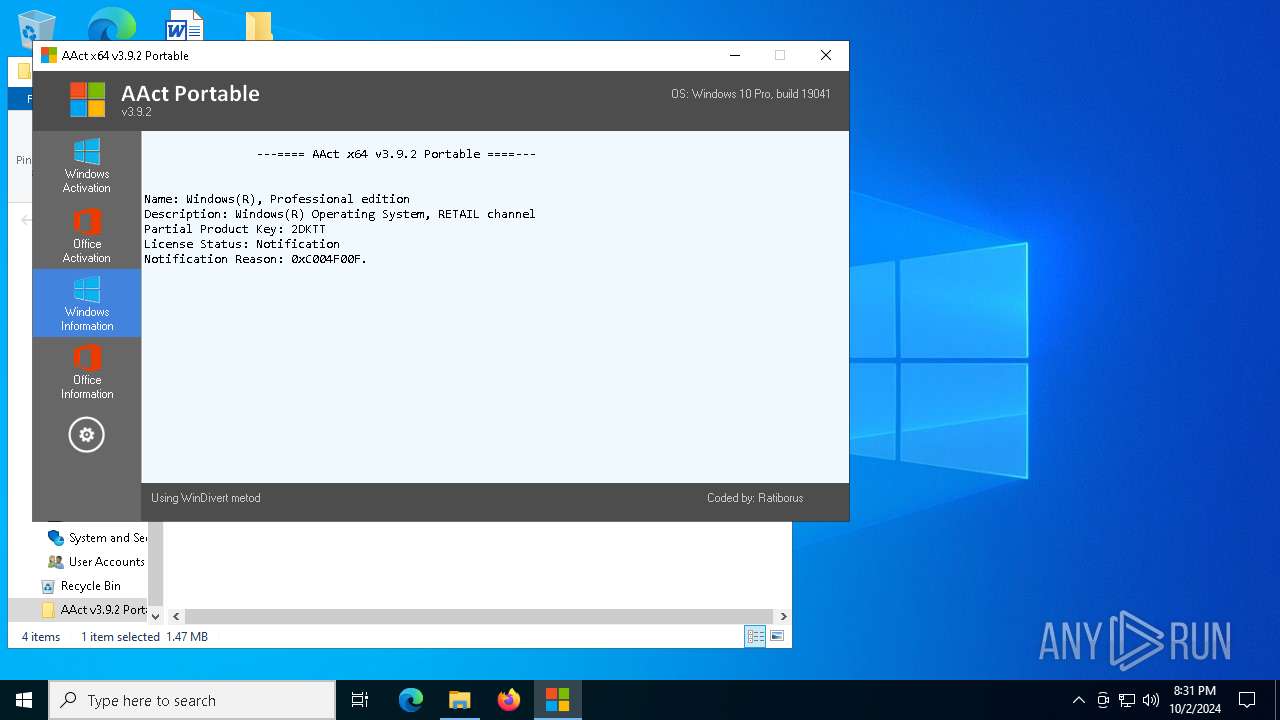
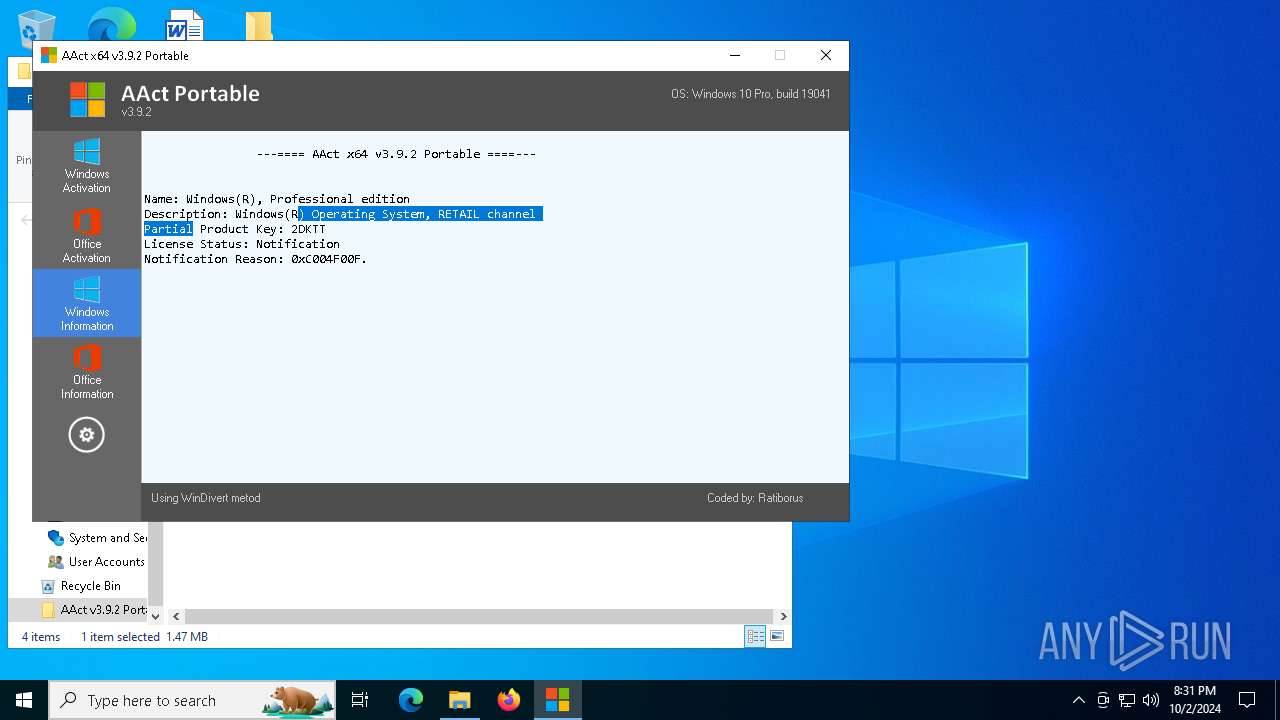
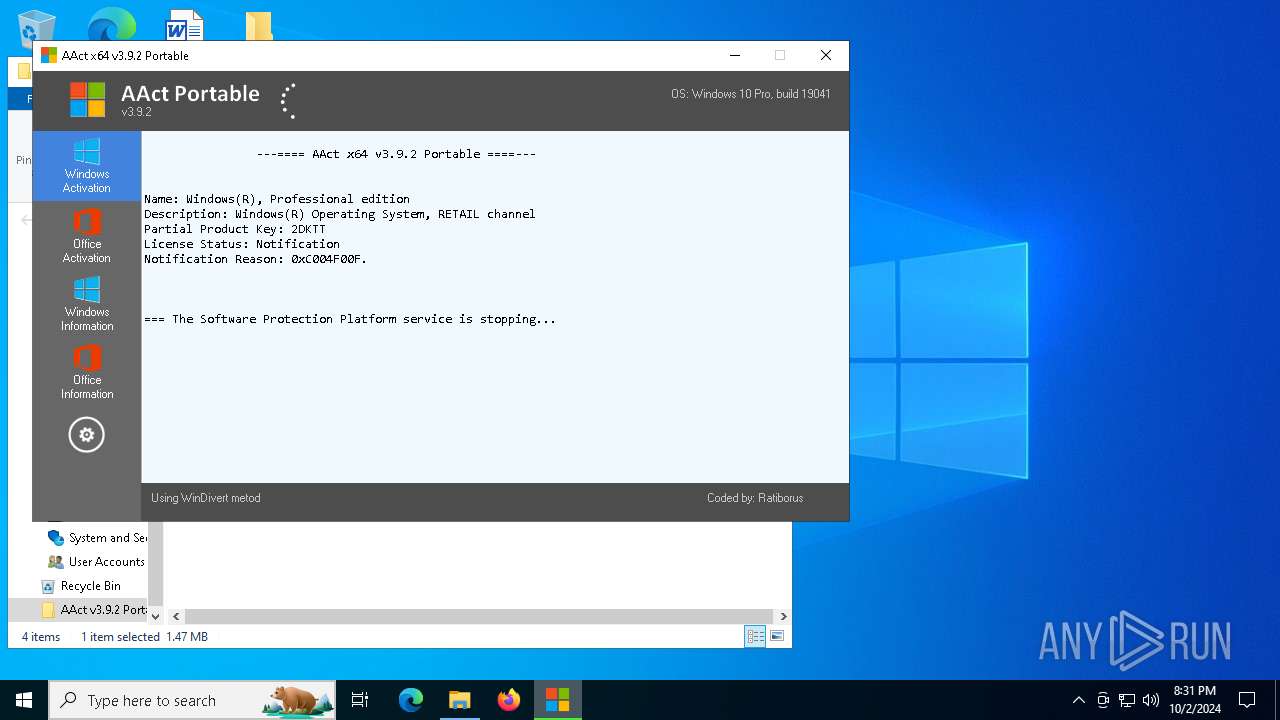
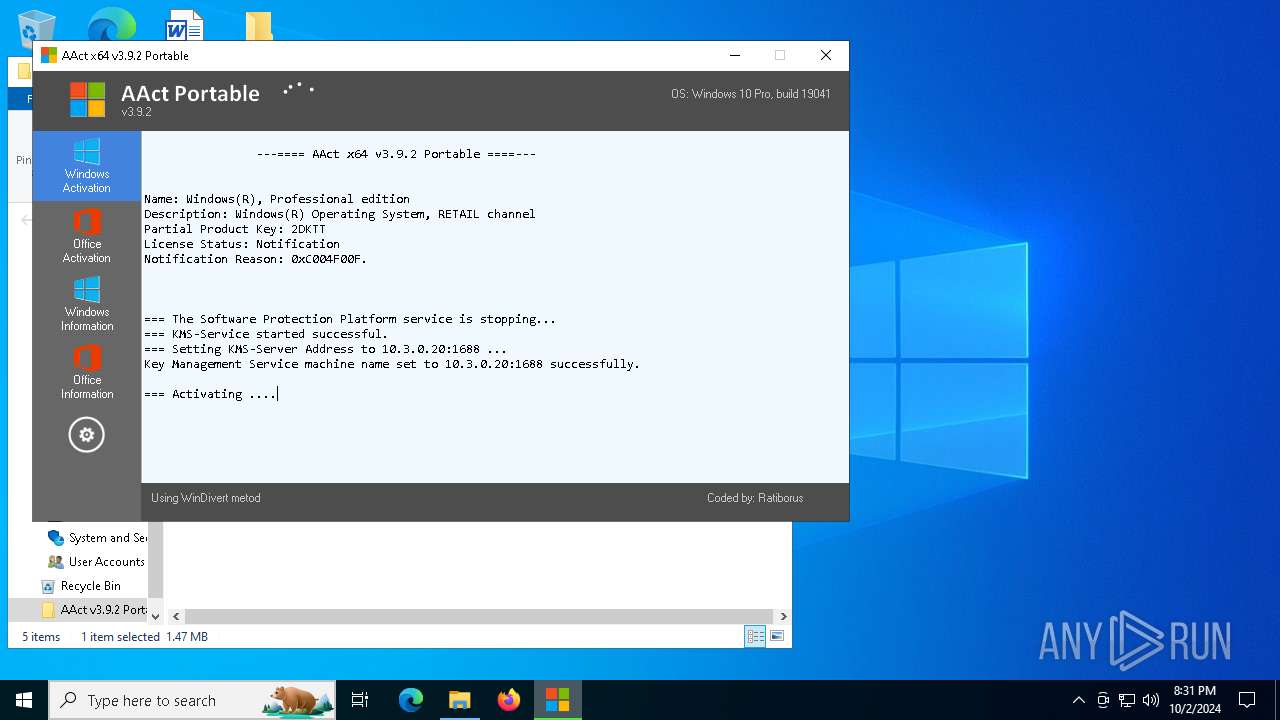
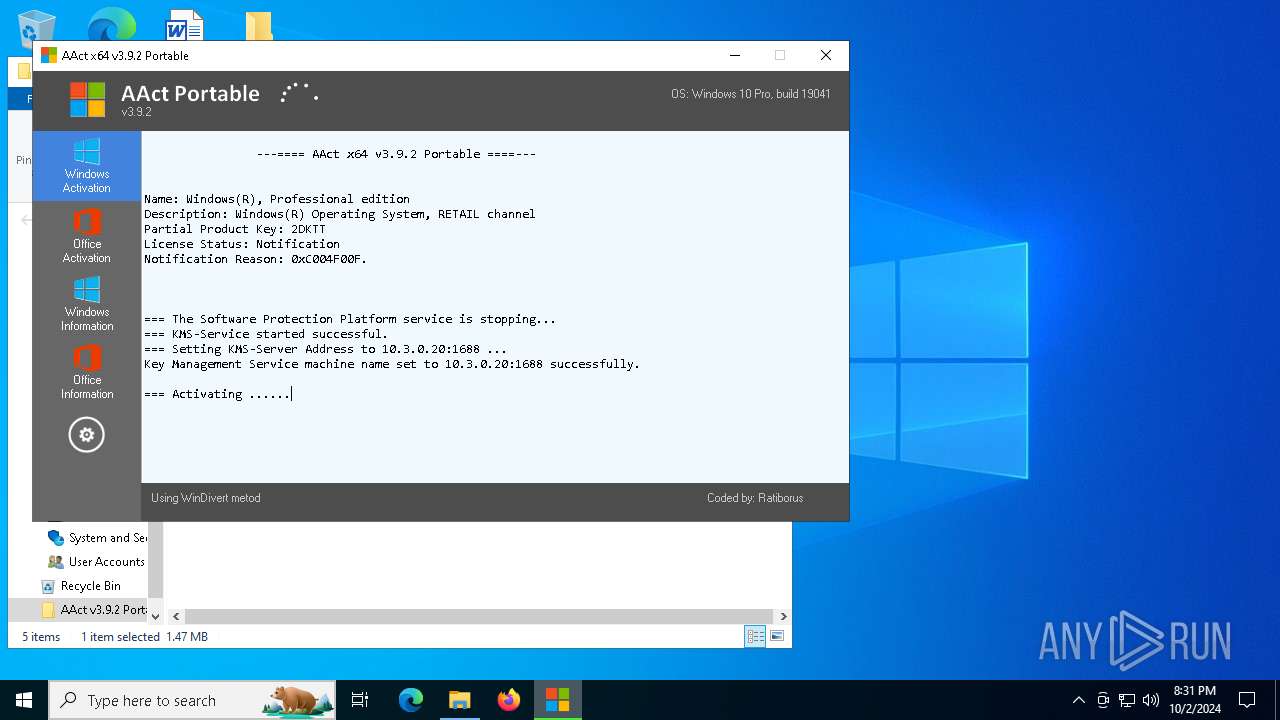
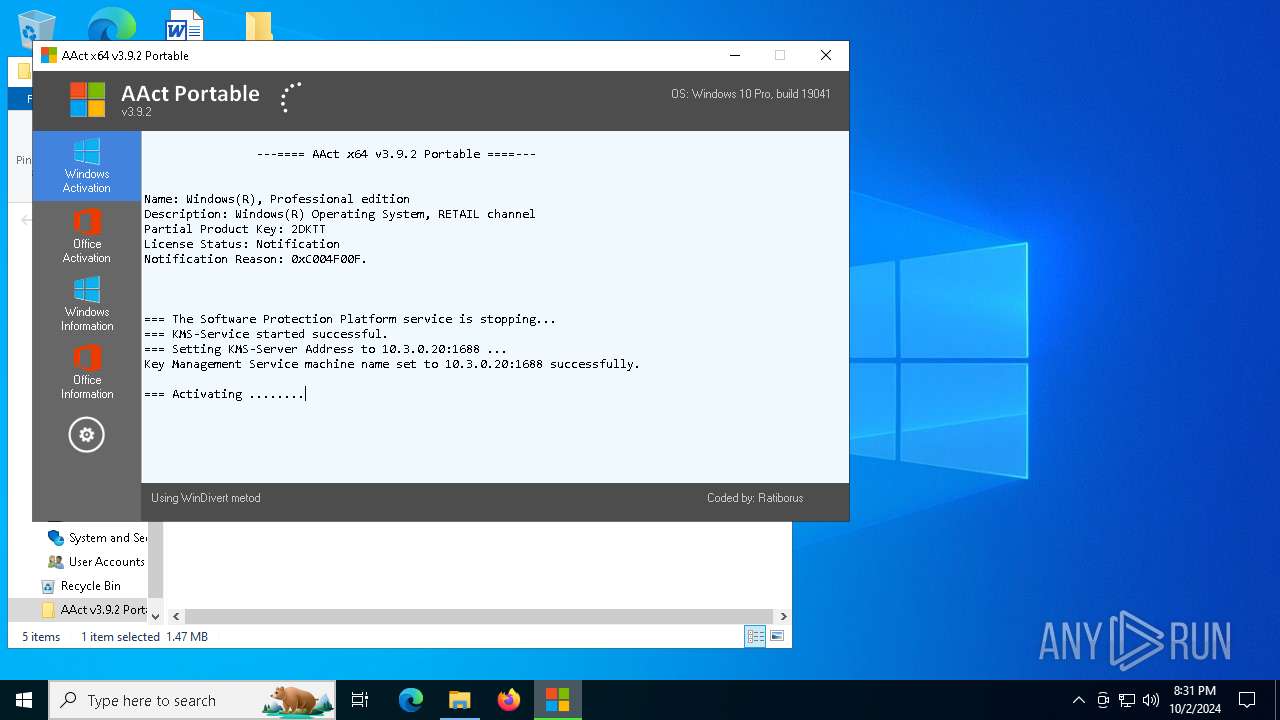
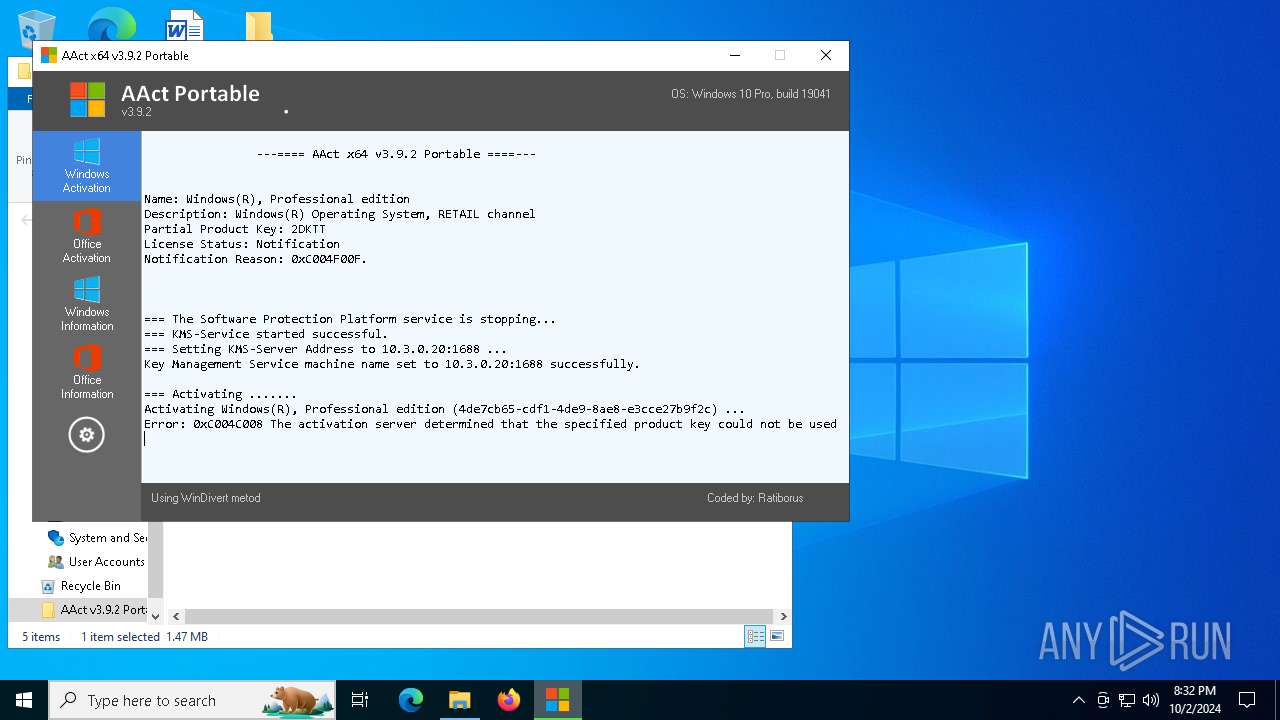
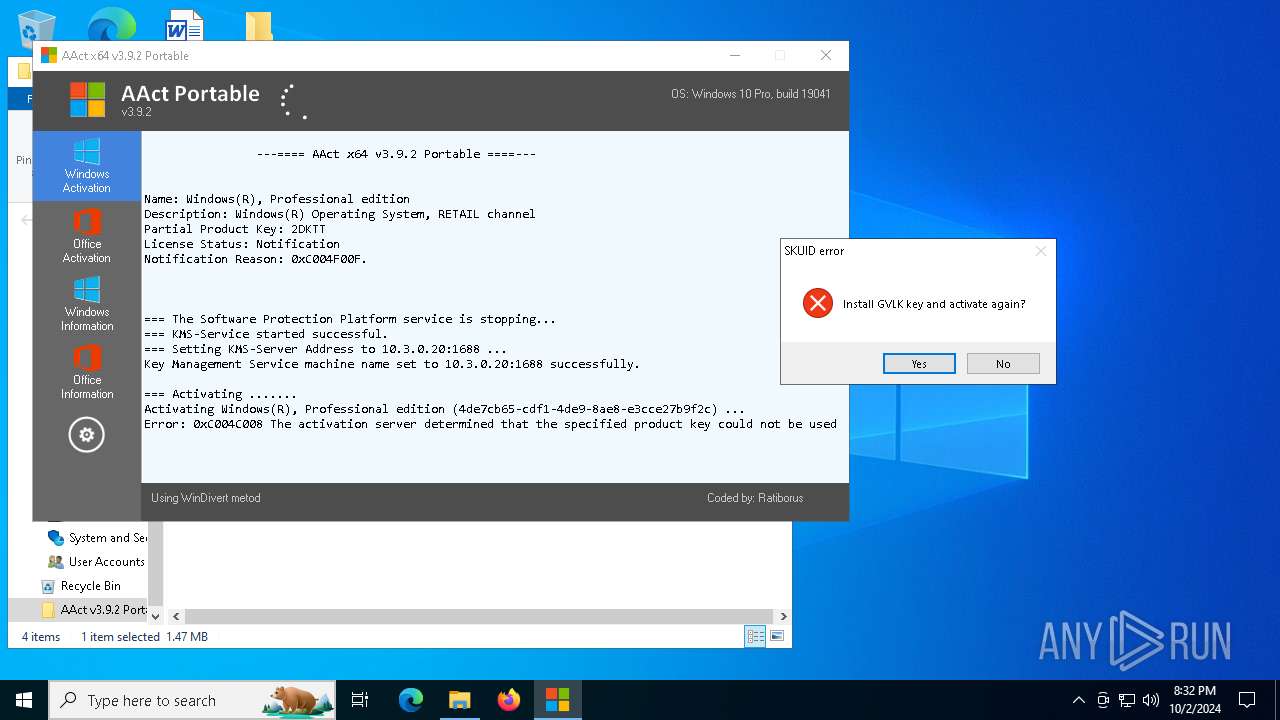
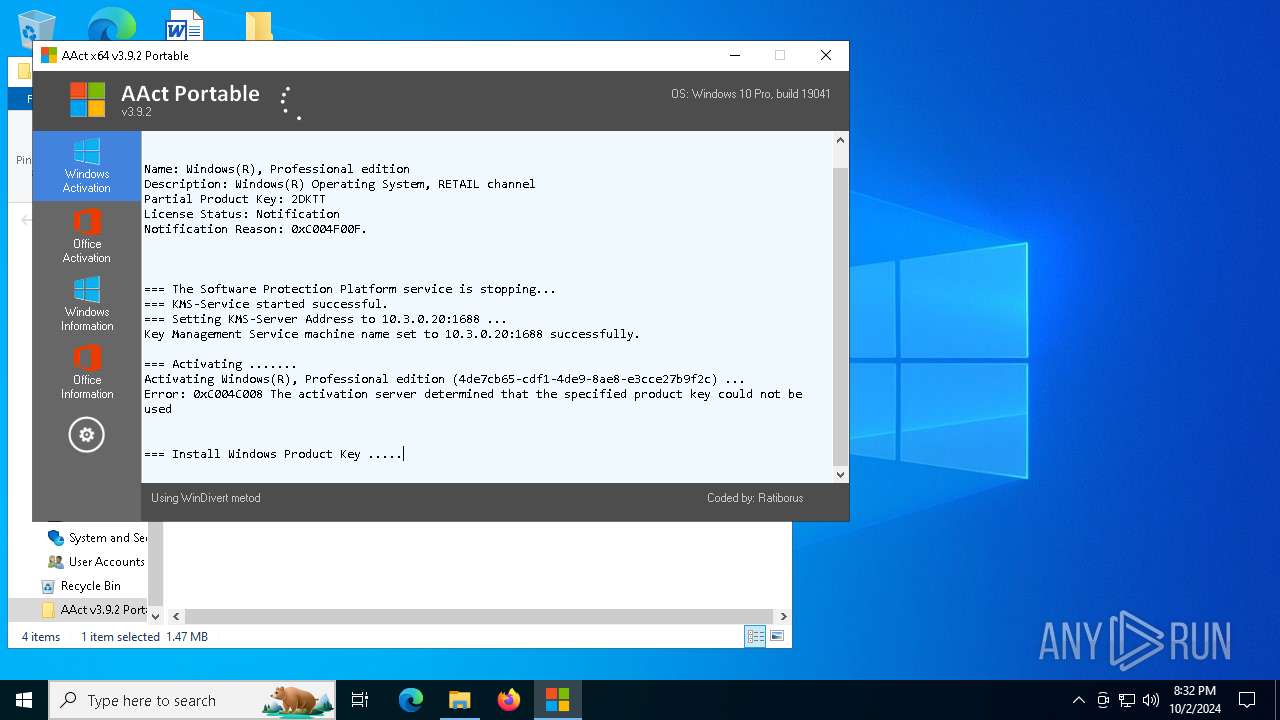
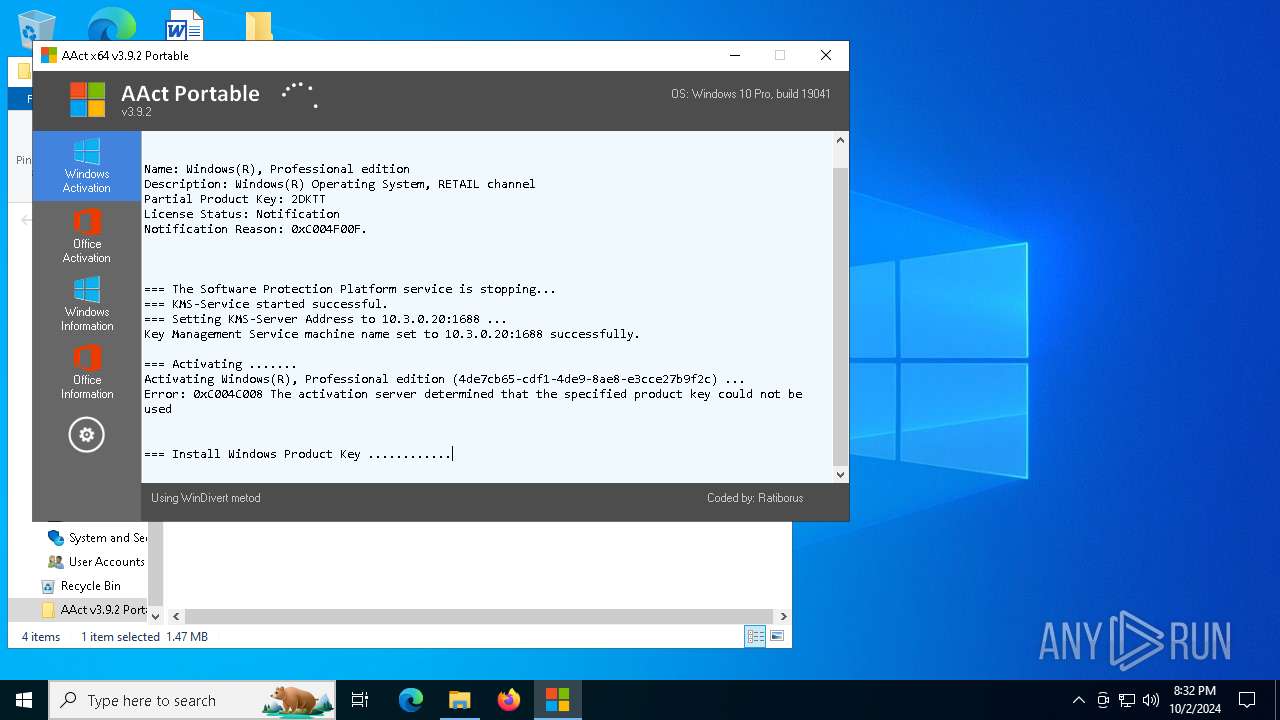
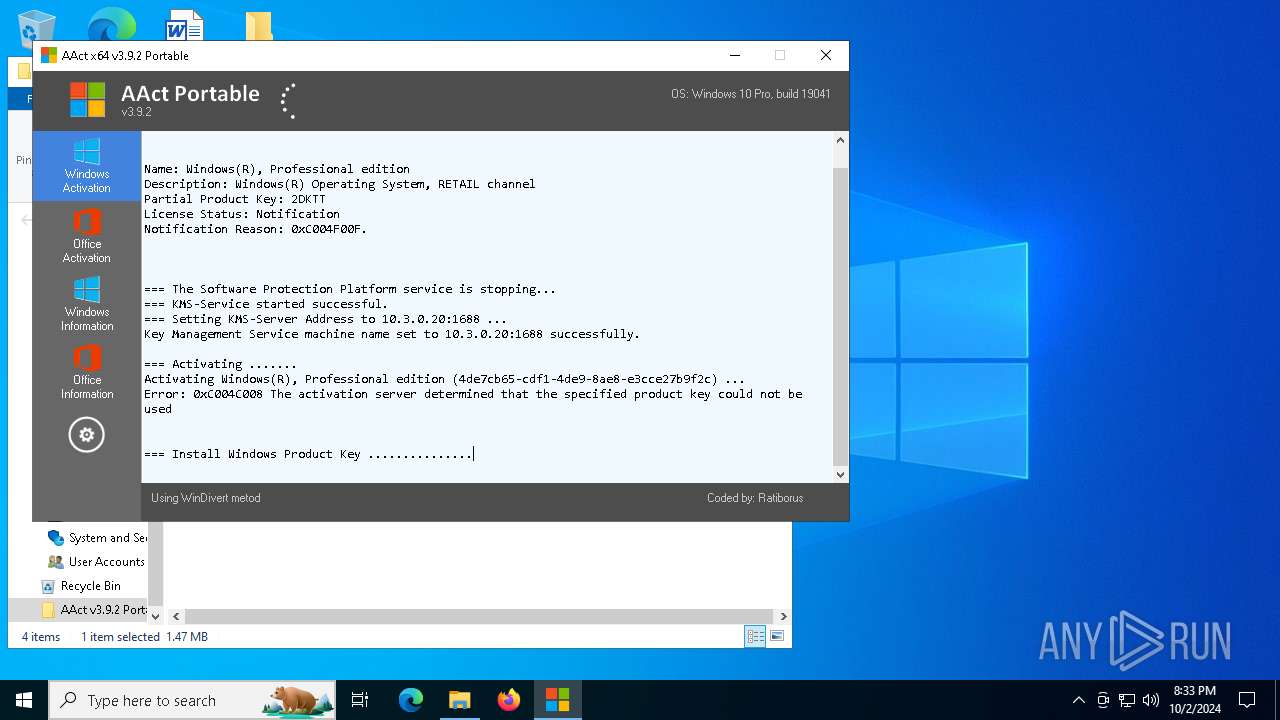
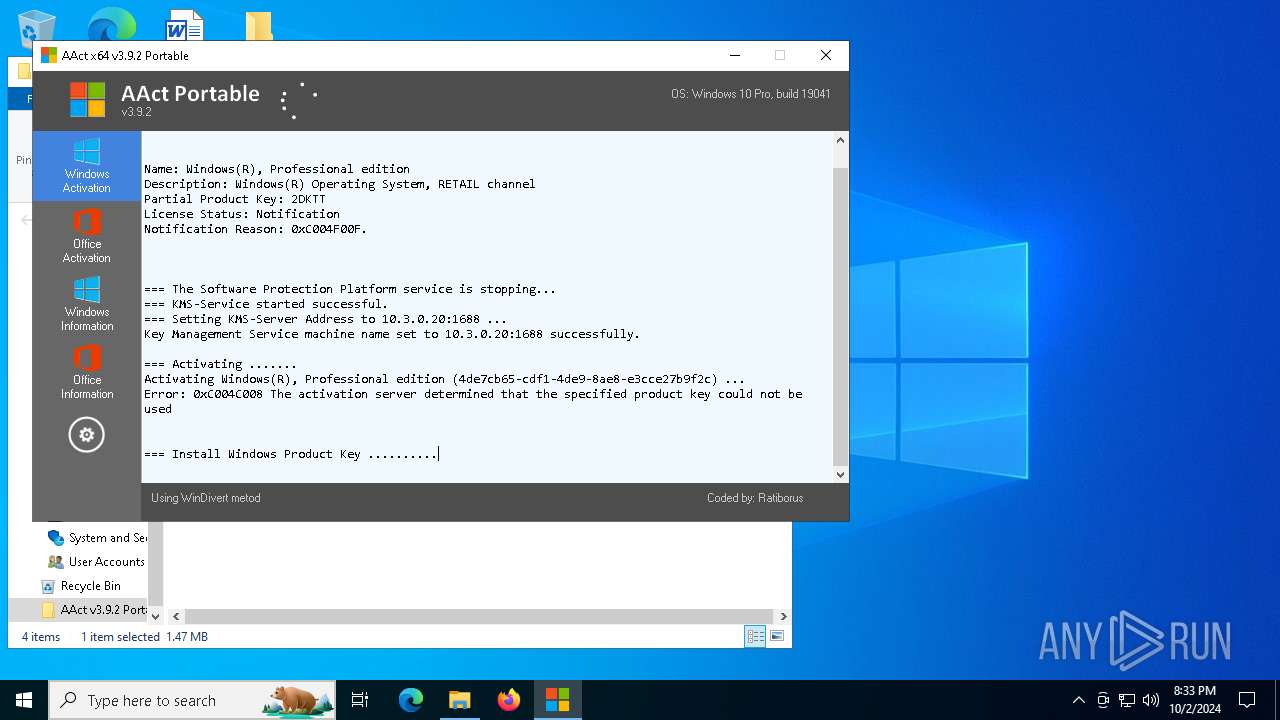
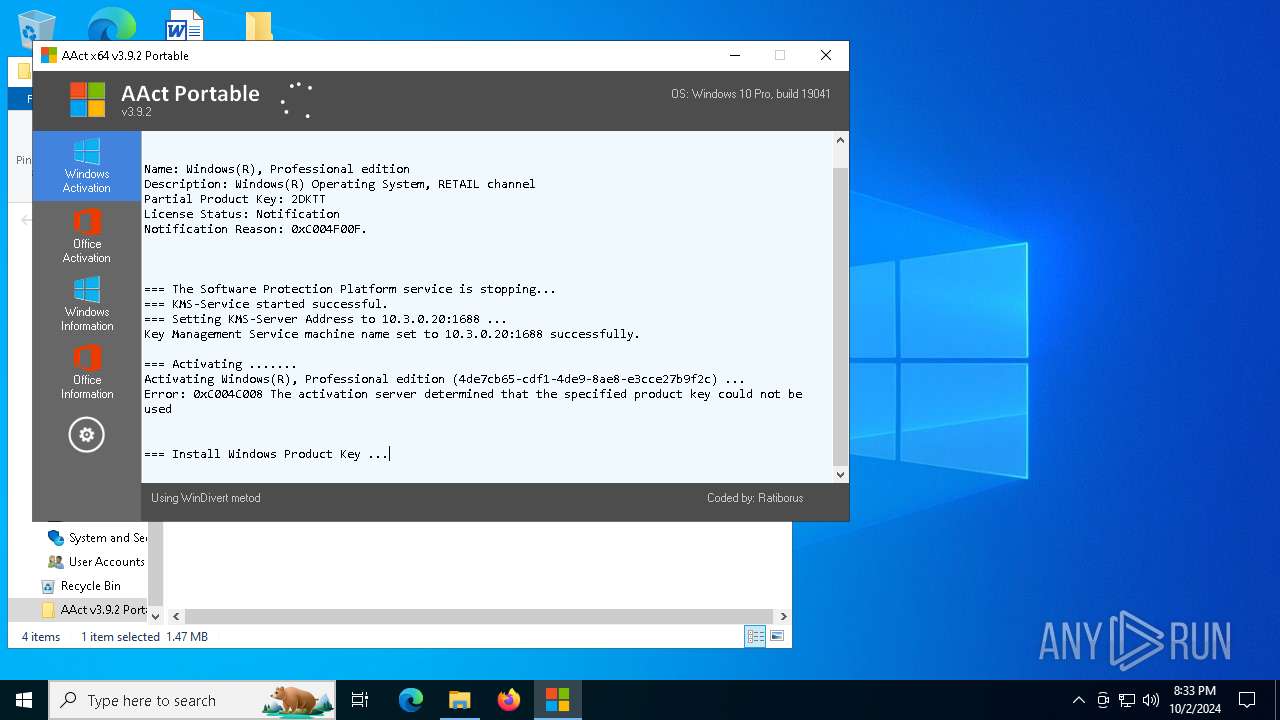
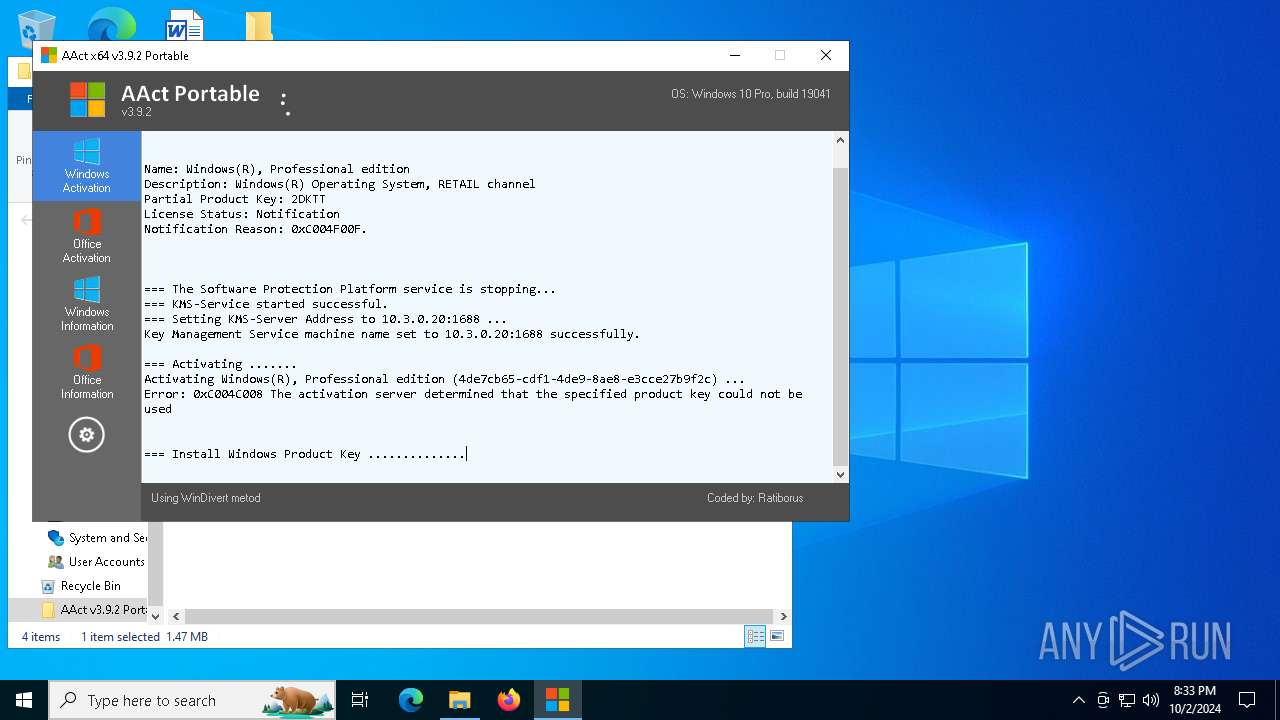
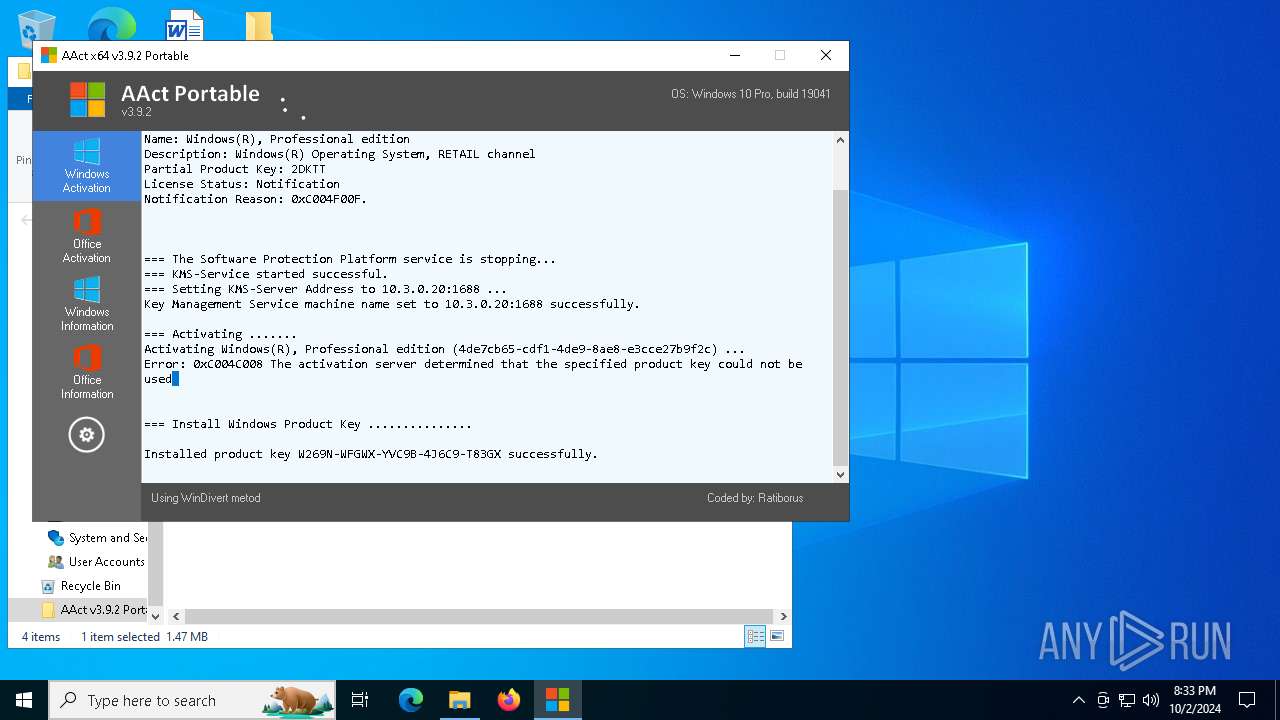
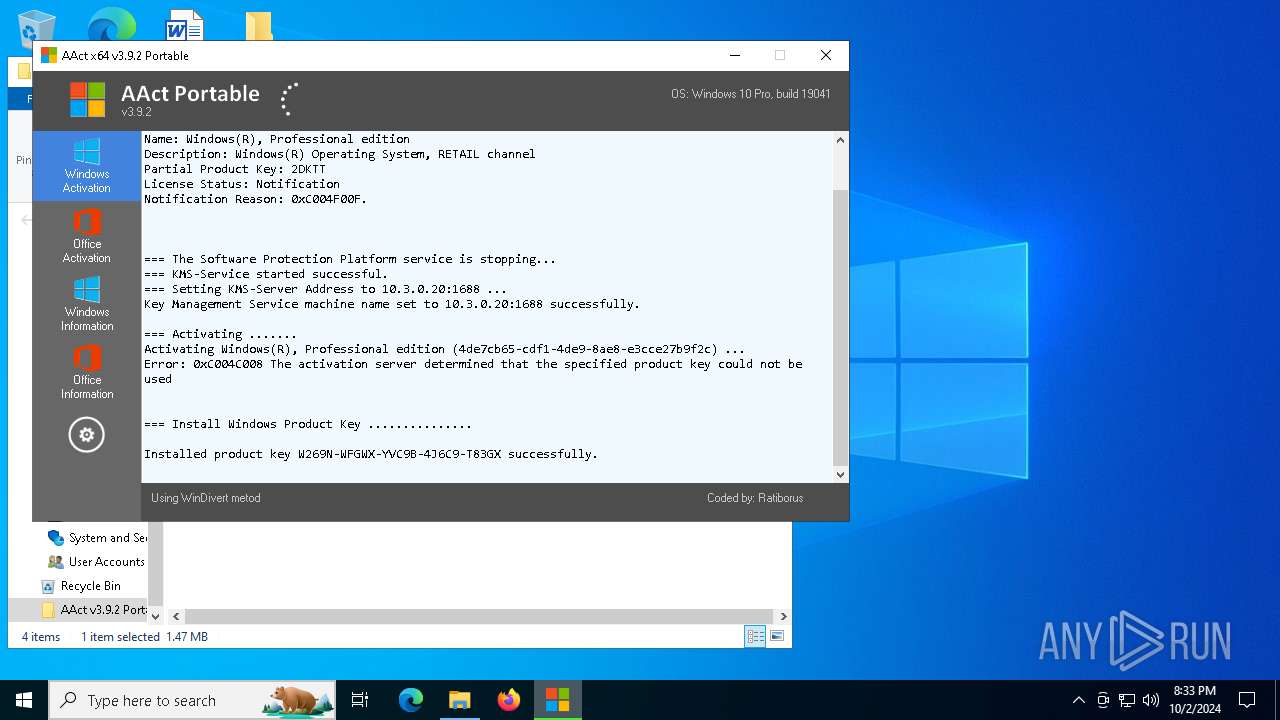
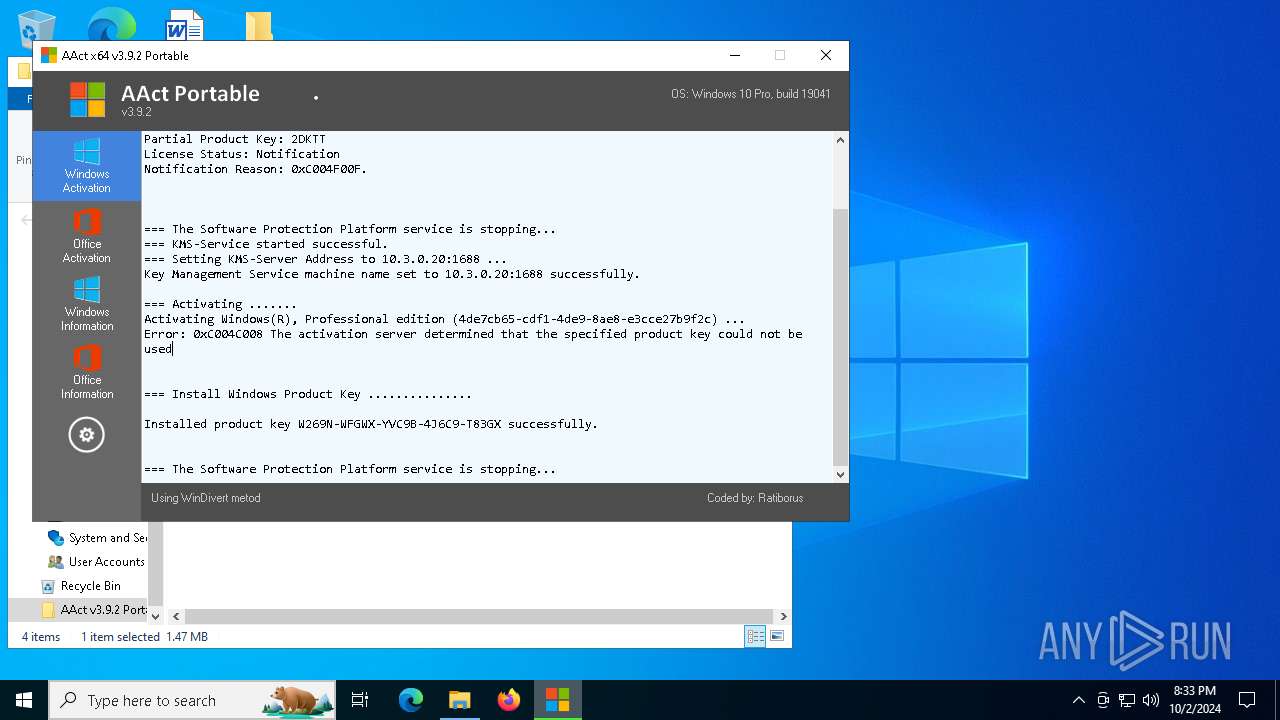
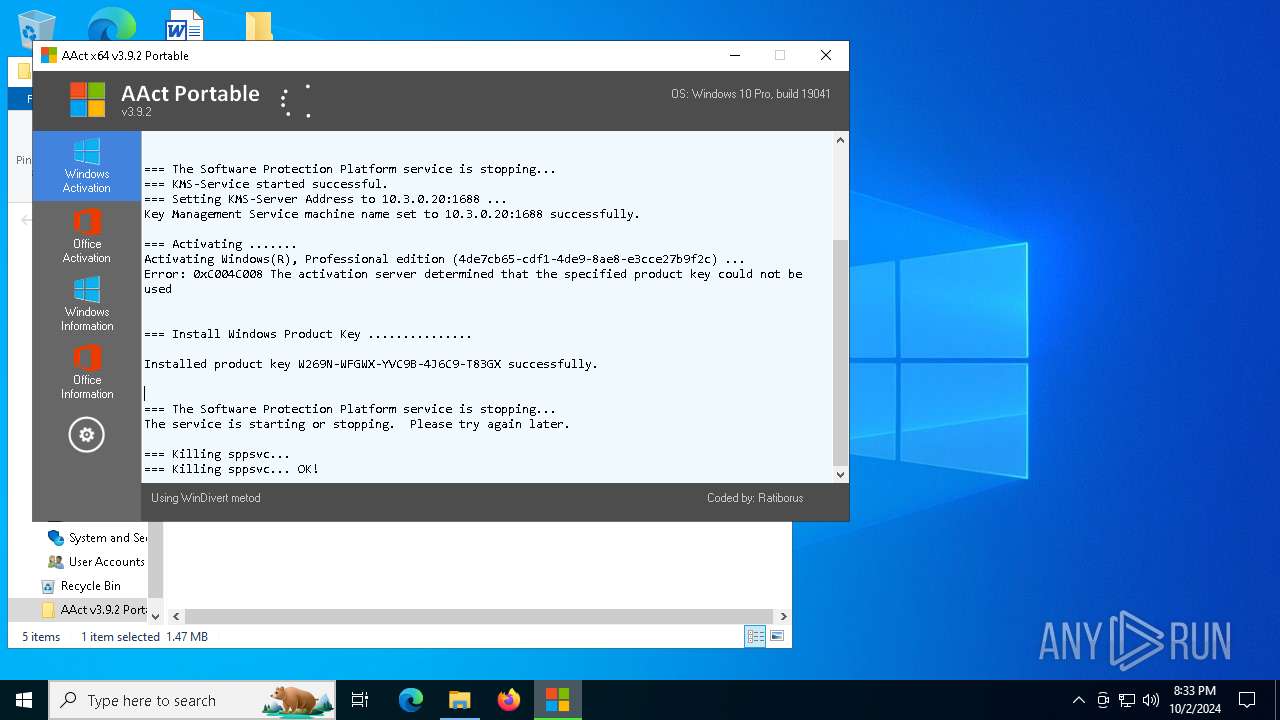
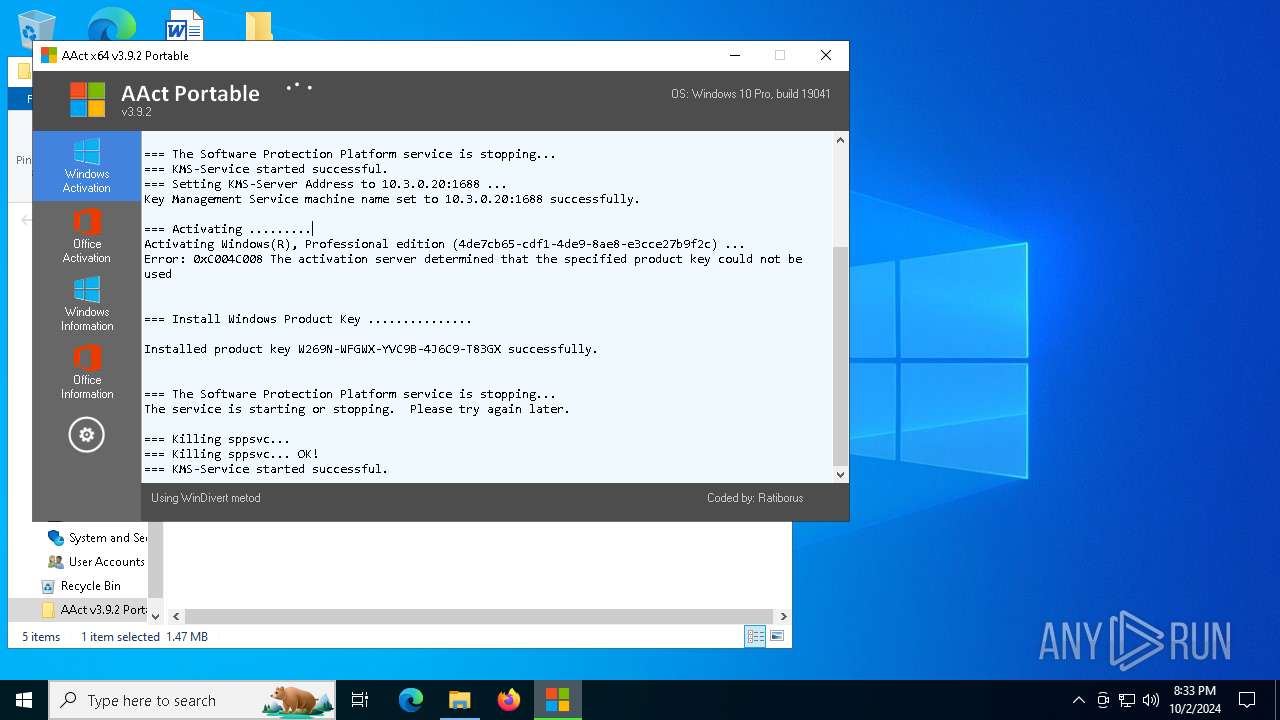
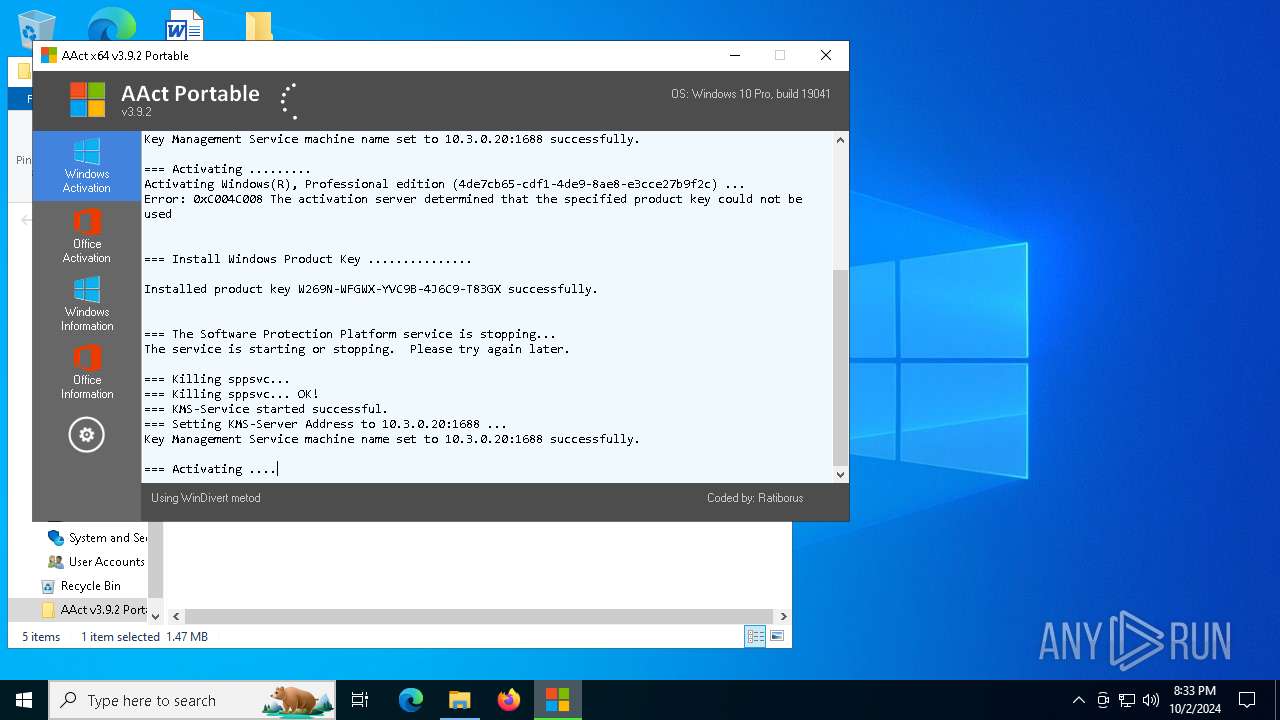
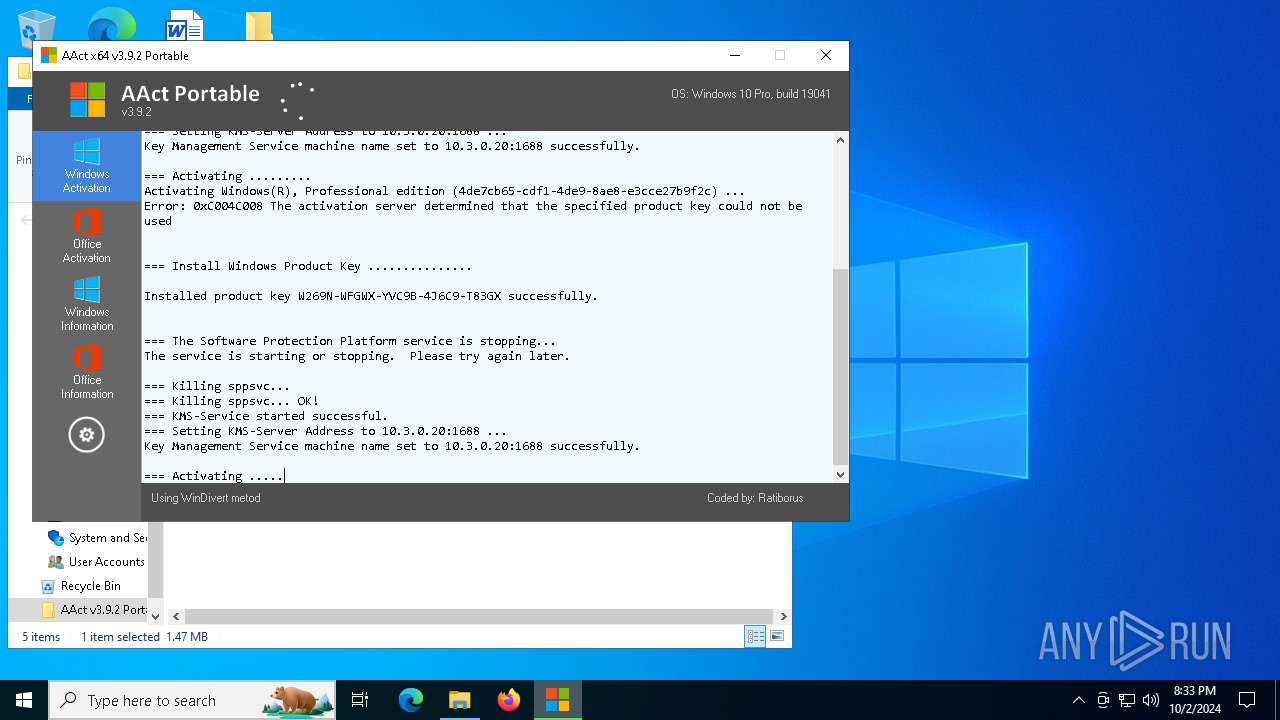
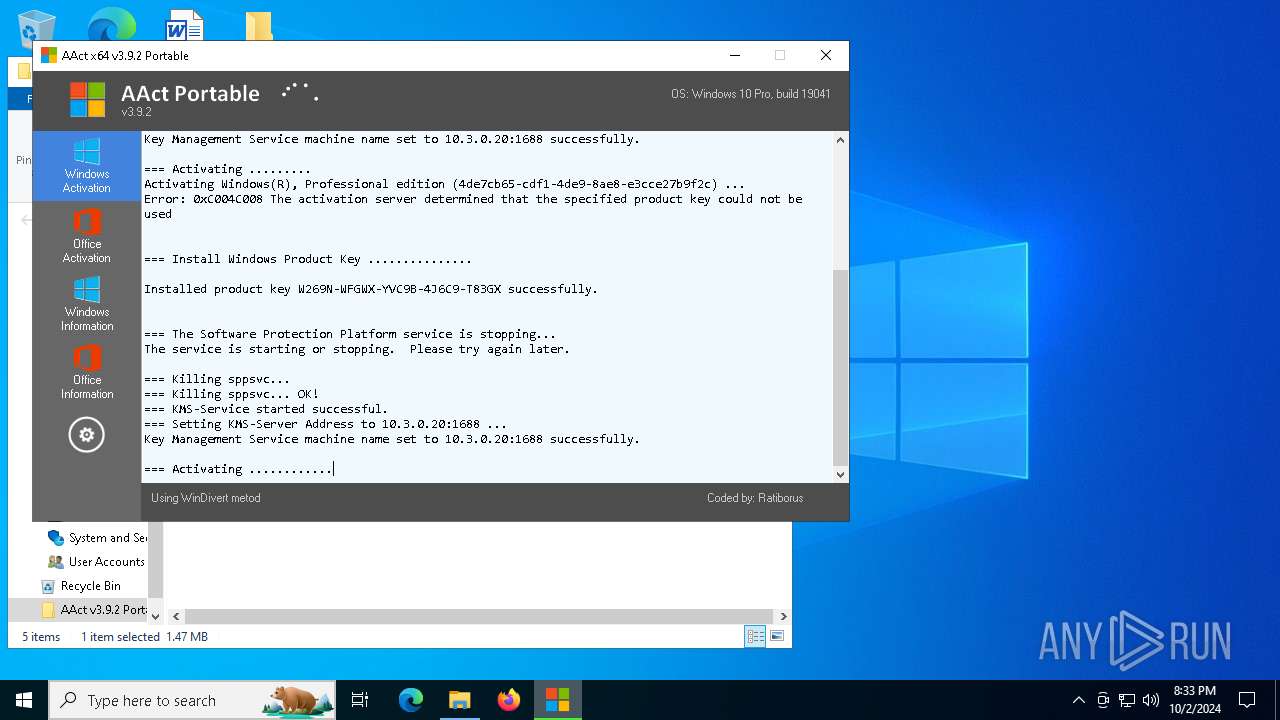
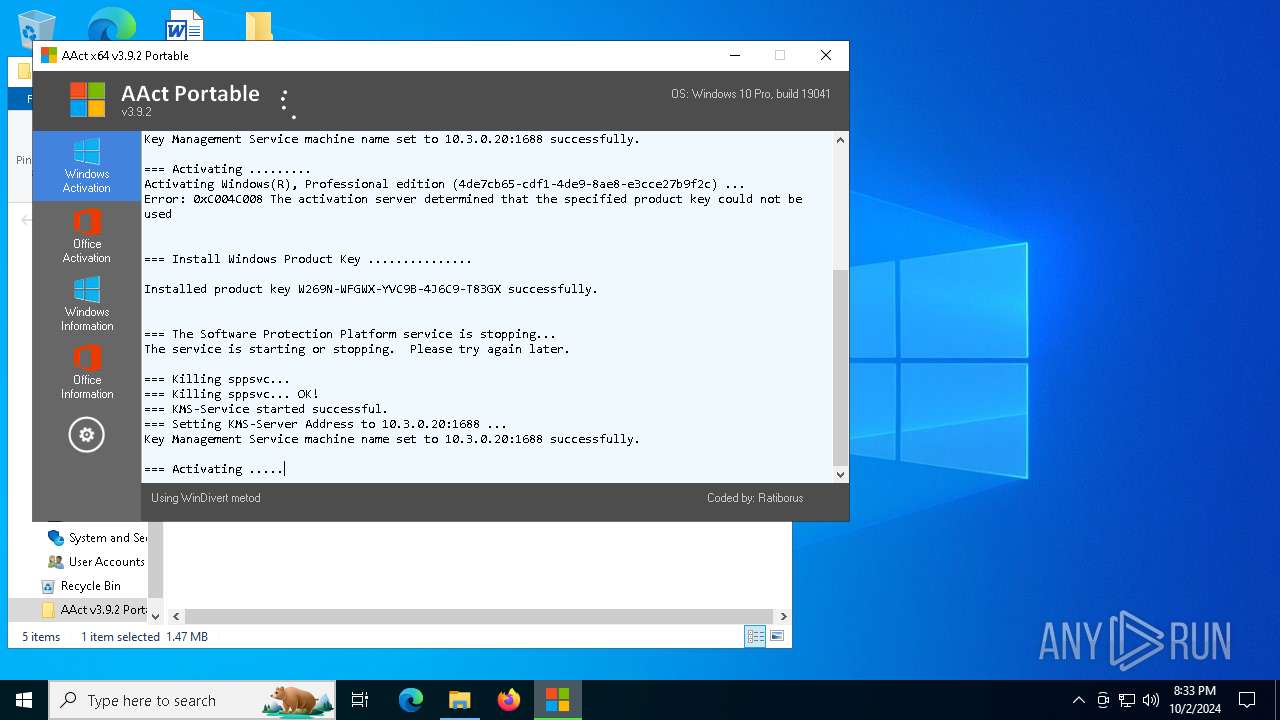
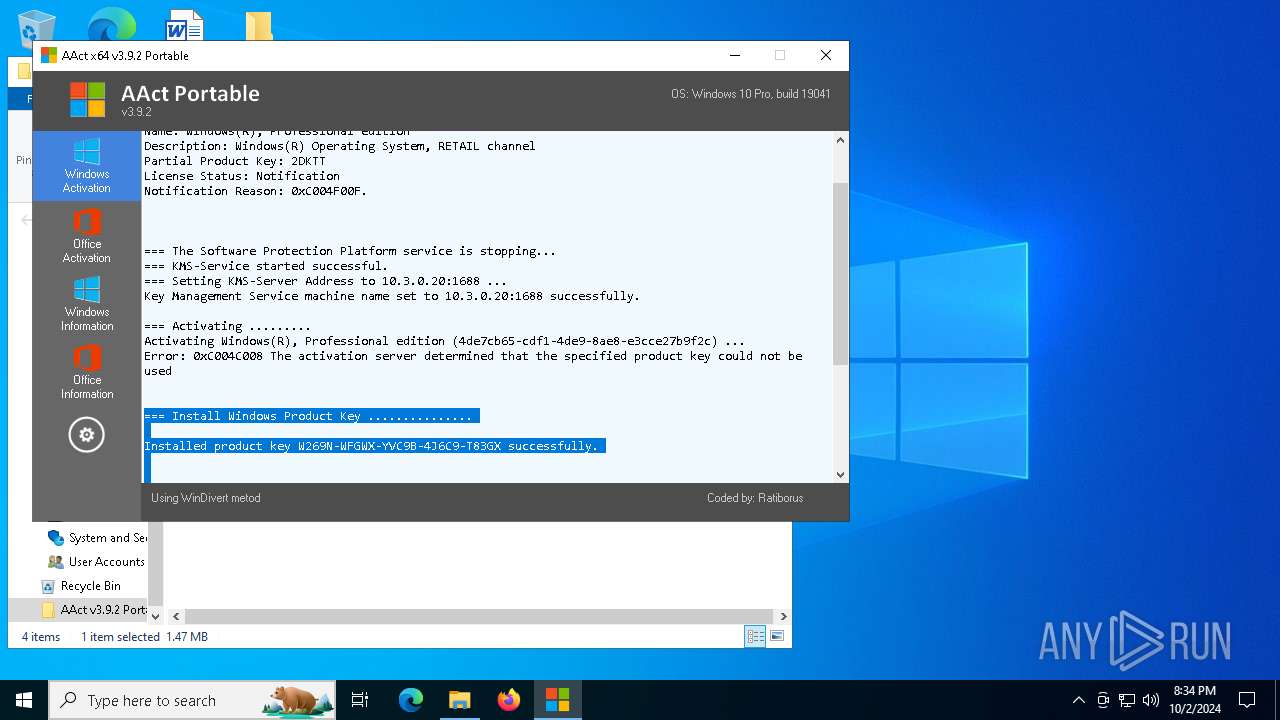
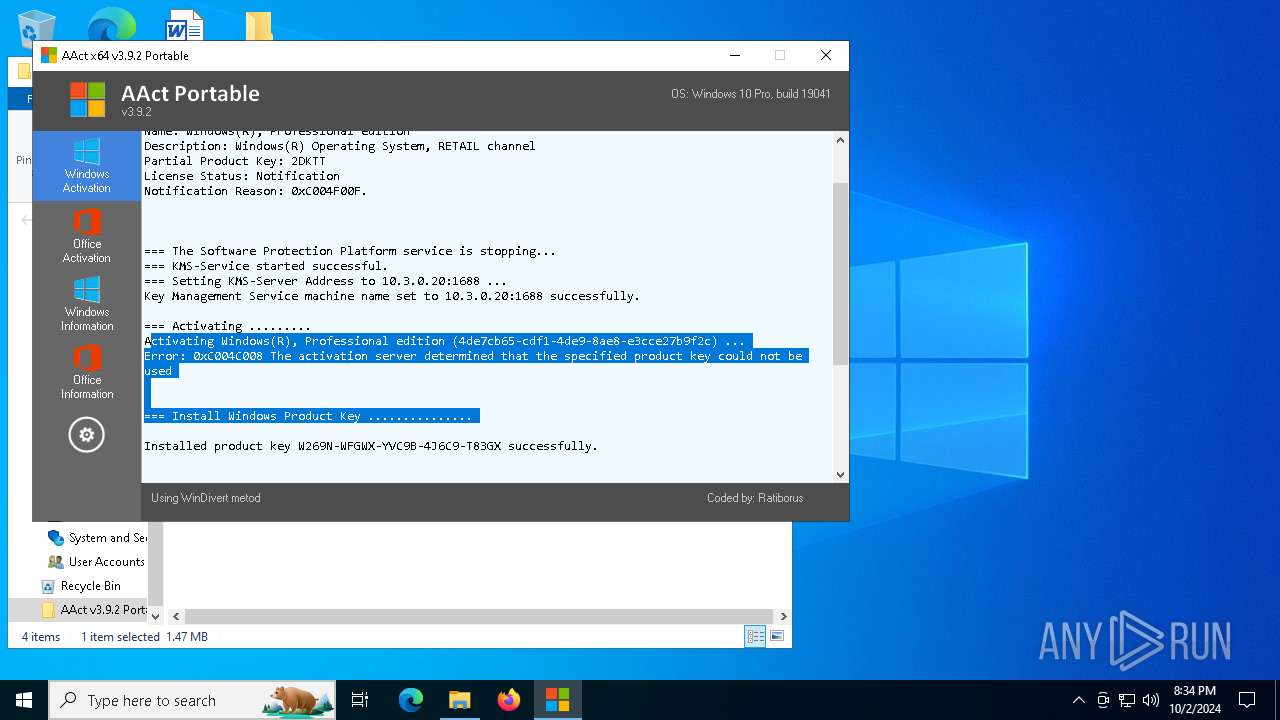
| File name: | AAct v3.9.2 Portable.7z |
| Full analysis: | https://app.any.run/tasks/263c619b-7047-4a2d-994d-512827d8ce30 |
| Verdict: | Malicious activity |
| Analysis date: | October 02, 2024, 20:29:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | D16D295657729B1BA36504F265EBC7CC |
| SHA1: | 23FE9FEC13F646FDD74475F54C53C55D8F31D707 |
| SHA256: | 95C598AC20D2800D55753B4ACF4D65DBAD188FCFB536E0460F429C5E0DB82DCE |
| SSDEEP: | 98304:LWY2RYJNLIMsFP6I5UHQowyFlRfRqtA9ykCKulJ7sXQRDthyA+IjJ8MGb9TGXIIq:k1OT7rnH |
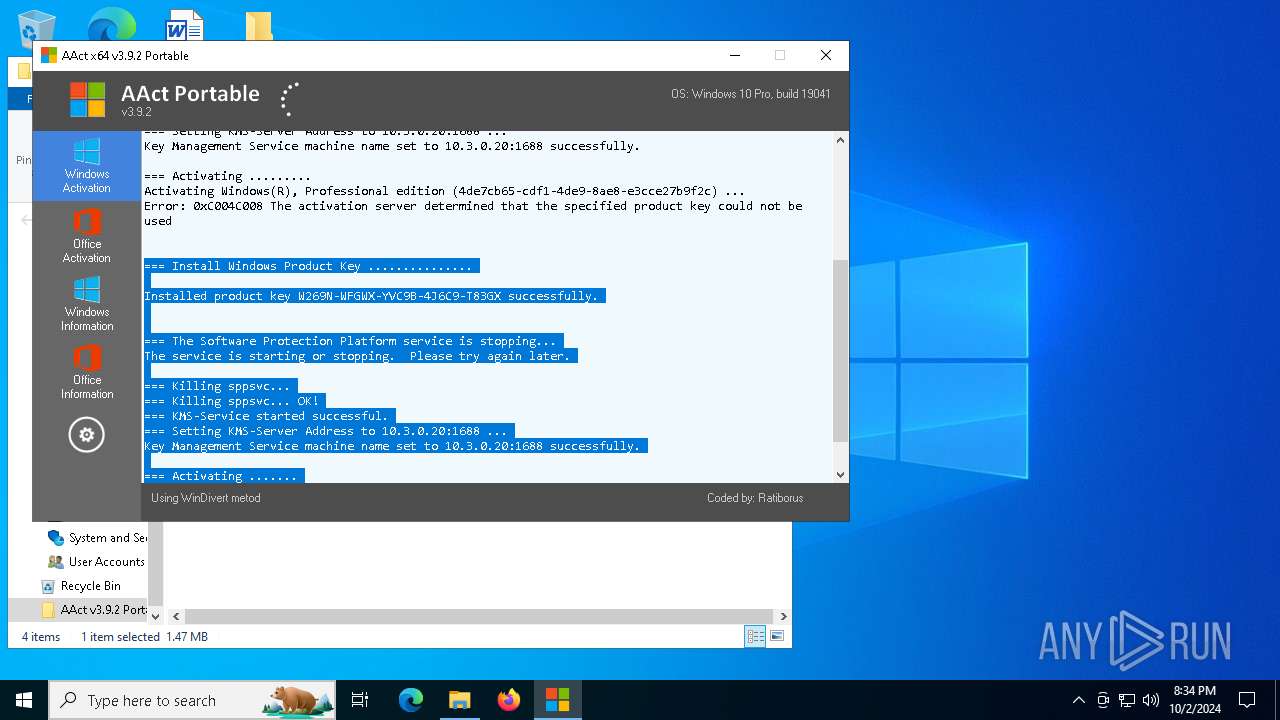
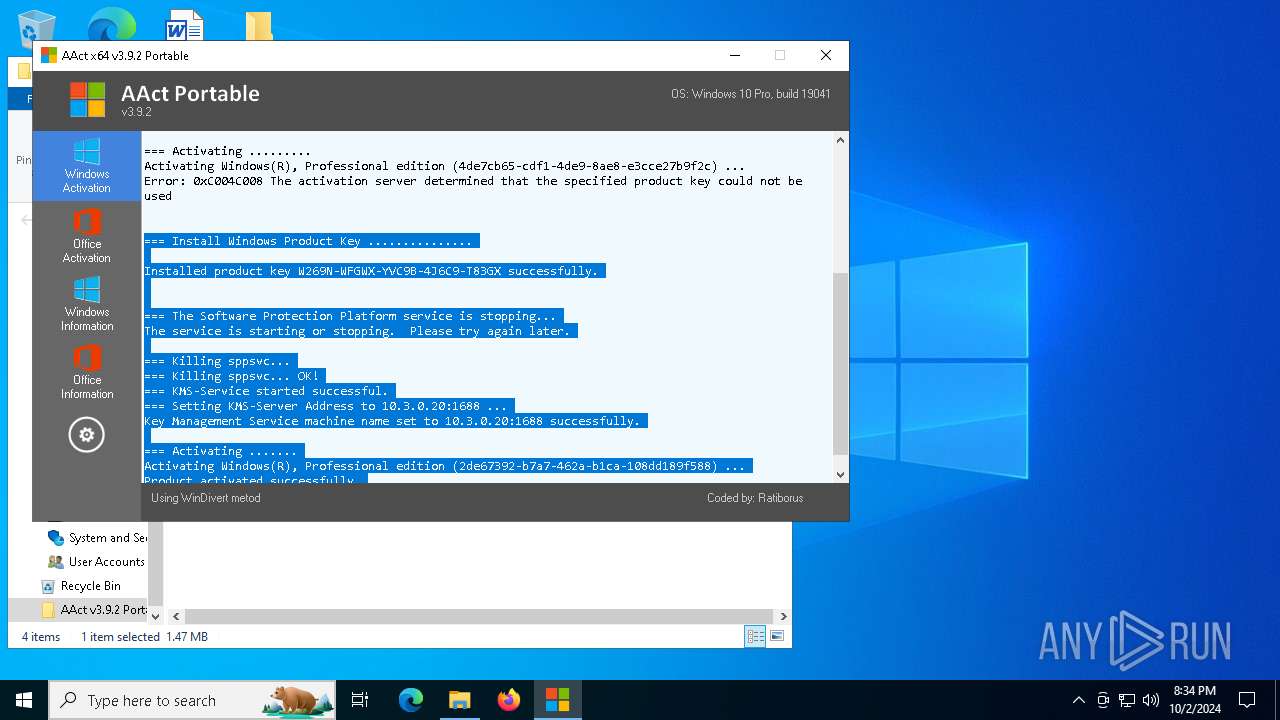
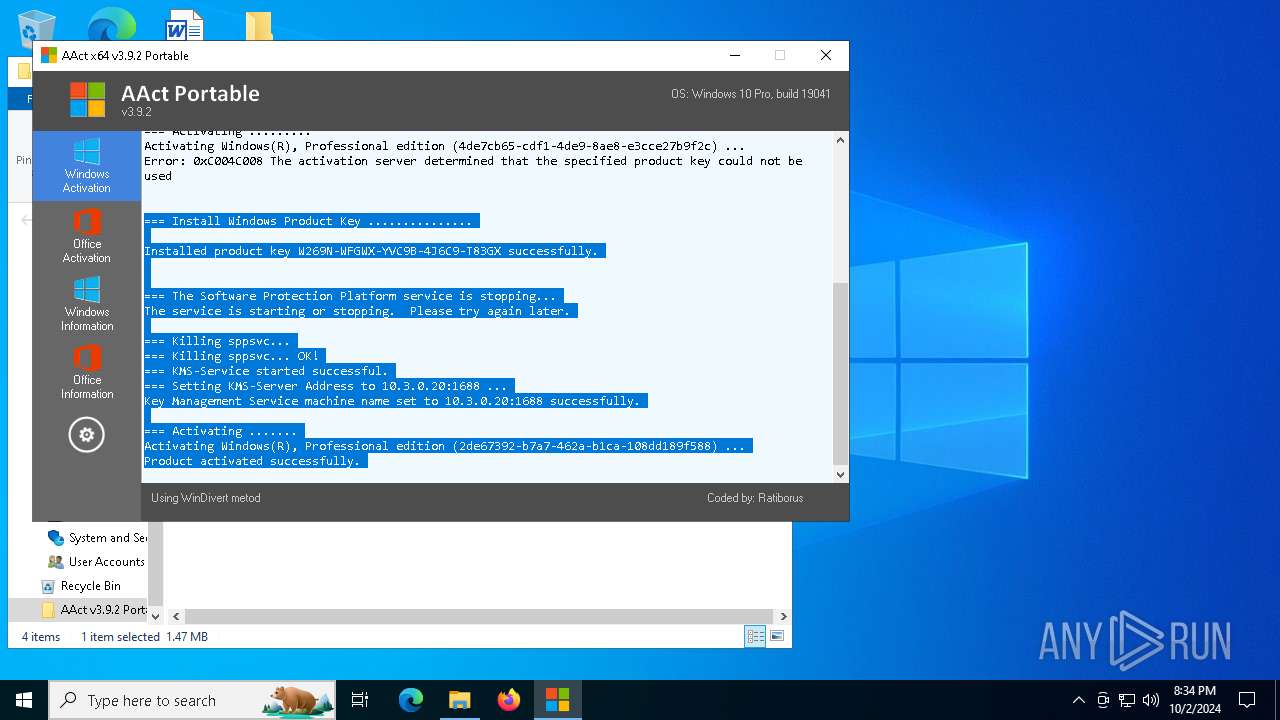
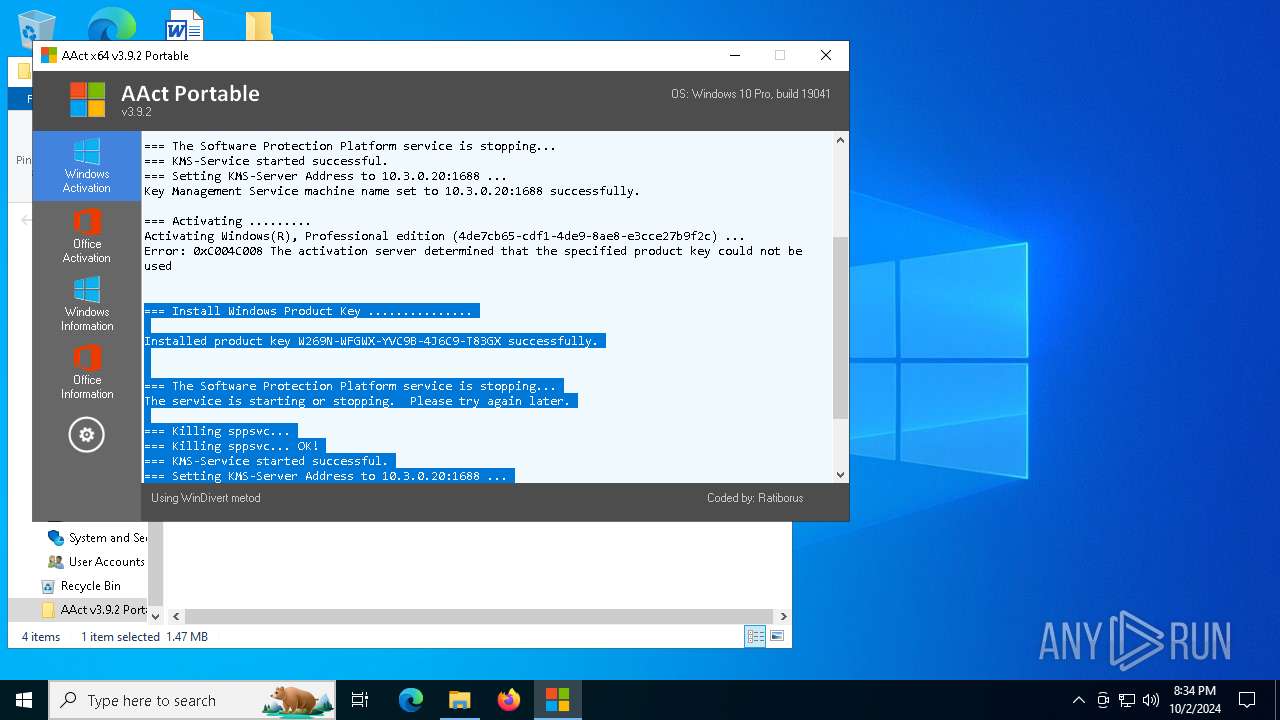
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3444)
- cmd.exe (PID: 4056)
SUSPICIOUS
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5920)
- cmd.exe (PID: 6436)
- cmd.exe (PID: 640)
- cmd.exe (PID: 4196)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 1808)
- cmd.exe (PID: 2892)
- cmd.exe (PID: 4104)
- cmd.exe (PID: 6632)
- cmd.exe (PID: 2924)
- cmd.exe (PID: 1312)
- cmd.exe (PID: 6708)
- cmd.exe (PID: 4716)
The process executes VB scripts
- cmd.exe (PID: 6424)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 4832)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 1784)
- cmd.exe (PID: 5976)
- cmd.exe (PID: 2460)
- cmd.exe (PID: 6708)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 992)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 6440)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 3924)
- cmd.exe (PID: 812)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 2728)
Hides command output
- cmd.exe (PID: 5912)
- cmd.exe (PID: 3476)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 6660)
- cmd.exe (PID: 1108)
- cmd.exe (PID: 4196)
- cmd.exe (PID: 5060)
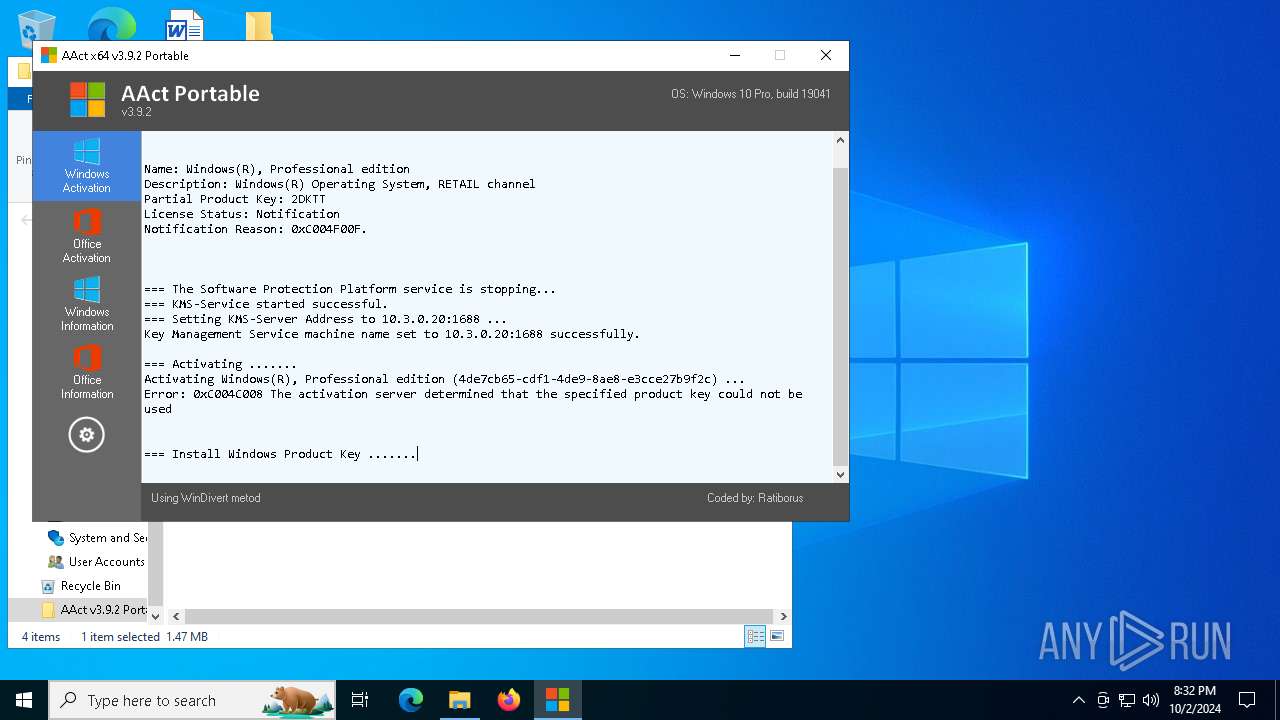
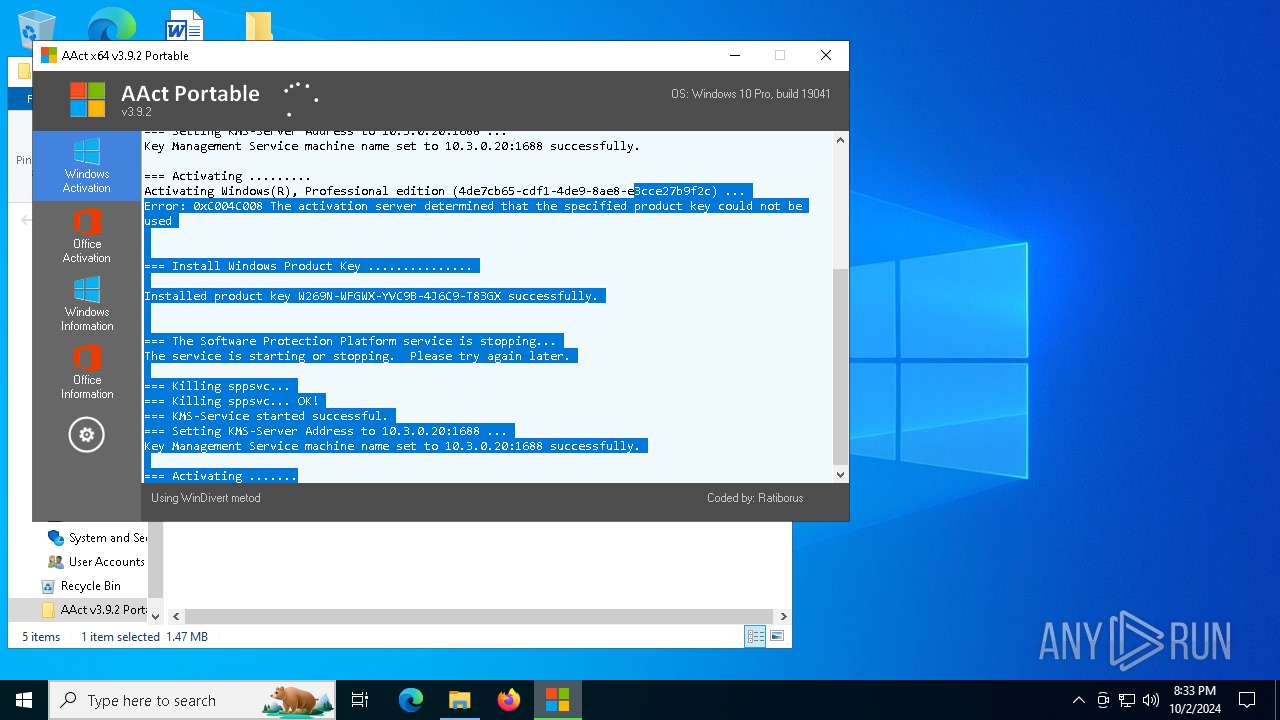
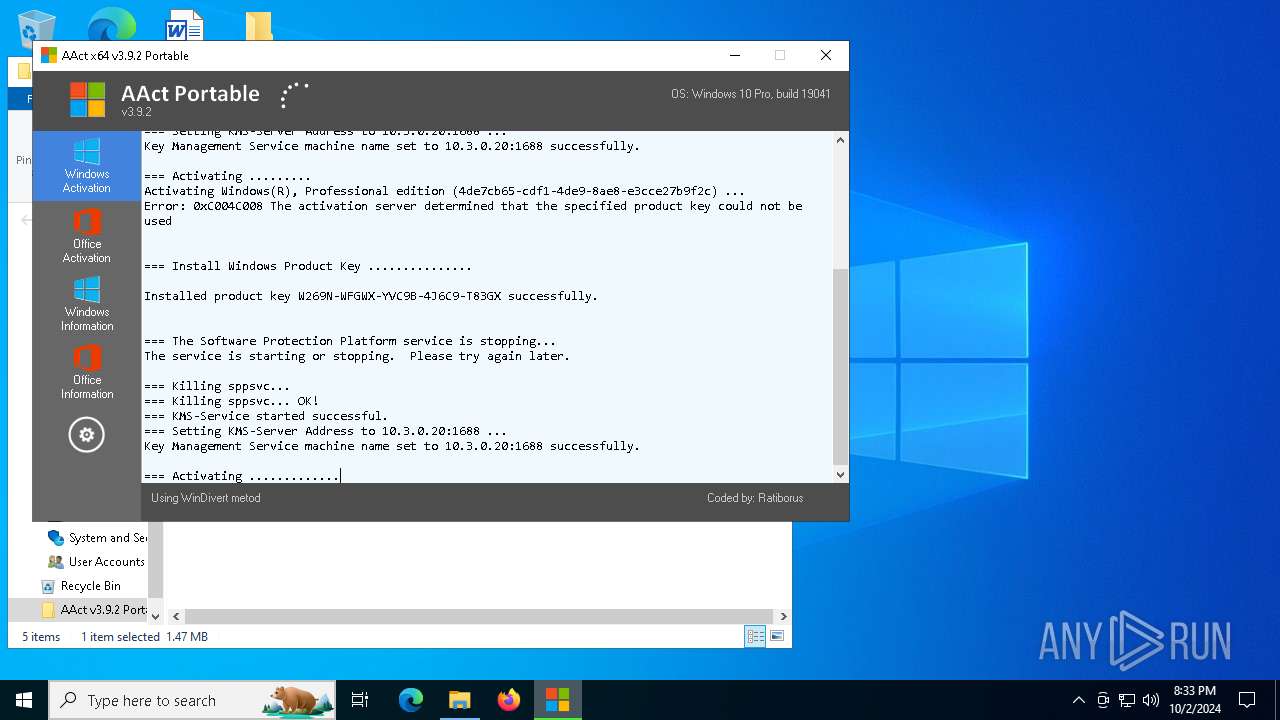
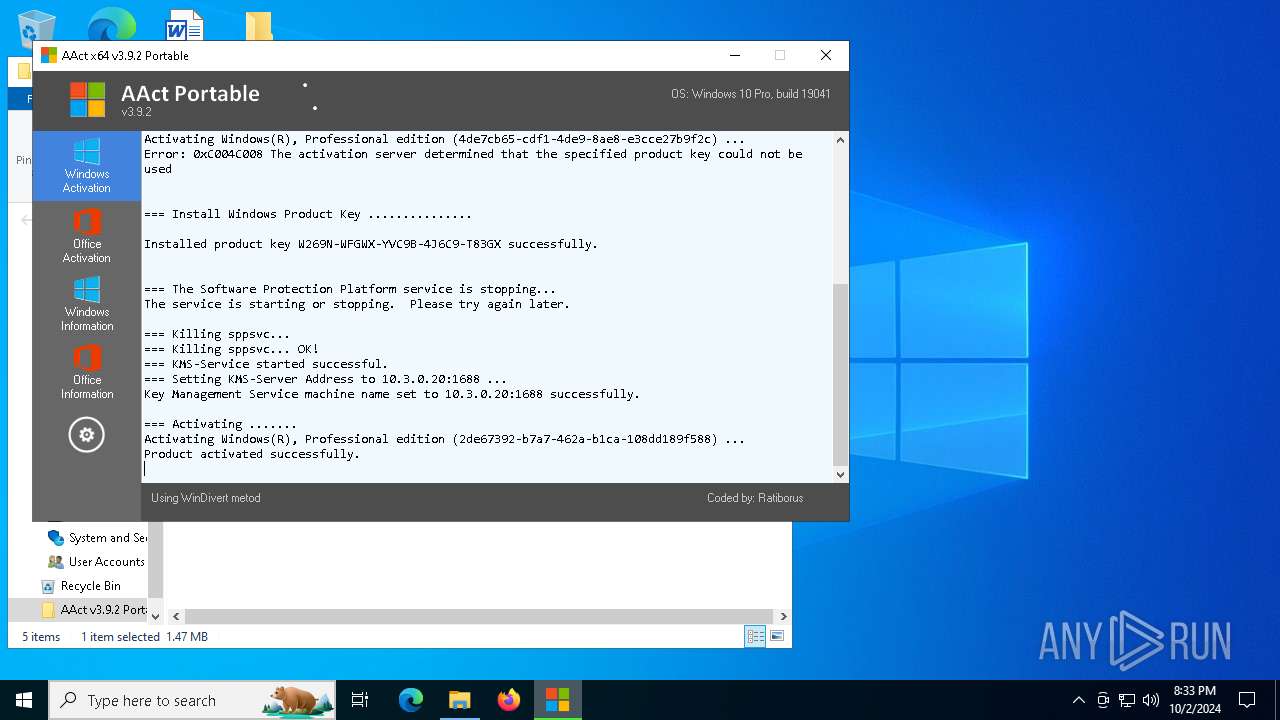
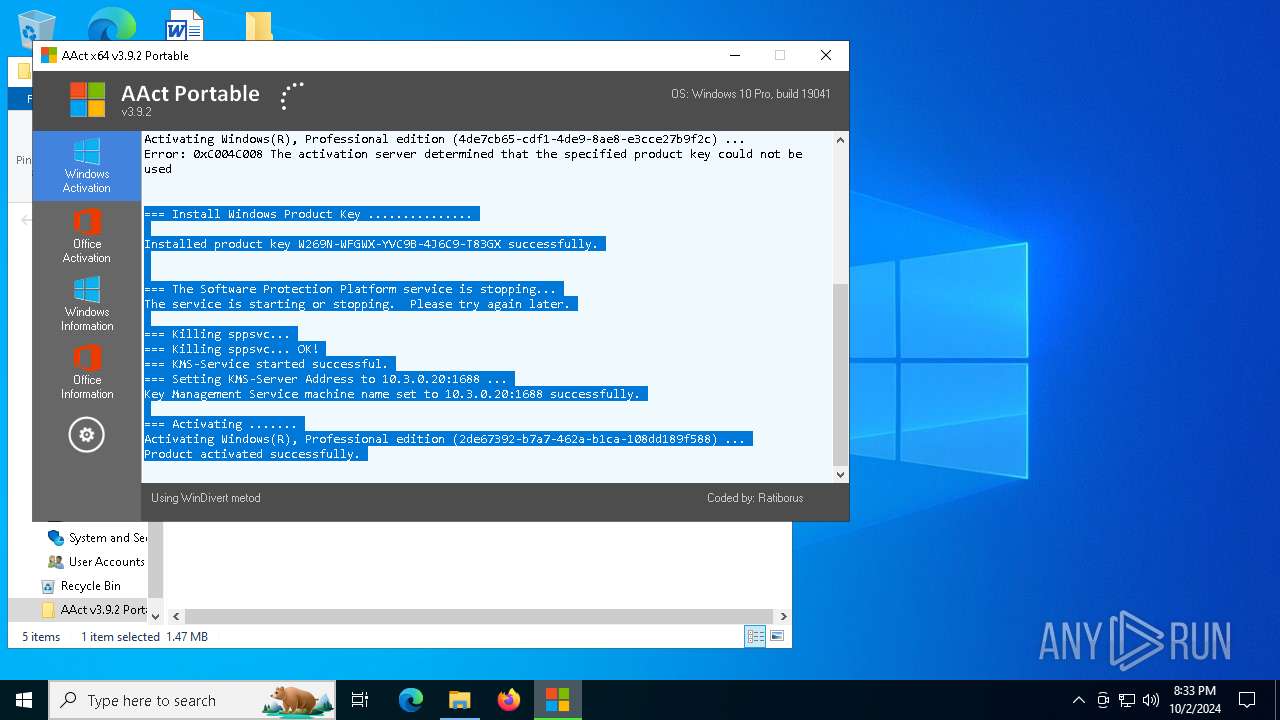
Executable content was dropped or overwritten
- AAct_x64.exe (PID: 3104)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 4424)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 3832)
Starts SC.EXE for service management
- cmd.exe (PID: 5912)
- cmd.exe (PID: 5028)
- cmd.exe (PID: 5328)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 1108)
- cmd.exe (PID: 3476)
- cmd.exe (PID: 6732)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 2532)
- cmd.exe (PID: 5940)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 6100)
- cmd.exe (PID: 6552)
Drops a system driver (possible attempt to evade defenses)
- AAct_x64.exe (PID: 3104)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1436)
- cmd.exe (PID: 1568)
Starts application with an unusual extension
- AAct_x64.exe (PID: 3104)
Starts CMD.EXE for commands execution
- AAct_x64.exe (PID: 3104)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 5976)
- cmd.exe (PID: 5400)
Uses REG/REGEDIT.EXE to modify registry
- AAct_x64.exe (PID: 3104)
INFO
Manual execution by a user
- AAct_x64.exe (PID: 3104)
Checks operating system version
- AAct_x64.exe (PID: 3104)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
Total processes
334
Monitored processes
188
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "FakeClient.exe" 10.3.0.20 | C:\Users\admin\Desktop\AAct v3.9.2 Portable\wdvdriver\x64WDV\FakeClient.exe | — | AAct_x64.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 188 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ckms-domain | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 640 | "C:\WINDOWS\System32\cmd.exe" /c taskkill.exe /t /f /IM SppExtComObj.Exe | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\WINDOWS\System32\cmd.exe" /c cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ckms | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 992 | "C:\WINDOWS\System32\cmd.exe" /c cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /sdns | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | "C:\WINDOWS\System32\cmd.exe" /c route delete 10.3.0.20 0.0.0.0 | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 416
Read events
14 378
Write events
23
Delete events
15
Modification events
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AAct v3.9.2 Portable.7z | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
6
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3104 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\wdvdriver\x64WDV\FakeClient.exe | executable | |
MD5:6241A145A6BC3511E7690DCF107CEFD8 | SHA256:2218293E4442DEB06E398AA0357AEF54DF377B95E46B6ED79B48B65B666C9405 | |||
| 3104 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\wdvdriver\AAct.dll | executable | |
MD5:124BA791D8C28151ABCD27D3D81E820B | SHA256:AFD72E00B8B6021CBD104D2CDF59FD9B58D245205D4E72E5D8BD8D75B88CCE48 | |||
| 6252 | WinRAR.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\readme_en.txt | text | |
MD5:B0163044ADD8486D1391521F22D4AB72 | SHA256:208DC6DA14C1318F39B51007A9C5B04F8E662F4A23BFE2F298BFFA96E10C8806 | |||
| 6252 | WinRAR.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\readme_ru.txt | text | |
MD5:7A4215CE64B49A852F6D2363A71870F4 | SHA256:A740E813221FC76A6C62BFCB659B8EAC22F3E07F49BC1308B011E538E1CB41E2 | |||
| 6252 | WinRAR.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\AAct.exe | executable | |
MD5:A0C19C36BEC3AFBABF15FF2C6BA4D446 | SHA256:E571BAC47A48A72DC772D93F1889C4456D699EA9259A59210FA3F5CFFE666258 | |||
| 6252 | WinRAR.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\AAct_x64.exe | executable | |
MD5:A4BCE0AD5D3D676286F0C04661A0E690 | SHA256:C13A3F578026F8CF99A50D2DB5A02B1F09E7E5C38EAAF75C5859BFE03F6B4FB3 | |||
| 3104 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\wdvdriver\x64WDV\WinDivert.dll | executable | |
MD5:EE42F18F56E8AB20103D0EACC6CB3056 | SHA256:D0D8E5806952CE8F321D106551C680AFE5A074CB9366A54282FF83397C64C27F | |||
| 3104 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v3.9.2 Portable\wdvdriver\x64WDV\WinDivert64.sys | executable | |
MD5:D6F42128C81965E12578FECA7DAC500F | SHA256:9026147943BD44A1EB5E2F0C89CC8F441C7D1F13C1571ABA54E262D2E7354798 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
65
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6436 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2100 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2952 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.190.155.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2100 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2100 | svchost.exe | 20.190.155.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2868 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |