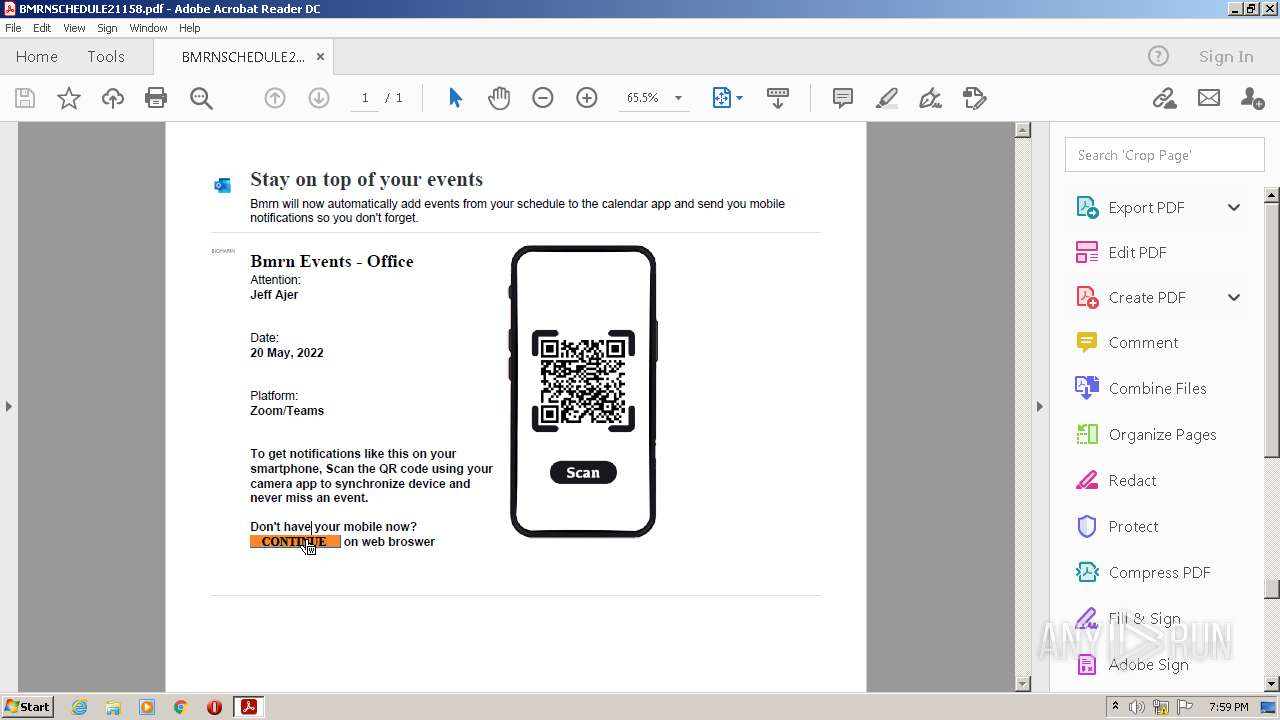
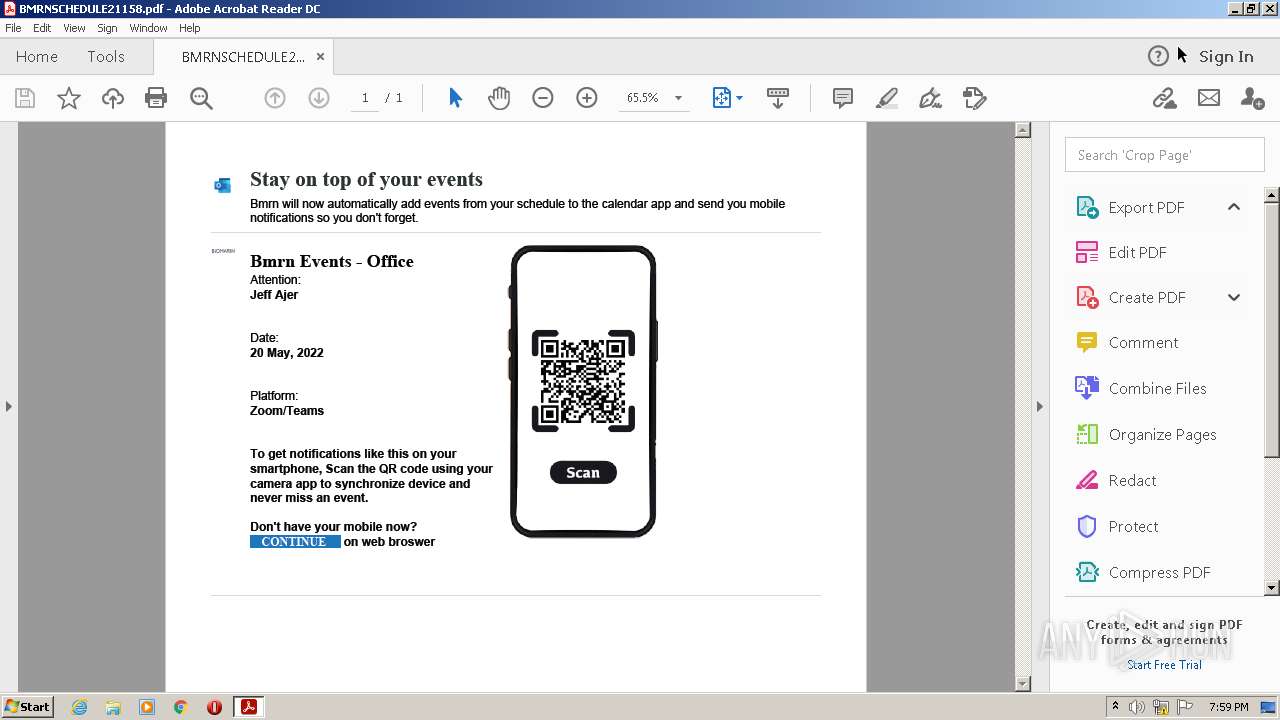
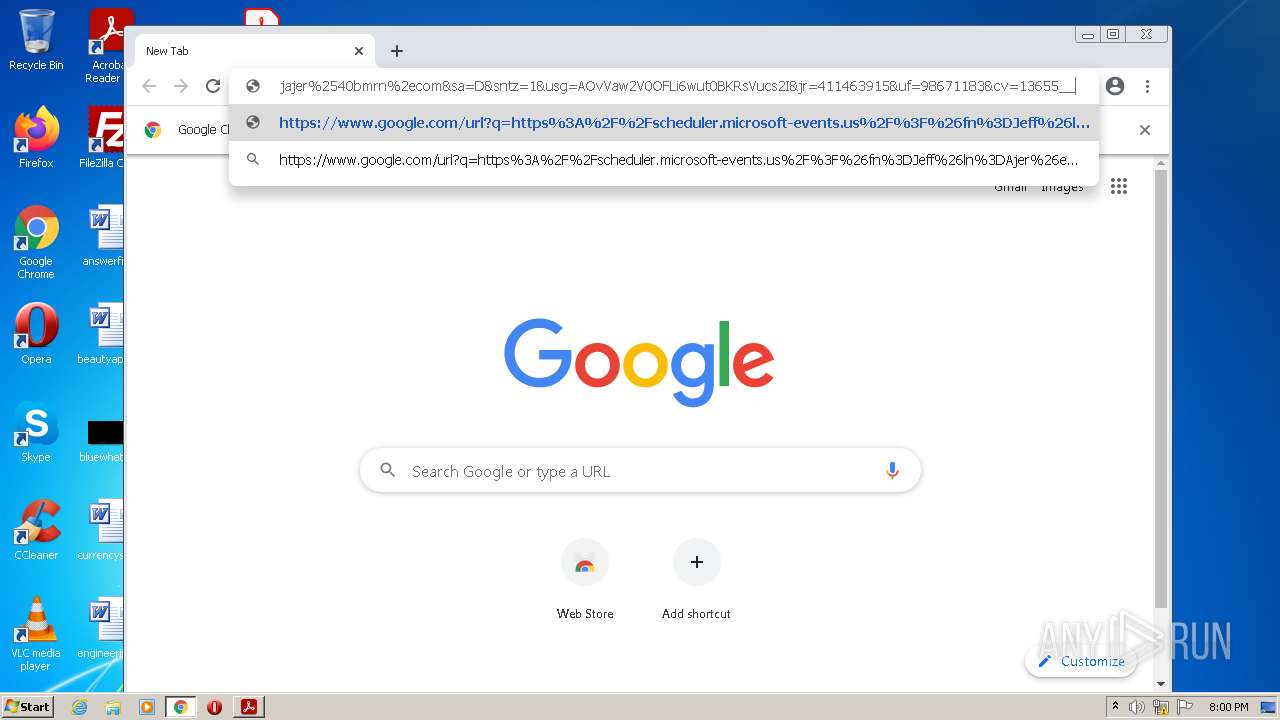
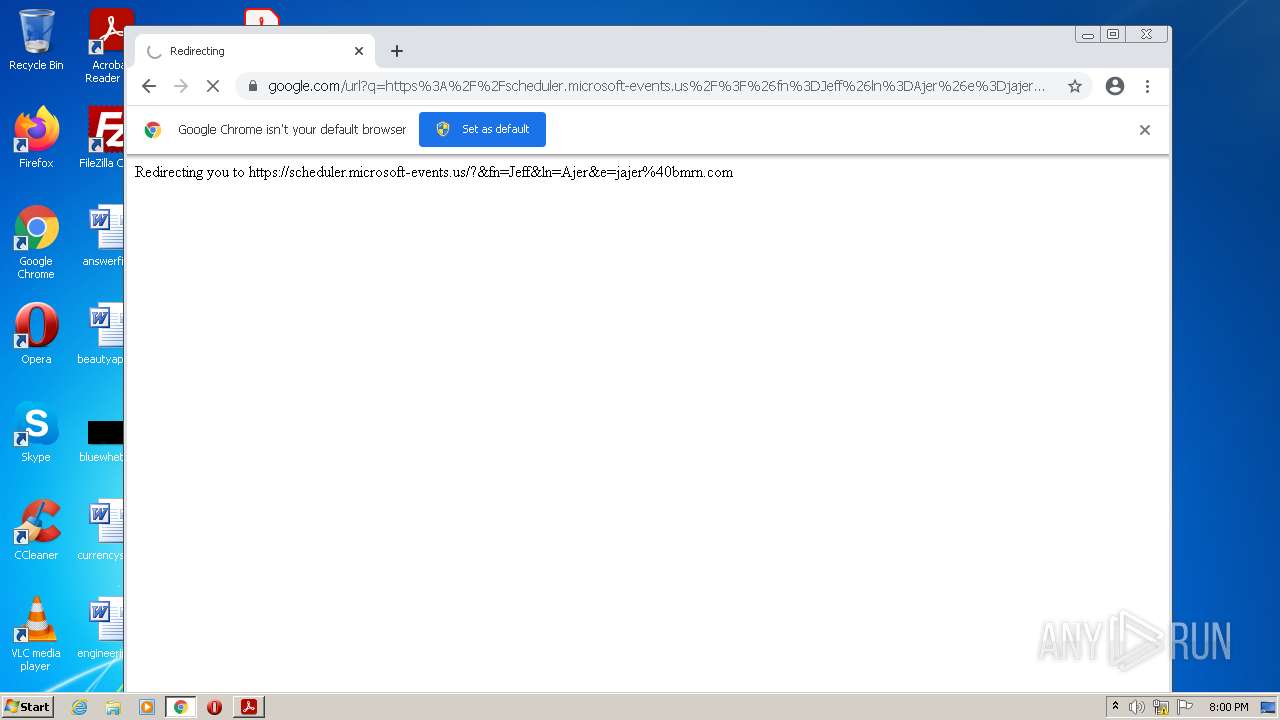
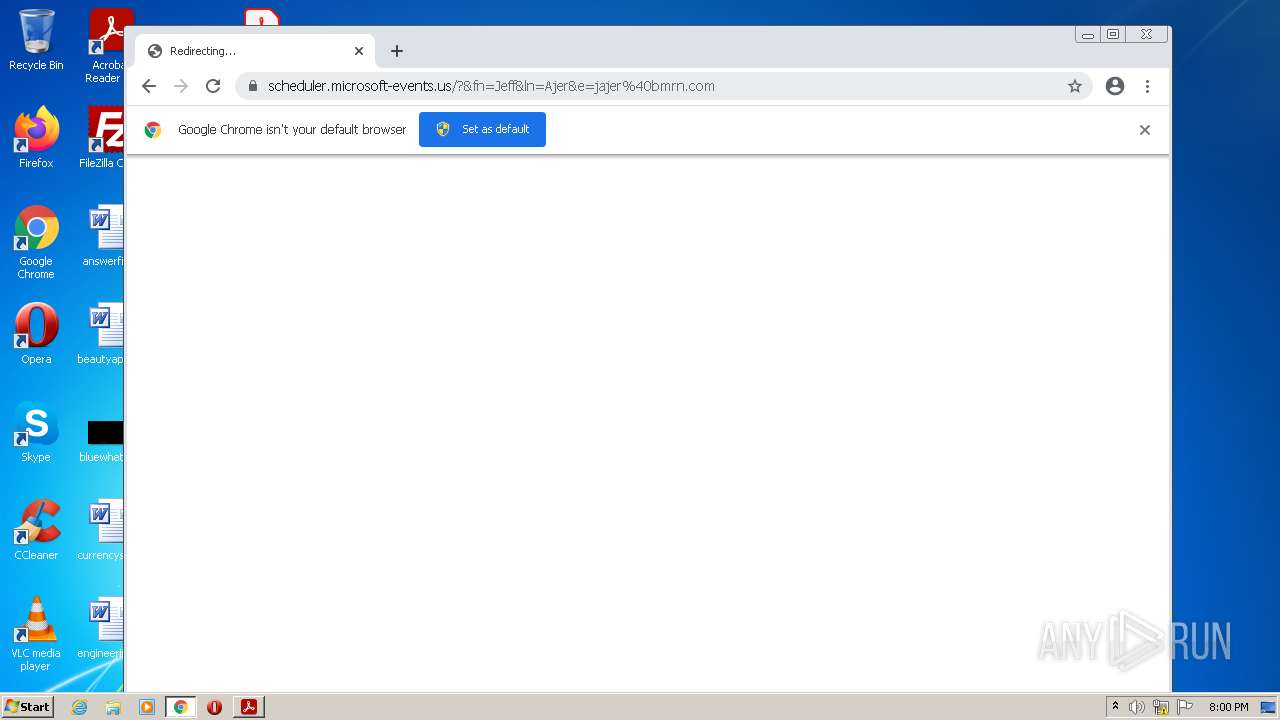
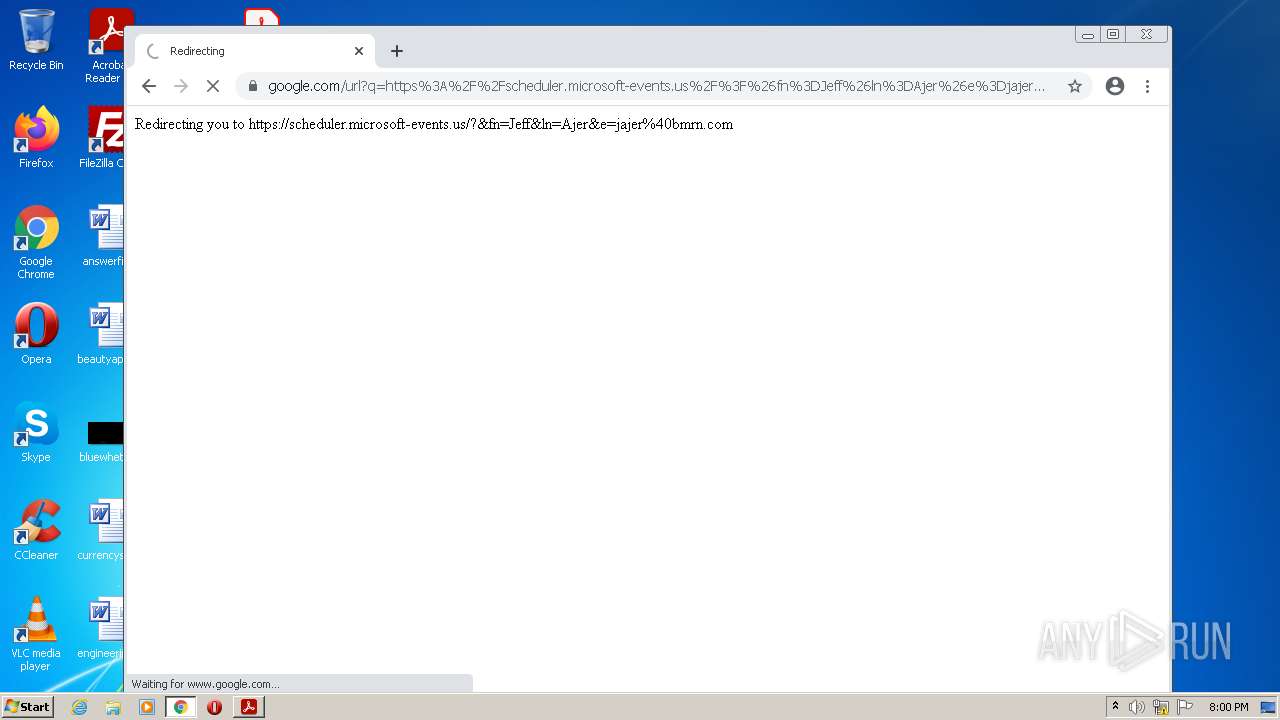
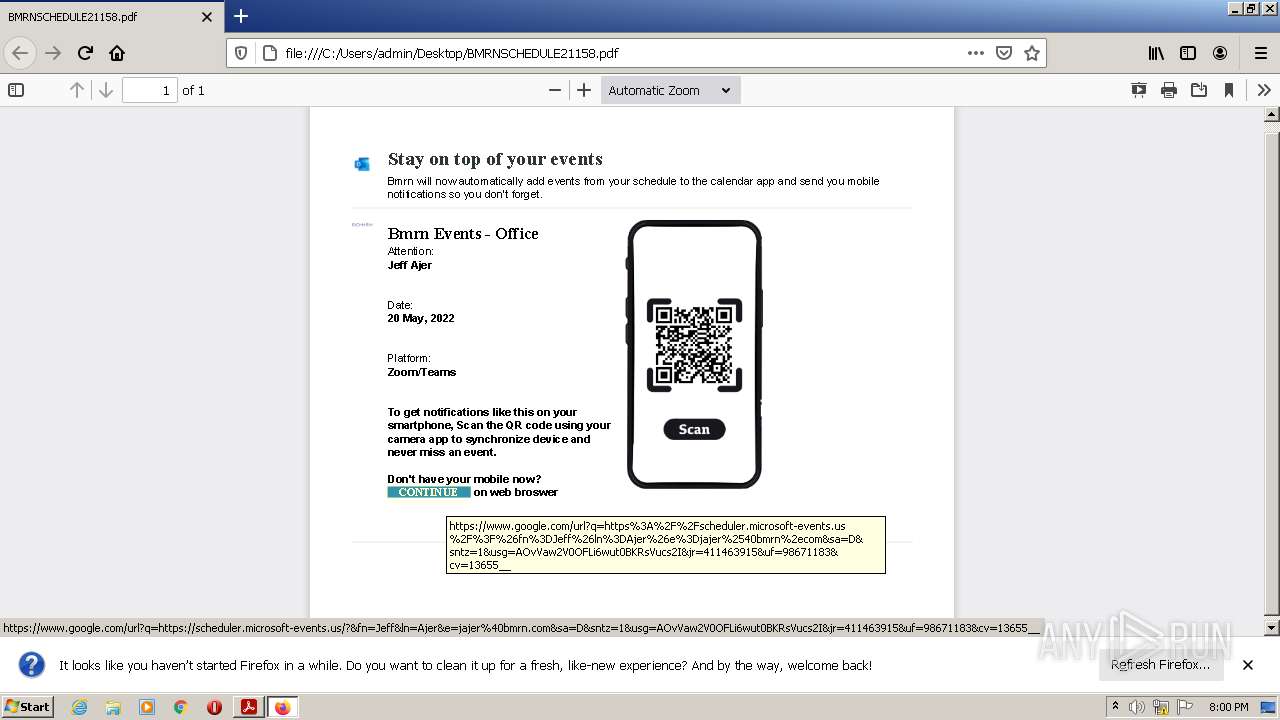
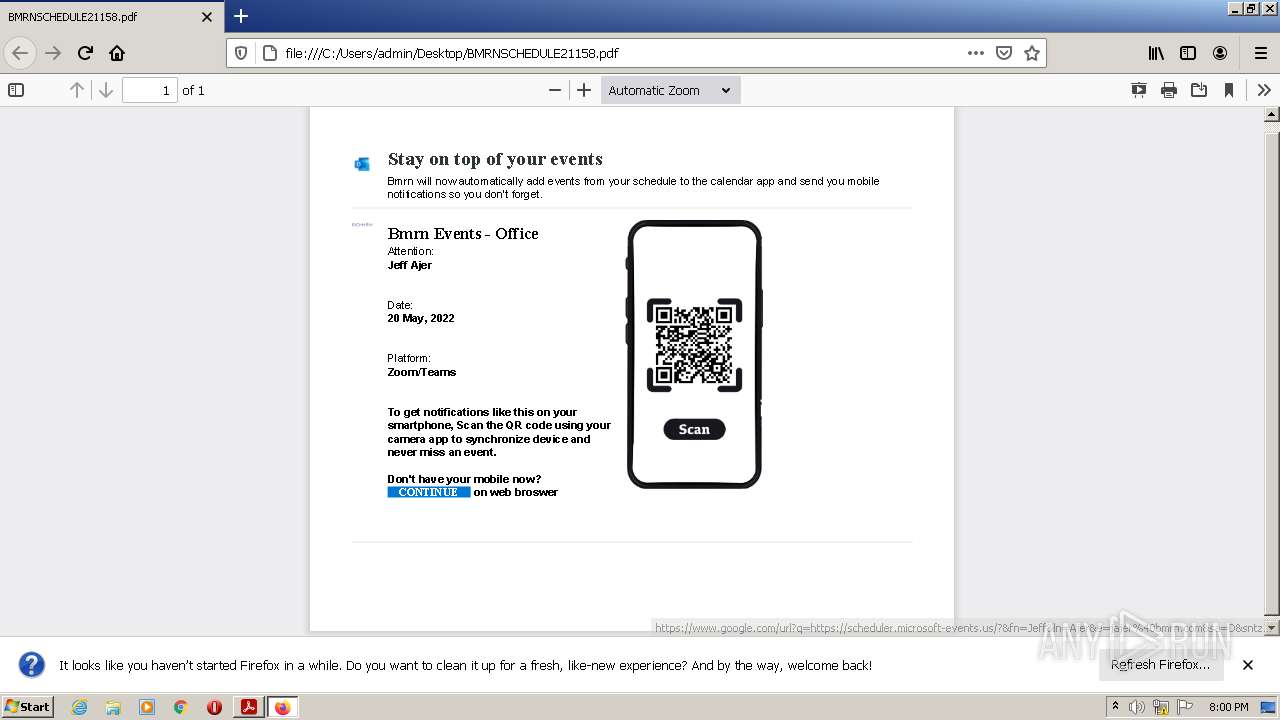
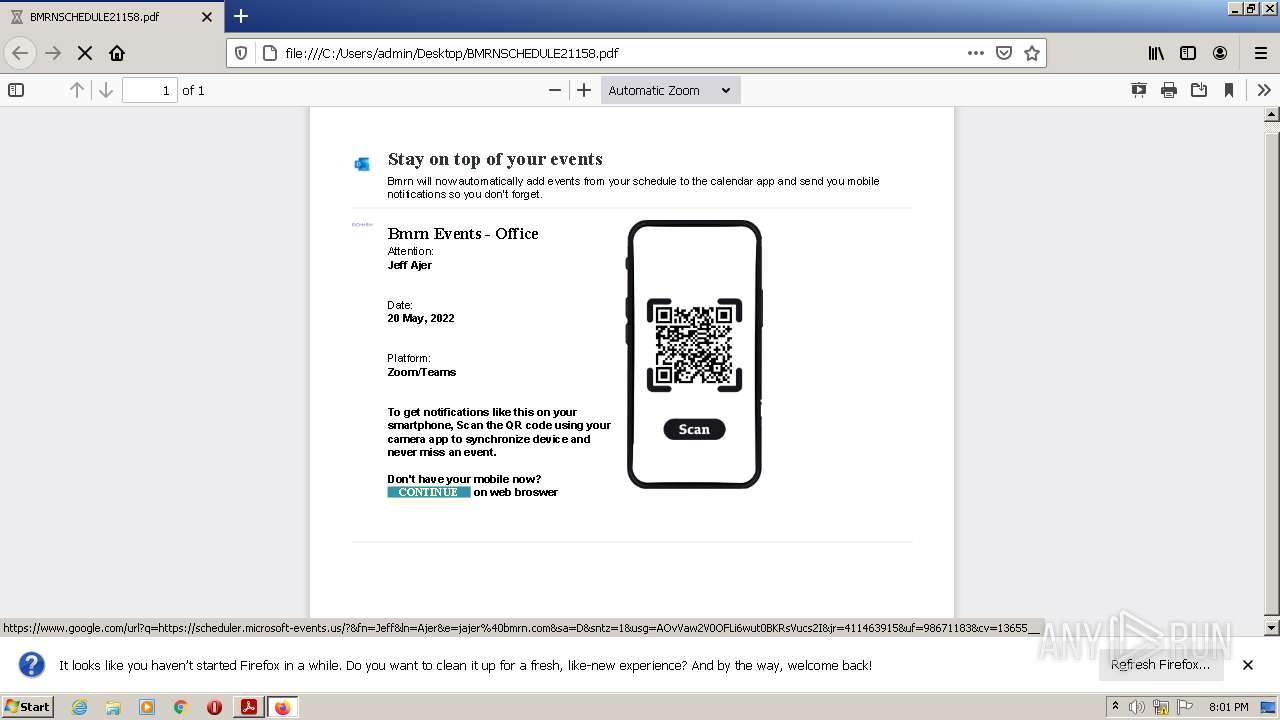
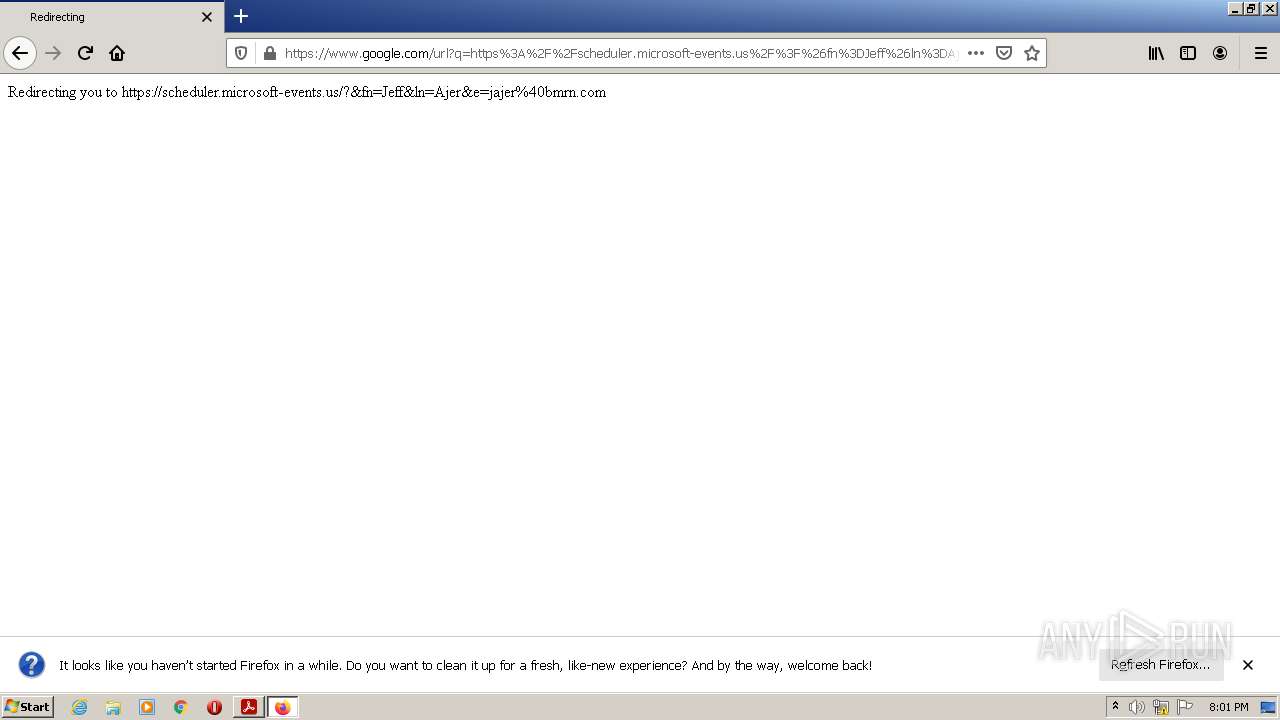
| File name: | BMRNSCHEDULE21158.pdf |
| Full analysis: | https://app.any.run/tasks/7964e0f8-68c2-4438-a092-3c8430c46cd5 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 18:59:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7 |
| MD5: | EB001122A84665C4BA8C47F66C3BE0D4 |
| SHA1: | 46A744B7F1E41309407BBA92036BD1ED854F4B6D |
| SHA256: | 956B2E530528242D980F0D910F512732580564CECBE461D6669048C6FAF5C7E4 |
| SSDEEP: | 1536:AlviyAkCtSGzfcsiT4uutx/7uMJh155rW1TMTp4njI:UqyiUsgv8/HJh8TwpkjI |
MALICIOUS
No malicious indicators.SUSPICIOUS
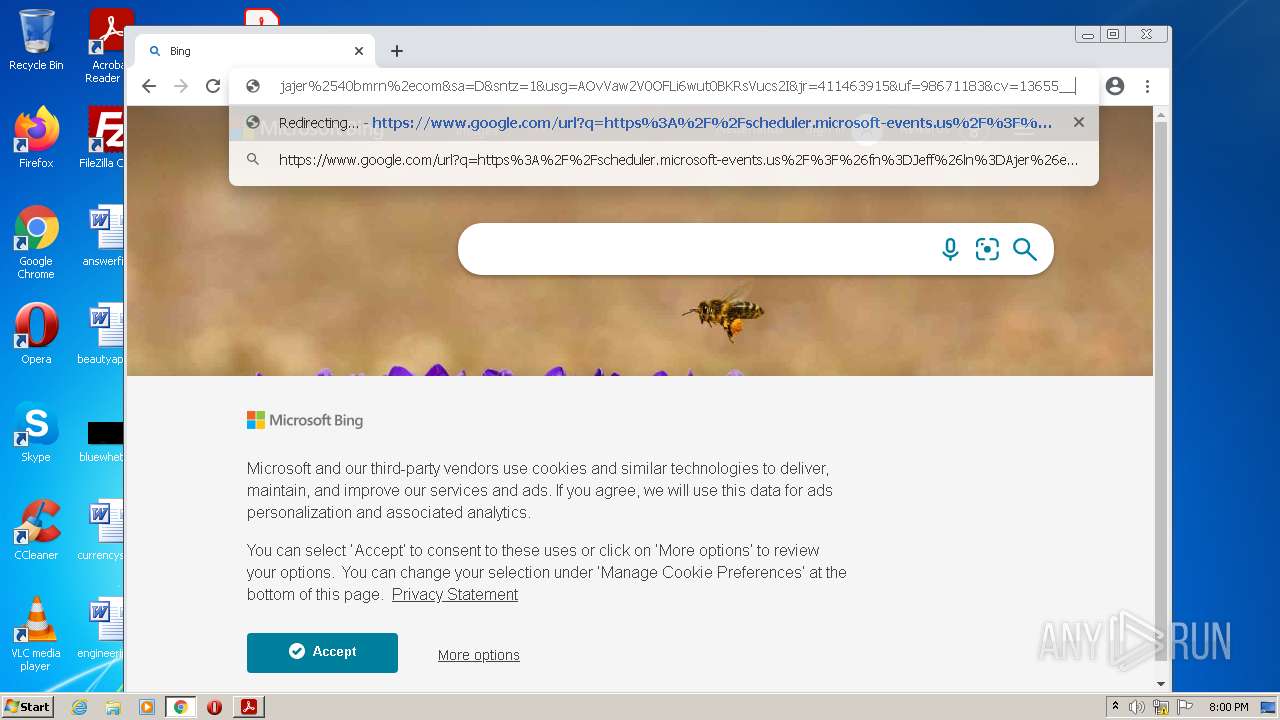
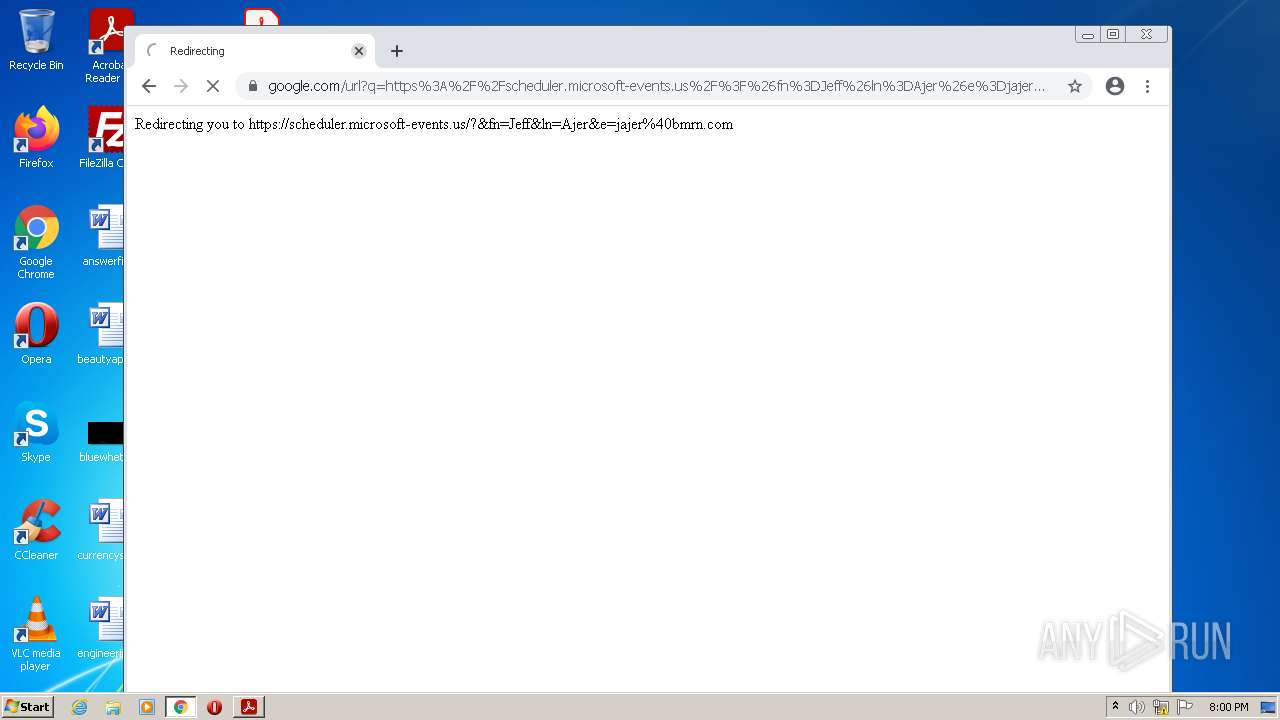
Starts Internet Explorer
- AcroRd32.exe (PID: 804)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2536)
Reads the computer name
- AdobeARM.exe (PID: 2368)
Checks supported languages
- AdobeARM.exe (PID: 2368)
- Reader_sl.exe (PID: 2120)
Modifies files in Chrome extension folder
- chrome.exe (PID: 284)
Creates files in the program directory
- AdobeARM.exe (PID: 2368)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 2368)
INFO
Checks supported languages
- AcroRd32.exe (PID: 804)
- AcroRd32.exe (PID: 3248)
- RdrCEF.exe (PID: 3532)
- RdrCEF.exe (PID: 3212)
- RdrCEF.exe (PID: 3684)
- iexplore.exe (PID: 1404)
- RdrCEF.exe (PID: 3060)
- RdrCEF.exe (PID: 3868)
- RdrCEF.exe (PID: 3524)
- iexplore.exe (PID: 2536)
- RdrCEF.exe (PID: 2280)
- RdrCEF.exe (PID: 3376)
- chrome.exe (PID: 284)
- chrome.exe (PID: 1216)
- chrome.exe (PID: 3088)
- chrome.exe (PID: 2404)
- chrome.exe (PID: 268)
- chrome.exe (PID: 1624)
- chrome.exe (PID: 2600)
- chrome.exe (PID: 1148)
- chrome.exe (PID: 3100)
- chrome.exe (PID: 1004)
- chrome.exe (PID: 2656)
- chrome.exe (PID: 3136)
- chrome.exe (PID: 4068)
- chrome.exe (PID: 1808)
- chrome.exe (PID: 4080)
- chrome.exe (PID: 2004)
- chrome.exe (PID: 2704)
- chrome.exe (PID: 1036)
- chrome.exe (PID: 2640)
- chrome.exe (PID: 3512)
- chrome.exe (PID: 1180)
- chrome.exe (PID: 3360)
- chrome.exe (PID: 912)
- chrome.exe (PID: 2876)
- chrome.exe (PID: 2404)
- chrome.exe (PID: 3868)
- chrome.exe (PID: 892)
- chrome.exe (PID: 2940)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 128)
- chrome.exe (PID: 368)
- chrome.exe (PID: 1816)
- chrome.exe (PID: 3812)
- firefox.exe (PID: 448)
- firefox.exe (PID: 3288)
- firefox.exe (PID: 2440)
- firefox.exe (PID: 1080)
- firefox.exe (PID: 1984)
- firefox.exe (PID: 2356)
- firefox.exe (PID: 1580)
- firefox.exe (PID: 3624)
- firefox.exe (PID: 2608)
- chrome.exe (PID: 2824)
Reads the computer name
- AcroRd32.exe (PID: 804)
- AcroRd32.exe (PID: 3248)
- RdrCEF.exe (PID: 3532)
- iexplore.exe (PID: 1404)
- iexplore.exe (PID: 2536)
- chrome.exe (PID: 284)
- chrome.exe (PID: 1216)
- chrome.exe (PID: 268)
- chrome.exe (PID: 1624)
- chrome.exe (PID: 2004)
- chrome.exe (PID: 1004)
- chrome.exe (PID: 3812)
- firefox.exe (PID: 3288)
- firefox.exe (PID: 2440)
- firefox.exe (PID: 1080)
- firefox.exe (PID: 2356)
- firefox.exe (PID: 2608)
- firefox.exe (PID: 1580)
- firefox.exe (PID: 3624)
- firefox.exe (PID: 1984)
Application launched itself
- AcroRd32.exe (PID: 804)
- RdrCEF.exe (PID: 3532)
- iexplore.exe (PID: 1404)
- chrome.exe (PID: 284)
- firefox.exe (PID: 448)
- firefox.exe (PID: 3288)
Searches for installed software
- AcroRd32.exe (PID: 804)
- AcroRd32.exe (PID: 3248)
Reads CPU info
- AcroRd32.exe (PID: 3248)
- firefox.exe (PID: 3288)
Reads the hosts file
- RdrCEF.exe (PID: 3532)
- chrome.exe (PID: 284)
- chrome.exe (PID: 1624)
Reads settings of System Certificates
- AcroRd32.exe (PID: 804)
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 1404)
- RdrCEF.exe (PID: 3532)
- chrome.exe (PID: 1624)
- AdobeARM.exe (PID: 2368)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 804)
- iexplore.exe (PID: 2536)
- iexplore.exe (PID: 1404)
- AdobeARM.exe (PID: 2368)
Changes internet zones settings
- iexplore.exe (PID: 1404)
Reads the date of Windows installation
- iexplore.exe (PID: 1404)
Manual execution by user
- chrome.exe (PID: 284)
- firefox.exe (PID: 448)
Creates files in the user directory
- firefox.exe (PID: 3288)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3288)
Creates files in the program directory
- firefox.exe (PID: 3288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| ModifyDate: | 2022:05:20 10:53:01-07:00 |
|---|---|
| CreateDate: | 2022:05:20 10:53:01-07:00 |
| Producer: | dompdf 0.8.6 + CPDF |
| PageCount: | 1 |
| Linearized: | No |
| PDFVersion: | 1.7 |
Total processes
97
Monitored processes
57
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3232 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2860 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3080 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -osint -url "C:\Users\admin\Desktop\BMRNSCHEDULE21158.pdf" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 804 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\BMRNSCHEDULE21158.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | Explorer.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3172 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3708 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=2060 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,2503015055169372557,7946912248666674559,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3648 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
55 448
Read events
55 105
Write events
333
Delete events
10
Modification events
| (PID) Process: | (3248) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3248) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 2 | |||
| (PID) Process: | (3248) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | write | Name: | bShowUpdateFTE |
Value: 1 | |||
| (PID) Process: | (3248) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcome |
| Operation: | write | Name: | bIsAcrobatUpdated |
Value: 1 | |||
| (PID) Process: | (3248) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcomeFirstMileReader |
| Operation: | write | Name: | iCardCountShown |
Value: 2 | |||
| (PID) Process: | (3248) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | delete value | Name: | iLastCardShown |
Value: 0 | |||
| (PID) Process: | (804) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1404) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1404) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1404) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960763 | |||
Executable files
1
Suspicious files
408
Text files
195
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\86b8040b7132b608_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\f941376b2efdd6e6_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\983b7a3da8f39a46_0 | binary | |
MD5:— | SHA256:— | |||
| 3532 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\92c56fa2a6c4d5ba_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
75
DNS requests
196
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2536 | iexplore.exe | GET | — | 216.58.214.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | — | — | whitelisted |
804 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
1404 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3288 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3288 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1624 | chrome.exe | GET | 200 | 2.23.12.75:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b9f7cd00d02c28a0 | unknown | compressed | 60.0 Kb | whitelisted |
3288 | firefox.exe | POST | 200 | 216.58.214.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3288 | firefox.exe | POST | 200 | 216.58.214.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3288 | firefox.exe | POST | 200 | 2.23.159.147:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
3288 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1404 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1404 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3532 | RdrCEF.exe | 23.57.81.34:443 | geo2.adobe.com | Akamai Technologies, Inc. | US | whitelisted |
3532 | RdrCEF.exe | 23.46.164.174:443 | armmf.adobe.com | Cox Communications Inc. | US | suspicious |
804 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1624 | chrome.exe | 142.250.75.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
3532 | RdrCEF.exe | 52.6.155.20:443 | p13n.adobe.io | Amazon.com, Inc. | US | unknown |
1624 | chrome.exe | 216.58.206.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
2536 | iexplore.exe | 142.250.179.68:443 | www.google.com | Google Inc. | US | whitelisted |
1624 | chrome.exe | 142.250.178.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3288 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3288 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |