| File name: | 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f |
| Full analysis: | https://app.any.run/tasks/68c573ba-bea2-4694-ae0f-05e79a93d7e9 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 11:25:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 1FCB02D41942072784B783BBBA7CE04A |
| SHA1: | 19D455644F52F420BF86992C52DB41BC4F7E417D |
| SHA256: | 971D4A9B031A721FE60AC30C7C8466F0A13AE6039A1F73886C0BC37D13E3128F |
| SSDEEP: | 98304:lxL5qjsE50+h+J2tFaAQQOX4iwmHDV/8nqA3zWh/s2OHdRyfe0cC9d+APP18YYB9:w1hn9 |
MALICIOUS
Executing a file with an untrusted certificate
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 7148)
SUSPICIOUS
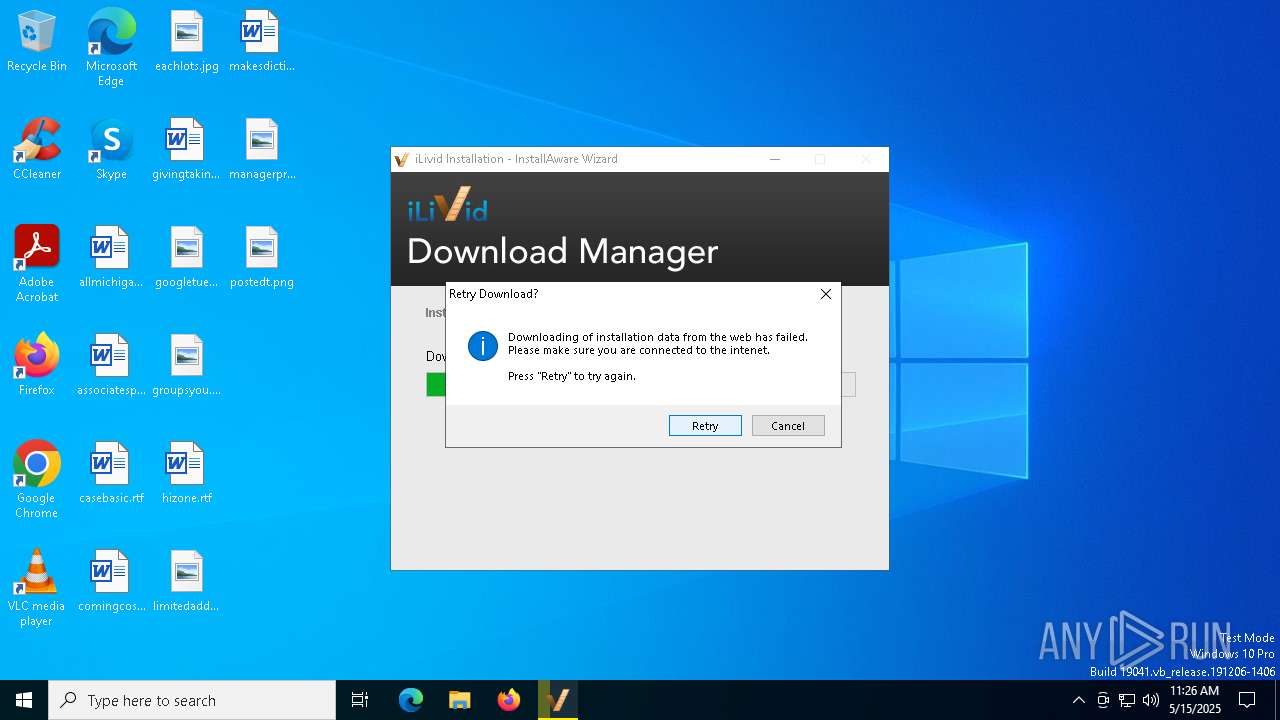
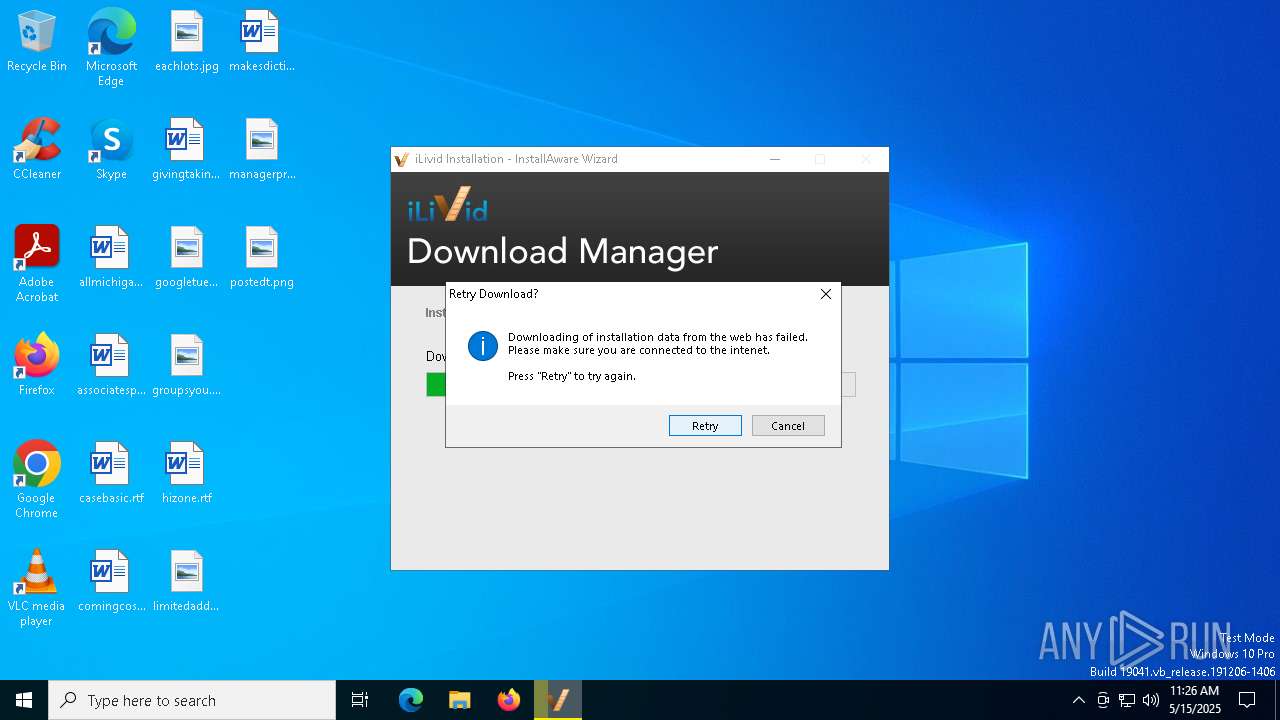
Executable content was dropped or overwritten
- iLividSetupV1.exe (PID: 5280)
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
Drops 7-zip archiver for unpacking
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
Reads security settings of Internet Explorer
- iLividSetupV1.exe (PID: 5280)
INFO
The sample compiled with english language support
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
Checks proxy server information
- iLividSetupV1.exe (PID: 5280)
Reads the software policy settings
- slui.exe (PID: 4560)
Compiled with Borland Delphi (YARA)
- iLividSetupV1.exe (PID: 5280)
Reads the computer name
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
- iLividSetupV1.exe (PID: 5280)
Checks supported languages
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
- iLividSetupV1.exe (PID: 5280)
Create files in a temporary directory
- 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe (PID: 2692)
- iLividSetupV1.exe (PID: 5280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:04:15 20:43:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 98816 |
| InitializedDataSize: | 121856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x12a70 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.92.871.32734 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | This installation was built with InstallAware: http://www.installaware.com |
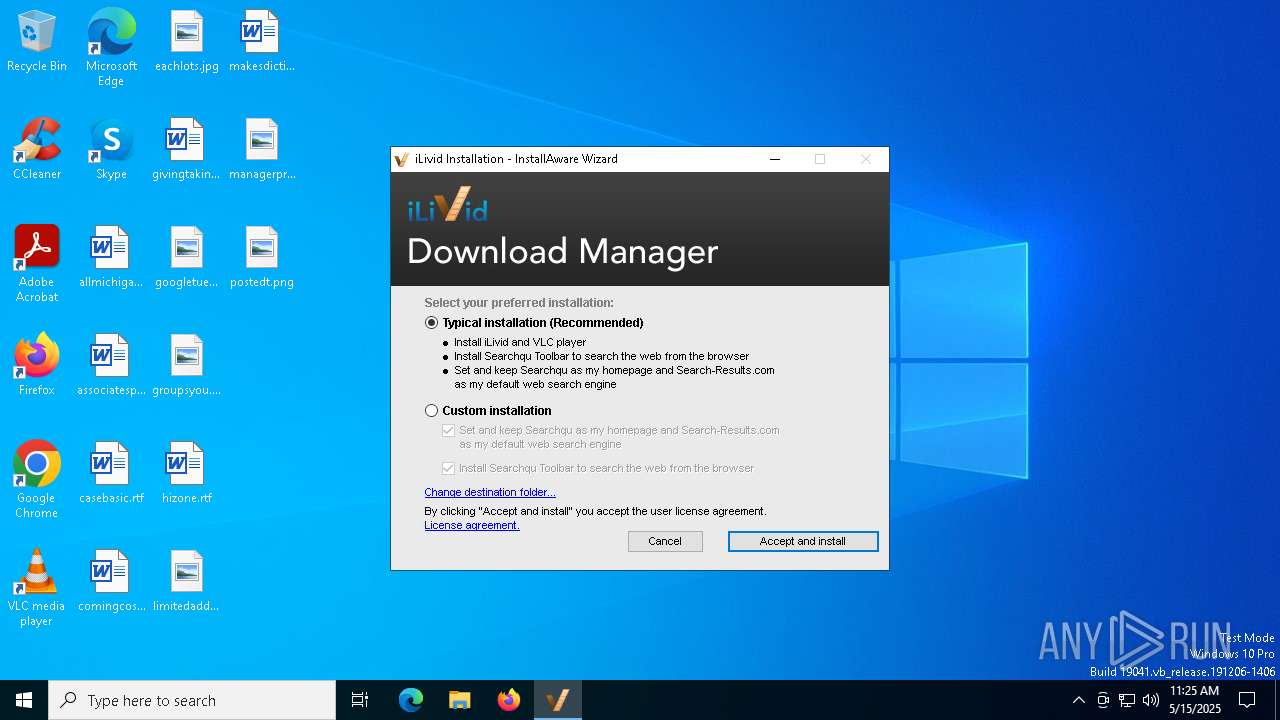
| CompanyName: | Bandoo Media Inc. |
| FileDescription: | iLivid Installation |
| FileVersion: | 1.92.0.117387 |
| LegalCopyright: | All rights reserved |
Total processes
133
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2692 | "C:\Users\admin\AppData\Local\Temp\971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe" | C:\Users\admin\AppData\Local\Temp\971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | explorer.exe | ||||||||||||
User: admin Company: Bandoo Media Inc. Integrity Level: HIGH Description: iLivid Installation Version: 1.92.0.117387 Modules
| |||||||||||||||
| 4560 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5280 | .\iLividSetupV1.exe /m="C:\Users\admin\AppData\Local\Temp\971D4A~1.EXE" /k="" | C:\Users\admin\AppData\Local\Temp\miaB817.tmp\iLividSetupV1.exe | 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | ||||||||||||
User: admin Company: Bandoo Media Inc. Integrity Level: HIGH Description: iLivid Installation Version: 1.92.0.117387 Modules
| |||||||||||||||
| 6512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\Users\admin\AppData\Local\Temp\971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe" | C:\Users\admin\AppData\Local\Temp\971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | — | explorer.exe | |||||||||||
User: admin Company: Bandoo Media Inc. Integrity Level: MEDIUM Description: iLivid Installation Exit code: 3221226540 Version: 1.92.0.117387 Modules
| |||||||||||||||
Total events
1 154
Read events
1 132
Write events
20
Delete events
2
Modification events
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\iLividSetupV1.exe |
| Operation: | write | Name: | IsHostApp |
Value: | |||
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | 8D15E1B2 |
Value: | |||
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | 8D15E1B2 |
Value: | |||
| (PID) Process: | (2692) 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe |
| Operation: | write | Name: | IsHostApp |
Value: | |||
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ReceiveTimeout |
Value: 10000 | |||
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5280) iLividSetupV1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
8
Suspicious files
11
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2692 | 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | C:\Users\admin\AppData\Local\Temp\miaB817.tmp\data\iLividSetupV1.msi | binary | |
MD5:A2D691886D299E9C9316220D43EA399E | SHA256:994D7EA227648AB91A50D5B579513B97417CB94A51413648CB29711A6F2F823D | |||
| 2692 | 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | C:\Users\admin\AppData\Local\Temp\miaB817.tmp\data\OFFLINE\mIDEFunc.dll\mEXEFunc.dll | executable | |
MD5:F184BE47FF281B17D8AC5C702F4CA896 | SHA256:D2446D97172A0199DDC532D901B1A814B2B55F3B243998D2725754610B975312 | |||
| 2692 | 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | C:\Users\admin\AppData\Local\Temp\miaB817.tmp\data\OFFLINE\mDown.dll\mDownExec.dll | executable | |
MD5:B7F0D95E4E97D518496FD9D90A4E0786 | SHA256:51512BA85758FB12CFD9A1850C9BEB9151FD41C5997F07F74D174CC4C787C876 | |||
| 2692 | 971d4a9b031a721fe60ac30c7c8466f0a13ae6039a1f73886c0bc37d13e3128f.exe | C:\Users\admin\AppData\Local\Temp\miaB817.tmp\iLividSetupV1.exe | executable | |
MD5:9C0D16DA08434A1BA63E274C0A54328D | SHA256:0301AA6B53752FD66364FA3FAA19BA3F8C0D9289D27394884025EAE739343ABB | |||
| 5280 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\mia1\progress.dfm | binary | |
MD5:B8AE31A7FD1A1660B4EA1E46BD862422 | SHA256:A23B2AD6564C60D1C23C5AB4F919D5D7DFF504ACF0CB8A87487D9F6BBB563916 | |||
| 5280 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\mia.tmp | text | |
MD5:DF2B9BD3FCE2B49E1560A55E5EE31669 | SHA256:60D3EBB61FC3BBFF74E1F50ED121FDBE90695FA60115A2AA104351A66215D99F | |||
| 5280 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\mia1\ftalk.ico | image | |
MD5:CC902FD067FE0A0686352300711E91E8 | SHA256:C018C4AE7E23C12C477CBAD98C4A8DFD8499B6ABE10F4CB77E42F0867C260A14 | |||
| 5280 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\mia1\unfinish.dfm | binary | |
MD5:CF296159B2365D878F043EB55C166168 | SHA256:C015A7E5EF11F373FC613B86B5325FB32ADC5578CCB28B647A6158E32C3F7E18 | |||
| 5280 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\mia1\license.txt | text | |
MD5:ADC52E4DF9473983D7C1BBE0F67B2891 | SHA256:46AEFAA17E63EF0FBC4EA1ED1C405BD8D55CE1CC107151404AD79FD78838CD1E | |||
| 5280 | iLividSetupV1.exe | C:\Users\admin\AppData\Local\Temp\mia1\progress.dfm.miaf | text | |
MD5:58F9CEE2A23ACD0F2A6DF937353CD012 | SHA256:8C39111E0E3DE96E65D1A610863DE42813A55AB21EBE9A780DFC4960D07CF068 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6652 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6652 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
download.cdn.ilivid.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |