| File name: | 3C722F99DF5D1018DCD361D8DEB5CDC425C725EDBEB0A688D62F1B6C67ABD22C.zip |
| Full analysis: | https://app.any.run/tasks/3b10ec13-1f0c-4e5d-b803-d1c9df799224 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2019, 17:25:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E157A53F006D70E6E80E4FAD75BD150E |
| SHA1: | E96210B19BE3A77AA0E430C2426F4E12CDD30A65 |
| SHA256: | 9556872F594F32F07EA1A045C7C303F33666C0D144B1451A122FA95883C061B1 |
| SSDEEP: | 196608:z99dwPPvn8RlkLiy8spcuMFzPSXh99VAexciLnHxuRWB9u:zpwP3ulJiM9KXh9VucB8 |
MALICIOUS
Application was dropped or rewritten from another process
- a.exe (PID: 3128)
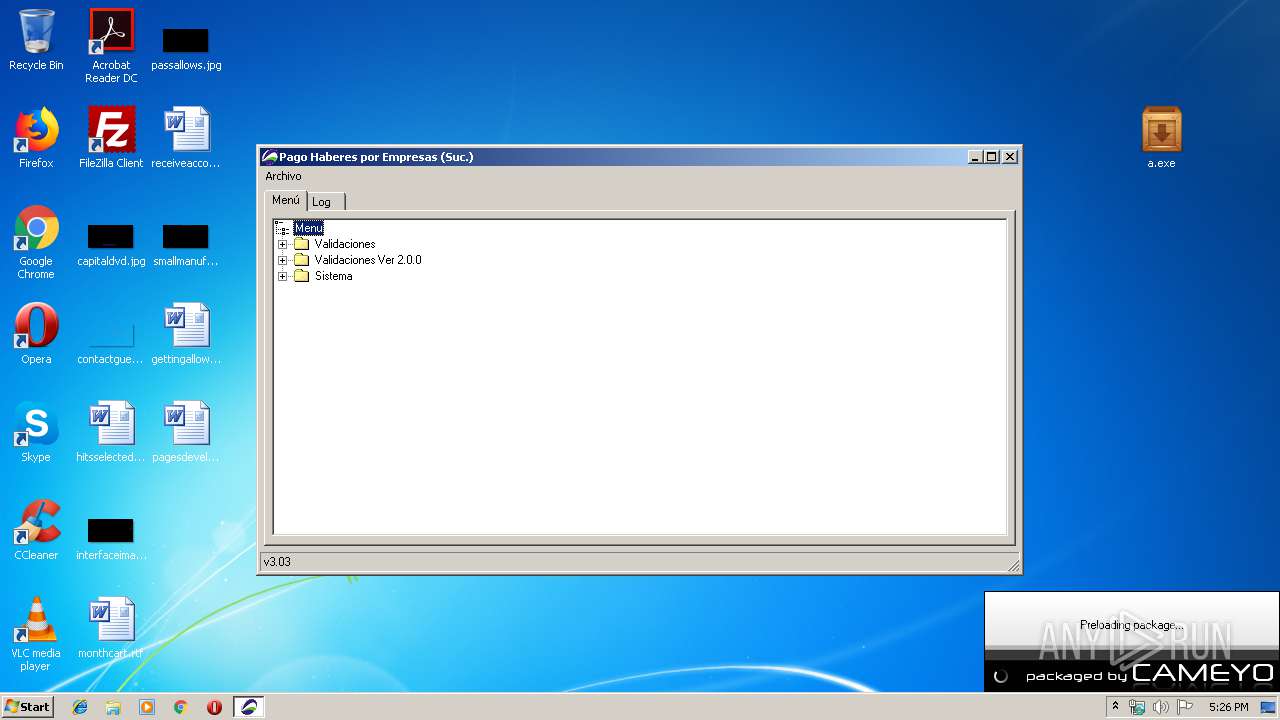
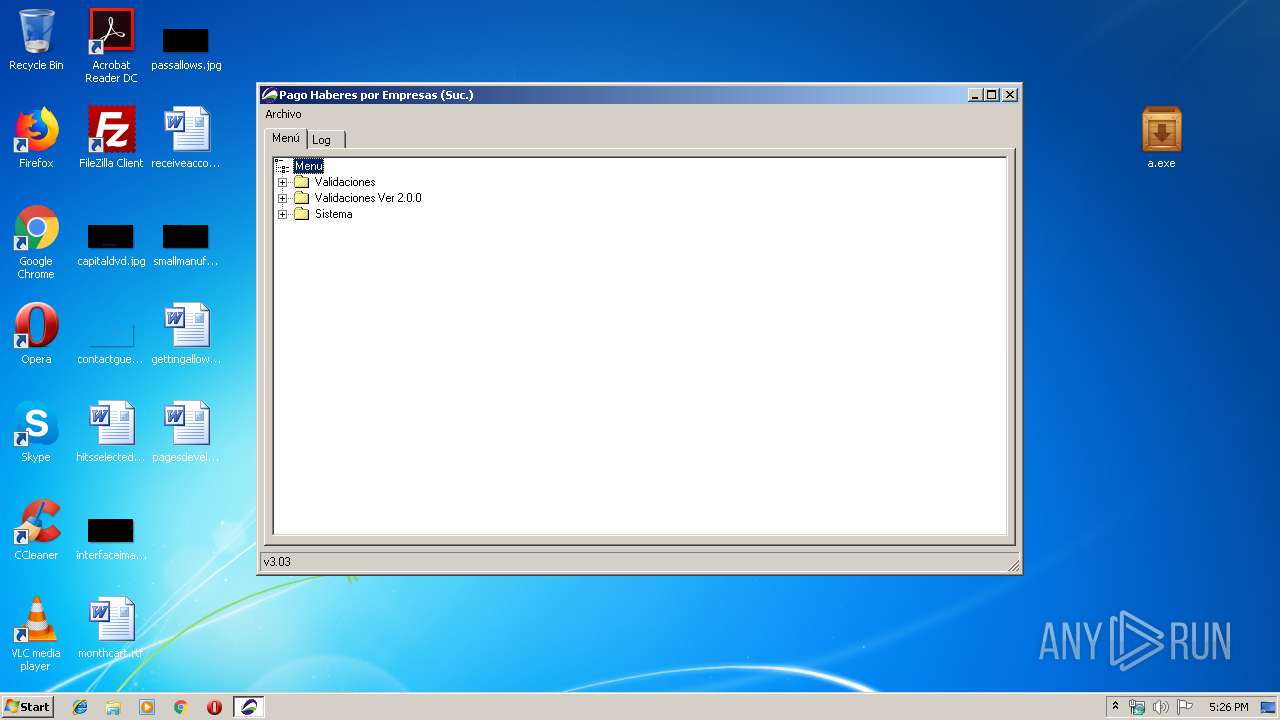
- Pago Haberes y Recaudaciones Suc.exe (PID: 2176)
Loads dropped or rewritten executable
- Pago Haberes y Recaudaciones Suc.exe (PID: 2176)
- a.exe (PID: 3128)
SUSPICIOUS
Creates files in the user directory
- Pago Haberes y Recaudaciones Suc.exe (PID: 2176)
- a.exe (PID: 3128)
Executable content was dropped or overwritten
- a.exe (PID: 3128)
INFO
Manual execution by user
- a.exe (PID: 3128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:12:02 16:55:00 |
| ZipCRC: | 0xdaab3608 |
| ZipCompressedSize: | 8745137 |
| ZipUncompressedSize: | 12341332 |
| ZipFileName: | 3C722F99DF5D1018DCD361D8DEB5CDC425C725EDBEB0A688D62F1B6C67ABD22C |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\3C722F99DF5D1018DCD361D8DEB5CDC425C725EDBEB0A688D62F1B6C67ABD22C.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Pago Haberes por Empresas (Suc.)\BPSSucursal.exe" | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\Pago Haberes y Recaudaciones Suc.exe | — | a.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\Desktop\a.exe" | C:\Users\admin\Desktop\a.exe | explorer.exe | ||||||||||||
User: admin Company: Cameyo (cameyo.com) Integrity Level: MEDIUM Exit code: 0 Version: 2, 6, 1209, 0 Modules
| |||||||||||||||
Total events
539
Read events
506
Write events
31
Delete events
2
Modification events
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\3C722F99DF5D1018DCD361D8DEB5CDC425C725EDBEB0A688D62F1B6C67ABD22C.zip | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
4
Suspicious files
13
Text files
0
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb388.7015\3C722F99DF5D1018DCD361D8DEB5CDC425C725EDBEB0A688D62F1B6C67ABD22C | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\AppVirtDll_Pago Haberes y Recaudaciones Suc.dll.20140625-182934.274.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\AppVirtDll64_Pago Haberes y Recaudaciones Suc.dll.20140625-182934.424.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\Pago Haberes y Recaudaciones Suc.exe.20140625-182934.634.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\Pago Haberes y Recaudaciones Suc64.exe.20140625-182934.634.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\VirtFiles.Prog.db.20140630-174023.811.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\SandboxCfg.db.20140625-182934.644.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\EngineStamps\VirtReg.Prog.dat.20140630-174023.847.stamp | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\CHANGES\VirtReg.dat | — | |
MD5:— | SHA256:— | |||
| 3128 | a.exe | C:\Users\admin\AppData\Roaming\VOS\Pago Haberes y Recaudaciones Suc\CHANGES\VirtFiles.db.3148.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report