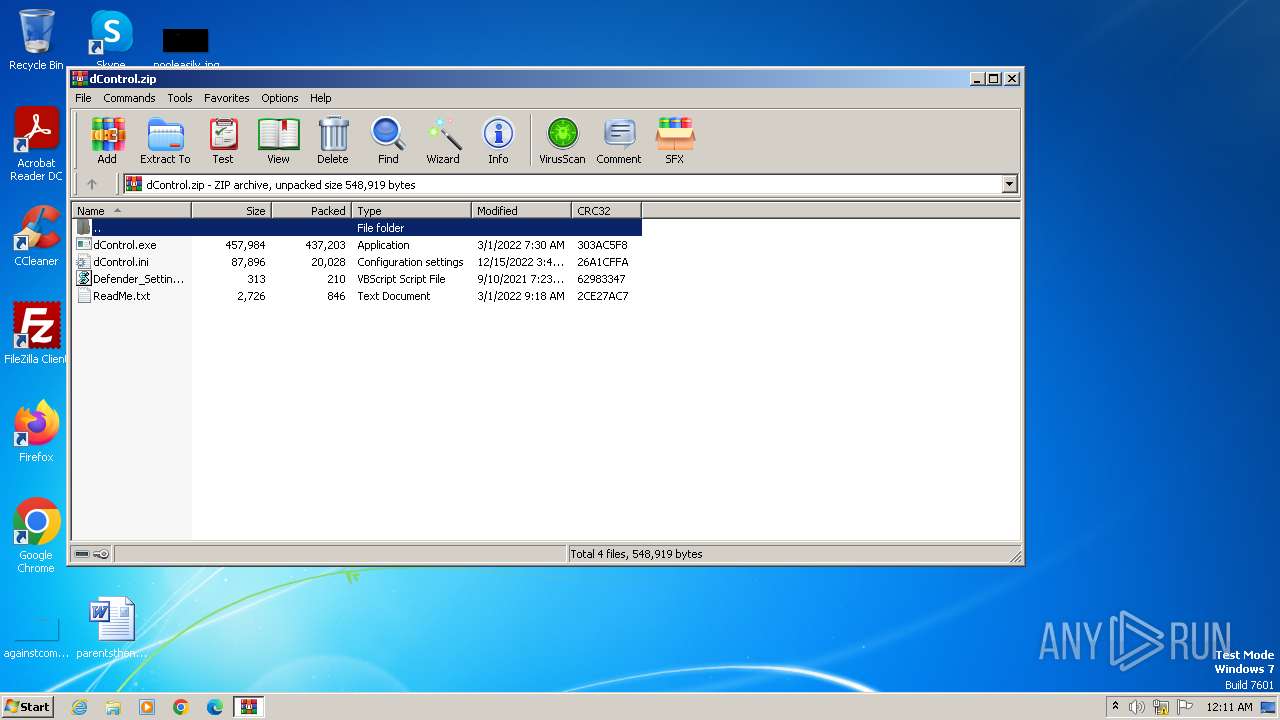
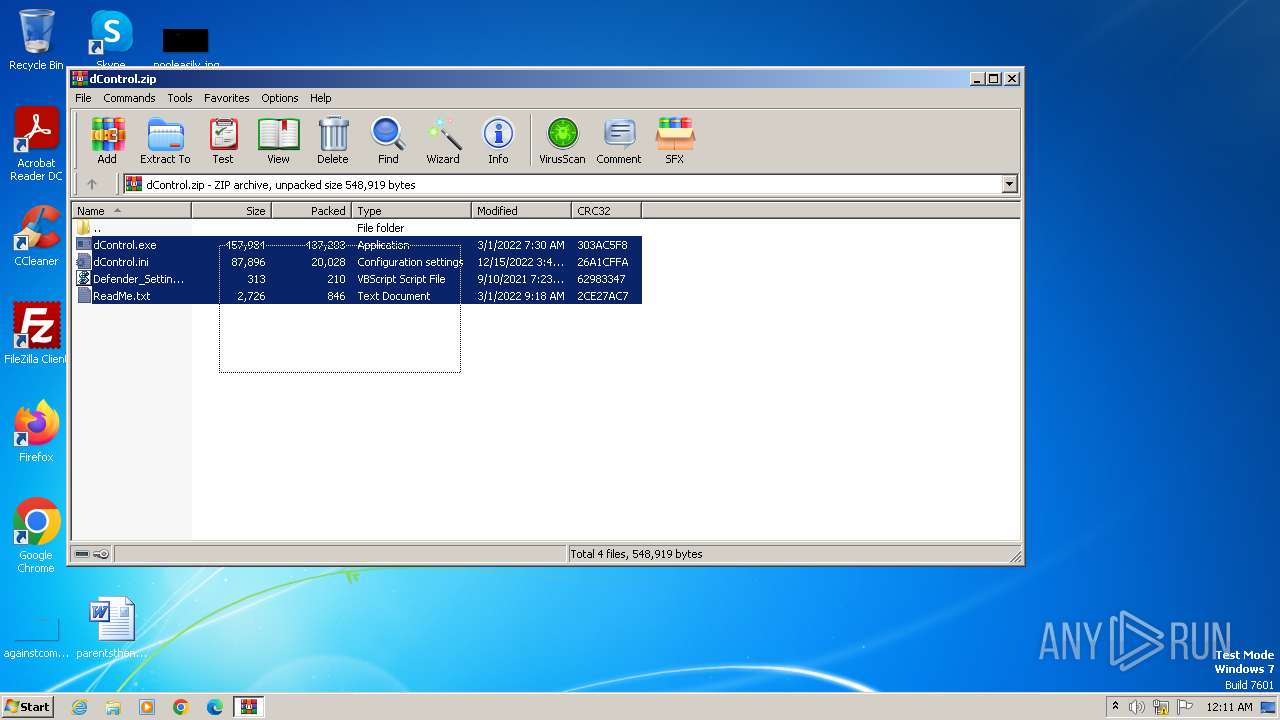
| File name: | dControl.zip |
| Full analysis: | https://app.any.run/tasks/42477246-a092-41f8-b68e-cf8362dfc1c6 |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2024, 23:10:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B5EFFFA70593F266A19762292160A9A5 |
| SHA1: | 7B494F7AD517ADF6AB2E5204FCEC65A9719866A1 |
| SHA256: | 959327D037F4402440854882E8C02ABBA0AA9F0A6494D079DA6D7D03E7E41E37 |
| SSDEEP: | 24576:AG4o5PnbV5ssrMGcJnPJYAOF6gDYwFGy8Tq3aLTMJC:n4o5PnbV5trMGcJnPJaF6gDYwFGy8Tqy |
MALICIOUS
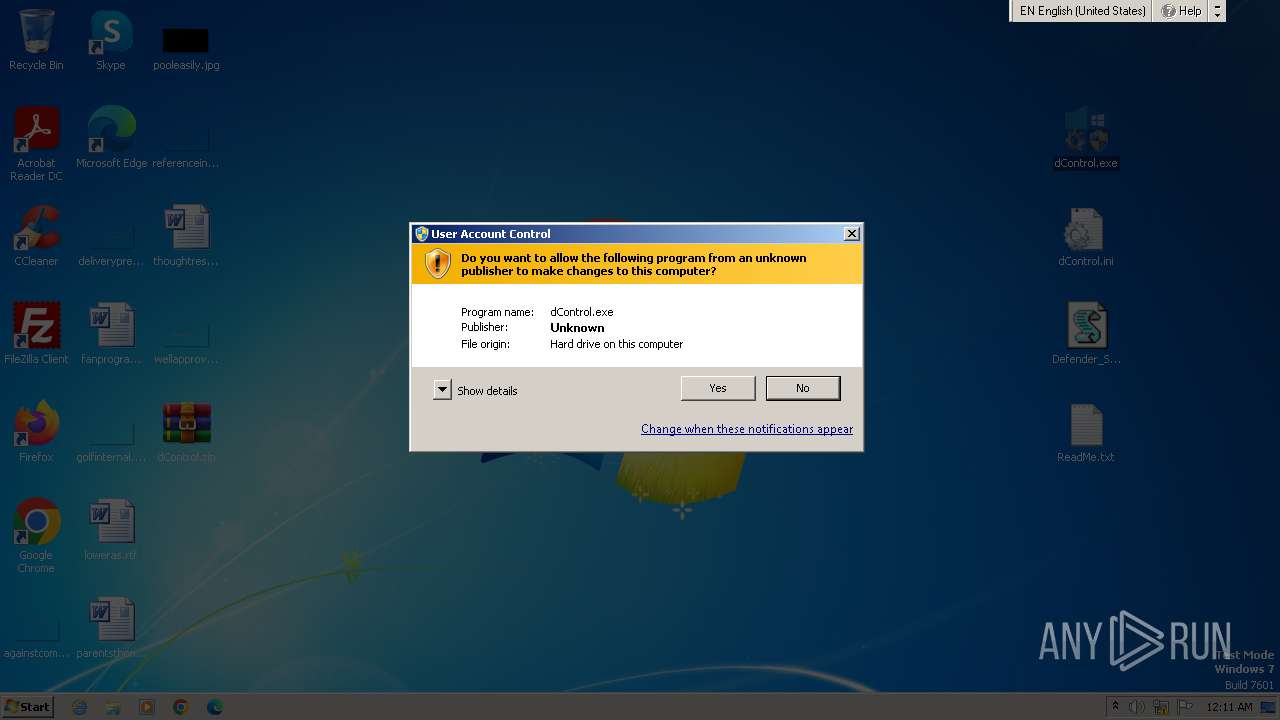
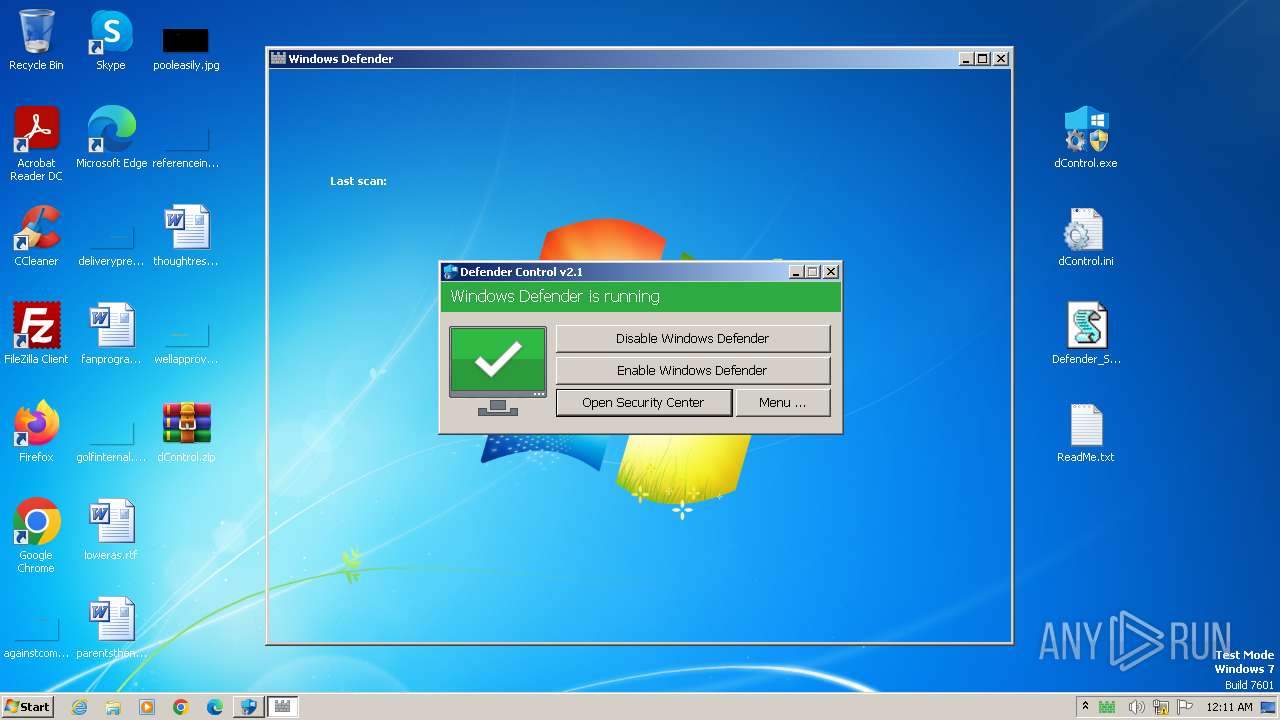
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3976)
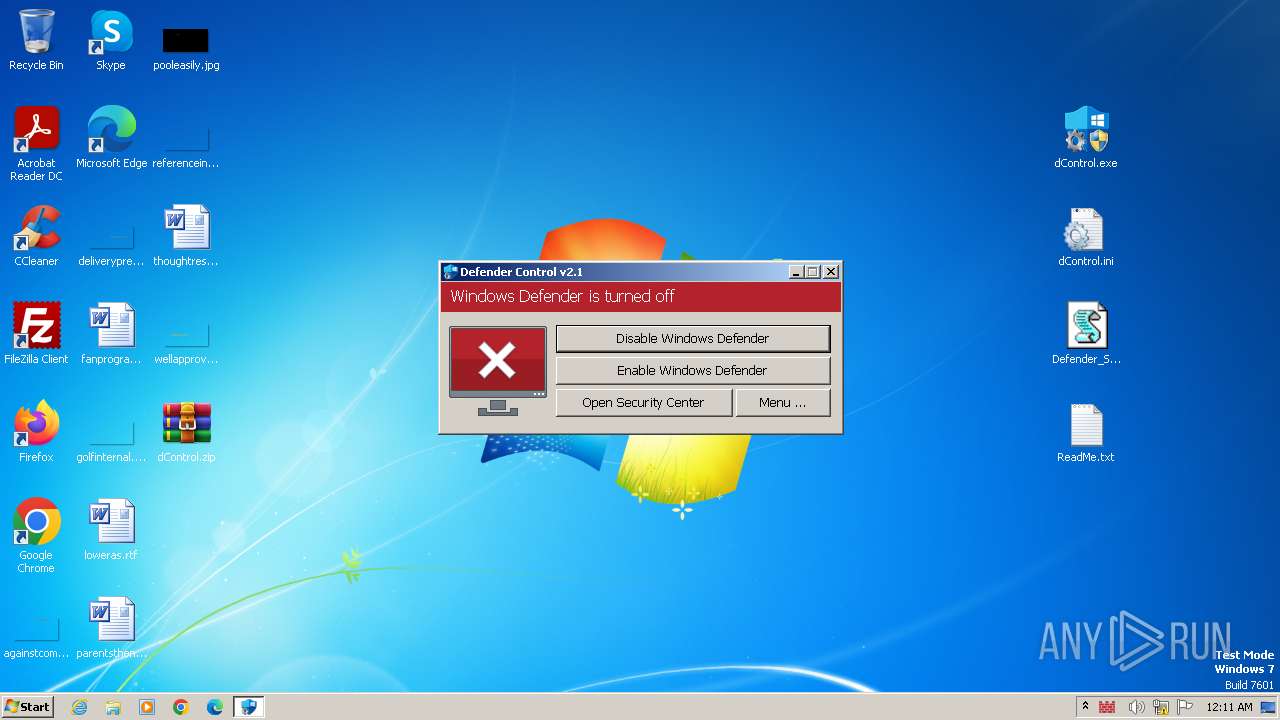
Creates or modifies Windows services
- dControl.exe (PID: 1944)
SUSPICIOUS
Application launched itself
- dControl.exe (PID: 1660)
- dControl.exe (PID: 1704)
- dControl.exe (PID: 1944)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 1936)
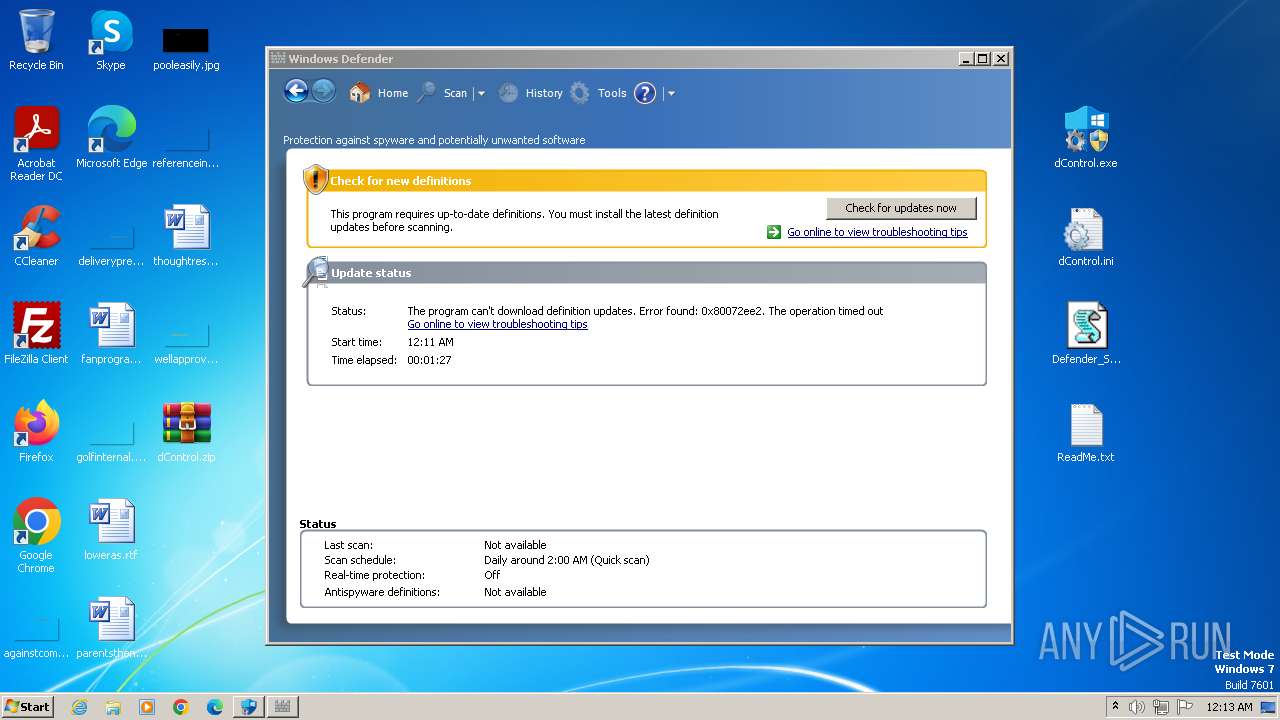
Reads the Internet Settings
- MSASCui.exe (PID: 2464)
Reads settings of System Certificates
- MSASCui.exe (PID: 2464)
INFO
Reads mouse settings
- dControl.exe (PID: 1660)
- dControl.exe (PID: 1704)
- dControl.exe (PID: 2336)
- dControl.exe (PID: 1944)
Checks supported languages
- dControl.exe (PID: 1660)
- dControl.exe (PID: 1704)
- dControl.exe (PID: 1944)
- dControl.exe (PID: 2336)
- wmpnscfg.exe (PID: 2076)
- MSASCui.exe (PID: 2464)
Reads the computer name
- dControl.exe (PID: 1660)
- dControl.exe (PID: 1704)
- dControl.exe (PID: 2336)
- dControl.exe (PID: 1944)
- wmpnscfg.exe (PID: 2076)
- MSASCui.exe (PID: 2464)
Reads the Internet Settings
- explorer.exe (PID: 2520)
Create files in a temporary directory
- dControl.exe (PID: 1660)
- MSASCui.exe (PID: 2464)
Manual execution by a user
- dControl.exe (PID: 1660)
- dControl.exe (PID: 820)
- wmpnscfg.exe (PID: 2076)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3976)
Reads the software policy settings
- MSASCui.exe (PID: 2464)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2520)
Reads the machine GUID from the registry
- MSASCui.exe (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:03:01 07:30:28 |
| ZipCRC: | 0x303ac5f8 |
| ZipCompressedSize: | 437203 |
| ZipUncompressedSize: | 457984 |
| ZipFileName: | dControl.exe |
Total processes
53
Monitored processes
10
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 820 | "C:\Users\admin\Desktop\dControl.exe" | C:\Users\admin\Desktop\dControl.exe | — | explorer.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: dControl v2.1 Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\dControl.exe" | C:\Users\admin\Desktop\dControl.exe | explorer.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1704 | C:\Users\admin\Desktop\dControl.exe | C:\Users\admin\Desktop\dControl.exe | dControl.exe | ||||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1936 | "C:\Windows\Explorer.exe" C:\Program Files\Windows Defender\MSASCui.exe | C:\Windows\explorer.exe | — | dControl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1944 | "C:\Users\admin\Desktop\dControl.exe" /TI | C:\Users\admin\Desktop\dControl.exe | — | dControl.exe | |||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2076 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | "C:\Users\admin\Desktop\dControl.exe" /EXP |1180| | C:\Users\admin\Desktop\dControl.exe | — | dControl.exe | |||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Windows Defender\MSASCui.exe" | C:\Program Files\Windows Defender\MSASCui.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender User Interface Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3976 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\dControl.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 407
Read events
7 344
Write events
53
Delete events
10
Modification events
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\dControl.zip | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
13
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1944 | dControl.exe | C:\Windows\TEMP\aut8EB5.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 1660 | dControl.exe | C:\Users\admin\AppData\Local\Temp\1f6k6m0j.tmp | text | |
MD5:E00DCC76E4DCD90994587375125DE04B | SHA256:C8709F5A8B971D136E2273D66E65449791CA8EBA1F47DD767733EA52EE635447 | |||
| 1944 | dControl.exe | C:\Windows\TEMP\aut8F71.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 2464 | MSASCui.exe | C:\Users\admin\AppData\Local\Temp\mpam-3824cc73.exe | — | |
MD5:— | SHA256:— | |||
| 1660 | dControl.exe | C:\Users\admin\AppData\Local\Temp\aut8B4B.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 1944 | dControl.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:4B0E38B7CCE439EFE81ACB36067F2526 | SHA256:E61D108D9280352A654E1BBAE11EA1F3132735F2C71BFFC414C4A6B7B3171DC4 | |||
| 1704 | dControl.exe | C:\Windows\TEMP\aut8D40.tmp | binary | |
MD5:ECFFD3E81C5F2E3C62BCDC122442B5F2 | SHA256:9874AB363B07DCC7E9CD6022A380A64102C1814343642295239A9F120CB941C5 | |||
| 1660 | dControl.exe | C:\Users\admin\AppData\Local\Temp\aut8B2B.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 1704 | dControl.exe | C:\Windows\TEMP\aut8D2F.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 1704 | dControl.exe | C:\Windows\TEMP\aut8D1F.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2464 | MSASCui.exe | GET | 302 | 23.38.86.151:80 | http://go.microsoft.com/fwlink/?LinkID=121721&clcid=0x409&arch=x86&eng=0.0.0.0&asdelta=0.0.0.0&prod=925A3ACA-C353-458A-AC8D-A7E5EB378092 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2464 | MSASCui.exe | 23.38.86.151:80 | go.microsoft.com | AKAMAI-AS | US | unknown |
2464 | MSASCui.exe | 23.203.17.160:443 | www.microsoft.com | AKAMAI-AS | US | unknown |
2464 | MSASCui.exe | 23.206.124.214:443 | definitionupdates.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
definitionupdates.microsoft.com |
| whitelisted |