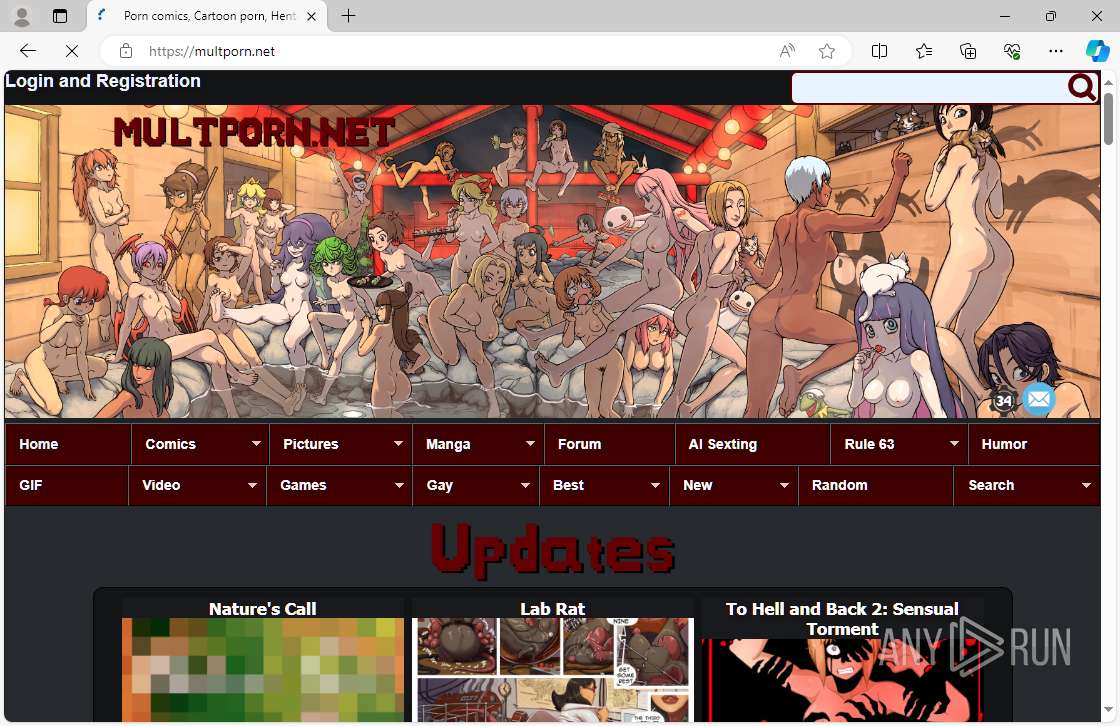
| URL: | Multporn.net |
| Full analysis: | https://app.any.run/tasks/d2375a1d-5662-4e1f-8962-a9ed81134b9b |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 04:50:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 031EDCD98727E2884A700B4A747D50B1 |
| SHA1: | 4A2EE55C3A8007896B353421D070791535DC77C3 |
| SHA256: | 96684B32573A32D3AD1147123282FBEBBEC84A75E31BBA8A01658A2E3401BE47 |
| SSDEEP: | 3:NJRSLLo:bRGo |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 4792)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
150
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 4792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2604 --field-trial-handle=2320,i,16194277592197507296,15814343983252007256,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
96
Text files
121
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c7 | image | |
MD5:EDF17329CABCA690CFEBE595F74B3054 | SHA256:E58ABFECC7DA31A73B1A21C4462D517163C4E3DF14F13FA77B9461CB778A5F2C | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bc | compressed | |
MD5:AD44E3B47CC5EC65765031C8A426C1A4 | SHA256:A1D315E5C6F14E432CE0481A62F8323C4E5FA56029ADCE0D7AE4DD75AD9247D7 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000bd | image | |
MD5:2E48D12D02C91666ECB99713983EFC6B | SHA256:5C7FF0B07DB98B2B8C31CE88FFF4206803F4D97B5FED544AF4ADC80E80B5FDD8 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000cb | image | |
MD5:2180FD6FFF7C3D3EA389A83862CC9C43 | SHA256:CE62E3C6E9227E5B250361E8736FA14A2AA9550298E7B54C666275ABB9C58C97 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c8 | image | |
MD5:6316332FFBB99FDDF02FB2A5A260A730 | SHA256:3796894225BF37B5222E388653FC2879F2603847273345C9EEC1E2BDDEA59470 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c5 | image | |
MD5:BFAC8D6F2E0E39445B41EA1D374365C8 | SHA256:4BB008B2C326EC91D04ED6D864A0CC955DEA5CD75267D08D64ABF13B33FF89A5 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c9 | image | |
MD5:06FB2CFF1547C7E7198B295ACF7F3463 | SHA256:333966E8BA163238C7200E5862051F93394536584FB250F69659E69EFDAFE50A | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000c0 | image | |
MD5:01EAF82F380C49F64D81F5C8B2C90AE1 | SHA256:71013A3AD7922834E65FFFD21A55CDB08DF977D9F83A7B80F347BCEC54903652 | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000ca | image | |
MD5:135E3CD6C3974ECC3E54414C6CA4E300 | SHA256:E299FAFD19F89359F3A3EF96576B6B5CBBFF0E34CE57E98D845CE264DA0C7C2F | |||
| 4792 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_0000cc | image | |
MD5:93B6FB1DAFAD20E616331233E25246DE | SHA256:85AFF122BE23B71818CED05D419AAA3481F284C0DE121585760C349912ECA531 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
556
TCP/UDP connections
118
DNS requests
135
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
1900 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6528 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1900 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4304 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6528 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.22.22.184:443 | https://multporn.net/modules/system/system.messages.css?sodojg | unknown | text | 961 b | whitelisted |
— | — | GET | 200 | 104.22.23.184:443 | https://multporn.net/sites/all/modules/scald/modules/fields/mee/css/editor-global.css?sodojg | unknown | text | 539 b | whitelisted |
— | — | GET | 200 | 104.22.23.184:443 | https://multporn.net/modules/system/system.theme.css?sodojg | unknown | text | 3.62 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4792 | msedge.exe | 20.189.173.24:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
1900 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4304 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6528 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4792 | msedge.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5988 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4792 | msedge.exe | 104.22.22.184:443 | multporn.net | CLOUDFLARENET | — | whitelisted |
6812 | svchost.exe | 184.30.17.174:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
6528 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
multporn.net |
| whitelisted |
fs.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
stat.rule34.art |
| unknown |
a.pemsrv.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .show-sb .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .show-sb .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .creative-stat1 .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .creative-stat1 .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain (tributeparticle .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain (tributeparticle .com) |