
- FACConnector.exe (PID: 7892)
Application launched itself
- msedgewebview2.exe (PID: 6408)
- msedgewebview2.exe (PID: 3656)
The process executes via Task Scheduler
- CWSAppsMonitor.exe (PID: 7928)
Searches for installed software
- msedgewebview2.exe (PID: 6408)
INFO
Checks supported languages
- identity_helper.exe (PID: 7552)
- Fiery-Software-Manager.exe (PID: 2452)
- Fiery Software Manager.exe (PID: 7548)
- curl.exe (PID: 4132)
- curl.exe (PID: 7844)
- curl.exe (PID: 3992)
- WebView2-Installer.exe (PID: 6440)
- WebView2-Installer.exe (PID: 8136)
- msiexec.exe (PID: 4944)
- msiexec.exe (PID: 7900)
- _is3B3.exe (PID: 3996)
- _is3B3.exe (PID: 7224)
- _is3B3.exe (PID: 7772)
- _is3B3.exe (PID: 5340)
- _is3B3.exe (PID: 2380)
- _is3B3.exe (PID: 2928)
- _is3B3.exe (PID: 7428)
- _is3B3.exe (PID: 6084)
- _is3B3.exe (PID: 4392)
- _is3B3.exe (PID: 6156)
- _is2A85.exe (PID: 6544)
- _is2A85.exe (PID: 1476)
- _is2A85.exe (PID: 4472)
- _is2A85.exe (PID: 1172)
- _is2A85.exe (PID: 8040)
- _is2A85.exe (PID: 4012)
- _is2A85.exe (PID: 4980)
- _is2A85.exe (PID: 5936)
- _is2A85.exe (PID: 6924)
- _is2A85.exe (PID: 6744)
- expand.exe (PID: 1752)
- _isAA07.exe (PID: 6764)
- _isAA07.exe (PID: 5568)
- _isAA07.exe (PID: 7812)
- _isAA07.exe (PID: 4652)
- _isAA07.exe (PID: 2736)
- _isAA07.exe (PID: 6168)
- curl.exe (PID: 8128)
- FACConnector.exe (PID: 7892)
- curl.exe (PID: 1020)
- curl.exe (PID: 8180)
- FACConnector.exe (PID: 3524)
- _isE9FC.exe (PID: 5892)
- _isE9FC.exe (PID: 3564)
- _isE9FC.exe (PID: 3140)
- _isE9FC.exe (PID: 1580)
- _isF353.exe (PID: 1200)
- msiexec.exe (PID: 7432)
- _isE9FC.exe (PID: 6404)
- _isF353.exe (PID: 4336)
- _isF353.exe (PID: 4076)
- _isF846.exe (PID: 1876)
- _isF846.exe (PID: 5916)
- _isF846.exe (PID: 2408)
- _isF846.exe (PID: 2124)
- _isF846.exe (PID: 1796)
- _isF846.exe (PID: 1740)
- FieryAppsCloudConnector.exe (PID: 5728)
- CWSAppsMonitor.exe (PID: 7928)
- curl.exe (PID: 68)
- curl.exe (PID: 6752)
- msedgewebview2.exe (PID: 3656)
- curl.exe (PID: 5892)
- msedgewebview2.exe (PID: 6408)
- msedgewebview2.exe (PID: 3864)
- msedgewebview2.exe (PID: 372)
- curl.exe (PID: 6936)
- msedgewebview2.exe (PID: 5448)
- curl.exe (PID: 2408)
- curl.exe (PID: 7576)
- curl.exe (PID: 7932)
- msedgewebview2.exe (PID: 7344)
- curl.exe (PID: 7596)
- msedgewebview2.exe (PID: 1796)
- msedgewebview2.exe (PID: 7828)
- curl.exe (PID: 8084)
Executable content was dropped or overwritten
- msedge.exe (PID: 6264)
- msedge.exe (PID: 6628)
- msiexec.exe (PID: 4944)
- msiexec.exe (PID: 7900)
- msedge.exe (PID: 7928)
- msiexec.exe (PID: 7432)
Reads the computer name
- identity_helper.exe (PID: 7552)
- Fiery-Software-Manager.exe (PID: 2452)
- Fiery Software Manager.exe (PID: 7548)
- curl.exe (PID: 4132)
- curl.exe (PID: 7844)
- WebView2-Installer.exe (PID: 6440)
- curl.exe (PID: 3992)
- msiexec.exe (PID: 4944)
- WebView2-Installer.exe (PID: 8136)
- msiexec.exe (PID: 7900)
- _is3B3.exe (PID: 3996)
- _is3B3.exe (PID: 7772)
- _is3B3.exe (PID: 5340)
- _is3B3.exe (PID: 7224)
- _is3B3.exe (PID: 2380)
- _is3B3.exe (PID: 2928)
- _is3B3.exe (PID: 7428)
- _is3B3.exe (PID: 6084)
- _is3B3.exe (PID: 4392)
- _is3B3.exe (PID: 6156)
- _is2A85.exe (PID: 6544)
- _is2A85.exe (PID: 4472)
- _is2A85.exe (PID: 8040)
- _is2A85.exe (PID: 1476)
- _is2A85.exe (PID: 1172)
- _is2A85.exe (PID: 4012)
- _is2A85.exe (PID: 4980)
- _is2A85.exe (PID: 5936)
- _is2A85.exe (PID: 6924)
- _is2A85.exe (PID: 6744)
- _isAA07.exe (PID: 5568)
- _isAA07.exe (PID: 6764)
- _isAA07.exe (PID: 7812)
- _isAA07.exe (PID: 4652)
- _isAA07.exe (PID: 2736)
- _isAA07.exe (PID: 6168)
- curl.exe (PID: 8128)
- curl.exe (PID: 6184)
- curl.exe (PID: 8180)
- FACConnector.exe (PID: 3524)
- _isE9FC.exe (PID: 3564)
- _isE9FC.exe (PID: 5892)
- _isE9FC.exe (PID: 3140)
- _isE9FC.exe (PID: 1580)
- _isF353.exe (PID: 1200)
- msiexec.exe (PID: 7432)
- _isE9FC.exe (PID: 6404)
- _isF846.exe (PID: 1740)
- _isF353.exe (PID: 4336)
- _isF353.exe (PID: 4076)
- _isF846.exe (PID: 5916)
- _isF846.exe (PID: 2408)
- _isF846.exe (PID: 2124)
- _isF846.exe (PID: 1796)
- _isF846.exe (PID: 1876)
- curl.exe (PID: 68)
- msedgewebview2.exe (PID: 3656)
- curl.exe (PID: 5892)
- curl.exe (PID: 776)
- msedgewebview2.exe (PID: 6820)
- msedgewebview2.exe (PID: 3864)
- curl.exe (PID: 7932)
- curl.exe (PID: 7596)
- curl.exe (PID: 6936)
The process uses the downloaded file
- msedge.exe (PID: 7284)
- msedge.exe (PID: 6264)
- Fiery-Software-Manager.exe (PID: 2452)
Reads Environment values
- identity_helper.exe (PID: 7552)
- msedgewebview2.exe (PID: 6408)
Creates files or folders in the user directory
- Fiery-Software-Manager.exe (PID: 2452)
- Fiery Software Manager.exe (PID: 7548)
Process checks computer location settings
- Fiery-Software-Manager.exe (PID: 2452)
- msedgewebview2.exe (PID: 6408)
- msedgewebview2.exe (PID: 5448)
Application launched itself
- msedge.exe (PID: 6264)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7828)
Creates files in the program directory
- Fiery Software Manager.exe (PID: 7548)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7828)
Checks proxy server information
- Fiery Software Manager.exe (PID: 7548)
- msiexec.exe (PID: 7900)
- msedgewebview2.exe (PID: 6408)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 640)
Reads the machine GUID from the registry
- msiexec.exe (PID: 4944)
- msiexec.exe (PID: 7900)
- expand.exe (PID: 1752)
- msiexec.exe (PID: 7432)
- FieryAppsCloudConnector.exe (PID: 5728)
Reads the software policy settings
- msiexec.exe (PID: 4944)
- msiexec.exe (PID: 7900)
- msiexec.exe (PID: 7432)
Creates a software uninstall entry
- msiexec.exe (PID: 4944)
Sends debugging messages
- msedgewebview2.exe (PID: 6408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
333
Monitored processes
200
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | curl.exe -s --insecure -H "Authorization:Basic RmllcnkgU29mdHdhcmUgTWFuYWdlcjo2QjYyOTM3MC0wNjFELTQ3RkMtQjM5Ri0zNzg3OUQzMTE2OUI=" -H "Accept:application/json" -H "Content-Type:application/json" -X POST -d @"C:\Users\admin\AppData\Roaming\Fiery Software Manager\Analytics\\efi_tmp_install.json" "https://ews.fiery.com/api/v1/analytics/fsm" | C:\Users\admin\AppData\Roaming\Fiery Software Manager\extract\fsm-2024-11-27-04-35-15-582\FSM\curl.exe | Fiery Software Manager.exe | ||||||||||||
User: admin Company: curl, https://curl.haxx.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 7.73.0 Modules
| |||||||||||||||
| 308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | "C:\Program Files\Common Files\EFI\WebView2\Microsoft.WebView2.FixedVersionRuntime.126.0.2592.87.x64\msedgewebview2.exe" --type=renderer --noerrdialogs --user-data-dir="C:\ProgramData\Fiery Software Manager\7548\EBWebView" --webview-exe-name="Fiery Software Manager.exe" --webview-exe-version=7.1.0.10 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=0 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --js-flags="--harmony-weak-refs-with-cleanup-some --expose-gc --ms-user-locale=" --field-trial-handle=3392,i,7692510181509964795,15045528791675791661,262144 --enable-features=MojoIpcz --variations-seed-version --mojo-platform-channel-handle=3400 /prefetch:1 | C:\Program Files\Common Files\EFI\WebView2\Microsoft.WebView2.FixedVersionRuntime.126.0.2592.87.x64\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Version: 126.0.2592.87 | |||||||||||||||
| 640 | wmic cpu get Name | C:\Windows\System32\wbem\WMIC.exe | — | Fiery Software Manager.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\Users\admin\AppData\Local\Temp\{E4225F7F-BBE0-43DC-BA78-63B2D1451FF5}\_isAA07.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{020AFFCF-0A0B-480E-B2B9-A4EEF35891F1} | C:\Users\admin\AppData\Local\Temp\{E4225F7F-BBE0-43DC-BA78-63B2D1451FF5}\_isAA07.exe | — | msiexec.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 28.0.759 Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5332 --field-trial-handle=2348,i,8444360536497623914,3579114221099040666,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 776 | curl.exe -s --insecure --output "C:\Fiery Software Manager\Downloads\assets\icons\ffc.png" "https://d1umxs9ckzarso.cloudfront.net/Products/assets/icons/48/ffc.png" | C:\Users\admin\AppData\Roaming\Fiery Software Manager\extract\fsm-2024-11-27-04-35-15-582\FSM\curl.exe | Fiery Software Manager.exe | ||||||||||||
User: admin Company: curl, https://curl.haxx.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 7.73.0 Modules
| |||||||||||||||
| 836 | "C:\Program Files\Common Files\EFI\WebView2\Microsoft.WebView2.FixedVersionRuntime.126.0.2592.87.x64\msedgewebview2.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --noerrdialogs --user-data-dir="C:\ProgramData\Fiery Software Manager\7548\EBWebView" --webview-exe-name="Fiery Software Manager.exe" --webview-exe-version=7.1.0.10 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=0 --field-trial-handle=5012,i,7692510181509964795,15045528791675791661,262144 --enable-features=MojoIpcz --variations-seed-version --mojo-platform-channel-handle=5096 /prefetch:8 | C:\Program Files\Common Files\EFI\WebView2\Microsoft.WebView2.FixedVersionRuntime.126.0.2592.87.x64\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 126.0.2592.87 | |||||||||||||||
| 1020 | curl.exe -s --insecure --output "C:\Fiery Software Manager\Downloads\FieryAppsCloudConnector\7.1.0011\config.xml" "https://d1umxs9ckzarso.cloudfront.net/Products/FACC/71/config_facc_win.xml" | C:\Users\admin\AppData\Roaming\Fiery Software Manager\extract\fsm-2024-11-27-04-35-15-582\FSM\curl.exe | Fiery Software Manager.exe | ||||||||||||
User: admin Company: curl, https://curl.haxx.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 7.73.0 Modules
| |||||||||||||||
| 1172 | C:\Users\admin\AppData\Local\Temp\{07879E5C-88C2-4AB6-8687-396AA6F8A518}\_is2A85.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{BE579844-672B-4D51-AC09-0E4F70EE7C45} | C:\Users\admin\AppData\Local\Temp\{07879E5C-88C2-4AB6-8687-396AA6F8A518}\_is2A85.exe | — | msiexec.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 28.0.759 Modules
| |||||||||||||||
Total events
41 858
Read events
41 535
Write events
303
Delete events
20
Modification events
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: EE6E26C573862F00 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E1B72FC573862F00 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393902 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DF32EB33-ABB4-4134-801B-6C389D281255} | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393902 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C3D5FC87-0E16-4672-AE1D-6AE58EEC47DD} | |||
| (PID) Process: | (6264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393902 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F9467B33-A203-4A8F-A6F5-34D3D1BD1C37} | |||
Executable files
205
Suspicious files
684
Text files
262
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13540f.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13540f.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13540f.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13541e.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13541e.TMP | — | |
MD5:— | SHA256:— | |||
| 6264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
105
DNS requests
84
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4996 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1733055667&P2=404&P3=2&P4=fs%2boLNixyhg8Ldvgzm03aerElfoZsypwm76JgChziopK3PLtY1TVsDH%2bAjcp8os3Gz2MRdLE2V%2f%2fkLNdagy49g%3d%3d | unknown | — | — | whitelisted |
4996 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1733055667&P2=404&P3=2&P4=fs%2boLNixyhg8Ldvgzm03aerElfoZsypwm76JgChziopK3PLtY1TVsDH%2bAjcp8os3Gz2MRdLE2V%2f%2fkLNdagy49g%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6264 | msedge.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6264 | msedge.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7728 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6772 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4992 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6628 | msedge.exe | 3.160.156.135:80 | d1umxs9ckzarso.cloudfront.net | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
d1umxs9ckzarso.cloudfront.net |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6820 | msedgewebview2.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6820 | msedgewebview2.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
Process | Message |
|---|---|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\ProgramData directory exists )
|