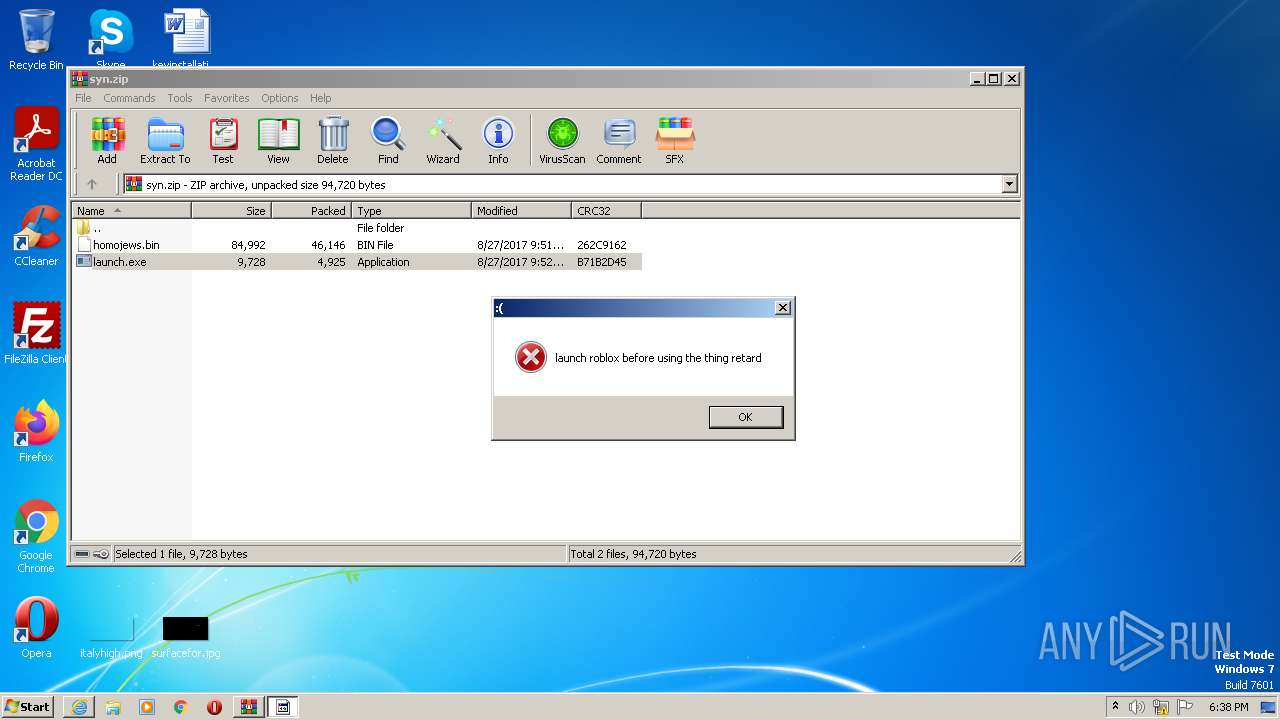
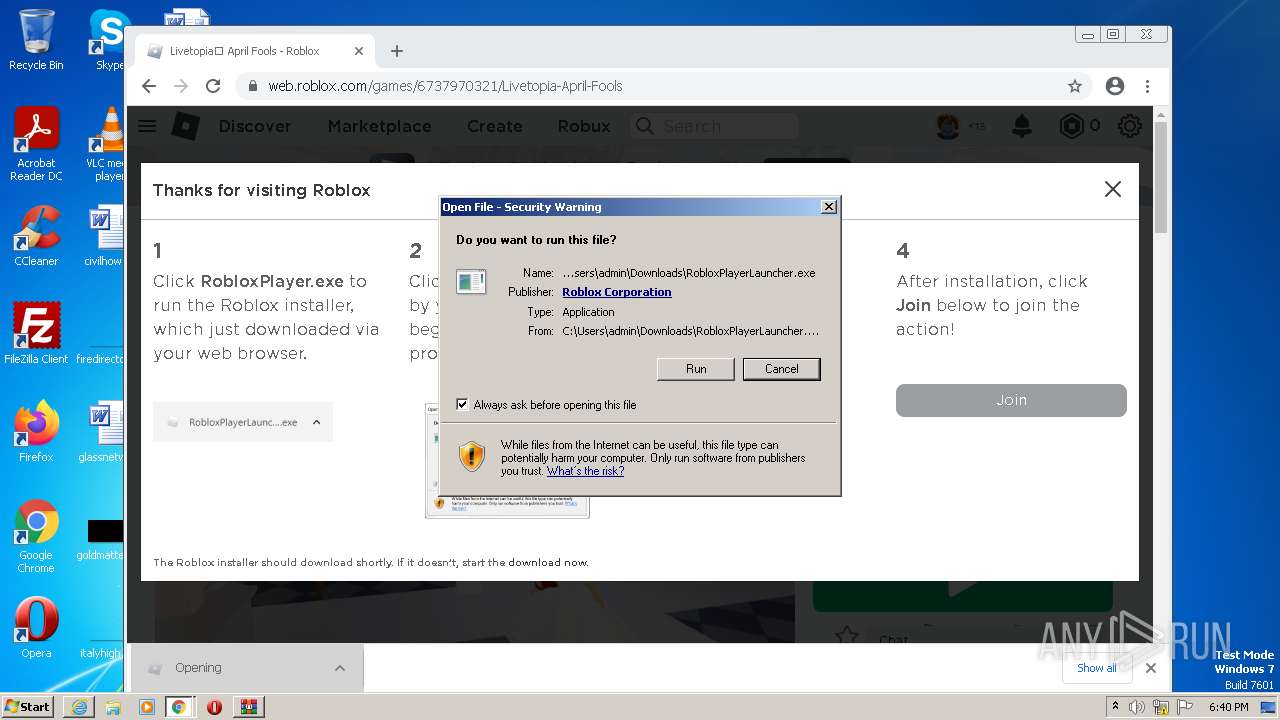
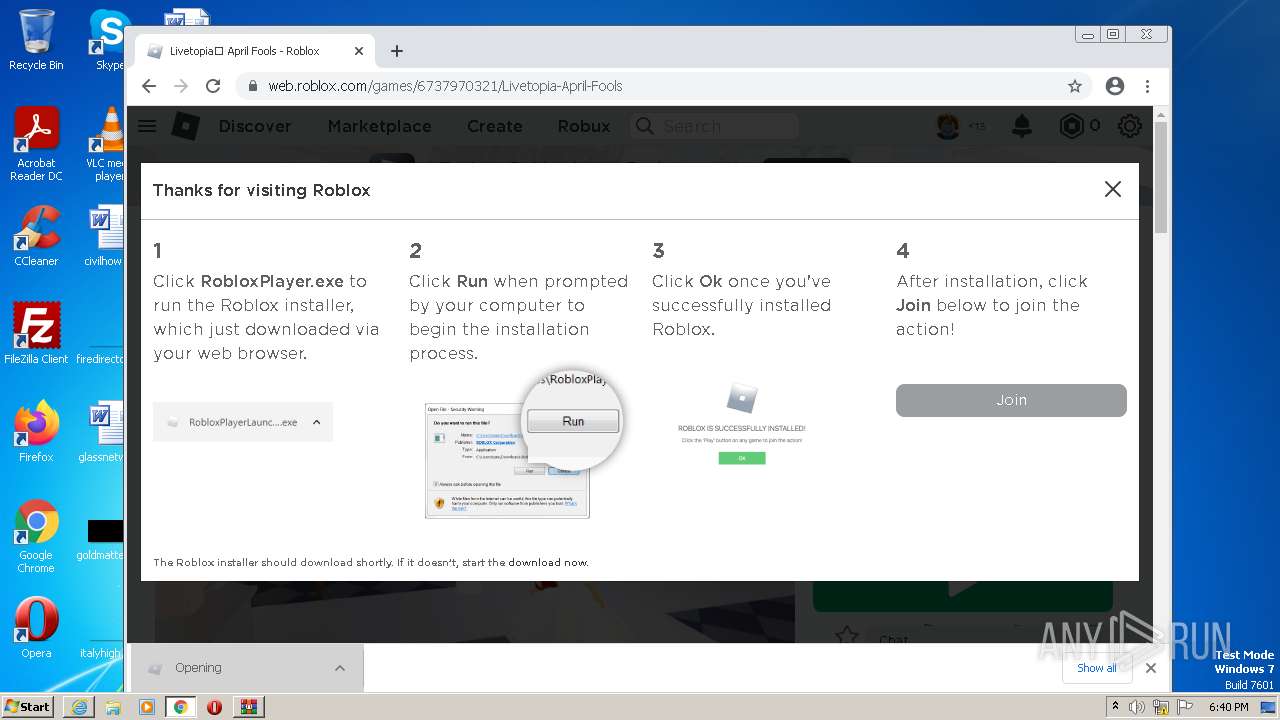
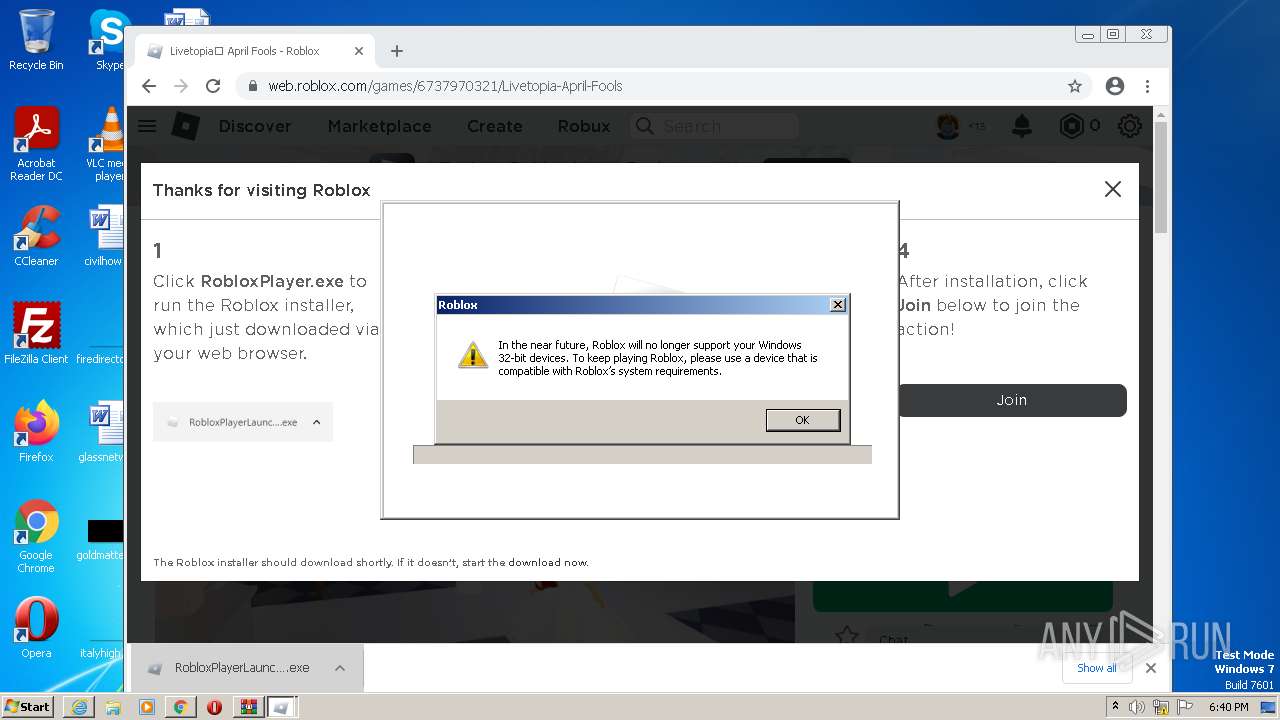
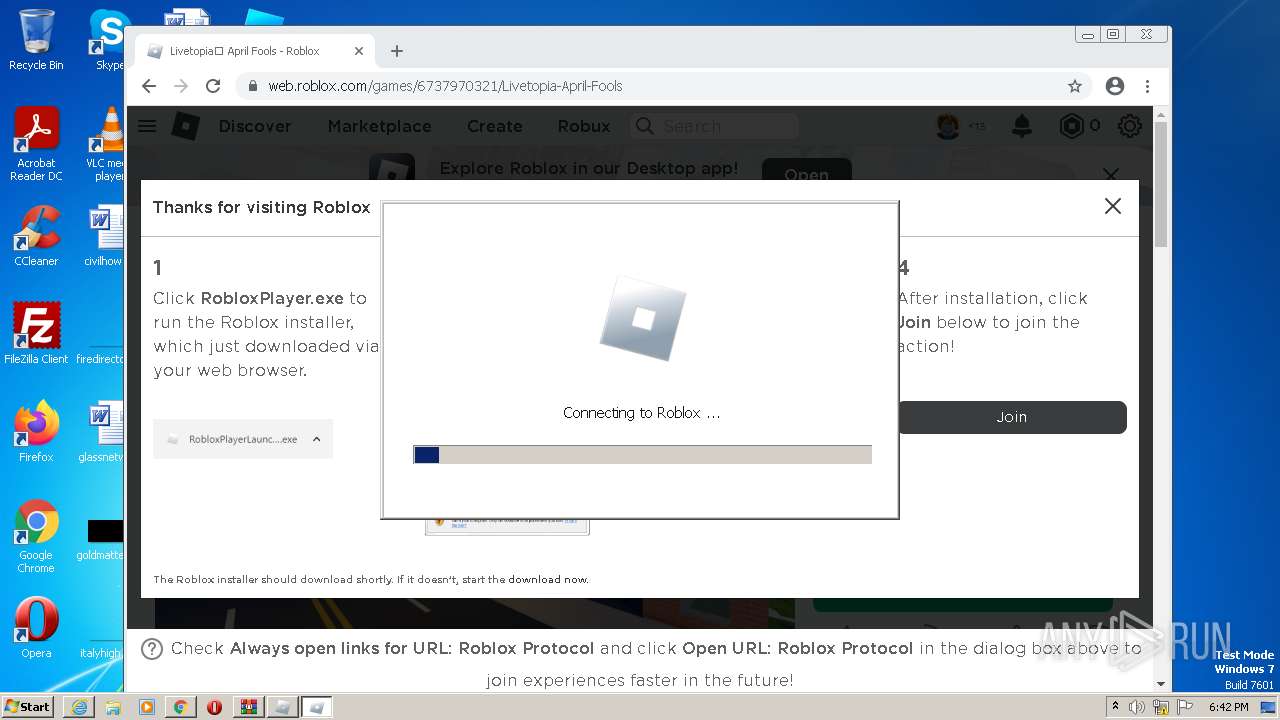
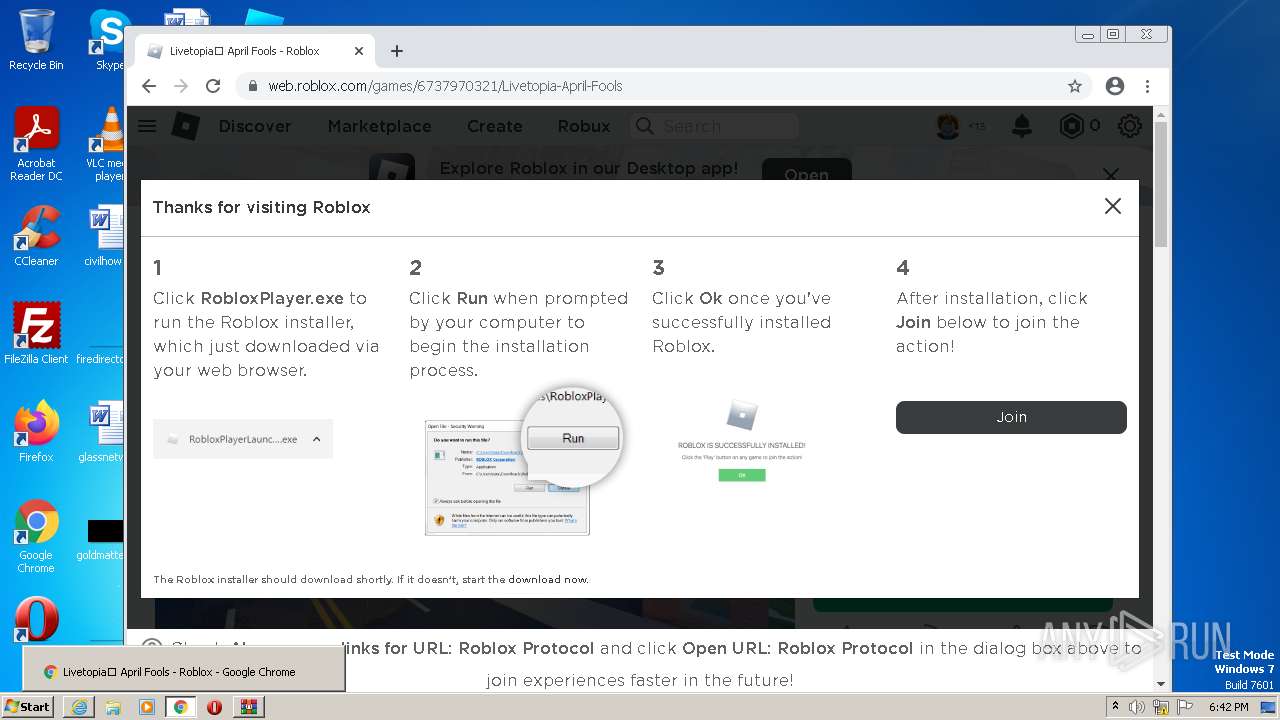
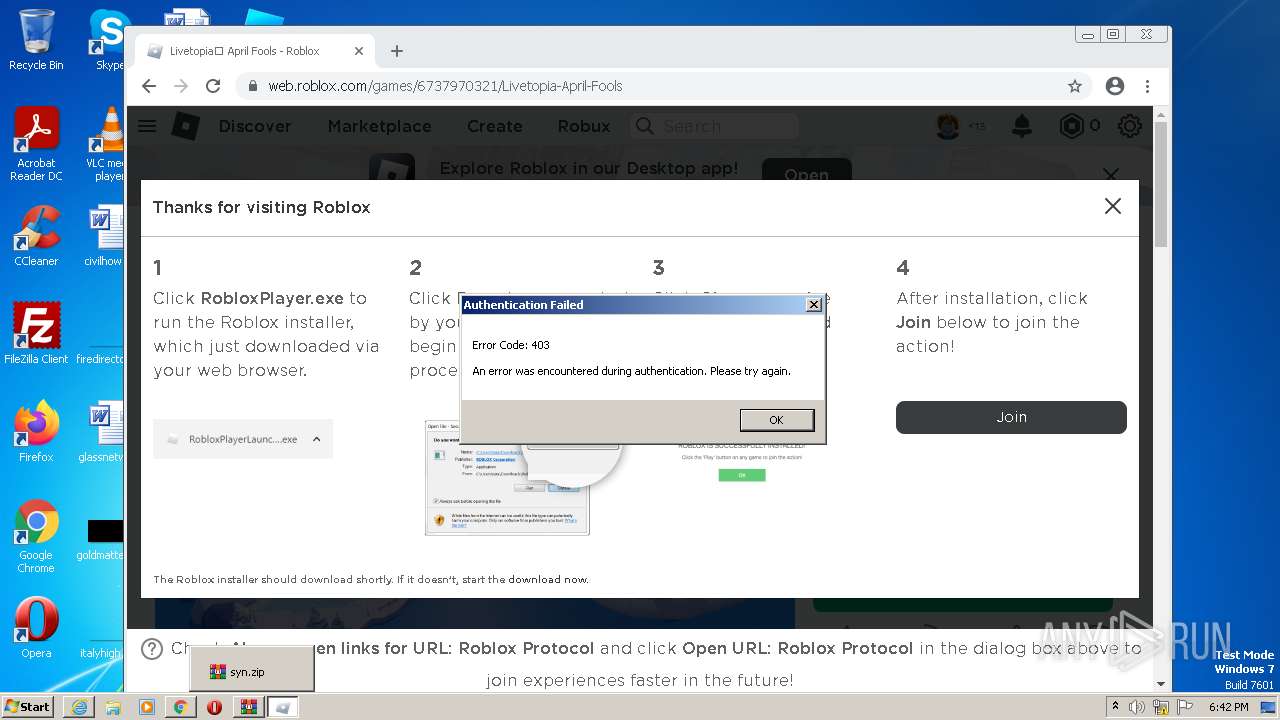
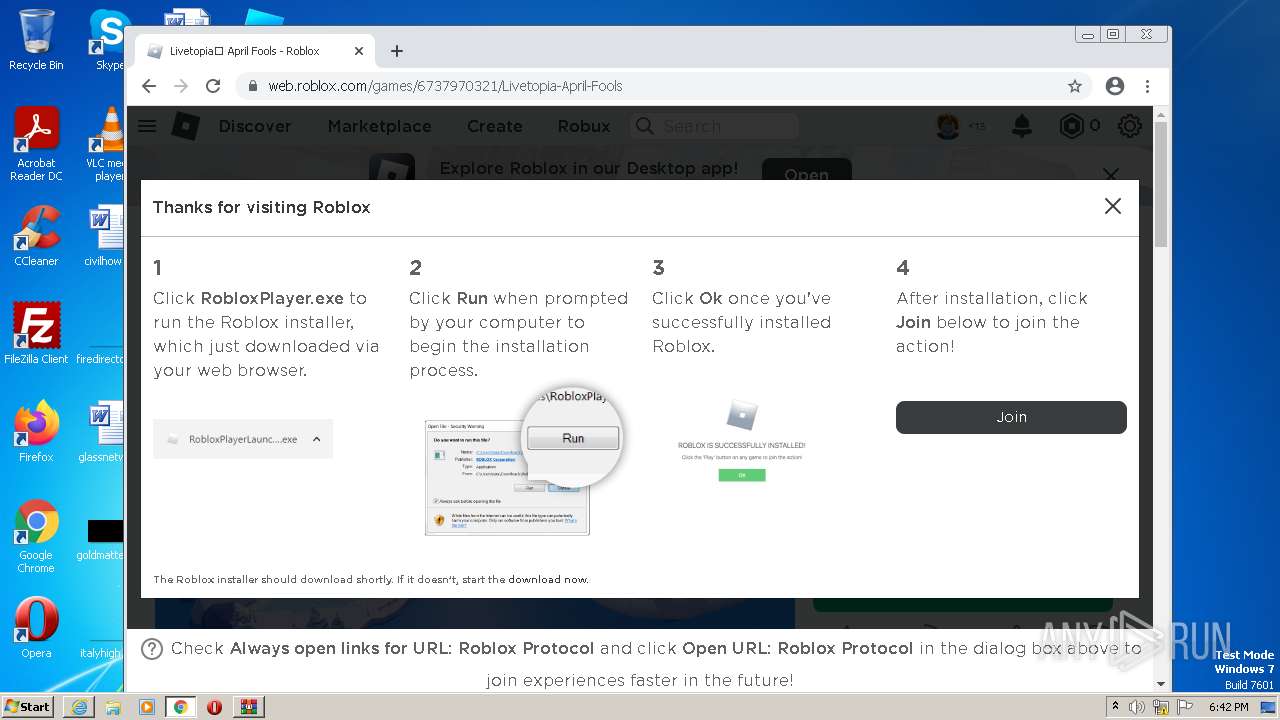
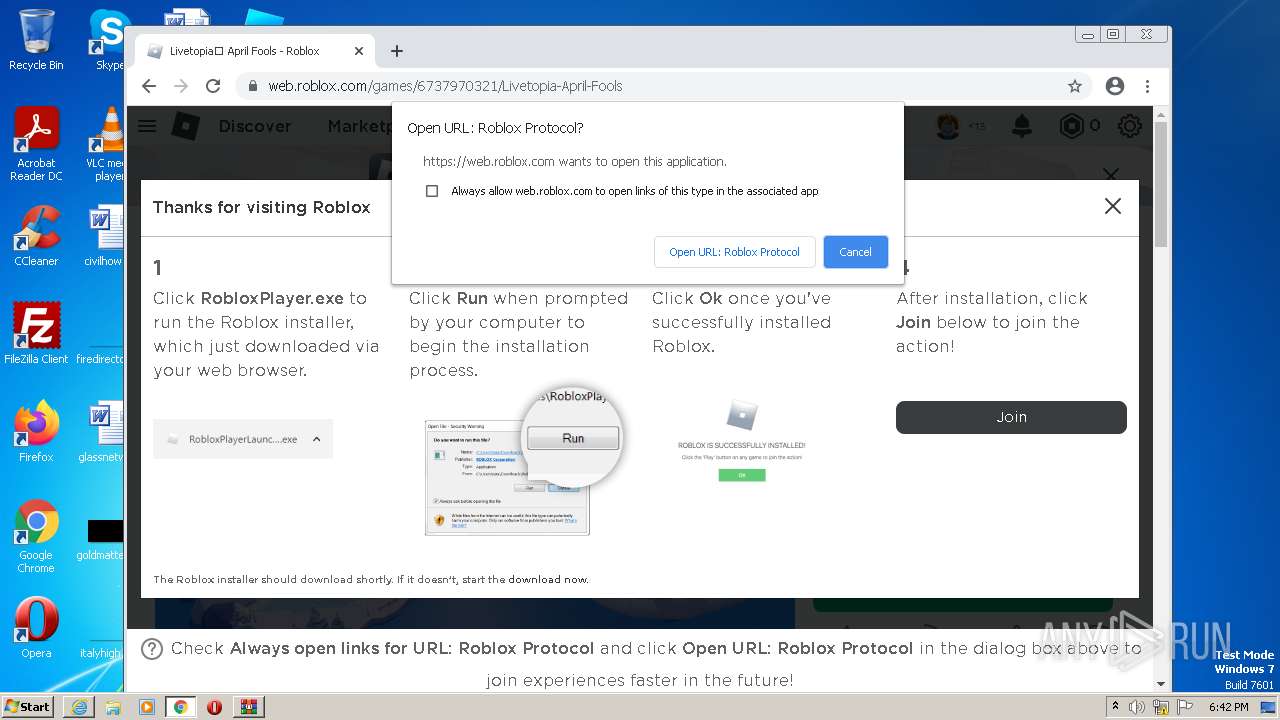
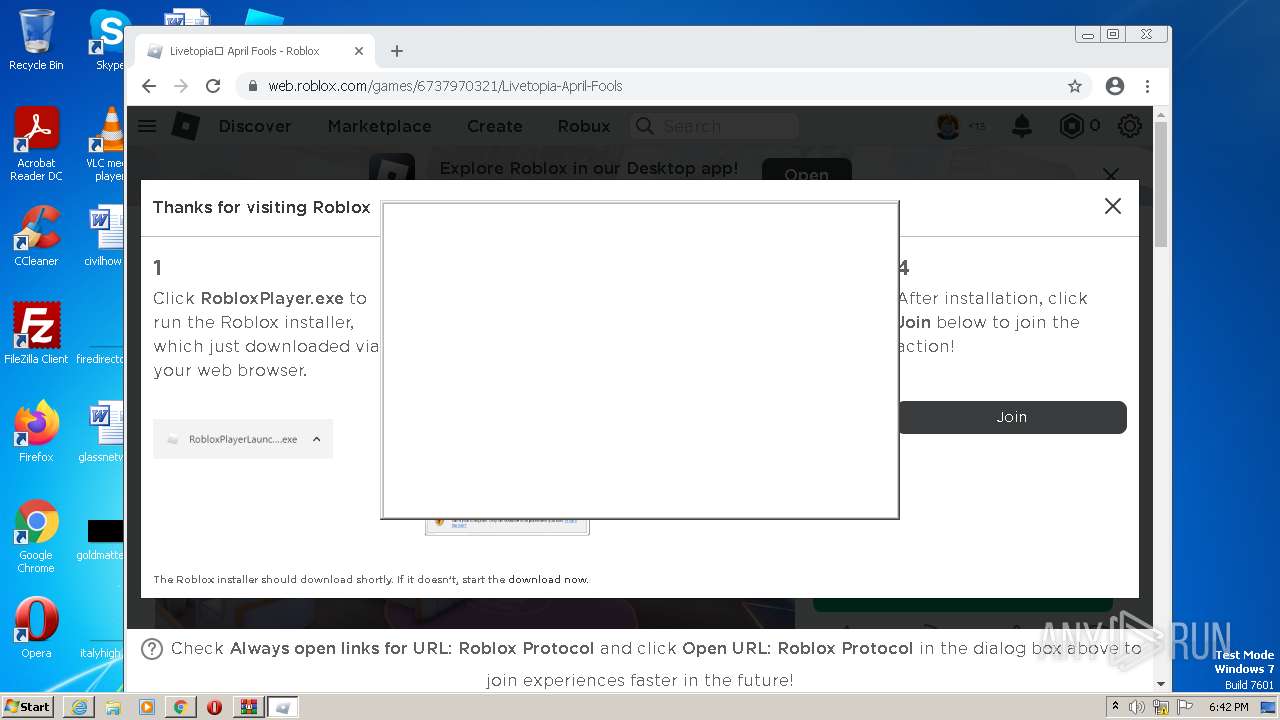
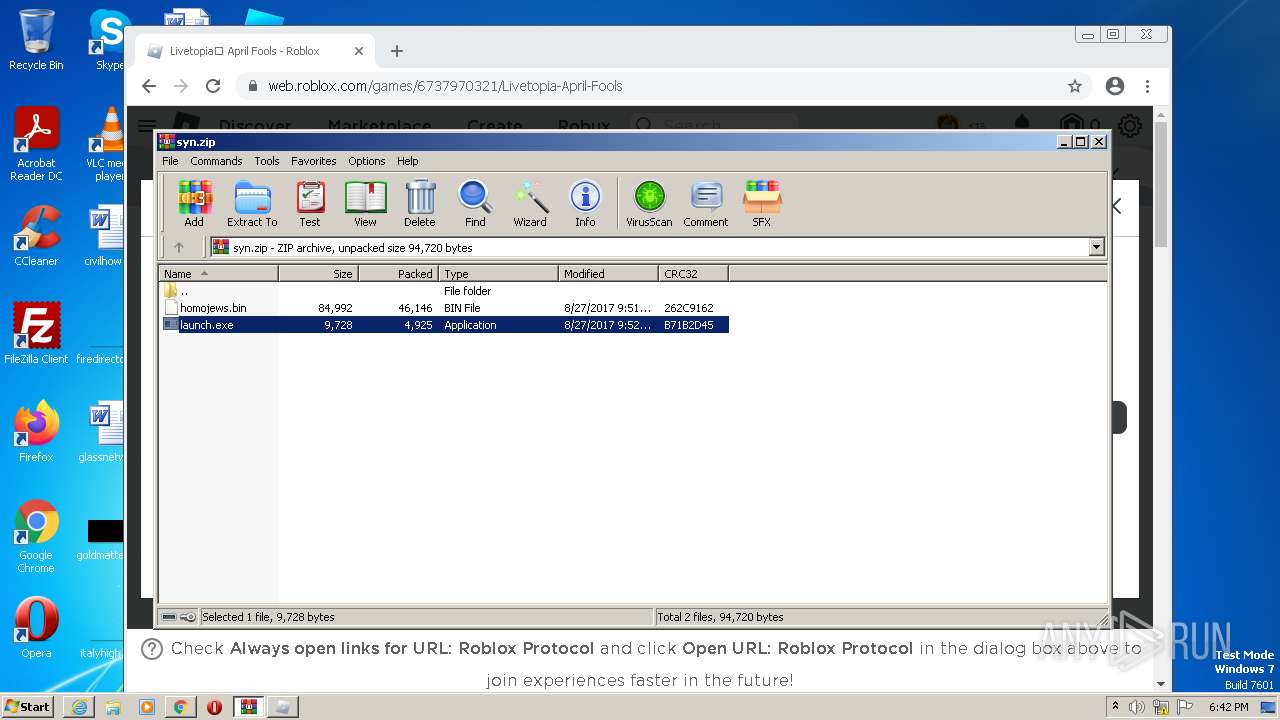
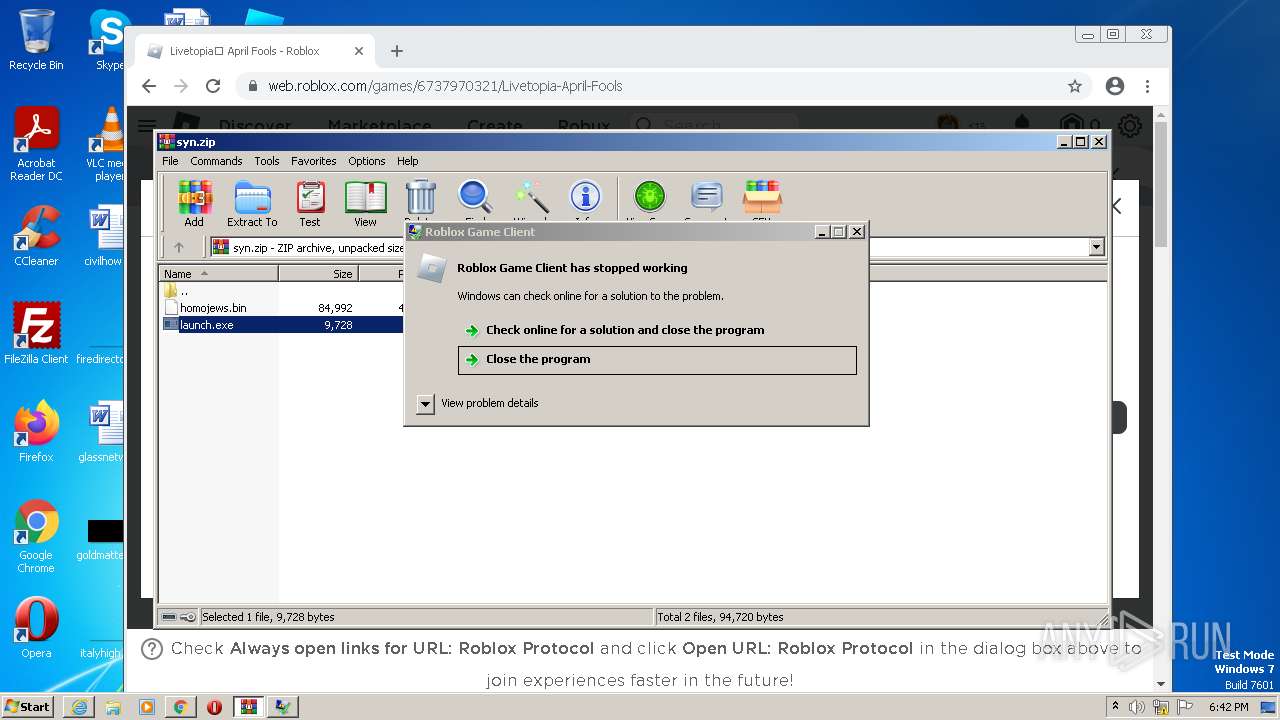
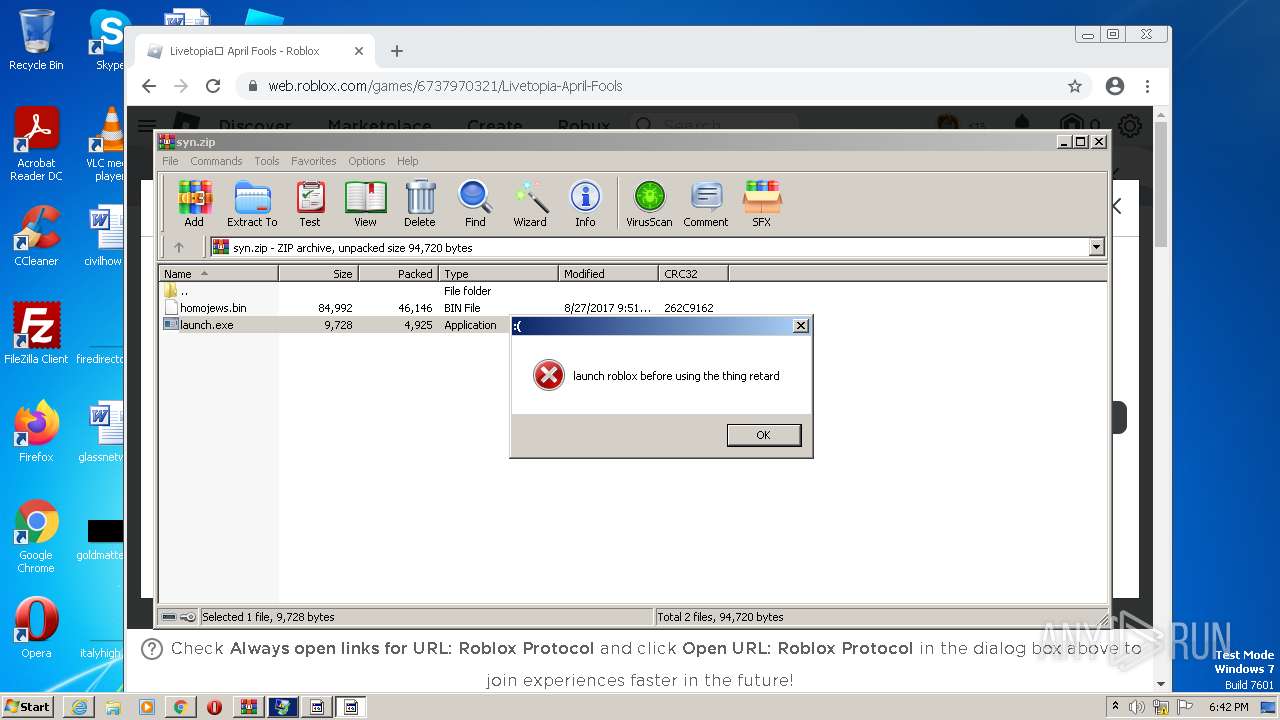
| URL: | https://cdn-141.anonfiles.com/T6i9u8ibz6/f2ee03fb-1680371123/syn.zip |
| Full analysis: | https://app.any.run/tasks/a31f82e0-bbb4-47a1-8ad5-b6922a4628b7 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 17:38:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 26BBEF885DE9A4A55A402B842E1B7FB1 |
| SHA1: | 6D1ADE9F3C505723E8216A8284372E8631B53FB1 |
| SHA256: | 96BCEB018F7185D27FB6C850144D9439987AEA1CC7E7B752A24057355BFE953C |
| SSDEEP: | 3:N8cFROLD026xbY/WbIUKC4:2cFQLQ269IH |
MALICIOUS
Application was dropped or rewritten from another process
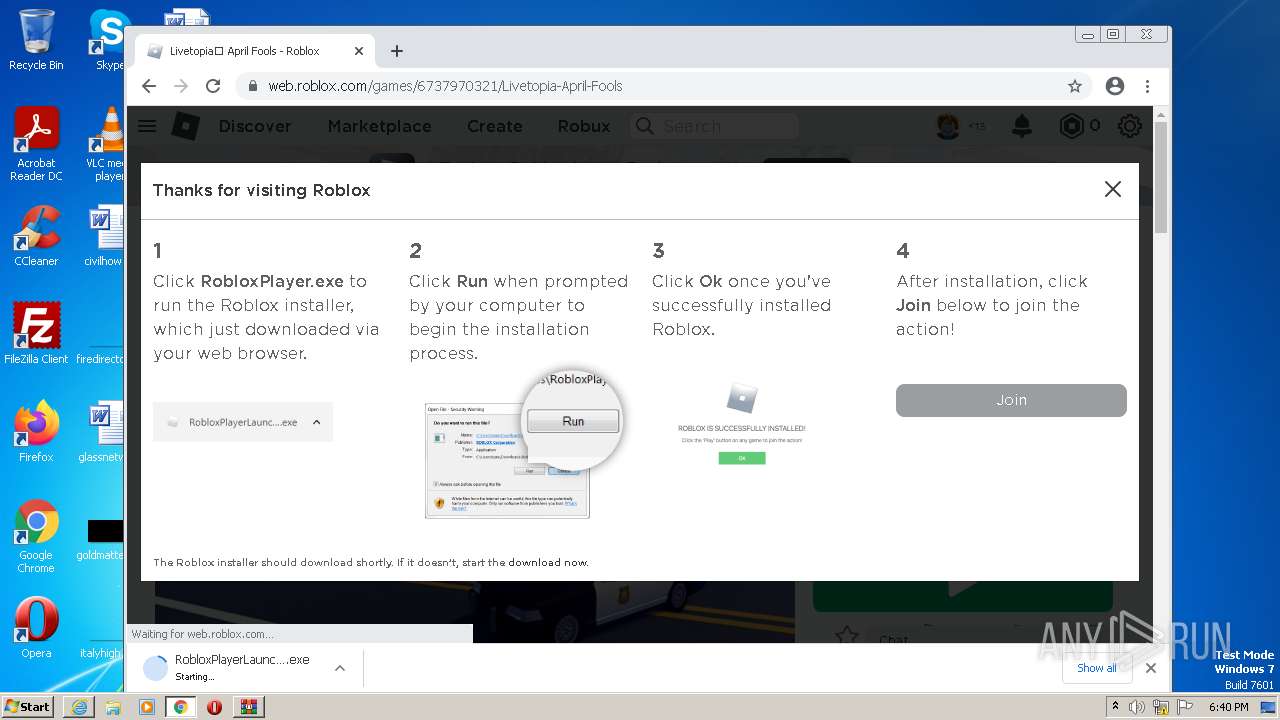
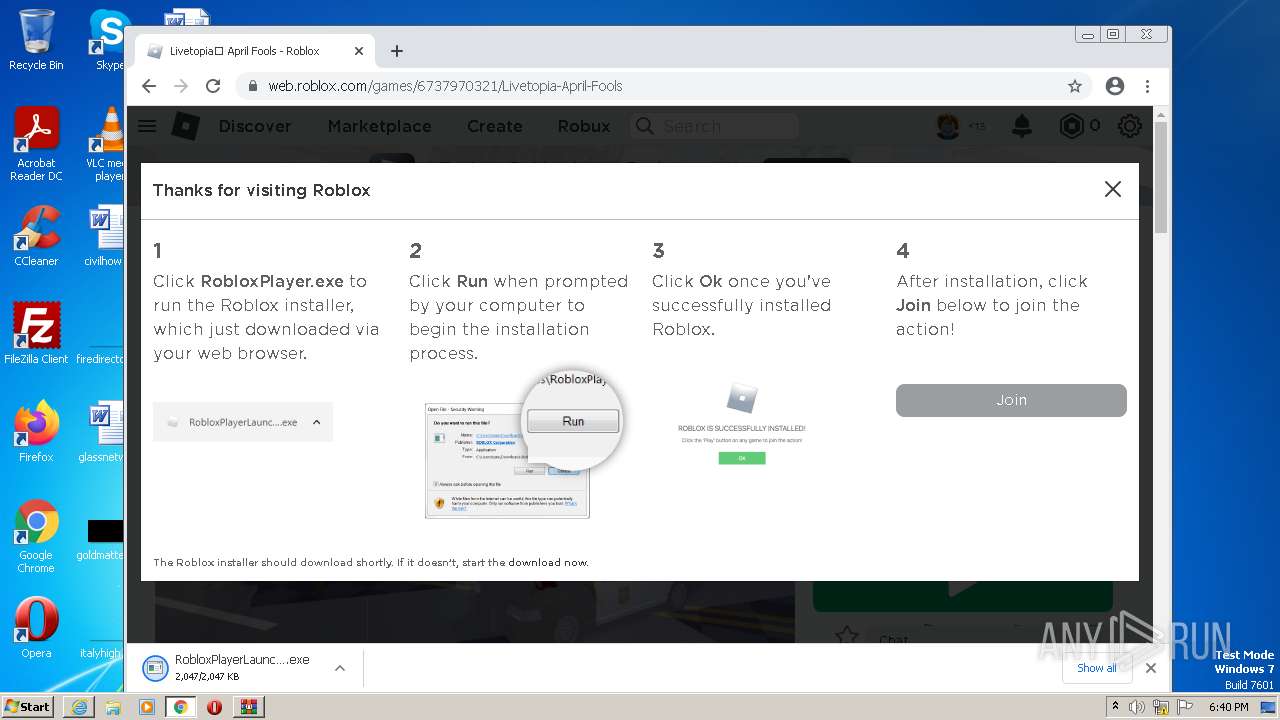
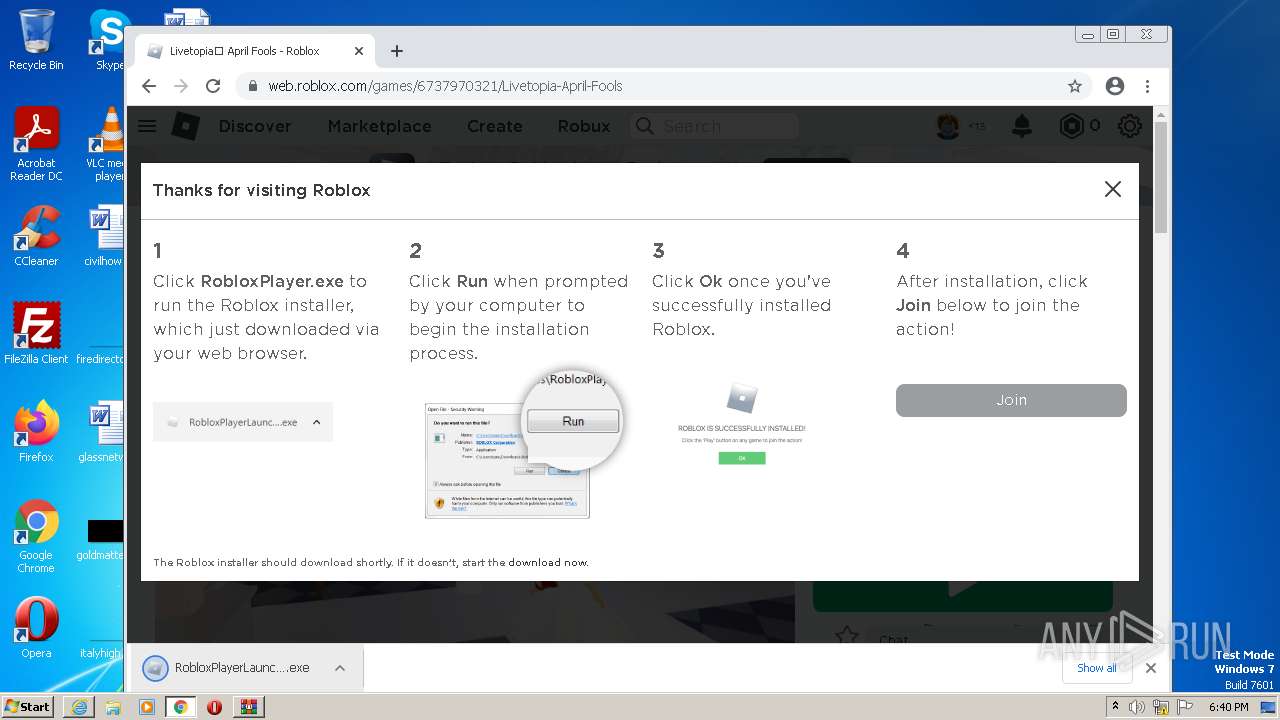
- RobloxPlayerLauncher.exe (PID: 2180)
- launch.exe (PID: 3352)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- launch.exe (PID: 3480)
- launch.exe (PID: 3384)
- launch.exe (PID: 3392)
- launch.exe (PID: 1416)
- launch.exe (PID: 2560)
Actions looks like stealing of personal data
- RobloxPlayerLauncher.exe (PID: 2180)
SUSPICIOUS
Reads security settings of Internet Explorer
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
Reads settings of System Certificates
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
Reads the Internet Settings
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- RobloxPlayerBeta.exe (PID: 2436)
Checks Windows Trust Settings
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
Application launched itself
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3820)
Cleans NTFS data stream (Zone Identifier)
- RobloxPlayerLauncher.exe (PID: 2180)
Executable content was dropped or overwritten
- RobloxPlayerLauncher.exe (PID: 2180)
INFO
Create files in a temporary directory
- iexplore.exe (PID: 2672)
- iexplore.exe (PID: 3112)
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- chrome.exe (PID: 3680)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
The process uses the downloaded file
- WinRAR.exe (PID: 1272)
- chrome.exe (PID: 3024)
- iexplore.exe (PID: 2672)
- chrome.exe (PID: 3680)
- RobloxPlayerLauncher.exe (PID: 2180)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1272)
- chrome.exe (PID: 3680)
Application launched itself
- iexplore.exe (PID: 2672)
- chrome.exe (PID: 3680)
The process checks LSA protection
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerBeta.exe (PID: 2436)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- RobloxPlayerBeta.exe (PID: 2756)
Checks supported languages
- launch.exe (PID: 3352)
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerBeta.exe (PID: 2436)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- launch.exe (PID: 3480)
- launch.exe (PID: 3392)
- launch.exe (PID: 3384)
- launch.exe (PID: 1416)
- RobloxPlayerBeta.exe (PID: 2756)
- launch.exe (PID: 2560)
Reads the machine GUID from the registry
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerBeta.exe (PID: 2436)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- RobloxPlayerBeta.exe (PID: 2756)
Manual execution by a user
- chrome.exe (PID: 3680)
Reads the computer name
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerBeta.exe (PID: 2436)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- RobloxPlayerBeta.exe (PID: 2756)
Checks proxy server information
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerLauncher.exe (PID: 3956)
- RobloxPlayerBeta.exe (PID: 2436)
Creates files or folders in the user directory
- RobloxPlayerLauncher.exe (PID: 4092)
- RobloxPlayerLauncher.exe (PID: 3148)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerBeta.exe (PID: 2436)
- RobloxPlayerLauncher.exe (PID: 3820)
- RobloxPlayerBeta.exe (PID: 2756)
- RobloxPlayerLauncher.exe (PID: 3956)
- RobloxPlayerLauncher.exe (PID: 2180)
Process checks computer location settings
- RobloxPlayerLauncher.exe (PID: 2180)
- RobloxPlayerLauncher.exe (PID: 2844)
- RobloxPlayerBeta.exe (PID: 2436)
- RobloxPlayerBeta.exe (PID: 2756)
- RobloxPlayerLauncher.exe (PID: 3820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
114
Monitored processes
68
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3540 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2764 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
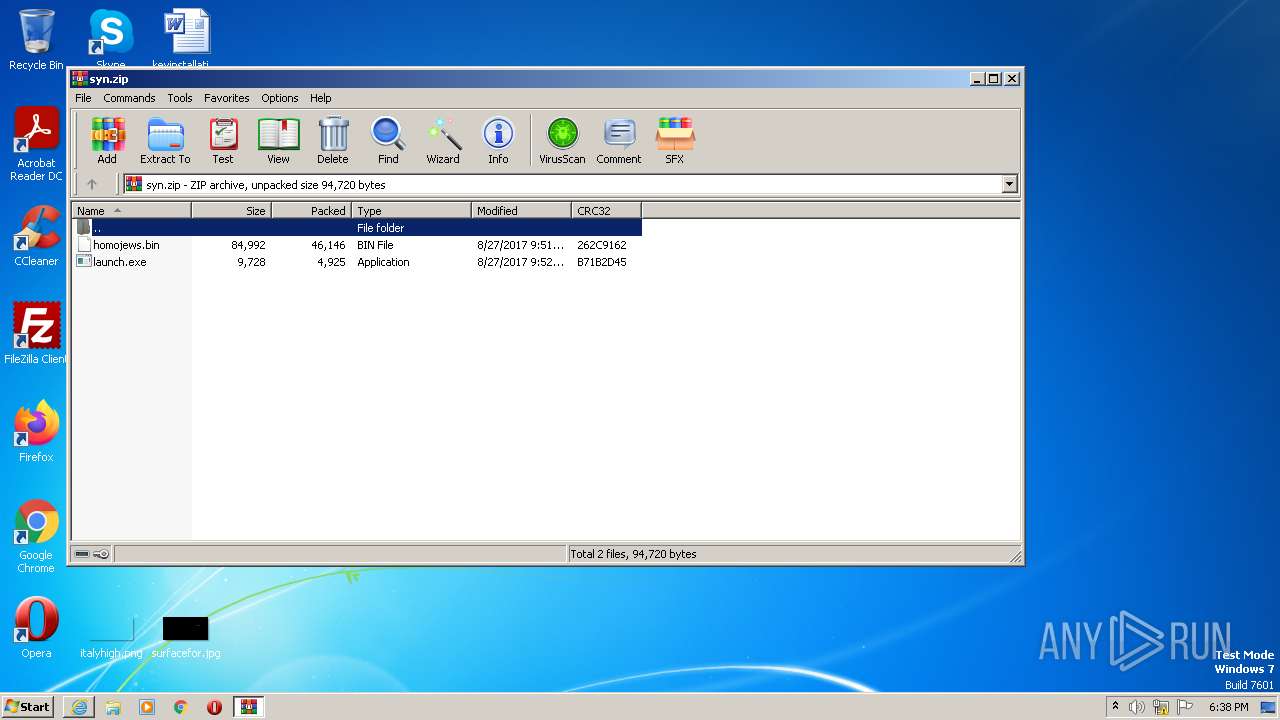
| 1272 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\syn.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1416 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1272.44236\launch.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1272.44236\launch.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3588 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1052 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3004 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3000 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3204 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1072,248820016686747480,5825033914899944025,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1400 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
124 346
Read events
123 312
Write events
1 012
Delete events
22
Modification events
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
38
Suspicious files
950
Text files
820
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3680 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-64286C32-E60.pma | — | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{03286CAB-D0B4-11ED-94DF-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\Downloads\syn.zip.ou2lfpy.partial | compressed | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2672 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6538CE4411208967.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\syn[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 2672 | iexplore.exe | C:\Users\admin\Downloads\syn.zip | compressed | |
MD5:— | SHA256:— | |||
| 3112 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2672 | iexplore.exe | C:\Users\admin\Downloads\syn.zip.ou2lfpy.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
125
DNS requests
103
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
2672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 779 b | whitelisted |
2672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
2672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2180 | RobloxPlayerLauncher.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 65.1 Kb | whitelisted |
3112 | iexplore.exe | GET | 200 | 23.37.41.57:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
3112 | iexplore.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ce6002017abddbbd | US | compressed | 61.1 Kb | whitelisted |
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | crx | 2.81 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3112 | iexplore.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
3112 | iexplore.exe | 23.37.41.57:80 | x1.c.lencr.org | AKAMAI-AS | DE | suspicious |
3112 | iexplore.exe | 195.96.151.34:443 | cdn-141.anonfiles.com | Svea Hosting AB | SE | unknown |
3112 | iexplore.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
— | — | 142.250.185.77:443 | accounts.google.com | GOOGLE | US | suspicious |
— | — | 142.250.185.206:443 | clients2.google.com | GOOGLE | US | whitelisted |
2128 | chrome.exe | 142.250.185.193:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 172.217.18.3:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2672 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn-141.anonfiles.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 2023-04-01T17:42:29.106Z,0.106972,0418,6 [FLog::ClientRunInfo] The channel is production |
RobloxPlayerBeta.exe | 2023-04-01T17:42:29.106Z,0.106972,0418,6 [FLog::ClientRunInfo] The base url is http://www.roblox.com/ |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | |
RobloxPlayerBeta.exe | 2023-04-01T17:42:29.106Z,0.106972,0418,6 [FLog::ClientRunInfo] The channel is production |
RobloxPlayerBeta.exe | 2023-04-01T17:42:29.106Z,0.106972,0418,6 [FLog::ClientRunInfo] RobloxGitHash: 6867c2d3365d29f9b40f61bb5c51a4bc7df908c0 |