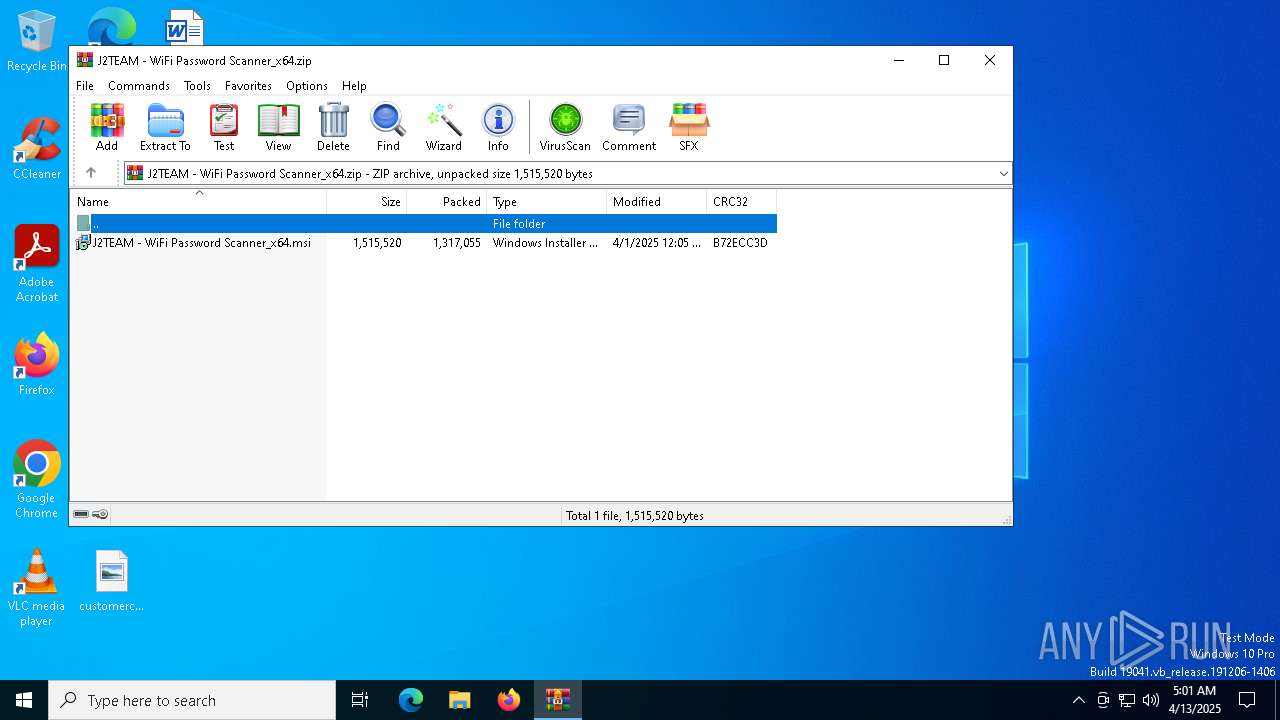
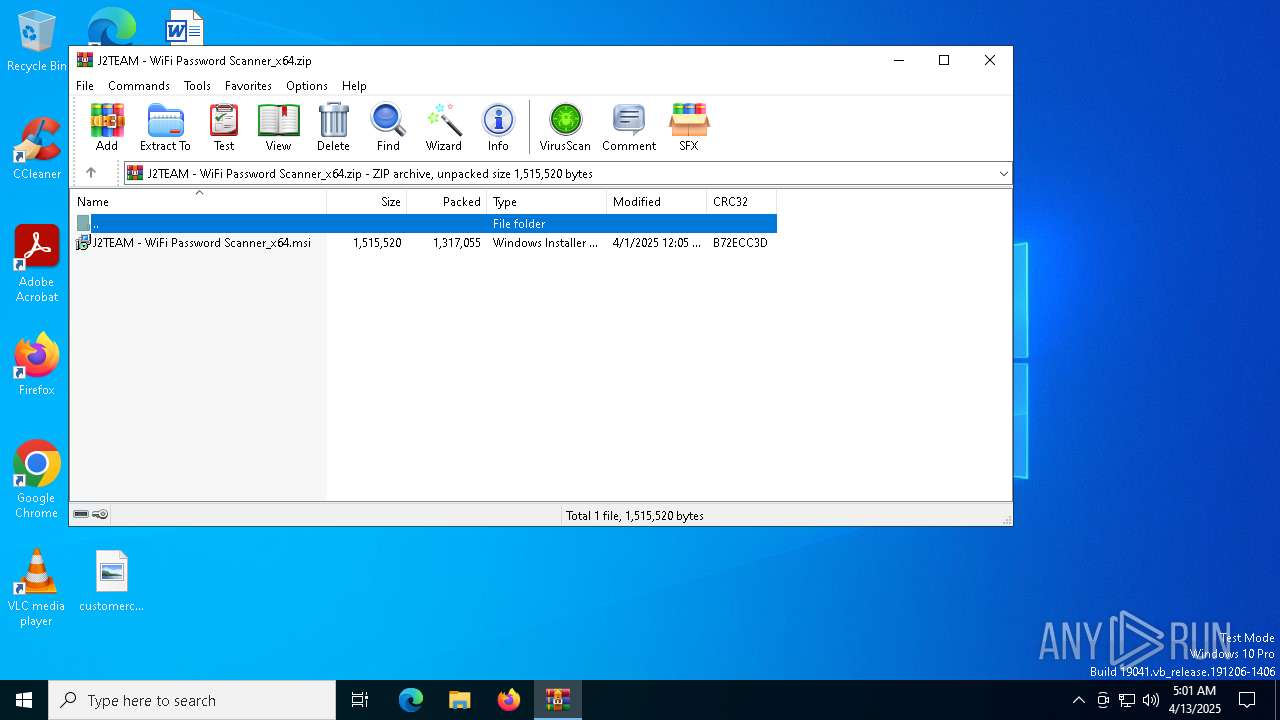
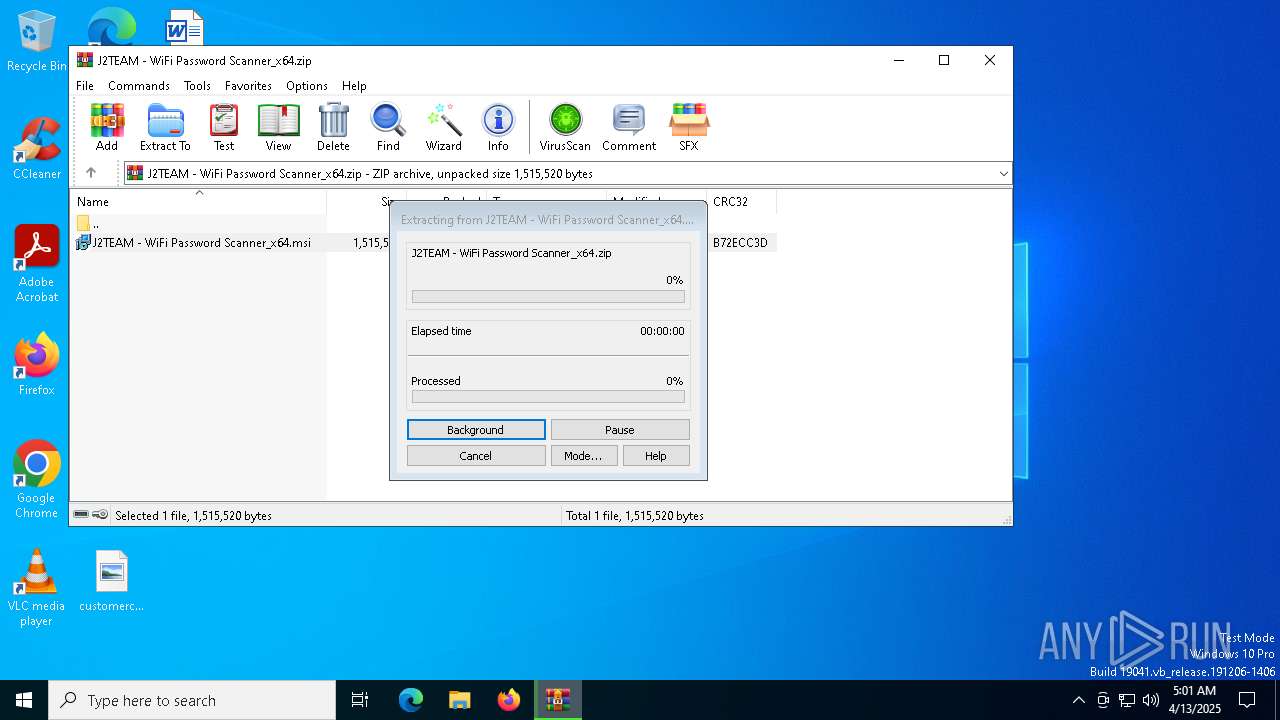
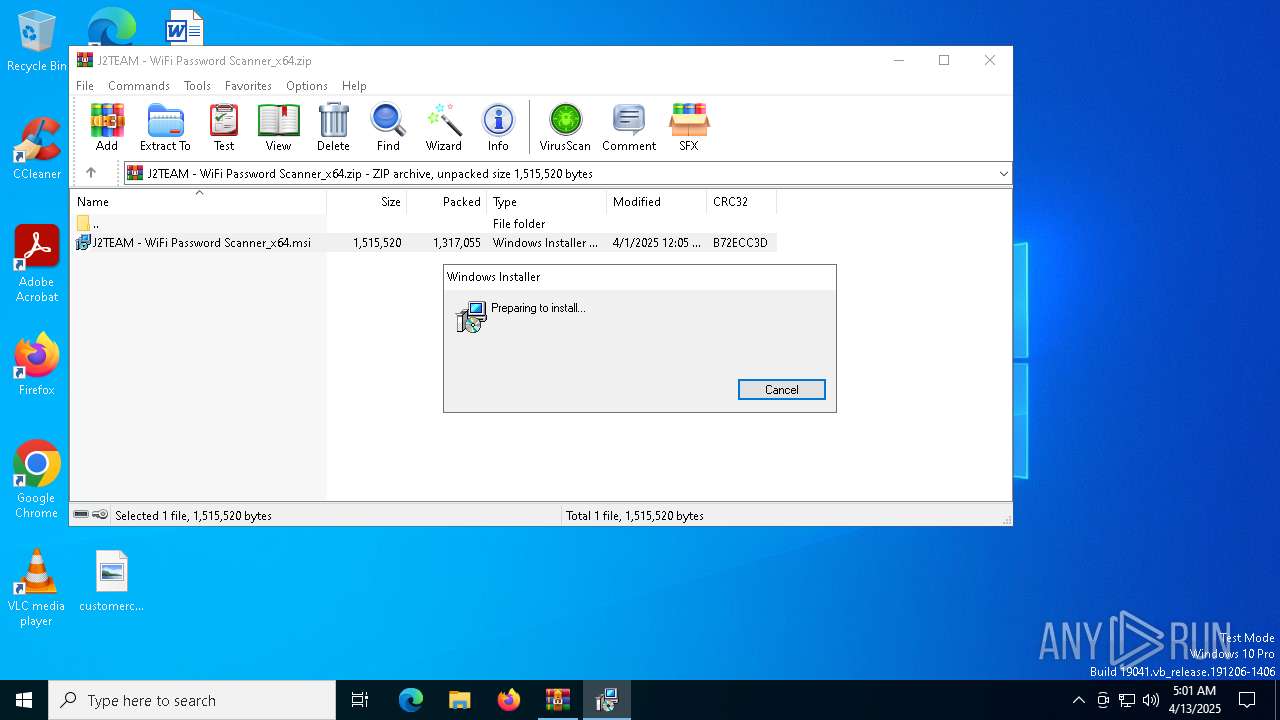
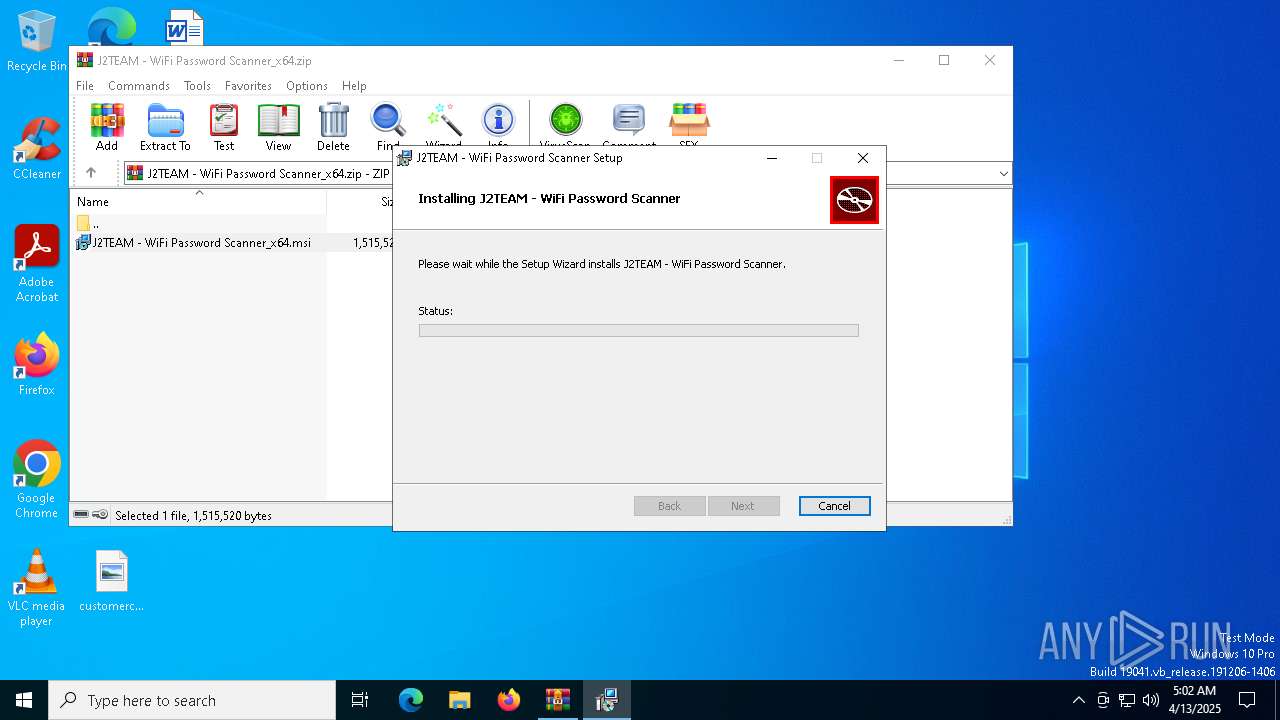
| File name: | J2TEAM - WiFi Password Scanner_x64.zip |
| Full analysis: | https://app.any.run/tasks/c55404ba-1c66-4f3c-9798-26b2e2e69585 |
| Verdict: | Malicious activity |
| Analysis date: | April 13, 2025, 05:01:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CF03D04F82CF6AF76051403428B6F4F9 |
| SHA1: | BFCFEE6EA4CBD9B606CFDD9BF3283C8904F09EEE |
| SHA256: | 955831772D1F2AC12DC3C35018A79594D4081A3B3D545EB642B00226BD2BA6FB |
| SSDEEP: | 49152:mKmvICAeoHae3oNVSRFSUACaV1Y3xSq+fUXCT86Ml7+hy6UqDKBuvhi7axg9u1VQ:fmvc3aCoNVSRFSUAD1JfME86Ml7+hy6G |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 660)
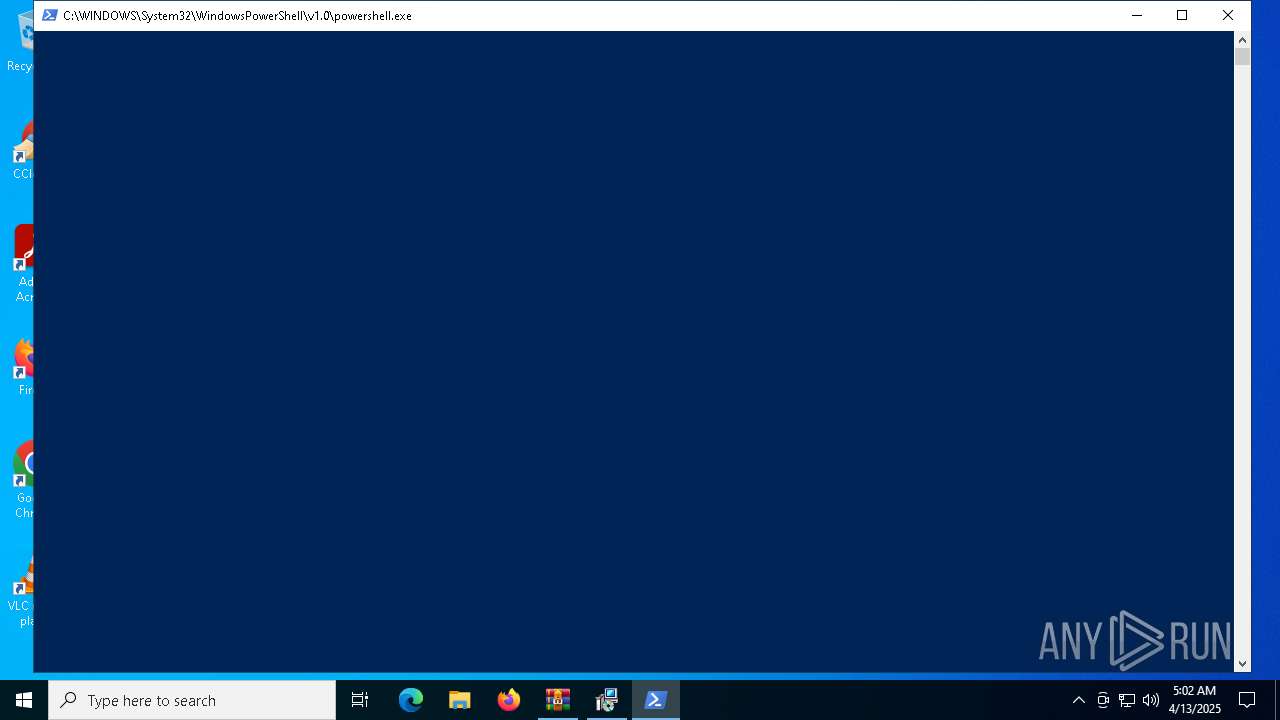
Run PowerShell with an invisible window
- powershell.exe (PID: 1184)
SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6192)
Executes as Windows Service
- VSSVC.exe (PID: 6676)
Manipulates environment variables
- powershell.exe (PID: 1184)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 660)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6192)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1184)
Executable content was dropped or overwritten
- powershell.exe (PID: 1184)
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Process drops legitimate windows executable
- powershell.exe (PID: 1184)
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6192)
Downloads file from URI via Powershell
- powershell.exe (PID: 1184)
Starts process via Powershell
- powershell.exe (PID: 1184)
INFO
Checks supported languages
- msiexec.exe (PID: 6192)
- msiexec.exe (PID: 720)
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Reads the computer name
- msiexec.exe (PID: 720)
- msiexec.exe (PID: 6192)
Manages system restore points
- SrTasks.exe (PID: 2344)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 660)
Creates a software uninstall entry
- msiexec.exe (PID: 6192)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6192)
- msiexec.exe (PID: 2096)
- WinRAR.exe (PID: 660)
Disables trace logs
- powershell.exe (PID: 1184)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Checks proxy server information
- powershell.exe (PID: 1184)
The sample compiled with english language support
- powershell.exe (PID: 1184)
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 5232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:01 19:05:28 |
| ZipCRC: | 0xb72ecc3d |
| ZipCompressedSize: | 1317055 |
| ZipUncompressedSize: | 1515520 |
| ZipFileName: | J2TEAM - WiFi Password Scanner_x64.msi |
Total processes
143
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\J2TEAM - WiFi Password Scanner_x64.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 720 | C:\Windows\syswow64\MsiExec.exe -Embedding 6273EBC913B182F1AF993D21CACCF93D C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa660.32367\J2TEAM - WiFi Password Scanner_x64.msi" | C:\Windows\System32\msiexec.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2344 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5232 | "C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe" /silent /install | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Setup Version: 1.3.195.49 Modules
| |||||||||||||||
| 5508 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 656
Read events
10 388
Write events
259
Delete events
9
Modification events
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\J2TEAM - WiFi Password Scanner_x64.zip | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (6192) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000002BFD7F3131ACDB013018000080030000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
60
Suspicious files
13
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6192 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6192 | msiexec.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\J2TEAM - WiFi Password Scanner\J2TEAM - WiFi Password Scanner.lnk | binary | |
MD5:9B43F0CE52C8D98446C11B7C894B9CBA | SHA256:19F291500EF2F3BF2EF92ABFB6C0ADA3DF2B70888245BF3C72D64E0A65EE6EC3 | |||
| 6192 | msiexec.exe | C:\Windows\Installer\MSI95A5.tmp | binary | |
MD5:B804B3420E59D11E2A32B833C786062A | SHA256:51FF5A51396BF491400838CC39C5DFA92AF44B6C3C07121CE7C1EBB9681E1A48 | |||
| 6192 | msiexec.exe | C:\Windows\Installer\119066.msi | executable | |
MD5:8CADBE8142076940437B2E7DF92BBED7 | SHA256:9E3955383252AD3C906C77A4166970BB8A84E357448C0AF8E8CFB8F6B96053AA | |||
| 6192 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{a208909b-bf54-420b-a4ab-67b971a07cb7}_OnDiskSnapshotProp | binary | |
MD5:FC8E93D6EBC34A81726B0942E60DECAC | SHA256:505D475203E9A1B67A86C82909300DE13859F7C62989A1863DB9D4CCBC87AE89 | |||
| 6192 | msiexec.exe | C:\Windows\Temp\~DF164B536499656465.TMP | binary | |
MD5:451C89C4738D42141F8D641D56A87232 | SHA256:57DA460681F7FA73F9D592931882ED5276C4832CA212912E14641CAAAACE67F3 | |||
| 6192 | msiexec.exe | C:\Windows\Installer\{05A254BE-95CD-47C2-B5E7-6AB4C915DFEF}\ProductIcon | image | |
MD5:D8E74EFCBF68BF9A4D7154A2EDD3FB8E | SHA256:919CCDE84D36AF2C0C23C12818C8D7800FD2EA34E3C6EC1842E128D92337742D | |||
| 6192 | msiexec.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\J2TEAM - WiFi Password Scanner\J2TEAM - WiFi Password Scanner.lnk~RF1196af.TMP | binary | |
MD5:9B43F0CE52C8D98446C11B7C894B9CBA | SHA256:19F291500EF2F3BF2EF92ABFB6C0ADA3DF2B70888245BF3C72D64E0A65EE6EC3 | |||
| 6192 | msiexec.exe | C:\Program Files\J2TEAM - WiFi Password Scanner\j2team-wifi-password-scanner.exe | executable | |
MD5:52488605DFF559A514AF88B96B130DA7 | SHA256:2AD19038F4C5C0F16DF5C531641BCB0558C33176308380829FD61E538AB9B812 | |||
| 6192 | msiexec.exe | C:\Windows\Temp\~DFB4D53F6FFBDF9CF0.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4008 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4008 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |