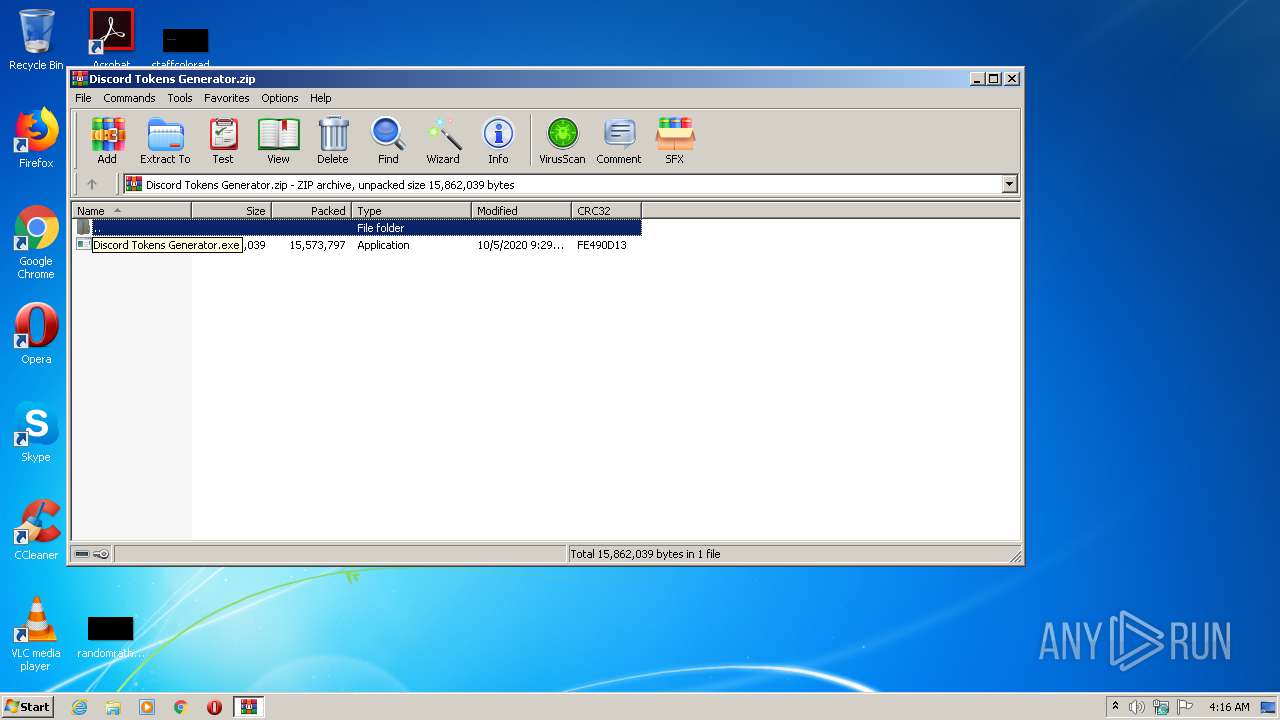
| File name: | Discord Tokens Generator.zip |
| Full analysis: | https://app.any.run/tasks/6e33a61b-b5dc-45fc-bd73-87a364639964 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 03:16:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B1B310BB23492228FEC2352927E3B6EE |
| SHA1: | 14E28A28A5D67562B145EB34012A98769D69F654 |
| SHA256: | 95E4FF61B8BD20F5FB6B4A445F59503447926B30BB886C6335FE3339002AE1A1 |
| SSDEEP: | 393216:Xz6wDVoaHjC9xH2/qX3e4dt4BQDP6Ew/1p21vys:Xz6wDnHm9xWUpHAkU/1p+ |
MALICIOUS
Application was dropped or rewritten from another process
- Discord Tokens Generator.exe (PID: 3620)
- Discord Tokens Generator.exe (PID: 2584)
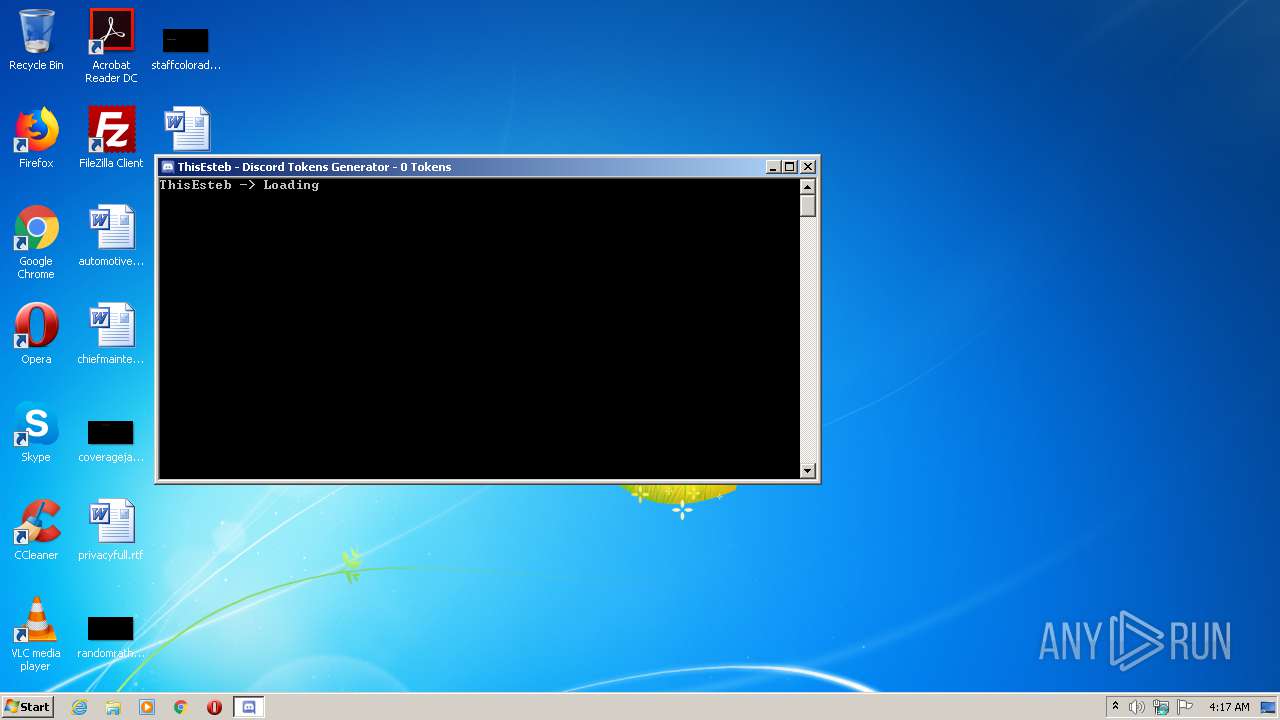
Actions looks like stealing of personal data
- Discord Tokens Generator.exe (PID: 2584)
Loads dropped or rewritten executable
- Discord Tokens Generator.exe (PID: 2584)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3260)
- Discord Tokens Generator.exe (PID: 3620)
Application launched itself
- Discord Tokens Generator.exe (PID: 3620)
Creates files in the user directory
- Discord Tokens Generator.exe (PID: 2584)
Starts CMD.EXE for commands execution
- Discord Tokens Generator.exe (PID: 2584)
Loads Python modules
- Discord Tokens Generator.exe (PID: 2584)
INFO
Manual execution by user
- cmd.exe (PID: 2928)
- NOTEPAD.EXE (PID: 3192)
- notepad.exe (PID: 3904)
- chrome.exe (PID: 3876)
- NOTEPAD.EXE (PID: 1204)
- cmd.exe (PID: 1876)
Reads settings of System Certificates
- chrome.exe (PID: 3596)
- Discord Tokens Generator.exe (PID: 2584)
Reads the hosts file
- chrome.exe (PID: 3596)
- chrome.exe (PID: 3876)
Dropped object may contain Bitcoin addresses
- Discord Tokens Generator.exe (PID: 3620)
Application launched itself
- chrome.exe (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:10:05 10:29:01 |
| ZipCRC: | 0xfe490d13 |
| ZipCompressedSize: | 15573797 |
| ZipUncompressedSize: | 15862039 |
| ZipFileName: | Discord Tokens Generator.exe |
Total processes
94
Monitored processes
50
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5952552047521484143 --renderer-client-id=39 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
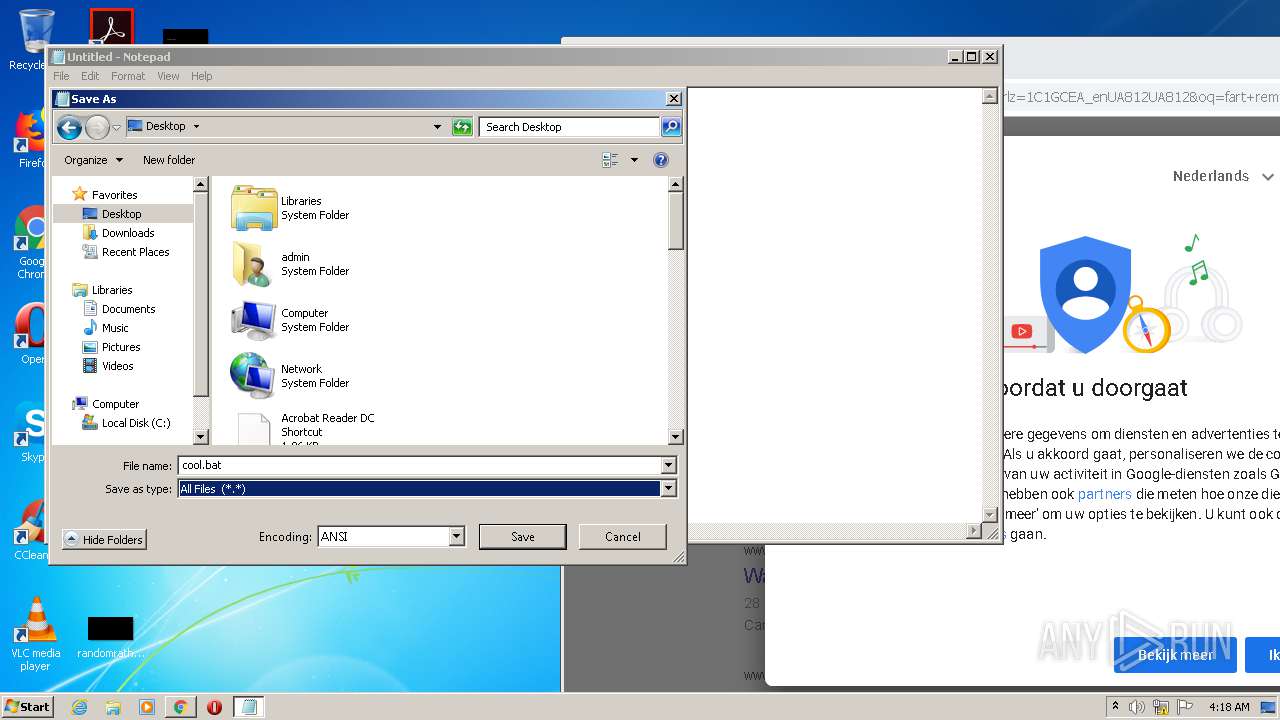
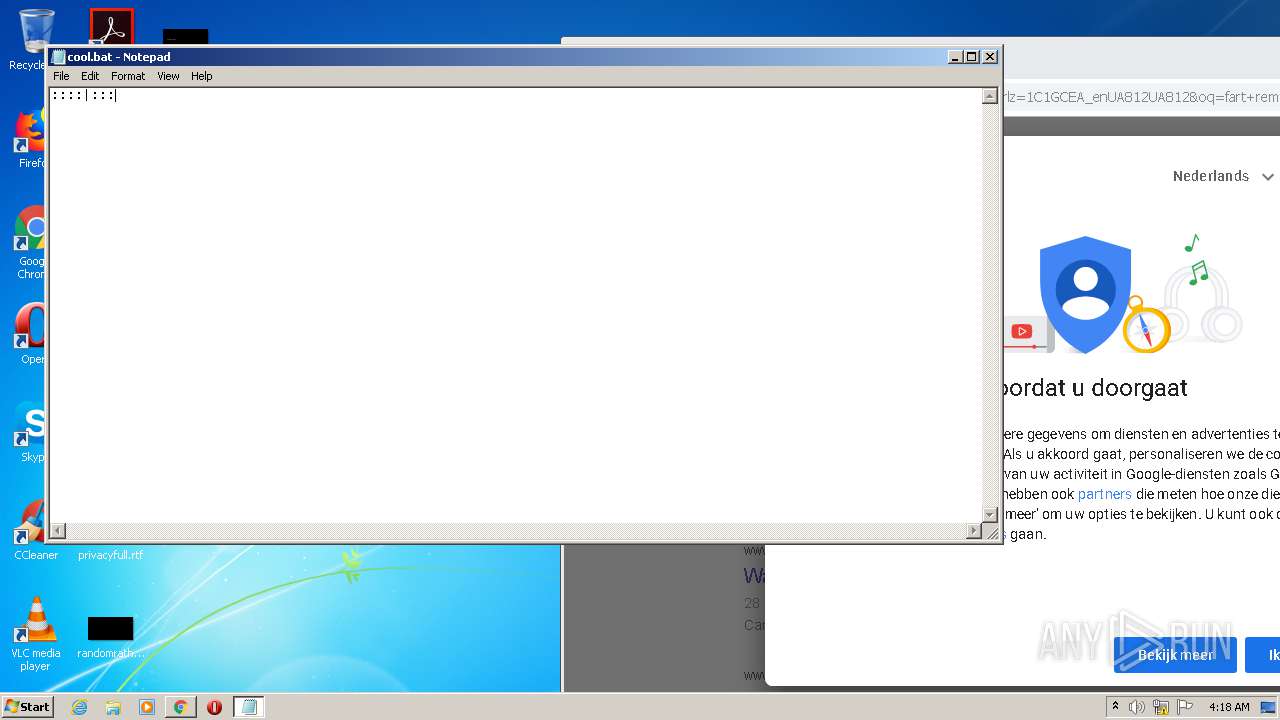
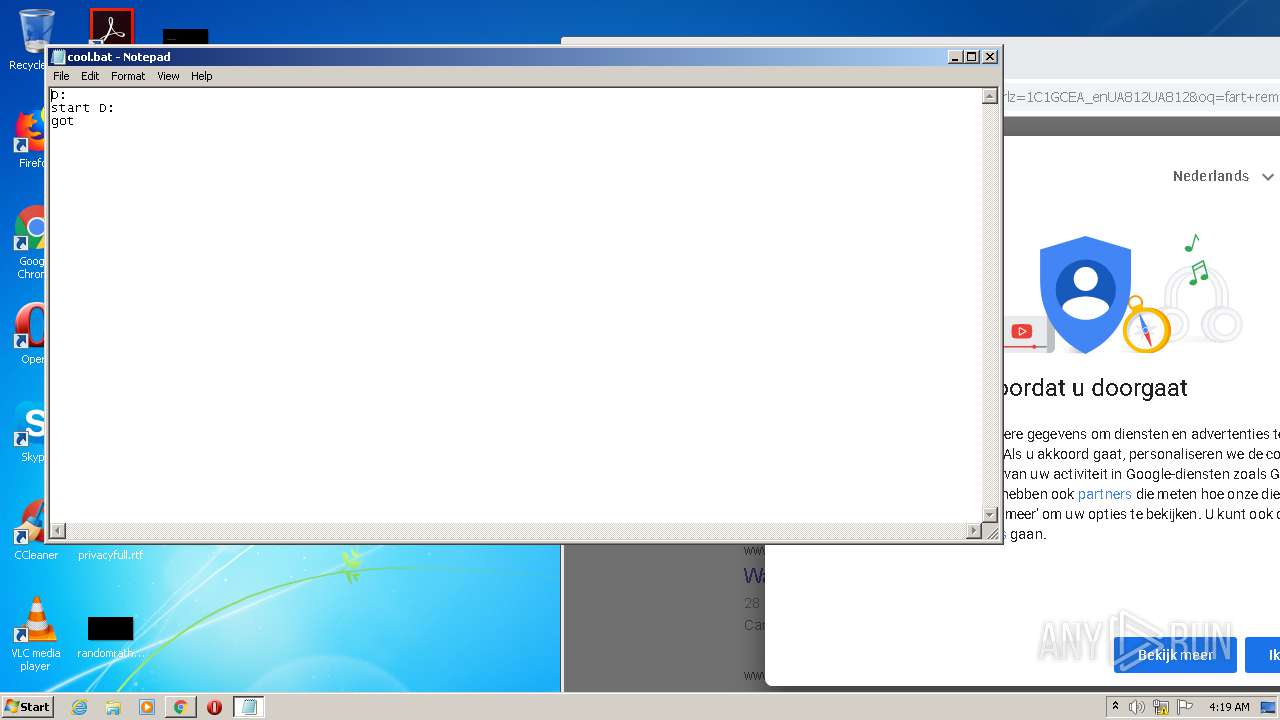
| 1204 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\cool.bat | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8436995375847808842 --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3956 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10699065611576411019 --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1332 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3436704667062221845 --renderer-client-id=36 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4092 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7334028933953192805 --mojo-platform-channel-handle=4068 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1876 | cmd /c ""C:\Users\admin\Desktop\cool.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8741610048066867782 --renderer-client-id=40 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15662266847321349872 --renderer-client-id=38 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4060 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,1031986387425097470,12622182521222023346,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15846681105093190761 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2496 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 895
Read events
1 675
Write events
214
Delete events
6
Modification events
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Discord Tokens Generator.zip | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
76
Suspicious files
163
Text files
1 089
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3260.15810\Discord Tokens Generator.exe | executable | |
MD5:— | SHA256:— | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_des3.cp38-win32.pyd | executable | |
MD5:9E782D4950C2BB6D3C187EC17C3B9E4C | SHA256:58085B581F2BE8761ABF22163B0F06C06AD285F6F8C383C1BB980F61C13DD37B | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_chacha20.cp38-win32.pyd | executable | |
MD5:100BE873039DF2C8A2DA4F9554BAEEA3 | SHA256:4861F5CA729112D56C4CD6B3301AACB2803DAF6371BD3992D4339E4BAE968AF5 | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_arc2.cp38-win32.pyd | executable | |
MD5:81F04220BF3B7B779BFAD8C0FE2C38DE | SHA256:6980DA95392C9B334B41757C0D19A95B8CABFA2608E64ADBA0838A852A2CB5D6 | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_cbc.cp38-win32.pyd | executable | |
MD5:C9CD927AB77F219B74C29C9CED9D4A87 | SHA256:CB0667A3366AB483055376A94BCC551545333DEF8461DB49EB18559AD4473855 | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_Salsa20.cp38-win32.pyd | executable | |
MD5:D60C062852DDF6117AB9764DEC4BC50D | SHA256:9A77AB2C8BFEE75F572B22BFF1ACE6A0E96D6C2969F38164B541B4266A35773B | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_blowfish.cp38-win32.pyd | executable | |
MD5:9B219BBC67D899C608718FB267B9E786 | SHA256:90E8448B0BAD3AC2AF599488D9BA4E43C93FF83193B3E8F37D43C8F2D13A63EE | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_aes.cp38-win32.pyd | executable | |
MD5:662BF265439BB6C3A009EE41DBC4F6E4 | SHA256:E73E54B991A1D5BDDD2E8497AEA1598D2A14602D3A12108F84FB685C34EFC239 | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_cfb.cp38-win32.pyd | executable | |
MD5:D26D006C35E1F37C8ACA392787521B4F | SHA256:E6B6959B7104B86D80C47E0D538077D8705043431EC4DAE61471543533E16FA4 | |||
| 3620 | Discord Tokens Generator.exe | C:\Users\admin\AppData\Local\Temp\_MEI36202\Crypto\Cipher\_raw_ecb.cp38-win32.pyd | executable | |
MD5:7D3A38202EB74897B45517BDAF7F5DF8 | SHA256:45D7AEF129DB43A587B864F9C9304969B4089579CE91AD4BB762820196418613 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
70
DNS requests
44
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3596 | chrome.exe | 172.217.17.36:443 | www.google.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 216.58.214.13:443 | accounts.google.com | Google Inc. | US | suspicious |
3596 | chrome.exe | 172.217.17.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 216.58.214.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 216.58.208.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 216.58.211.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 216.58.208.110:443 | ogs.google.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 172.217.168.238:443 | apis.google.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 216.58.214.14:443 | consent.google.com | Google Inc. | US | whitelisted |
3596 | chrome.exe | 172.217.17.34:443 | adservice.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discord.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
consent.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3596 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
3596 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
1 ETPRO signatures available at the full report