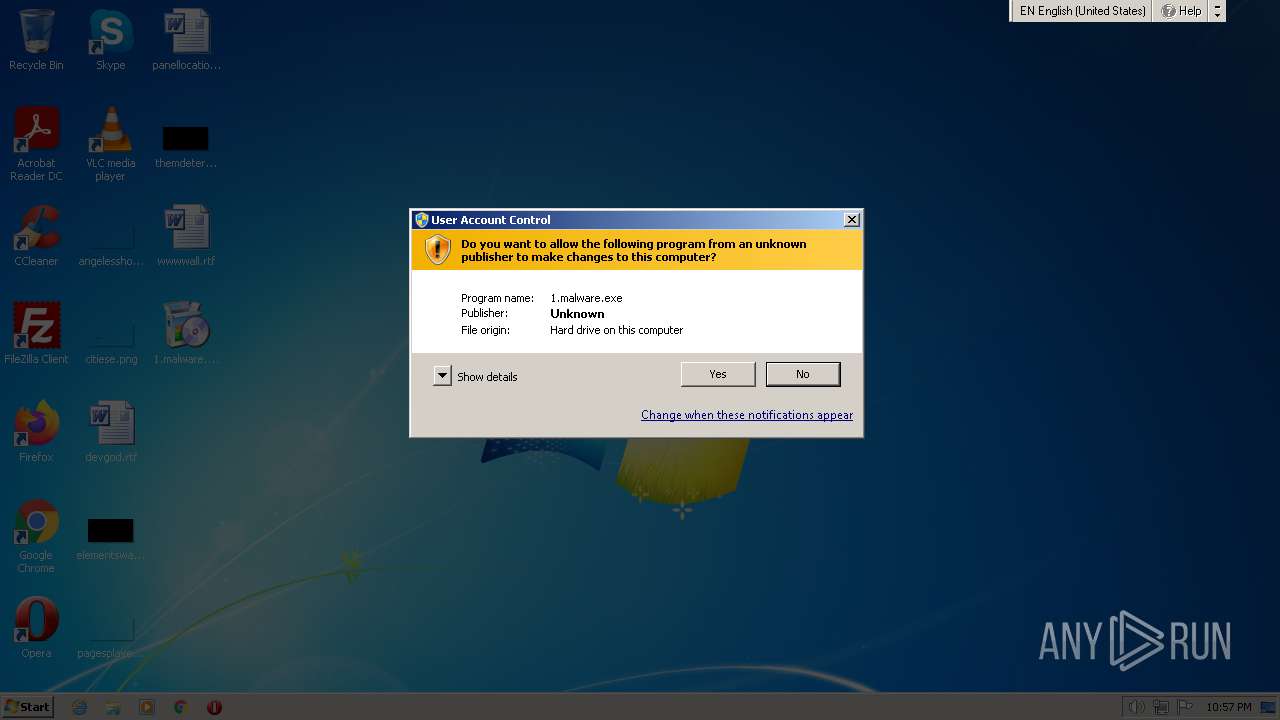
| File name: | 1.malware |
| Full analysis: | https://app.any.run/tasks/9c9b378d-3b87-4b91-83ea-a20e9704963f |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 22:57:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 035D68032502DD1B2FAE8CD5CC81BEFA |
| SHA1: | 64FEB660189E7C5E4F7AFBF28A232B8D3FC692A7 |
| SHA256: | 961A53089F14C69061C3E156BF279550FB108F8023CC54E1086343ECA6D3C437 |
| SSDEEP: | 24576:F4nXubIQGyxbPV0db26AFe/lTuIeDNUEv2fyAMBY/pHyq0BNF5:Fqe3f6m6Vu10ybRl7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application was dropped or rewritten from another process
- 1.malware.tmp (PID: 3080)
- 1.malware.tmp (PID: 2508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2021-Jun-03 08:09:11 |
| Detected languages: |
|
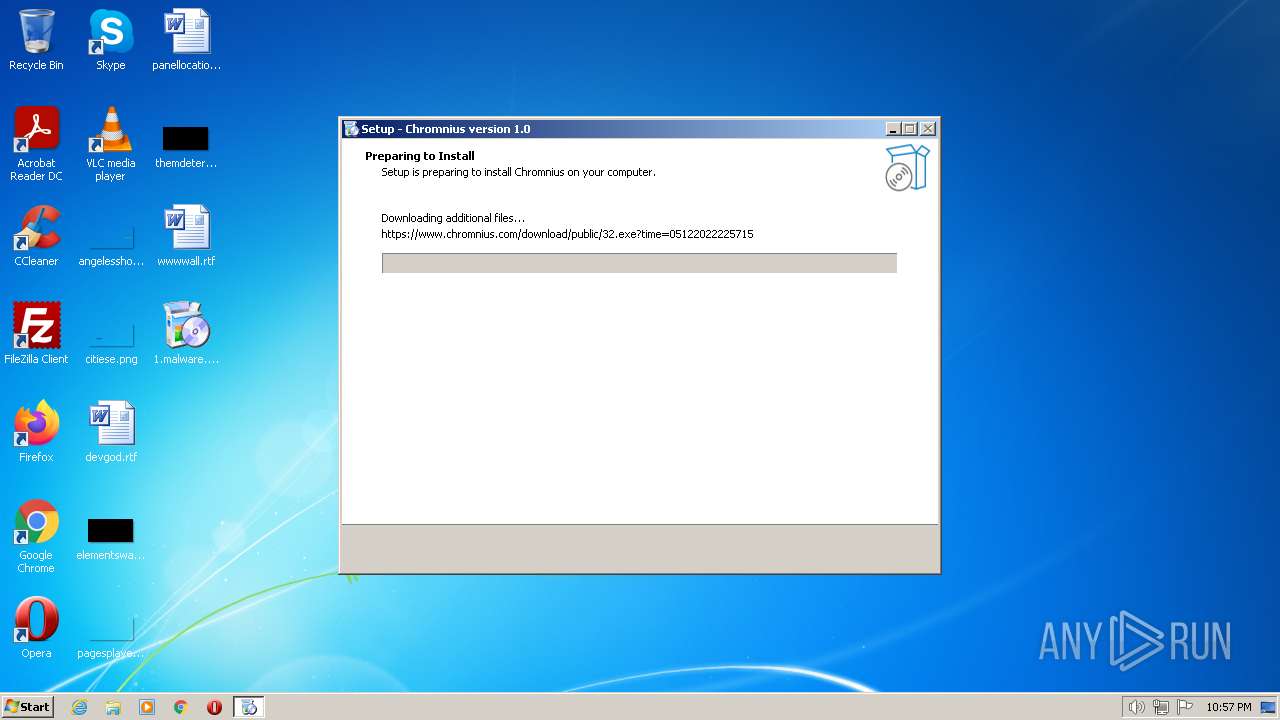
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Dragon Boss Solutions LLC |
| FileDescription: | Chromnius Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | Chromnius |
| ProductVersion: | 1.0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 10 |
| TimeDateStamp: | 2021-Jun-03 08:09:11 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 734748 | 735232 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.35606 |
.itext | 741376 | 5768 | 6144 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.97275 |
.data | 749568 | 14244 | 14336 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.0444 |
.bss | 765952 | 28136 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 794624 | 3894 | 4096 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8987 |
.didata | 798720 | 420 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75636 |
.edata | 802816 | 154 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.87222 |
.tls | 806912 | 24 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 811008 | 93 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.38389 |
.rsrc | 815104 | 23496 | 23552 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.94251 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.75207 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
2 | 4.12472 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.90366 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 4.83453 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 3.68002 | 1640 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 4.49965 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
4086 | 3.16547 | 864 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4087 | 3.40938 | 608 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4088 | 3.31153 | 1116 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4089 | 3.33977 | 1036 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 779836 |
__dbk_fcall_wrapper | 2 | 53408 |
TMethodImplementationIntercept | 3 | 344160 |
Total processes
41
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2308 | "C:\Users\admin\Desktop\1.malware.exe" | C:\Users\admin\Desktop\1.malware.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Dragon Boss Solutions LLC Integrity Level: MEDIUM Description: Chromnius Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\AppData\Local\Temp\is-0ILKA.tmp\1.malware.tmp" /SL5="$6019E,785920,785920,C:\Users\admin\Desktop\1.malware.exe" /SPAWNWND=$501C8 /NOTIFYWND=$50198 | C:\Users\admin\AppData\Local\Temp\is-0ILKA.tmp\1.malware.tmp | 1.malware.exe | ||||||||||||
User: admin Company: Dragon Boss Solutions LLC Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2588 | "C:\Users\admin\Desktop\1.malware.exe" /SPAWNWND=$501C8 /NOTIFYWND=$50198 | C:\Users\admin\Desktop\1.malware.exe | 1.malware.tmp | ||||||||||||
User: admin Company: Dragon Boss Solutions LLC Integrity Level: HIGH Description: Chromnius Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3080 | "C:\Users\admin\AppData\Local\Temp\is-7BM4Q.tmp\1.malware.tmp" /SL5="$50198,785920,785920,C:\Users\admin\Desktop\1.malware.exe" | C:\Users\admin\AppData\Local\Temp\is-7BM4Q.tmp\1.malware.tmp | — | 1.malware.exe | |||||||||||
User: admin Company: Dragon Boss Solutions LLC Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
3 022
Read events
3 005
Write events
17
Delete events
0
Modification events
| (PID) Process: | (2508) 1.malware.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: CC090000C714F7EAFC08D901 | |||
| (PID) Process: | (2508) 1.malware.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 5A18FA352663E02BDFE5123C882D54545012A2FB9CBF319F251F6DD715184009 | |||
| (PID) Process: | (2508) 1.malware.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2508) 1.malware.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2508 | 1.malware.tmp | C:\Users\admin\AppData\Local\Temp\is-RG9CD.tmp\is-MC3A5.tmp | executable | |
MD5:— | SHA256:— | |||
| 2308 | 1.malware.exe | C:\Users\admin\AppData\Local\Temp\is-7BM4Q.tmp\1.malware.tmp | executable | |
MD5:8414E5E35E0046908D6FA180B8EAB078 | SHA256:CDABA98E37E511935183050213D5E08C485F7077A55A95A69A1719CF5EDB2B6C | |||
| 2588 | 1.malware.exe | C:\Users\admin\AppData\Local\Temp\is-0ILKA.tmp\1.malware.tmp | executable | |
MD5:8414E5E35E0046908D6FA180B8EAB078 | SHA256:CDABA98E37E511935183050213D5E08C485F7077A55A95A69A1719CF5EDB2B6C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
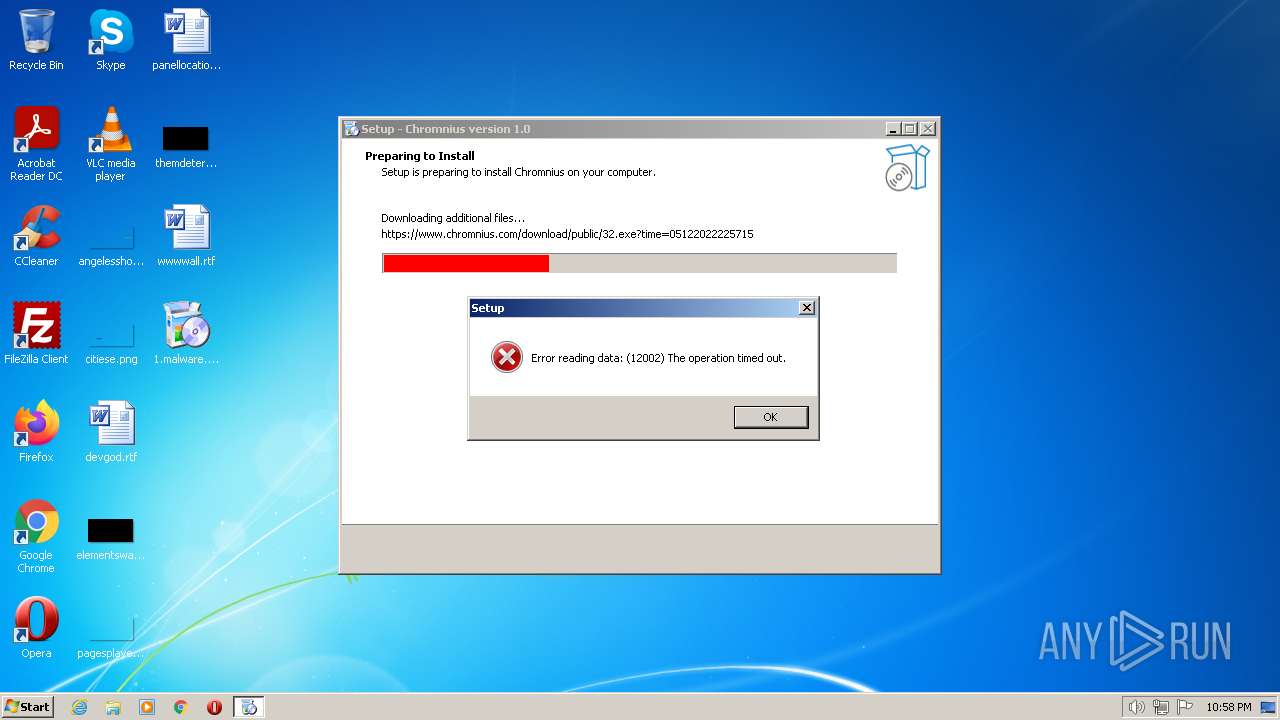
2508 | 1.malware.tmp | 188.114.96.3:443 | www.chromnius.com | CLOUDFLARENET | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.chromnius.com |
| malicious |