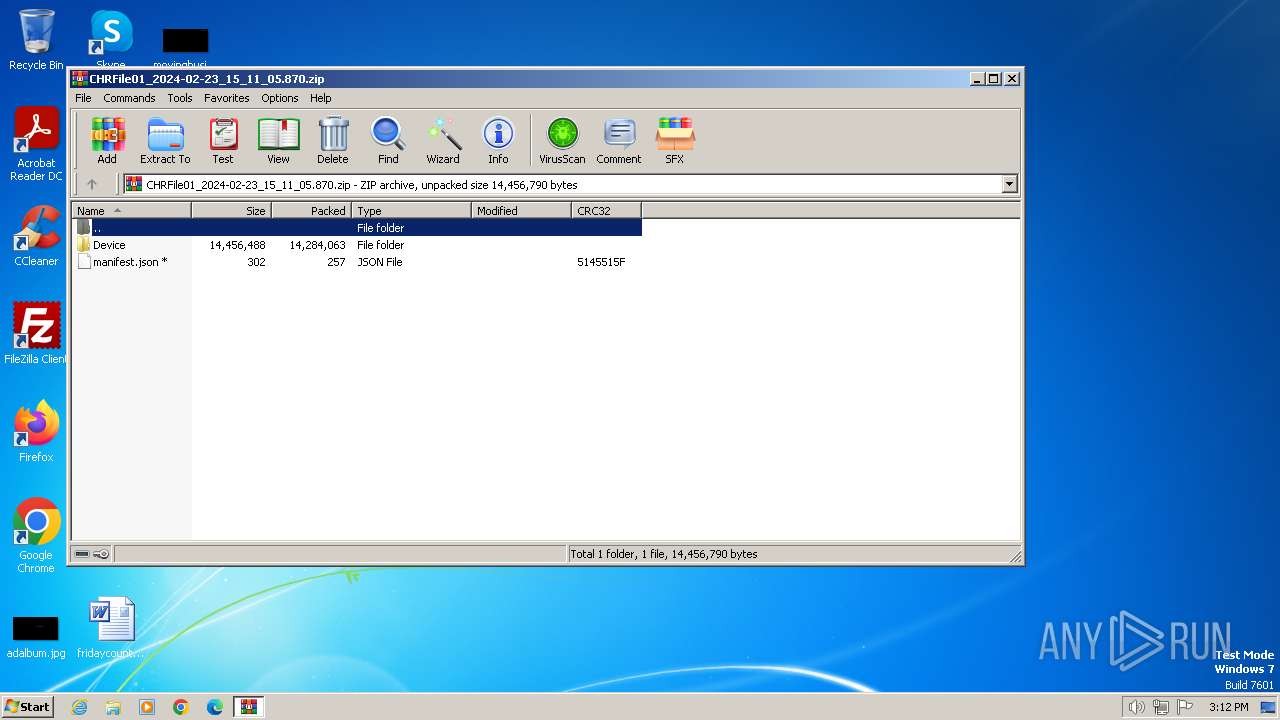
| File name: | CHRFile01_2024-02-23_15_11_05.870.zip |
| Full analysis: | https://app.any.run/tasks/bdb73749-d3ec-4bf9-aa28-678d4507adcb |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 15:11:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 3DC5DAB0D6F33BE6BB2C3D4A321DBBF1 |
| SHA1: | 1A0229D6D7E19AD661949585079EE3E41BA43DC7 |
| SHA256: | 964AB08EEF10DC0120D99FD3E696816AB572587BA0AA1941A785E177F9FC39B4 |
| SSDEEP: | 98304:xhJ2jiYSSRBCHo5VanaUtiJP8tqj0ov0z4ViPHWGwXzbfU7eycbg10HtSXUVvj0E:8hPrz8ru4AGUx6OkUa0uOQMAI |
MALICIOUS
Drops the executable file immediately after the start
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3864)
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Executable content was dropped or overwritten
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Reads Microsoft Outlook installation path
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Reads Internet Explorer settings
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Process drops legitimate windows executable
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Reads the Internet Settings
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
INFO
Reads the computer name
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3864)
Reads the machine GUID from the registry
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Manual execution by a user
- WINWORD.EXE (PID: 2364)
- WINWORD.EXE (PID: 2580)
- explorer.exe (PID: 3308)
Checks supported languages
- XSetupCpu.exe (PID: 2124)
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3864)
Checks proxy server information
- WC78XX_5.433.16.0_PCL6_x64.exe (PID: 3916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x6cefcadf |
| ZipCompressedSize: | 14284063 |
| ZipUncompressedSize: | 14456488 |
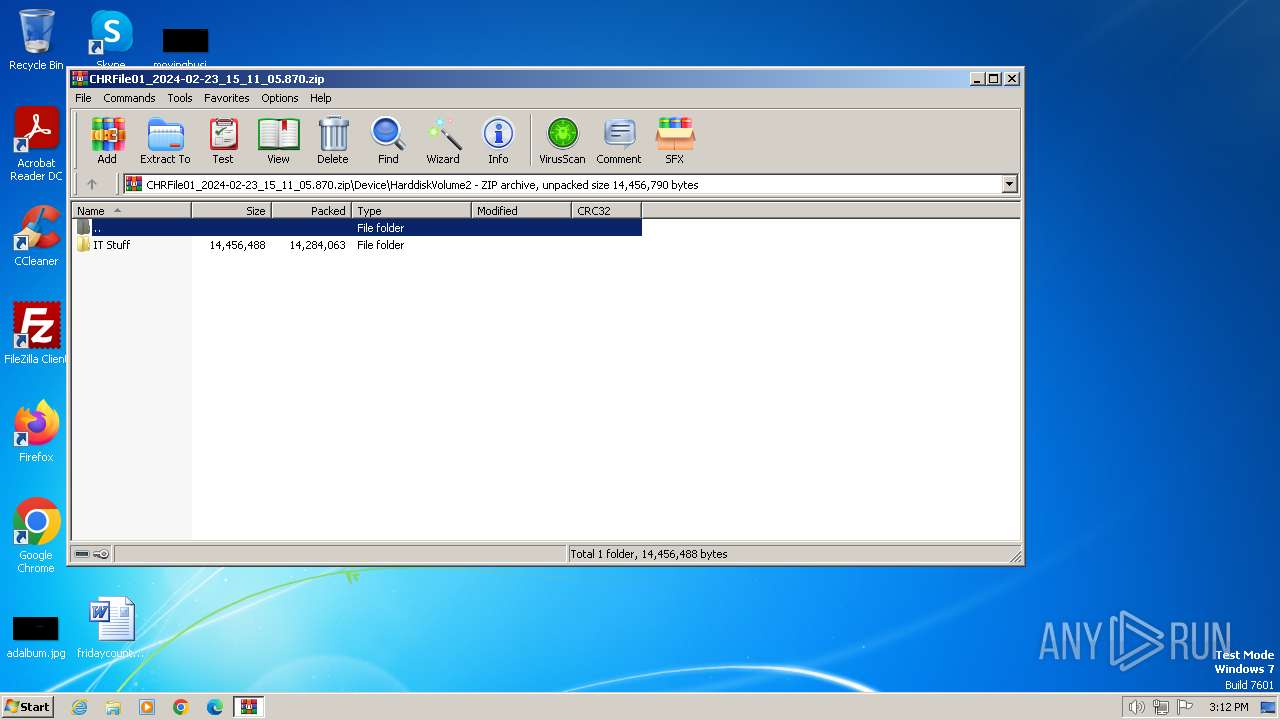
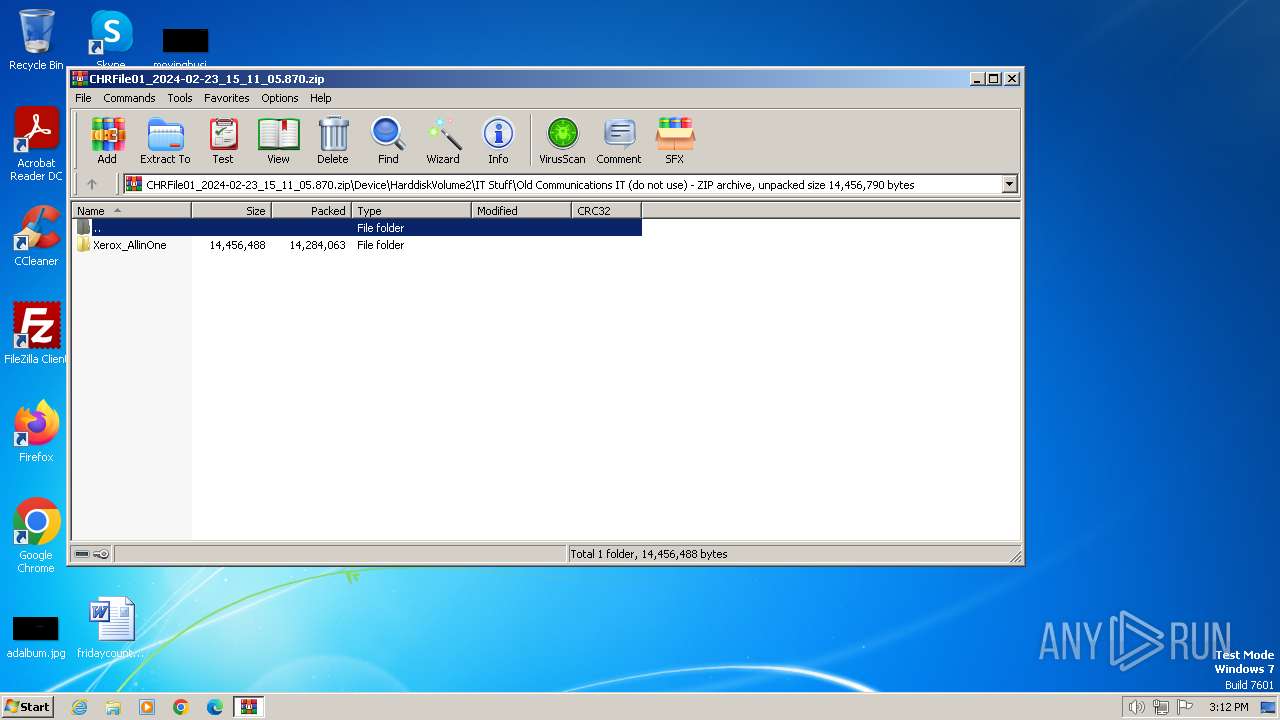
| ZipFileName: | Device/HarddiskVolume2/IT Stuff/Old Communications IT (do not use)/Xerox_AllinOne/WC78XX_5.433.16.0_PCL6_x64.exe |
Total processes
49
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2124 | "C:\Xerox\XSetupCpu.exe" "/CMD32:Setup32.exe; /CMD64:Setup64.exe; /CMD:cmd.exe; /PARAM1:/C; /PARAM2:launch.bat" | C:\Xerox\XSetupCpu.exe | WC78XX_5.433.16.0_PCL6_x64.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2364 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\fridaycountry.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2580 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\fridaycountry.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2848 | "C:\Xerox\XSetupCpu.exe" "/CMD32:Setup32.exe; /CMD64:Setup64.exe; /CMD:cmd.exe; /PARAM1:/C; /PARAM2:launch.bat" | C:\Xerox\XSetupCpu.exe | — | WC78XX_5.433.16.0_PCL6_x64.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3308 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CHRFile01_2024-02-23_15_11_05.870.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3916 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3864.11396\Device\HarddiskVolume2\IT Stuff\Old Communications IT (do not use)\Xerox_AllinOne\WC78XX_5.433.16.0_PCL6_x64.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3864.11396\Device\HarddiskVolume2\IT Stuff\Old Communications IT (do not use)\Xerox_AllinOne\WC78XX_5.433.16.0_PCL6_x64.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
14 921
Read events
13 952
Write events
329
Delete events
640
Modification events
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CHRFile01_2024-02-23_15_11_05.870.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
36
Suspicious files
13
Text files
30
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\launch.bat | text | |
MD5:80F167E6942F1EA51B156040786F44D8 | SHA256:4B1890BA7148ABDD5FF82494A491ACFDD253787469573FBDE108AA272DF56A7D | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\XSetupCpu.exe | executable | |
MD5:7246207F70882DCE6F60C6629B119A54 | SHA256:B840B0F65031FC231395826A27B52FC93A39CA2D26D1EAA4FE6FC490D0508ACB | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\ntprint.inf_amd64\amd64\unidrv.hlp | hlp | |
MD5:6798F64959C913673BD66CD4E47F4A65 | SHA256:0C02B226BE4E7397F8C98799E58B0A512515E462CCDAAC04EDC10E3E1091C011 | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\WC78XX_5.433.16.0_PCL6_x64_Driver.inf\x2jobtVH.exe | executable | |
MD5:433E9C66DD37AC3C72C37B9384EA0AB4 | SHA256:5A6B228AA9F6B132172F2266C11CE76144E304A491F921DC40641E9EFF71C855 | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\Setup64.exe | executable | |
MD5:FD730AA34EC1D82790F0EC33D62317E9 | SHA256:B017890A6FEE8DE1F3BE73BEE510270CE1E4A2B356A13FDE15B924A93EC93AE0 | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\ntprint.inf_amd64\amd64\mxdwdrv.dll | executable | |
MD5:93B06E4E32E4572BDE8DC970C829AD26 | SHA256:D006263A4461F7620F9D4769B1285F59E7A982117EF612945BA390DA7544CE73 | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\APWinstall.bat | text | |
MD5:5C059B0E9901394877D3A961114EECD0 | SHA256:3490CD24E20999F1D79BFDCB3FFB3344C10CBC13DE987FA66ACAEEAA2964613B | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\WC78XX_5.433.16.0_PCL6_x64_Driver.inf\x2fpbVH.exe | executable | |
MD5:45A9EF4A77A068E6354387B59629C321 | SHA256:8B931F6A0ABFB6482920262D4DCAED93CA2027E54515F98020DBD02897AC63BC | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3864.11396\manifest.json | ini | |
MD5:CCBA7AF98F7765054660D8B1519B28DE | SHA256:C5D2A8C8DA203D7FA87BE447C6E6679844C988CB17AD176749562E0812AB31FC | |||
| 3916 | WC78XX_5.433.16.0_PCL6_x64.exe | C:\Xerox\WC78XX_5.433.16.0_PCL6_x64_Driver.inf\xDSPYxVH.ini | ini | |
MD5:125C6F5071350211FA2E907DCDC1EC91 | SHA256:F81B434B950C8DAB86207013ED5B99B029FF8DFE7B9BD6BC869F239FCD1FECFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |