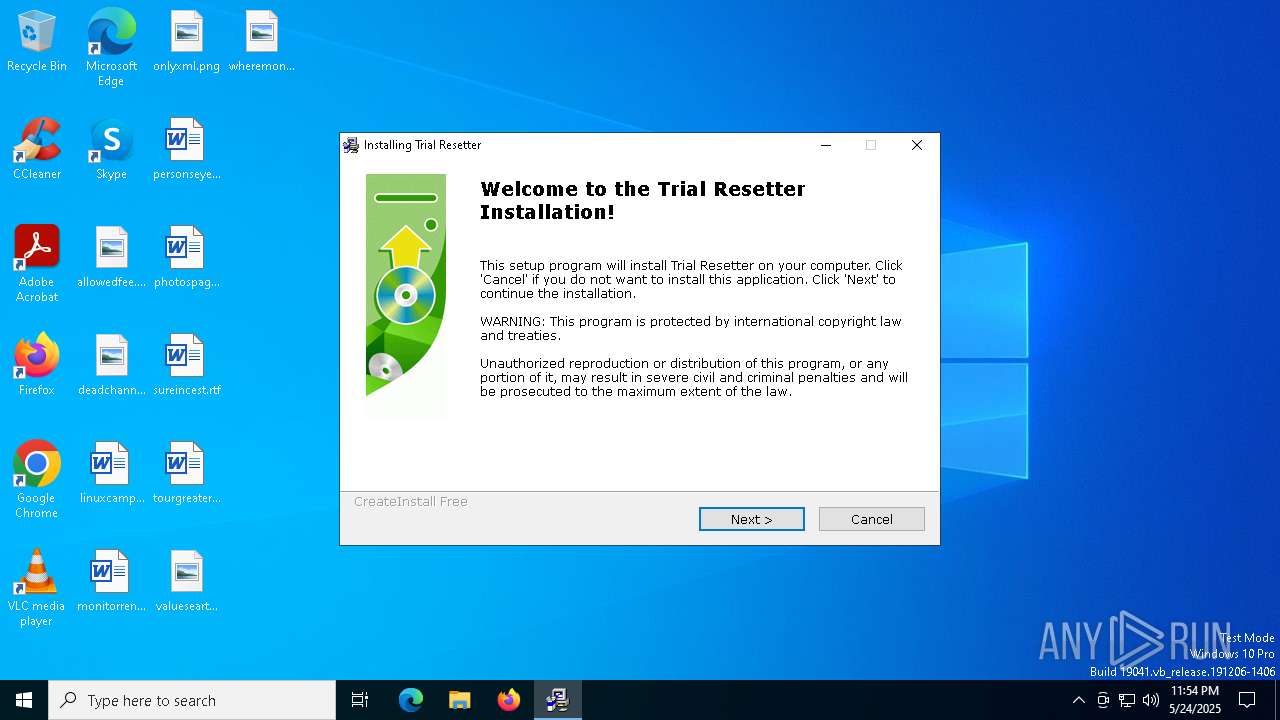
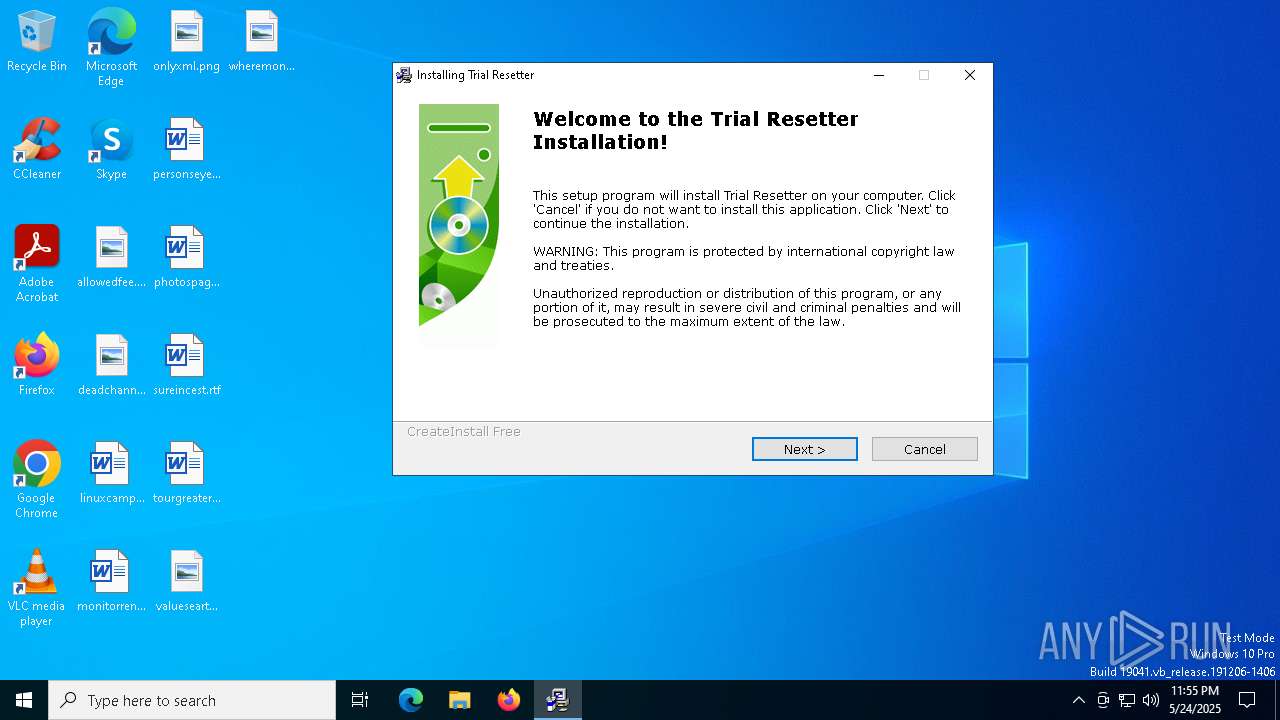
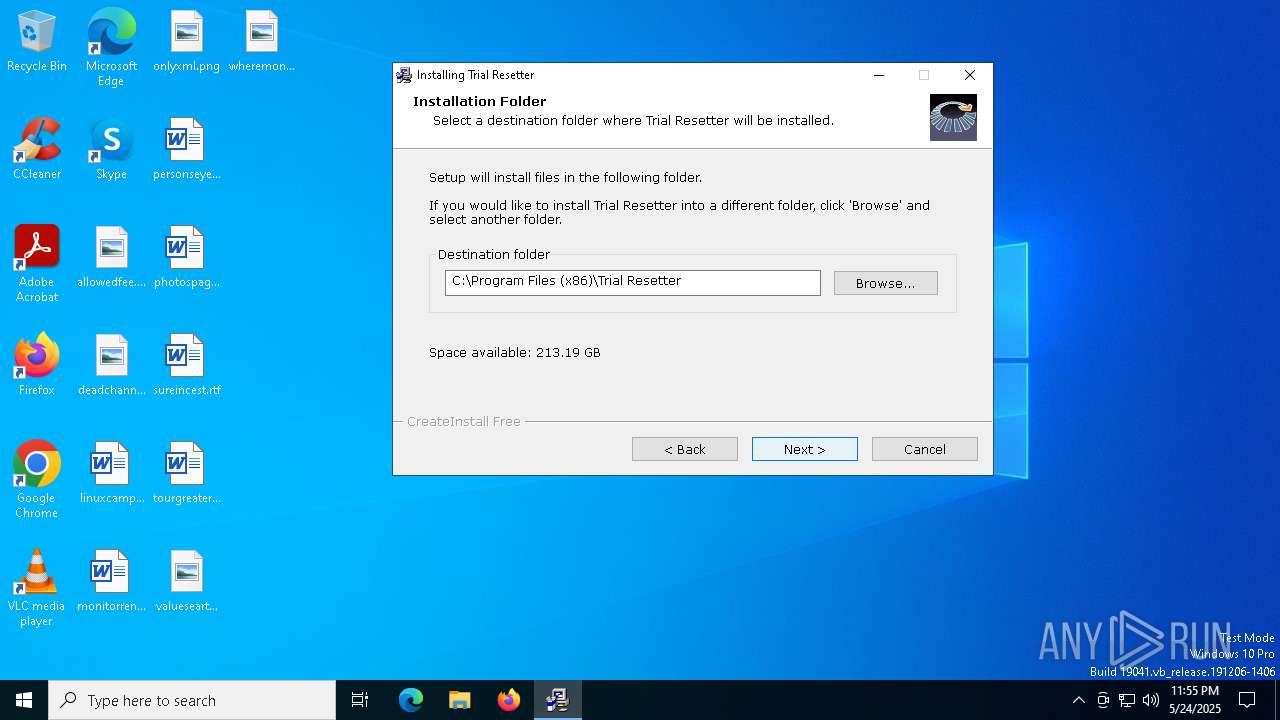
| File name: | Trial Resetter.exe |
| Full analysis: | https://app.any.run/tasks/30a70369-e074-409f-a185-02885bbc9750 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 23:54:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | A2878E7C584B11C585795BE25029F0CA |
| SHA1: | F1483D12A4A3FA84ACCDE0F52EC20BEF6AE39088 |
| SHA256: | 96EAA8A3ADFEE87B17665AB2DF07F2EC8DF99B66F546019D7B478EB089D73217 |
| SSDEEP: | 3072:5zlSRC9Z/eVqzHFyo8JMGiO7ZpYXr/vCow+:RlSRC9ZeozFyo8JM3O7LYXr/6ow+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Trial Resetter.exe (PID: 1228)
There is functionality for taking screenshot (YARA)
- Trial Resetter.exe (PID: 1228)
Starts CMD.EXE for commands execution
- Trial Resetter.exe (PID: 1228)
Executing commands from a ".bat" file
- Trial Resetter.exe (PID: 1228)
Searches for installed software
- Trial Resetter.exe (PID: 1228)
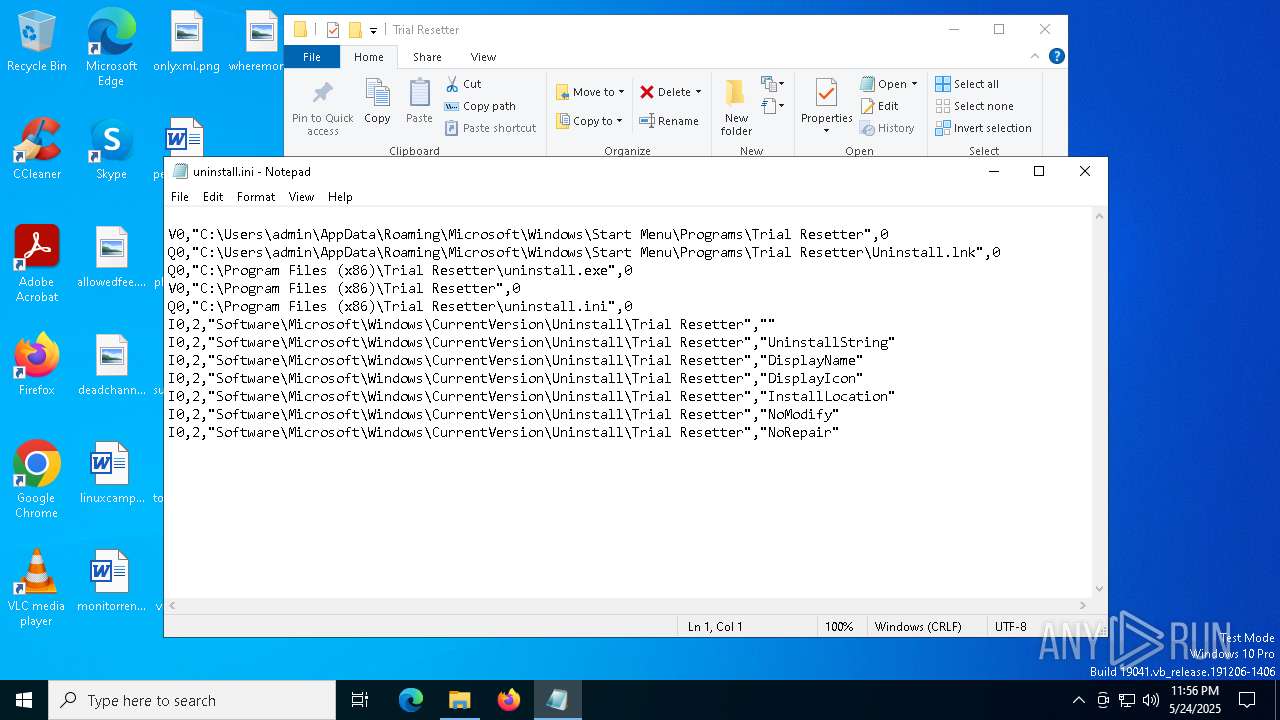
Creates a software uninstall entry
- Trial Resetter.exe (PID: 1228)
INFO
Checks supported languages
- Trial Resetter.exe (PID: 1228)
Create files in a temporary directory
- Trial Resetter.exe (PID: 1228)
Reads the computer name
- Trial Resetter.exe (PID: 1228)
The sample compiled with english language support
- Trial Resetter.exe (PID: 1228)
Creates files in the program directory
- Trial Resetter.exe (PID: 1228)
Creates files or folders in the user directory
- Trial Resetter.exe (PID: 1228)
Reads the software policy settings
- slui.exe (PID: 6184)
- slui.exe (PID: 2852)
Manual execution by a user
- notepad.exe (PID: 1244)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1244)
Checks proxy server information
- slui.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:01:31 17:44:13+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 4096 |
| InitializedDataSize: | 110592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d20 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
145
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 1228 | "C:\Users\admin\AppData\Local\Temp\Trial Resetter.exe" | C:\Users\admin\AppData\Local\Temp\Trial Resetter.exe | explorer.exe | |
User: admin Integrity Level: HIGH Exit code: 0 | ||||
| 1244 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Program Files (x86)\Trial Resetter\uninstall.ini | C:\Windows\System32\notepad.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2432 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | ||||
| 2852 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 4040 | "C:\Users\admin\AppData\Local\Temp\Trial Resetter.exe" | C:\Users\admin\AppData\Local\Temp\Trial Resetter.exe | — | explorer.exe |
User: admin Integrity Level: MEDIUM Exit code: 3221226540 | ||||
| 6032 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 6184 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 6768 | cmd.exe /c deldll.bat | C:\Windows\SysWOW64\cmd.exe | — | Trial Resetter.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
6
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\gentee23\4default - 2.bmp | binary | |
MD5:5CDF0741BEAD2AFDC7F381D82D43A1B3 | SHA256:7294B02EEBBE31D7A01026883FA8A95D94F47AB408F611E9E4A7421BEF2673C8 | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\genteert.dll | executable | |
MD5:6CE814FD1AD7AE07A9E462C26B3A0F69 | SHA256:54C0DA1735BB1CB02B60C321DE938488345F8D1D26BF389C8CB2ACAD5D01B831 | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\gentee23\guig.dll | executable | |
MD5:D3F8C0334C19198A109E44D074DAC5FD | SHA256:005C251C21D6A5BA1C3281E7B9F3B4F684D007E0C3486B34A545BB370D8420AA | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\gentee23\setup_temp.gea | binary | |
MD5:496D233BE39A91FAC471E7646CBA5FF8 | SHA256:B5A63681A4E78B4795D60DEC9F0A69C038BF89DE2CB35D041E00D02D582C2FD3 | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\~DF54F31EEAE80888B2.TMP | binary | |
MD5:827EE7F5A065AF5D6271D74C287E423F | SHA256:04248AE8E171A8BCC39372C99A6EC0FDA2ABC4F30D77716AF5D00FFA43FDECE5 | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\deldll.bat | text | |
MD5:EA190EF9B139757A890CD48BDD44B0EE | SHA256:9131DE0FCAAF968896AF9D58B6F37B4AA443455BB97C97BC142F295CEE577BC4 | |||
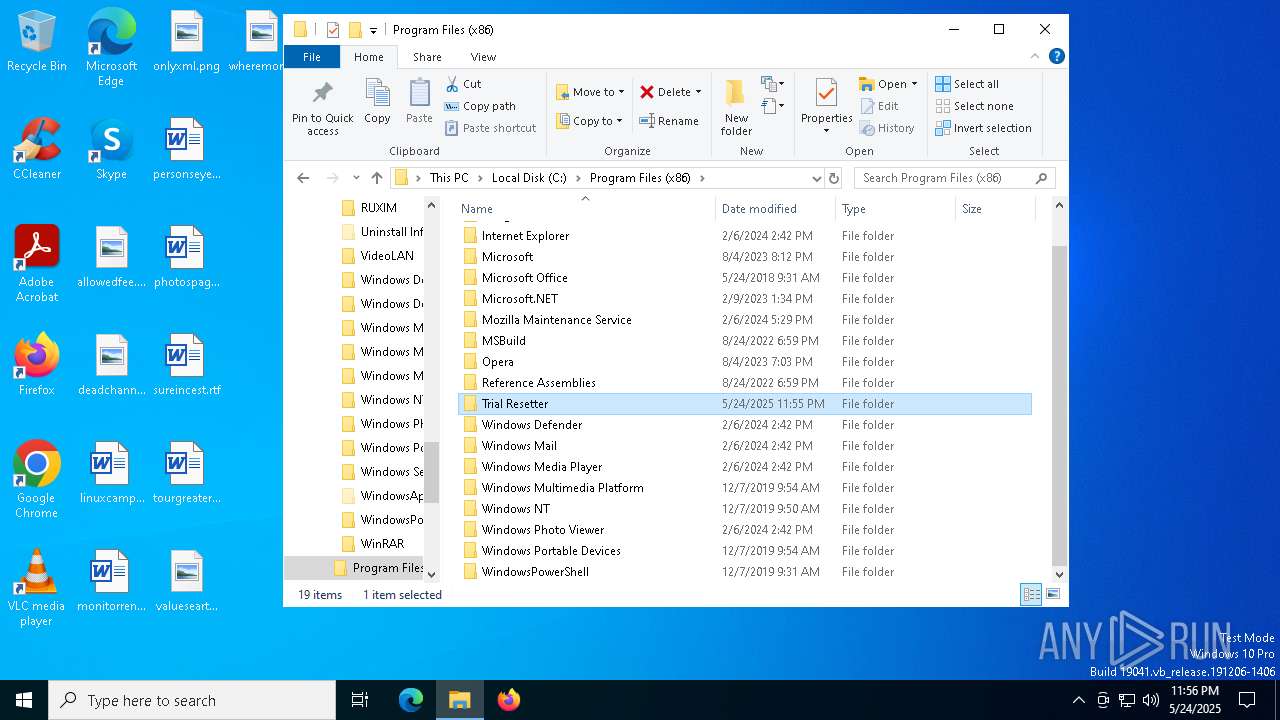
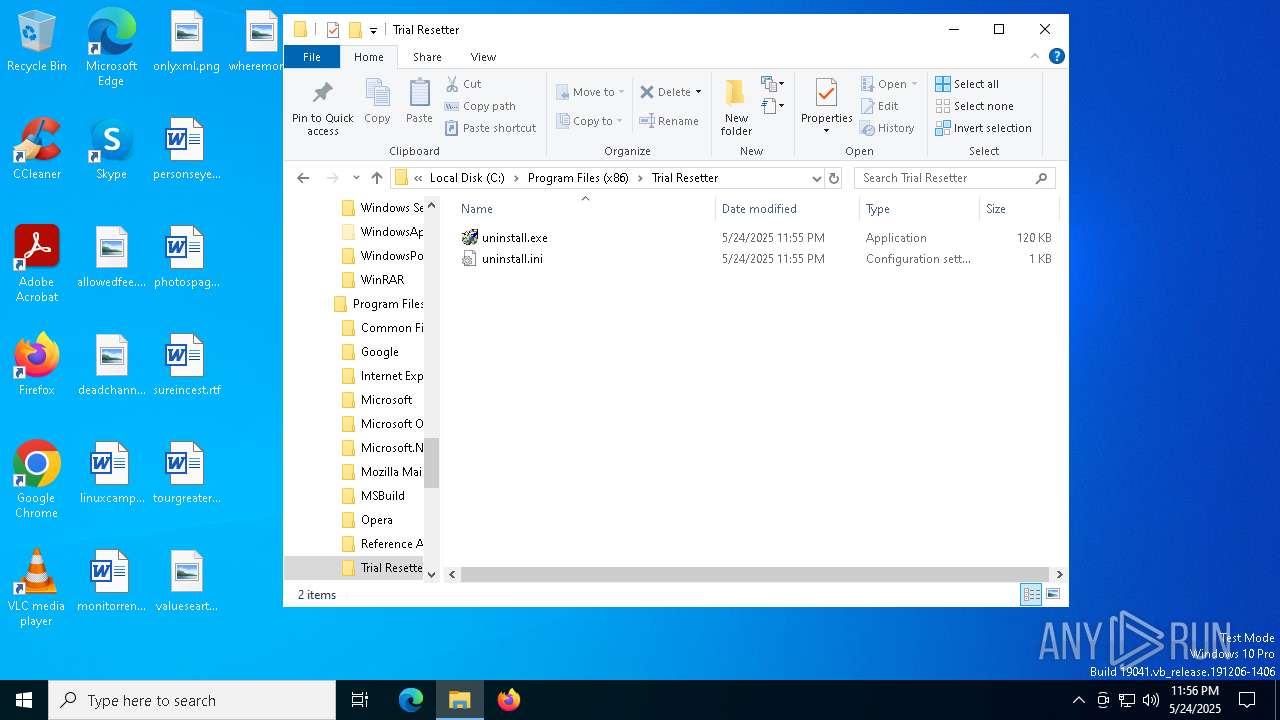
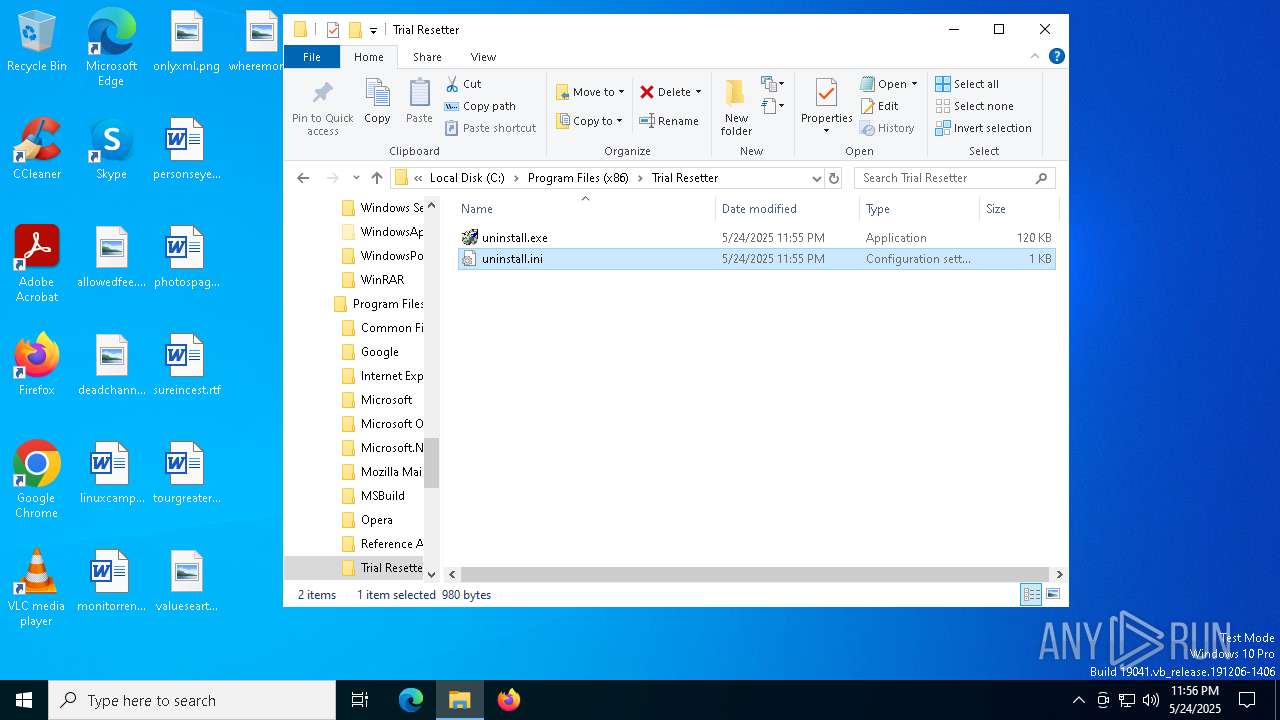
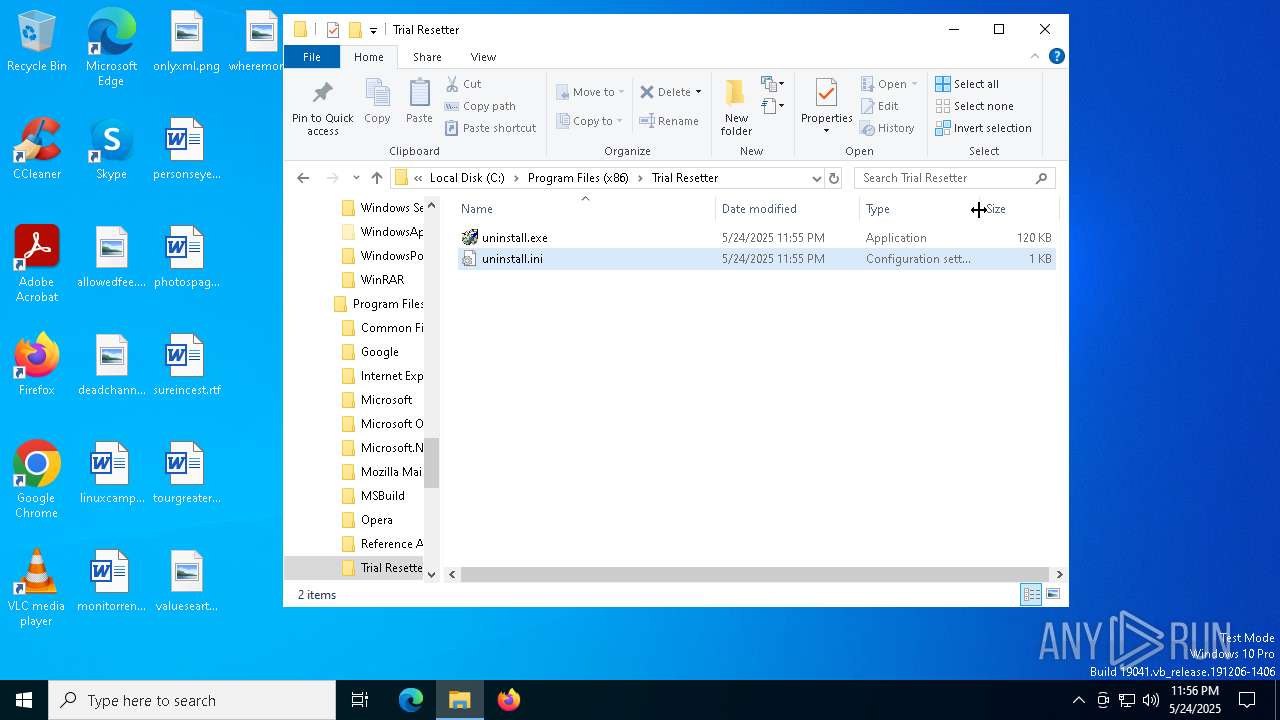
| 1228 | Trial Resetter.exe | C:\Program Files (x86)\Trial Resetter\uninstall.exe | executable | |
MD5:65AB1E0A17FF76C160EC97042EC3F958 | SHA256:AC9AD2D96DFE7223373F929734BF0BE1D1A6F80ED51CD0DA5A4492E228182240 | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\~DFD67DEB247228894D.TMP | binary | |
MD5:06BB5DA0F58620FCAC1D9B79BFB1A94B | SHA256:3557ED611D0663690AD8A9A3A5AE8269C1CAA8FFDF3BFCB14D7D0A9F3D8BD551 | |||
| 1228 | Trial Resetter.exe | C:\Program Files (x86)\Trial Resetter\uninstall.ini | text | |
MD5:6D7C5A0D5A6C0C8A405A9D8A552FB25E | SHA256:5CA52270A151FADBB668B62889DFE488E524449F8C2EFEB1AF7D9548D89DF9F2 | |||
| 1228 | Trial Resetter.exe | C:\Users\admin\AppData\Local\Temp\gentee23\2install - 1.bmp | binary | |
MD5:E168634D6C44995C14608F16C2E28693 | SHA256:06263008AB7AB756D1254CE744B389F71B0DFFB186EBFA8BB0D2603271E9C6DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5588 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5588 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2420 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5588 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5588 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |