| URL: | https://bazaar.abuse.ch/download/78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6/ |
| Full analysis: | https://app.any.run/tasks/fb401d8d-890a-407b-99c2-1340a249b734 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 00:01:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 64AAC62E0B36711385ED0EECF0D0DD32 |
| SHA1: | 8A54392D57690176917B7C2752D9495D840357F9 |
| SHA256: | 96E75E407CDCBBFE29D6BD5FA4BC7AD7714046A862B6D83B60D50D4452E92452 |
| SSDEEP: | 3:N8N0uDWB4SP5SLABwRQuEBHQSWptoKn:23GfB727oHQljoK |
MALICIOUS
Changes Windows Defender settings
- cmd.exe (PID: 7552)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 7552)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 7552)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
- 7z2201.exe (PID: 8440)
The executable file from the user directory is run by the CMD process
- 7z2201.exe (PID: 8440)
- VC_redist.x86.exe (PID: 8212)
- wzone.exe (PID: 812)
- Windows Driver Foundation (WDF).exe (PID: 1196)
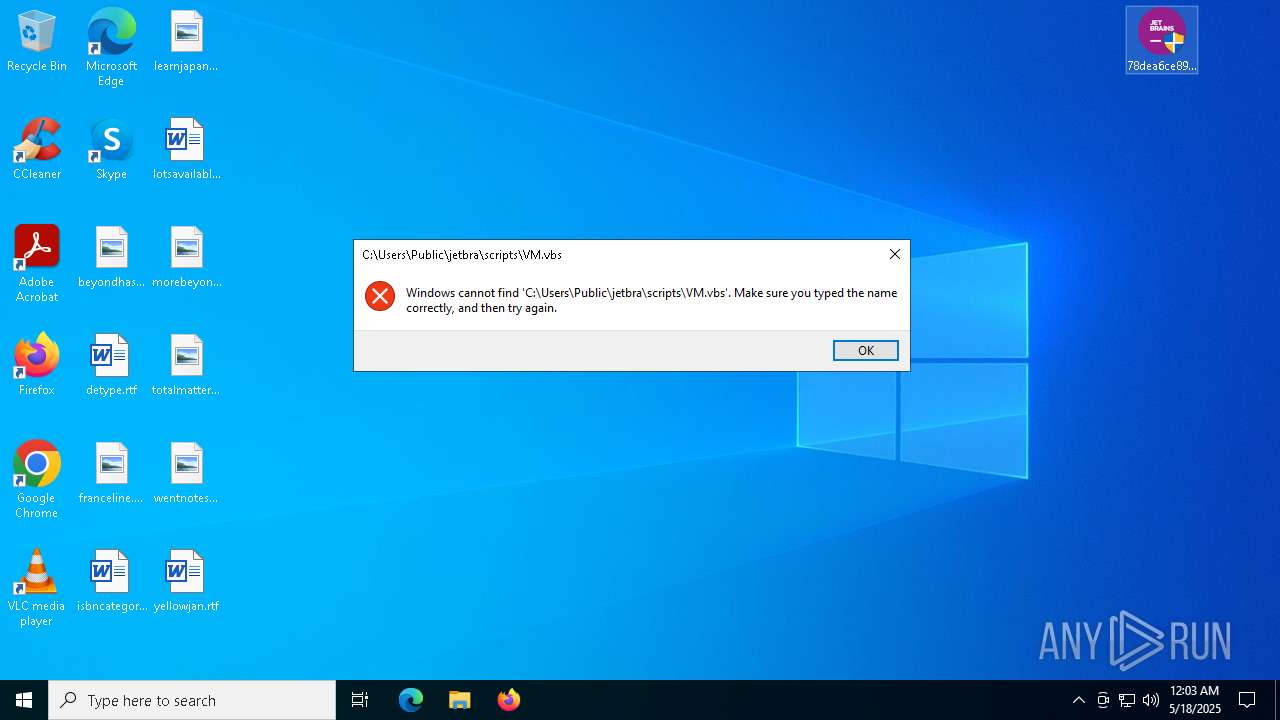
Executing commands from a ".bat" file
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
- powershell.exe (PID: 5244)
Executable content was dropped or overwritten
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
- 7z2201.exe (PID: 8440)
- 7z.exe (PID: 5392)
- VC_redist.x86.exe (PID: 8212)
- VC_redist.x86.exe (PID: 7476)
- VC_redist.x86.exe (PID: 8624)
- VC_redist.x86.exe (PID: 7404)
- VC_redist.x86.exe (PID: 7392)
Starts CMD.EXE for commands execution
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
- cmd.exe (PID: 516)
- powershell.exe (PID: 5244)
- cmd.exe (PID: 7552)
- wzone.exe (PID: 812)
Uses WMIC.EXE
- cmd.exe (PID: 8496)
Creates a software uninstall entry
- 7z2201.exe (PID: 8440)
Application launched itself
- cmd.exe (PID: 516)
- cmd.exe (PID: 7552)
- VC_redist.x86.exe (PID: 8492)
- VC_redist.x86.exe (PID: 8624)
- Windows Driver Foundation (WDF).exe (PID: 1196)
Creates/Modifies COM task schedule object
- 7z2201.exe (PID: 8440)
Get information on the list of running processes
- cmd.exe (PID: 8632)
- cmd.exe (PID: 8652)
- cmd.exe (PID: 8696)
- cmd.exe (PID: 516)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 516)
- cmd.exe (PID: 7552)
The process verifies whether the antivirus software is installed
- cmd.exe (PID: 516)
Checks for external IP
- svchost.exe (PID: 2196)
- curl.exe (PID: 8864)
- curl.exe (PID: 8284)
Hides command output
- cmd.exe (PID: 684)
- cmd.exe (PID: 7144)
- cmd.exe (PID: 7748)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 5864)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 684)
- cmd.exe (PID: 5020)
- cmd.exe (PID: 5864)
- cmd.exe (PID: 7144)
- cmd.exe (PID: 7748)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 516)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 516)
- cmd.exe (PID: 7552)
Execution of CURL command
- cmd.exe (PID: 516)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 7552)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7552)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7552)
Process drops legitimate windows executable
- 7z.exe (PID: 5392)
- VC_redist.x86.exe (PID: 8212)
- VC_redist.x86.exe (PID: 7404)
- VC_redist.x86.exe (PID: 7476)
- msiexec.exe (PID: 444)
- VC_redist.x86.exe (PID: 7392)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7552)
Starts a Microsoft application from unusual location
- VC_redist.x86.exe (PID: 7404)
- VC_redist.x86.exe (PID: 7476)
Starts itself from another location
- VC_redist.x86.exe (PID: 7404)
Executes as Windows Service
- VSSVC.exe (PID: 7268)
The process drops C-runtime libraries
- msiexec.exe (PID: 444)
Executing commands from ".cmd" file
- wzone.exe (PID: 812)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5936)
INFO
Application launched itself
- firefox.exe (PID: 5972)
- firefox.exe (PID: 5428)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8272)
- msiexec.exe (PID: 444)
Manual execution by a user
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 6080)
- WinRAR.exe (PID: 8272)
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
Checks supported languages
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
- 7z2201.exe (PID: 8440)
- curl.exe (PID: 8864)
- curl.exe (PID: 8792)
Reads the software policy settings
- slui.exe (PID: 8144)
The sample compiled with english language support
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
- 7z2201.exe (PID: 8440)
- 7z.exe (PID: 5392)
- VC_redist.x86.exe (PID: 8212)
- VC_redist.x86.exe (PID: 7404)
- msiexec.exe (PID: 444)
- VC_redist.x86.exe (PID: 8624)
- VC_redist.x86.exe (PID: 7476)
- VC_redist.x86.exe (PID: 7392)
Create files in a temporary directory
- 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe (PID: 7320)
The sample compiled with russian language support
- 7z2201.exe (PID: 8440)
Creates files in the program directory
- 7z2201.exe (PID: 8440)
Reads the computer name
- 7z2201.exe (PID: 8440)
- curl.exe (PID: 8864)
- curl.exe (PID: 8792)
Execution of CURL command
- cmd.exe (PID: 3268)
- cmd.exe (PID: 8796)
- cmd.exe (PID: 516)
- cmd.exe (PID: 7600)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 7552)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8540)
- WMIC.exe (PID: 8884)
Manages system restore points
- SrTasks.exe (PID: 8056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
238
Monitored processes
101
Malicious processes
7
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\8Y26W4EG.bat" "C:\Users\admin\Desktop\78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe" " | C:\Windows\System32\cmd.exe | — | 78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | reg query "HKEY_LOCAL_MACHINE\SYSTEM\HardwareConfig\Current" /v "SystemProductName" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /S /D /c" ( findstr /ilc:"Windows 7" 1>nul )" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | wmic os get caption | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | tasklist /fi "imagename eq ekrn.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Users\admin\AppData\Local\google\chrome\user data\wzone.exe" "C:\Users\admin\AppData\Local\google\chrome\user data\wtime.cmd" wlocale.cmd | C:\Users\admin\AppData\Local\Google\Chrome\User Data\wzone.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: wtime Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
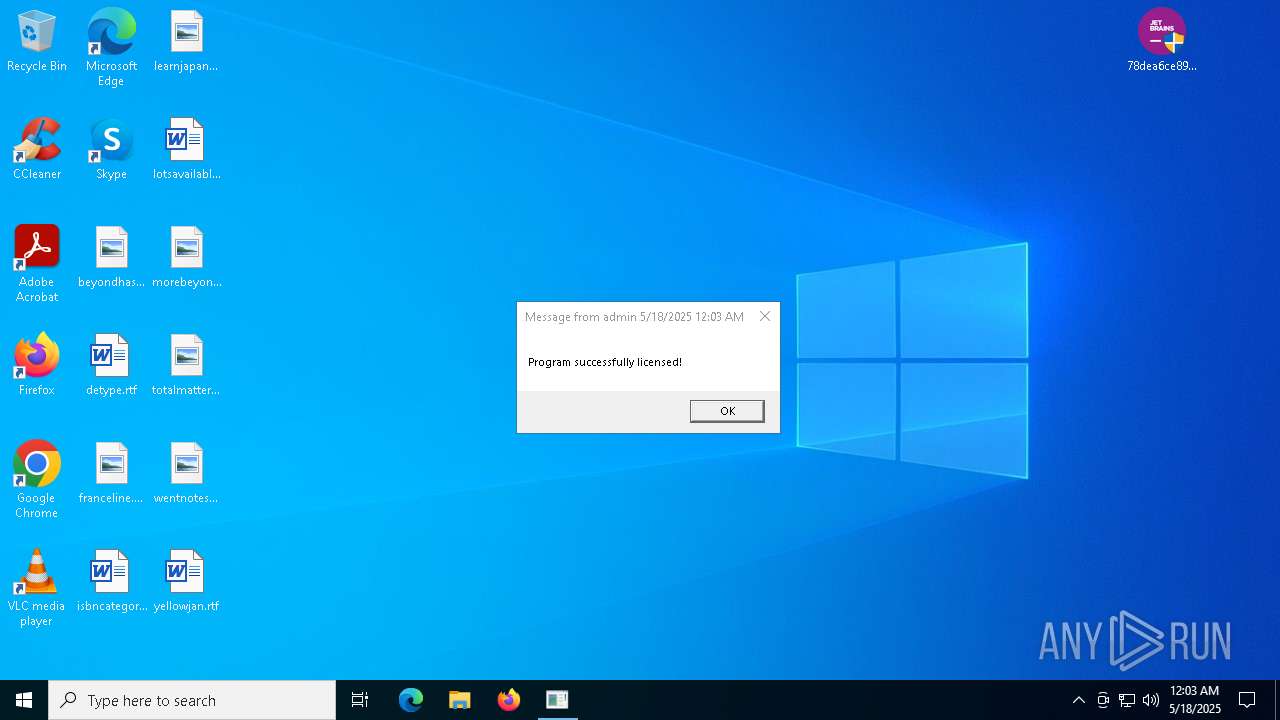
| 904 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo Program successfully licensed! " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | tasklist /fi "imagename eq QHActiveDefense.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\AppData\Local\google\chrome\user data\windows driver foundation (wdf).exe" --dhfghghfh | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Windows Driver Foundation (WDF).exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
78 801
Read events
77 896
Write events
642
Delete events
263
Modification events
| (PID) Process: | (5428) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\78dea6ce89d0ef782aaeddc45abbf492f6b272e8804d9f1528e3fea7aa81b6c6.zip | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
184
Suspicious files
296
Text files
264
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5428 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:5DE9EFB99CE63DD26C0700AC5E054AF4 | SHA256:A9AB32DCA7FE366314AF310C94E2922B87C371B05B9B53AF15008971ED9CBFD6 | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:56D853DF7F955D4685B00E15F1E953CE | SHA256:2C5D8C1471FDED7C16F3CB2CCCC6B2838765107B87ECF48682A180C472F20590 | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:D30F5B10F3D4B3992E4D666F622163F4 | SHA256:2585819A7401A308DA879FA416278E473CEA5F6D0D24C59F514C5A698C61D03A | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:D30F5B10F3D4B3992E4D666F622163F4 | SHA256:2585819A7401A308DA879FA416278E473CEA5F6D0D24C59F514C5A698C61D03A | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
146
DNS requests
154
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5428 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5428 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5428 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5428 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
5428 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5428 | firefox.exe | POST | 200 | 184.24.77.56:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5428 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5428 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5428 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
5428 | firefox.exe | 151.101.130.49:443 | bazaar.abuse.ch | FASTLY | US | whitelisted |
5428 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
5428 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
p2.shared.global.fastly.net |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |