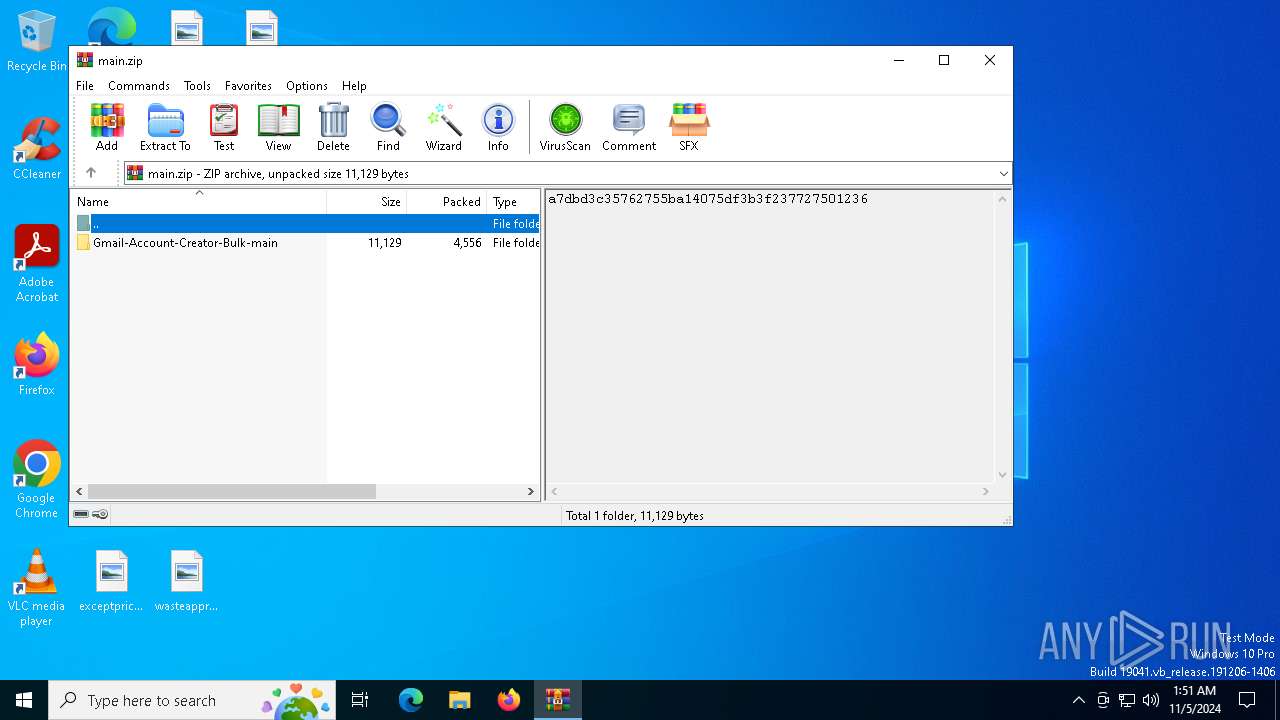
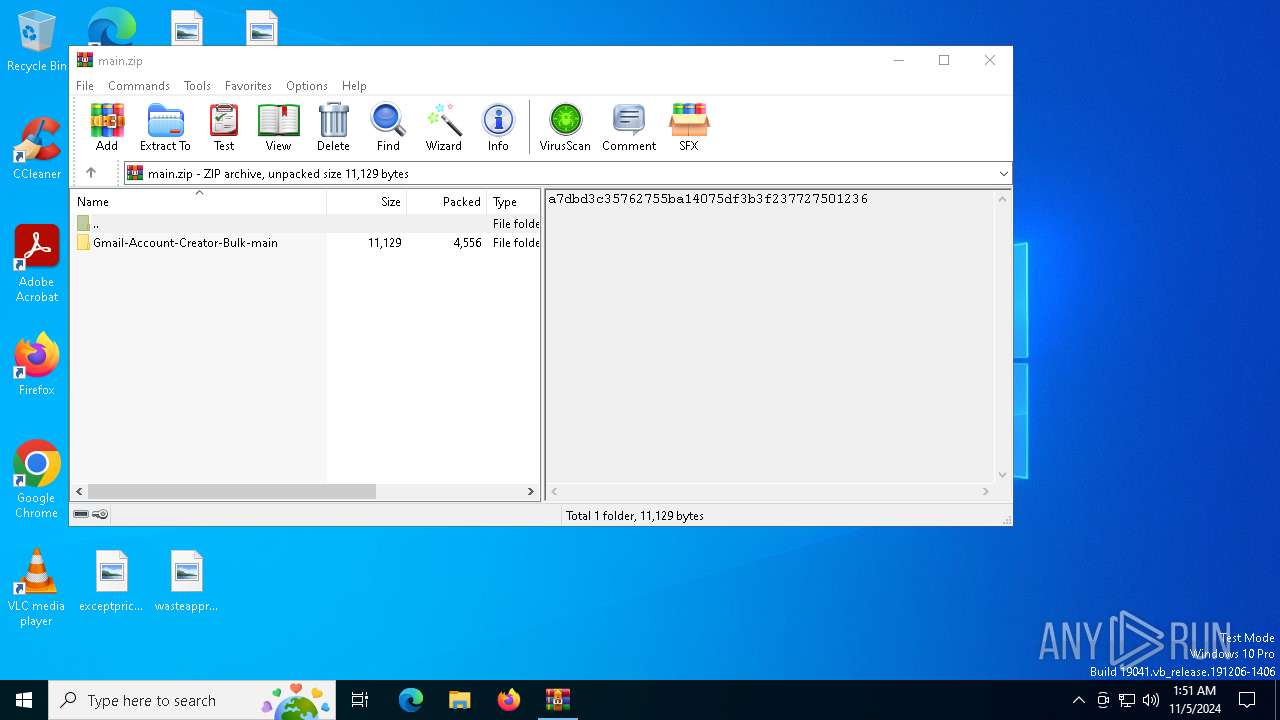
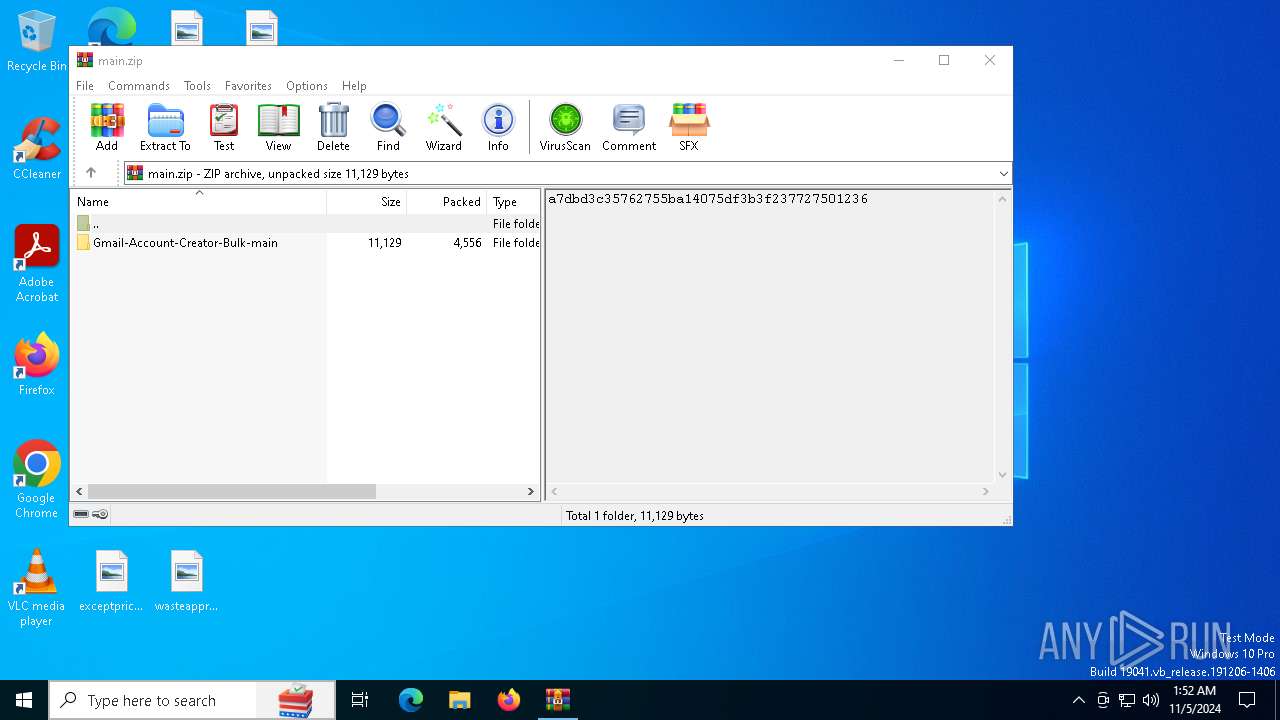
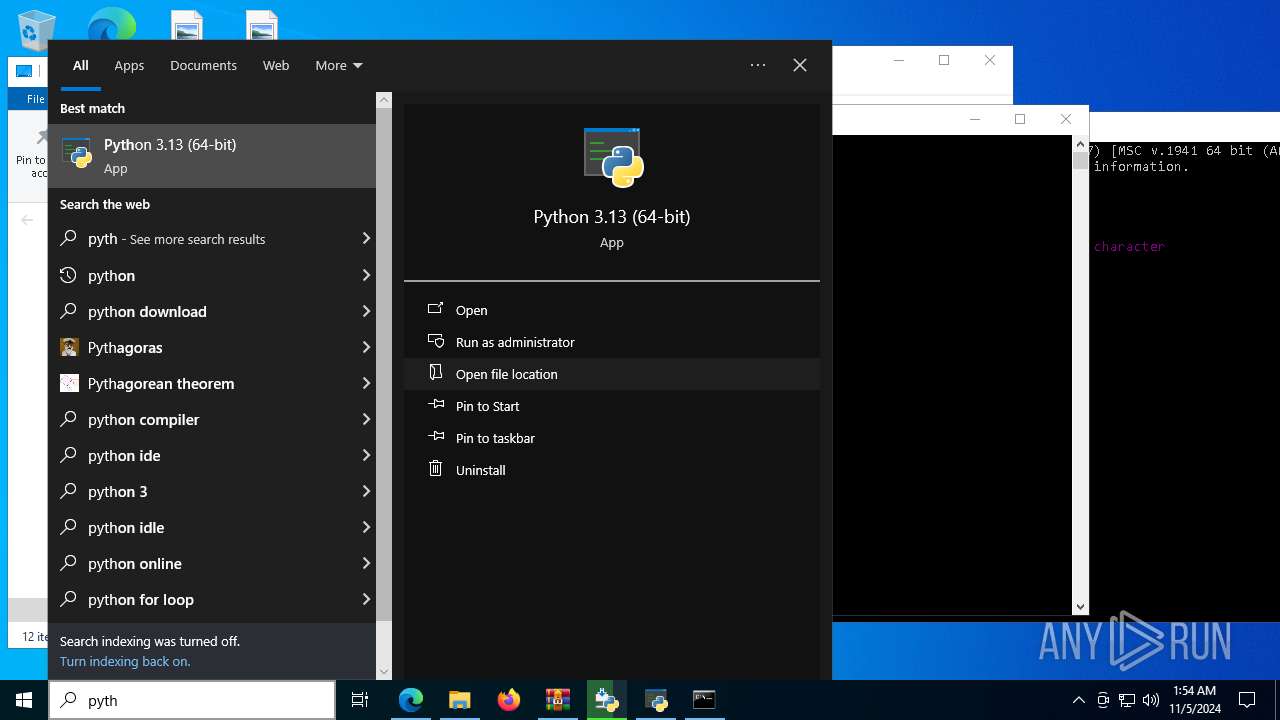
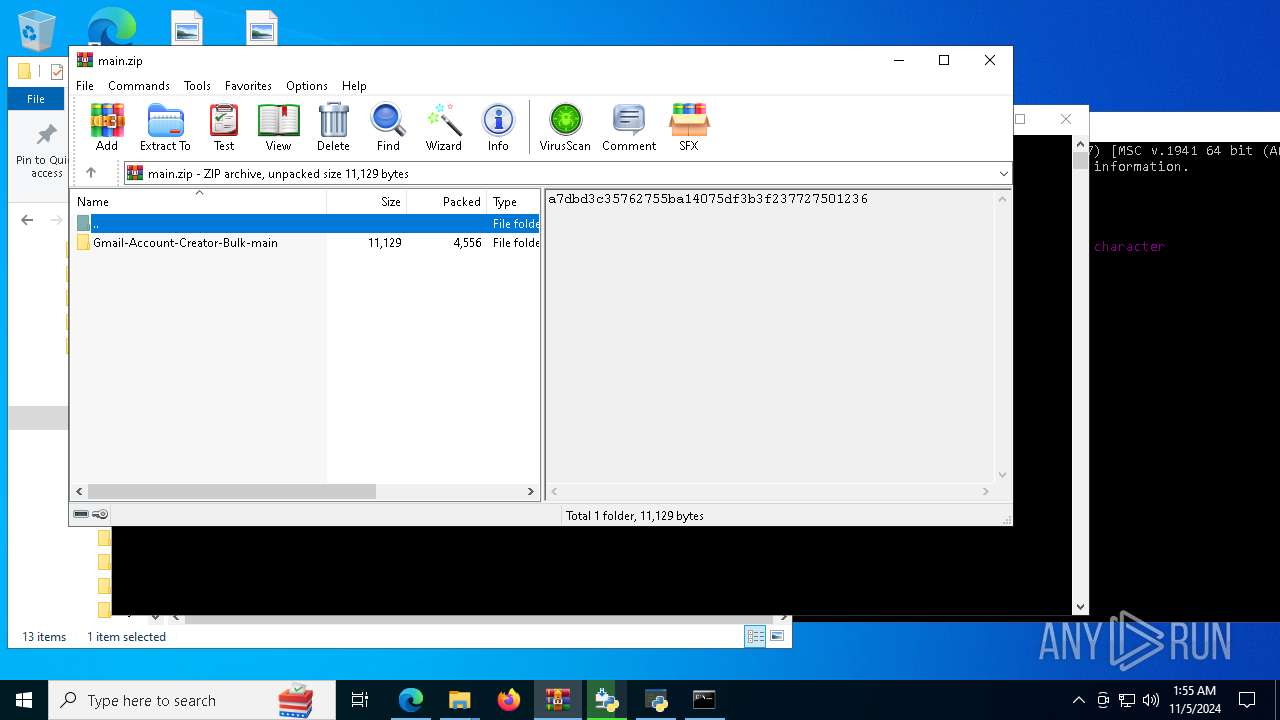
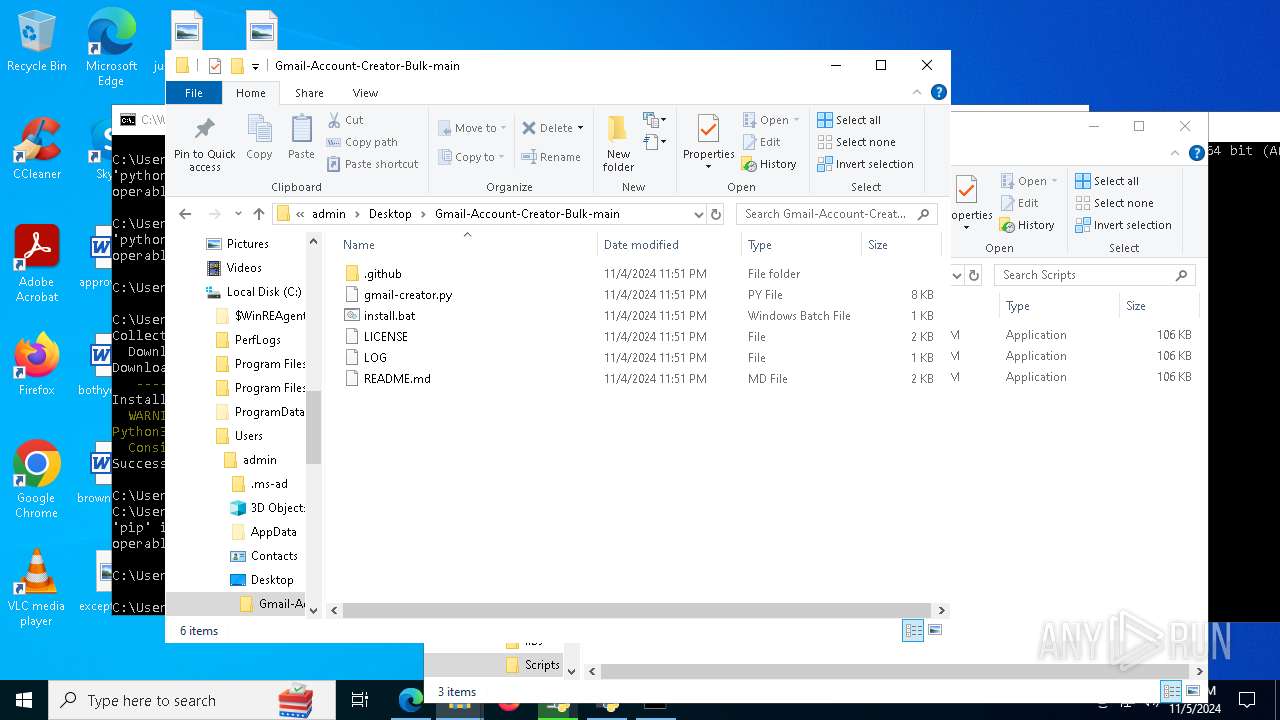
| download: | /Mystrosto/Gmail-Account-Creator-Bulk/archive/refs/heads/main.zip |
| Full analysis: | https://app.any.run/tasks/f0f6fd89-bbca-4739-ae1a-d8ea222bab37 |
| Verdict: | Malicious activity |
| Analysis date: | November 05, 2024, 01:51:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | D4CEA5B3DEE9A17A6E4582C96CCAD299 |
| SHA1: | EED336F14C502B64178E138EC35E670FD767C0C7 |
| SHA256: | 96D37B2CE7F2EABB216095D4E7A5F96386543B9B13587CEA04A62A2652095551 |
| SSDEEP: | 192:9cJWMgQBd4EkM7huouFg3cJd9+weSp0aYrmPtV:9c9BSEkFHn9+y9qmlV |
MALICIOUS
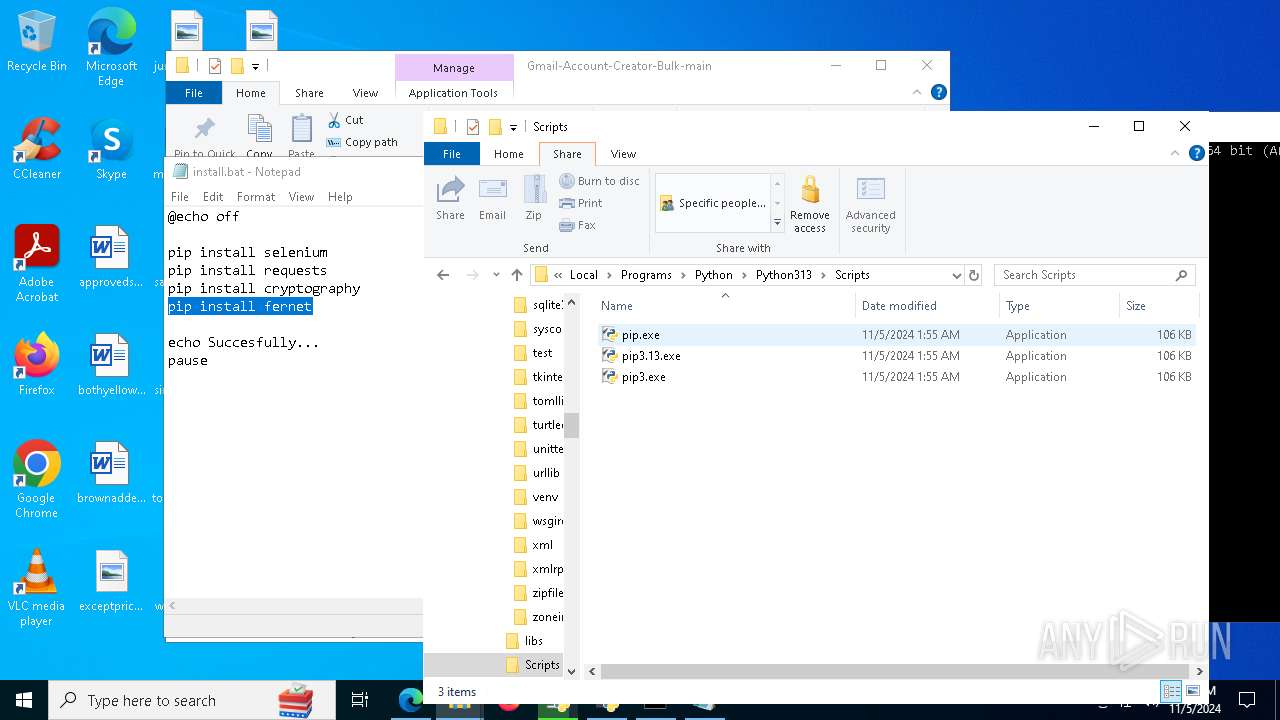
Generic archive extractor
- WinRAR.exe (PID: 6668)
SUSPICIOUS
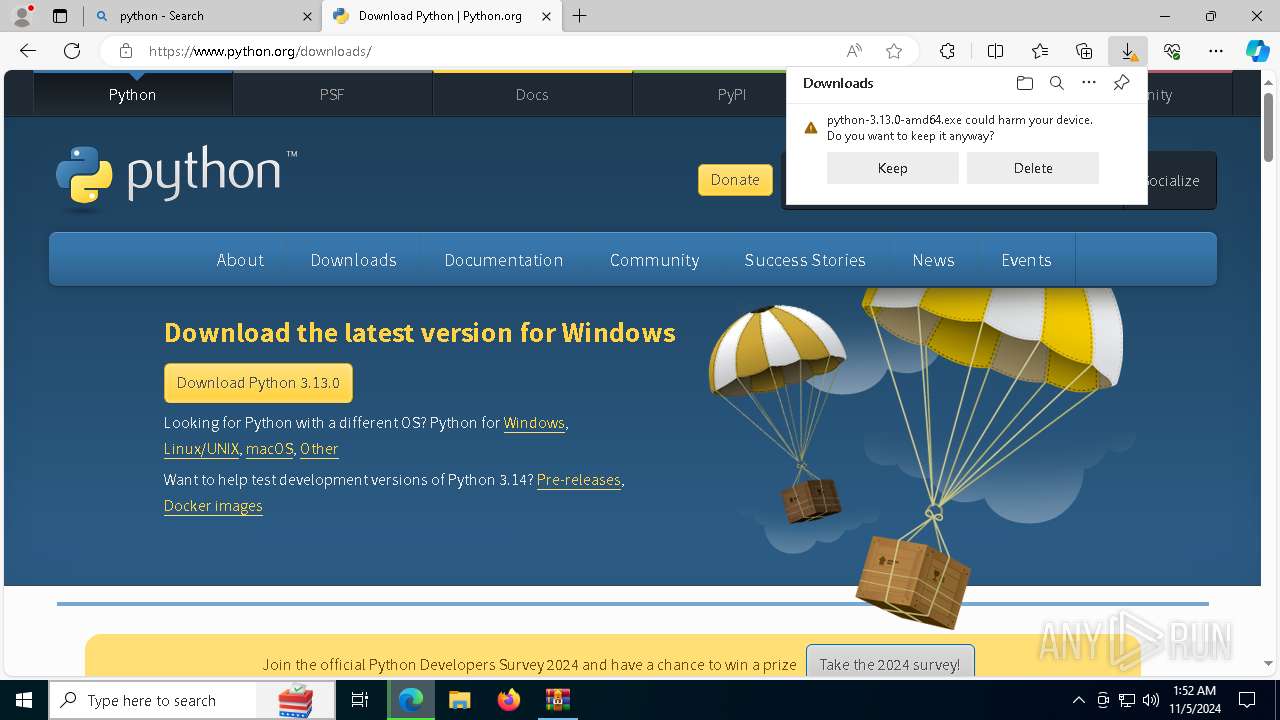
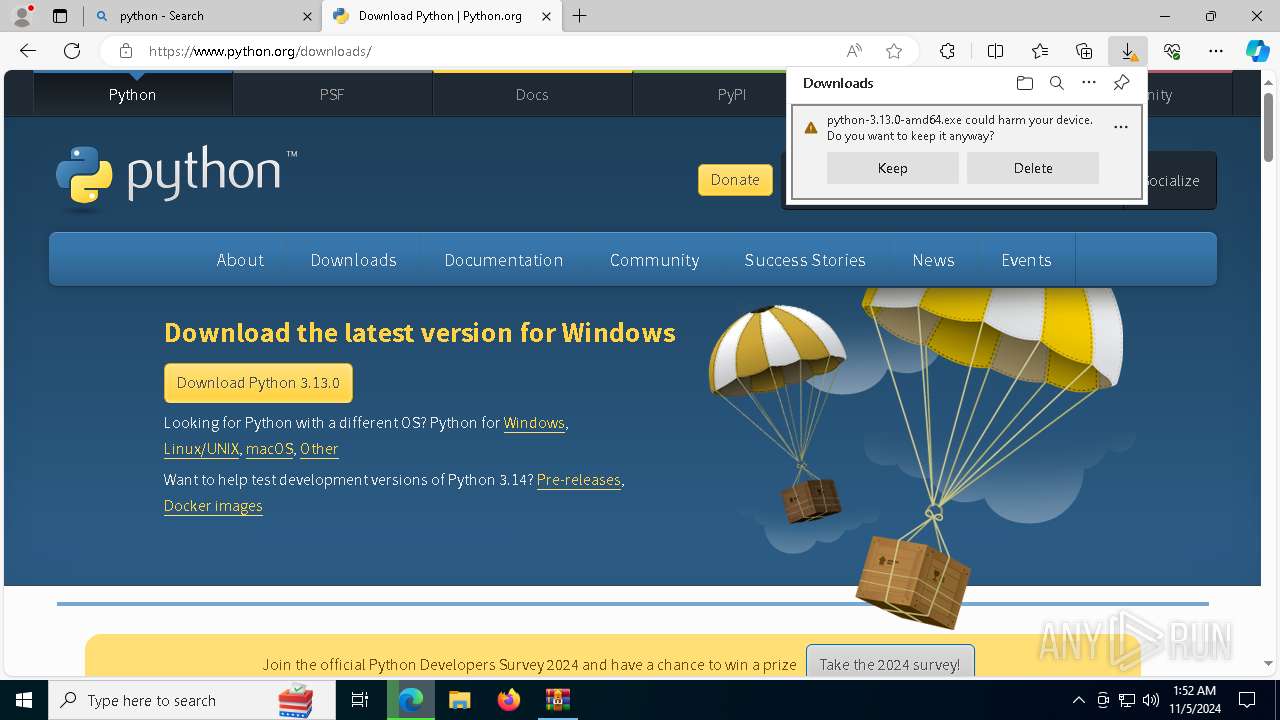
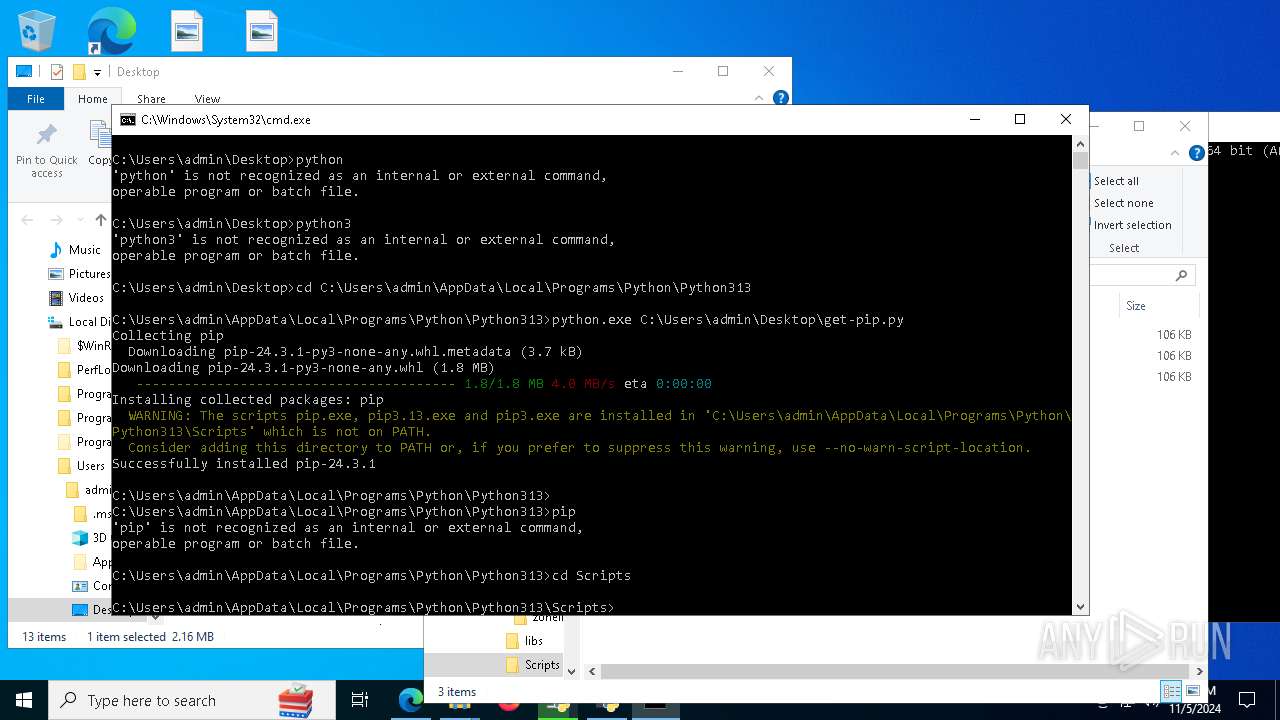
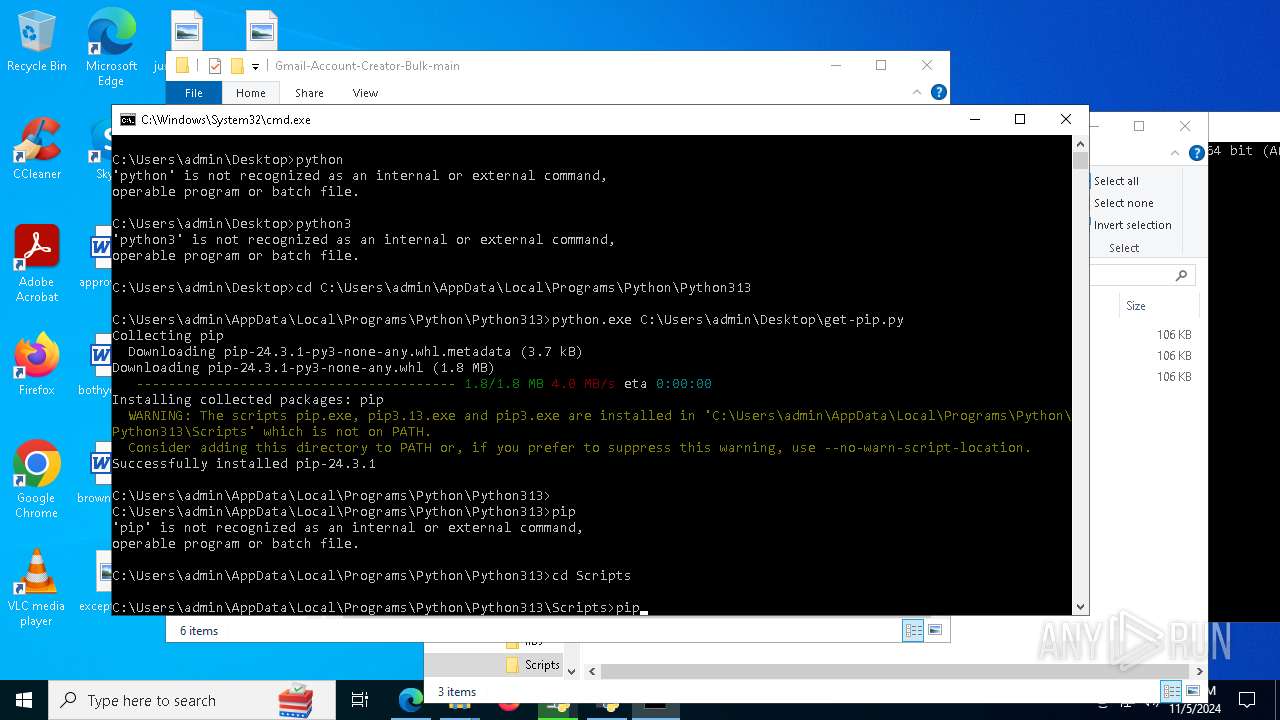
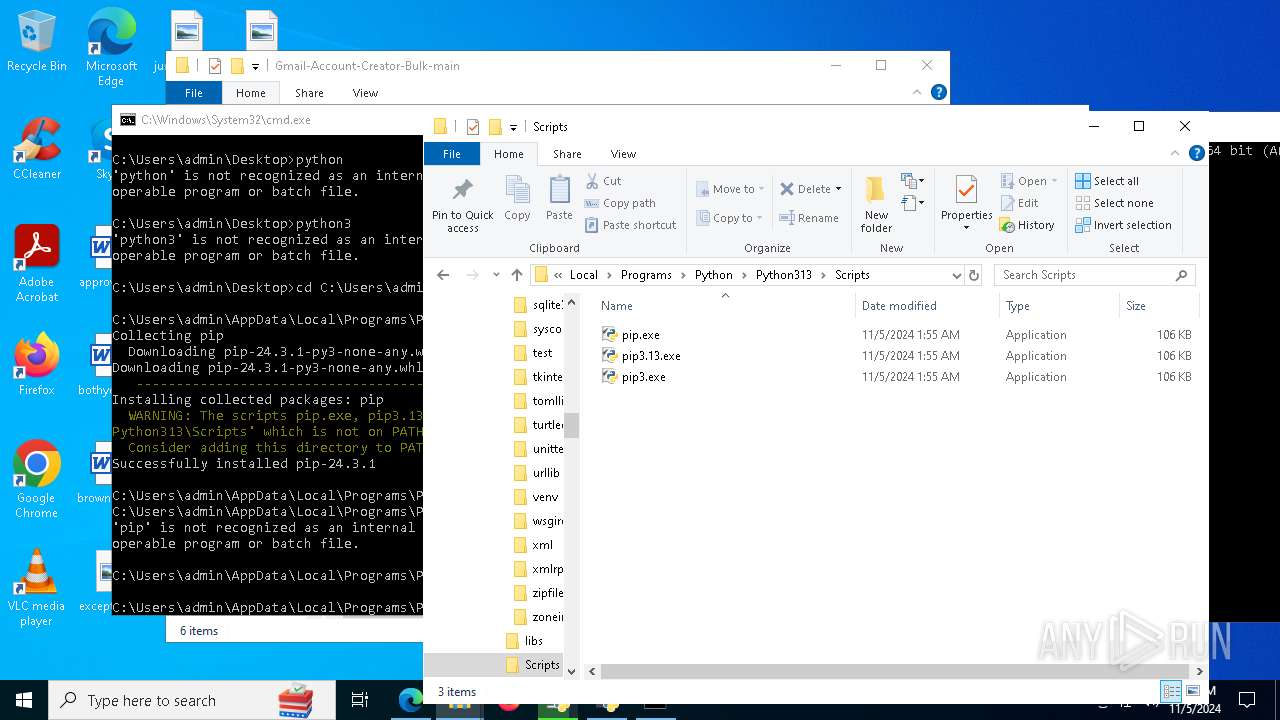
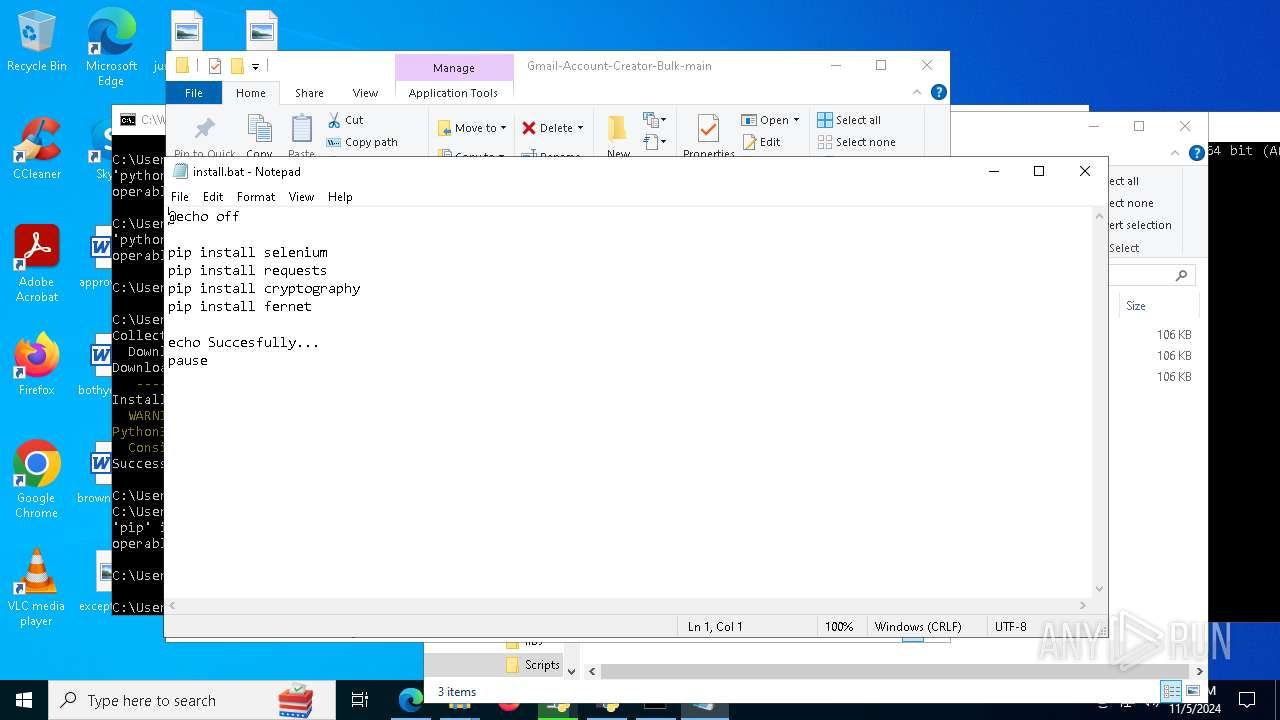
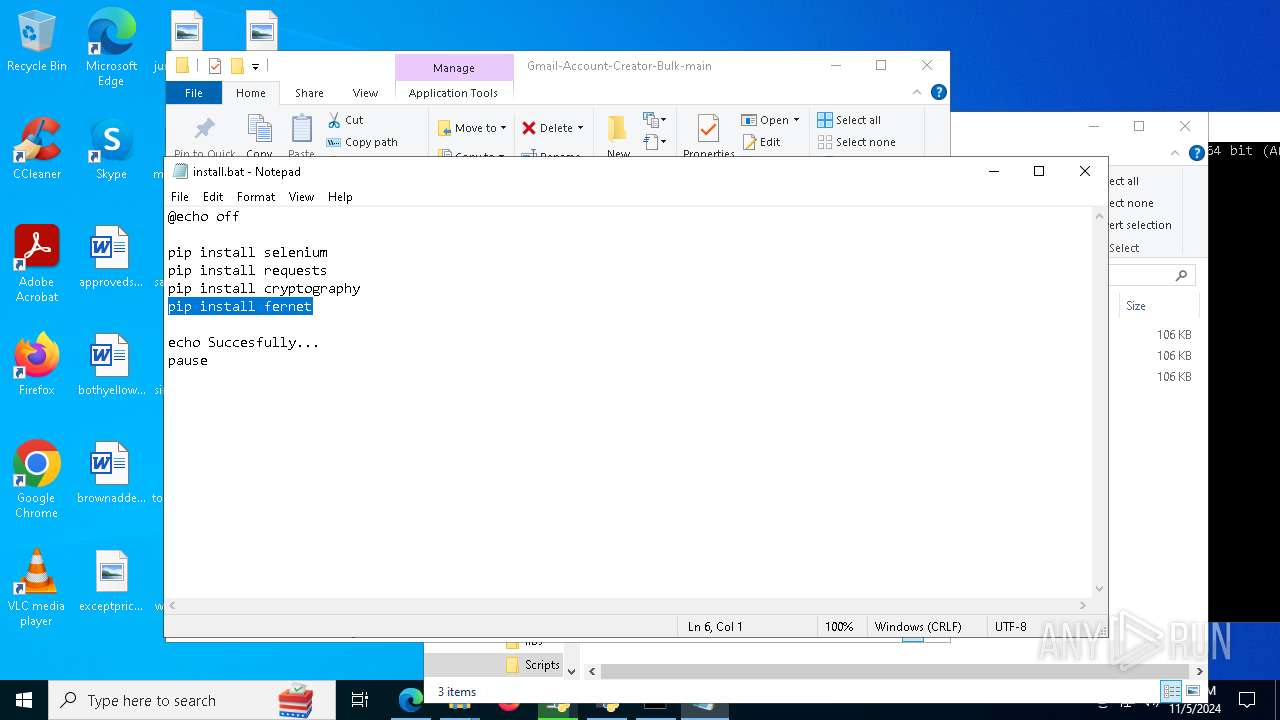
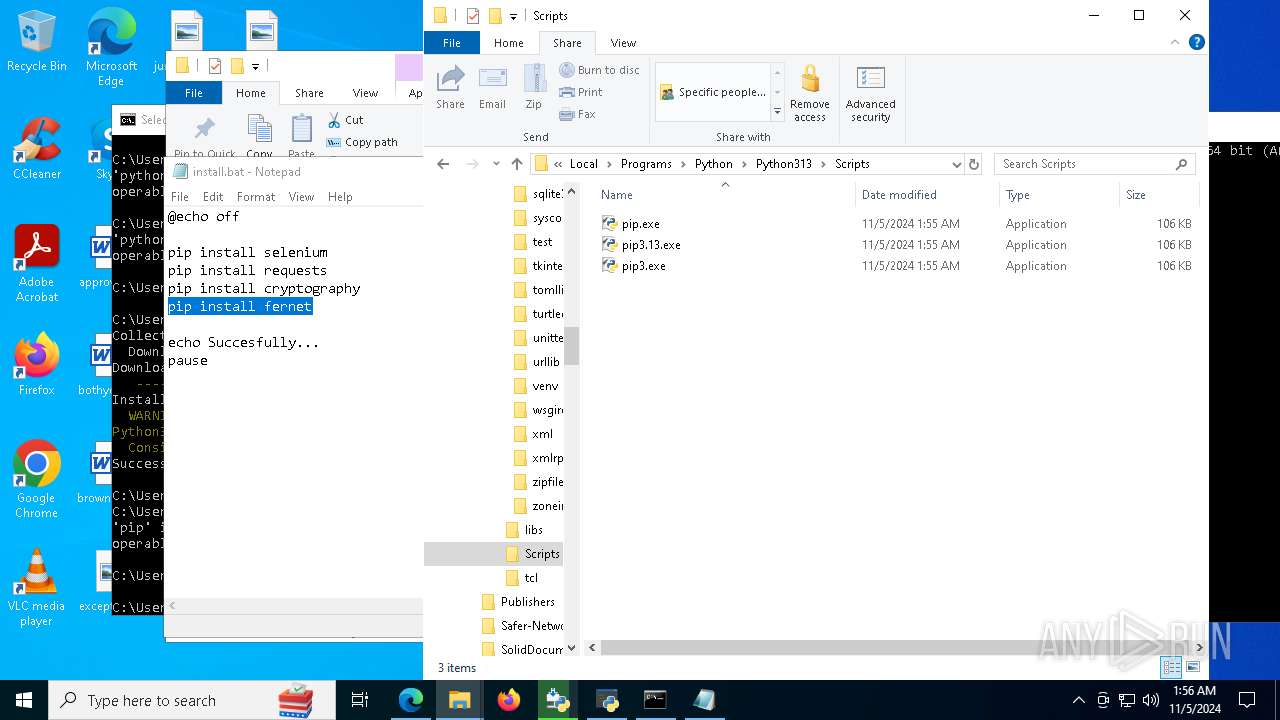
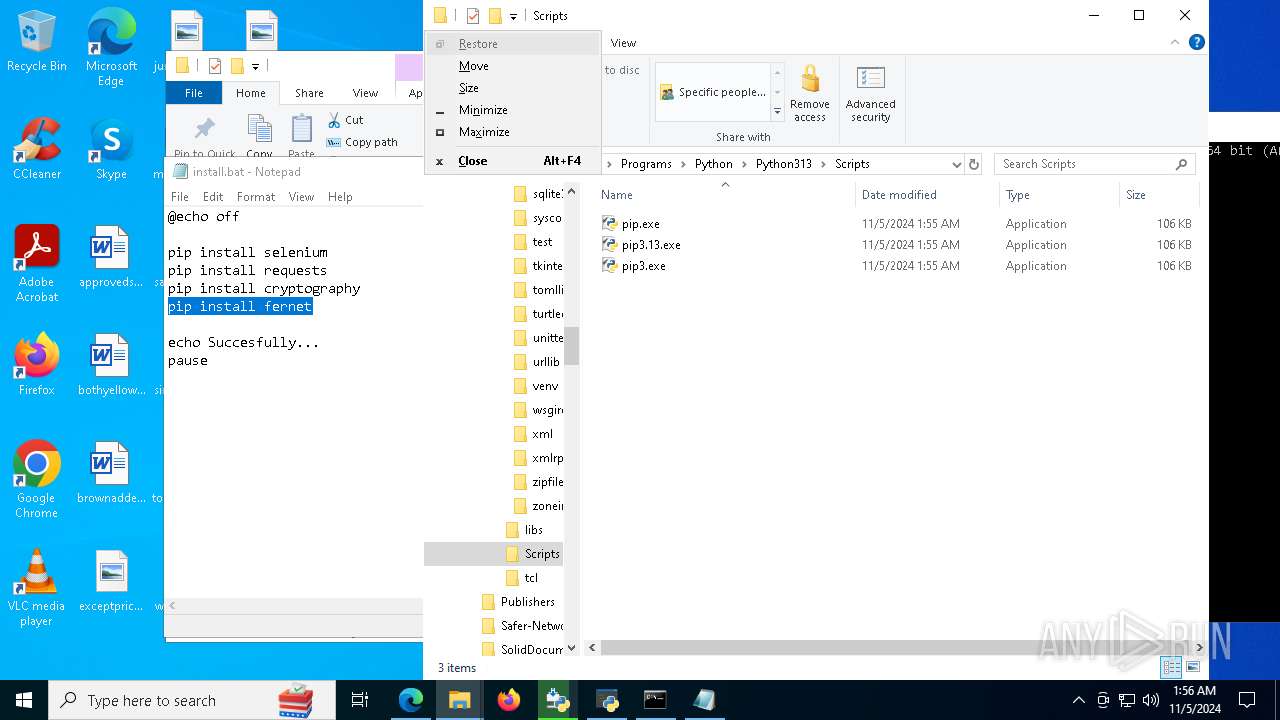
Executable content was dropped or overwritten
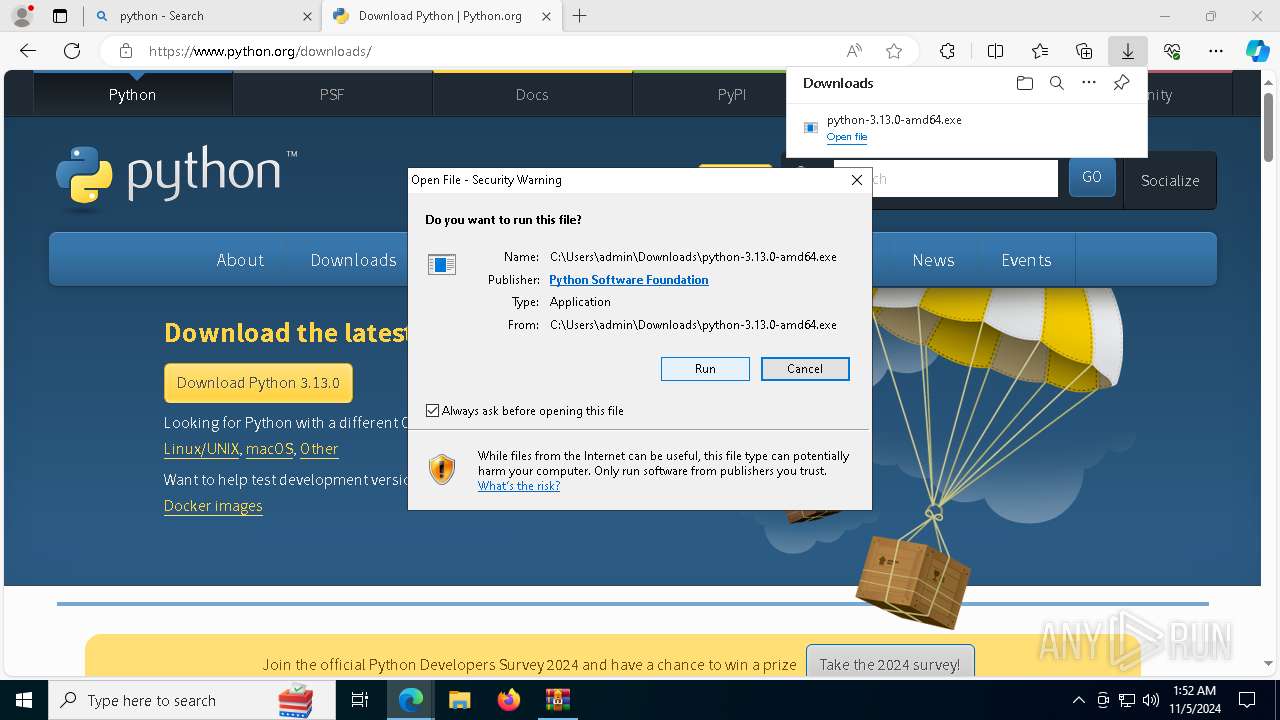
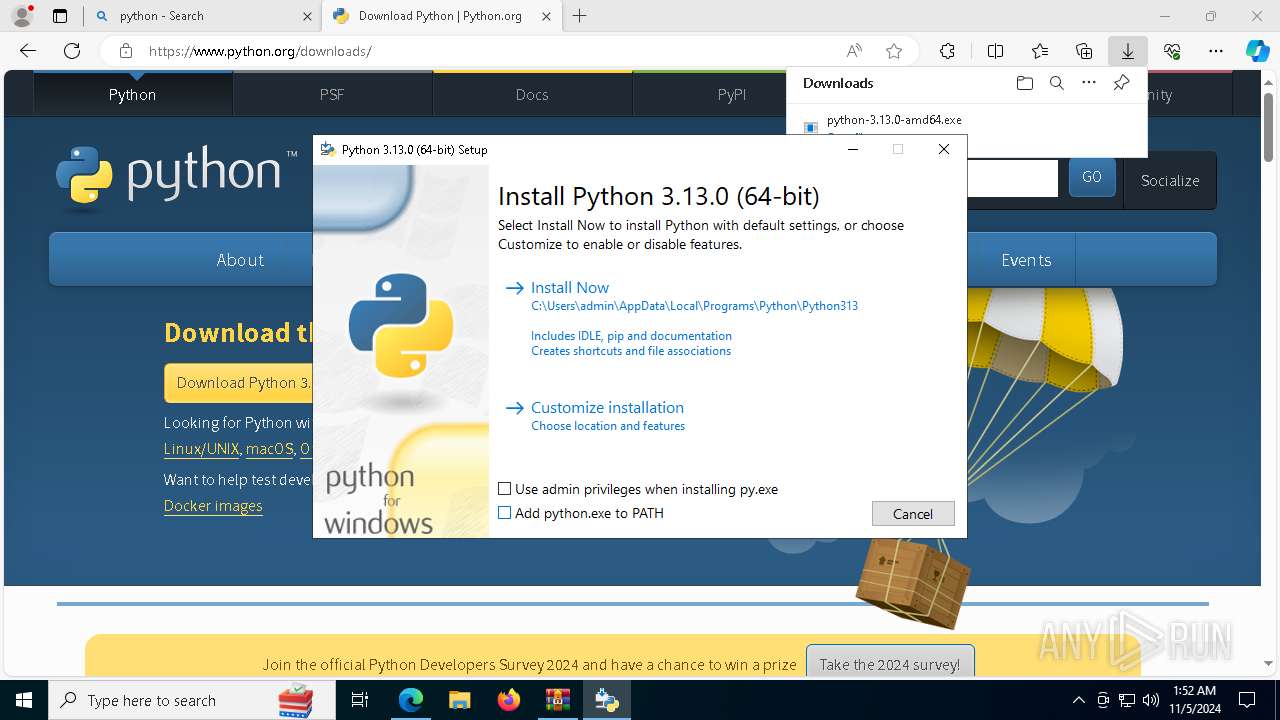
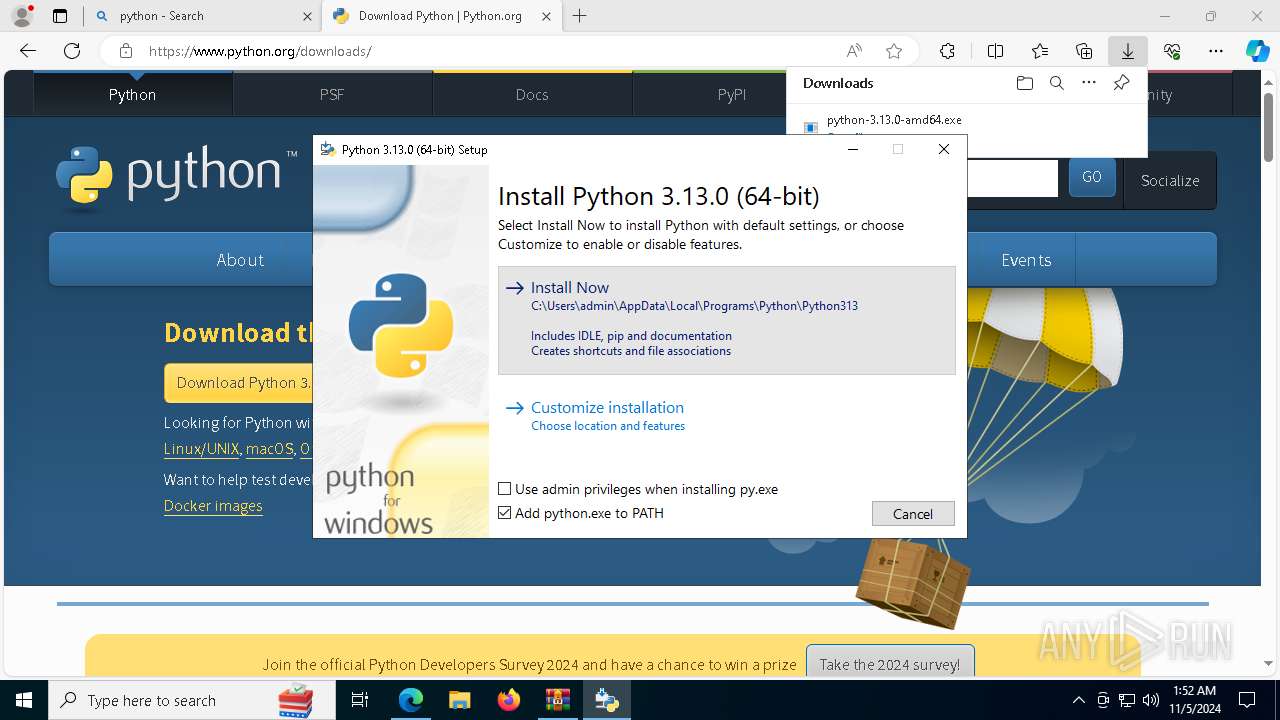
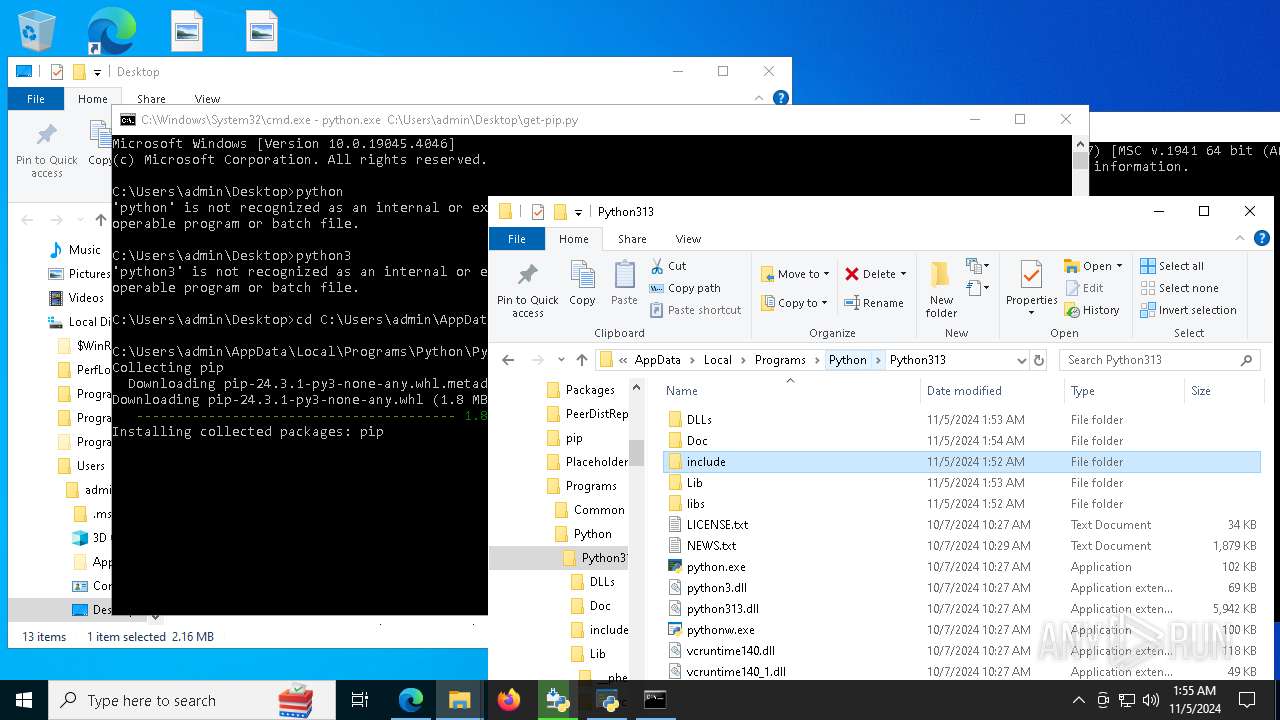
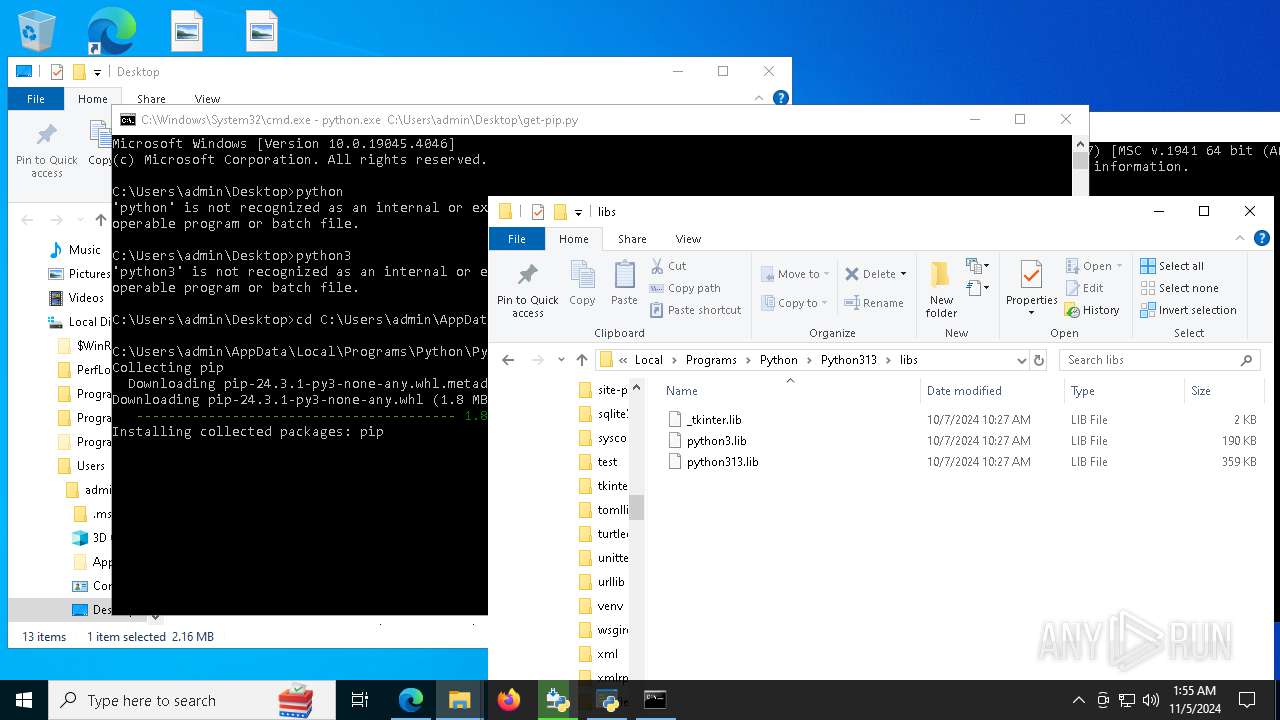
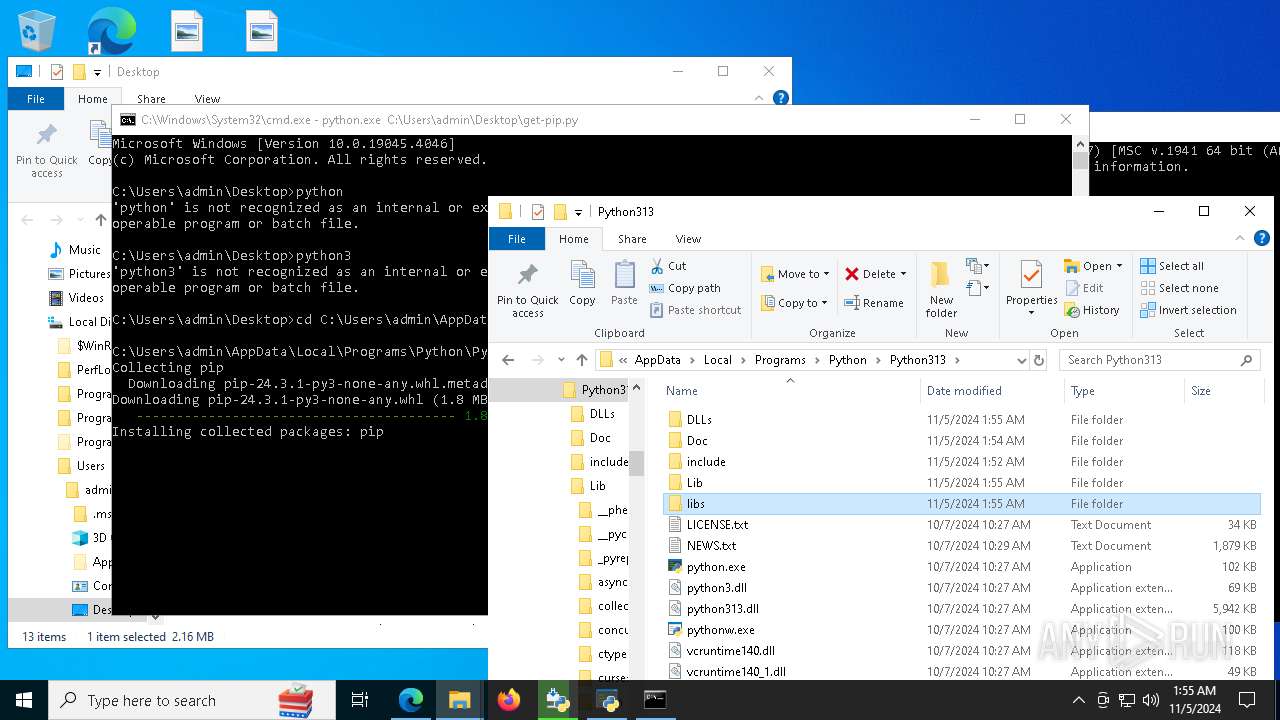
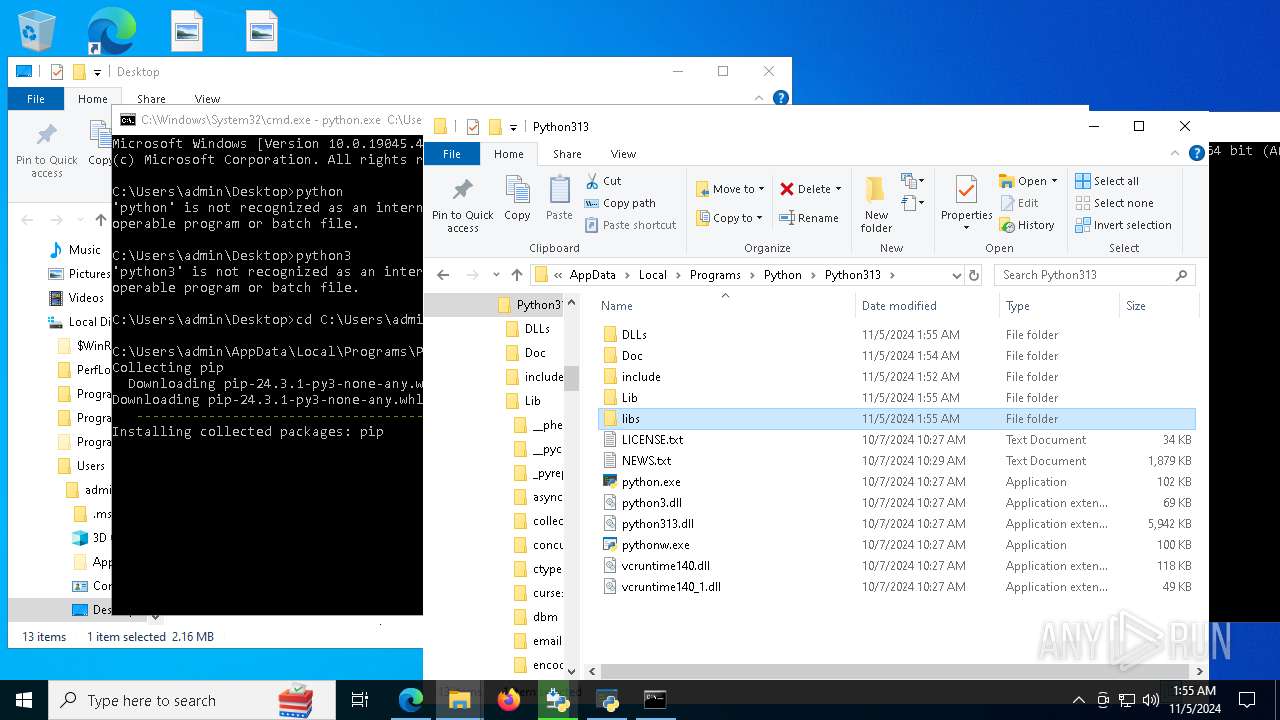
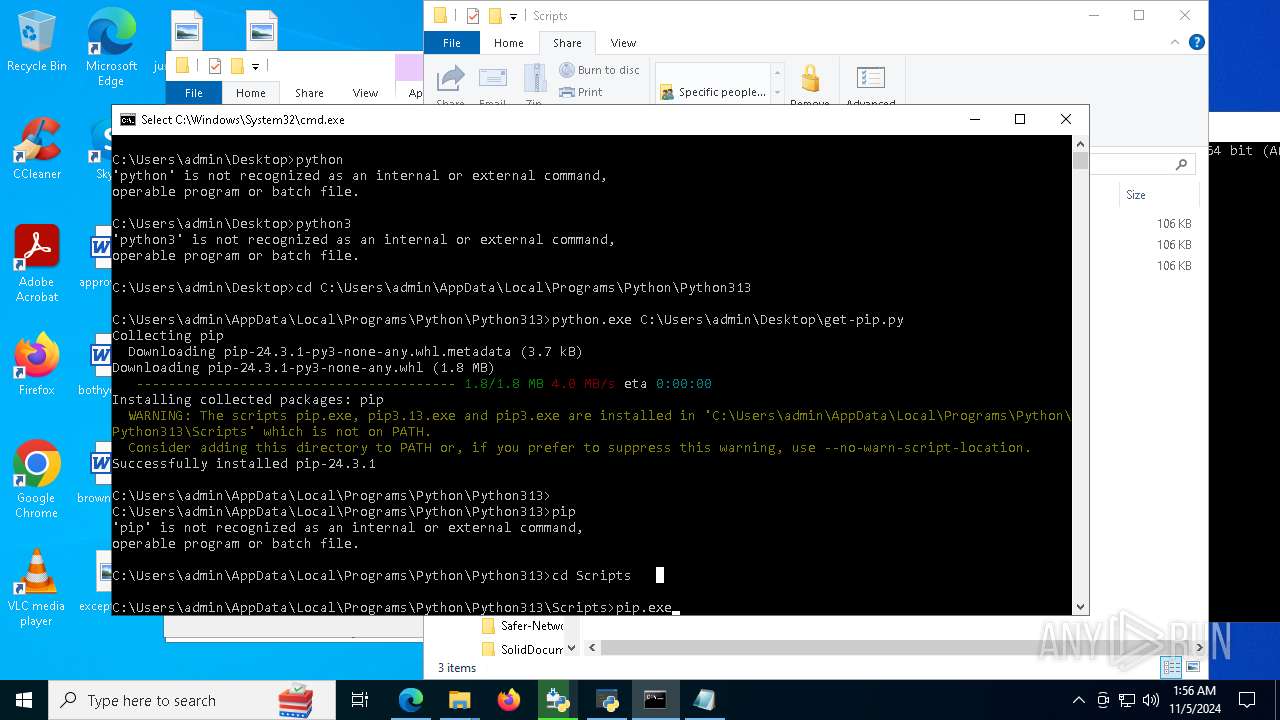
- python-3.13.0-amd64.exe (PID: 8088)
- python.exe (PID: 8292)
Process drops legitimate windows executable
- msiexec.exe (PID: 7040)
- python-3.13.0-amd64.exe (PID: 8088)
The process drops C-runtime libraries
- msiexec.exe (PID: 7040)
- python-3.13.0-amd64.exe (PID: 8088)
Process drops python dynamic module
- msiexec.exe (PID: 7040)
INFO
Executable content was dropped or overwritten
- msiexec.exe (PID: 7040)
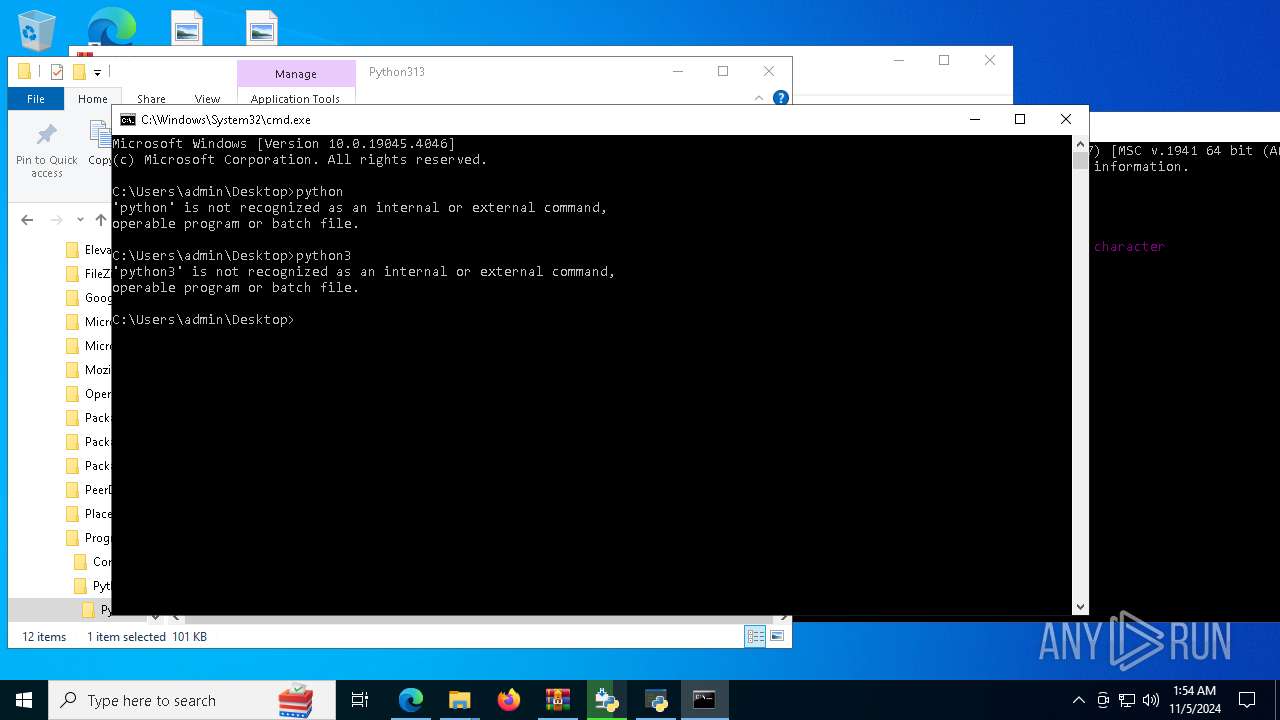
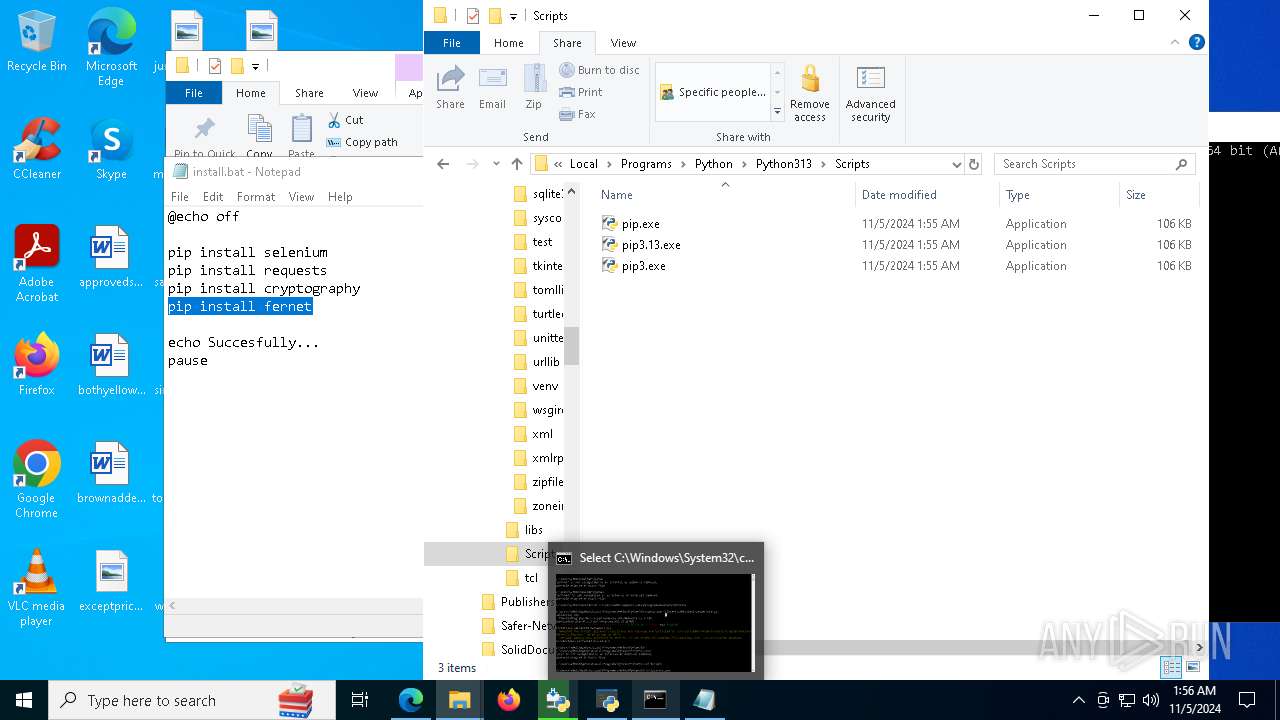
Manual execution by a user
- cmd.exe (PID: 7072)
- python.exe (PID: 8980)
- notepad.exe (PID: 9148)
- powershell.exe (PID: 700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:04 15:51:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Gmail-Account-Creator-Bulk-main/ |
Total processes
232
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "PowerShell.exe" -noexit -command Set-Location -literalPath 'C:\Users\admin\AppData\Local\Programs\Python\Python313\Scripts' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | python.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6436 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument microsoft-edge:https://go.microsoft.com/fwlink/?LinkId=528884 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | HelpPane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 6668 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7040 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 7072 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
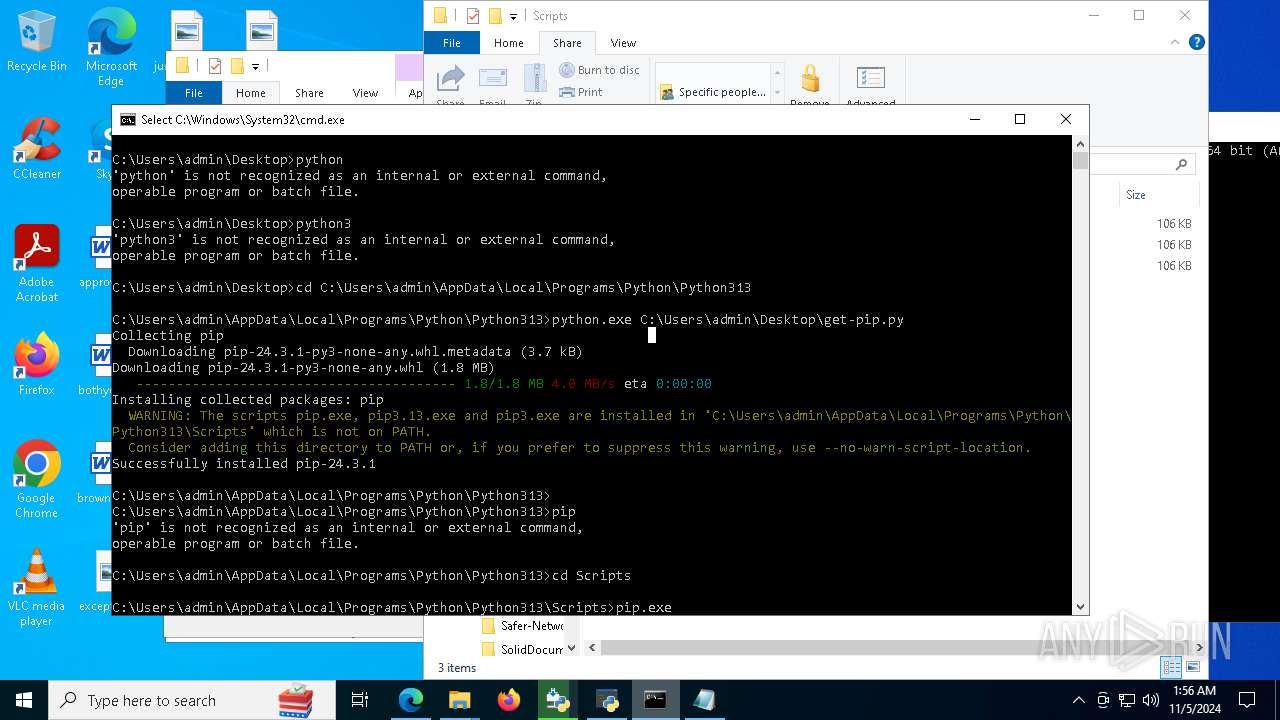
| 8088 | "C:\Users\admin\AppData\Local\Temp\{5380C4B8-1EE5-4A95-BA01-203EDE3B2330}\.cr\python-3.13.0-amd64.exe" -burn.clean.room="C:\Users\admin\Downloads\python-3.13.0-amd64.exe" -burn.filehandle.attached=540 -burn.filehandle.self=548 | C:\Users\admin\AppData\Local\Temp\{5380C4B8-1EE5-4A95-BA01-203EDE3B2330}\.cr\python-3.13.0-amd64.exe | python-3.13.0-amd64.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.13.0 (64-bit) Version: 3.13.150.0 | |||||||||||||||
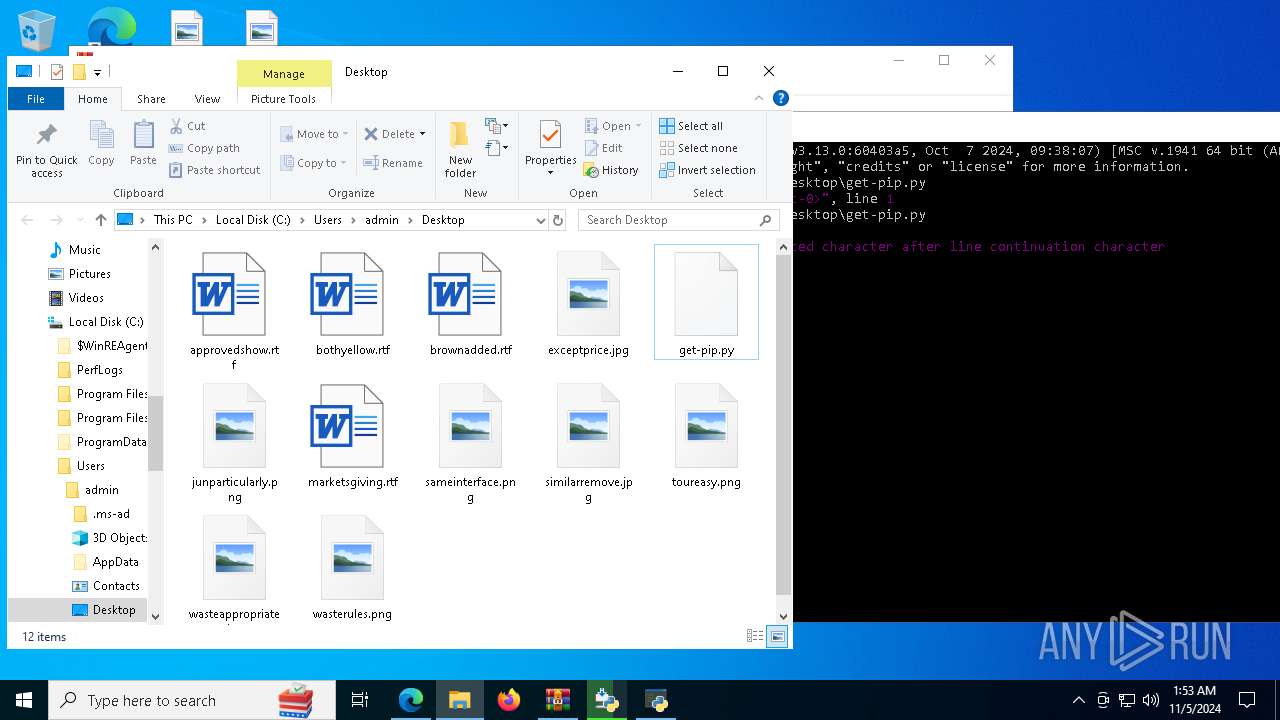
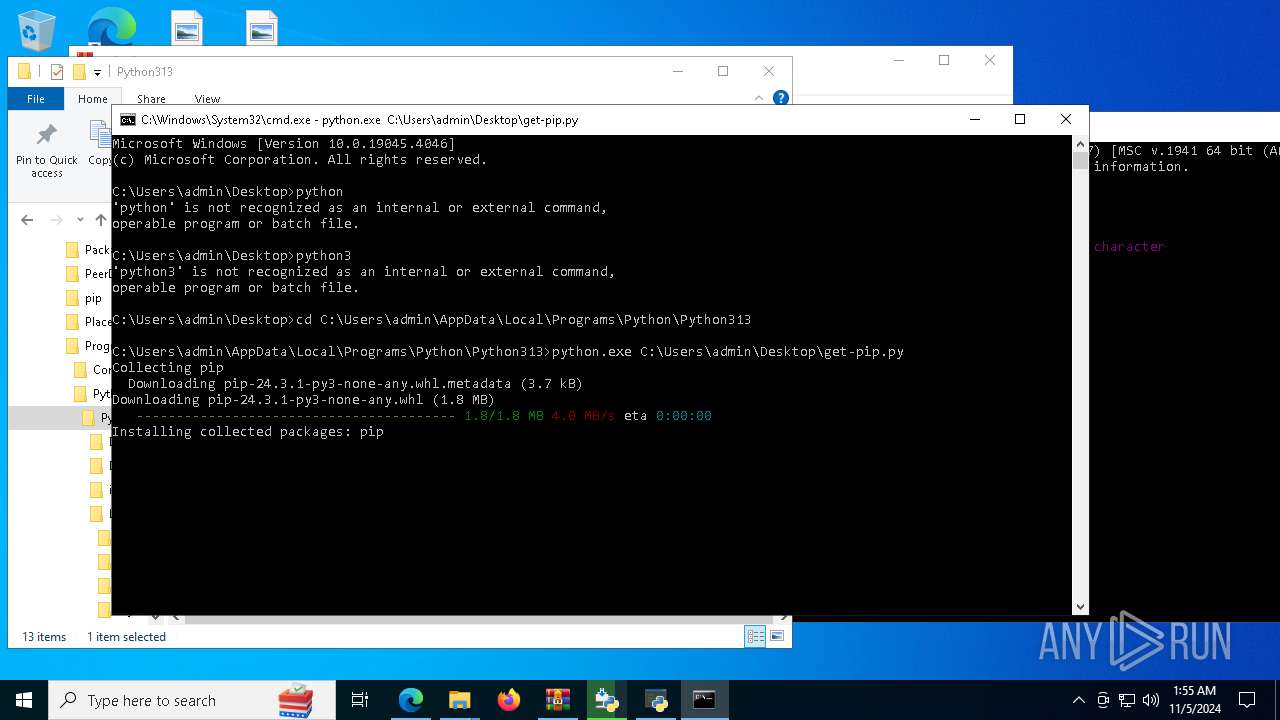
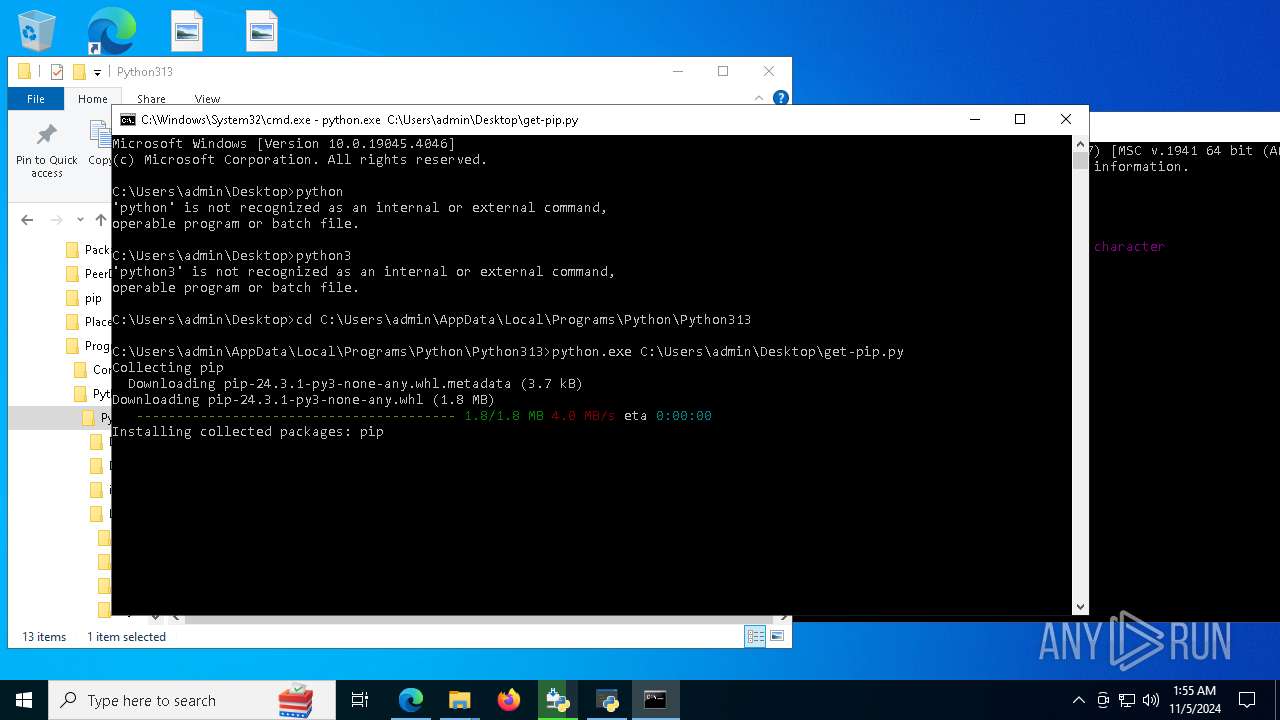
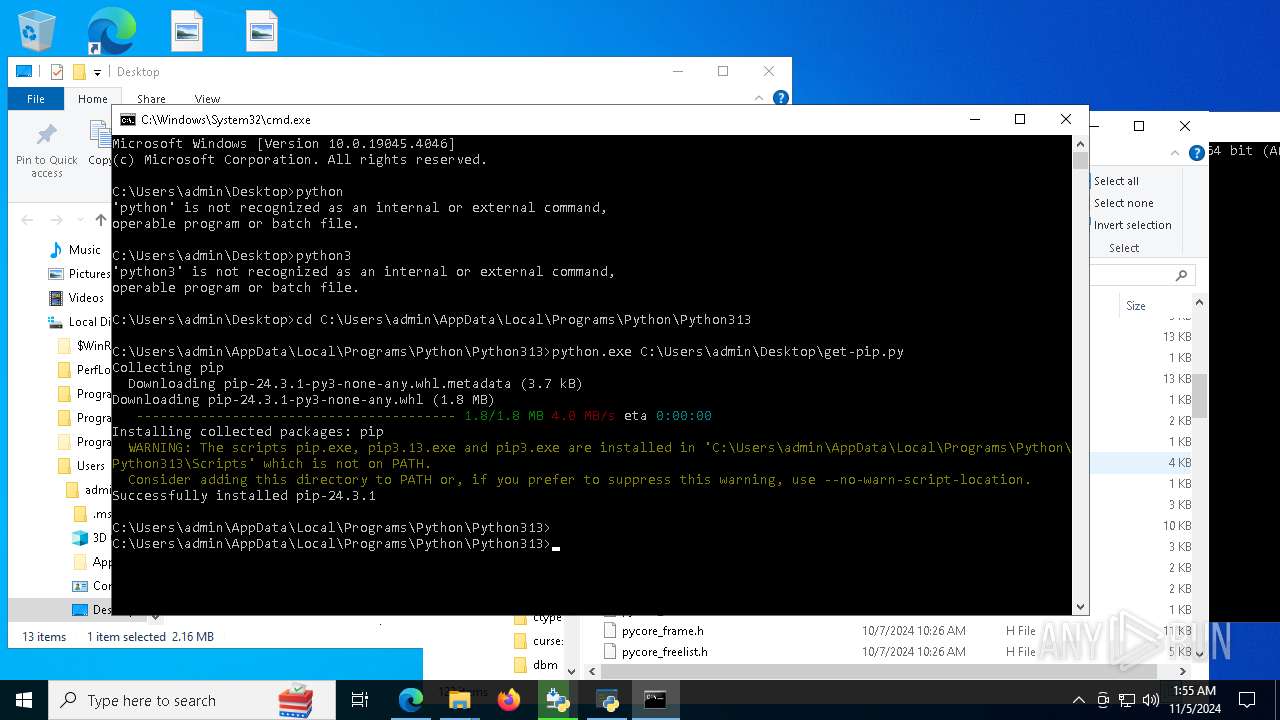
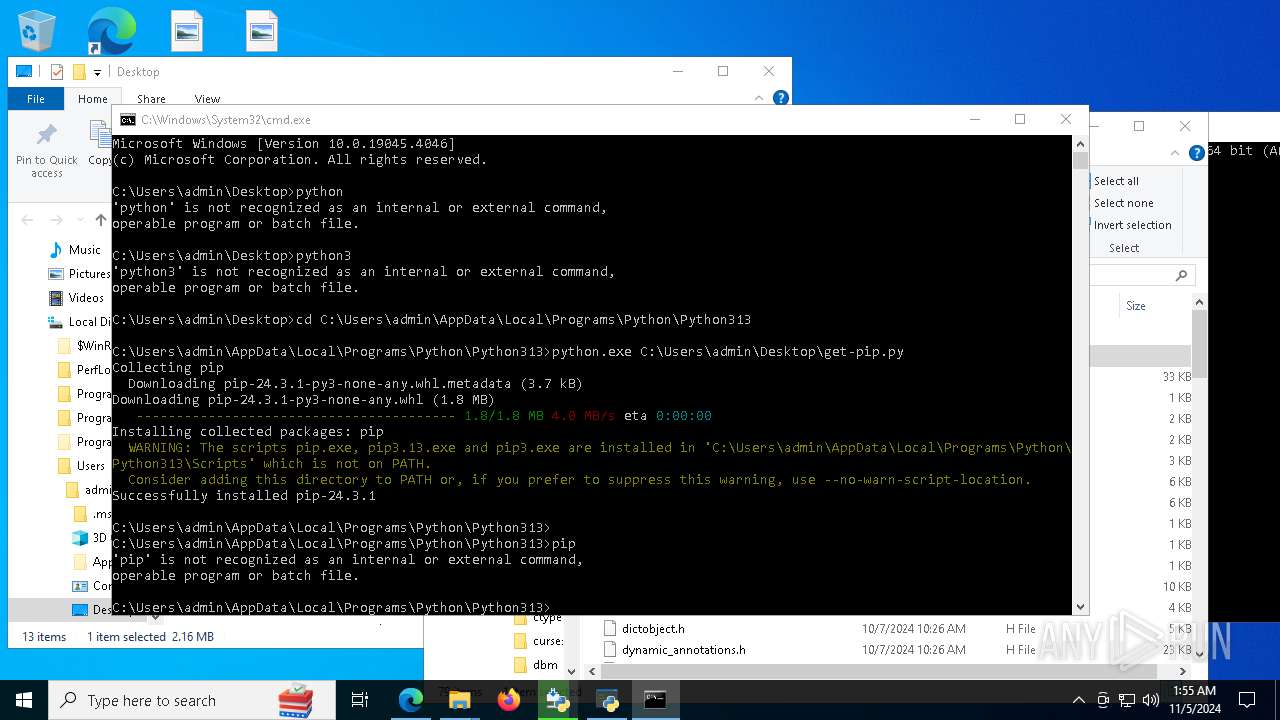
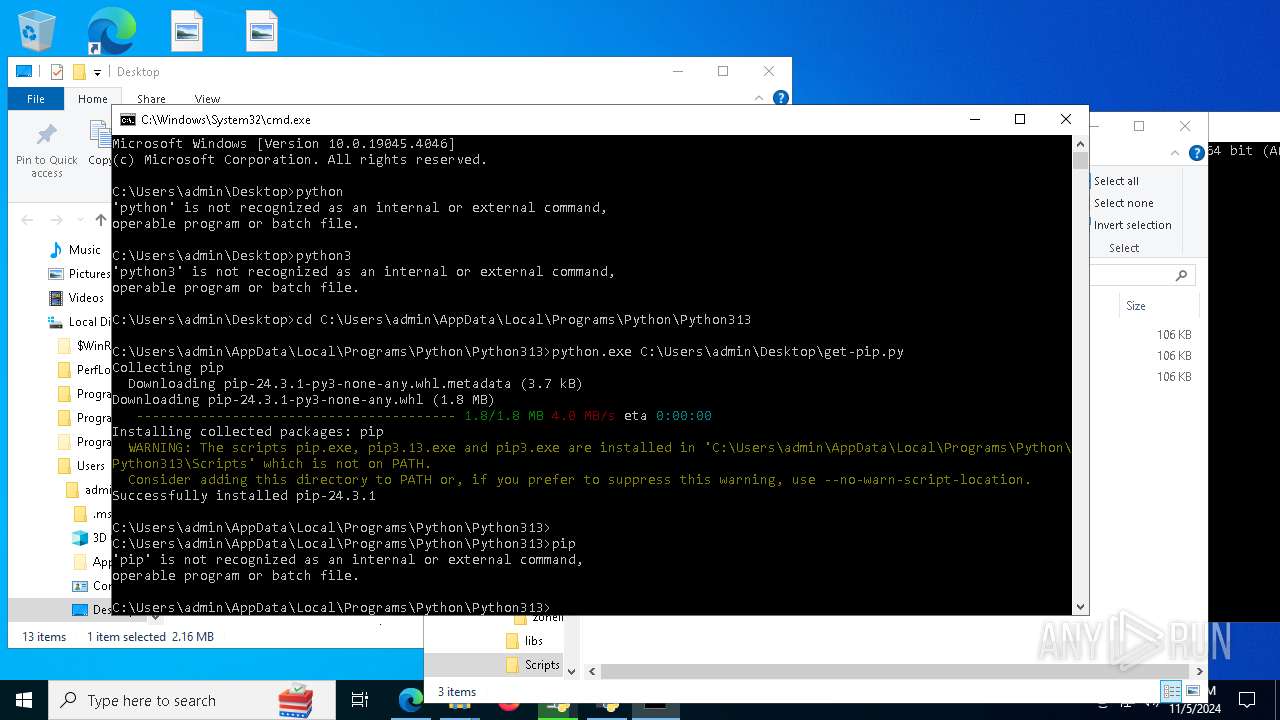
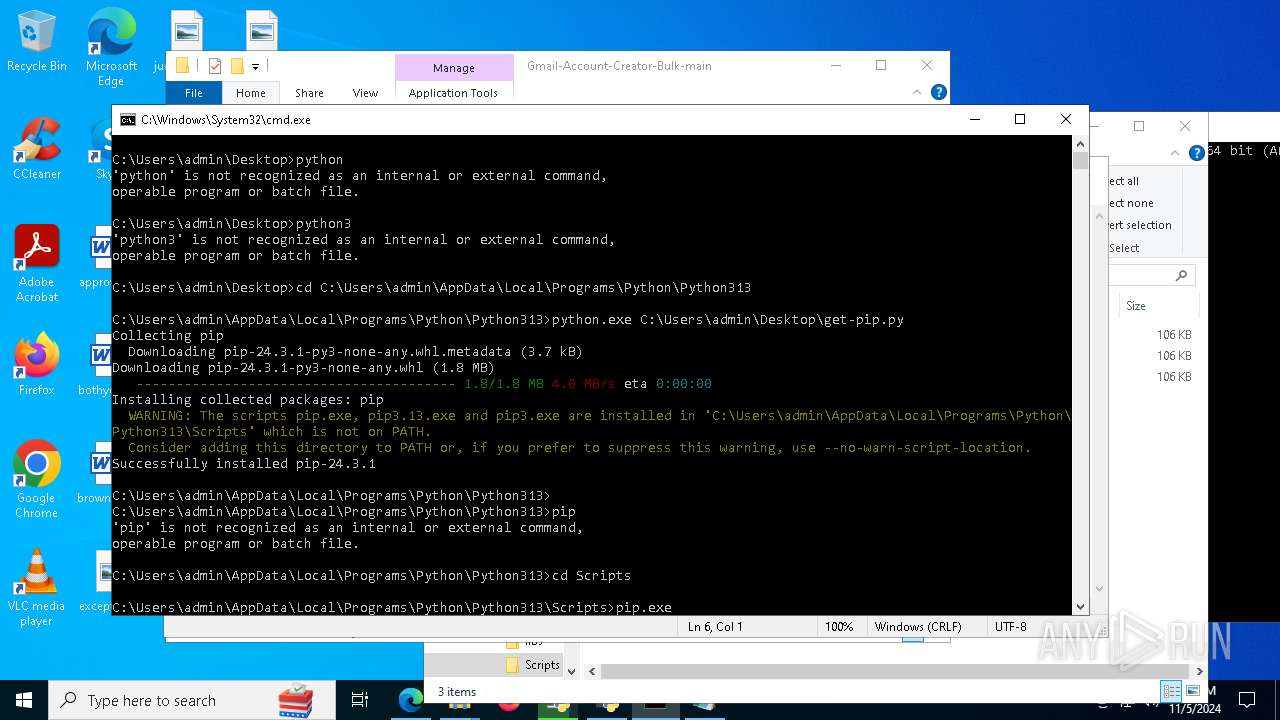
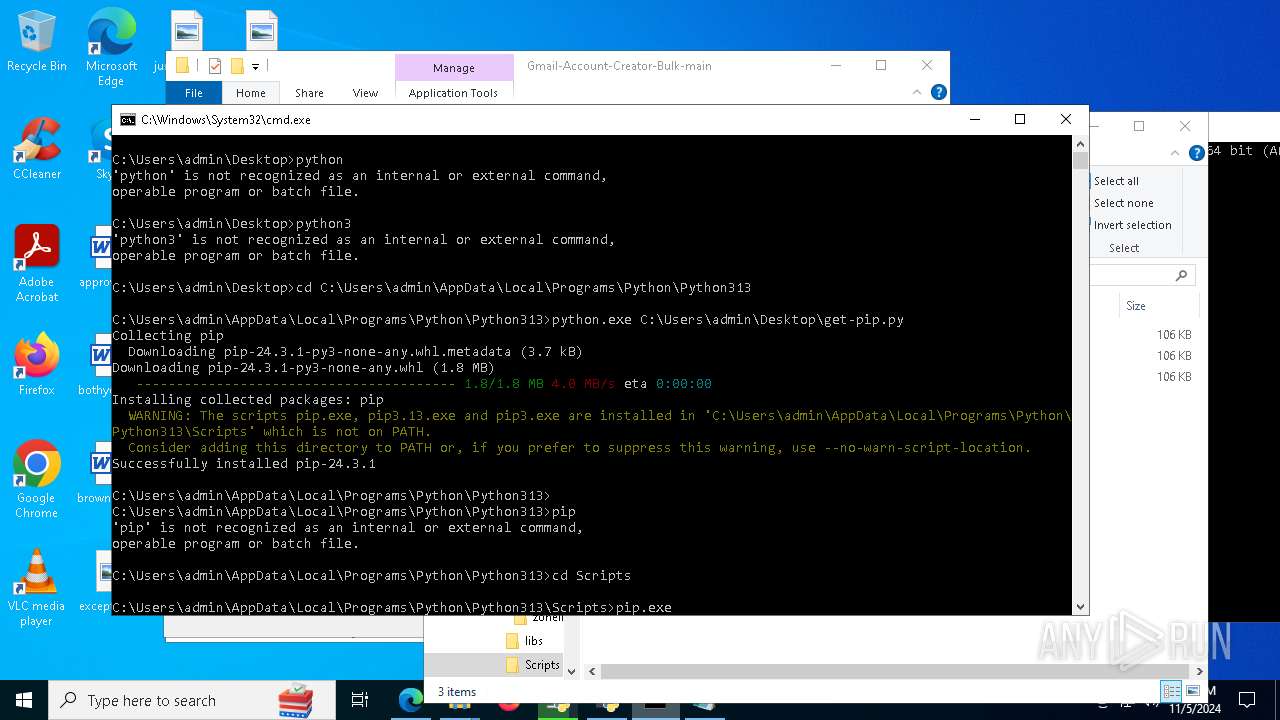
| 8292 | python.exe C:\Users\admin\Desktop\get-pip.py | C:\Users\admin\AppData\Local\Programs\Python\Python313\python.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.13.0 | |||||||||||||||
| 8944 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
1 605
Read events
1 599
Write events
6
Delete events
0
Modification events
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\main.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
91
Suspicious files
1 417
Text files
4 439
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Temp\{7E8546F8-CF75-4D19-9556-CAC8E54F1815}\lib_JustForMe | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Temp\{7E8546F8-CF75-4D19-9556-CAC8E54F1815}\test_JustForMe | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Temp\{7E8546F8-CF75-4D19-9556-CAC8E54F1815}\doc_JustForMe | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Temp\{7E8546F8-CF75-4D19-9556-CAC8E54F1815}\.ba\Default.wxl | xml | |
MD5:E1A9ABB2936BC6E980C9BACEBE71C5A9 | SHA256:7F30044D0B14262F8BACD2891A810B127550CA56FC4D0E1D619AE489AAF6EC18 | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Temp\{7E8546F8-CF75-4D19-9556-CAC8E54F1815}\.ba\BootstrapperApplicationData.xml | xml | |
MD5:54FA5B3436BA5E578F9AEBFC984F1863 | SHA256:A944B368ACC8C6F0B23B20B6DDABE3AD7F9CEAD90747E93F390B1A1FA71161E0 | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Package Cache\.unverified\lib_JustForMe | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Package Cache\{09D95048-E91D-4F33-9197-1182FCA17B16}v3.13.150.0\lib.msi | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Package Cache\.unverified\test_JustForMe | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Package Cache\{D1F9D9AE-E7E2-48AA-BA3A-6E760D2B5F7D}v3.13.150.0\test.msi | — | |
MD5:— | SHA256:— | |||
| 8088 | python-3.13.0-amd64.exe | C:\Users\admin\AppData\Local\Package Cache\.unverified\doc_JustForMe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
145
DNS requests
142
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7048 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.189.173.3:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www2.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
— | — | Misc activity | ET INFO File Hosting Service Domain Domain in DNS Lookup (files .pythonhosted .org) |
— | — | Misc activity | ET INFO Observed File Hosting Service Domain (files .pythonhosted .org in TLS SNI) |