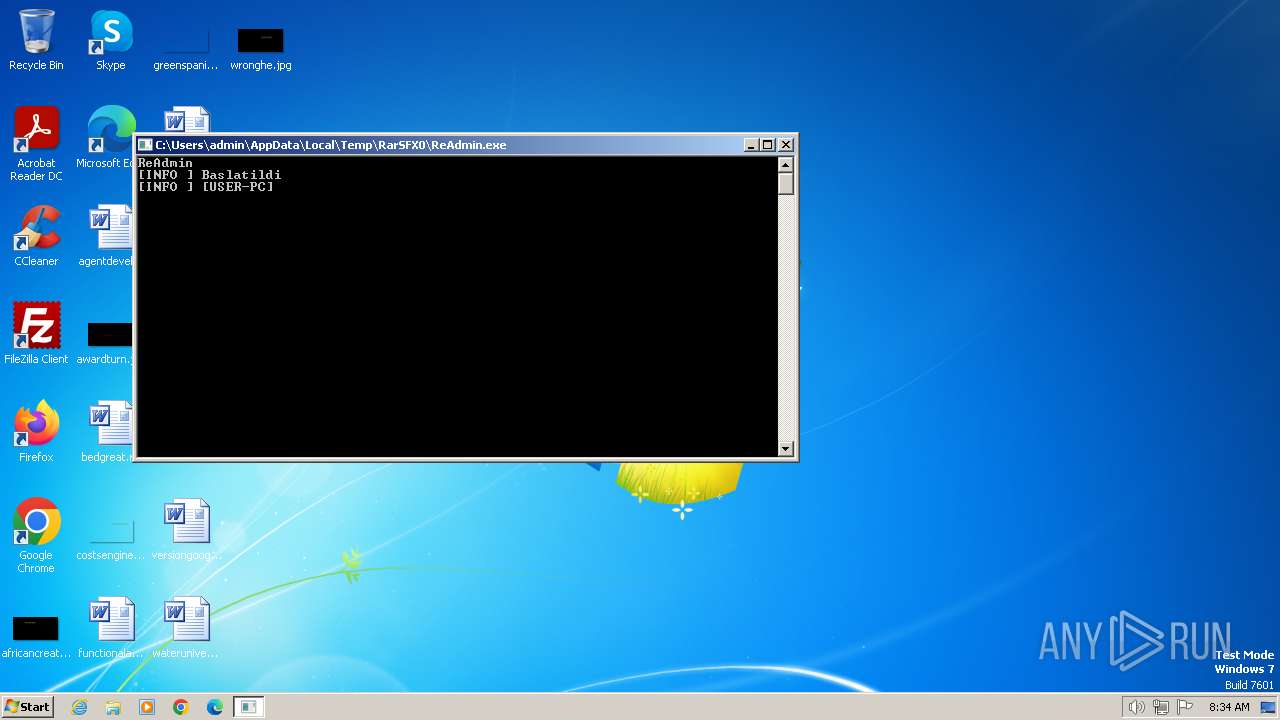
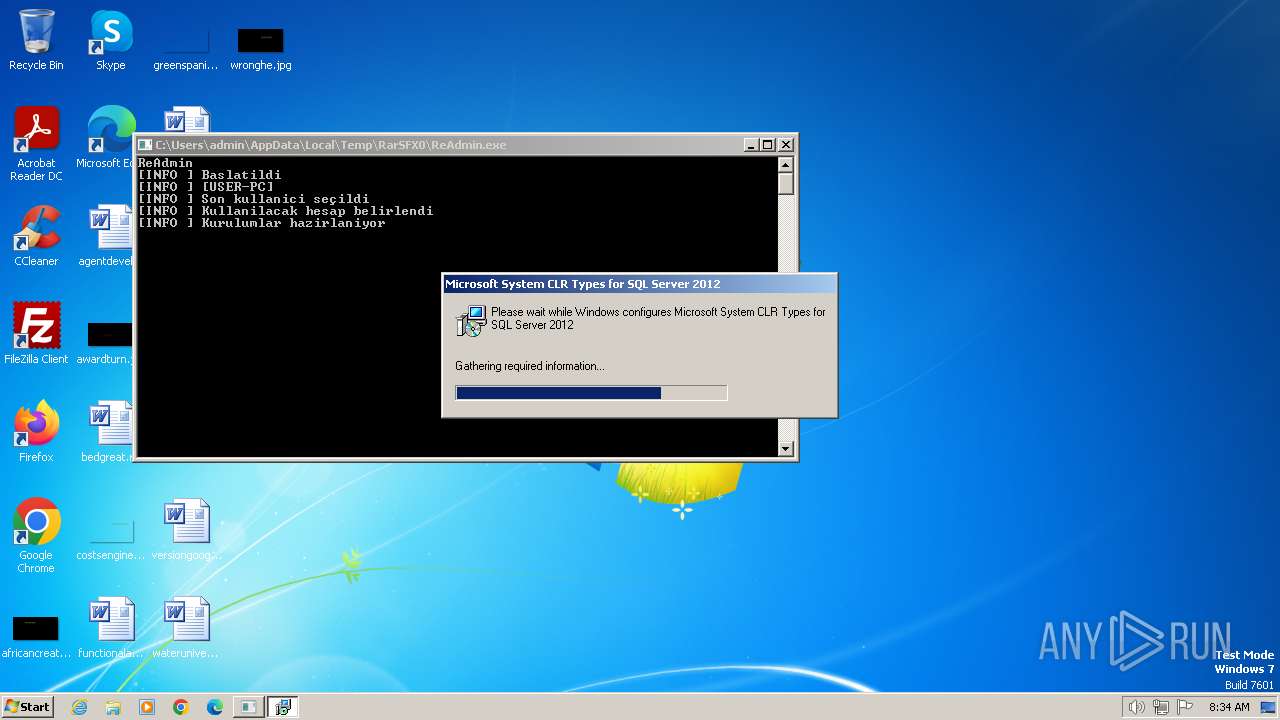
| File name: | Microsoft System CLR Types for SQL Server 2012.exe |
| Full analysis: | https://app.any.run/tasks/22a157c2-9dfd-4d60-b035-afa1a42607b0 |
| Verdict: | Malicious activity |
| Analysis date: | February 29, 2024, 08:34:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 9B567D1B0D0919F62286718562D2586F |
| SHA1: | AFF7AA33E2BC85A2A160D87FB4F3F76E52480320 |
| SHA256: | 962EB650C70CAA4E77632BBB9B70E75ECA6664E604328021FA9218DDFFF3E6AC |
| SSDEEP: | 49152:bh6AdAEdeymb5OUzHJS1945ptOLaVWSqZCjDRTn3/rk8qEo2vHWy3nHHIy6WNtD7:hrdeyuO6Q8ptcyGZCjx3jkvd2v20HHIO |
MALICIOUS
Drops the executable file immediately after the start
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
- ReAdmin.exe (PID: 3692)
SUSPICIOUS
Reads security settings of Internet Explorer
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
- ReAdmin.exe (PID: 3692)
Reads the Internet Settings
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
- ReAdmin.exe (PID: 3692)
Executable content was dropped or overwritten
- ReAdmin.exe (PID: 3692)
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
Executes as Windows Service
- VSSVC.exe (PID: 2692)
INFO
Reads the computer name
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
- ReAdmin.exe (PID: 3692)
- DummyExecutable.exe (PID: 2840)
Reads Environment values
- ReAdmin.exe (PID: 3692)
Reads the machine GUID from the registry
- ReAdmin.exe (PID: 3692)
- DummyExecutable.exe (PID: 2840)
Checks supported languages
- ReAdmin.exe (PID: 3692)
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
- DummyExecutable.exe (PID: 2840)
Create files in a temporary directory
- Microsoft System CLR Types for SQL Server 2012.exe (PID: 3656)
- ReAdmin.exe (PID: 3692)
Creates files in the program directory
- ReAdmin.exe (PID: 3692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:06:09 13:19:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 74752 |
| InitializedDataSize: | 121344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xac87 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
44
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2304 | "c:\windows\system32\msiexec.exe" /qb! /jm "C:\ProgramData\ReAdmin_240229083431\Microsoft System CLR Types for SQL Server 2012.msi" | C:\Windows\System32\msiexec.exe | — | ReAdmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2648 | "c:\windows\system32\msiexec.exe" /qb! /i "C:\ProgramData\ReAdmin_240229083431\Microsoft System CLR Types for SQL Server 2012.msi" | C:\Windows\System32\msiexec.exe | — | ReAdmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2692 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2840 | "C:\ProgramData\ReAdmin_240229083431\DummyExecutable.exe" | C:\ProgramData\ReAdmin_240229083431\DummyExecutable.exe | — | ReAdmin.exe | |||||||||||
User: admin Company: Hewlett-Packard Company Integrity Level: MEDIUM Description: DummyExecutable Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3656 | "C:\Users\admin\AppData\Local\Temp\Microsoft System CLR Types for SQL Server 2012.exe" | C:\Users\admin\AppData\Local\Temp\Microsoft System CLR Types for SQL Server 2012.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3692 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\ReAdmin.exe" Microsoft System CLR Types for SQL Server 2012.msi | C:\Users\admin\AppData\Local\Temp\RarSFX0\ReAdmin.exe | Microsoft System CLR Types for SQL Server 2012.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ReAdmin Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 087
Read events
4 071
Write events
16
Delete events
0
Modification events
| (PID) Process: | (3656) Microsoft System CLR Types for SQL Server 2012.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3656) Microsoft System CLR Types for SQL Server 2012.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3656) Microsoft System CLR Types for SQL Server 2012.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3656) Microsoft System CLR Types for SQL Server 2012.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3692) ReAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3692) ReAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3692) ReAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3692) ReAdmin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
6
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | Microsoft System CLR Types for SQL Server 2012.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Microsoft System CLR Types for SQL Server 2012.msi | executable | |
MD5:7AC710A153A554124490479080D2159F | SHA256:A9CF3E40C9A06DD9E9D0F689F3636BA3F58EC701B9405BA67881A802271BBBA1 | |||
| 3656 | Microsoft System CLR Types for SQL Server 2012.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\log4net.xml | xml | |
MD5:0139449BAB45772A1CFA45CB73017224 | SHA256:3831118D9DDF8FA5BBFBDAAC52E8EF9AD010B3E3F1C211E3AC5B3382689FDC24 | |||
| 3692 | ReAdmin.exe | C:\ProgramData\ReAdmin_240229083431\Microsoft System CLR Types for SQL Server 2012.msi | executable | |
MD5:7AC710A153A554124490479080D2159F | SHA256:A9CF3E40C9A06DD9E9D0F689F3636BA3F58EC701B9405BA67881A802271BBBA1 | |||
| 3656 | Microsoft System CLR Types for SQL Server 2012.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\ReAdmin.exe | executable | |
MD5:C0D2A5BCC43394170E1C9B81E2F03B59 | SHA256:467F7C9959709E8F028910B21668C5B42093DAA12E4D0C6235FB28214DD60D00 | |||
| 3692 | ReAdmin.exe | C:\ProgramData\ReAdmin_240229083431\DummyExecutable.exe | executable | |
MD5:F9A12D6699372B0B5F730039FB9328ED | SHA256:5BC6C54379078BAC193CDD832243FA95BA94938277F115B61A00516654E47492 | |||
| 3656 | Microsoft System CLR Types for SQL Server 2012.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\DummyExecutable.exe | executable | |
MD5:F9A12D6699372B0B5F730039FB9328ED | SHA256:5BC6C54379078BAC193CDD832243FA95BA94938277F115B61A00516654E47492 | |||
| 3656 | Microsoft System CLR Types for SQL Server 2012.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\log4net.dll | executable | |
MD5:4EB9B506B3454921782A60D40690ED37 | SHA256:3C67113EB19B85EEDD10AE5316A3DDC832D4DC7D97EB1AABA853674A018E4B51 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |