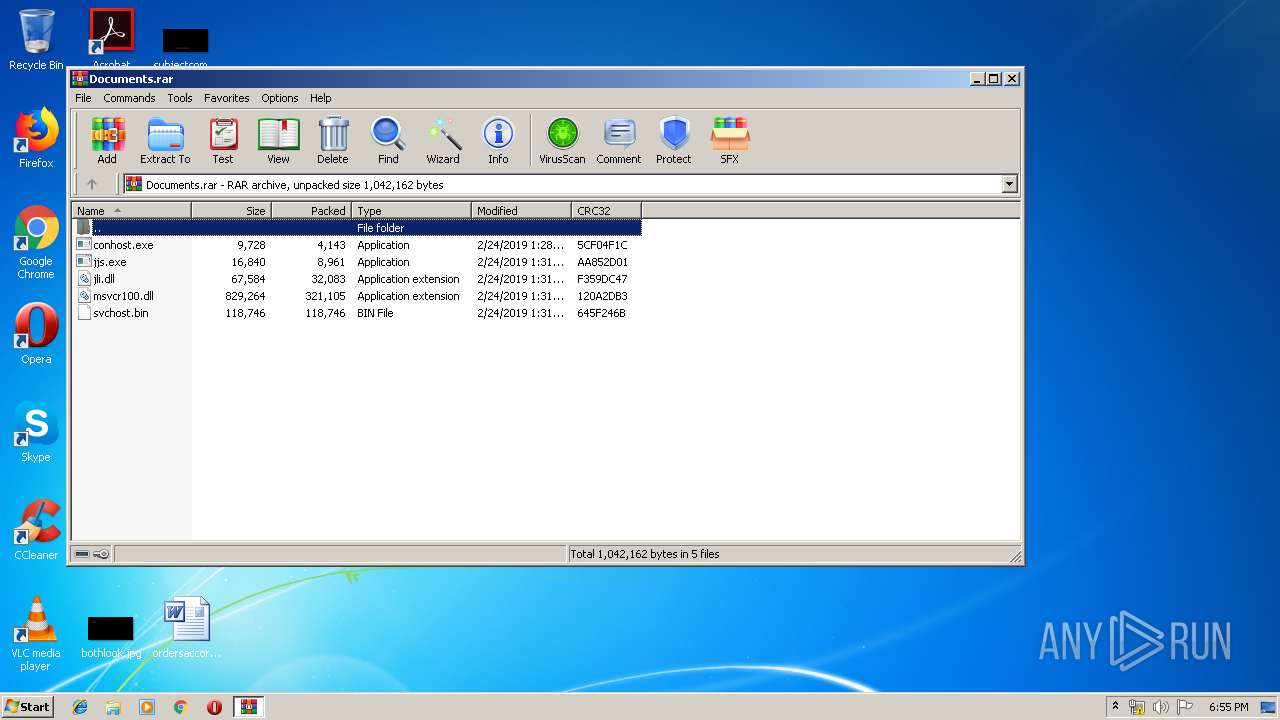
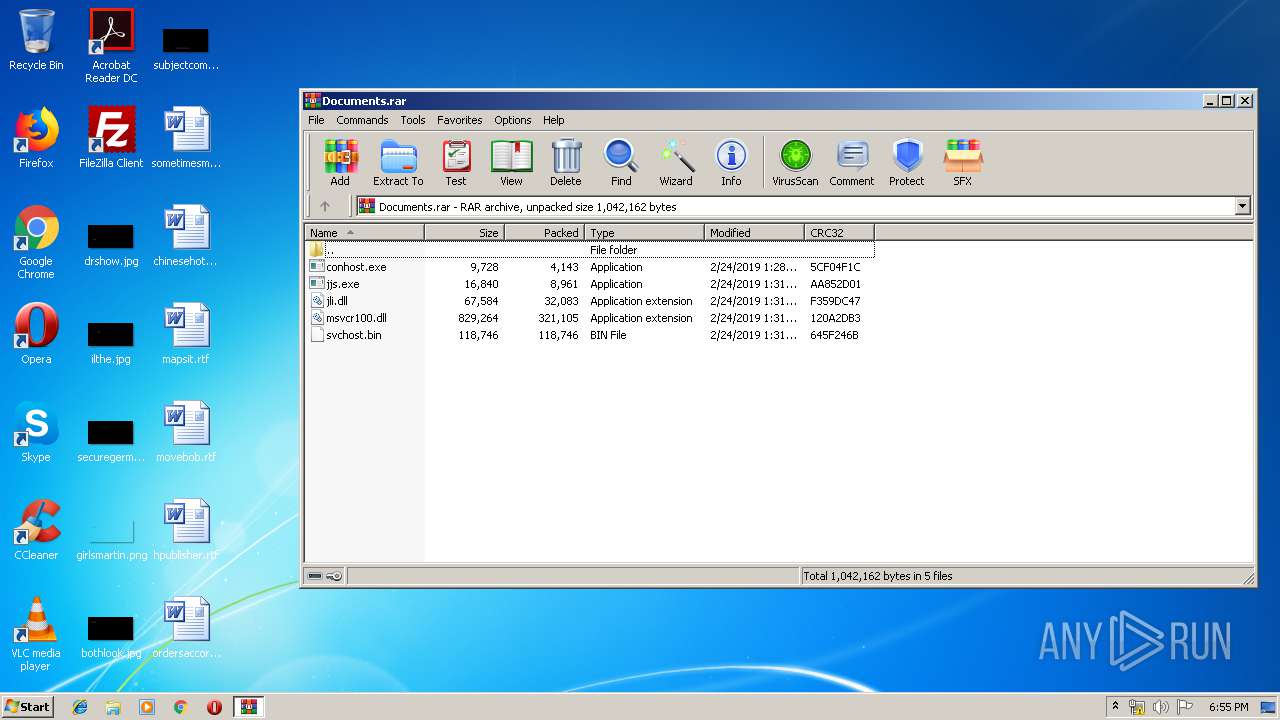
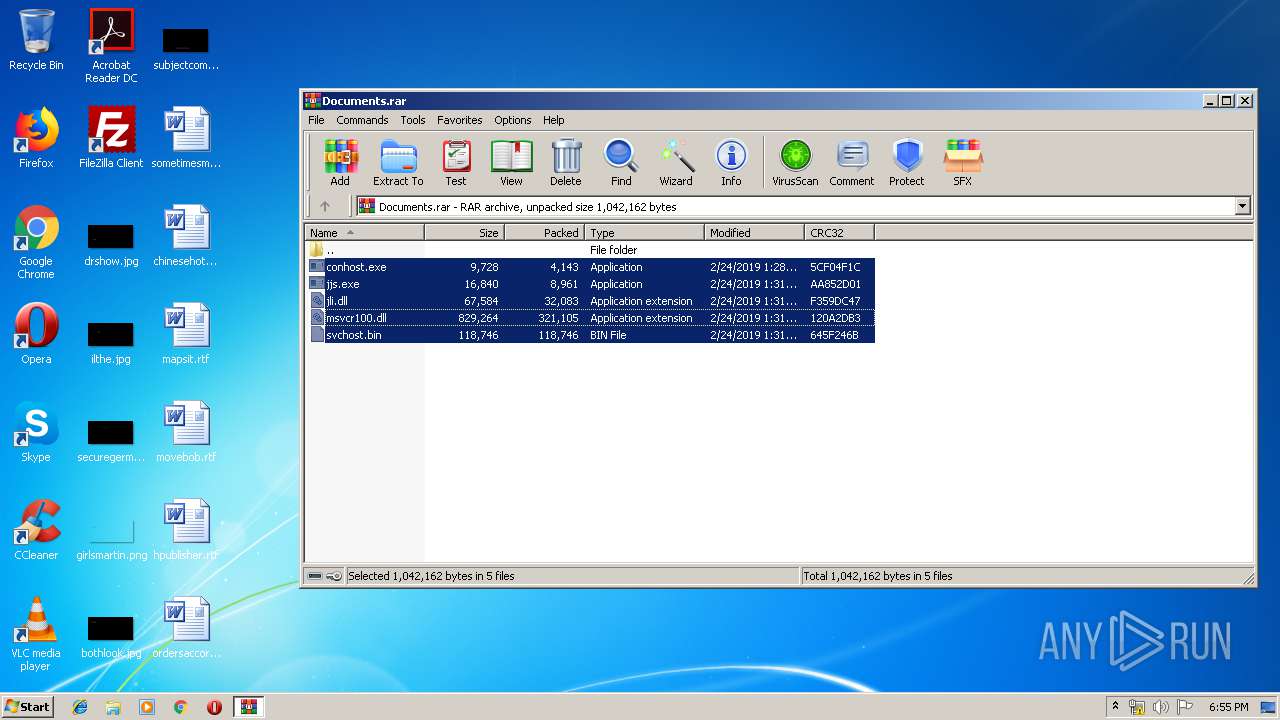
| File name: | Documents.rar |
| Full analysis: | https://app.any.run/tasks/615728fc-985a-4a83-9199-a30910857f00 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2019, 17:54:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CAA6BB46CA715449FDC0ECA3ABE727DD |
| SHA1: | 7D6E1D9307295F698E35791000318B825FD77ADB |
| SHA256: | 95ECD23E496FD99C5F77F61F9B5C6743523AF4E1FB14D120702B12F70A325137 |
| SSDEEP: | 12288:P0fUBbp0d9AUwIaig2+5tYq1i/mHTkWIwm:0GUDQ2g6Ki/mzkum |
MALICIOUS
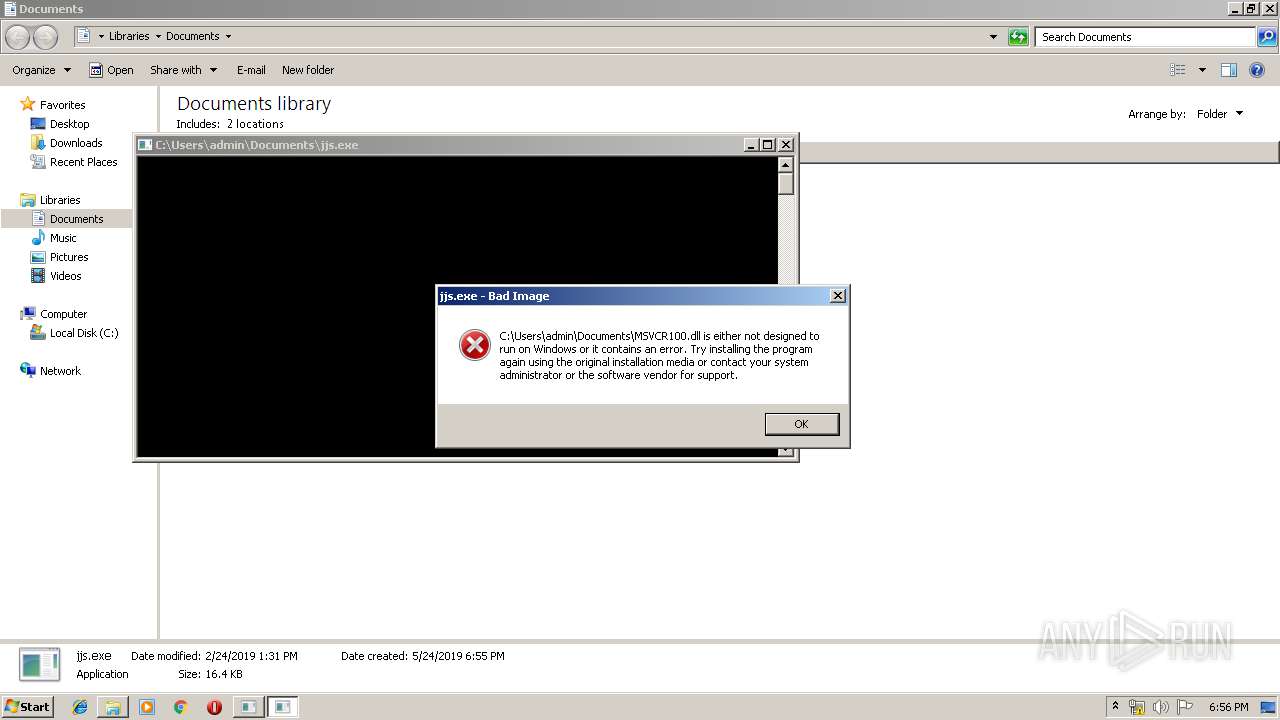
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2080)
- explorer.exe (PID: 116)
Application was dropped or rewritten from another process
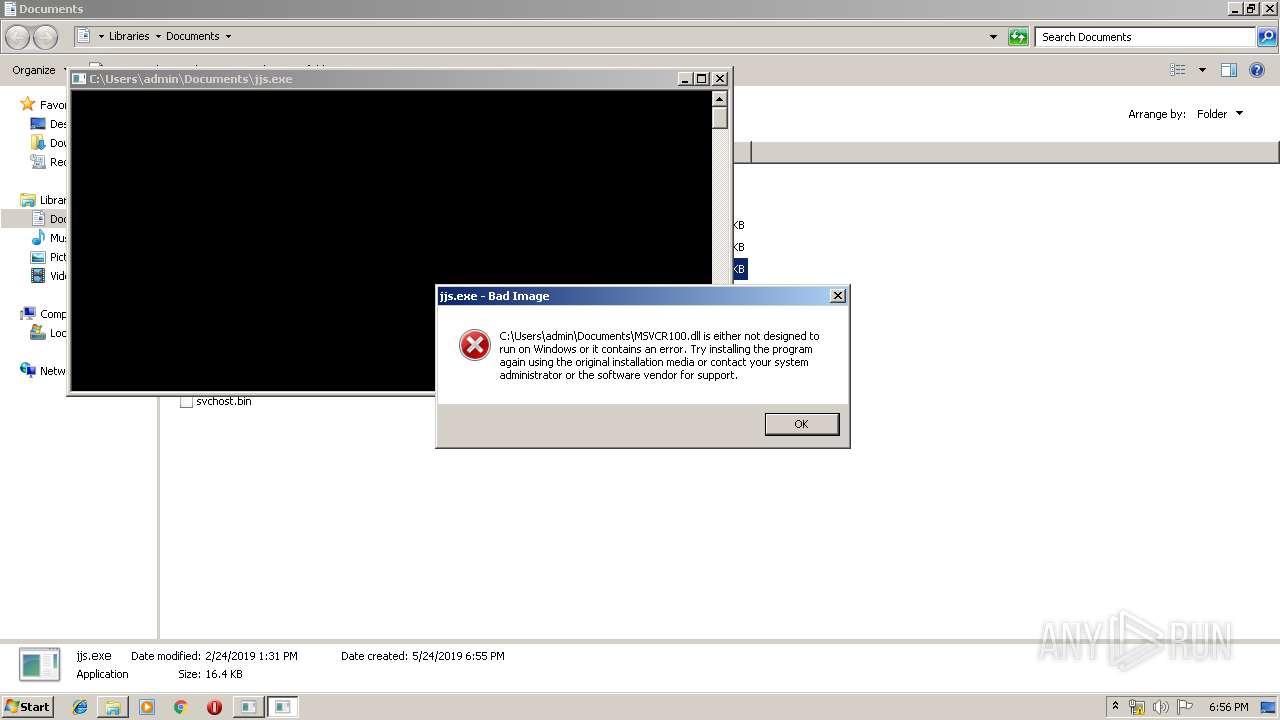
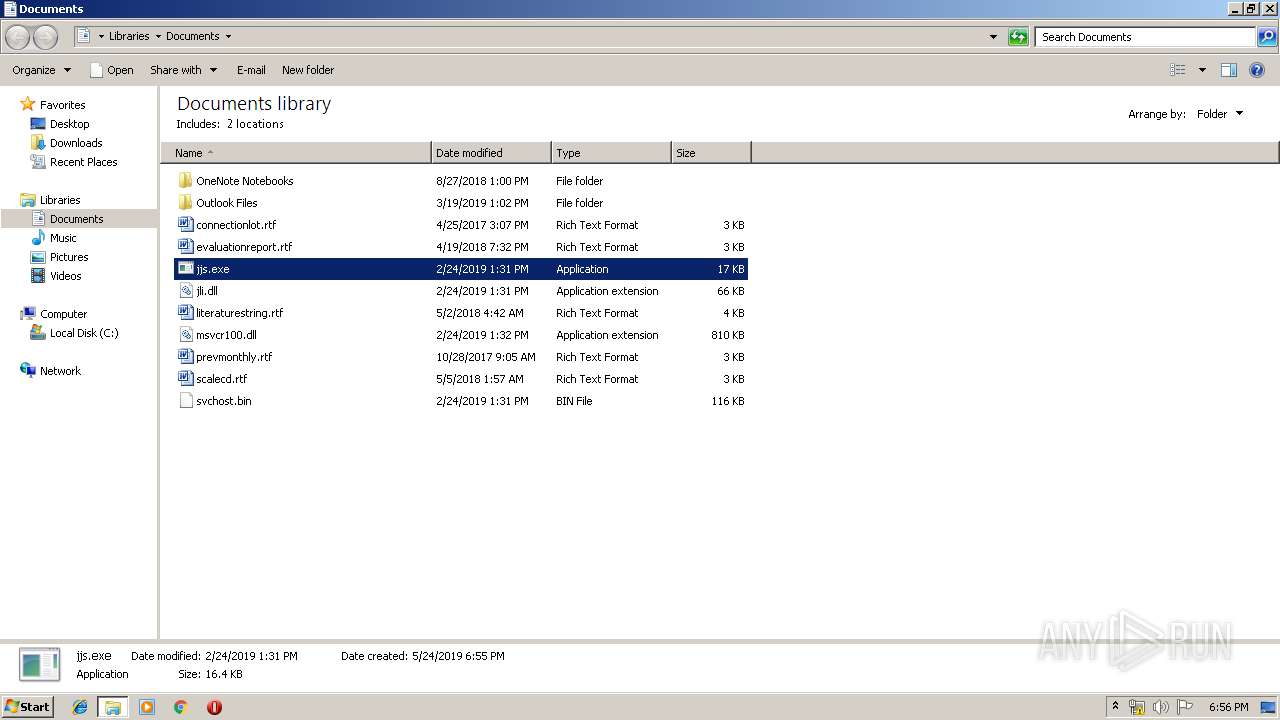
- jjs.exe (PID: 3196)
- jjs.exe (PID: 2676)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 116)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 116)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
38
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
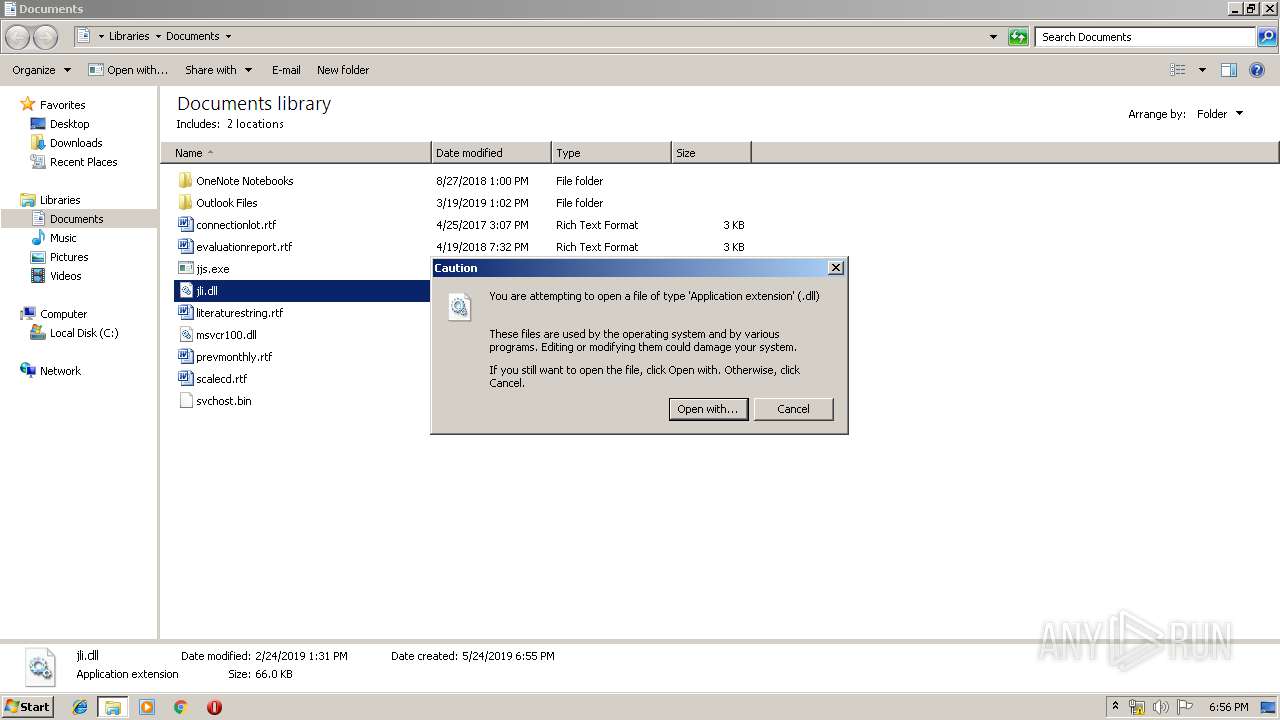
| 2612 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Documents\jli.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\Documents\jjs.exe" | C:\Users\admin\Documents\jjs.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 3221226330 Version: 8.0.1710.11 Modules
| |||||||||||||||
| 3196 | "C:\Users\admin\Documents\jjs.exe" | C:\Users\admin\Documents\jjs.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 3221226330 Version: 8.0.1710.11 Modules
| |||||||||||||||
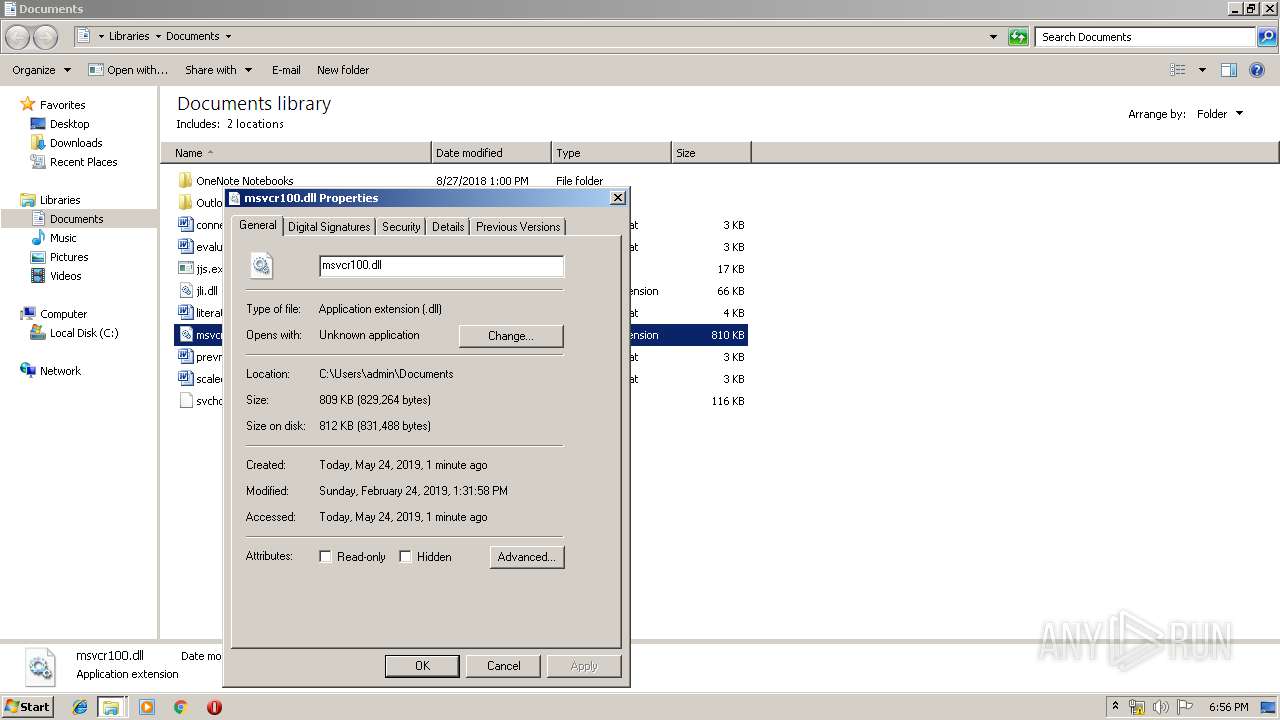
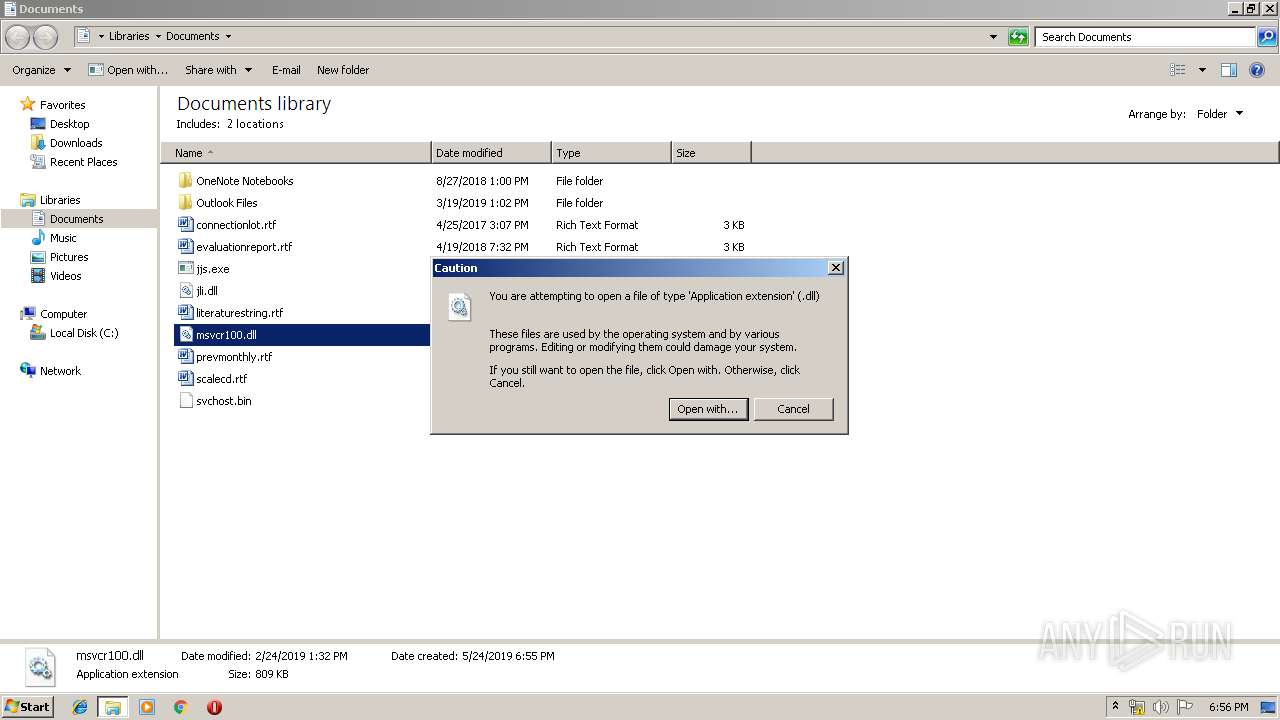
| 3208 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Documents\msvcr100.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3336 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Documents.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
3 562
Read events
3 362
Write events
199
Delete events
1
Modification events
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000418795FC2F2C5A46852A5EA30B2A11D100000000020000000000106600000001000020000000DB0ADD4A17F563B77CC6DED7834ADD4C78B980F48608ED2968371C1938C2DFEB000000000E8000000002000020000000ABC62E13B82E8C6885D0D9909884C4ED242640BEDAE2624F67C4357B76DF55963000000003E27C437D72324EFB97101071BE10C041ECCFC2DC2817A45DD8C90A44E42FC4E623E49DA039658FD2F61E505C3EB6F740000000DD9388B22336BD367BF81A38DC3788DE7223FB0447D56D12AD4CBB69E036A9C1D6CC4FBFAD606E2537D999F1C9003995810D82DEFF0653C73006A10426FB4B59 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Documents.rar | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3336) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
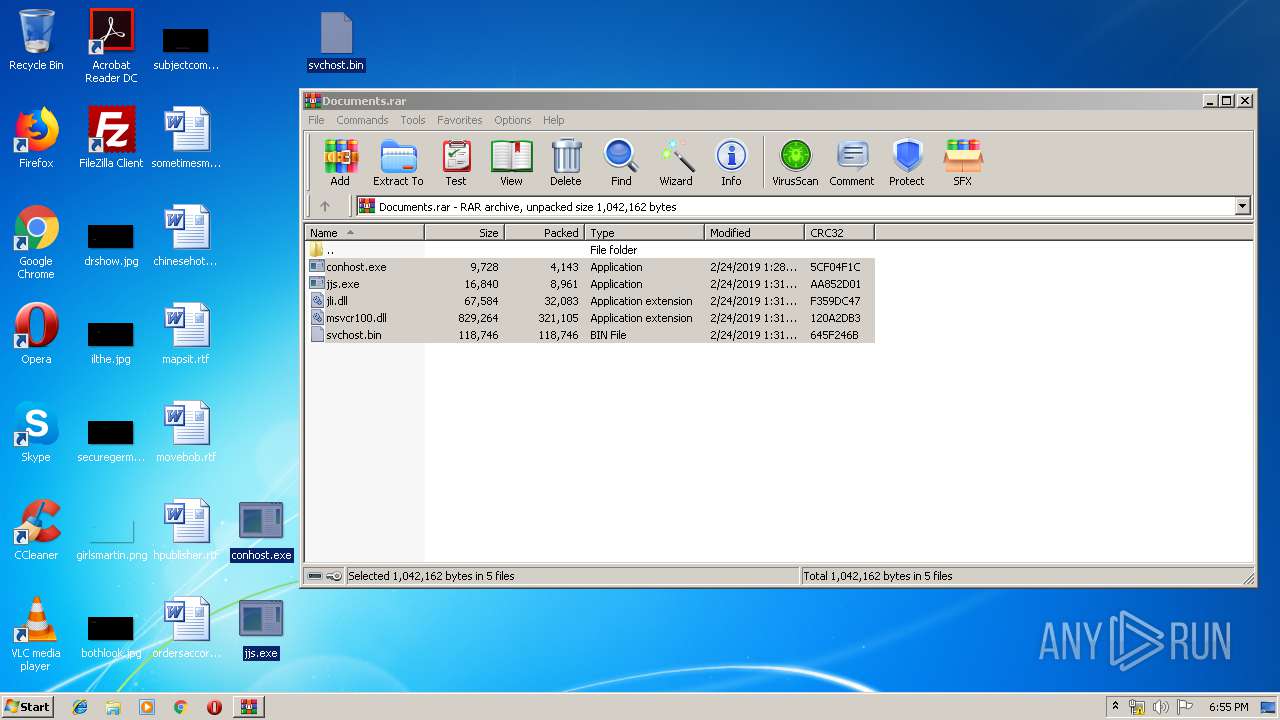
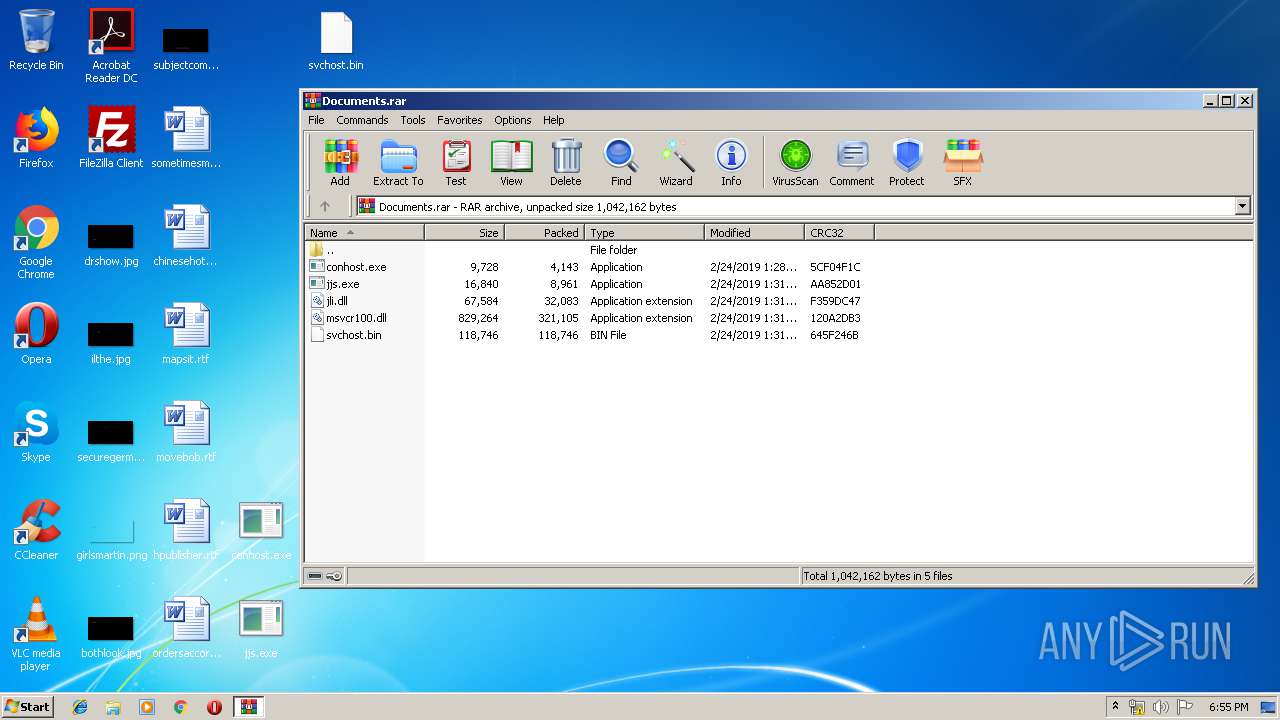
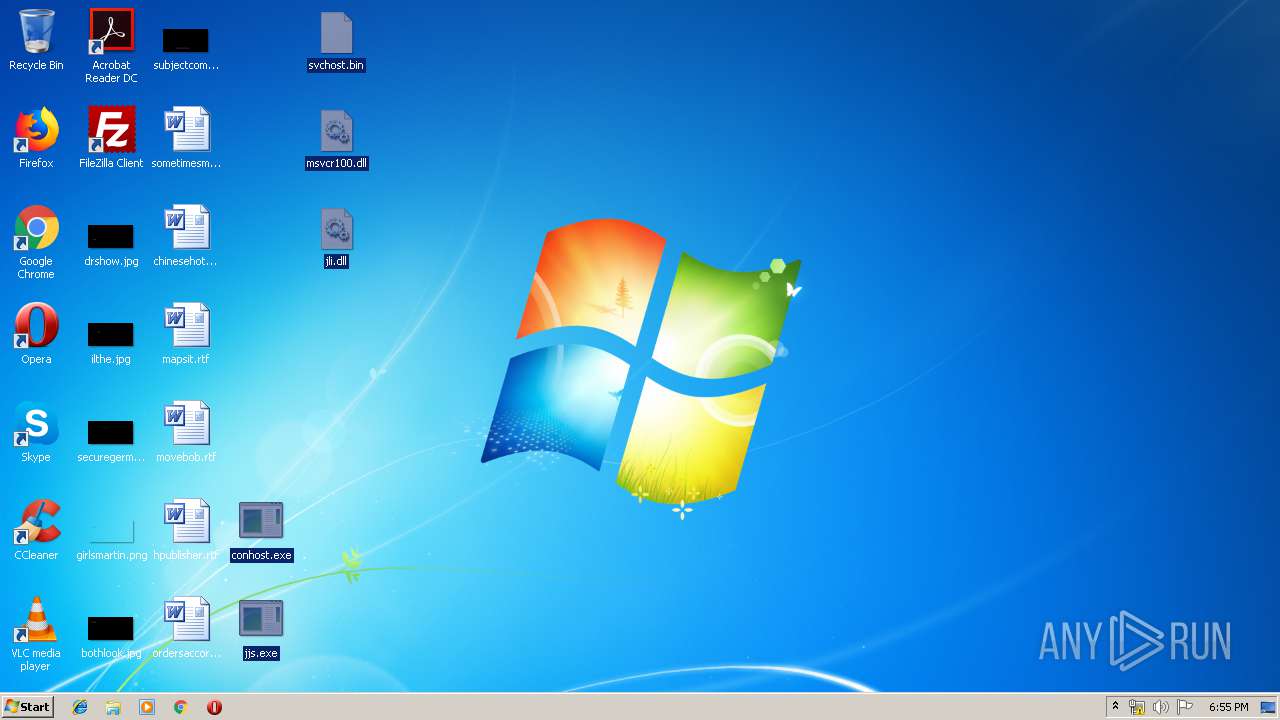
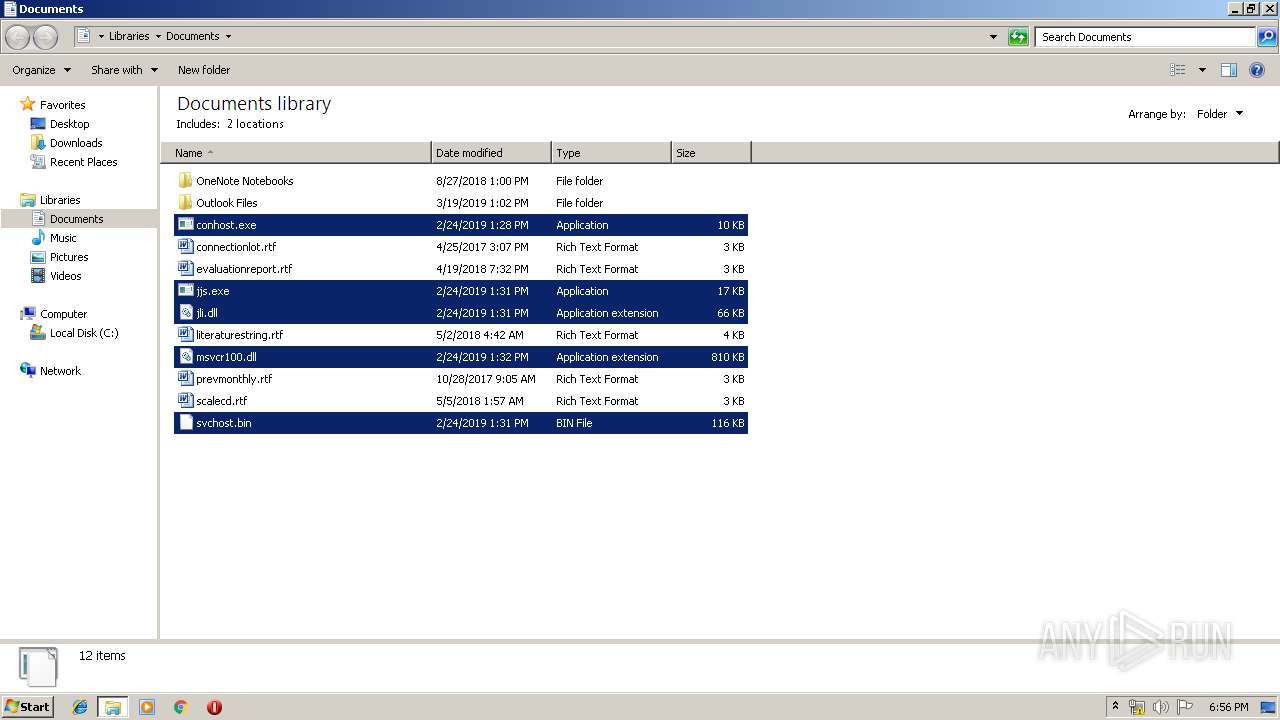
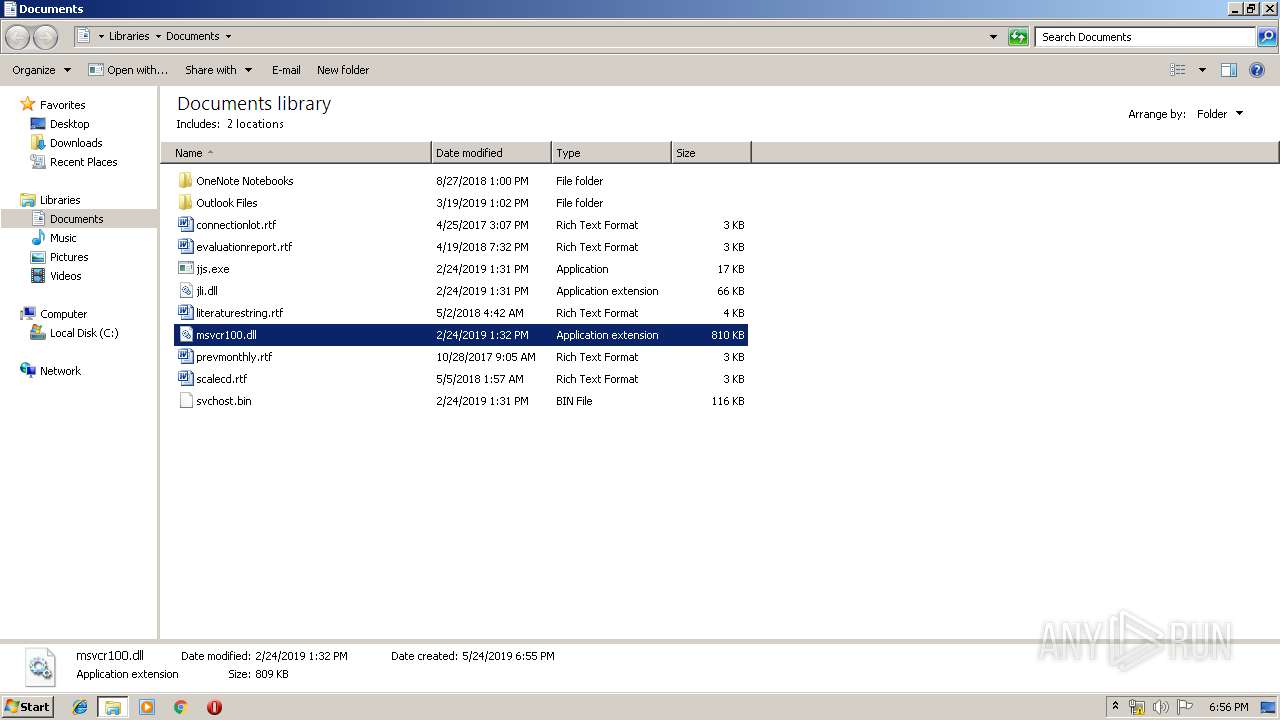
Executable files
9
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.3918\jjs.exe | — | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.3918\jli.dll | — | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.3918\msvcr100.dll | — | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.3918\svchost.bin | — | |
MD5:— | SHA256:— | |||
| 3336 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3336.3918\conhost.exe | — | |
MD5:— | SHA256:— | |||
| 116 | explorer.exe | C:\Users\admin\Documents\jli.dll | executable | |
MD5:— | SHA256:— | |||
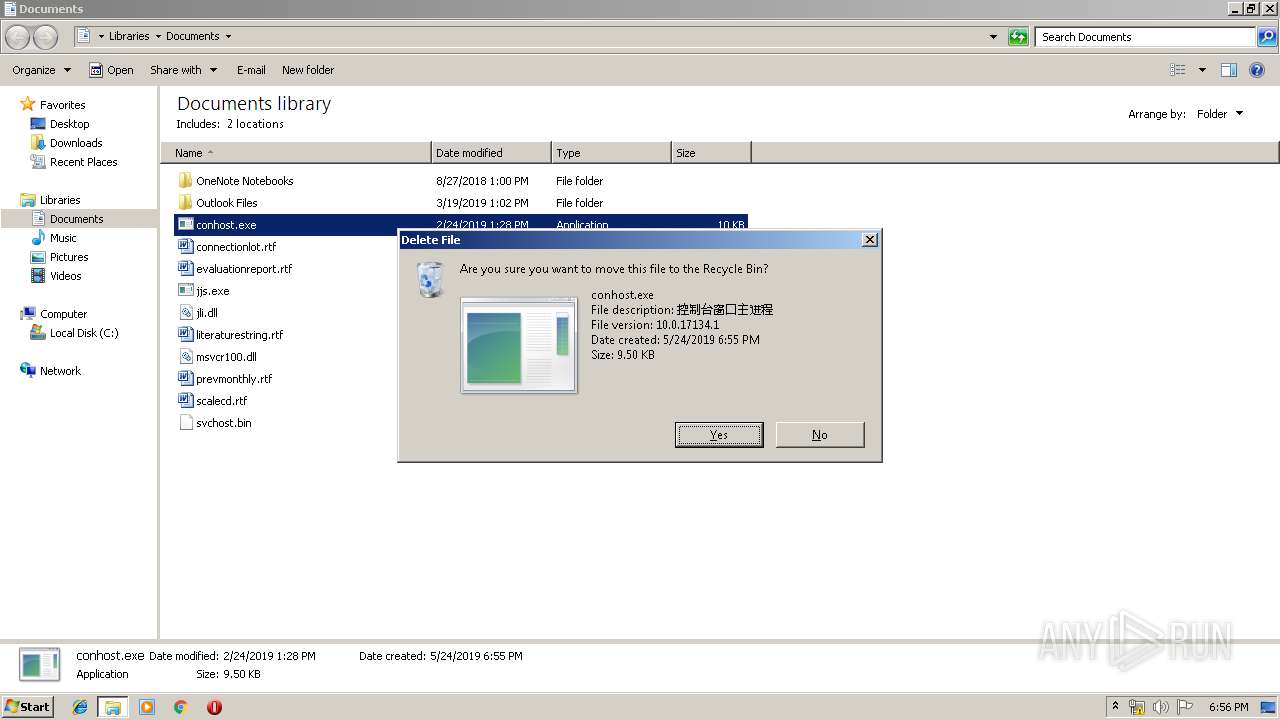
| 116 | explorer.exe | C:\Users\admin\Documents\conhost.exe | executable | |
MD5:— | SHA256:— | |||
| 116 | explorer.exe | C:\$RECYCLE.BIN\S-1-5-21-1302019708-1500728564-335382590-1000\$RY0FL9Q.exe | executable | |
MD5:— | SHA256:— | |||
| 116 | explorer.exe | C:\$RECYCLE.BIN\S-1-5-21-1302019708-1500728564-335382590-1000\$IY0FL9Q.exe | binary | |
MD5:— | SHA256:— | |||
| 116 | explorer.exe | C:\Users\admin\Desktop\conhost.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report