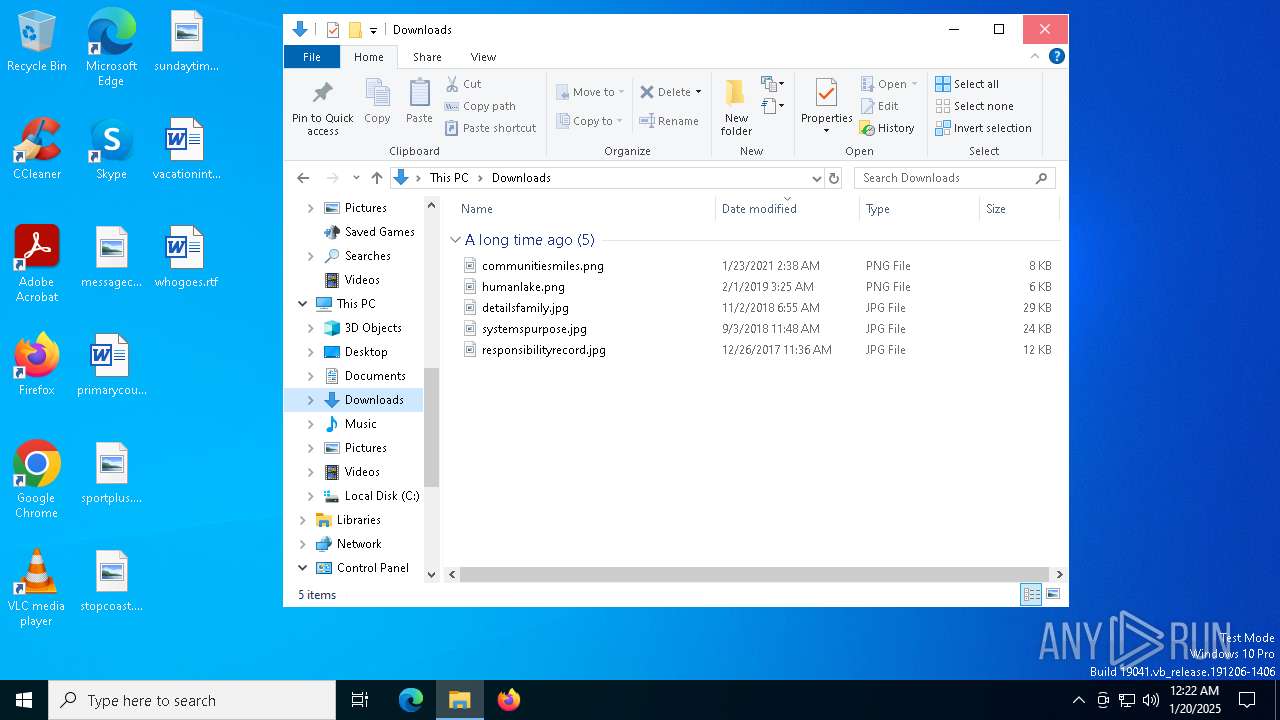
| File name: | Marvel Rivals Executor.exe |
| Full analysis: | https://app.any.run/tasks/b3aedd20-cece-4d06-9f0d-ac7f1d07d09f |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | January 20, 2025, 00:21:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | B01F60EB9F3D1BB4E0E7674C95FBBC53 |
| SHA1: | 44DD0FDC5B2A1A9FBA9208EFF91296B6C1555F15 |
| SHA256: | 9787C91D7F8732CEBADC7047BC6775ABC062260E456E00BF95B6FD4D37D4A068 |
| SSDEEP: | 98304:0yi3eaYRaDqp4+aEc7xPFPHlt8YOesmZ9tWDp9XZy2QG82UpxLgHczYm:SRZ |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6184)
Connects to the CnC server
- wininit.exe (PID: 5892)
Steals credentials from Web Browsers
- wininit.exe (PID: 5892)
Actions looks like stealing of personal data
- wininit.exe (PID: 5892)
DARKCRYSTAL has been detected (SURICATA)
- wininit.exe (PID: 5892)
SUSPICIOUS
Reads security settings of Internet Explorer
- Marvel Rivals Executor.exe (PID: 244)
- SessionCrtmonitor.exe (PID: 7148)
Executable content was dropped or overwritten
- Marvel Rivals Executor.exe (PID: 244)
- SessionCrtmonitor.exe (PID: 7148)
- wininit.exe (PID: 5892)
Executing commands from a ".bat" file
- wscript.exe (PID: 6184)
- SessionCrtmonitor.exe (PID: 7148)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6184)
- SessionCrtmonitor.exe (PID: 7148)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6184)
The process creates files with name similar to system file names
- SessionCrtmonitor.exe (PID: 7148)
Reads the date of Windows installation
- SessionCrtmonitor.exe (PID: 7148)
Starts application with an unusual extension
- cmd.exe (PID: 3172)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 3172)
Loads DLL from Mozilla Firefox
- wininit.exe (PID: 5892)
Connects to the server without a host name
- wininit.exe (PID: 5892)
INFO
Reads the computer name
- Marvel Rivals Executor.exe (PID: 244)
- SessionCrtmonitor.exe (PID: 7148)
- wininit.exe (PID: 5892)
Checks supported languages
- Marvel Rivals Executor.exe (PID: 244)
- SessionCrtmonitor.exe (PID: 7148)
- chcp.com (PID: 6208)
- wininit.exe (PID: 5892)
Drops encrypted VBS script (Microsoft Script Encoder)
- Marvel Rivals Executor.exe (PID: 244)
- wscript.exe (PID: 6184)
- wininit.exe (PID: 5892)
Process checks computer location settings
- Marvel Rivals Executor.exe (PID: 244)
- SessionCrtmonitor.exe (PID: 7148)
The process uses the downloaded file
- Marvel Rivals Executor.exe (PID: 244)
- wscript.exe (PID: 6184)
- SessionCrtmonitor.exe (PID: 7148)
Reads the machine GUID from the registry
- SessionCrtmonitor.exe (PID: 7148)
- wininit.exe (PID: 5892)
Reads Environment values
- SessionCrtmonitor.exe (PID: 7148)
- wininit.exe (PID: 5892)
Failed to create an executable file in Windows directory
- SessionCrtmonitor.exe (PID: 7148)
Create files in a temporary directory
- SessionCrtmonitor.exe (PID: 7148)
- wininit.exe (PID: 5892)
Changes the display of characters in the console
- cmd.exe (PID: 3172)
Disables trace logs
- wininit.exe (PID: 5892)
Checks proxy server information
- wininit.exe (PID: 5892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 488960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
136
Monitored processes
11
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:\Users\admin\AppData\Local\Temp\Marvel Rivals Executor.exe" | C:\Users\admin\AppData\Local\Temp\Marvel Rivals Executor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3172 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\VvxuVq60pw.bat" " | C:\Windows\System32\cmd.exe | — | SessionCrtmonitor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3640 | w32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 | C:\Windows\System32\w32tm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Service Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | "C:\BlockAgentProviderInto\wininit.exe" | C:\BlockAgentProviderInto\wininit.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 16.10.31418.88 Modules
| |||||||||||||||
| 6176 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6184 | "C:\WINDOWS\System32\WScript.exe" "C:\BlockAgentProviderInto\PjnstjcvPY7Lzl6nvMIVWIEKqqKpxghO5JeSx3djwQLOxG0mHAk0HXCLi6.vbe" | C:\Windows\SysWOW64\wscript.exe | — | Marvel Rivals Executor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6208 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | C:\WINDOWS\system32\cmd.exe /c ""C:\BlockAgentProviderInto\9gPeLytJW1s8p3jUCK.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 098
Read events
4 081
Write events
17
Delete events
0
Modification events
| (PID) Process: | (244) Marvel Rivals Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (7148) SessionCrtmonitor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\dc755e20c3956ce10dc5d57983d393828798e0c2 |
| Operation: | write | Name: | 6ce49301ab1c54f5abffd003b557929649d95134 |
Value: H4sIAAAAAAAEAI3MsQ7CMAwE0H/pjPgAttKJDSlIDJihSkwTldqV7ab07xsxMaHohlve3aPpTgDnN/uxHZDsKpxTQLmQMYDDXnxs5/mIH2wOf+0SVbOvgC8mC5Ijq/3oe6LAqwLceh1LuU0NJ4dmiQatuF0TlViFdKiamDqxicuC5bt57of9rawLAQAA | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5892) wininit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wininit_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
12
Suspicious files
24
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 244 | Marvel Rivals Executor.exe | C:\BlockAgentProviderInto\PjnstjcvPY7Lzl6nvMIVWIEKqqKpxghO5JeSx3djwQLOxG0mHAk0HXCLi6.vbe | binary | |
MD5:D87DEB22F708BEDB00EF3D8EC13E99C9 | SHA256:C262F37A9599F8D97B352BDD622E9446B0AF66C141A894E5ABCF7A8275C1BB96 | |||
| 244 | Marvel Rivals Executor.exe | C:\BlockAgentProviderInto\9gPeLytJW1s8p3jUCK.bat | text | |
MD5:8C3BF6186F713EE49D532A73CCB90E3F | SHA256:77ED1C1EBAF014D5F0D8857215E7DF2531F6DBF8C9ABCB4AFCBE6307BE24CF39 | |||
| 7148 | SessionCrtmonitor.exe | C:\BlockAgentProviderInto\SearchApp.exe | executable | |
MD5:3008B3A2D8FA96CD7B26B6DEEE1E3CED | SHA256:B6608D50DDCC1DBEDA65F37E65D9AB565DA1511292D0EC26CF9C63C45D75C9C5 | |||
| 7148 | SessionCrtmonitor.exe | C:\Users\admin\Desktop\mclVKgns.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 5892 | wininit.exe | C:\Users\admin\Desktop\unfUvkXP.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 7148 | SessionCrtmonitor.exe | C:\BlockAgentProviderInto\105eec298f1910 | text | |
MD5:073CC24F65A2C7768E9815678CEF7EF5 | SHA256:BB0A0F6C11629A90E4EFFB25BBD2FF6673FD0D09829F01CD5A80A863345056F2 | |||
| 7148 | SessionCrtmonitor.exe | C:\BlockAgentProviderInto\uhssvc.exe | executable | |
MD5:3008B3A2D8FA96CD7B26B6DEEE1E3CED | SHA256:B6608D50DDCC1DBEDA65F37E65D9AB565DA1511292D0EC26CF9C63C45D75C9C5 | |||
| 7148 | SessionCrtmonitor.exe | C:\BlockAgentProviderInto\38384e6a620884 | text | |
MD5:79778468873C87A441F8A0FCB36C8D9E | SHA256:4BBD6F515CAE2F45620D2D23475487DCD8930C86F5F8296753F7FEAE957524F9 | |||
| 7148 | SessionCrtmonitor.exe | C:\Users\admin\AppData\Local\Temp\GPbrOUwdvr | text | |
MD5:93EE49278E9FAFC60868BD4F362555CE | SHA256:0CB58DACEE3A1C1617911E517A455329B7CFD222F6EE5EABF690038D61B0C7C7 | |||
| 7148 | SessionCrtmonitor.exe | C:\BlockAgentProviderInto\fontdrvhost.exe | executable | |
MD5:3008B3A2D8FA96CD7B26B6DEEE1E3CED | SHA256:B6608D50DDCC1DBEDA65F37E65D9AB565DA1511292D0EC26CF9C63C45D75C9C5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
85
TCP/UDP connections
30
DNS requests
15
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5856 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5892 | wininit.exe | POST | 200 | 176.123.1.211:80 | http://176.123.1.211/dbDatalifeprivatecdn.php | unknown | — | — | malicious |
6524 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5892 | wininit.exe | POST | 200 | 176.123.1.211:80 | http://176.123.1.211/dbDatalifeprivatecdn.php | unknown | — | — | malicious |
5892 | wininit.exe | POST | 200 | 176.123.1.211:80 | http://176.123.1.211/dbDatalifeprivatecdn.php | unknown | — | — | malicious |
6908 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6908 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5892 | wininit.exe | POST | 200 | 176.123.1.211:80 | http://176.123.1.211/dbDatalifeprivatecdn.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5856 | svchost.exe | 95.101.149.131:80 | — | Akamai International B.V. | NL | unknown |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5856 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5892 | wininit.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5892 | wininit.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5892 | wininit.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Exfiltration (POST) |
5892 | wininit.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Exfiltration (POST) |