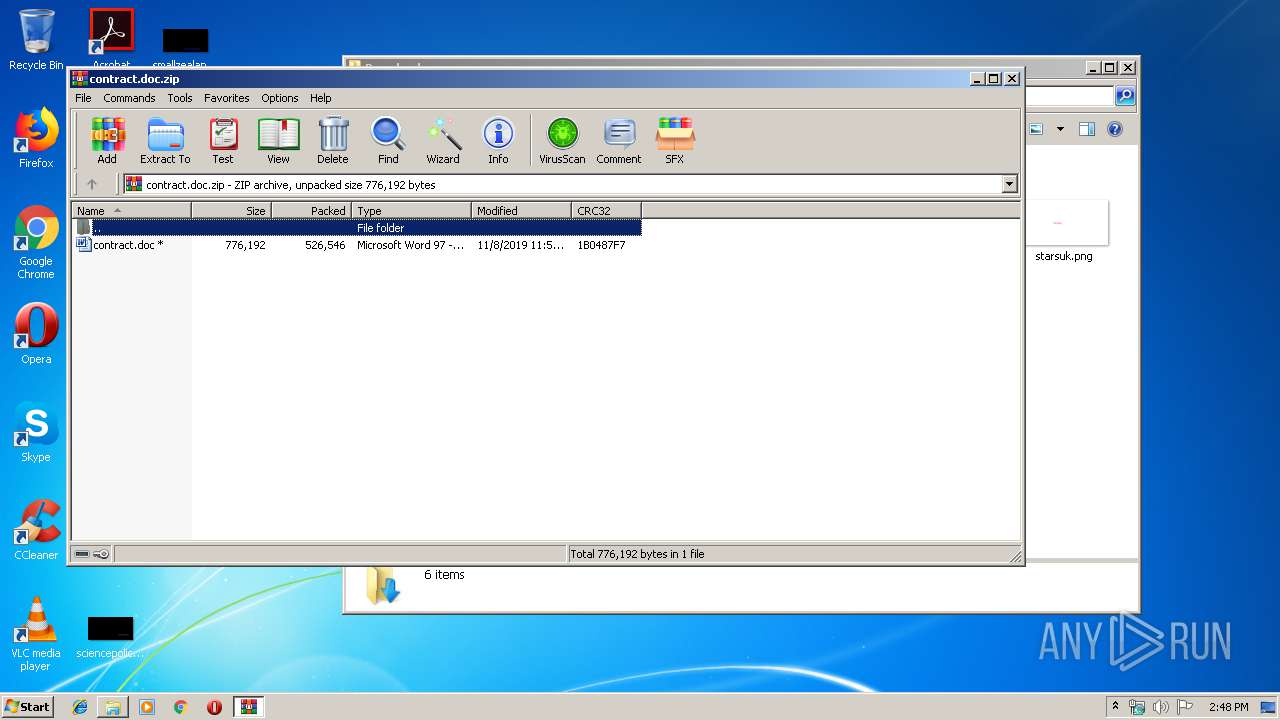
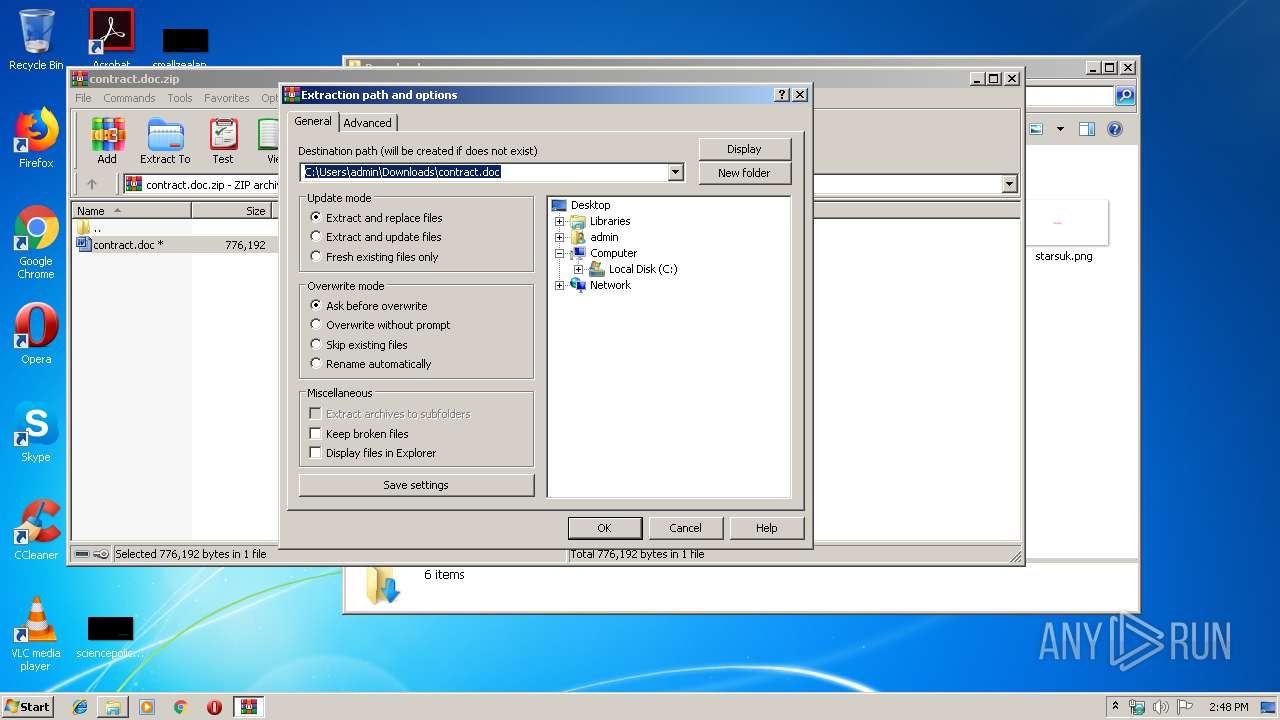
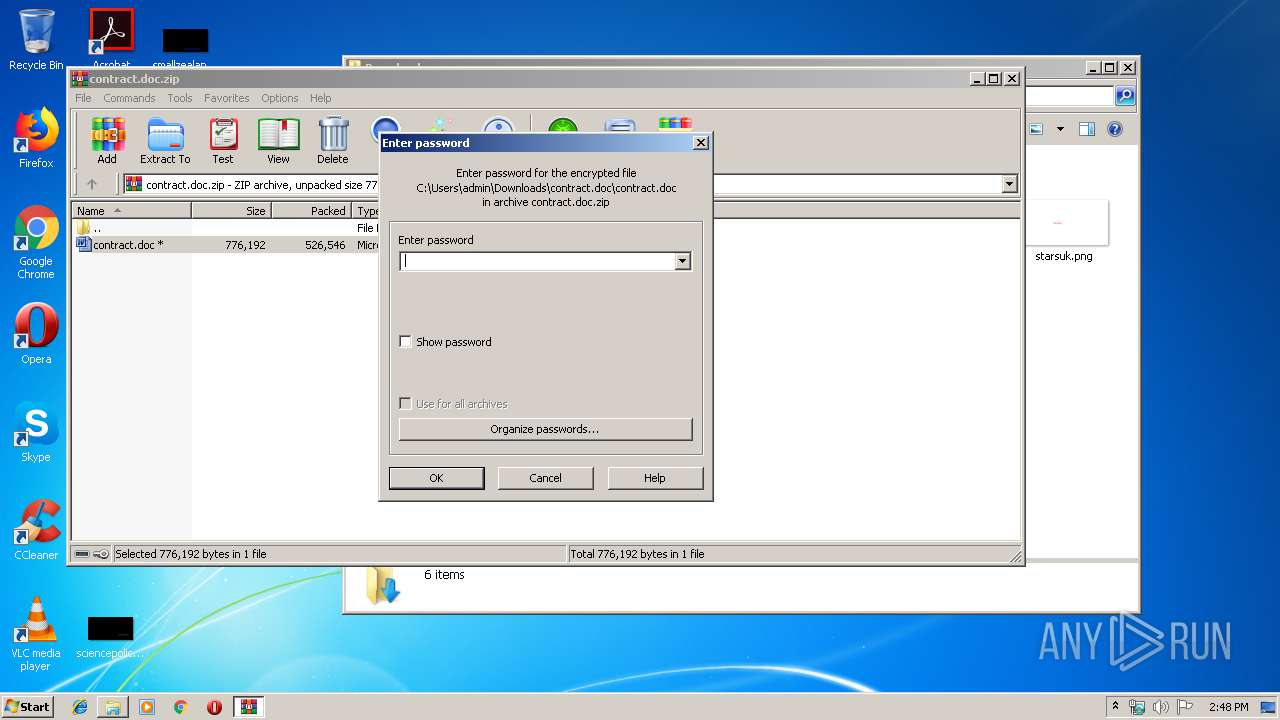
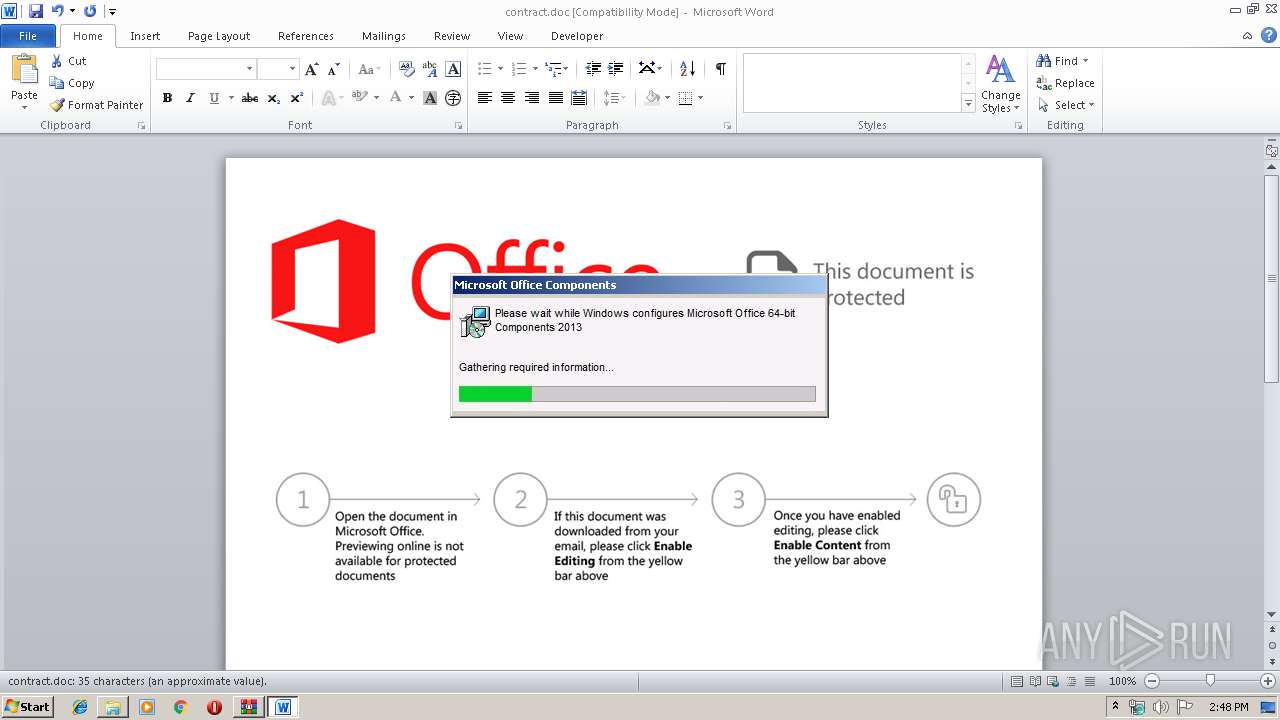
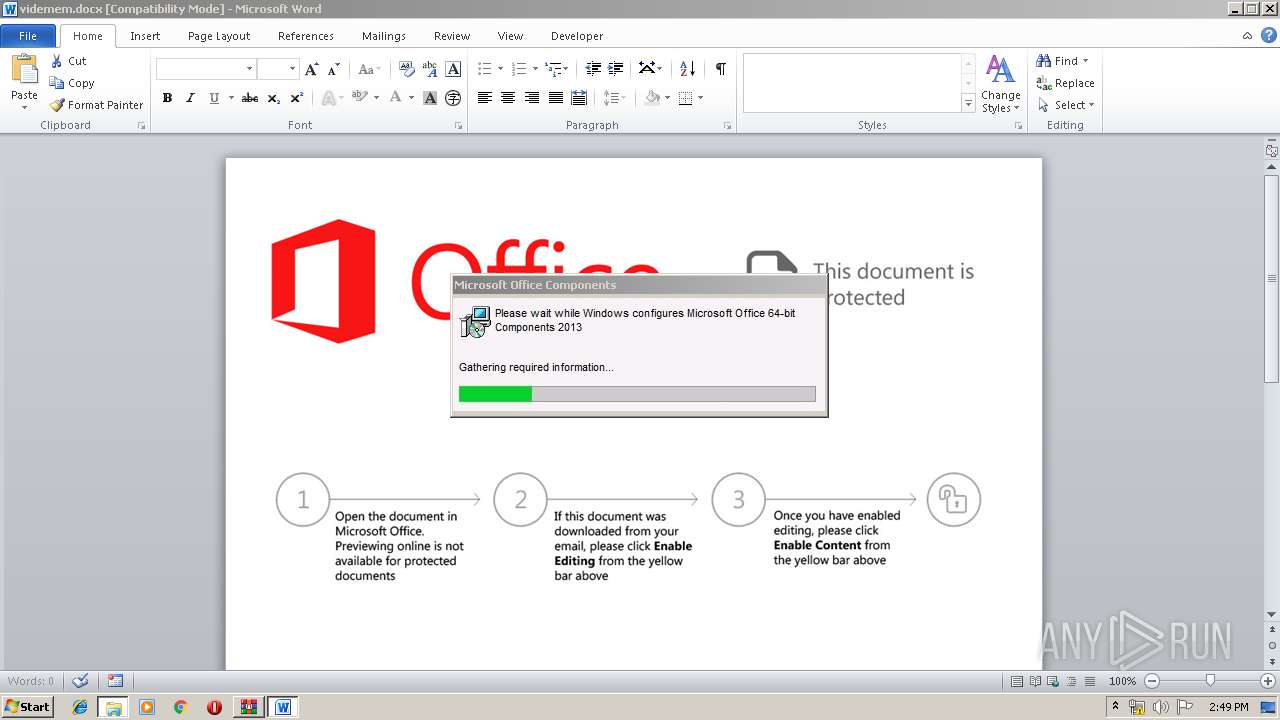
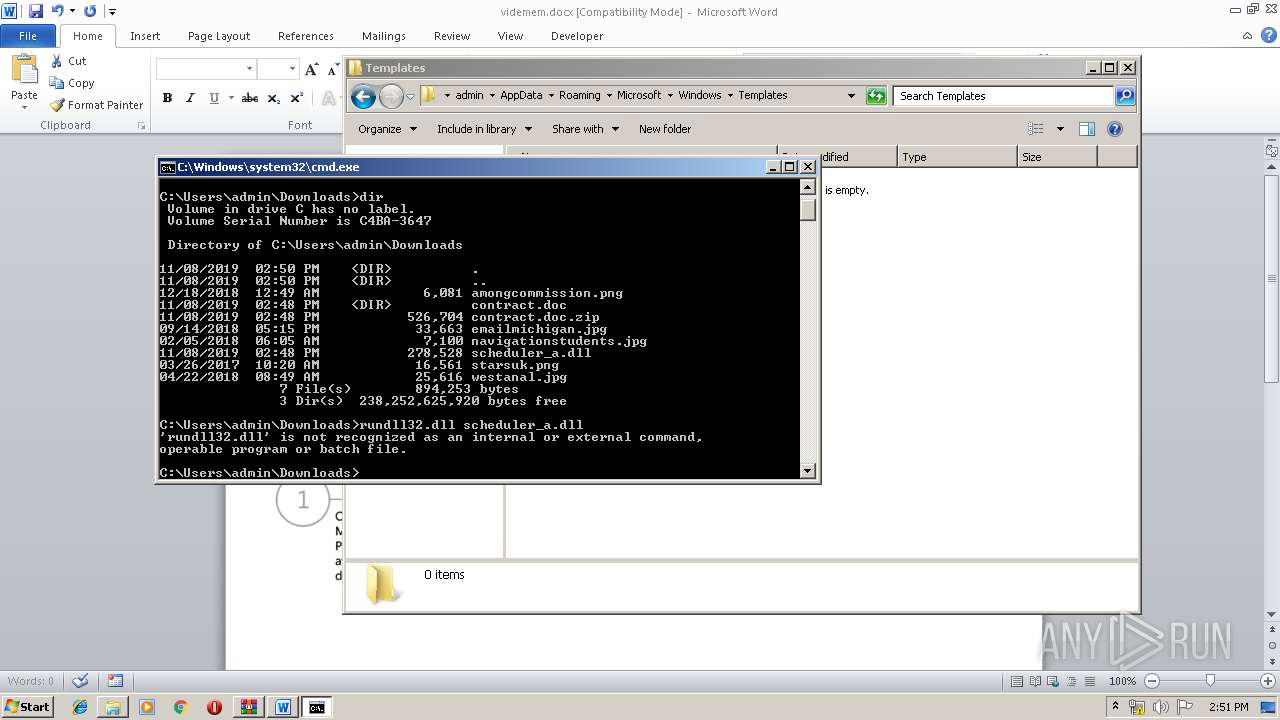
| File name: | contract.doc.zip |
| Full analysis: | https://app.any.run/tasks/4c450ea5-12ee-48ad-b28d-1f755bdf0b43 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 14:47:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 45866B1F7B671618CD1ADBE02EB4327D |
| SHA1: | D9AD19154F9A94E76D77E27634C6C0C9426758F2 |
| SHA256: | 969B6102A7F6C971336D6FE1F9492A63DDB6BF21FD59F43A0A7ECB46D70E2883 |
| SSDEEP: | 12288:t4WR+MU+6K6/+dzRMkgPi+F9aMZiBIE5AmWaDzrUyEcT:tTU+jbLMkI10TUyR |
MALICIOUS
Loads dropped or rewritten executable
- WINWORD.EXE (PID: 2488)
- explorer.exe (PID: 352)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2488)
Runs app for hidden code execution
- explorer.exe (PID: 352)
SUSPICIOUS
Reads Internet Cache Settings
- explorer.exe (PID: 352)
Creates files in the user directory
- explorer.exe (PID: 352)
- notepad++.exe (PID: 2028)
Executable content was dropped or overwritten
- explorer.exe (PID: 352)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 352)
INFO
Manual execution by user
- explorer.exe (PID: 2512)
- WINWORD.EXE (PID: 2488)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2488)
Starts Microsoft Office Application
- explorer.exe (PID: 352)
Creates files in the user directory
- WINWORD.EXE (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:11:08 12:52:27 |
| ZipCRC: | 0x1b0487f7 |
| ZipCompressedSize: | 526546 |
| ZipUncompressedSize: | 776192 |
| ZipFileName: | contract.doc |
Total processes
47
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\scheduler_a.dll" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2300 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\contract.doc.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\contract.doc\contract.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2512 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3228 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3440 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 026
Read events
2 887
Write events
1 080
Delete events
59
Modification events
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2300) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr |
Value: 00000000070000000900000055CE0500000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFE0EBB48C4396D50100000000 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 0000000033000000370000000DDA1200090000000D000000CC19050033003000380030003400360042003000410046003400410033003900430042000000460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C0049006E007400650072006E006500740020004500780070006C006F007200650072005C0051007500690063006B0020004C00610075006E00630068005C0055007300650072002000500069006E006E006500000000000034FF01F832FF01D4E3E1013DA94A7600000000FBFFFF7FF8E3E101987880574F8C6244BB6371042380B1090000000001100211FFFFFFFF000000000000000000000000534275066D42750653427506000000000000000000000000080000002E006C00E72F0A77A48EF37600000000AC032E0000002E00E72F0A77B08EF37603005B019604010000002E005B148D23020000006CE4E101B07F0A7744E5E1010000000058005A0044E5E1010200000010E5E101F2700A7791830A771C8FF37611000000B8453100B045310078192F00F8FD580600E500008F148D23B0E4E10182914A7600E5E101B4E4E10127954A7600000000CC90FF01DCE4E101CD944A76CC90FF0188E5E101408CFF01E1944A7600000000408CFF0188E5E101E4E4E101090000000D000000CC19050033003000380030003400360042003000410046003400410033003900430042000000460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C0049006E007400650072006E006500740020004500780070006C006F007200650072005C0051007500690063006B0020004C00610075006E00630068005C0055007300650072002000500069006E006E006500000000000034FF01F832FF01D4E3E1013DA94A7600000000FBFFFF7FF8E3E101987880574F8C6244BB6371042380B1090000000001100211FFFFFFFF000000000000000000000000534275066D42750653427506000000000000000000000000080000002E006C00E72F0A77A48EF37600000000AC032E0000002E00E72F0A77B08EF37603005B019604010000002E005B148D23020000006CE4E101B07F0A7744E5E1010000000058005A0044E5E1010200000010E5E101F2700A7791830A771C8FF37611000000B8453100B045310078192F00F8FD580600E500008F148D23B0E4E10182914A7600E5E101B4E4E10127954A7600000000CC90FF01DCE4E101CD944A76CC90FF0188E5E101408CFF01E1944A7600000000408CFF0188E5E101E4E4E101090000000D000000CC19050033003000380030003400360042003000410046003400410033003900430042000000460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E006500780065000000740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C0049006E007400650072006E006500740020004500780070006C006F007200650072005C0051007500690063006B0020004C00610075006E00630068005C0055007300650072002000500069006E006E006500000000000034FF01F832FF01D4E3E1013DA94A7600000000FBFFFF7FF8E3E101987880574F8C6244BB6371042380B1090000000001100211FFFFFFFF000000000000000000000000534275066D42750653427506000000000000000000000000080000002E006C00E72F0A77A48EF37600000000AC032E0000002E00E72F0A77B08EF37603005B019604010000002E005B148D23020000006CE4E101B07F0A7744E5E1010000000058005A0044E5E1010200000010E5E101F2700A7791830A771C8FF37611000000B8453100B045310078192F00F8FD580600E500008F148D23B0E4E10182914A7600E5E101B4E4E10127954A7600000000CC90FF01DCE4E101CD944A76CC90FF0188E5E101408CFF01E1944A7600000000408CFF0188E5E101E4E4E101 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 00000000070000000000000006000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFE0EBB48C4396D50100000000 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 0000000019000000000000001800000009000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C00460069007200650066006F0078002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000002E0098B1750600000000386E410348B32E03386E41030000000000000000A11100003626A70218D7AA0533AB0A7736C28A73030C0000102700001D000000315502004CD7AA05F8AA0A77315502003626A7026CD7AA0568A8FF01ECD7AA0500000000A3010000ACD700005327C6275CD7AA0582914A76ACD7AA0560D7AA0527954A7600000000F4ACFF0188D7AA05CD944A76F4ACFF0134D8AA0568A8FF01E1944A760000000068A8FF0134D8AA0590D7AA0509000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C00460069007200650066006F0078002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000002E0098B1750600000000386E410348B32E03386E41030000000000000000A11100003626A70218D7AA0533AB0A7736C28A73030C0000102700001D000000315502004CD7AA05F8AA0A77315502003626A7026CD7AA0568A8FF01ECD7AA0500000000A3010000ACD700005327C6275CD7AA0582914A76ACD7AA0560D7AA0527954A7600000000F4ACFF0188D7AA05CD944A76F4ACFF0134D8AA0568A8FF01E1944A760000000068A8FF0134D8AA0590D7AA0509000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C00460069007200650066006F0078002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000002E0098B1750600000000386E410348B32E03386E41030000000000000000A11100003626A70218D7AA0533AB0A7736C28A73030C0000102700001D000000315502004CD7AA05F8AA0A77315502003626A7026CD7AA0568A8FF01ECD7AA0500000000A3010000ACD700005327C6275CD7AA0582914A76ACD7AA0560D7AA0527954A7600000000F4ACFF0188D7AA05CD944A76F4ACFF0134D8AA0568A8FF01E1944A760000000068A8FF0134D8AA0590D7AA05 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 00000000070000000000000007000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFE0EBB48C4396D50100000000 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 0000000019000000000000001900000009000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C00460069007200650066006F0078002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000002E0098B1750600000000386E410348B32E03386E41030000000000000000A11100003626A70218D7AA0533AB0A7736C28A73030C0000102700001D000000315502004CD7AA05F8AA0A77315502003626A7026CD7AA0568A8FF01ECD7AA0500000000A3010000ACD700005327C6275CD7AA0582914A76ACD7AA0560D7AA0527954A7600000000F4ACFF0188D7AA05CD944A76F4ACFF0134D8AA0568A8FF01E1944A760000000068A8FF0134D8AA0590D7AA0509000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C00460069007200650066006F0078002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000002E0098B1750600000000386E410348B32E03386E41030000000000000000A11100003626A70218D7AA0533AB0A7736C28A73030C0000102700001D000000315502004CD7AA05F8AA0A77315502003626A7026CD7AA0568A8FF01ECD7AA0500000000A3010000ACD700005327C6275CD7AA0582914A76ACD7AA0560D7AA0527954A7600000000F4ACFF0188D7AA05CD944A76F4ACFF0134D8AA0568A8FF01E1944A760000000068A8FF0134D8AA0590D7AA0509000000000000000900000043003A005C00550073006500720073005C005000750062006C00690063005C004400650073006B0074006F0070005C00460069007200650066006F0078002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000002E0098B1750600000000386E410348B32E03386E41030000000000000000A11100003626A70218D7AA0533AB0A7736C28A73030C0000102700001D000000315502004CD7AA05F8AA0A77315502003626A7026CD7AA0568A8FF01ECD7AA0500000000A3010000ACD700005327C6275CD7AA0582914A76ACD7AA0560D7AA0527954A7600000000F4ACFF0188D7AA05CD944A76F4ACFF0134D8AA0568A8FF01E1944A760000000068A8FF0134D8AA0590D7AA05 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
2
Suspicious files
4
Text files
8
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR17F2.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~WRD0001.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 352 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\a7bd71699cd38d1c.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 2488 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2300 | WinRAR.exe | C:\Users\admin\Downloads\contract.doc\contract.doc | document | |
MD5:— | SHA256:— | |||
| 352 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Downloads.lnk | lnk | |
MD5:— | SHA256:— | |||
| 352 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 352 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\contract.doc.zip.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2488 | WINWORD.EXE | 195.123.246.12:443 | microsoft-hub-us.com | — | UA | unknown |
3228 | gup.exe | 104.31.88.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
microsoft-hub-us.com |
| unknown |
notepad-plus-plus.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|