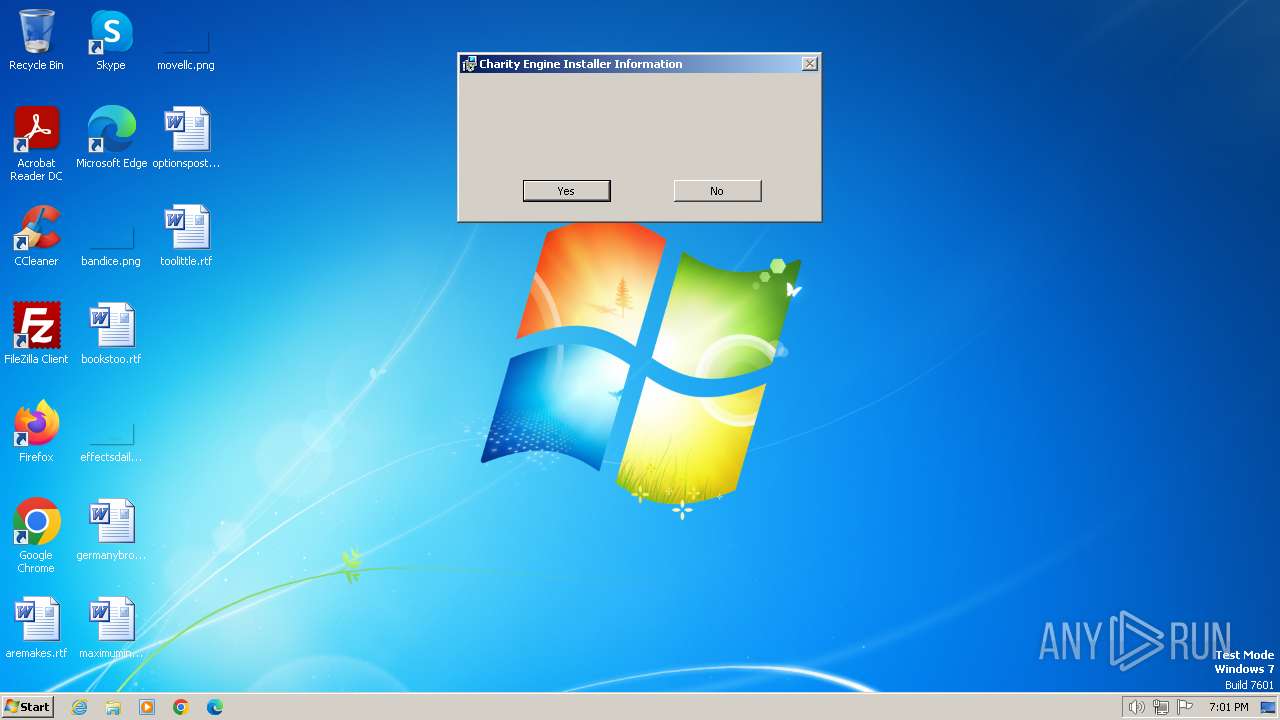
| File name: | charity-engine-setup.exe |
| Full analysis: | https://app.any.run/tasks/d50bdd32-cfb8-4efe-a268-cb7260a8ddf4 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 19:00:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2860402B3279305E9109FBB79309A880 |
| SHA1: | B18E64908B49C6039B321B31F80C74E8205FD904 |
| SHA256: | 96957E93D14BE793693F289F547F9BB5B7A9345761F514C9039B0DCE52367558 |
| SSDEEP: | 98304:+5S94pyq+k8weIL+P+0bQqQeEO2uFDbr1gCyjib2u//uvUDY5cHd5scHfkpvGVi/:P6eBfkkNDdKfX7 |
MALICIOUS
Drops the executable file immediately after the start
- charity-engine-setup.exe (PID: 2840)
Actions looks like stealing of personal data
- charityengine.exe (PID: 2236)
Steals credentials from Web Browsers
- charityengine.exe (PID: 2236)
SUSPICIOUS
The process executes via Task Scheduler
- ctfmon.exe (PID: 2068)
- sipnotify.exe (PID: 2100)
Reads the Internet Settings
- sipnotify.exe (PID: 2100)
- charityengine.exe (PID: 2236)
- IELowutil.exe (PID: 2572)
Executes as Windows Service
- VSSVC.exe (PID: 2580)
Starts application with an unusual extension
- charityengine.exe (PID: 2236)
Reads security settings of Internet Explorer
- charityengine.exe (PID: 2236)
- IELowutil.exe (PID: 2572)
Reads browser cookies
- charityengine.exe (PID: 2236)
Reads settings of System Certificates
- sipnotify.exe (PID: 2100)
Adds/modifies Windows certificates
- msiexec.exe (PID: 1492)
INFO
Reads the computer name
- charity-engine-setup.exe (PID: 2840)
- IMEKLMG.EXE (PID: 2212)
- IMEKLMG.EXE (PID: 2220)
- charityengine.exe (PID: 2236)
- boincscr.exe (PID: 2444)
- IELowutil.exe (PID: 2572)
- wmpnscfg.exe (PID: 2756)
- wmpnscfg.exe (PID: 2724)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1492)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1492)
Manual execution by a user
- IMEKLMG.EXE (PID: 2212)
- IMEKLMG.EXE (PID: 2220)
- charityengine.exe (PID: 2236)
- boinctray.exe (PID: 2256)
- ctfmon.exe (PID: 2288)
- wmpnscfg.exe (PID: 2756)
- wmpnscfg.exe (PID: 2724)
Checks supported languages
- IMEKLMG.EXE (PID: 2220)
- IMEKLMG.EXE (PID: 2212)
- charity-engine-setup.exe (PID: 2840)
- charityengine.exe (PID: 2236)
- boincscr.exe (PID: 2444)
- boinc.scr (PID: 2432)
- IELowutil.exe (PID: 2572)
- boinctray.exe (PID: 2256)
- wmpnscfg.exe (PID: 2756)
- wmpnscfg.exe (PID: 2724)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2212)
- IMEKLMG.EXE (PID: 2220)
- charityengine.exe (PID: 2236)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 2100)
- msiexec.exe (PID: 1492)
Checks proxy server information
- charityengine.exe (PID: 2236)
- IELowutil.exe (PID: 2572)
Creates files or folders in the user directory
- charityengine.exe (PID: 2236)
Creates files in the program directory
- charityengine.exe (PID: 2236)
Reads the machine GUID from the registry
- IELowutil.exe (PID: 2572)
- charity-engine-setup.exe (PID: 2840)
- charityengine.exe (PID: 2236)
Reads the software policy settings
- sipnotify.exe (PID: 2100)
- msiexec.exe (PID: 1492)
Create files in a temporary directory
- charity-engine-setup.exe (PID: 2840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:10:05 20:39:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 700416 |
| InitializedDataSize: | 849920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x68208 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.8.44.0 |
| ProductVersionNumber: | 6.8.44.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Charity Engine |
| FileDescription: | Downloads, executes, and uploads BOINC tasks |
| FileVersion: | 6.8.44 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (C) 2009 University of California at Berkeley. All Rights Reserved. |
| OriginalFileName: | InstallShield Setup.exe |
| ProductName: | Charity Engine |
| ProductVersion: | 6.8.44 |
| InternalBuildNumber: | 99584 |
| ISInternalVersion: | 17.0.717 |
| ISInternalDescription: | Setup Launcher Unicode |
Total processes
106
Monitored processes
16
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1492 | MSIEXEC.EXE /i "C:\Windows\Downloaded Installations\{8E4BAAC1-5346-49FD-927E-3B3974DCB685}\Charity Engine.msi" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp" SETUPEXENAME="charity-engine-setup.exe" | C:\Windows\System32\msiexec.exe | charity-engine-setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 1641 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2100 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Charity Engine\charityengine.exe" /a /s | C:\Program Files\Charity Engine\charityengine.exe | explorer.exe | ||||||||||||
User: admin Company: Charity Engine Integrity Level: MEDIUM Description: Charity Engine for Windows Exit code: 0 Version: 6.8.44 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\Charity Engine\boinctray.exe" | C:\Program Files\Charity Engine\boinctray.exe | — | explorer.exe | |||||||||||
User: admin Company: Charity Engine Integrity Level: MEDIUM Description: Charity Engine System Tray for Windows Exit code: 0 Version: 6.8.44 Modules
| |||||||||||||||
| 2288 | "C:\Windows\System32\ctfmon.exe" C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Windows\boinc.scr" /t | C:\Windows\boinc.scr | — | charityengine.exe | |||||||||||
User: admin Company: Charity Engine Integrity Level: MEDIUM Description: Charity Engine Screensaver Exit code: 0 Version: 6.8.44 Modules
| |||||||||||||||
| 2444 | "C:\Program Files\Charity Engine\\boincscr.exe" --test | C:\Program Files\Charity Engine\boincscr.exe | — | charityengine.exe | |||||||||||
User: admin Company: Charity Engine Integrity Level: MEDIUM Description: Charity Engine Screensaver Exit code: 4294967189 Version: 6.8.44 Modules
| |||||||||||||||
Total events
10 318
Read events
10 076
Write events
221
Delete events
21
Modification events
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates |
| Operation: | delete value | Name: | 9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
Value: | |||
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D80300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 91C6D6EE3E8AC86384E548C299295C756C817B81 |
Value: | |||
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000008CCADC0B22CEF5BE72AC411A11A8D812190000000100000010000000DC73F9B71E16D51D26527D32B11A6A3D53000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C06200000001000000200000008D722F81A9C113C0791DF136A2966DB26C950A971DB46B4199F4EA54B78BFB9F1400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748501D00000001000000100000005B3B67000EEB80022E42605B6B3B72400B000000010000000E00000074006800610077007400650000007F000000010000000C000000300A06082B060105050703017E00000001000000080000000040D0D1B0FFD40103000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B810F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE09000000010000002A000000302806082B0601050507030206082B0601050507030306082B0601050507030406082B060105050703012000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\91C6D6EE3E8AC86384E548C299295C756C817B81 |
| Operation: | write | Name: | Blob |
Value: 5C00000001000000040000000008000009000000010000002A000000302806082B0601050507030206082B0601050507030306082B0601050507030406082B060105050703010F000000010000001400000085FEF11B4F47FE3952F98301C9F98976FEFEE0CE03000000010000001400000091C6D6EE3E8AC86384E548C299295C756C817B817E00000001000000080000000040D0D1B0FFD4017F000000010000000C000000300A06082B060105050703010B000000010000000E00000074006800610077007400650000001D00000001000000100000005B3B67000EEB80022E42605B6B3B72401400000001000000140000007B5B45CFAFCECB7AFD31921A6AB6F346EB5748506200000001000000200000008D722F81A9C113C0791DF136A2966DB26C950A971DB46B4199F4EA54B78BFB9F53000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C0190000000100000010000000DC73F9B71E16D51D26527D32B11A6A3D0400000001000000100000008CCADC0B22CEF5BE72AC411A11A8D8122000000001000000240400003082042030820308A0030201020210344ED55720D5EDEC49F42FCE37DB2B6D300D06092A864886F70D01010505003081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F74204341301E170D3036313131373030303030305A170D3336303731363233353935395A3081A9310B300906035504061302555331153013060355040A130C7468617774652C20496E632E31283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E31383036060355040B132F2863292032303036207468617774652C20496E632E202D20466F7220617574686F72697A656420757365206F6E6C79311F301D06035504031316746861777465205072696D61727920526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100ACA0F0FB8059D49CC7A4CF9DA159730910450C0D2C6E68F16C5B4868495937FC0B3319C2777FCC102D95341CE6EB4D09A71CD2B8C9973602B789D4245F06C0CC4494948D02626FEB5ADD118D289A5C8490107A0DBD74662F6A38A0E2D55444EB1D079F07BA6FEEE9FD4E0B29F53E84A001F19CABF81C7E89A4E8A1D871650DA3517BEEBCD222600DB95B9DDFBAFC515B0BAF98B2E92EE904E86287DE2BC8D74EC14C641EDDCF8758BA4A4FCA68071D1C9D4AC6D52F91CC7C71721CC5C067EB32FDC9925C94DA85C09BBF537D2B09F48C9D911F976A52CBDE0936A477D87B875044D53E6E2969FB3949261E09A5807B402DEBE82785C9FE61FD7EE67C971DD59D0203010001A3423040300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020106301D0603551D0E041604147B5B45CFAFCECB7AFD31921A6AB6F346EB574850300D06092A864886F70D010105050003820101007911C04BB391B6FCF0E967D40D6E45BE55E893D2CE033FEDDA25B01D57CB1E3A76A04CEC5076E864720CA4A9F1B88BD6D68784BB32E54111C077D9B3609DEB1BD5D16E4444A9A601EC55621D77B85C8E48497C9C3B5711ACAD73378E2F785C906847D96060E6FC073D222017C4F716E9C4D872F9C8737CDF162F15A93EFD6A27B6A1EB5ABA981FD5E34D640A9D13C861BAF5391C87BAB8BD7B227FF6FEAC4079E5AC106F3D8F1B79768BC437B3211884E53600EB632099B9E9FE3304BB41C8C102F94463209E81CE42D3D63F2C76D3639C59DD8FA6E10EA02E41F72E9547CFBCFD33F3F60B617E7E912B8147C22730EEA7105D378F5C392BE404F07B8D568C68 | |||
| (PID) Process: | (1492) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 190000000100000010000000BCC80DAA2F98A4692805BFF4CBB372EB0300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB60F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D8200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (2580) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B2B3211BE668DA01140A0000F4080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2580) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B2B3211BE668DA01140A00002C0B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2580) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B2B3211BE668DA01140A0000B8080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
7
Suspicious files
7
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\_isEF6.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\{AD51BF64-897F-4251-B96C-F5D1333CE52F}\Charity Engine.msi | — | |
MD5:— | SHA256:— | |||
| 2840 | charity-engine-setup.exe | C:\Windows\Downloaded Installations\{8E4BAAC1-5346-49FD-927E-3B3974DCB685}\Charity Engine.msi | — | |
MD5:— | SHA256:— | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\{AD51BF64-897F-4251-B96C-F5D1333CE52F}\_ISMSIDEL.INI | text | |
MD5:C362C4954922F2CA58077586D77AF3FC | SHA256:555B7B97BAE643301A54584BDD815CE405ED8121213831A8D5F1C7BA60ECF500 | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\_is9AF.tmp | binary | |
MD5:E8CE9E8CD1D8B6E76E7BAEAF13C69341 | SHA256:82DBA0FCE5399CA6CA1AC0D882ECF9B246E9E151D1BEA511B35D056FEA3D7F65 | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\{AD51BF64-897F-4251-B96C-F5D1333CE52F}\0x0409.ini | text | |
MD5:BE345D0260AE12C5F2F337B17E07C217 | SHA256:E994689A13B9448C074F9B471EDEEC9B524890A0D82925E98AB90B658016D8F3 | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\_isB2C.tmp | binary | |
MD5:0FF678C3399BFB663CDEDD0FCC324E3F | SHA256:23F2E48E47CE67A3BE09D27AB0DD42299890C9A0FBDD52BBBD88DF4690AA9A3E | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\~12C0.tmp | text | |
MD5:4B5A7A491ECC7AF9FB29E1101FB79C75 | SHA256:A0392F56E83B7B7049E8B7CEA8A9E6CD4263EB230F9C9A1E99F12E80C37A1D72 | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\~ABB.tmp | text | |
MD5:4B5A7A491ECC7AF9FB29E1101FB79C75 | SHA256:A0392F56E83B7B7049E8B7CEA8A9E6CD4263EB230F9C9A1E99F12E80C37A1D72 | |||
| 2840 | charity-engine-setup.exe | C:\Users\admin\AppData\Local\Temp\_is12C1.tmp | pz | |
MD5:E8CE9E8CD1D8B6E76E7BAEAF13C69341 | SHA256:82DBA0FCE5399CA6CA1AC0D882ECF9B246E9E151D1BEA511B35D056FEA3D7F65 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
16
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1500 | boinc.exe | GET | 302 | 142.250.185.196:80 | http://www.google.com/ | unknown | html | 396 b | unknown |
1500 | boinc.exe | GET | 429 | 142.250.185.196:80 | http://www.google.com/sorry/index?continue=http://www.google.com/&q=EgRUETC-GKjA864GIjDBsZ1Gd0o2TiZKm835vGZ083aiJWVik7mX8BwB_C2KVKchY5FBCdvFXXrjjBy7IJMyAXJKGVNPUlJZX0FCVVNJVkVfTkVUX01FU1NBR0VaAUM | unknown | html | 2.98 Kb | unknown |
2100 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133534476952180000 | unknown | — | — | unknown |
1500 | boinc.exe | GET | 200 | 65.97.63.40:80 | http://www.charityengine.com/get_project_config.php | unknown | text | 118 b | unknown |
1500 | boinc.exe | GET | 301 | 208.68.240.115:80 | http://boinc.berkeley.edu/project_list.php | unknown | html | 335 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1132 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1572 | svchost.exe | 239.255.255.250:3702 | — | — | — | unknown |
1500 | boinc.exe | 208.68.240.115:80 | boinc.berkeley.edu | UCB | US | unknown |
1500 | boinc.exe | 208.68.240.115:443 | boinc.berkeley.edu | UCB | US | unknown |
2100 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
1500 | boinc.exe | 65.97.63.40:80 | www.charityengine.com | — | — | unknown |
1500 | boinc.exe | 142.250.185.196:80 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
boinc.berkeley.edu |
| unknown |
query.prod.cms.rt.microsoft.com |
| whitelisted |
www.charityengine.com |
| unknown |
www.google.com |
| whitelisted |