| URL: | http://totallpuss.in/ |
| Full analysis: | https://app.any.run/tasks/db5f5452-6459-4d51-81b2-b20c6dd6053a |
| Verdict: | Suspicious activity |
| Analysis date: | September 02, 2019, 04:52:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5B61AC275AE564D761FD68C8492222B3 |
| SHA1: | 047A260E2848FDA12E49B84BFCA2DA1FFCD3B11F |
| SHA256: | 955567B306E4041950F82D16B8C2EE7336F898F2E69B3500624CEF2B3FF02200 |
| SSDEEP: | 3:N1KKKqbDZK:CKhvZK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2760)
INFO
Application launched itself
- chrome.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
86
Monitored processes
52
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15447742564099604889 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5552 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9804819504209901808 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5160 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17795615880240295969 --renderer-client-id=40 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6132 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15372914846446144615 --renderer-client-id=48 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5876 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=11014988619162378390 --mojo-platform-channel-handle=3980 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2705815849821652731 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3316 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=12844054159024269341 --mojo-platform-channel-handle=1592 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2233203388556677645 --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4040 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6284391458173495965 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5316 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,2808521579063662300,2381437257828957443,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13770243107198011959 --mojo-platform-channel-handle=3412 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
701
Read events
579
Write events
117
Delete events
5
Modification events
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2760-13211873577408375 |
Value: 259 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (2760) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
136
Text files
468
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\726e8dee-ff93-41c8-996a-2ab3c6779d5d.tmp | — | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF168c08.TMP | text | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF168c18.TMP | text | |
MD5:— | SHA256:— | |||
| 2760 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF168c08.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
102
TCP/UDP connections
201
DNS requests
129
Threats
46
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
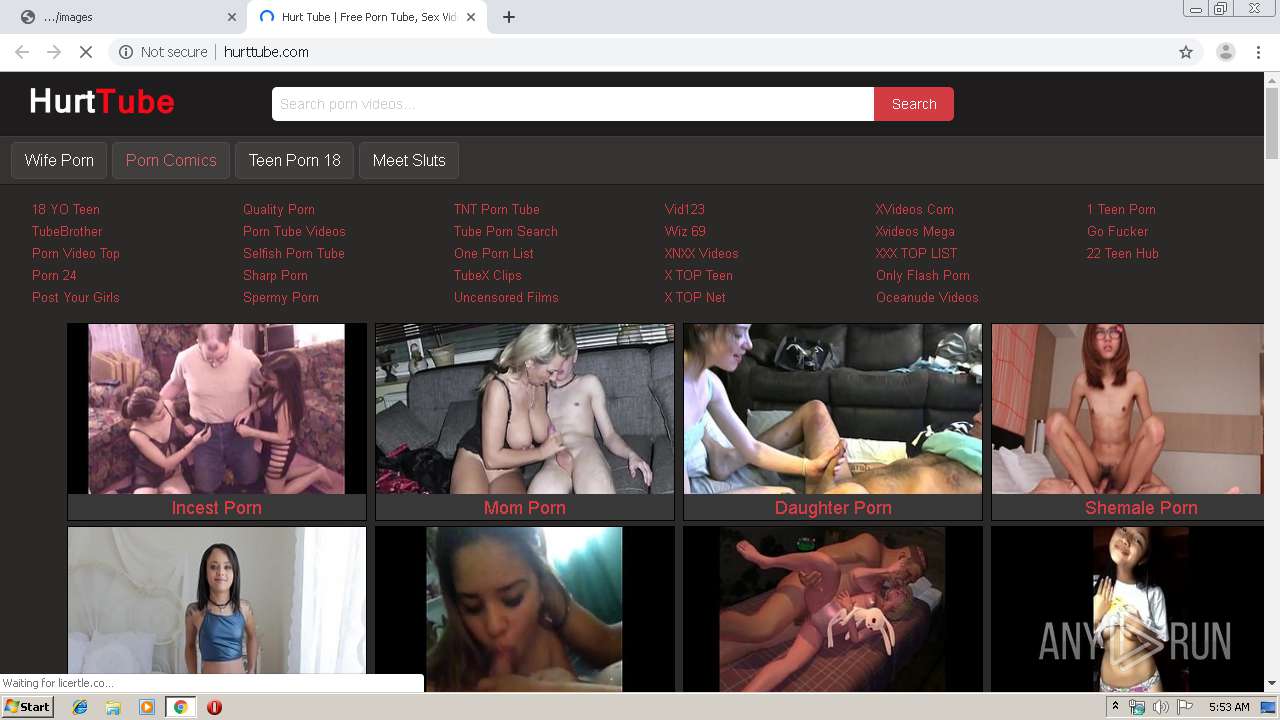
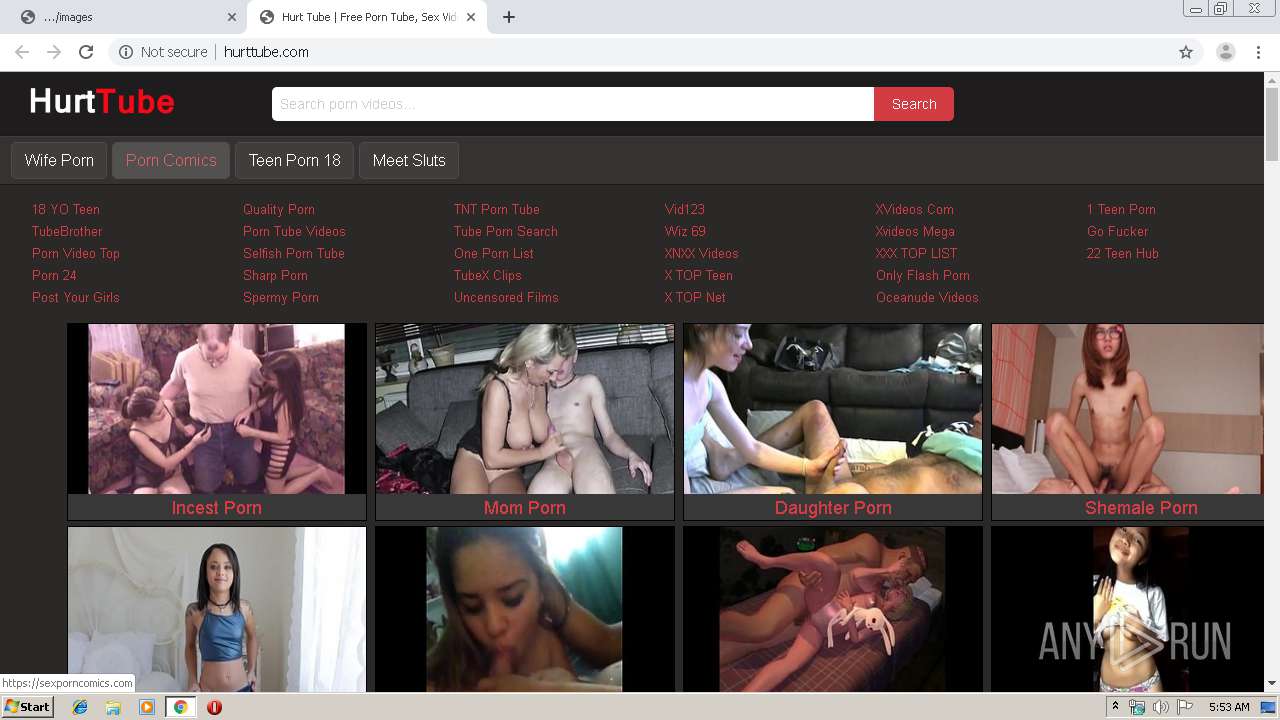
2220 | chrome.exe | GET | 200 | 64.188.2.237:80 | http://hurttube.com/xxx/top/tt/pornvideotop.com.jpg | US | image | 8.51 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.2.237:80 | http://hurttube.com/logo.png | US | image | 1.49 Kb | suspicious |
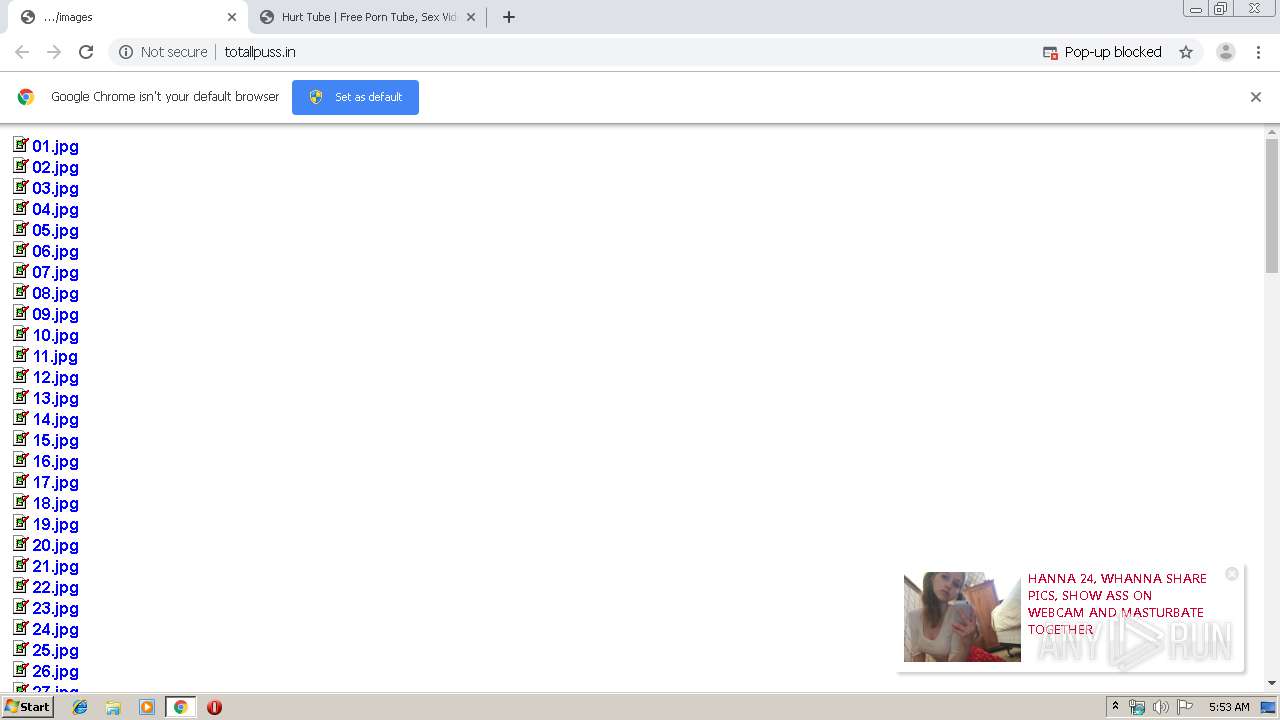
2220 | chrome.exe | GET | 200 | 64.188.10.16:80 | http://totallpuss.in/jquery.js | US | text | 1.38 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.2.237:80 | http://hurttube.com/ | US | html | 8.30 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.10.16:80 | http://totallpuss.in/ | US | html | 2.63 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.2.237:80 | http://hurttube.com/xxx/top/tt/pornxxx24.com.jpg | US | image | 10.4 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.10.16:80 | http://totallpuss.in/index_files/Sv2fB65.png | US | image | 315 b | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.2.237:80 | http://hurttube.com/xxx/top/tt/raresextube.com.jpg | US | image | 4.01 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.10.16:80 | http://totallpuss.in/avatar-hanna-img.png | US | image | 90.0 Kb | suspicious |
2220 | chrome.exe | GET | 200 | 64.188.10.16:80 | http://totallpuss.in/index_files/WPa4CVl.gif | US | image | 169 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2220 | chrome.exe | 64.188.10.16:80 | totallpuss.in | QuadraNet, Inc | US | suspicious |
2220 | chrome.exe | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2220 | chrome.exe | 216.58.206.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
2220 | chrome.exe | 104.19.196.151:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | shared |
2220 | chrome.exe | 88.212.201.199:80 | counter.yadro.ru | United Network LLC | RU | unknown |
2220 | chrome.exe | 172.217.22.1:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2220 | chrome.exe | 172.217.22.110:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
2220 | chrome.exe | 74.125.8.172:80 | r6---sn-5hne6nlk.gvt1.com | Google Inc. | US | whitelisted |
2220 | chrome.exe | 216.58.207.68:443 | www.google.com | Google Inc. | US | whitelisted |
2220 | chrome.exe | 64.188.2.237:80 | hurttube.com | QuadraNet, Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
totallpuss.in |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
cdnjs.cloudflare.com |
| whitelisted |
counter.yadro.ru |
| whitelisted |
loveamour.me |
| unknown |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r6---sn-5hne6nlk.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2220 | chrome.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2220 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Suspicious Darkwave Popads Pop Under Redirect |
2220 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2220 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |