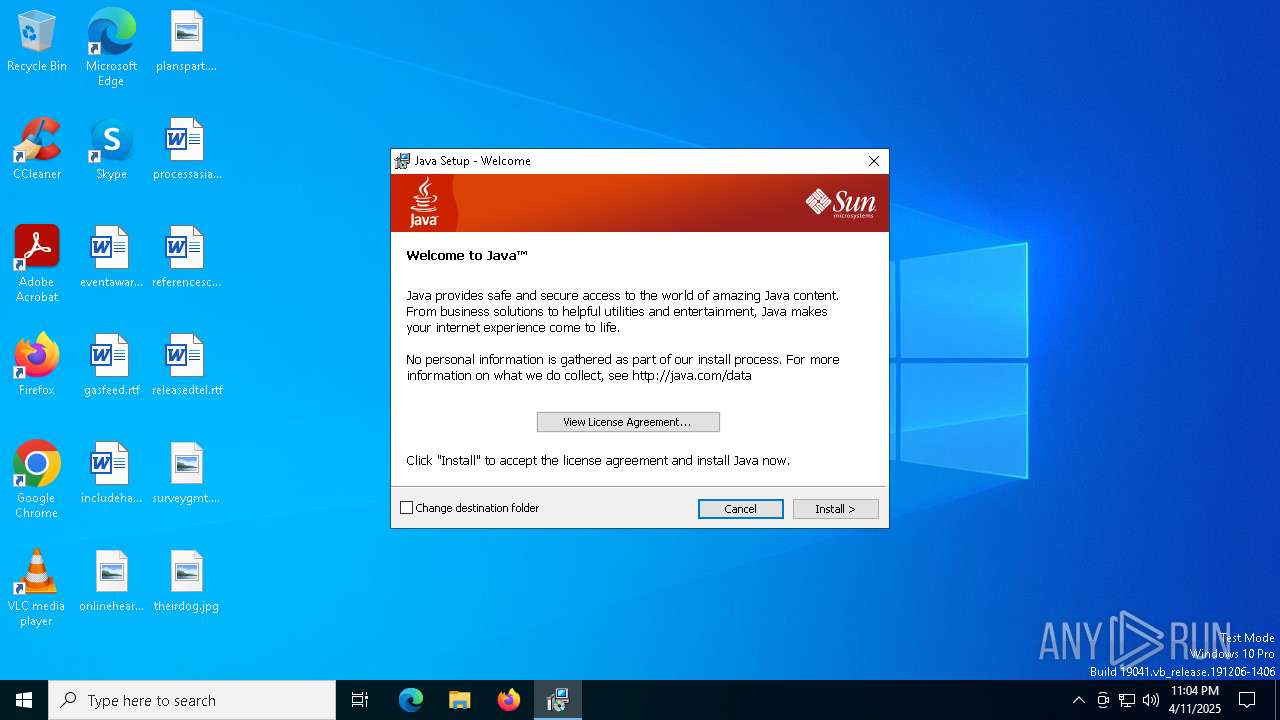
| File name: | jre-6u20-windows-i586-s.exe |
| Full analysis: | https://app.any.run/tasks/4c724fd5-f20d-4b17-9985-84d75b4b1d47 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2025, 23:04:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 71FDDE020A4920F55C96E1121A1DBD4A |
| SHA1: | 308C860F5A8F3BCE26D4AB96D85DA4426993189B |
| SHA256: | 96A86B09BCD3546832C1228DD9CD34F9FE6C3CB3FD478BFB4126C8FA88CE2C51 |
| SSDEEP: | 98304:hFWtc8kiaBkNdElkfpwfCGIWUNQYng4OwDKrsG5KlB2mmo0Zf2v5eqGBRss5B+5/:yN/9zPpB/mRlhdjXrxDyjkFQyLy |
MALICIOUS
Executing a file with an untrusted certificate
- unpack200.exe (PID: 4980)
- unpack200.exe (PID: 1324)
- unpack200.exe (PID: 1748)
- unpack200.exe (PID: 4448)
- unpack200.exe (PID: 6960)
- unpack200.exe (PID: 1228)
- javaw.exe (PID: 4452)
- javaw.exe (PID: 2852)
- unpack200.exe (PID: 6156)
- javaws.exe (PID: 3396)
- javaw.exe (PID: 6392)
- javaw.exe (PID: 4880)
Changes the autorun value in the registry
- msiexec.exe (PID: 2560)
SUSPICIOUS
Checks for Java to be installed
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 6816)
- msiexec.exe (PID: 2560)
- javaws.exe (PID: 3396)
- msiexec.exe (PID: 7052)
- javaw.exe (PID: 4880)
Adds/modifies Windows certificates
- msiexec.exe (PID: 6248)
Executable content was dropped or overwritten
- jre-6u20-windows-i586-s.exe (PID: 7148)
- zipper.exe (PID: 928)
Reads security settings of Internet Explorer
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 2560)
- msiexec.exe (PID: 7052)
- javaw.exe (PID: 4880)
Starts application with an unusual extension
- msiexec.exe (PID: 6248)
There is functionality for taking screenshot (YARA)
- jre-6u20-windows-i586-s.exe (PID: 7148)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6816)
Executes as Windows Service
- VSSVC.exe (PID: 5964)
The process drops C-runtime libraries
- zipper.exe (PID: 928)
- msiexec.exe (PID: 2560)
Process drops legitimate windows executable
- msiexec.exe (PID: 2560)
- zipper.exe (PID: 928)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2288)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 5084)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 2560)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 2852)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 684)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 6876)
INFO
The sample compiled with english language support
- jre-6u20-windows-i586-s.exe (PID: 7148)
- zipper.exe (PID: 928)
- msiexec.exe (PID: 2560)
Checks supported languages
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 7052)
- MSIF552.tmp (PID: 1912)
- msiexec.exe (PID: 6816)
- msiexec.exe (PID: 5556)
- msiexec.exe (PID: 2560)
- zipper.exe (PID: 928)
- unpack200.exe (PID: 4980)
- unpack200.exe (PID: 1748)
- unpack200.exe (PID: 1324)
- unpack200.exe (PID: 4448)
- unpack200.exe (PID: 6156)
- unpack200.exe (PID: 1228)
- unpack200.exe (PID: 6960)
- javaw.exe (PID: 4452)
- javaw.exe (PID: 2852)
- javaw.exe (PID: 6392)
- javaws.exe (PID: 3396)
- javaw.exe (PID: 4880)
- jaureg.exe (PID: 2332)
Creates files or folders in the user directory
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 6248)
- javaw.exe (PID: 2852)
- msiexec.exe (PID: 7052)
Reads the computer name
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 6816)
- msiexec.exe (PID: 7052)
- msiexec.exe (PID: 5556)
- msiexec.exe (PID: 2560)
- javaw.exe (PID: 2852)
- javaw.exe (PID: 4880)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6248)
- WMIC.exe (PID: 924)
- WMIC.exe (PID: 2332)
- WMIC.exe (PID: 6240)
- WMIC.exe (PID: 2656)
- WMIC.exe (PID: 6156)
Create files in a temporary directory
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 2560)
- javaw.exe (PID: 4452)
- javaw.exe (PID: 6392)
- javaw.exe (PID: 4880)
- javaw.exe (PID: 2852)
Reads the software policy settings
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 6816)
- msiexec.exe (PID: 7052)
- slui.exe (PID: 496)
- jre-6u20-windows-i586-s.exe (PID: 7148)
- javaw.exe (PID: 4880)
- slui.exe (PID: 6372)
Checks proxy server information
- jre-6u20-windows-i586-s.exe (PID: 7148)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 7052)
- javaw.exe (PID: 4880)
- slui.exe (PID: 6372)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 6816)
- msiexec.exe (PID: 2560)
Manages system restore points
- SrTasks.exe (PID: 6136)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6816)
- javaw.exe (PID: 2852)
- msiexec.exe (PID: 7052)
- javaw.exe (PID: 4880)
- jre-6u20-windows-i586-s.exe (PID: 7148)
Creates a software uninstall entry
- msiexec.exe (PID: 6816)
Creates files in the program directory
- zipper.exe (PID: 928)
- unpack200.exe (PID: 4980)
- unpack200.exe (PID: 1324)
- unpack200.exe (PID: 1748)
- unpack200.exe (PID: 4448)
- unpack200.exe (PID: 6156)
- unpack200.exe (PID: 1228)
- unpack200.exe (PID: 6960)
- javaw.exe (PID: 4452)
- javaw.exe (PID: 2852)
Reads the time zone
- javaw.exe (PID: 4880)
- javaw.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (38.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (28.2) |
| .exe | | | Win64 Executable (generic) (25) |
| .exe | | | Win32 Executable (generic) (4) |
| .exe | | | Generic Win/DOS Executable (1.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:04:13 03:22:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 65536 |
| InitializedDataSize: | 16461824 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9717 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.200.2 |
| ProductVersionNumber: | 6.0.200.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sun Microsystems, Inc. |
| FileDescription: | Java(TM) Platform SE binary |
| FileVersion: | 6.0.200.2 |
| FullVersion: | 1.6.0_20-b02 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2004 |
| OriginalFileName: | jinstall.exe |
| ProductName: | Java(TM) Platform SE 6 U20 |
| ProductVersion: | 6.0.200.2 |
Total processes
188
Monitored processes
46
Malicious processes
4
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | cmd /C WMIC bios get serialnumber | C:\Windows\SysWOW64\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | WMIC computersystem get model | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | "C:\Program Files (x86)\Java\jre6\zipper.exe" "C:\Program Files (x86)\Java\jre6\core.zip" "C:\Program Files (x86)\Java\jre6\" "C:\Users\admin\AppData\Local\Temp\java_install.log" | C:\Program Files (x86)\Java\jre6\zipper.exe | msiexec.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\Java\jre6\bin\unpack200.exe" -r -v -l "C:\Users\admin\AppData\Local\Temp\java_install.log" "C:\Program Files (x86)\Java\jre6\lib\charsets.pack" "C:\Program Files (x86)\Java\jre6\lib\charsets.jar" | C:\Program Files (x86)\Java\jre6\bin\unpack200.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Sun Microsystems, Inc. Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 6.0.200.2 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Java\jre6\bin\unpack200.exe" -r -v -l "C:\Users\admin\AppData\Local\Temp\java_install.log" "C:\Program Files (x86)\Java\jre6\lib\jsse.pack" "C:\Program Files (x86)\Java\jre6\lib\jsse.jar" | C:\Program Files (x86)\Java\jre6\bin\unpack200.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Sun Microsystems, Inc. Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 6.0.200.2 Modules
| |||||||||||||||
| 1748 | "C:\Program Files (x86)\Java\jre6\bin\unpack200.exe" -r -v -l "C:\Users\admin\AppData\Local\Temp\java_install.log" "C:\Program Files (x86)\Java\jre6\lib\plugin.pack" "C:\Program Files (x86)\Java\jre6\lib\plugin.jar" | C:\Program Files (x86)\Java\jre6\bin\unpack200.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Sun Microsystems, Inc. Integrity Level: SYSTEM Description: Java(TM) Platform SE binary Exit code: 0 Version: 6.0.200.2 Modules
| |||||||||||||||
| 1912 | "C:\Users\admin\AppData\Local\Temp\MSIF552.tmp" C:\Program Files (x86)\Java\jre6\;C | C:\Users\admin\AppData\Local\Temp\MSIF552.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Sun Microsystems, Inc. Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 6.0.200.2 Modules
| |||||||||||||||
| 2236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2288 | cmd /C WMIC computersystem get model | C:\Windows\SysWOW64\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 271
Read events
15 167
Write events
1 024
Delete events
80
Modification events
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Country |
Value: DE | |||
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | PostStatusUrl |
Value: https://sjremetrics.java.com/b/ss//6 | |||
| (PID) Process: | (7148) jre-6u20-windows-i586-s.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Method |
Value: joff-s | |||
| (PID) Process: | (6248) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6248) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 85371CA6E550143DCE2803471BDE3A09E8F8770F |
Value: | |||
| (PID) Process: | (6248) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\85371CA6E550143DCE2803471BDE3A09E8F8770F |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000A2339B4C747873D46CE7C1F38DCB5CE91D00000001000000100000007173FA7247886438EB10B0F4E8A0CC181400000001000000140000001A21B4952B6293CE18B365EC9C0E934CB381E6D409000000010000002A000000302806082B0601050507030206082B0601050507030306082B0601050507030406082B060105050703010F0000000100000014000000D95944F5BD92127092218F9F02C719C42386B49903000000010000001400000085371CA6E550143DCE2803471BDE3A09E8F8770F190000000100000010000000B24F9926AFCB335D4349D24B71F41A6762000000010000002000000083CE3C1229688A593D485F81973C0F9195431EDA37CC5E36430E79C7A888638B0B000000010000001200000056006500720069005300690067006E0000006800000001000000080000000000876ACE99D101200000000100000006030000308203023082026B02107DD9FE07CFA81EB7107967FBA78934C6300D06092A864886F70D01010505003081C1310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E313C303A060355040B1333436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479202D204732313A3038060355040B1331286329203139393820566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D060355040B1316566572695369676E205472757374204E6574776F726B301E170D3938303531383030303030305A170D3238303830313233353935395A3081C1310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E313C303A060355040B1333436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479202D204732313A3038060355040B1331286329203139393820566572695369676E2C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D060355040B1316566572695369676E205472757374204E6574776F726B30819F300D06092A864886F70D010101050003818D0030818902818100CC5ED1115D5C69D0ABD3B96A4C991F5998308E168520466D473FD4852084E16DB3F8A4ED0CF1170F3BF9A7F925D7C1CF8463F27C63CFA247F2C65B338E64400468C180B9641C4577C7D86EF595293C50E834D7781FA8BA6D4391958F45575E7EC5FBCAA404EBEA973754306FBB01473233CDDC579B646961F89B1D1C894F5C670203010001300D06092A864886F70D010105050003818100514DCDBE5CCB98199C15B20139782E4D0F67707099C6105A94A4534D546D2BAF0D5D408B64D3D7EEDE5661925FA6C41D106136D32C273CE82909B9116474CCB5739F1C48A9BC6101EEE217A60CE340083B0EE7EB44732A9AF16992EF7114C339AC71A791096FE47106B3BA5957267900F6F80DA2333028D4AA58A09D9D6991FD | |||
Executable files
129
Suspicious files
510
Text files
76
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7148 | jre-6u20-windows-i586-s.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\jre1.6.0_20\Data1.cab | — | |
MD5:— | SHA256:— | |||
| 6816 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7148 | jre-6u20-windows-i586-s.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:28C7EE12202907BD78FC086563538891 | SHA256:080D0224A0B4F30E222CA35BB48387776BE1EB08B19BAD79FF4D13BDBBAFB6B4 | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E8974A4669383843486E5AFDB09650F5 | binary | |
MD5:91A28E55448AF4769C19D0247E421EB0 | SHA256:72D5DC6A00EE3637AB21E1D5B1C760780F09FC44B8119D2D86355B90403DD283 | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIEA23.tmp | executable | |
MD5:994D3CA9EDD427F612B77024570216B8 | SHA256:9A88F9E7125425BA6CE68C425B4395F54707C51A59EDF419185D2F1A38365EBF | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A92F33496848CFF4F115ED04BCDD933A_6C14F82F698E40985D569864739DB21B | binary | |
MD5:30942349C452923EA1689060C5A18ACF | SHA256:2E0A73BB40223D5C38B6EF317C4908511C124D9269D2FDC49BCC26D70928067F | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C554DCF706A5AAB8B360FAD227EAB9C7 | binary | |
MD5:4C7F9CF8C3ACD63223B8A9180E94AF37 | SHA256:65117DB12D365AB03A1BF49BDF2FE2553F74385D1CA0D6555148E7A29CC3CDF6 | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45781A86D7D79A4E3FE6F4DF8CDF171D_E0B7CDE0B6AB7ABECB214E5A7A028B64 | binary | |
MD5:03893CA70FB71233A9DFCE36511A1D59 | SHA256:2BC74A16E6FBDEB67623BC33C6F8D93488E62DF77E45D396EBAA0DD38002F92D | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45781A86D7D79A4E3FE6F4DF8CDF171D_E0B7CDE0B6AB7ABECB214E5A7A028B64 | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 6248 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIF63F.tmp | executable | |
MD5:994D3CA9EDD427F612B77024570216B8 | SHA256:9A88F9E7125425BA6CE68C425B4395F54707C51A59EDF419185D2F1A38365EBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
61
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7148 | jre-6u20-windows-i586-s.exe | GET | 200 | 2.22.242.227:80 | http://javadl-esd.sun.com/update/1.6.0/1.6.0_20-b02.xml | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7148 | jre-6u20-windows-i586-s.exe | HEAD | 200 | 2.16.168.111:80 | http://rps-svcs.sun.com/services/countrylookup | unknown | — | — | whitelisted |
6248 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTEemCaVgs8Tuh2B9fGVE0pKKNyzgQUTF%2BnNhcF4oZhIkk5jLmo40rgOBoCEC6utoKGY%2F7ZdVX4%2FiTzOxo%3D | unknown | — | — | whitelisted |
7148 | jre-6u20-windows-i586-s.exe | GET | 404 | 2.22.242.227:80 | http://javadl-esd.sun.com/update/1.6.0/sp-1.6.0_20-b02/sp1033.MST | unknown | — | — | whitelisted |
6248 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTEemCaVgs8Tuh2B9fGVE0pKKNyzgQUTF%2BnNhcF4oZhIkk5jLmo40rgOBoCEC6utoKGY%2F7ZdVX4%2FiTzOxo%3D | unknown | — | — | whitelisted |
6248 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://crl.verisign.com/pca3-g2.crl | unknown | — | — | whitelisted |
6248 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRODEXefhs%2FUZFum2o8YfzOFwceMwQUkz5j3yJ0BOBkhDHd2yOfDq%2B2TZMCEA89qsgV9niZmSI6gIO0S%2FU%3D | unknown | — | — | whitelisted |
6248 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRODEXefhs%2FUZFum2o8YfzOFwceMwQUkz5j3yJ0BOBkhDHd2yOfDq%2B2TZMCEA89qsgV9niZmSI6gIO0S%2FU%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4244 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7148 | jre-6u20-windows-i586-s.exe | 2.22.242.227:80 | javadl-esd.sun.com | Akamai International B.V. | DE | whitelisted |
7148 | jre-6u20-windows-i586-s.exe | 2.16.168.111:80 | rps-svcs.sun.com | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
javadl-esd.sun.com |
| whitelisted |
rps-svcs.sun.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
crl.verisign.com |
| whitelisted |