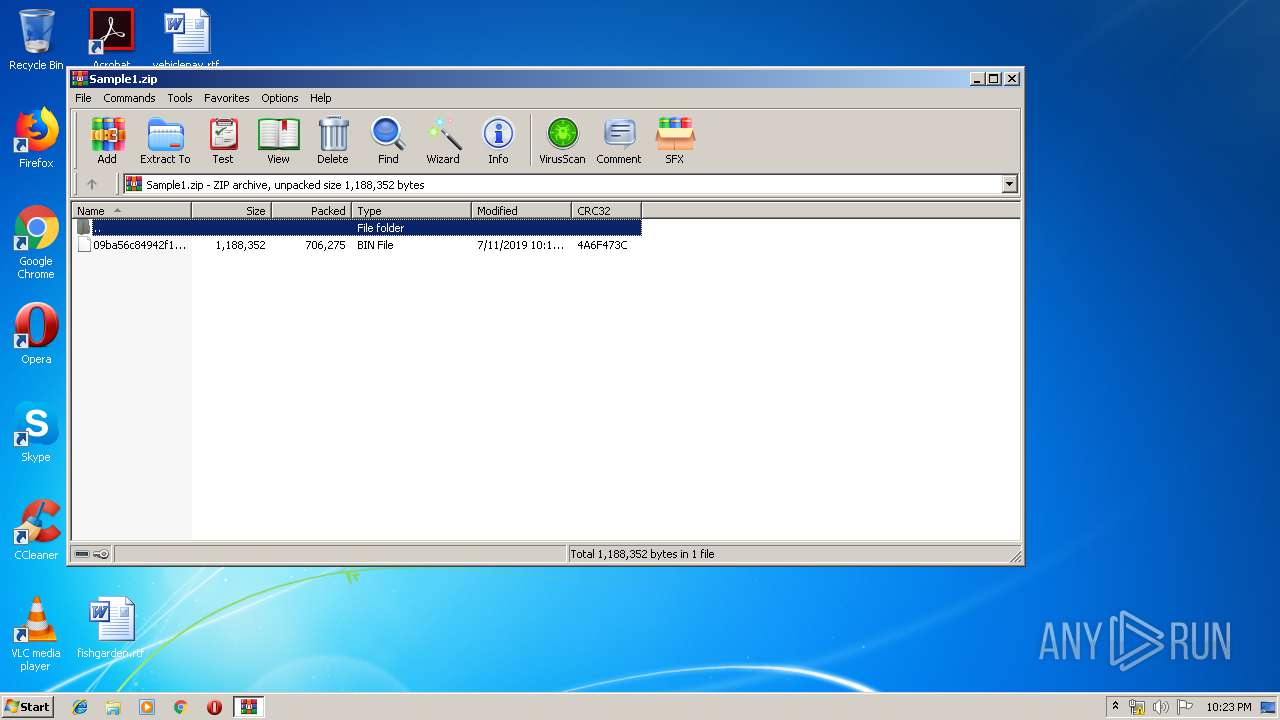
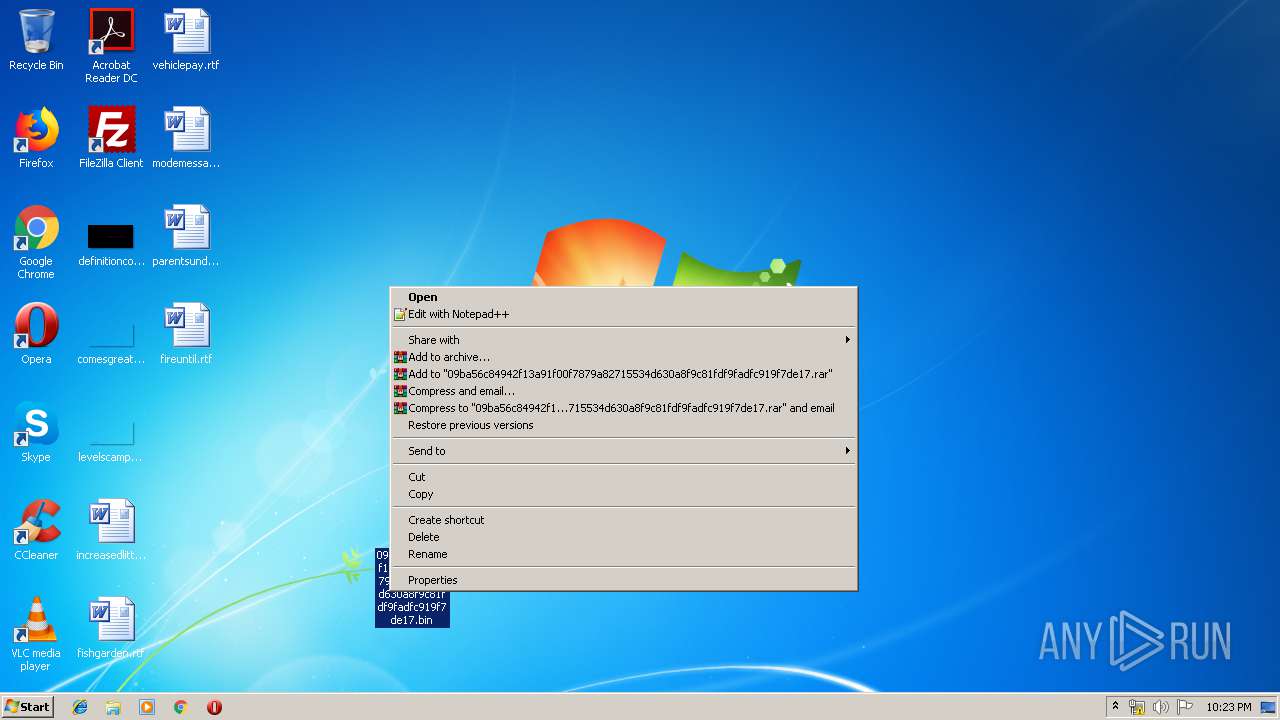
| File name: | Sample1.zip |
| Full analysis: | https://app.any.run/tasks/c7fa93e0-cfdd-4b32-809e-d586c3f5e0c6 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 21:21:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A0BF7FDF56CC2A84A2F555A7B6832B79 |
| SHA1: | 8F089EE6E280ED185C2B8B5F17DA5FADB6625CC0 |
| SHA256: | 95CA5DEC3E1C00EF77A58DC279897CB784936F6080ED4A1F204CE37AFBB713FF |
| SSDEEP: | 12288:B5uFwmTUPkuzxEHHwRGIbRFnzU1JJjnzdbTLWH9Dvaqr0lPvr7PLRU:aFjMtEiJbvU1JlnzdqHtvQlPvPFU |
MALICIOUS
Application was dropped or rewritten from another process
- ayy.exe (PID: 2780)
- ayy.exe (PID: 3656)
SUSPICIOUS
Creates files in the user directory
- ayy.exe (PID: 3656)
Application launched itself
- ayy.exe (PID: 2780)
INFO
Manual execution by user
- opera.exe (PID: 2888)
- ayy.exe (PID: 2780)
Creates files in the user directory
- opera.exe (PID: 2888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:11 21:15:11 |
| ZipCRC: | 0x4a6f473c |
| ZipCompressedSize: | 706275 |
| ZipUncompressedSize: | 1188352 |
| ZipFileName: | 09ba56c84942f13a91f00f7879a82715534d630a8f9c81fdf9fadfc919f7de17.bin |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2780 | "C:\Users\admin\Desktop\ayy.exe" | C:\Users\admin\Desktop\ayy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2888 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 3100 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Sample1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3656 | "C:\Users\admin\Desktop\ayy.exe" | C:\Users\admin\Desktop\ayy.exe | ayy.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
742
Read events
582
Write events
160
Delete events
0
Modification events
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Sample1.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2888) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
| (PID) Process: | (2888) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
36
Text files
23
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr3A3C.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr3A7B.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\TAMJ2TLEW1WT5CP0RBT7.temp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprC7A9.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprD3CF.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr1CA1.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr2879.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr44AD.tmp | — | |
MD5:— | SHA256:— | |||
| 2888 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr5085.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
24
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2888 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
2888 | opera.exe | GET | 200 | 185.26.182.109:80 | http://redir.opera.com/favicons/google/favicon.ico | unknown | image | 5.30 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2888 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2888 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
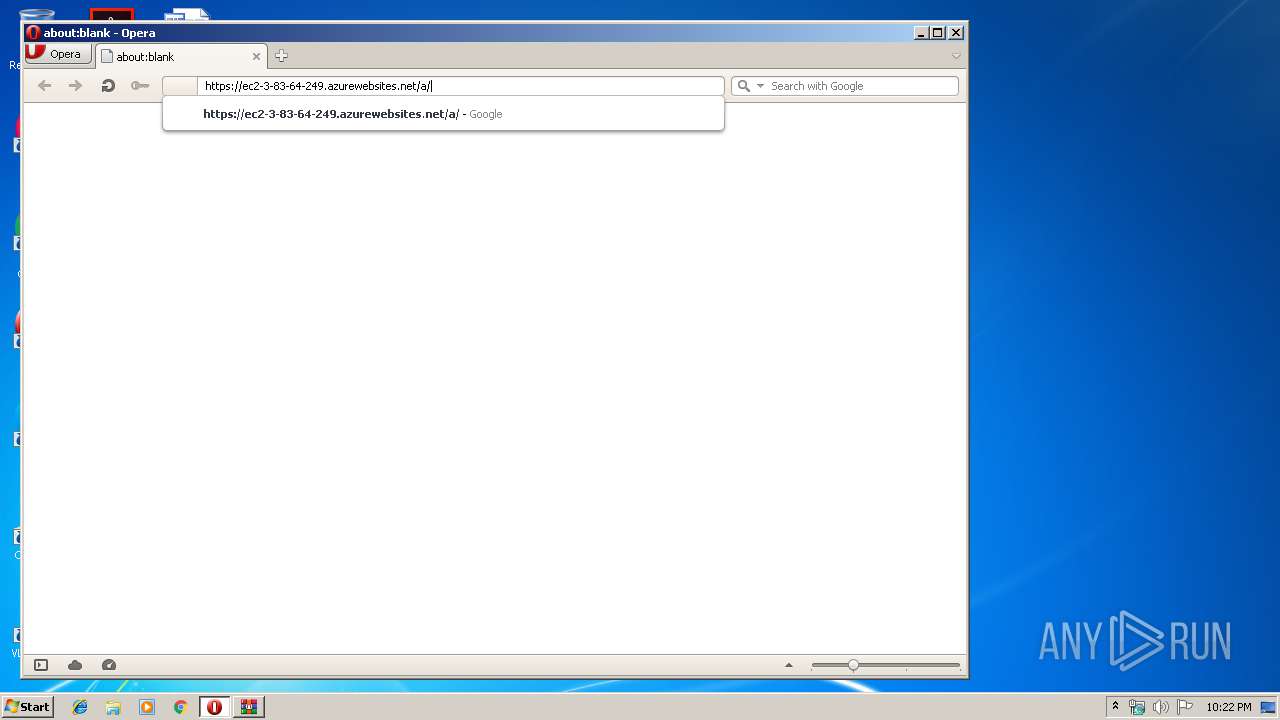
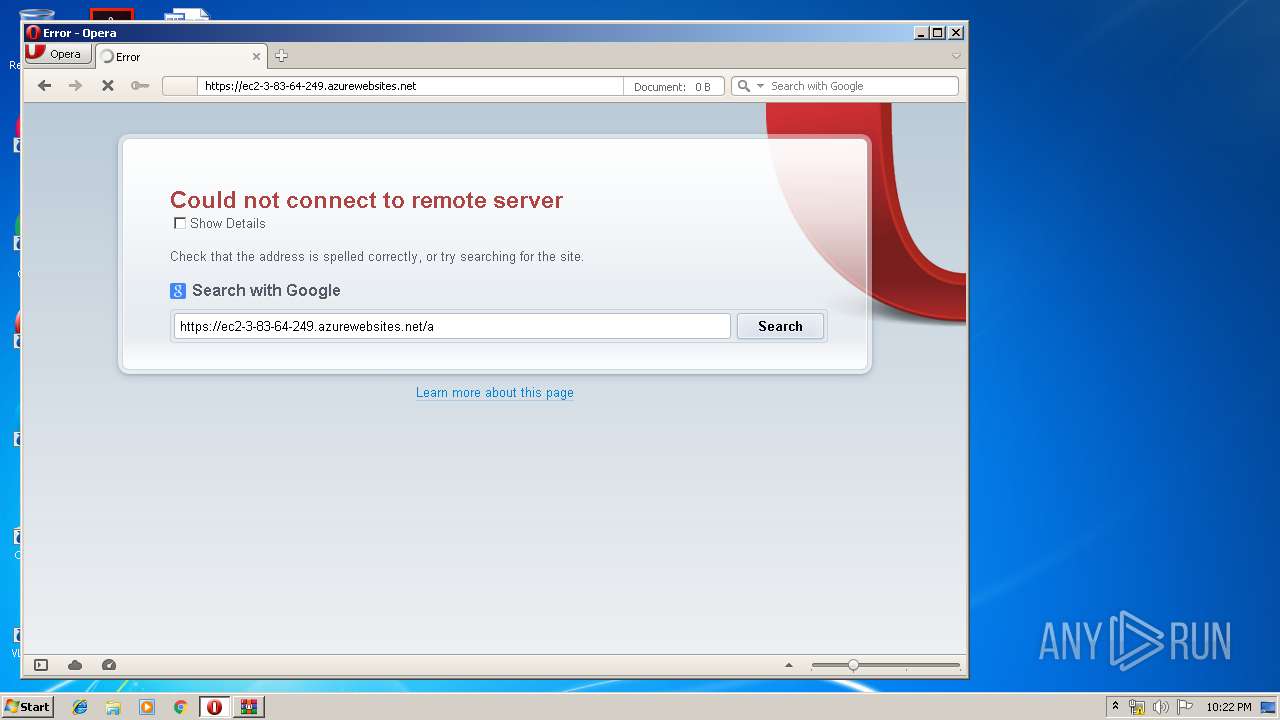
2888 | opera.exe | 52.237.22.139:443 | ec2-3-83-64-249.azurewebsites.net | Microsoft Corporation | CA | unknown |
2888 | opera.exe | 185.26.182.112:443 | sitecheck2.opera.com | Opera Software AS | — | malicious |
— | — | 52.237.22.139:443 | ec2-3-83-64-249.azurewebsites.net | Microsoft Corporation | CA | unknown |
2888 | opera.exe | 185.26.182.109:80 | redir.opera.com | Opera Software AS | — | unknown |
3656 | ayy.exe | 194.5.179.42:443 | k.icf-fx.kz | — | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
ec2-3-83-64-249.azurewebsites.net |
| unknown |
sitecheck2.opera.com |
| whitelisted |
redir.opera.com |
| whitelisted |
k.icf-fx.kz |
| unknown |