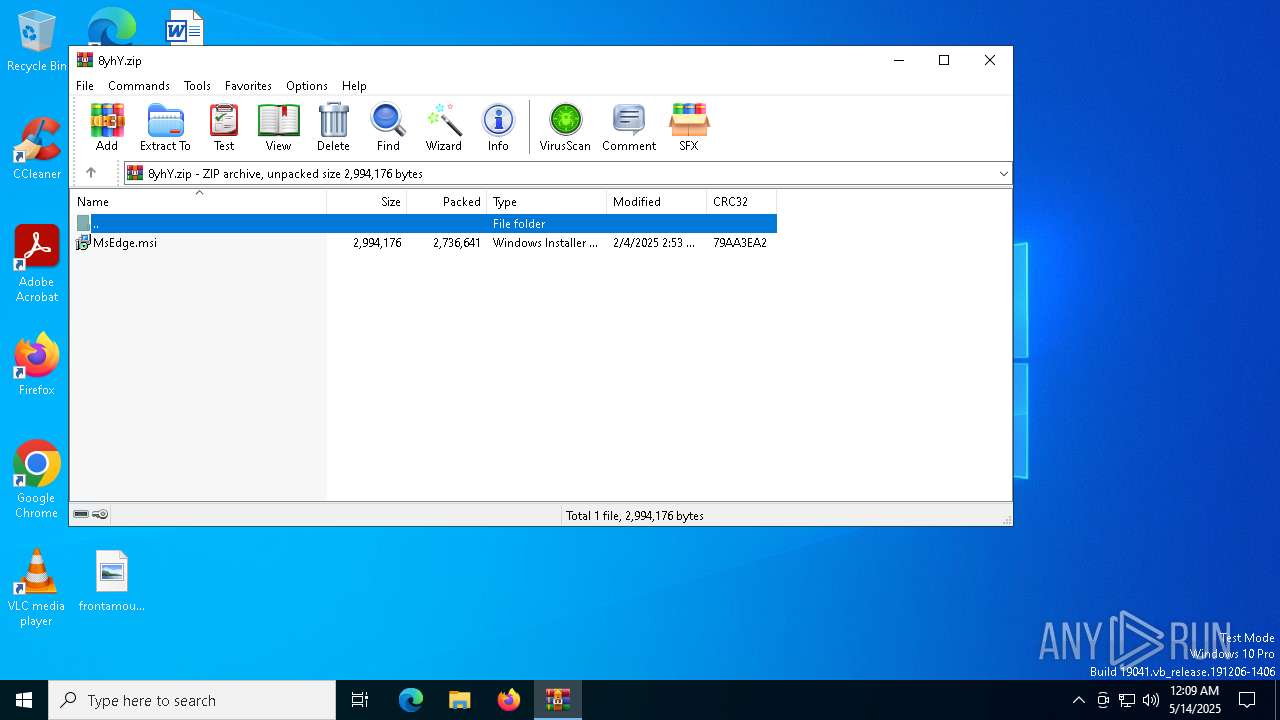
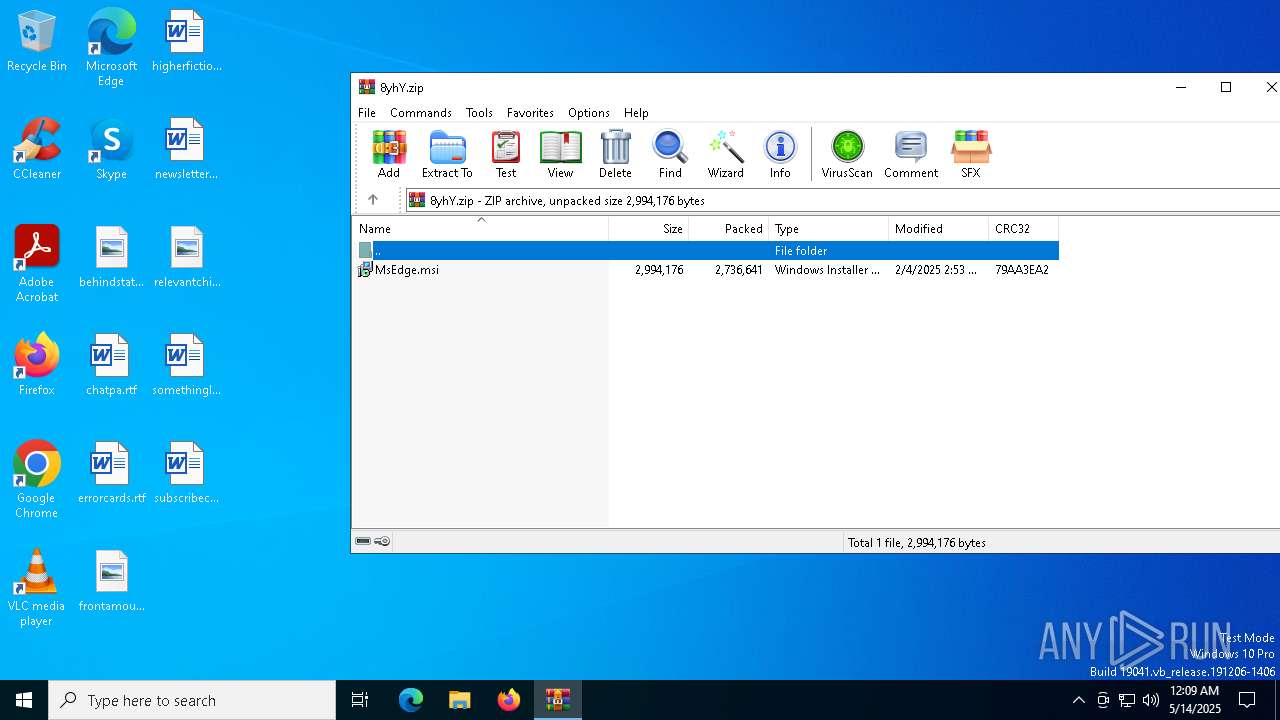
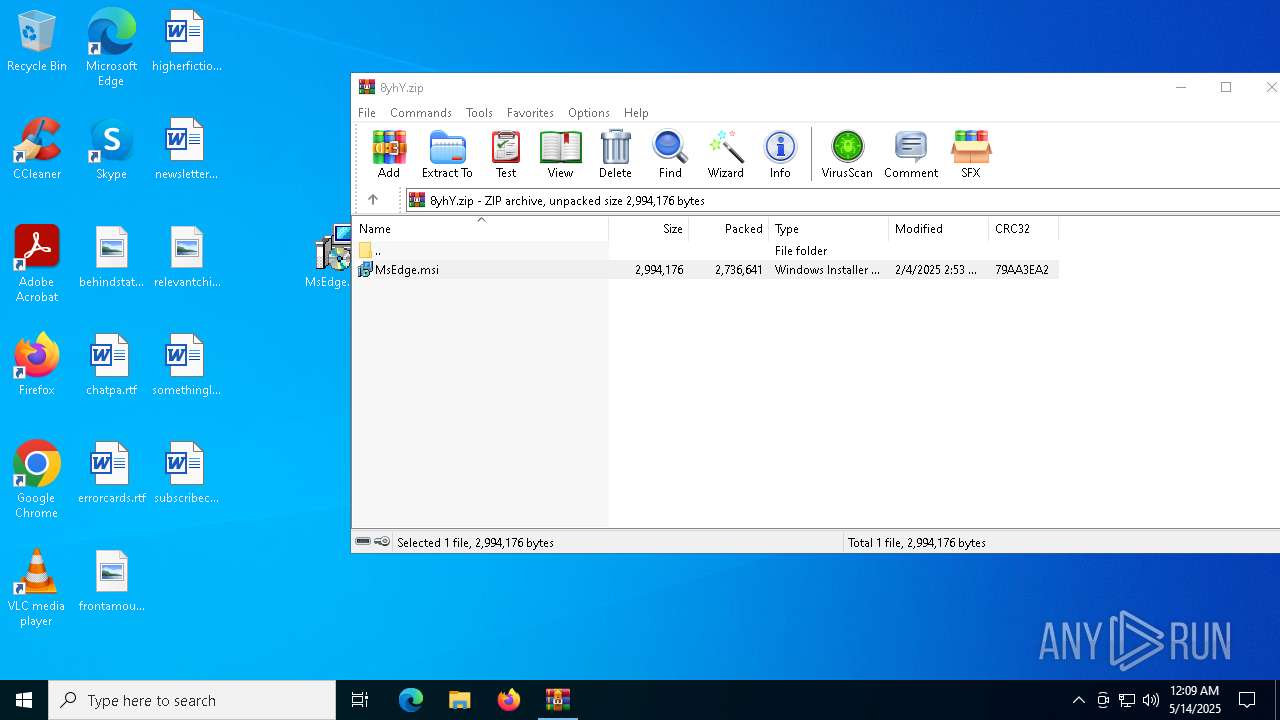
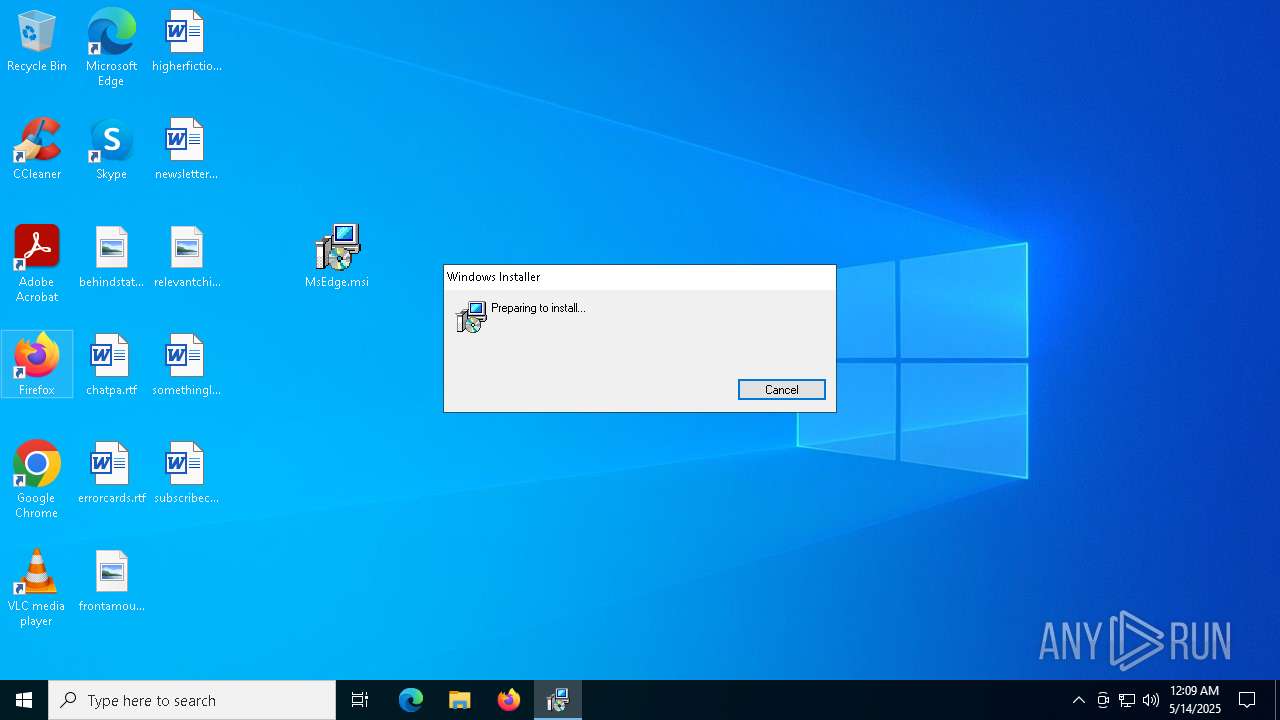
| File name: | 8yhY.zip |
| Full analysis: | https://app.any.run/tasks/99c9c8ff-449b-42f8-a270-6efe01c99fdb |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 00:08:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 731744E0A108A307BAA798896F789F9B |
| SHA1: | 4B90966D7CB37D301EC3887E456B7643133F3C56 |
| SHA256: | 9730CB1D40459EDF34C609445675C89CF568F8EC3290925BDE194B030C53BE67 |
| SSDEEP: | 98304:ZoW7k4vnXOQRh46w3RbEjCTuFS+OQXndiuaJzytSbNmaAQ3VlKKvjKOBvzeLj74D:H6m/rEu4 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6184)
ATERAAGENT has been detected (YARA)
- msiexec.exe (PID: 660)
- msiexec.exe (PID: 2096)
Executing a file with an untrusted certificate
- msedgewebview2.exe (PID: 6136)
- msedgewebview2.exe (PID: 1196)
Starts NET.EXE for service management
- net.exe (PID: 5776)
- msiexec.exe (PID: 2344)
Bypass execution policy to execute commands
- powershell.exe (PID: 4572)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 1300)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6184)
- msiexec.exe (PID: 2096)
- msedgewebview2.exe (PID: 6136)
Executes as Windows Service
- VSSVC.exe (PID: 4336)
- msedgewebview2.exe (PID: 6136)
Executable content was dropped or overwritten
- rundll32.exe (PID: 2564)
- rundll32.exe (PID: 6108)
- rundll32.exe (PID: 928)
- rundll32.exe (PID: 2288)
- msedgewebview2.exe (PID: 6136)
- csc.exe (PID: 5132)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 6108)
- msedgewebview2.exe (PID: 6136)
- AgentPackageMonitoring.exe (PID: 5544)
- AgentPackageAgentInformation.exe (PID: 1300)
- AgentPackageAgentInformation.exe (PID: 2084)
- AgentPackageAgentInformation.exe (PID: 4528)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 2344)
Restarts service on failure
- sc.exe (PID: 4436)
Starts SC.EXE for service management
- msedgewebview2.exe (PID: 6136)
CSC.EXE is used to compile C# code
- csc.exe (PID: 5132)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5528)
- AgentPackageAgentInformation.exe (PID: 1300)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 1300)
The process executes VB scripts
- cmd.exe (PID: 2664)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 1300)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 1300)
- cmd.exe (PID: 5528)
Executes application which crashes
- cscript.exe (PID: 4784)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6184)
- msiexec.exe (PID: 2096)
Checks proxy server information
- msiexec.exe (PID: 660)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 660)
Manual execution by a user
- msiexec.exe (PID: 660)
Creates files or folders in the user directory
- msiexec.exe (PID: 660)
Reads the software policy settings
- msiexec.exe (PID: 660)
Checks supported languages
- msiexec.exe (PID: 2096)
Reads the computer name
- msiexec.exe (PID: 2096)
Manages system restore points
- SrTasks.exe (PID: 732)
The sample compiled with english language support
- rundll32.exe (PID: 6108)
- rundll32.exe (PID: 2564)
- rundll32.exe (PID: 928)
- rundll32.exe (PID: 2288)
- msedgewebview2.exe (PID: 6136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:04 11:53:42 |
| ZipCRC: | 0x79aa3ea2 |
| ZipCompressedSize: | 2736641 |
| ZipUncompressedSize: | 2994176 |
| ZipFileName: | MsEdge.msi |
Total processes
184
Monitored processes
47
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Desktop\MsEdge.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageMonitoring.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "TaskKill.exe" /f /im AteraAgent.exe | C:\Windows\SysWOW64\taskkill.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | rundll32.exe "C:\WINDOWS\Installer\MSI466E.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1132171 10 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.ShouldContinueInstallation | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "C:\Program Files (x86)\MsEdge\MsEdge\msedgewebview2.exe" /i /IntegratorLogin="otavioalveseventos@gmail.com" /CompanyId="3" /IntegratorLoginUI="" /CompanyIdUI="" /FolderId="" /AccountId="001Q300000O07oVIAR" /AgentId="d110279f-41ab-4dfe-833f-2fa176154b39" | C:\Program Files (x86)\MsEdge\MsEdge\msedgewebview2.exe | msiexec.exe | ||||||||||||
User: admin Company: MsEdgeNetworks Ltd. Integrity Level: MEDIUM Description: msedgewebview2 Exit code: 0 Version: 1.8.7.2 Modules
| |||||||||||||||
Total events
50 121
Read events
49 721
Write events
375
Delete events
25
Modification events
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\8yhY.zip | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF57010000480000001705000031020000 | |||
| (PID) Process: | (6184) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
65
Suspicious files
56
Text files
31
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2096 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 660 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:E9AD130935D9E3EF0C6D13682836CD97 | SHA256:E0F5878CCFC2785084FBC02238A5F31E9C6E88358040E184BF00DAD1DDD05F52 | |||
| 2096 | msiexec.exe | C:\Windows\Installer\MSI3CF6.tmp | executable | |
MD5:88D29734F37BDCFFD202EAFCDD082F9D | SHA256:87C97269E2B68898BE87B884CD6A21880E6F15336B1194713E12A2DB45F1DCCF | |||
| 2564 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3CF6.tmp-\Newtonsoft.Json.dll | executable | |
MD5:715A1FBEE4665E99E859EDA667FE8034 | SHA256:C5C83BBC1741BE6FF4C490C0AEE34C162945423EC577C646538B2D21CE13199E | |||
| 2564 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3CF6.tmp-\AlphaControlAgentInstallation.dll | executable | |
MD5:AA1B9C5C685173FAD2DABEBEB3171F01 | SHA256:E44A6582CD3F84F4255D3C230E0A2C284E0CFFA0CA5E62E4D749E089555494C7 | |||
| 2096 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:F8B8387A1CC48C4D909FD5870B6C4036 | SHA256:50667A65343456941BADAF58EDC678CEDC6DF37CADF2505C7536899824C4AD4D | |||
| 2564 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3CF6.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
| 2096 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{24456122-32fa-4bd5-9558-f88ac93d7d5a}_OnDiskSnapshotProp | binary | |
MD5:F8B8387A1CC48C4D909FD5870B6C4036 | SHA256:50667A65343456941BADAF58EDC678CEDC6DF37CADF2505C7536899824C4AD4D | |||
| 2564 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3CF6.tmp-\CustomAction.config | xml | |
MD5:BC17E956CDE8DD5425F2B2A68ED919F8 | SHA256:E4FF538599C2D8E898D7F90CCF74081192D5AFA8040E6B6C180F3AA0F46AD2C5 | |||
| 2564 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3CF6.tmp-\System.Management.dll | executable | |
MD5:878E361C41C05C0519BFC72C7D6E141C | SHA256:24DE61B5CAB2E3495FE8D817FB6E80094662846F976CF38997987270F8BBAE40 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
51
DNS requests
27
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
660 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
660 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
660 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6712 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6108 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
2084 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
4528 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6136 | msedgewebview2.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\MsEdge\MsEdge\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|