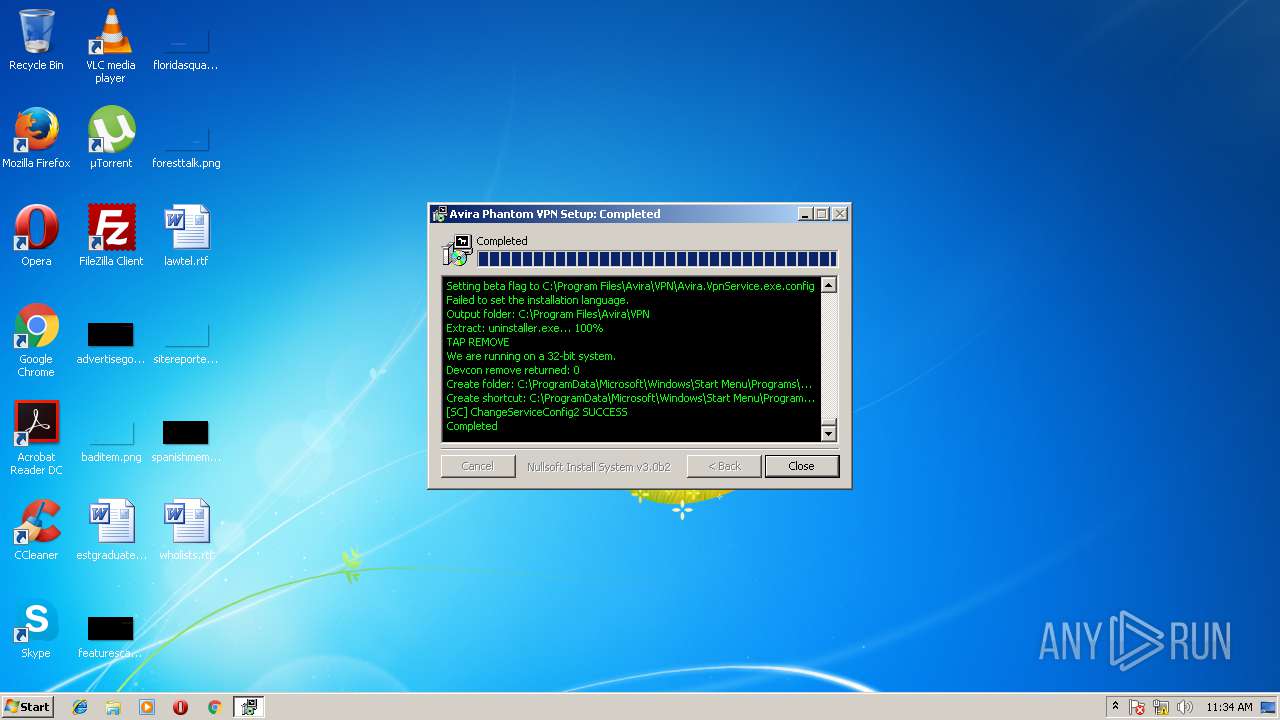
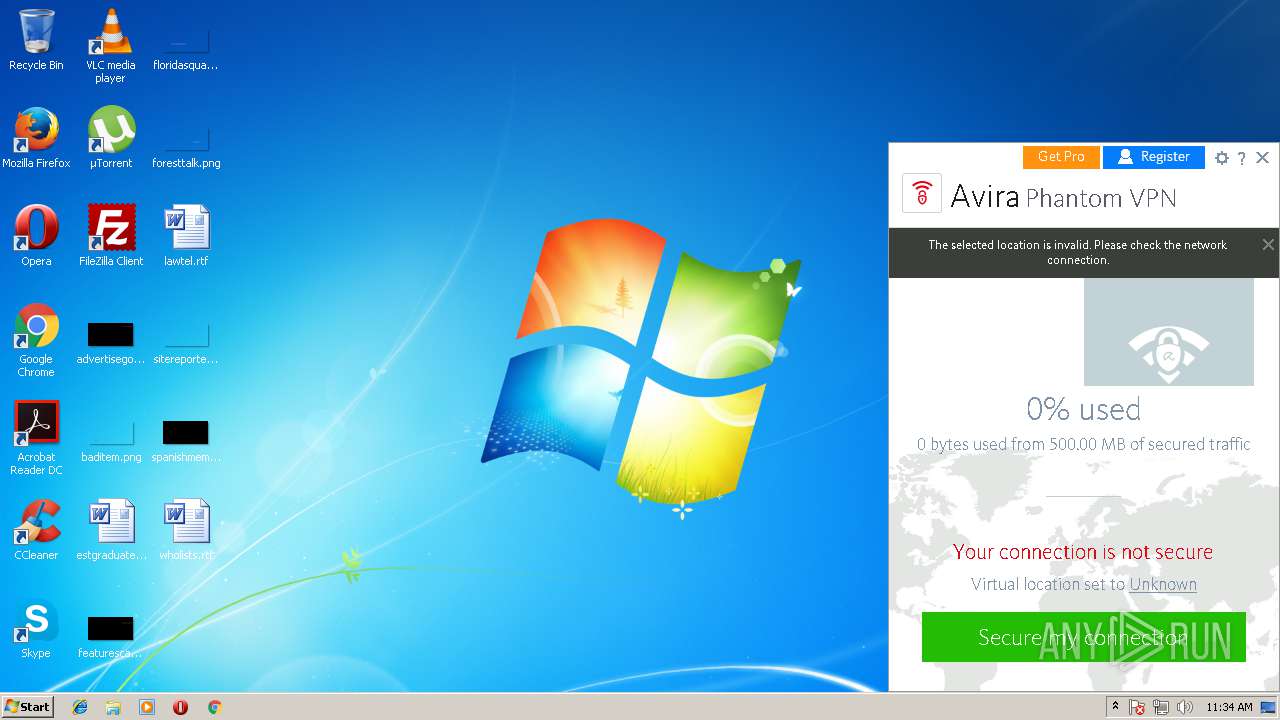
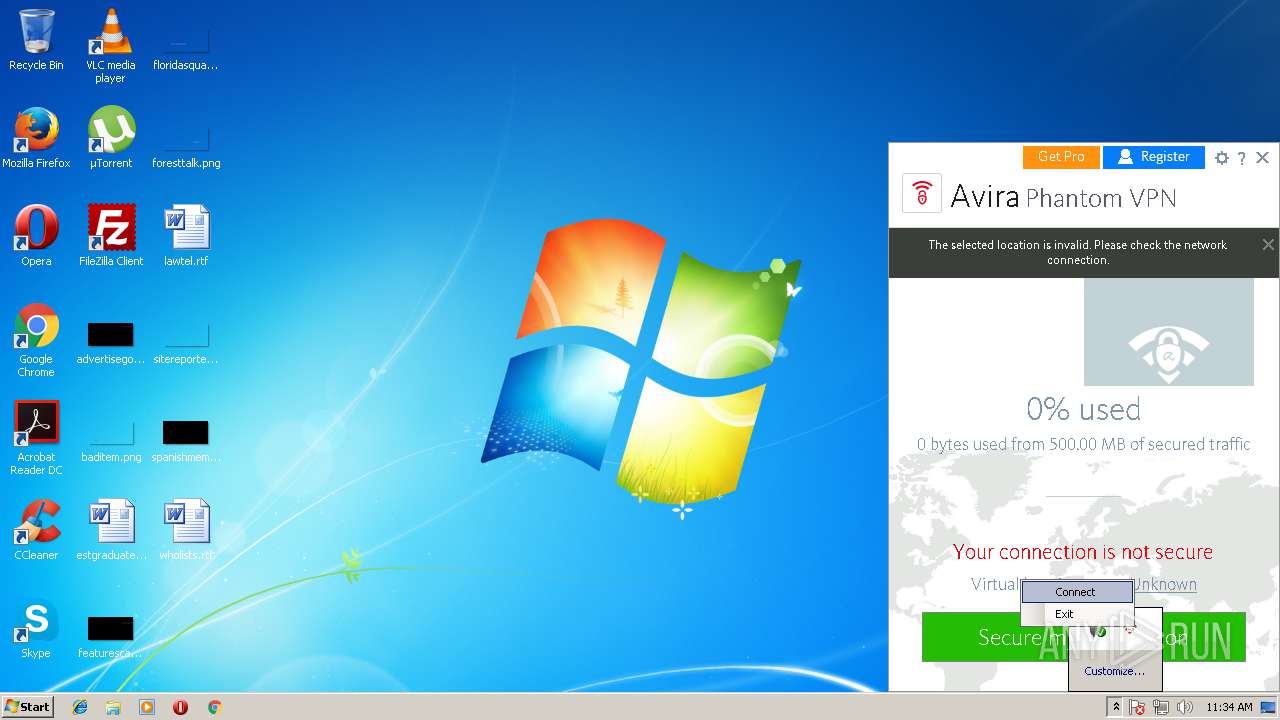
| download: | vpninstaller.exe |
| Full analysis: | https://app.any.run/tasks/99b3b9a2-2a6d-4903-848c-35612964694c |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2018, 11:33:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C778A321EC4FCB6951A831CE9FE288D9 |
| SHA1: | D36BA1495105C79699765DC2D75A3E79ED5B43E0 |
| SHA256: | 95DBD4CAD67E4E08BC8D21FE0E59F378663E7E0B5706469B1F9B344D58F931BC |
| SSDEEP: | 98304:7RT5m0WKwgB9tVUIDB9lpUjtIRFnkKKzPYb6mPc22C071ORmkWEAyM:dT5mPKwy9tVUIDB9lpUj8kTged22Cy1H |
MALICIOUS
Application loaded dropped or rewritten executable
- vpninstaller.exe (PID: 3860)
- Avira.WebAppHost.exe (PID: 1460)
- Avira.VpnService.exe (PID: 3560)
- Avira.WebAppHost.exe (PID: 2704)
Application was dropped or rewritten from another process
- tapinstall.exe (PID: 2380)
- Avira.VpnService.exe (PID: 3560)
- nsDBB8.tmp (PID: 3888)
- nsDE68.tmp (PID: 2580)
- nsD6D5.tmp (PID: 4004)
- Avira.WebAppHost.exe (PID: 1460)
- Avira.NetworkBlocker.exe (PID: 2800)
- Avira.WebAppHost.exe (PID: 2704)
Changes settings of System certificates
- Avira.VpnService.exe (PID: 3560)
SUSPICIOUS
Starts application with an unusual extension
- vpninstaller.exe (PID: 3860)
Creates a software uninstall entry
- vpninstaller.exe (PID: 3860)
Creates files in the Windows directory
- tapinstall.exe (PID: 2380)
- Avira.VpnService.exe (PID: 3560)
Starts SC.EXE for service management
- nsDE68.tmp (PID: 2580)
Creates files in the program directory
- Avira.VpnService.exe (PID: 3560)
- vpninstaller.exe (PID: 3860)
Creates or modifies windows services
- vpninstaller.exe (PID: 3860)
- Avira.VpnService.exe (PID: 3560)
Adds / modifies Windows certificates
- Avira.VpnService.exe (PID: 3560)
Reads internet explorer settings
- Avira.WebAppHost.exe (PID: 2704)
Reads Internet Cache Settings
- Avira.WebAppHost.exe (PID: 2704)
Removes files from Windows directory
- Avira.VpnService.exe (PID: 3560)
INFO
Loads rich edit control libraries
- vpninstaller.exe (PID: 3860)
Loads the .NET runtime environment
- Avira.WebAppHost.exe (PID: 1460)
- Avira.VpnService.exe (PID: 3560)
- Avira.WebAppHost.exe (PID: 2704)
Reads settings of System Certificates
- Avira.VpnService.exe (PID: 3560)
- Avira.WebAppHost.exe (PID: 2704)
Dropped object may contain URL's
- Avira.VpnService.exe (PID: 3560)
- vpninstaller.exe (PID: 3860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:08:05 02:46:21+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 117760 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30b6 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.12.7.22015 |
| ProductVersionNumber: | 2.12.7.22015 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Avira Operations GmbH & Co. KG |
| FileDescription: | Avira Phantom VPN Installer |
| FileVersion: | 2.12.7.22015 |
| LegalCopyright: | Copyright � Avira Operations GmbH & Co. KG |
| ProductName: | Avira Phantom VPN |
| ProductVersion: | 2.12.7.22015 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Aug-2015 00:46:21 |
| Detected languages: |
|
| CompanyName: | Avira Operations GmbH & Co. KG |
| FileDescription: | Avira Phantom VPN Installer |
| FileVersion: | 2.12.7.22015 |
| LegalCopyright: | Copyright � Avira Operations GmbH & Co. KG |
| ProductName: | Avira Phantom VPN |
| ProductVersion: | 2.12.7.22015 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000C8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Aug-2015 00:46:21 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005AC0 | 0x00005C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.43402 |
.rdata | 0x00007000 | 0x000011CE | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.23558 |
.data | 0x00009000 | 0x0001A7D8 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.96129 |
.ndata | 0x00024000 | 0x0000E000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00032000 | 0x00000D88 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.39431 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28836 | 842 | UNKNOWN | English - United States | RT_MANIFEST |
103 | 2.16096 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
49
Monitored processes
11
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1460 | "C:\Program Files\Avira\VPN\Avira.WebAppHost.exe" /migrateSettings | C:\Program Files\Avira\VPN\Avira.WebAppHost.exe | — | explorer.exe | |||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: MEDIUM Description: WebAppHost Exit code: 0 Version: 2.12.7.22012 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\Avira\VPN\OpenVpn\TAP\win7\i386\tapinstall.exe" tap_remove "phantomtap" | C:\Program Files\Avira\VPN\OpenVpn\TAP\win7\i386\tapinstall.exe | — | nsDBB8.tmp | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 10.0.10011.16384 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\nsDE68.tmp" "sc.exe" failure AviraPhantomVPN reset= 86400 actions= restart/1000 | C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\nsDE68.tmp | — | vpninstaller.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Avira\VPN\Avira.WebAppHost.exe" | C:\Program Files\Avira\VPN\Avira.WebAppHost.exe | — | explorer.exe | |||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: MEDIUM Description: WebAppHost Exit code: 0 Version: 2.12.7.22012 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Avira\VPN\Avira.NetworkBlocker.exe" delete | C:\Program Files\Avira\VPN\Avira.NetworkBlocker.exe | — | Avira.VpnService.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 2992 | "C:\Users\admin\AppData\Local\Temp\vpninstaller.exe" | C:\Users\admin\AppData\Local\Temp\vpninstaller.exe | — | explorer.exe | |||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: MEDIUM Description: Avira Phantom VPN Installer Exit code: 3221226540 Version: 2.12.7.22015 | |||||||||||||||
| 3128 | "sc.exe" failure AviraPhantomVPN reset= 86400 actions= restart/1000 | C:\Windows\system32\sc.exe | — | nsDE68.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3560 | "C:\Program Files\Avira\VPN\Avira.VpnService.exe" | C:\Program Files\Avira\VPN\Avira.VpnService.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Avira Operations GmbH & Co. KG Integrity Level: SYSTEM Description: VpnService Exit code: 0 Version: 2.12.7.22015 Modules
| |||||||||||||||
| 3860 | "C:\Users\admin\AppData\Local\Temp\vpninstaller.exe" | C:\Users\admin\AppData\Local\Temp\vpninstaller.exe | explorer.exe | ||||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: HIGH Description: Avira Phantom VPN Installer Exit code: 0 Version: 2.12.7.22015 Modules
| |||||||||||||||
| 3888 | "C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\nsDBB8.tmp" "C:\Program Files\Avira\VPN\OpenVpn\TAP\win7\i386\tapinstall.exe" tap_remove "phantomtap" | C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\nsDBB8.tmp | — | vpninstaller.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
618
Read events
510
Write events
108
Delete events
0
Modification events
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3860) vpninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\vpninstaller_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
54
Suspicious files
11
Text files
404
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3860 | vpninstaller.exe | C:\Users\admin\AppData\Local\Temp\nssCBB8.tmp | — | |
MD5:— | SHA256:— | |||
| 3860 | vpninstaller.exe | C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\nsD6D5.tmp | — | |
MD5:— | SHA256:— | |||
| 3860 | vpninstaller.exe | C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\base64.dll | executable | |
MD5:AC6FB776262B63562C00374392FE1C55 | SHA256:7E10EF2723A50B7346449F8BB39EFAB8A99E2815D33D311ECB8112734F91519D | |||
| 3860 | vpninstaller.exe | C:\Program Files\Avira\VPN\OpenVpn\TAP\win10\i386\phantomtap.cat | cat | |
MD5:83DC8E4776D663F3AA87FF0D6A568C85 | SHA256:E3FE7BCF382741C2253B53B7A94DD2722313031555D3F76C65A40FF94ECB5CFE | |||
| 3860 | vpninstaller.exe | C:\Program Files\Avira\VPN\OpenVpn\TAP\win10\amd64\tapinstall.exe | executable | |
MD5:2B1BDDF7F9D3190FF73563A41BCB72BE | SHA256:85AB4BBB77AB248956D0DA02ACE1A2BC58CE6C6DB9F421808EF03ED31BBCF3B6 | |||
| 3860 | vpninstaller.exe | C:\Program Files\Avira\VPN\OpenVpn\TAP\win10\i386\phantomtap.sys | executable | |
MD5:91DCD6105321E2DE3645A3AAFC6793A6 | SHA256:D38F4DA7B3FBD8255A3435D90743D15803FB84FA2C98E5A8A112480888826D23 | |||
| 3860 | vpninstaller.exe | C:\Program Files\Avira\VPN\OpenVpn\TAP\win10\i386\OemVista.inf | binary | |
MD5:97540D25234B5C838DBC8B976C8C111C | SHA256:8CE162F8D9B81CEC5EFF6FBD5C2C4150006D000A6454B3CFEF8FB664D913259F | |||
| 3860 | vpninstaller.exe | C:\Program Files\Avira\VPN\OpenVpn\VpnClient.ovpn | text | |
MD5:3900C295E5EC15986F71E78A3FC08DFE | SHA256:CB0230CF34398BF8008367DEDF0158796415C1247E6C18D2A3065F737E36B168 | |||
| 3860 | vpninstaller.exe | C:\Users\admin\AppData\Local\Temp\nscCBA7.tmp\System.dll | executable | |
MD5:6F5257C0B8C0EF4D440F4F4FCE85FB1B | SHA256:B7CCB923387CC346731471B20FC3DF1EAD13EC8C2E3147353C71BB0BD59BC8B1 | |||
| 3860 | vpninstaller.exe | C:\Program Files\Avira\VPN\OpenVpn\phantomvpn.exe | executable | |
MD5:8FB5F92B47009175E7EDE351C042EA6A | SHA256:3F952BD3E2536B53378BA5E99DC074A906D6B6E48DD4E79985A27F0DB7F7F28E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
12
DNS requests
56
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 68.232.34.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 52.7 Kb | whitelisted |
— | — | GET | 200 | 68.232.34.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 52.7 Kb | whitelisted |
— | — | GET | 200 | 2.21.246.24:80 | http://www.msftncsi.com/ncsi.txt | AT | text | 14 b | whitelisted |
— | — | GET | 200 | 2.21.246.24:80 | http://www.msftncsi.com/ncsi.txt | AT | text | 14 b | whitelisted |
— | — | GET | 200 | 159.122.19.201:80 | http://api.mixpanel.com/track/?data=eyAiZXZlbnQiOiAiVnBuIEluc3RhbGwgU3RhcnQiLCAicHJvcGVydGllcyI6IHsgImRpc3RpbmN0X2lkIjogIiIsICJWUE4gVmVyc2lvbiI6ICIyLjEyLjcuMjIwMTUiLCAidG9rZW4iOiAiMWUyNzNjMjY0YjA2NmE5ODQ4YWQyOGY0YjQ0ZTNkMjYiLCAidGltZSI6ICIxNTIxODA0ODIwIiB9IH0= | US | binary | 1 b | whitelisted |
— | — | GET | 200 | 2.21.246.24:80 | http://www.msftncsi.com/ncsi.txt | AT | text | 14 b | whitelisted |
— | — | GET | 200 | 2.21.246.24:80 | http://www.msftncsi.com/ncsi.txt | AT | text | 14 b | whitelisted |
— | — | GET | 200 | 159.122.19.201:80 | http://api.mixpanel.com/track/?data=eyAiZXZlbnQiOiAiVnBuIEluc3RhbGwgU3VjY2VzcyIsICJwcm9wZXJ0aWVzIjogeyAiZGlzdGluY3RfaWQiOiAiZTcxZGRmNjA1MjgzNDRmMzk1NjdlYjhhNmQ1NjQzMjNkMDhjNTM4NSIsICJWUE4gVmVyc2lvbiI6ICIyLjEyLjcuMjIwMTUiLCAidG9rZW4iOiAiMWUyNzNjMjY0YjA2NmE5ODQ4YWQyOGY0YjQ0ZTNkMjYiLCAidGltZSI6ICIxNTIxODA0ODQyIiB9IH0=! | US | binary | 1 b | whitelisted |
— | — | GET | 200 | 2.21.246.24:80 | http://www.msftncsi.com/ncsi.txt | AT | text | 14 b | whitelisted |
— | — | GET | 200 | 2.21.246.24:80 | http://www.msftncsi.com/ncsi.txt | AT | text | 14 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 159.122.19.201:80 | api.mixpanel.com | SoftLayer Technologies Inc. | US | unknown |
— | — | 52.29.12.96:443 | api.phantom.avira-vpn.com | Amazon.com, Inc. | DE | unknown |
— | — | 159.122.19.201:443 | api.mixpanel.com | SoftLayer Technologies Inc. | US | unknown |
— | — | 68.232.34.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 35.157.220.176:443 | sentry.avira.com | Amazon.com, Inc. | DE | unknown |
— | — | 2.21.246.24:80 | www.msftncsi.com | Akamai International B.V. | AT | whitelisted |
— | — | 35.156.230.251:443 | api.my.avira.com | Amazon.com, Inc. | DE | unknown |
— | — | 52.29.117.211:443 | dispatch.avira-update.com | Amazon.com, Inc. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.mixpanel.com |
| whitelisted |
api.phantom.avira-vpn.com |
| unknown |
www.download.windowsupdate.com |
| whitelisted |
api.my.avira.com |
| unknown |
dns.msftncsi.com |
| shared |
www.msftncsi.com |
| whitelisted |
no.phantom.avira-vpn.com |
| unknown |
bg.phantom.avira-vpn.com |
| unknown |
br1.phantom.avira-vpn.com |
| unknown |
be.phantom.avira-vpn.com |
| unknown |