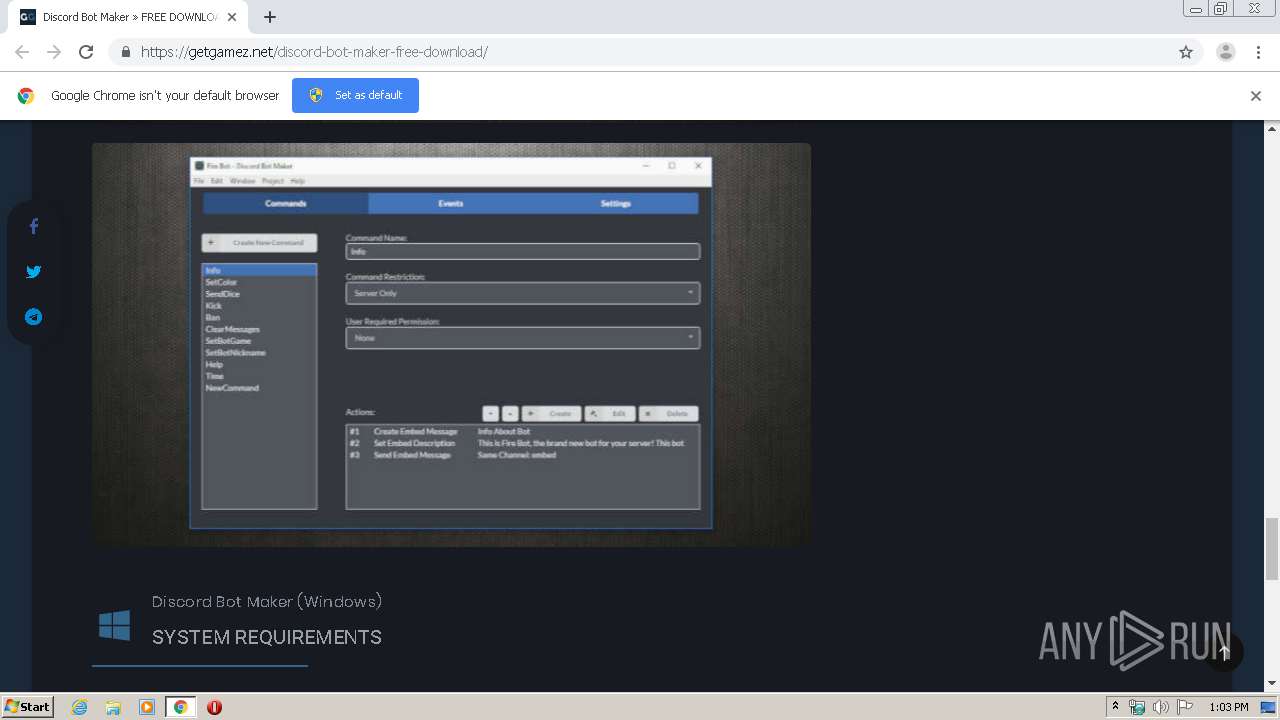
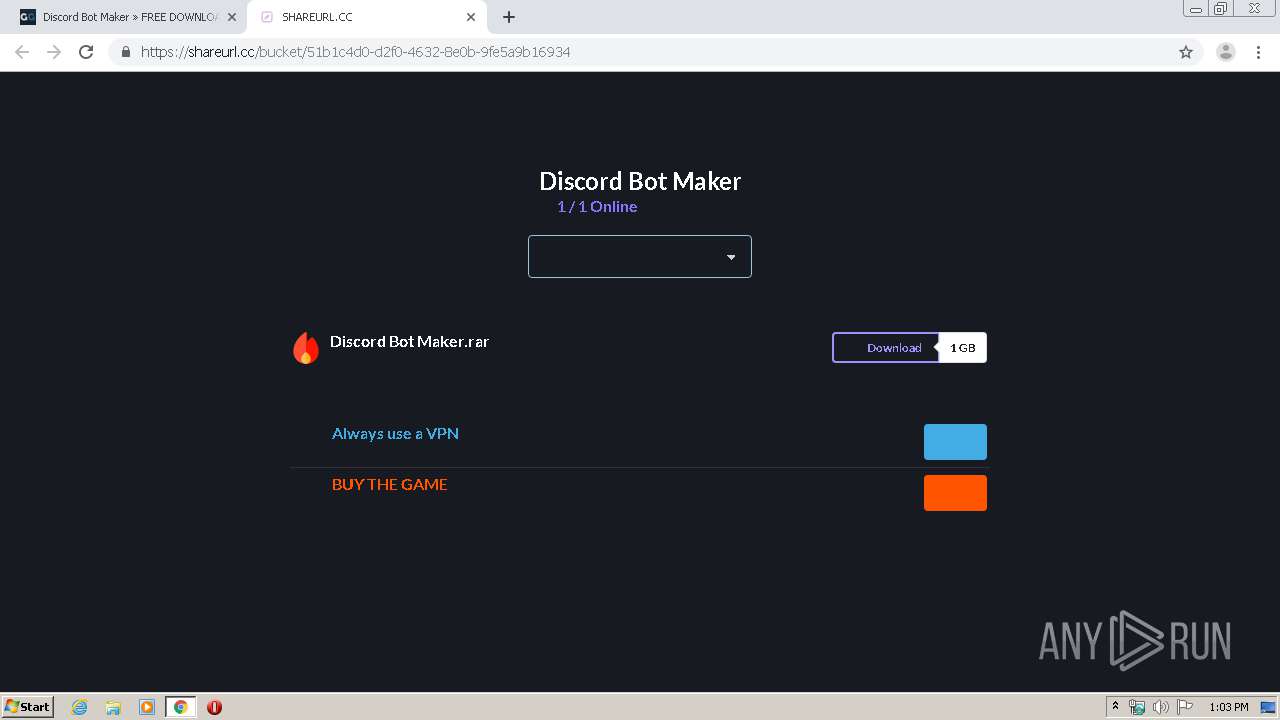
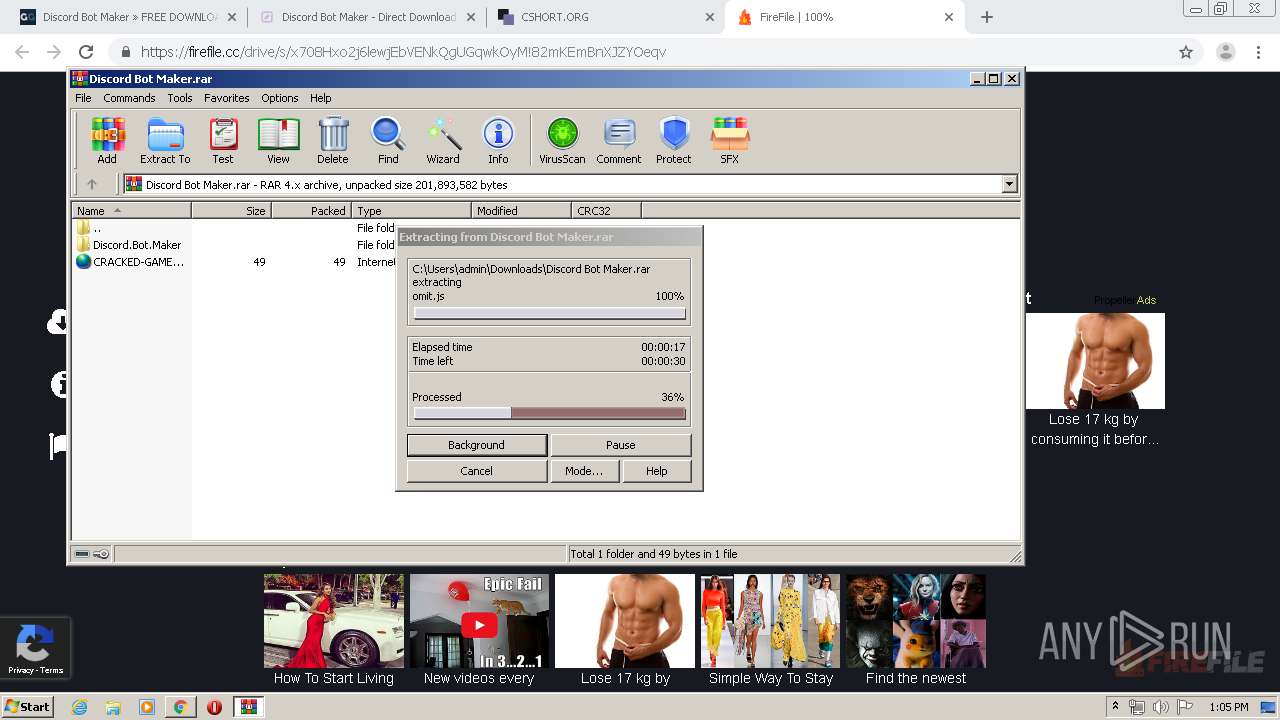
| URL: | https://getgamez.net/discord-bot-maker-free-download/ |
| Full analysis: | https://app.any.run/tasks/614281bb-333a-4775-bd0a-b121fc8c26d7 |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2020, 12:02:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B0B5595AA5F8EDB153E633AC4BA90CAD |
| SHA1: | 9C893AFC0FDF757AB5F203A6F6AC0B217B8A9439 |
| SHA256: | 9542F290C678520D16B75DC0755447330F6529B78971066013392C867D664FAC |
| SSDEEP: | 3:N8hN9D6WVHHbGFmn:2B6Gd |
MALICIOUS
Loads dropped or rewritten executable
- Discord Bot Maker.exe (PID: 2968)
- Discord Bot Maker.exe (PID: 4068)
- Discord Bot Maker.exe (PID: 3768)
- Discord Bot Maker.exe (PID: 2108)
- Discord Bot Maker.exe (PID: 2212)
- Discord Bot Maker.exe (PID: 2560)
- Discord Bot Maker.exe (PID: 3140)
- Discord Bot Maker.exe (PID: 3052)
Application was dropped or rewritten from another process
- Discord Bot Maker.exe (PID: 2968)
- Discord Bot Maker.exe (PID: 4068)
- Discord Bot Maker.exe (PID: 3768)
- LAUNCHER.exe (PID: 4072)
- Discord Bot Maker.exe (PID: 2108)
- Discord Bot Maker.exe (PID: 3052)
- Discord Bot Maker.exe (PID: 2560)
- Discord Bot Maker.exe (PID: 2212)
- Discord Bot Maker.exe (PID: 3140)
- LAUNCHER.exe (PID: 3684)
SUSPICIOUS
Executed via COM
- iexplore.exe (PID: 1852)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2432)
Application launched itself
- Discord Bot Maker.exe (PID: 2968)
- Discord Bot Maker.exe (PID: 4068)
- Discord Bot Maker.exe (PID: 2108)
- Discord Bot Maker.exe (PID: 2560)
INFO
Reads the hosts file
- chrome.exe (PID: 3164)
- chrome.exe (PID: 3244)
- Discord Bot Maker.exe (PID: 2968)
- Discord Bot Maker.exe (PID: 2560)
- Discord Bot Maker.exe (PID: 2108)
Application launched itself
- chrome.exe (PID: 3164)
- iexplore.exe (PID: 1852)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2432)
Reads Internet Cache Settings
- chrome.exe (PID: 3164)
- iexplore.exe (PID: 1688)
- iexplore.exe (PID: 1852)
Changes internet zones settings
- iexplore.exe (PID: 1852)
Creates files in the user directory
- iexplore.exe (PID: 1688)
Reads internet explorer settings
- iexplore.exe (PID: 1688)
Manual execution by user
- Discord Bot Maker.exe (PID: 2968)
- LAUNCHER.exe (PID: 4072)
- LAUNCHER.exe (PID: 3684)
Reads settings of System Certificates
- chrome.exe (PID: 3244)
- iexplore.exe (PID: 1688)
- iexplore.exe (PID: 1852)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1852)
Changes settings of System certificates
- iexplore.exe (PID: 1852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
94
Monitored processes
49
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1031004813227242468 --mojo-platform-channel-handle=3616 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14544191128377342553 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4780 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6707587619784821740 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2416 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=2329346088529577220 --mojo-platform-channel-handle=2584 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12083651618680129968 --mojo-platform-channel-handle=4012 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=8524232170581940708 --mojo-platform-channel-handle=3788 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1688 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1852 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1852 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\Desktop\Discord.Bot.Maker\Discord Bot Maker\Discord Bot Maker.exe" | C:\Users\admin\Desktop\Discord.Bot.Maker\Discord Bot Maker\Discord Bot Maker.exe | — | LAUNCHER.exe | |||||||||||
User: admin Company: The NWJS Community Integrity Level: MEDIUM Description: nwjs Exit code: 0 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,14564168019043718723,14277597738370265883,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16948867234229703362 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4864 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
7 680
Read events
2 960
Write events
3 213
Delete events
1 507
Modification events
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3164-13232548991259750 |
Value: 259 | |||
| (PID) Process: | (3164) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
22
Suspicious files
381
Text files
10 452
Unknown types
110
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5EA81B7F-C5C.pma | — | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ce4f16d4-bbea-4c94-b41e-2b06da16841b.tmp | — | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFa6f19c.TMP | text | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old~RFa6f3de.TMP | text | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa6f5b3.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
130
DNS requests
71
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1688 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 172.217.16.195:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEAu71Ha1lP6oy62yP0YdaAA%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 172.217.16.195:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEApFQkhjIuntAgAAAABiB5I%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEAu71Ha1lP6oy62yP0YdaAA%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 172.217.16.195:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 172.217.16.195:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCRu%2FeBs4lAmgIAAAAAYgcP | US | — | — | whitelisted |
1688 | iexplore.exe | GET | — | 172.217.16.195:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3244 | chrome.exe | 104.27.170.86:443 | getgamez.net | Cloudflare Inc | US | suspicious |
3244 | chrome.exe | 172.217.22.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 172.217.16.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 151.101.0.217:443 | player.vimeo.com | Fastly | US | suspicious |
3244 | chrome.exe | 216.58.208.46:443 | s.ytimg.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 216.58.208.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 172.217.22.14:443 | www.youtube.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 216.58.210.4:443 | www.google.com | Google Inc. | US | whitelisted |
3244 | chrome.exe | 104.16.132.229:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
getgamez.net |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
www.youtube.com |
| whitelisted |
player.vimeo.com |
| whitelisted |
cdn.onesignal.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
Process | Message |
|---|---|
Discord Bot Maker.exe | [S_API FAIL] SteamAPI_Init() failed; Sys_LoadModule failed to load: C:\Program Files\Steam\steamclient.dll
|
Discord Bot Maker.exe | [S_API FAIL] SteamAPI_Init() failed; unable to locate a running instance of Steam, or a local steamclient.dll.
|