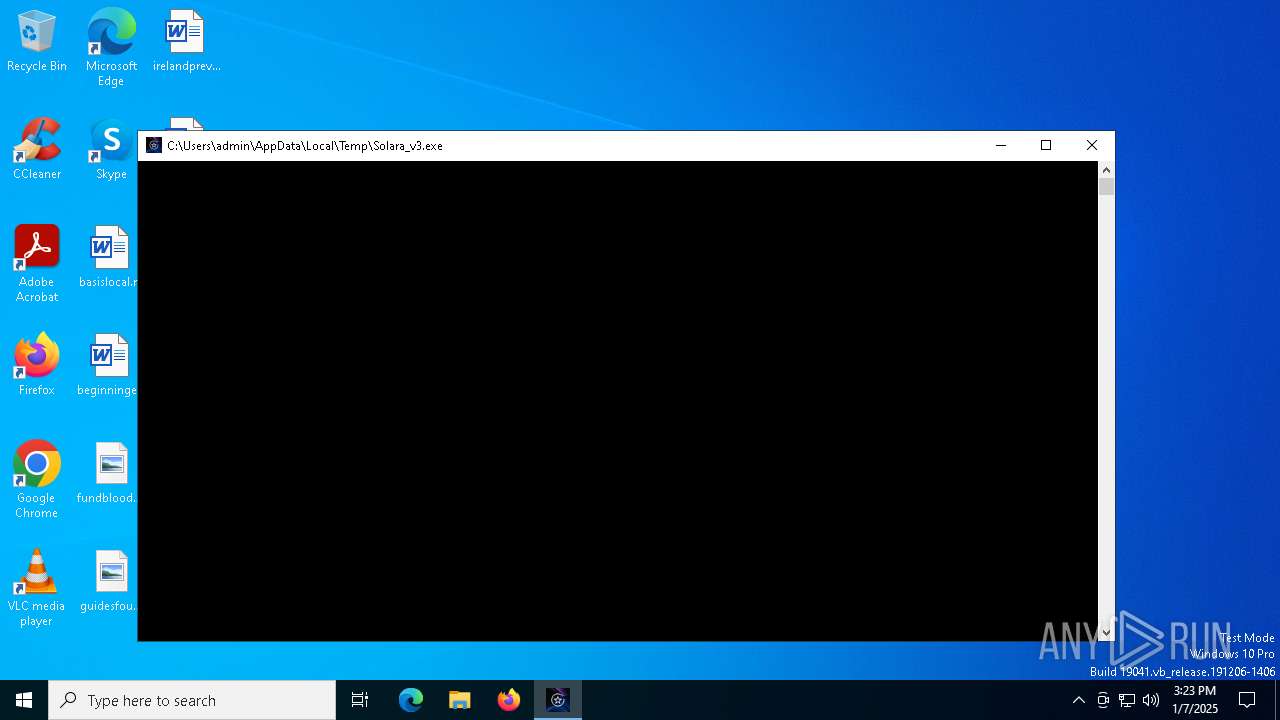
| File name: | Solara_v3.exe |
| Full analysis: | https://app.any.run/tasks/97552eca-9763-49d5-a2ef-193a3f2f8f35 |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2025, 15:23:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 404F9A9A90F2729D0ACBA7E76527FB88 |
| SHA1: | 441A37963638E3F4635EF8C5FA35FD8FA566E325 |
| SHA256: | 96559BA94A96B7A3AB66125A3556C6A8EC07FE561F8D60BD06F66520E3366C5E |
| SSDEEP: | 98304:md6zZgKhAdiHlg/riVfHl6/m8I1zG/mDQcioHSllhCqcW52UdV9GgpbRr7oDzGoZ:PvzN8/3h2QGdCvEvnt5 |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 2088)
Changes powershell execution policy (Bypass)
- Solara_v3.exe (PID: 7124)
SUSPICIOUS
BASE64 encoded PowerShell command has been detected
- Solara_v3.exe (PID: 7124)
Base64-obfuscated command line is found
- Solara_v3.exe (PID: 7124)
Starts POWERSHELL.EXE for commands execution
- Solara_v3.exe (PID: 7124)
The process bypasses the loading of PowerShell profile settings
- Solara_v3.exe (PID: 7124)
The process hides Powershell's copyright startup banner
- Solara_v3.exe (PID: 7124)
The process hide an interactive prompt from the user
- Solara_v3.exe (PID: 7124)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2088)
CSC.EXE is used to compile C# code
- csc.exe (PID: 6384)
Executable content was dropped or overwritten
- csc.exe (PID: 6384)
- powershell.exe (PID: 5568)
Uses ATTRIB.EXE to modify file attributes
- Solara_v3.exe (PID: 7124)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 5568)
Process drops python dynamic module
- powershell.exe (PID: 5568)
Process drops legitimate windows executable
- powershell.exe (PID: 5568)
The process drops C-runtime libraries
- powershell.exe (PID: 5568)
INFO
Checks supported languages
- Solara_v3.exe (PID: 7124)
- csc.exe (PID: 6384)
- cvtres.exe (PID: 3688)
The sample compiled with english language support
- Solara_v3.exe (PID: 7124)
- powershell.exe (PID: 5568)
Checks proxy server information
- Solara_v3.exe (PID: 7124)
Reads the machine GUID from the registry
- csc.exe (PID: 6384)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2088)
Create files in a temporary directory
- csc.exe (PID: 6384)
- cvtres.exe (PID: 3688)
Reads the computer name
- Solara_v3.exe (PID: 7124)
Found Base64 encoded text manipulation via PowerShell (YARA)
- Solara_v3.exe (PID: 7124)
Found Base64 encoded JSON usage via PowerShell (YARA)
- Solara_v3.exe (PID: 7124)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5568)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5568)
Application based on Rust
- Solara_v3.exe (PID: 7124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2020:12:22 16:26:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.28 |
| CodeSize: | 22298112 |
| InitializedDataSize: | 11738112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1515470 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.14.32.32 |
| ProductVersionNumber: | 1.6.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Solara Executor For Roblox |
| FileVersion: | 03.14.32.32 |
| CompanyName: | CMD |
Total processes
122
Monitored processes
8
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "powershell" -NoLogo -NonInteractive -NoProfile -ExecutionPolicy Bypass -EncodedCommand WwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACgAJwB7ACIAUwBjAHIAaQBwAHQAIgA6ACIAYQBXAFkAZwBLAEMAMQB1AGIAMwBRAGcASwBGAHQAVABlAFgATgAwAFoAVwAwAHUAVABXAEYAdQBZAFcAZABsAGIAVwBWAHUAZABDADUAQgBkAFgAUgB2AGIAVwBGADAAYQBXADkAdQBMAGwAQgBUAFYASABsAHcAWgBVADUAaABiAFcAVgBkAEoAMQBkAHAAYgBqAE0AeQBKAHkAawB1AFYASABsAHcAWgBTAGsAZwBlAHcAMABLAEkAQwBBAGcASQBFAEYAawBaAEMAMQBVAGUAWABCAGwASQBFAEEAaQBEAFEAbwBnAEkAQwBBAGcAZABYAE4AcABiAG0AYwBnAFUAMwBsAHoAZABHAFYAdABPAHcAMABLAEkAQwBBAGcASQBIAFYAegBhAFcANQBuAEkARgBOADUAYwAzAFIAbABiAFMANQBTAGQAVwA1ADAAYQBXADEAbABMAGsAbAB1AGQARwBWAHkAYgAzAEIAVABaAFgASgAyAGEAVwBOAGwAYwB6AHMATgBDAGcAMABLAEkAQwBBAGcASQBIAEIAMQBZAG0AeABwAFkAeQBCAGoAYgBHAEYAegBjAHkAQgBYAGEAVwA0AHoATQBpAEIANwBEAFEAbwBnAEkAQwBBAGcASQBDAEEAZwBJAEYAdABFAGIARwB4AEoAYgBYAEIAdgBjAG4AUQBvAEkAbgBWAHoAWgBYAEkAegBNAGkANQBrAGIARwB3AGkASwBWADAATgBDAGkAQQBnAEkAQwBBAGcASQBDAEEAZwBjAEgAVgBpAGIARwBsAGoASQBIAE4AMABZAFgAUgBwAFkAeQBCAGwAZQBIAFIAbABjAG0ANABnAFMAVwA1ADAAVQBIAFIAeQBJAEUAZABsAGQARQBaAHYAYwBtAFYAbgBjAG0AOQAxAGIAbQBSAFgAYQBXADUAawBiADMAYwBvAEsAVABzAE4AQwBnADAASwBJAEMAQQBnAEkAQwBBAGcASQBDAEIAYgBSAEcAeABzAFMAVwAxAHcAYgAzAEoAMABLAEMASgAxAGMAMgBWAHkATQB6AEkAdQBaAEcAeABzAEkAaQBsAGQARABRAG8AZwBJAEMAQQBnAEkAQwBBAGcASQBGAHQAeQBaAFgAUgAxAGMAbQA0ADYASQBFADEAaABjAG4ATgBvAFkAVwB4AEIAYwB5AGgAVgBiAG0AMQBoAGIAbQBGAG4AWgBXAFIAVQBlAFgAQgBsAEwAawBKAHYAYgAyAHcAcABYAFEAMABLAEkAQwBBAGcASQBDAEEAZwBJAEMAQgB3AGQAVwBKAHMAYQBXAE0AZwBjADMAUgBoAGQARwBsAGoASQBHAFYANABkAEcAVgB5AGIAaQBCAGkAYgAyADkAcwBJAEYATgBvAGIAMwBkAFgAYQBXADUAawBiADMAYwBvAFMAVwA1ADAAVQBIAFIAeQBJAEcAaABYAGIAbQBRAHMASQBHAGwAdQBkAEMAQgB1AFEAMgAxAGsAVQAyAGgAdgBkAHkAawA3AEQAUQBvAGcASQBDAEEAZwBmAFEAMABLAEkAawBBAE4AQwBuADAATgBDAG0AWgAxAGIAbQBOADAAYQBXADkAdQBJAEUAZABsAGQARQBGAGoAZABHAGwAMgBaAFYAZABwAGIAbQBSAHYAZAAxAFIAcABkAEcAeABsAEsAQwBrAGcAZQB3ADAASwBJAEMAQQBnAEkAQwBSAG8AVgAyADUAawBJAEQAMABnAFcAMQBkAHAAYgBqAE0AeQBYAFQAbwA2AFIAMgBWADAAUgBtADkAeQBaAFcAZAB5AGIAMwBWAHUAWgBGAGQAcABiAG0AUgB2AGQAeQBnAHAARABRAG8AZwBJAEMAQQBnAEoASABOAGkASQBEADAAZwBUAG0AVgAzAEwAVQA5AGkAYQBtAFYAagBkAEMAQgBUAGUAWABOADAAWgBXADAAdQBWAEcAVgA0AGQAQwA1AFQAZABIAEoAcABiAG0AZABDAGQAVwBsAHMAWgBHAFYAeQBLAEQASQAxAE4AaQBrAE4AQwBpAEEAZwBJAEMAQgBiAFYAMgBsAHUATQB6AEoAZABPAGoAcABIAFoAWABSAFgAYQBXADUAawBiADMAZABVAFoAWABoADAASwBDAFIAbwBWADIANQBrAEwAQwBBAGsAYwAyAEkAcwBJAEMAUgB6AFkAaQA1AEQAWQBYAEIAaABZADIAbAAwAGUAUwBrAGcAZgBDAEIAUABkAFgAUQB0AFQAbgBWAHMAYgBBADAASwBJAEMAQQBnAEkASABKAGwAZABIAFYAeQBiAGkAQQBrAGMAMgBJAHUAVgBHADkAVABkAEgASgBwAGIAbQBjAG8ASwBRADAASwBmAFEAMABLAFoAbgBWAHUAWQAzAFIAcABiADIANABnAFMARwBsAGsAWgBVAEYAagBkAEcAbAAyAFoAVgBkAHAAYgBtAFIAdgBkAHkAZwBwAEkASABzAE4AQwBpAEEAZwBJAEMAQQBrAGEARgBkAHUAWgBDAEEAOQBJAEYAdABYAGEAVwA0AHoATQBsADAANgBPAGsAZABsAGQARQBaAHYAYwBtAFYAbgBjAG0AOQAxAGIAbQBSAFgAYQBXADUAawBiADMAYwBvAEsAUQAwAEsASQBDAEEAZwBJAEYAdABYAGEAVwA0AHoATQBsADAANgBPAGwATgBvAGIAMwBkAFgAYQBXADUAawBiADMAYwBvAEoARwBoAFgAYgBtAFEAcwBJAEQAQQBwAEQAUQBwADkARABRAG8AawBZADMAVgB5AGMAbQBWAHUAZABGAGQAcABiAG0AUgB2AGQAMQBSAHAAZABHAHgAbABJAEQAMABnAFIAMgBWADAAUQBXAE4AMABhAFgAWgBsAFYAMgBsAHUAWgBHADkAMwBWAEcAbAAwAGIARwBVAE4AQwBrAGgAcABaAEcAVgBCAFkAMwBSAHAAZABtAFYAWABhAFcANQBrAGIAMwBjAE4AQwBnAD0APQAiAH0AJwAgAHwAIABDAG8AbgB2AGUAcgB0AEYAcgBvAG0ALQBKAHMAbwBuACkALgBTAGMAcgBpAHAAdAApACkAIAB8ACAAaQBlAHgA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Solara_v3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3688 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES88BB.tmp" "c:\Users\admin\AppData\Local\Temp\CSC1DB9801E221745D499808CFCB2A84C63.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 5568 | "powershell" -Command "Expand-Archive -Path \"C:\WindowsSystem\Worker\Update.zip\" -DestinationPath \"C:\WindowsSystem\Worker\" -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | Solara_v3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6384 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\gfsc1gfx.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6408 | "attrib" +h C:\WindowsSystem | C:\Windows\System32\attrib.exe | — | Solara_v3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7124 | "C:\Users\admin\AppData\Local\Temp\Solara_v3.exe" | C:\Users\admin\AppData\Local\Temp\Solara_v3.exe | explorer.exe | ||||||||||||
User: admin Company: CMD Integrity Level: MEDIUM Description: Solara Executor For Roblox Version: 03.14.32.32 Modules
| |||||||||||||||
| 7132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Solara_v3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 412
Read events
10 412
Write events
0
Delete events
0
Modification events
Executable files
124
Suspicious files
57
Text files
1 062
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7124 | Solara_v3.exe | C:\WindowsSystem\Worker\Update.zip | — | |
MD5:— | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_maotlasu.guu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_koytrlad.p0j.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gfsc1gfx.cmdline | text | |
MD5:A29481CD432F3A76460E832F7500393C | SHA256:D396DAAE1D443B991C284518F4D4491C0EA48021C2329AE03EBE7CD280D5A595 | |||
| 5568 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5aknagib.oax.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5568 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ttctfhyy.dpn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5568 | powershell.exe | C:\WindowsSystem\Worker\certifi\cacert.pem | text | |
MD5:181AC9A809B1A8F1BC39C1C5C777CF2A | SHA256:488BA960602BF07CC63F4EF7AEC108692FEC41820FC3328A8E3F3DE038149AEE | |||
| 5568 | powershell.exe | C:\WindowsSystem\Worker\charset_normalizer\md.pyd | executable | |
MD5:F33CA57D413E6B5313272FA54DBC8BAA | SHA256:9B3D70922DCFAEB02812AFA9030A40433B9D2B58BCF088781F9AB68A74D20664 | |||
| 5568 | powershell.exe | C:\WindowsSystem\Worker\charset_normalizer\md__mypyc.pyd | executable | |
MD5:494F5B9ADC1CFB7FDB919C9B1AF346E1 | SHA256:AD9BCC0DE6815516DFDE91BB2E477F8FB5F099D7F5511D0F54B50FA77B721051 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gfsc1gfx.0.cs | text | |
MD5:379570600F5439DDA873EDA8F0CE4A79 | SHA256:2C058658252D0F5A4613DC846D56329797E86033E3C61B9B68537AE167000072 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
34
DNS requests
20
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6588 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6332 | SIHClient.exe | GET | 200 | 23.192.42.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6332 | SIHClient.exe | GET | 200 | 23.192.42.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2040 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2040 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
pastebin.com |
| shared |
store9.gofile.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7124 | Solara_v3.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
7124 | Solara_v3.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7124 | Solara_v3.exe | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a file sharing service is observed |