| File name: | Drivers_Installer.exe |
| Full analysis: | https://app.any.run/tasks/8356be94-90f0-46ad-858e-6889d98255d2 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 13:47:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 9B0F1B13E99B9C975515C7AFC2AE7E8A |
| SHA1: | 4FFFAF7BC4E3E063DD4B7A91C3D28D9F195658B9 |
| SHA256: | 959BD69C62C25FBB21B009C4F22764DAC5893E1492FE08BD4D4869B7F623AA88 |
| SSDEEP: | 49152:CGCI+nJW6xorYxTCNCdX7mjqJ33/qsXaa5ybHnJcF:DCI+wAorncrmjo33/naa5ybHnJ |
MALICIOUS
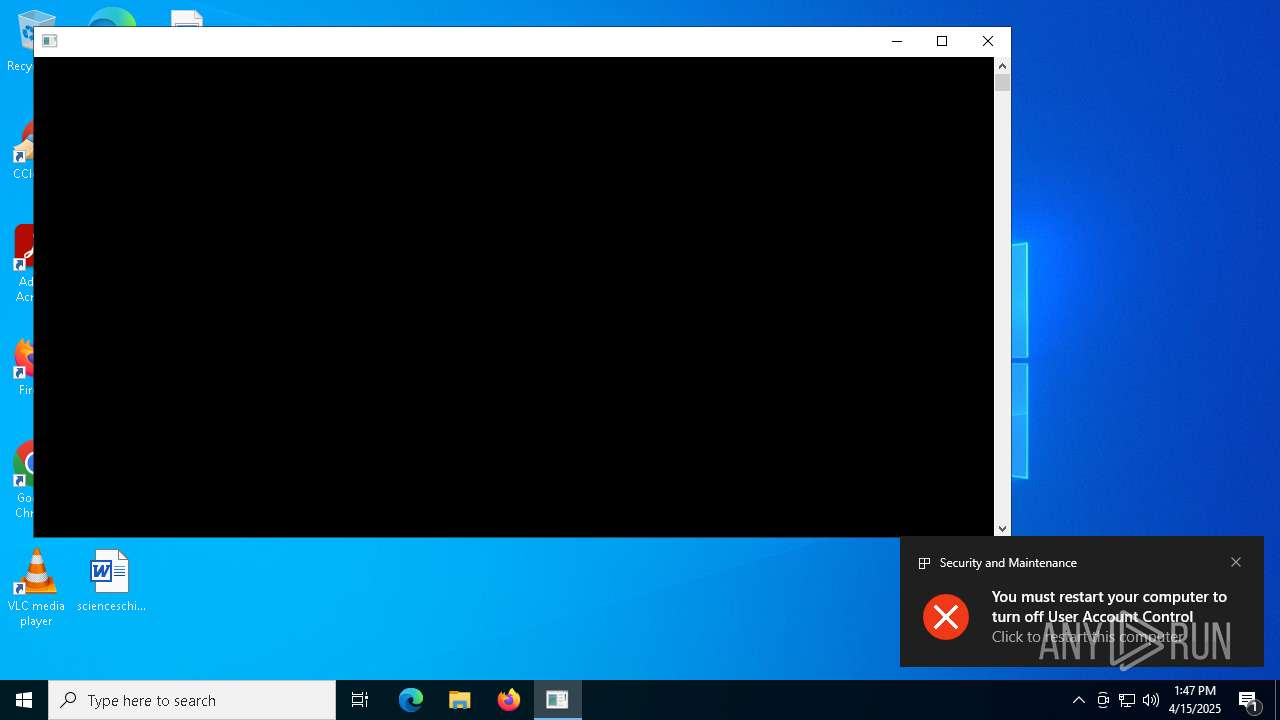
UAC/LUA settings modification
- reg.exe (PID: 8056)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Drivers_Installer.exe (PID: 7408)
Creates file in the systems drive root
- Drivers_Installer.exe (PID: 7408)
- msiexec.exe (PID: 7516)
- msiexec.exe (PID: 7552)
- cmd.exe (PID: 4976)
- Driver.exe (PID: 5048)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7552)
Executable content was dropped or overwritten
- Drivers_Installer.exe (PID: 7408)
- drvinst.exe (PID: 7828)
- Driver.exe (PID: 5048)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7552)
- drvinst.exe (PID: 7828)
- Driver.exe (PID: 5048)
Creates files in the driver directory
- drvinst.exe (PID: 7828)
- Driver.exe (PID: 5048)
- devcon.exe (PID: 7720)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8040)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 8172)
Creates or modifies Windows services
- Driver.exe (PID: 5048)
- drvinst.exe (PID: 7888)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4172)
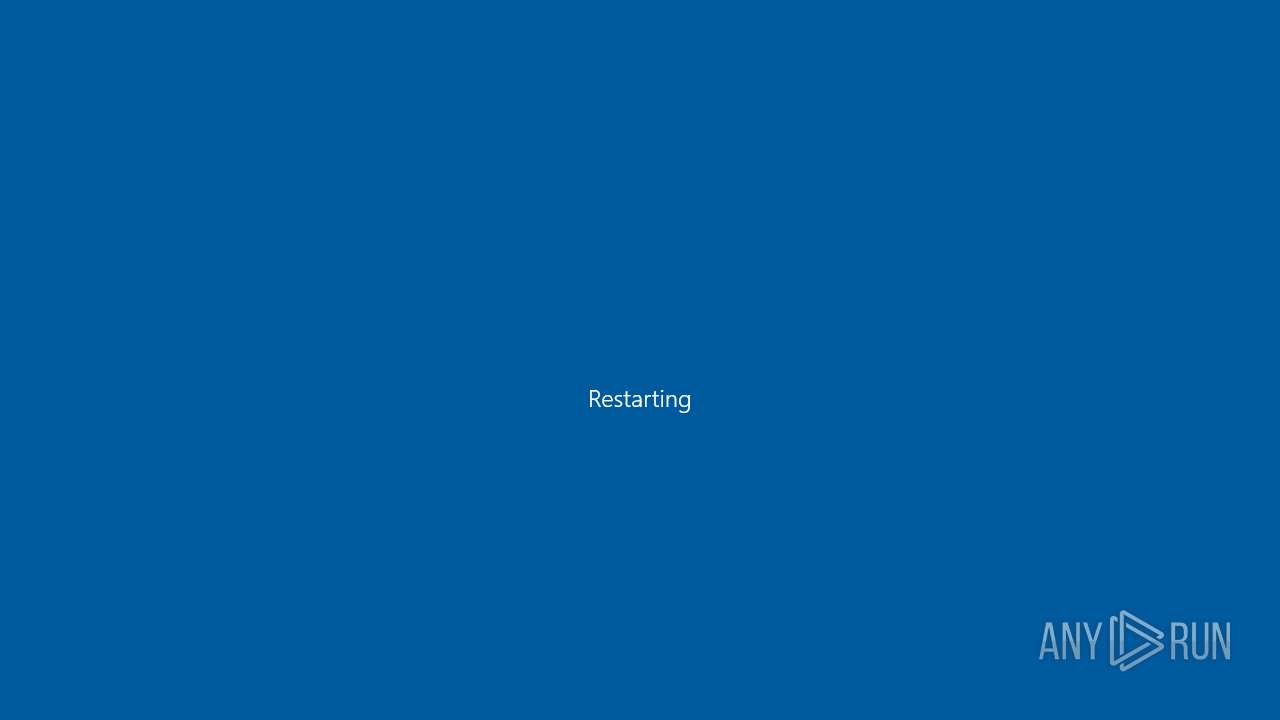
The system shut down or reboot
- cmd.exe (PID: 2692)
INFO
Checks supported languages
- Drivers_Installer.exe (PID: 7408)
- msiexec.exe (PID: 7552)
- devcon.exe (PID: 7720)
- drvinst.exe (PID: 7828)
- msiexec.exe (PID: 7684)
- ShellExperienceHost.exe (PID: 8172)
- Driver.exe (PID: 5048)
- drvinst.exe (PID: 7888)
- PLUGScheduler.exe (PID: 4172)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7552)
- devcon.exe (PID: 7720)
- drvinst.exe (PID: 7828)
The sample compiled with english language support
- Drivers_Installer.exe (PID: 7408)
- msiexec.exe (PID: 7552)
- drvinst.exe (PID: 7828)
- Driver.exe (PID: 5048)
Reads the computer name
- msiexec.exe (PID: 7552)
- devcon.exe (PID: 7720)
- msiexec.exe (PID: 7684)
- ShellExperienceHost.exe (PID: 8172)
- drvinst.exe (PID: 7828)
- drvinst.exe (PID: 7888)
- Drivers_Installer.exe (PID: 7408)
Creates files or folders in the user directory
- msiexec.exe (PID: 7552)
Reads the software policy settings
- msiexec.exe (PID: 7552)
- devcon.exe (PID: 7720)
- drvinst.exe (PID: 7828)
Creates a software uninstall entry
- msiexec.exe (PID: 7552)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7552)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:01:24 15:13:00+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 25088 |
| InitializedDataSize: | 1367040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x60c8 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
276
Monitored processes
22
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2692 | C:\WINDOWS\system32\cmd.exe /c shutdown /r /t 0 | C:\Windows\System32\cmd.exe | — | Drivers_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4172 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | C:\WINDOWS\system32\cmd.exe /c "C:\Driver.exe" /install | C:\Windows\System32\cmd.exe | — | Drivers_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | C:\Driver.exe /install | C:\Driver.exe | cmd.exe | ||||||||||||
User: admin Company: Francisco Lopes Integrity Level: HIGH Description: Interception command line installation tool Exit code: 0 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 5344 | shutdown /r /t 0 | C:\Windows\System32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Drivers_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7304 | "C:\Users\admin\Desktop\Drivers_Installer.exe" | C:\Users\admin\Desktop\Drivers_Installer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7408 | "C:\Users\admin\Desktop\Drivers_Installer.exe" | C:\Users\admin\Desktop\Drivers_Installer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 7420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Drivers_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7476 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | Drivers_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 260
Read events
12 133
Write events
111
Delete events
16
Modification events
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10de00.rbs |
Value: 31174156 | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10de00.rbsLow |
Value: | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Nefarius Software Solutions e.U.\ViGEm Bus Driver |
| Operation: | write | Name: | Version |
Value: 1.17.333.0 | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\WINDOWS\Installer\{93D91F60-7C94-4A79-863F-EA713D2EB3F3}\ |
Value: | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\06F19D3949C797A468F3AE17D3E23B3F\Patches |
| Operation: | write | Name: | AllPatches |
Value: | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\06F19D3949C797A468F3AE17D3E23B3F |
| Operation: | write | Name: | ProductName |
Value: Nefarius Virtual Gamepad Emulation Bus Driver | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\06F19D3949C797A468F3AE17D3E23B3F |
| Operation: | write | Name: | PackageCode |
Value: 0009B4F754538334F9B3C4D0AA2552EE | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\06F19D3949C797A468F3AE17D3E23B3F |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (7552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Installer\Products\06F19D3949C797A468F3AE17D3E23B3F |
| Operation: | write | Name: | Version |
Value: 17891661 | |||
Executable files
12
Suspicious files
71
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7552 | msiexec.exe | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\ViGEmBus.cat | binary | |
MD5:5312064607460BAAA4562AABC42B8922 | SHA256:58B8A1BF9160FD4310A183B3431580EDA2BC0A5ECAAC2E0FBD6399184FF02404 | |||
| 7552 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:93FAD1B304EB8445C23CFC4018544975 | SHA256:1284736C3C0600DBD88B5A1A3C7C704FD91CBFA68BF061EBD1B4D8220524844E | |||
| 7552 | msiexec.exe | C:\Windows\Installer\MSIE63C.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 7552 | msiexec.exe | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\LICENSE | text | |
MD5:D664B47A302868C10AE2C10CC3BF38D4 | SHA256:A54034B06DBFB9E8F33D17ED815486786561D8AF7368964ADD429CA7396E82FA | |||
| 7552 | msiexec.exe | C:\Windows\Temp\~DF752439B49308771D.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 7552 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DA3B6E45325D5FFF28CF6BAD6065C907_9680AC525D270E357A3E938724263431 | binary | |
MD5:8686CEA461A44B93F9420279E9BF58F8 | SHA256:B3BD05B574D88AD1F2C67B5900C6C995600327FA2957D5BD75DC902A69E05347 | |||
| 7552 | msiexec.exe | C:\Windows\Temp\~DFDDB9B4F9DE98564D.TMP | binary | |
MD5:93FAD1B304EB8445C23CFC4018544975 | SHA256:1284736C3C0600DBD88B5A1A3C7C704FD91CBFA68BF061EBD1B4D8220524844E | |||
| 7552 | msiexec.exe | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\ViGEmBus.sys | executable | |
MD5:87FE350C6FFE8D60CE58DBC16A2D091E | SHA256:8FB8402B7266FA9B9EA8841708317C8C25367B2947EEDA9B6462C0E4801F05A4 | |||
| 7552 | msiexec.exe | C:\Program Files\Nefarius Software Solutions\Virtual Gamepad Emulation Bus Driver\ViGEmBus.inf | binary | |
MD5:CD0027AA0F5A8A47A6596D880F06964B | SHA256:634B032A33CECBF2E43C46C5896A3C359CDDA452C632DA6396452419FFA301D6 | |||
| 7552 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | binary | |
MD5:7AD62786274C3E303D9FCBE72431BCB8 | SHA256:DED53CF41E270534F68F39C45851F64FA0069F5251B4FEFC71EC71ACE256A044 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
220
TCP/UDP connections
83
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7552 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | whitelisted |
7552 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAbleKgbyY4oq3sFsZHJmi0%3D | unknown | — | — | whitelisted |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.129:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7552 | msiexec.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7916 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |