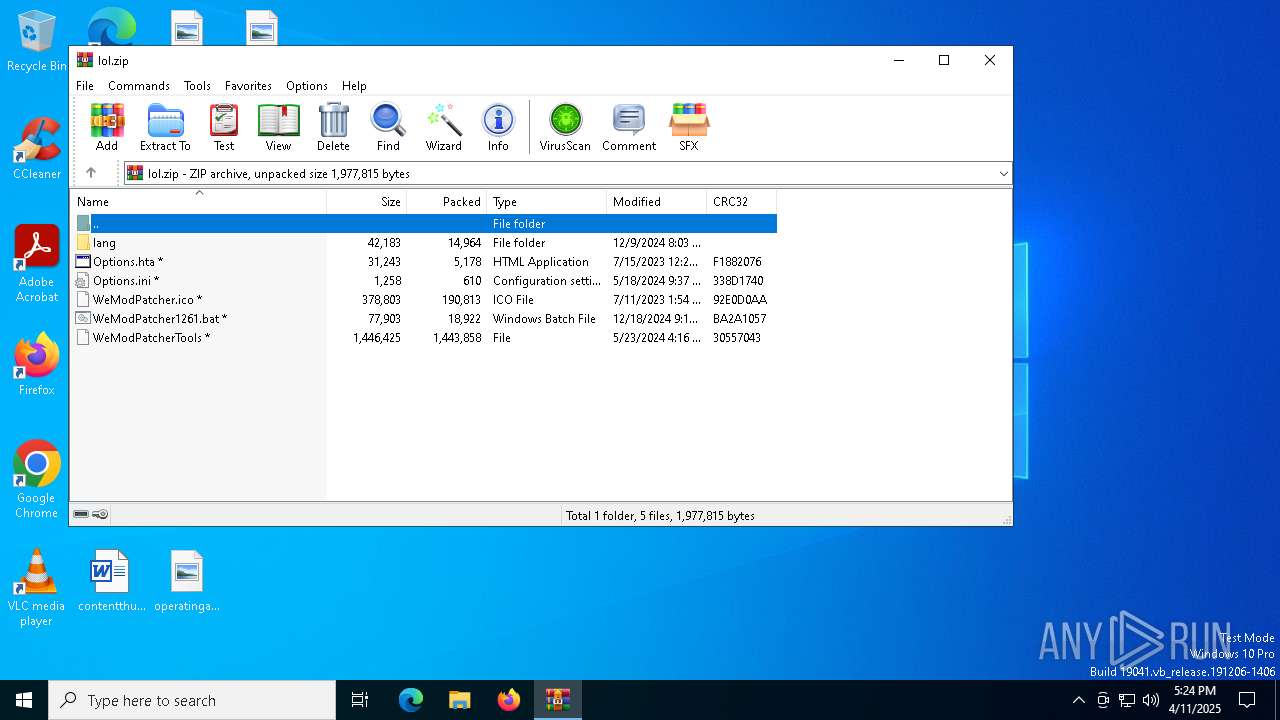
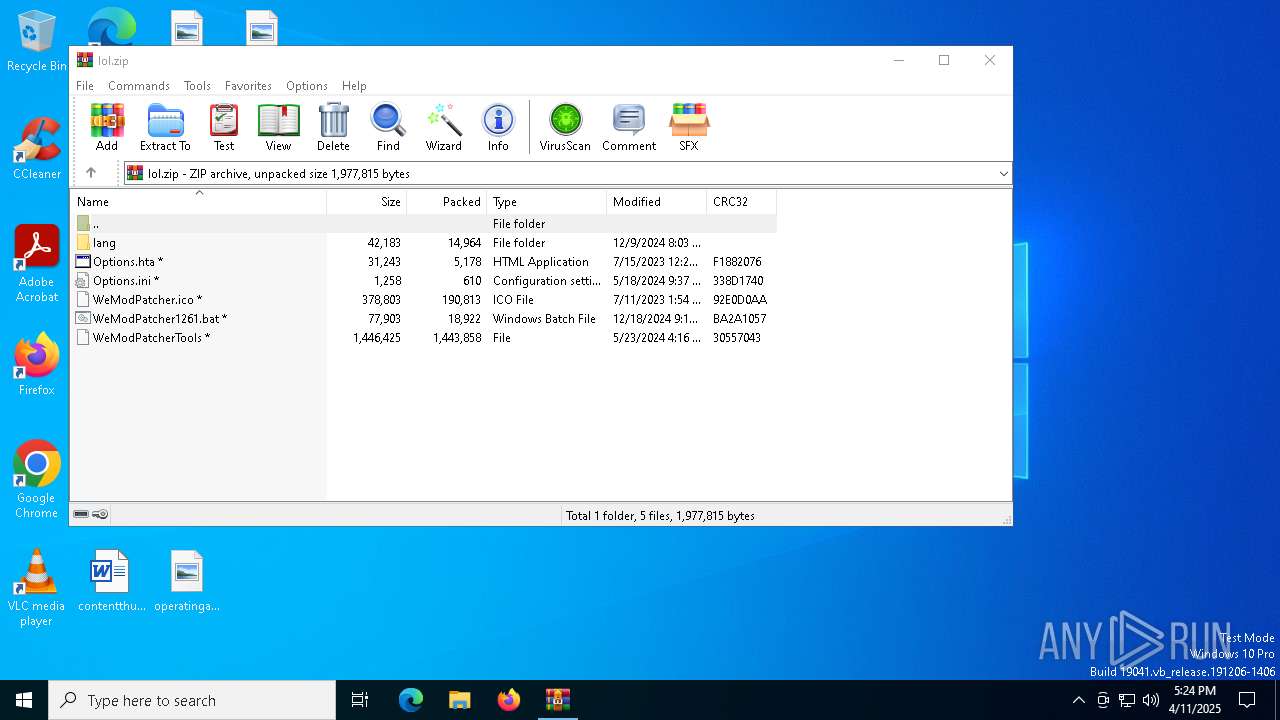
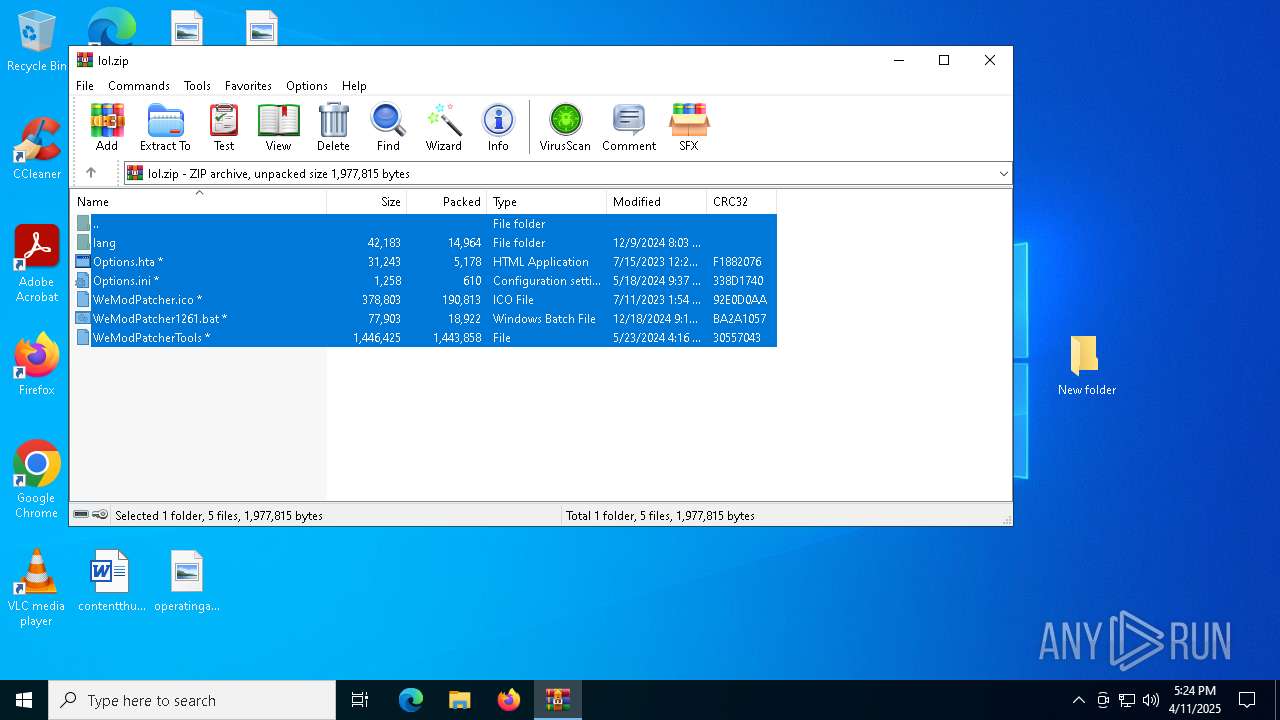
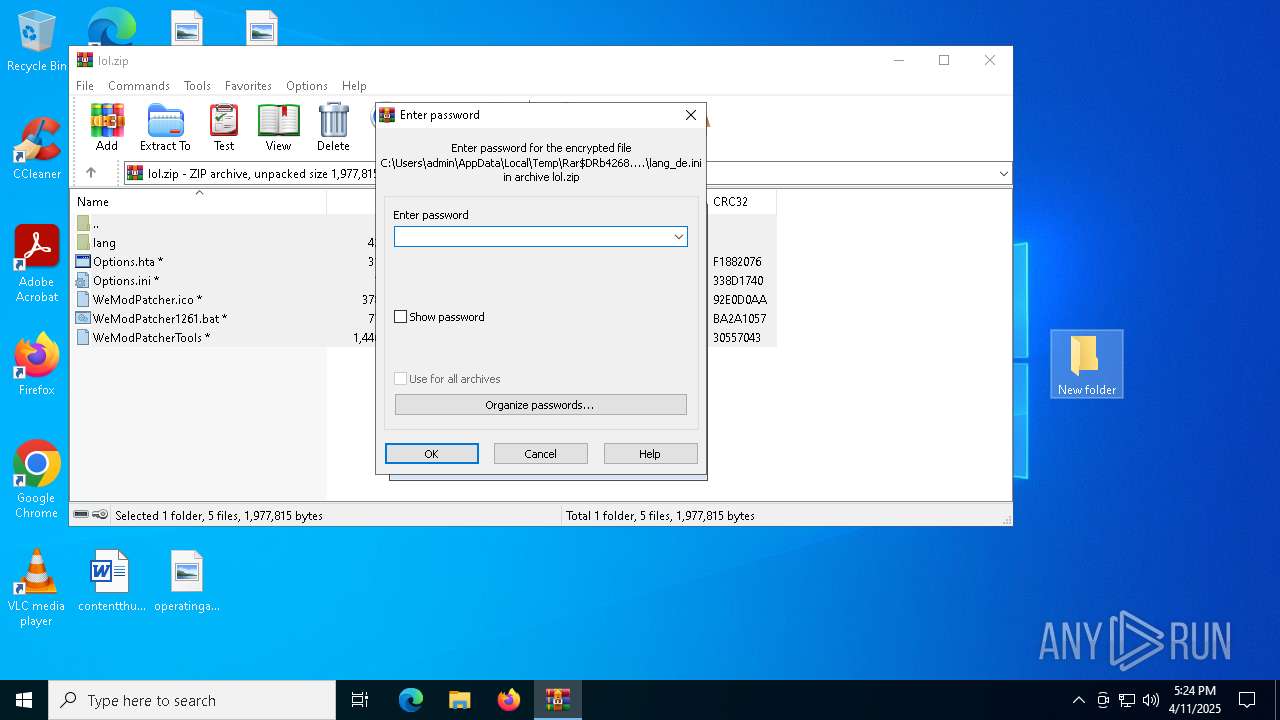
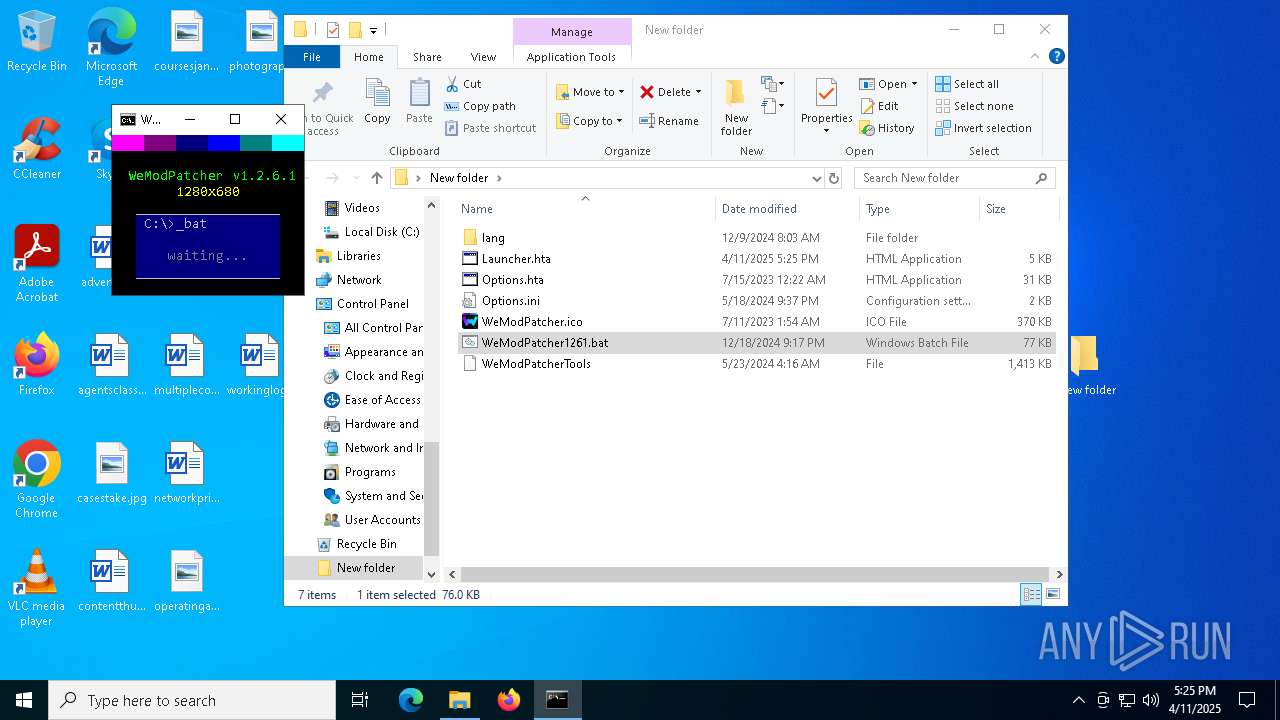
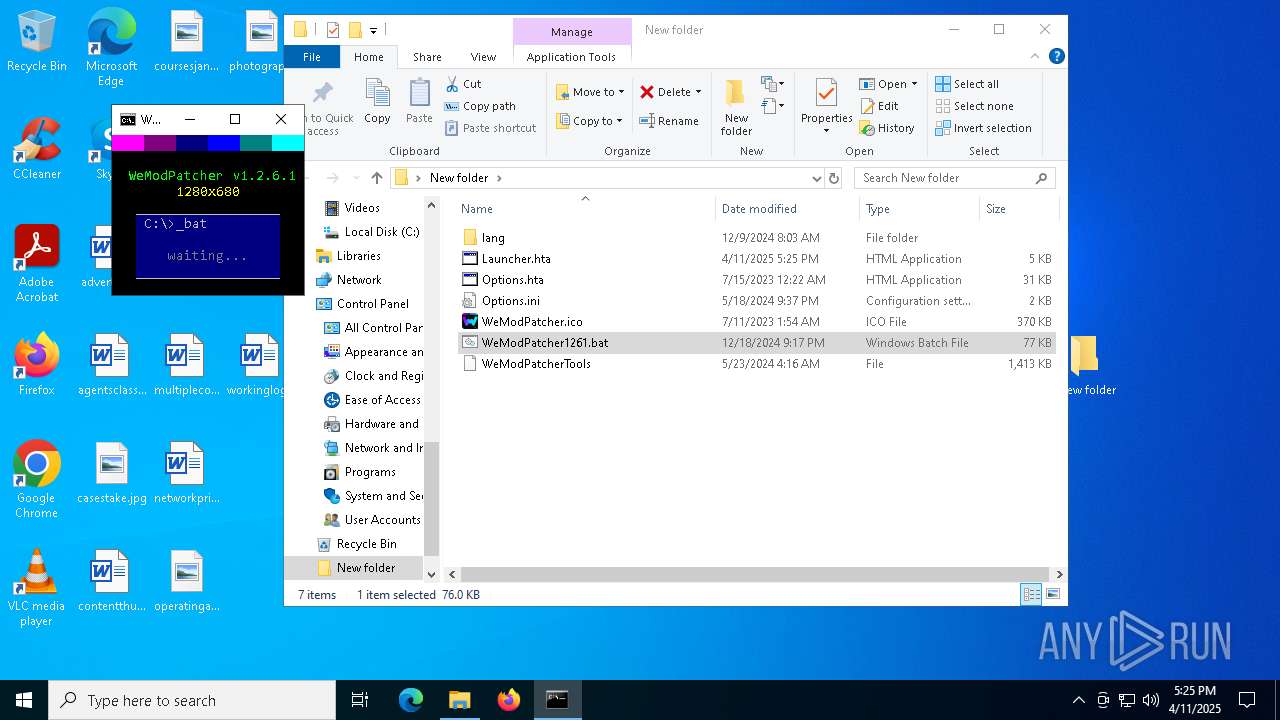
| File name: | lol.zip |
| Full analysis: | https://app.any.run/tasks/069c51a6-12f6-445b-90d3-350499f4c359 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2025, 17:24:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | C6AE19E2E21DE8605CE56E5C65B227A7 |
| SHA1: | 8CAC2EFC5F7CABA127177BA489765F54FF420D0D |
| SHA256: | 95BB4DDCE1D9E4F8F60F367530C60BCD6B6F7C31C8E7B81733E85BC43918588D |
| SSDEEP: | 49152:bxugY2K22xVXoBzieM3tQIzwU6Nd/l7e+cdXsz/Z6quS7ggA1u69utgnBlfD7lbQ:bYUyyB8zmNdNFdzZ6qAY8LfflTEk7FeV |
MALICIOUS
No malicious indicators.SUSPICIOUS
Execution of CURL command
- cmd.exe (PID: 7940)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 4268)
Application launched itself
- cmd.exe (PID: 7940)
Found IP address in command line
- powershell.exe (PID: 8084)
- powershell.exe (PID: 4068)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8068)
- cmd.exe (PID: 7940)
- cmd.exe (PID: 7224)
- cmd.exe (PID: 7200)
- cmd.exe (PID: 5728)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 7884)
- cmd.exe (PID: 4008)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 6640)
- cmd.exe (PID: 7512)
- cmd.exe (PID: 728)
- cmd.exe (PID: 5376)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 5720)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 5408)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 4728)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 7940)
- net.exe (PID: 8184)
Starts application with an unusual extension
- cmd.exe (PID: 7940)
- cmd.exe (PID: 4696)
Get information on the list of running processes
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7940)
- cmd.exe (PID: 7052)
- cmd.exe (PID: 5728)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7940)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 7264)
- mshta.exe (PID: 2136)
- mshta.exe (PID: 5344)
- mshta.exe (PID: 6852)
- mshta.exe (PID: 3364)
- mshta.exe (PID: 7708)
- mshta.exe (PID: 6540)
- mshta.exe (PID: 616)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 7548)
- mshta.exe (PID: 7336)
- mshta.exe (PID: 7916)
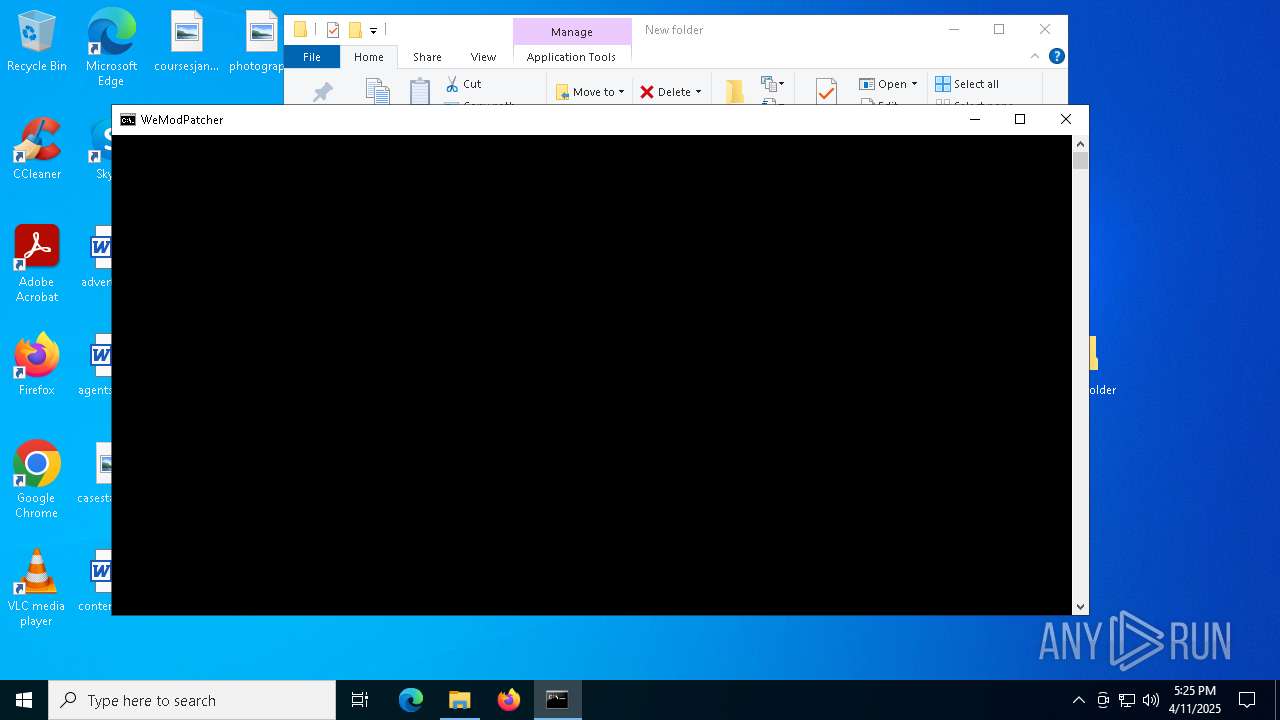
Executes application which crashes
- mshta.exe (PID: 7264)
- mshta.exe (PID: 2136)
- mshta.exe (PID: 6852)
- mshta.exe (PID: 5344)
- mshta.exe (PID: 3364)
- mshta.exe (PID: 7708)
- mshta.exe (PID: 6540)
- mshta.exe (PID: 616)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 7548)
- mshta.exe (PID: 7336)
- mshta.exe (PID: 7916)
The process creates files with name similar to system file names
- WerFault.exe (PID: 5508)
- WerFault.exe (PID: 7528)
- WerFault.exe (PID: 7348)
- WerFault.exe (PID: 864)
- WerFault.exe (PID: 8028)
- WerFault.exe (PID: 1240)
- WerFault.exe (PID: 7220)
- WerFault.exe (PID: 2600)
- WerFault.exe (PID: 7560)
- WerFault.exe (PID: 7628)
- WerFault.exe (PID: 6760)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4268)
Manual execution by a user
- cmd.exe (PID: 7940)
Execution of CURL command
- cmd.exe (PID: 8008)
Checks supported languages
- curl.exe (PID: 8024)
- chcp.com (PID: 6068)
- mode.com (PID: 7232)
- chcp.com (PID: 3896)
- chcp.com (PID: 8056)
- chcp.com (PID: 8040)
- chcp.com (PID: 6744)
- chcp.com (PID: 2064)
- chcp.com (PID: 6592)
- chcp.com (PID: 7956)
- chcp.com (PID: 7244)
- chcp.com (PID: 6640)
- chcp.com (PID: 7580)
- chcp.com (PID: 8024)
Reads the computer name
- curl.exe (PID: 8024)
Changes the display of characters in the console
- cmd.exe (PID: 7940)
- cmd.exe (PID: 4696)
Starts MODE.COM to configure console settings
- mode.com (PID: 7232)
Creates files or folders in the user directory
- WerFault.exe (PID: 5508)
- WerFault.exe (PID: 7348)
- WerFault.exe (PID: 7528)
- WerFault.exe (PID: 864)
- WerFault.exe (PID: 1240)
- WerFault.exe (PID: 2600)
- WerFault.exe (PID: 7220)
- WerFault.exe (PID: 7628)
- WerFault.exe (PID: 6760)
Reads Internet Explorer settings
- mshta.exe (PID: 5344)
- mshta.exe (PID: 2136)
- mshta.exe (PID: 6852)
- mshta.exe (PID: 6540)
- mshta.exe (PID: 7708)
- mshta.exe (PID: 616)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 7336)
- mshta.exe (PID: 7916)
Checks proxy server information
- mshta.exe (PID: 5344)
- mshta.exe (PID: 7264)
- mshta.exe (PID: 2136)
- mshta.exe (PID: 6852)
- mshta.exe (PID: 3364)
- mshta.exe (PID: 7708)
- mshta.exe (PID: 6540)
- mshta.exe (PID: 616)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 7336)
- mshta.exe (PID: 7548)
- mshta.exe (PID: 7916)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1240)
Reads the software policy settings
- slui.exe (PID: 7284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:09 05:03:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | lang/ |
Total processes
255
Monitored processes
112
Malicious processes
1
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
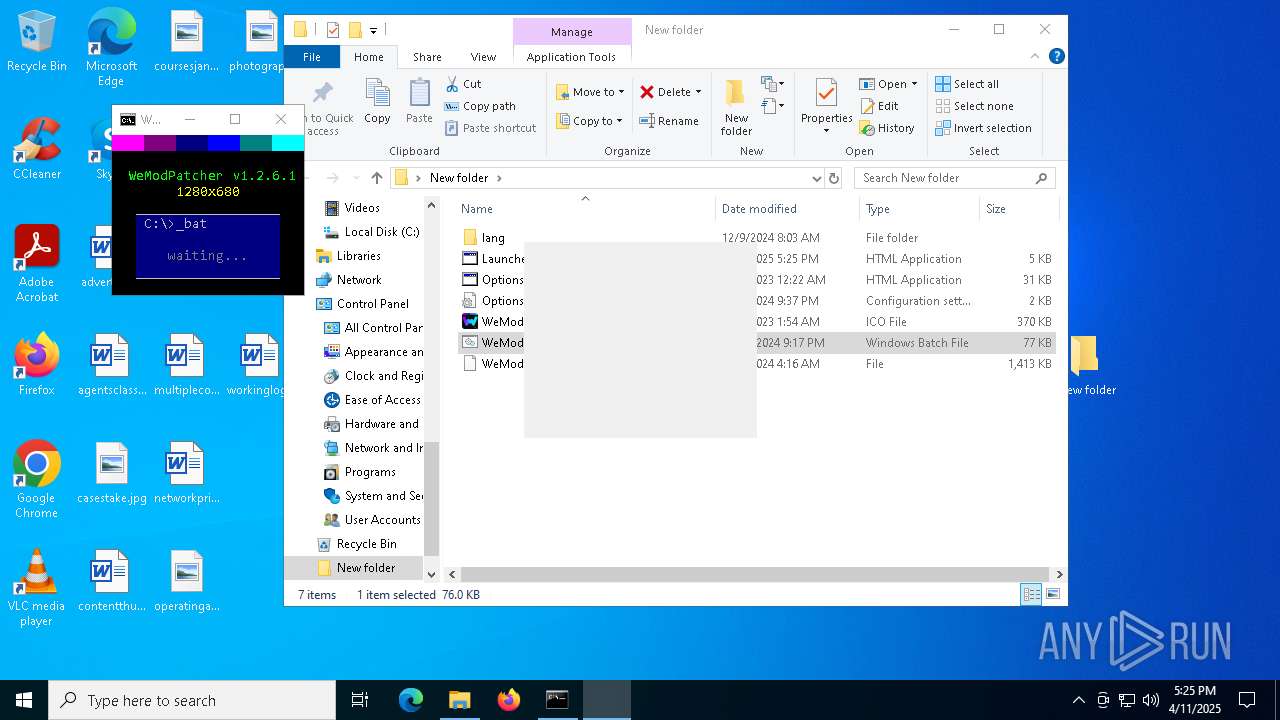
| 616 | mshta.exe "C:\Users\admin\Desktop\New folder\Launcher.hta" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225477 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | powershell -Command "(Get-FileHash Options.ini -Algorithm MD5).Hash" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\cmd.exe /c powershell -Command "(Get-FileHash Options.ini -Algorithm MD5).Hash" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | C:\WINDOWS\system32\WerFault.exe -u -p 3364 -s 1932 | C:\Windows\System32\WerFault.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | powershell -Command "[console]::title='WeModPatcher'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | powershell -Command "[math]::Round((24 - '1280x680'.length) / 2)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | C:\WINDOWS\system32\WerFault.exe -u -p 6852 -s 1948 | C:\Windows\System32\WerFault.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | reg query "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Themes\Personalize" /V "AppsUseLightTheme" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | C:\WINDOWS\system32\cmd.exe /c mshta.exe "C:\Users\admin\Desktop\New folder\Launcher.hta" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225477 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | tasklist /NH /FI "WindowTitle eq "WeModPatcher"" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
128 383
Read events
128 364
Write events
19
Delete events
0
Modification events
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\lol.zip | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4268) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
0
Suspicious files
34
Text files
70
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4268.10480\lang\lang_pt.ini | text | |
MD5:98D8CB666E73522D7478520D685183CC | SHA256:E56FB42EA5361EDF06D352ADCB3C46CD2A675C59D455B2FAF7D14727ACA1ADE3 | |||
| 4268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4268.10480\lang\lang_de.ini | text | |
MD5:56F718D833D85B64D368A746CEC7D311 | SHA256:9296A56AE3F33183E5DD78159EEDC14E7C55D58B6FF984D30480927F3491A0A6 | |||
| 4268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4268.10480\lang\lang_en.ini | text | |
MD5:DA7F78CEA561177B4593E43E472B8A61 | SHA256:5CE043FA53863E2FC94E42D72D870DA746D94CA5CDBC1E1F6FBD364681D69F26 | |||
| 8084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5zgj5vae.qfu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8084 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:5CF8802F273AA9BC372F4C382FBD2DA3 | SHA256:68C9CBFCE985C72E09518765FD1D6F7D150465A807E3C449CCA4C63D58E31F59 | |||
| 1196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_had15wuk.qpn.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8084 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rwowjejg.i3r.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
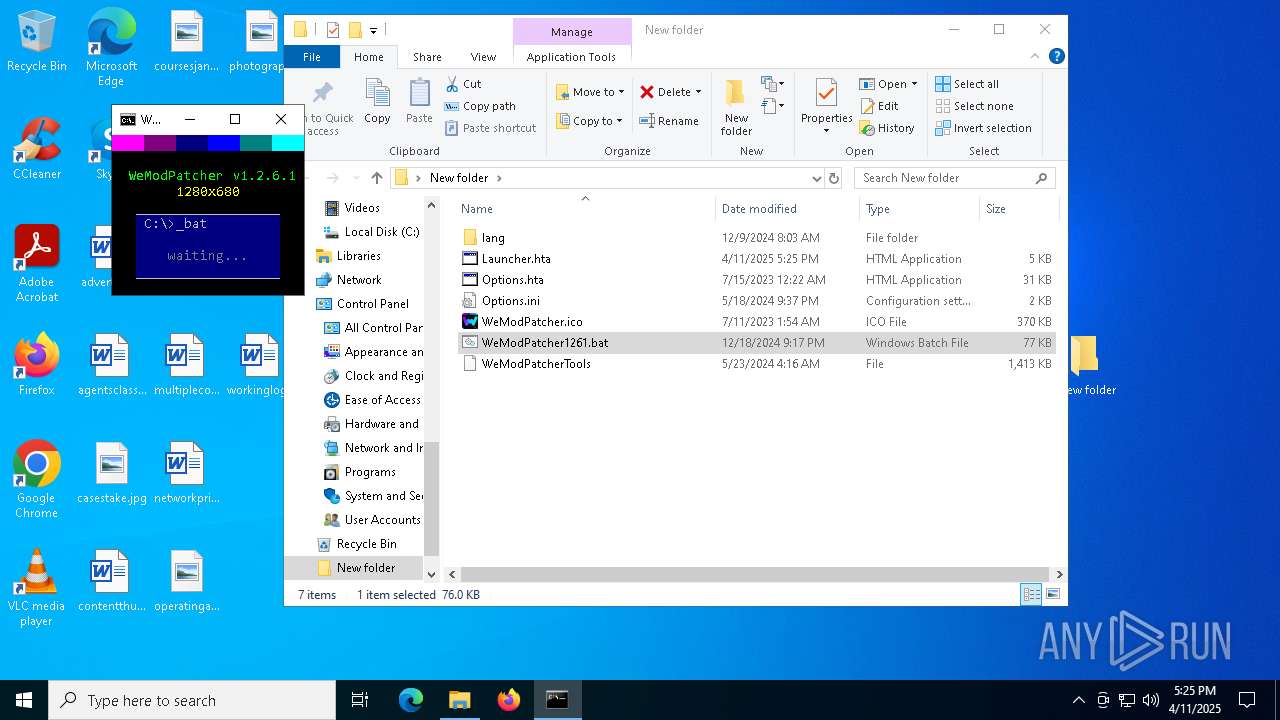
| 4268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4268.10480\WeModPatcher.ico | image | |
MD5:CCB4F0739B87DF9D7C9D0BEF63014E53 | SHA256:1F7DDFDA33CC1FF03F897AACAEDFB33A97B6430811089B96C136F362E90073F6 | |||
| 4268 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4268.10480\WeModPatcherTools | compressed | |
MD5:7D2DBEC2395D4CF262EAF10C9B944F4C | SHA256:43F2B4E8D63A62055E8A2CDF80C8809ED6A9FE1574141A9083CA998B65C7E082 | |||
| 7940 | cmd.exe | C:\Users\admin\Desktop\New folder\IsAdminNecessary | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
22
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7764 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
7764 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5588 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |