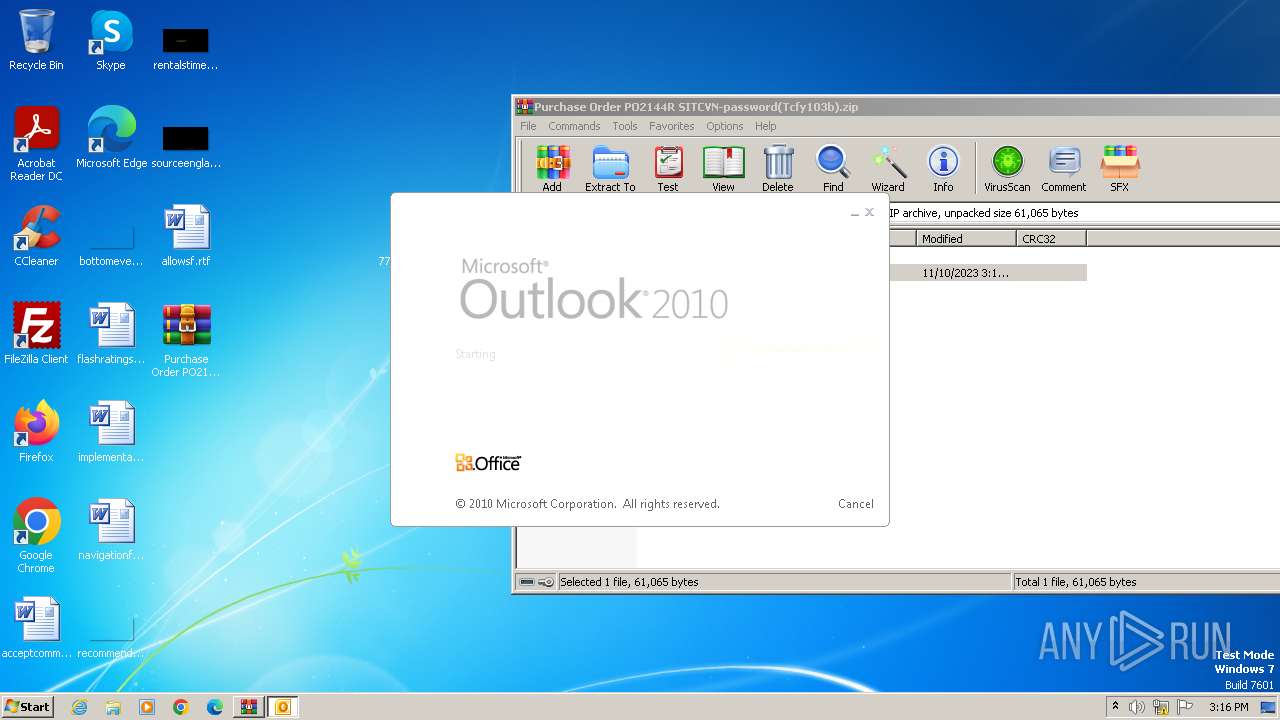
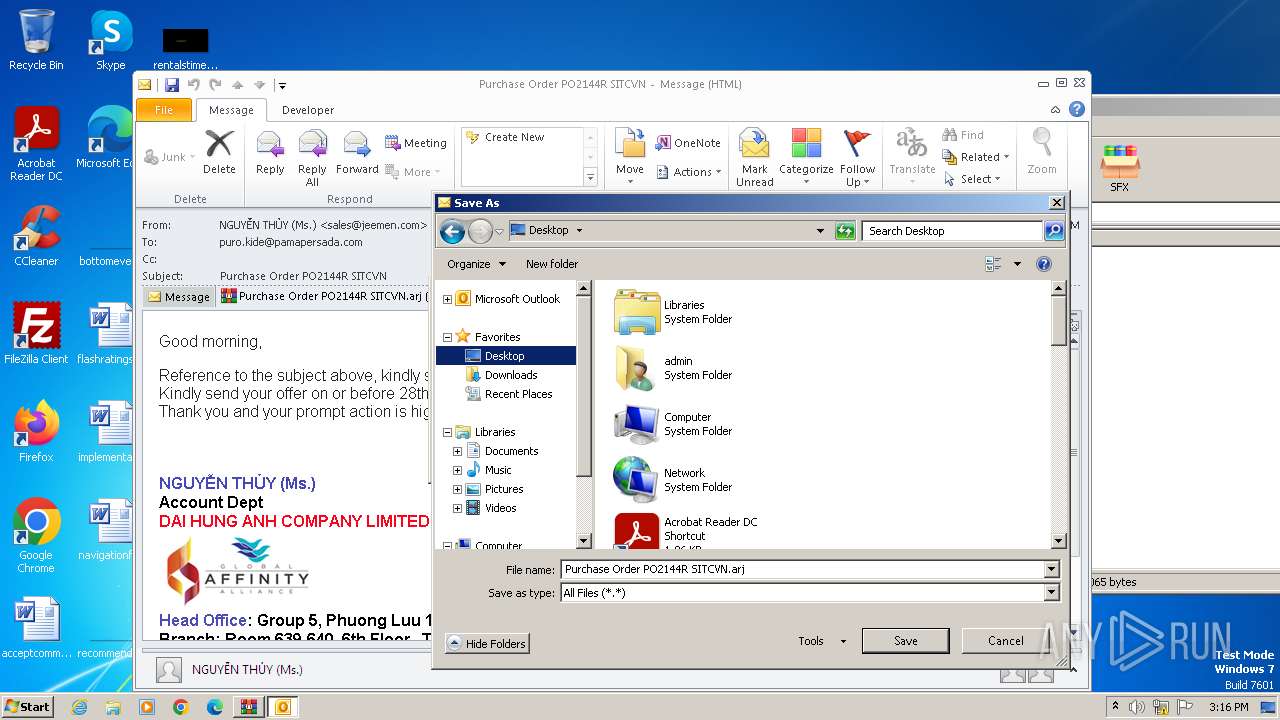
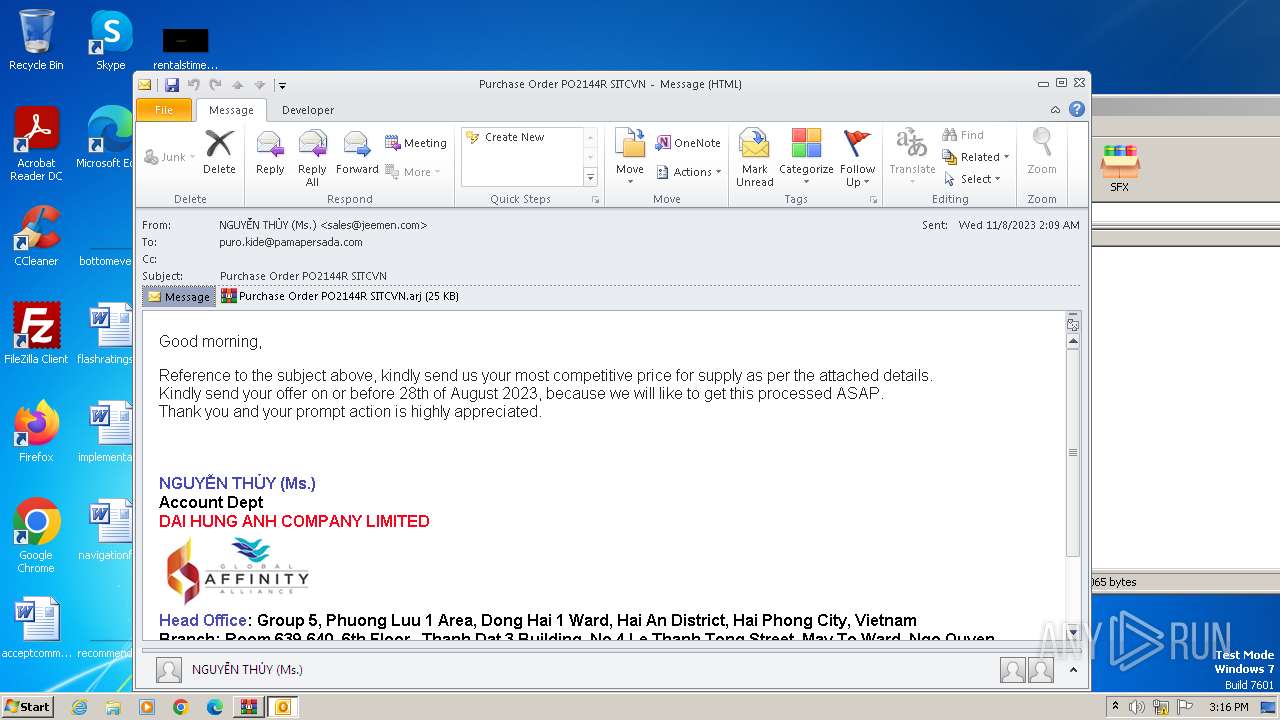
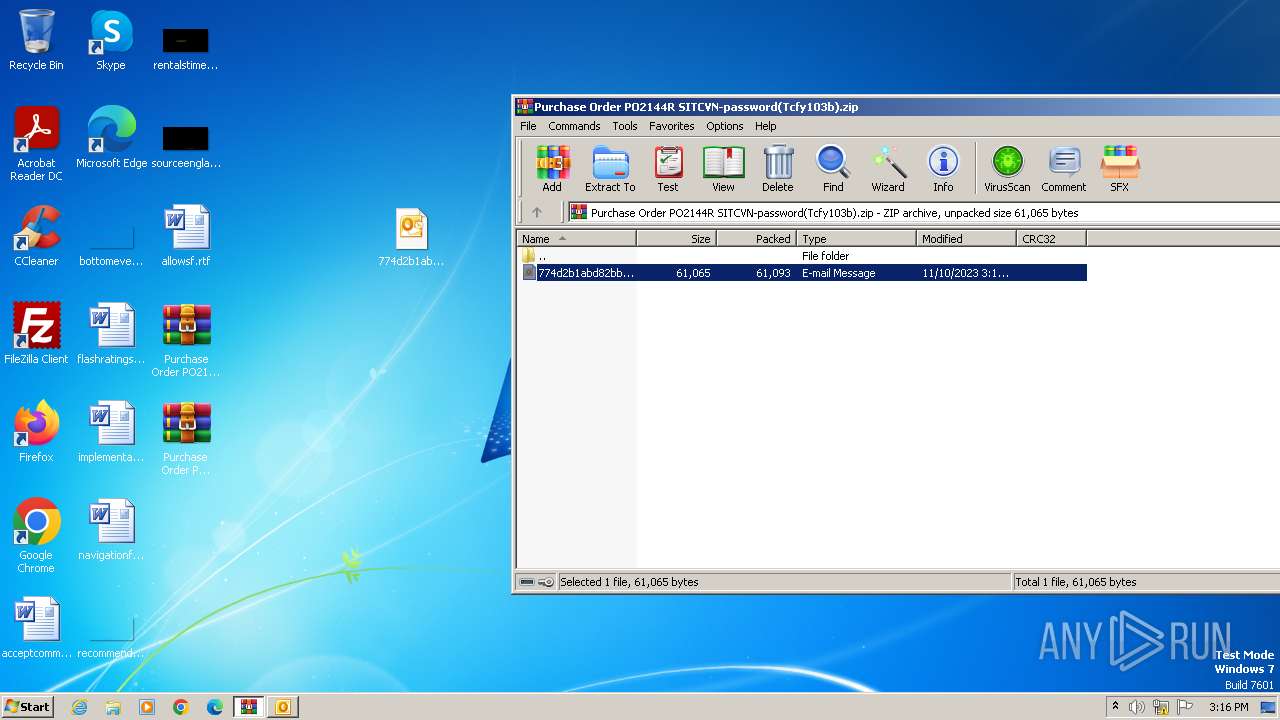
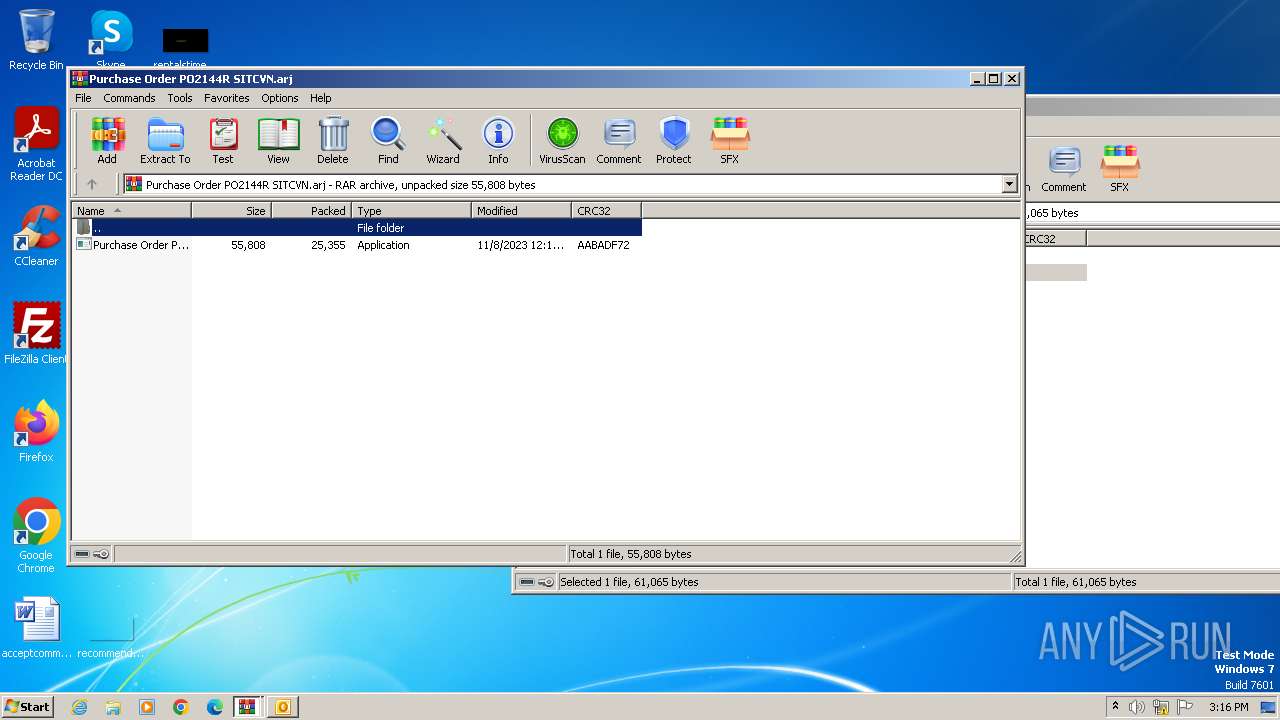
| File name: | Purchase Order PO2144R SITCVN-password(Tcfy103b).zip |
| Full analysis: | https://app.any.run/tasks/e75b1b9f-8d14-45ad-9c21-6379c5415c34 |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2023, 15:16:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 279A45666C837019F46F8CAA4FC81B5C |
| SHA1: | 865595D5F824490A2C62DF77138F97B6953F7577 |
| SHA256: | 95D1B2080B672C34B4362FE876706EEB3E25E129CDD6AB2B57788A7DE0045DE6 |
| SSDEEP: | 1536:7Fc2BDa/rAL+Zg7qyQuCLF4MU4F5oDNGKn2m:7ZDUpZeNQNF4MU4FODNGKnz |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
Reads settings of System Certificates
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
INFO
Manual execution by a user
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
- WinRAR.exe (PID: 4088)
- OUTLOOK.EXE (PID: 3480)
- wmpnscfg.exe (PID: 2376)
- Purchase Order PO2144R SITCVN.exe (PID: 664)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3480)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4088)
Checks supported languages
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
- wmpnscfg.exe (PID: 2376)
- Purchase Order PO2144R SITCVN.exe (PID: 664)
Reads the computer name
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
- wmpnscfg.exe (PID: 2376)
- Purchase Order PO2144R SITCVN.exe (PID: 664)
Reads the machine GUID from the registry
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
- wmpnscfg.exe (PID: 2376)
Reads Environment values
- Purchase Order PO2144R SITCVN.exe (PID: 3704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2023:11:10 15:13:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 61093 |
| ZipUncompressedSize: | 61065 |
| ZipFileName: | 774d2b1abd82bbdbb9cdd495272721511d350df4983dd09b75955359d8352e9e.eml |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN.exe" | C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3428 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN-password(Tcfy103b).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
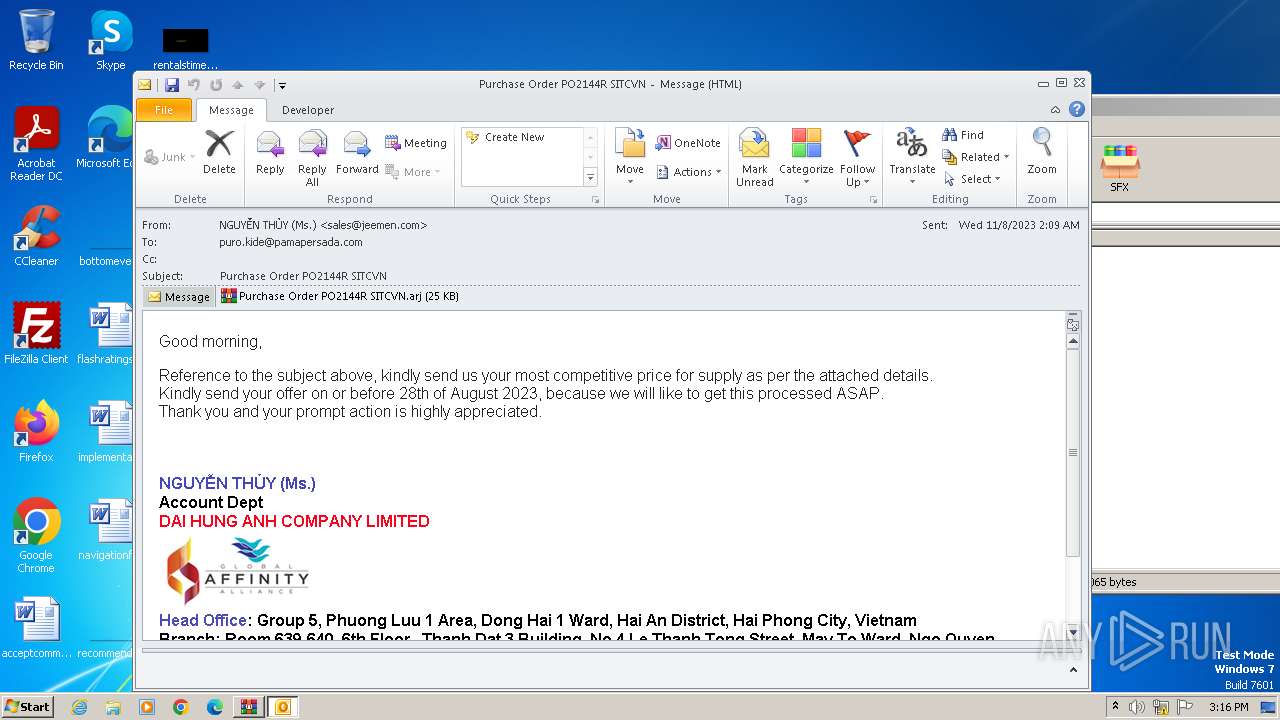
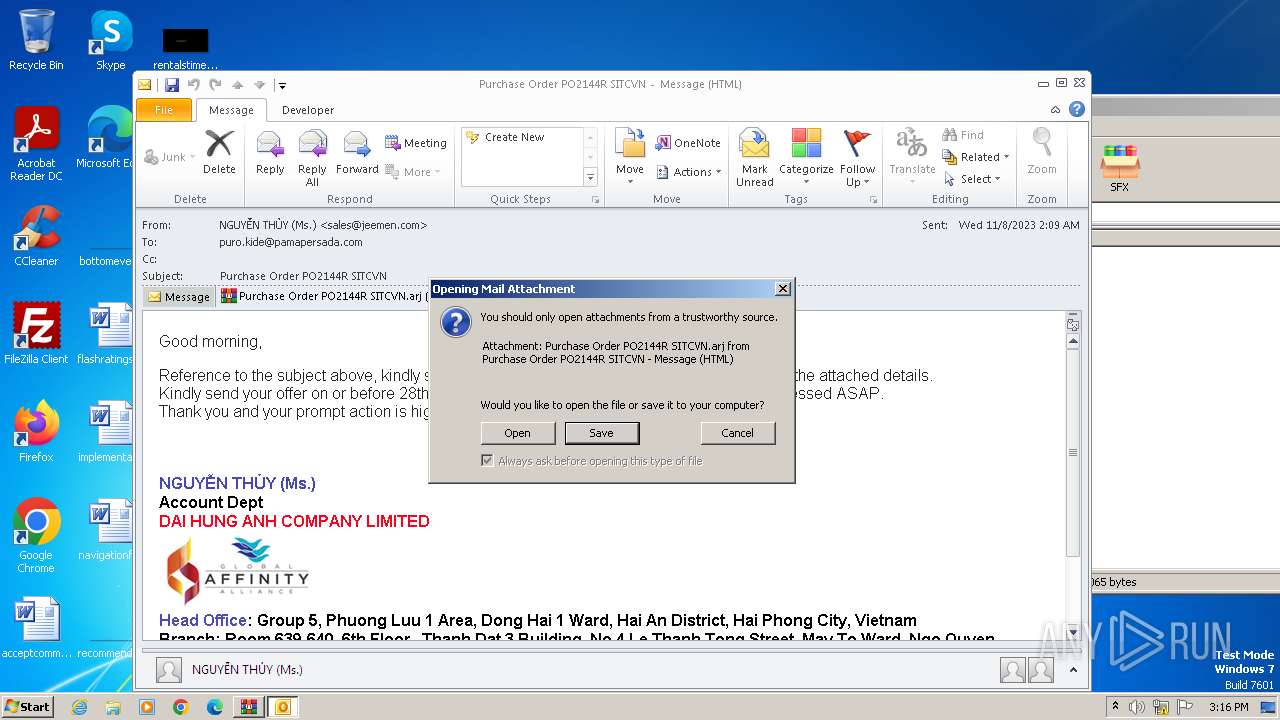
| 3480 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\774d2b1abd82bbdbb9cdd495272721511d350df4983dd09b75955359d8352e9e.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3704 | "C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN.exe" | C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN.arj" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 979
Read events
9 522
Write events
432
Delete events
25
Modification events
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3480) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
Executable files
1
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA879.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3428.35697\774d2b1abd82bbdbb9cdd495272721511d350df4983dd09b75955359d8352e9e.eml | html | |
MD5:F55B74828A35D8379C05FAF4EB9BA4B6 | SHA256:A71A61B9F476A10C3182302D821B1B2283B4F2C7260F1D26986036A8DDD7DD41 | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\CA1CXOJG\Purchase Order PO2144R SITCVN.arj:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{79759341-3BF1-4538-86CE-CEAC59C02189}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:909F9AE44B7929D297F7CDE9F3D96B41 | SHA256:E0B5116F49778DE291A7AC1B9C0C43CA7EFFAC4E831A35C76402A0545C6F22D3 | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\Desktop\Purchase Order PO2144R SITCVN.arj | compressed | |
MD5:8143F3B91A6BC3481264ED49625D207F | SHA256:4BAED2A5FDAE1CD2B59575336B1749C39EC898541A0457EB145F2EFDAFFE0D27 | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\617BE860.dat | image | |
MD5:3768F6AA2CDB06EBBD337C205E534402 | SHA256:BB28DD1CEF0CB97524826F64449895BF21A1C92C484F42FEDC7A93FD9A48CECB | |||
| 3480 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\CA1CXOJG\Purchase Order PO2144R SITCVN.arj | compressed | |
MD5:8143F3B91A6BC3481264ED49625D207F | SHA256:4BAED2A5FDAE1CD2B59575336B1749C39EC898541A0457EB145F2EFDAFFE0D27 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
15
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3480 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3704 | Purchase Order PO2144R SITCVN.exe | 13.107.42.13:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3704 | Purchase Order PO2144R SITCVN.exe | 13.107.43.12:443 | h5t2yg.dm.files.1drv.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
onedrive.live.com |
| shared |
h5t2yg.dm.files.1drv.com |
| unknown |