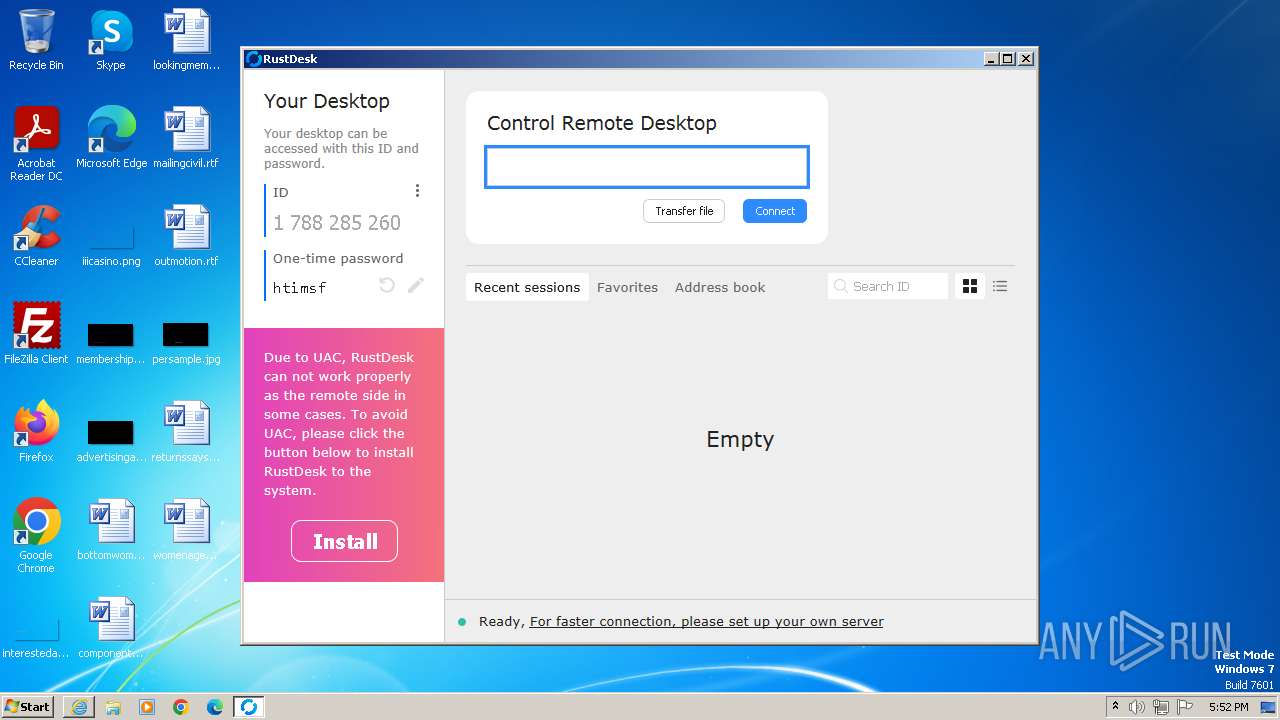
| URL: | https://github.com/rustdesk/rustdesk/releases/download/1.2.3-2/rustdesk-1.2.3-2-x86-sciter.exe |
| Full analysis: | https://app.any.run/tasks/216dd8ef-1b91-409a-976b-b5289edb6bdd |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2024, 16:51:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | ED267257A2CED64A17FA4748AE0C04DB |
| SHA1: | FD67D4A0C34F72CF116FA5E773A90E16F22041D6 |
| SHA256: | 9554945F54789C29D3F9E372FE8EAC92378B204D1C825ABFF995D9E380698EA3 |
| SSDEEP: | 3:N8tEdnyWBer2kCUmqZLXDKYAC:2ugPK6fZLznAC |
MALICIOUS
Drops the executable file immediately after the start
- rustdesk-1.2.3-2-x86-sciter.exe (PID: 1768)
RUSTDESK has been detected (SURICATA)
- rustdesk.exe (PID: 1664)
SUSPICIOUS
Executable content was dropped or overwritten
- rustdesk-1.2.3-2-x86-sciter.exe (PID: 1768)
Uses TASKKILL.EXE to kill process
- rustdesk-1.2.3-2-x86-sciter.exe (PID: 1768)
- cmd.exe (PID: 1944)
Starts CMD.EXE for commands execution
- rustdesk.exe (PID: 1664)
Reads the Internet Settings
- rustdesk.exe (PID: 1664)
Connects to unusual port
- rustdesk.exe (PID: 1664)
- rustdesk.exe (PID: 568)
Application launched itself
- rustdesk.exe (PID: 1664)
INFO
Application launched itself
- iexplore.exe (PID: 3988)
Drops the executable file immediately after the start
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 3988)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3988)
Checks supported languages
- wmpnscfg.exe (PID: 1680)
- rustdesk-1.2.3-2-x86-sciter.exe (PID: 1768)
- rustdesk.exe (PID: 1664)
- rustdesk.exe (PID: 568)
Reads the computer name
- wmpnscfg.exe (PID: 1680)
- rustdesk.exe (PID: 1664)
- rustdesk.exe (PID: 568)
The process uses the downloaded file
- iexplore.exe (PID: 3988)
Manual execution by a user
- wmpnscfg.exe (PID: 1680)
Executable content was dropped or overwritten
- iexplore.exe (PID: 4048)
- iexplore.exe (PID: 3988)
Creates files or folders in the user directory
- rustdesk-1.2.3-2-x86-sciter.exe (PID: 1768)
- rustdesk.exe (PID: 1664)
- rustdesk.exe (PID: 568)
Reads the machine GUID from the registry
- rustdesk.exe (PID: 568)
- rustdesk.exe (PID: 1664)
Checks proxy server information
- rustdesk.exe (PID: 1664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
9
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Users\admin\AppData\Local\rustdesk\.\rustdesk.exe" --connect 391028002 | C:\Users\admin\AppData\Local\rustdesk\rustdesk.exe | rustdesk.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RustDesk Version: 1.2.3-2 Modules
| |||||||||||||||
| 1580 | "taskkill" /F /IM RuntimeBroker_rustdesk.exe | C:\Windows\System32\taskkill.exe | — | rustdesk-1.2.3-2-x86-sciter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1664 | "C:\Users\admin\AppData\Local\rustdesk\.\rustdesk.exe" | C:\Users\admin\AppData\Local\rustdesk\rustdesk.exe | rustdesk-1.2.3-2-x86-sciter.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RustDesk Version: 1.2.3-2 Modules
| |||||||||||||||
| 1680 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\rustdesk-1.2.3-2-x86-sciter.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\rustdesk-1.2.3-2-x86-sciter.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1944 | "cmd" /c "taskkill /F /IM RuntimeBroker_rustdesk.exe" | C:\Windows\System32\cmd.exe | — | rustdesk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2276 | taskkill /F /IM RuntimeBroker_rustdesk.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3988 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/rustdesk/rustdesk/releases/download/1.2.3-2/rustdesk-1.2.3-2-x86-sciter.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4048 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3988 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
20 750
Read events
20 611
Write events
93
Delete events
46
Modification events
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31106993 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31106993 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
5
Suspicious files
18
Text files
16
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:957FFFCC3B656E65094C6768DEC46A0B | SHA256:2D5483C3395CA5B511B1BBC822D7A8FA81D0036DF245BF73C654D34CE97EA890 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A66A8DB907BADC9D16AD67B2FBFFDD5C | der | |
MD5:C7BE9397923ACA2EE21A22C76764E19B | SHA256:2CCFBF35EB025E9A1B659DF96D9B17EEB8D73768B549BE41EDD21D343E2A6F44 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | der | |
MD5:0E57294ED75D5737182607E95E369E00 | SHA256:316DE0E1B5F70F35DB62A1EAE0574273A7A6CA8E556EA306DC2C117D87670AA1 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:506A13DA4B456DDD7AE48C2C0D2355C0 | SHA256:DE12FA988B5DB2F72641A9A5EF4B3B81B22ABE59877E92154523E45BB863E0BD | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:056A86A1360DE4EF5C4ACF7DFF9528DA | SHA256:60C01DC2308BE5BC248DF97A056006CD0801E44DD0CAAA2B69CC7C2C8FC9F843 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A66A8DB907BADC9D16AD67B2FBFFDD5C | binary | |
MD5:E0A3B0BEA07A55C83BCA8DA45092C093 | SHA256:B5EAA065D7FF37116D33BFE86FD196EBF36F2586DEA3EE960BF6A043CBF2F008 | |||
| 1664 | rustdesk.exe | C:\Users\admin\AppData\Roaming\RustDesk\config\RustDesk2.1664_ThreadId(28)_1715878320555500000 | — | |
MD5:— | SHA256:— | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:88DE9F1F66B697BF73D077181AF3CC24 | SHA256:B8F667DFD4476C22E7FA9FB92C89E8C5AF50C1CB35E8A872C42D3C6EA8323935 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\rustdesk-1.2.3-2-x86-sciter[1].exe | executable | |
MD5:1449044A473BDF895666A5D405B89289 | SHA256:48EFD5AB3986E9A30DDBD4E6077592AE164E424C5B934A11F48D24F7C33CC626 | |||
| 4048 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:F4CF43768F928B60FB50245AA2BA197D | SHA256:7FB836A3BC5B532F165B3AEBFBE605B22ACDD379DB34939F47456864EFEBEC13 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
30
DNS requests
15
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4048 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d1fc3241a5fb83c4 | unknown | — | — | unknown |
4048 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?098b2ca3f74ef2d4 | unknown | — | — | unknown |
4048 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | unknown |
4048 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | unknown |
4048 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEE4o94a2bBo7lCzSxA63QqU%3D | unknown | — | — | unknown |
4048 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | unknown |
3988 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://crt.sectigo.com/SectigoPublicCodeSigningCAEVR36.crt | unknown | — | — | unknown |
3988 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://crt.sectigo.com/SectigoPublicCodeSigningRootR46.p7c | unknown | — | — | unknown |
3988 | iexplore.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c21588876f974d24 | unknown | — | — | unknown |
3988 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5ae977de40ce3b21 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4048 | iexplore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
4048 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
4048 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
4048 | iexplore.exe | 185.199.110.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
4048 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3988 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3988 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |
crt.sectigo.com |
| whitelisted |
rs-ny.rustdesk.com |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO RustDesk Relay Domain in DNS Lookup |
1088 | svchost.exe | Misc activity | ET INFO RustDesk Relay Domain in DNS Lookup |
1088 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
1088 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
1664 | rustdesk.exe | Misc activity | ET INFO RustDesk Register Public Key |