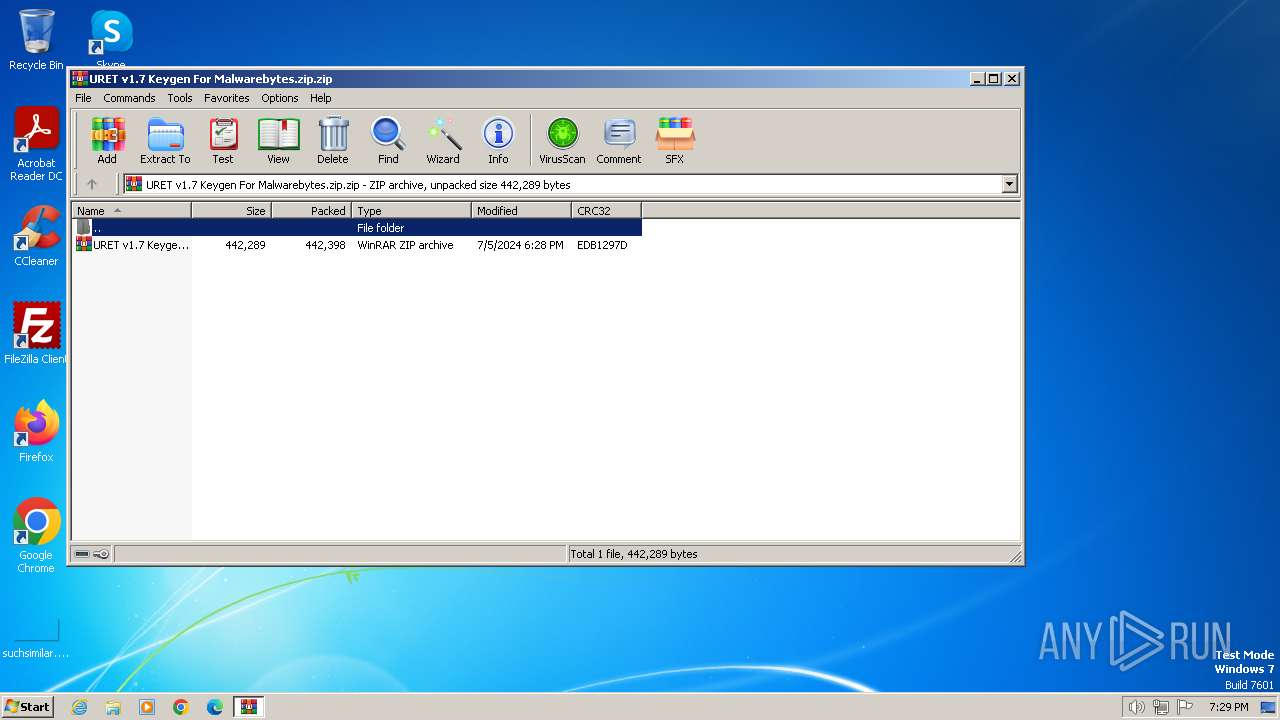
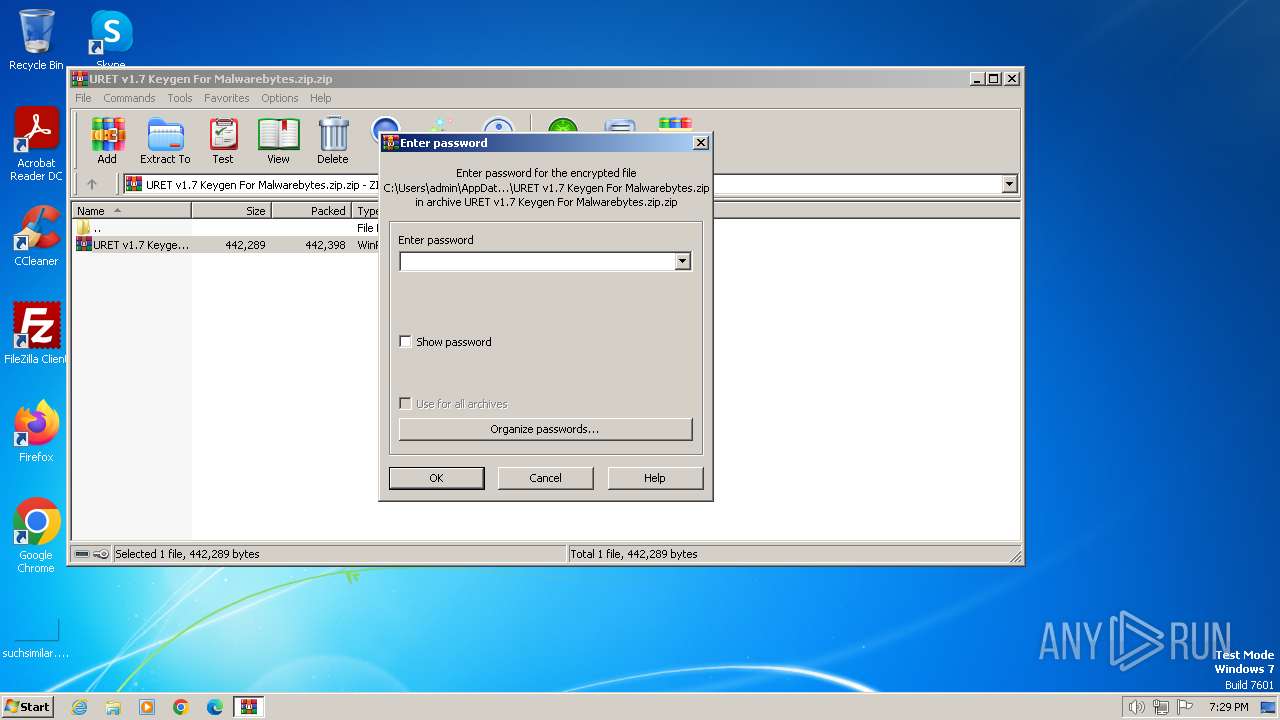
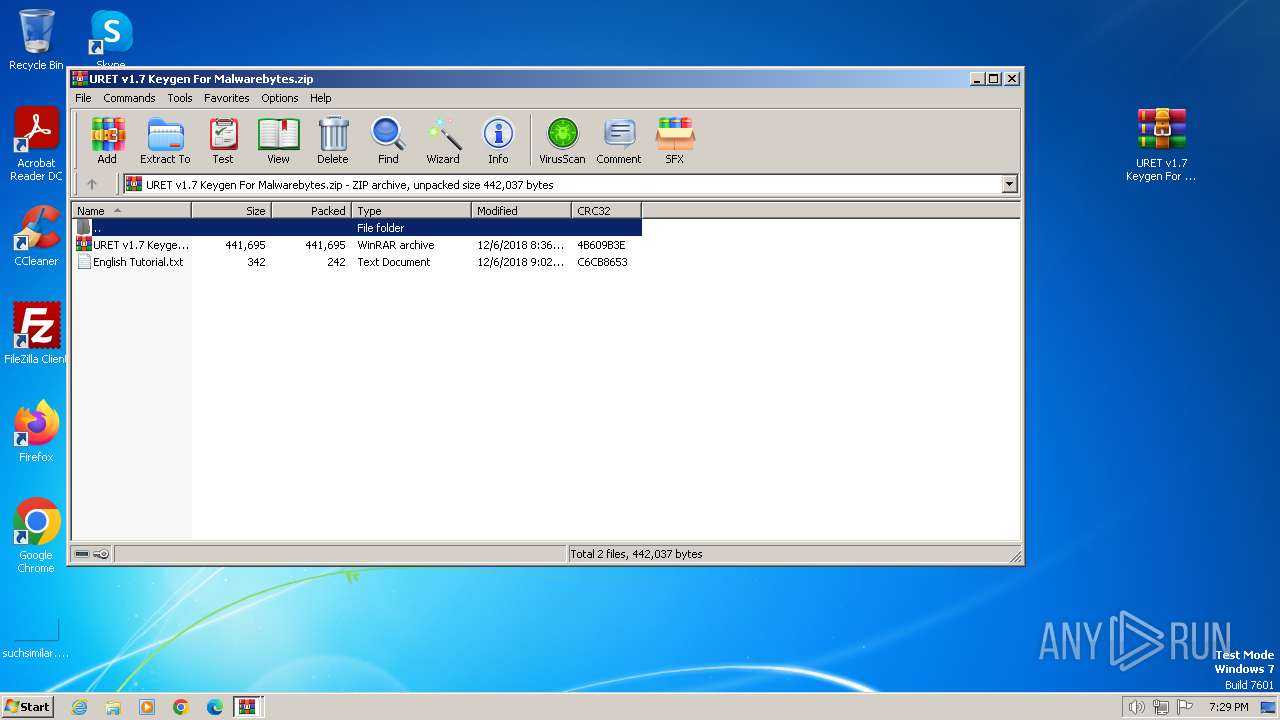
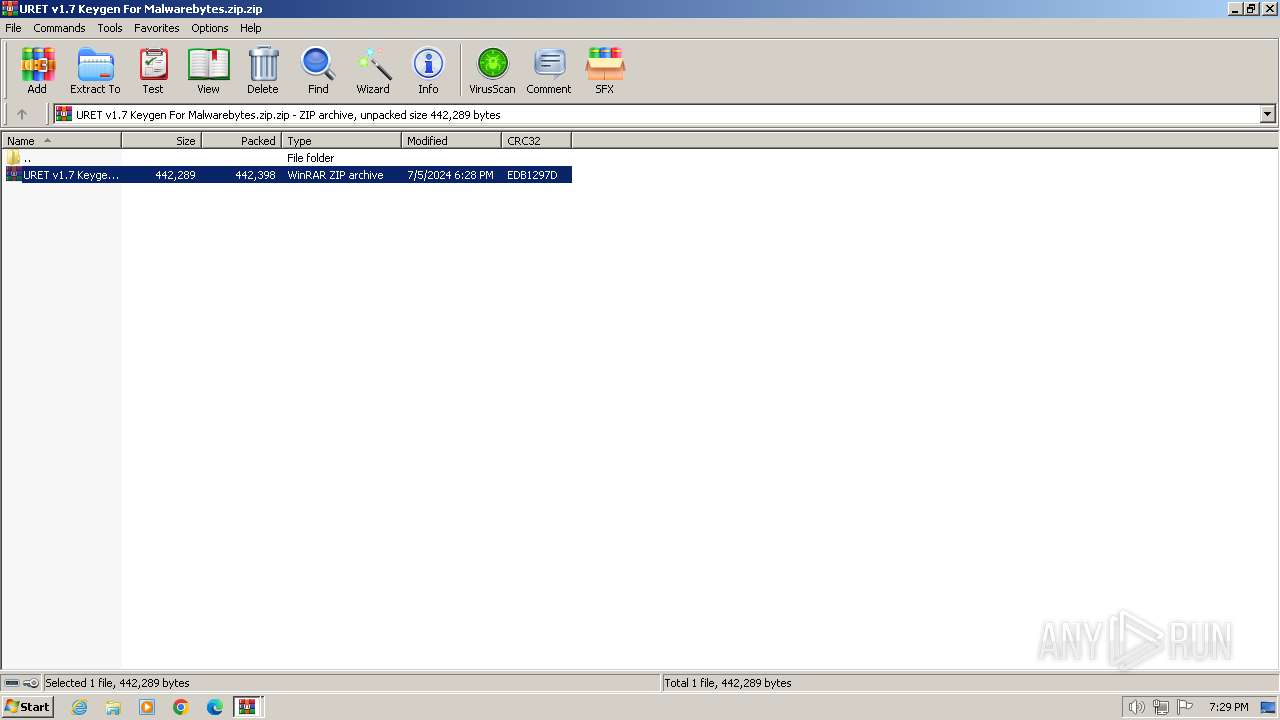
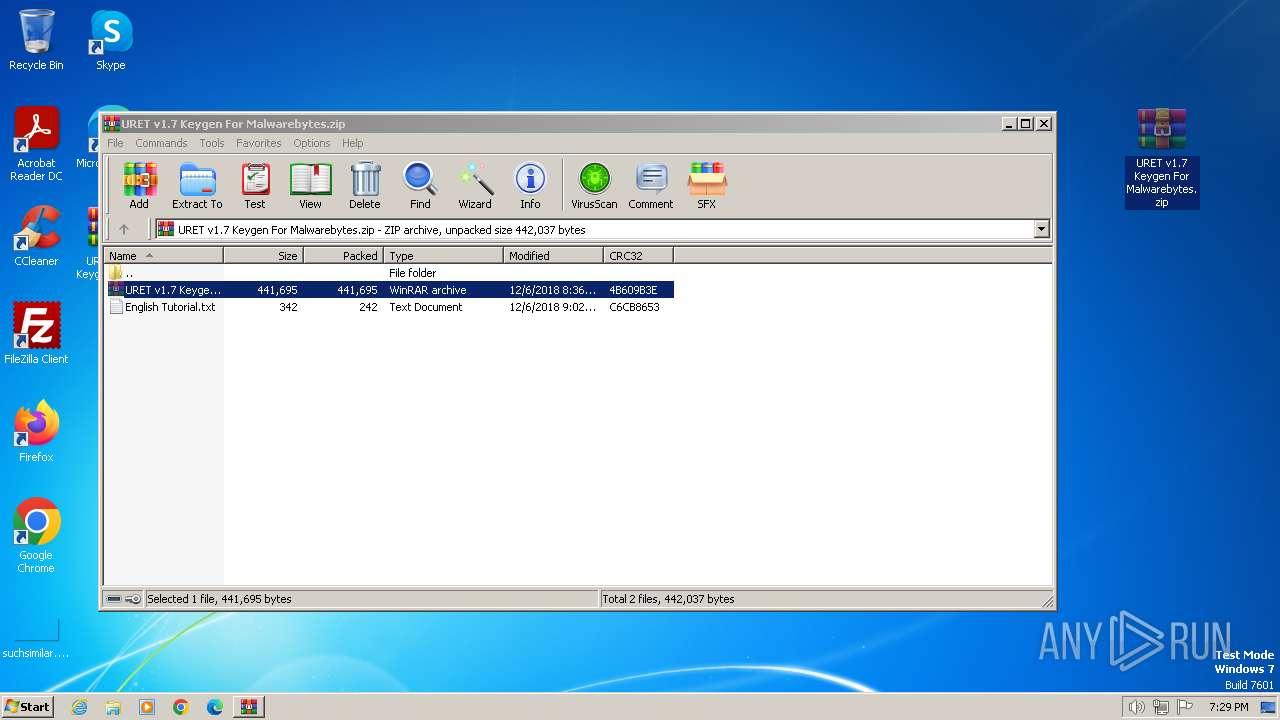
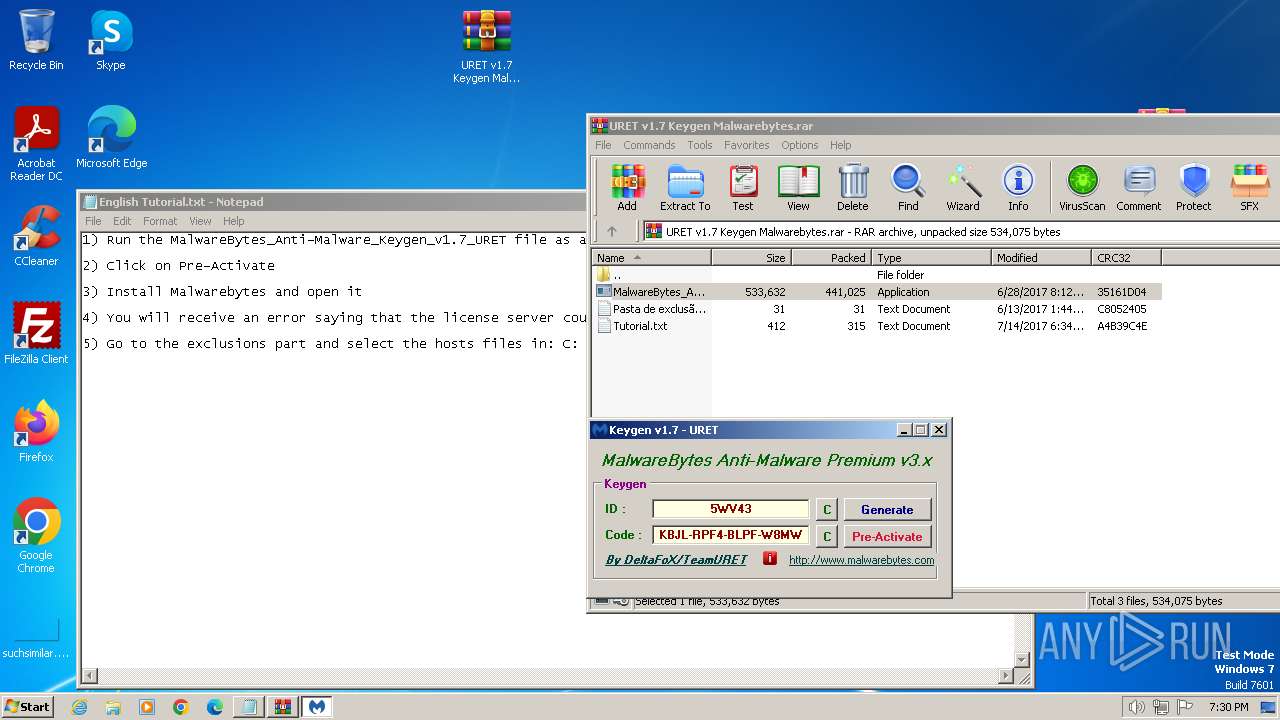
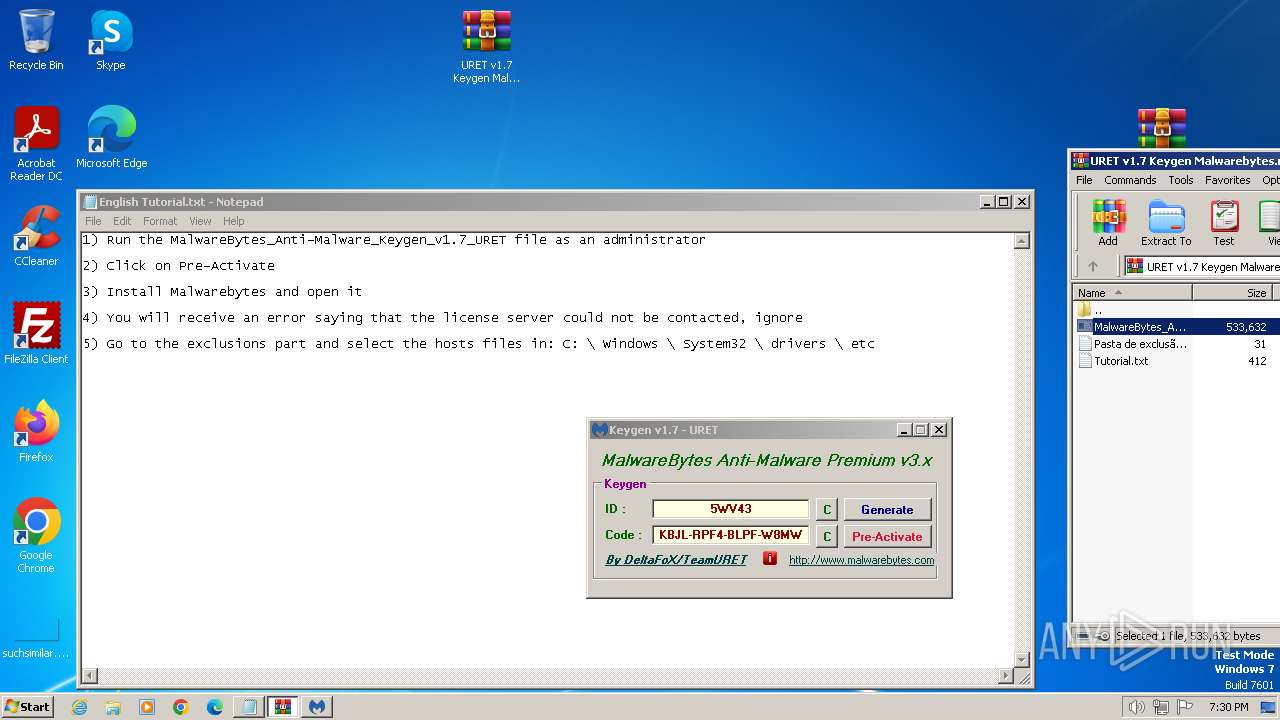
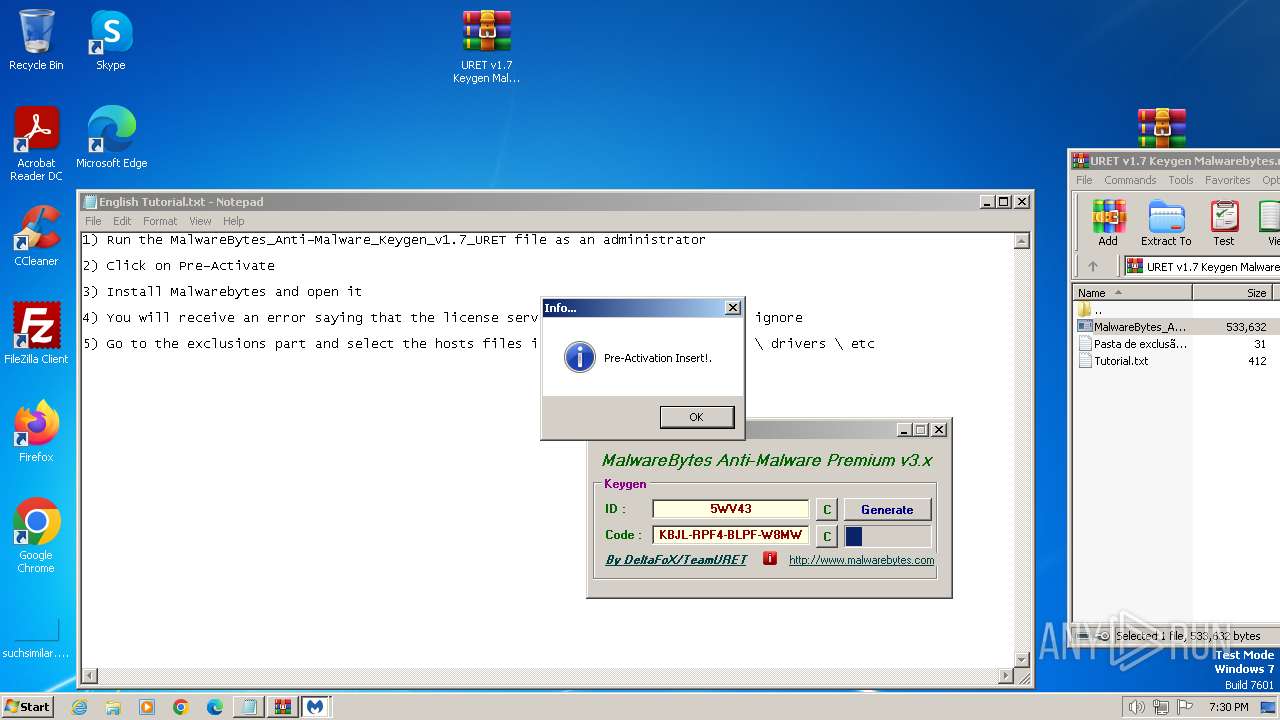
| File name: | URET v1.7 Keygen For Malwarebytes.zip.zip |
| Full analysis: | https://app.any.run/tasks/d20a977f-6c81-4d19-8cc4-27e53b390d81 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2024, 18:29:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 13FE222E06FCE514B6EA85D93CC8320E |
| SHA1: | 468346E98C1BF860B0CC753258624EB2EAAF8745 |
| SHA256: | 953887BA0C367A541A6B4A6244DE09F001F3D5F68D0F7698A323894A454ED8EC |
| SSDEEP: | 24576:Ytl10JMGl6gcM2NrzfEtyjRnmPoBFa+VKaHcJ:cl10Jvl6W2NrzfEtyjBmPqFa+VKWcJ |
MALICIOUS
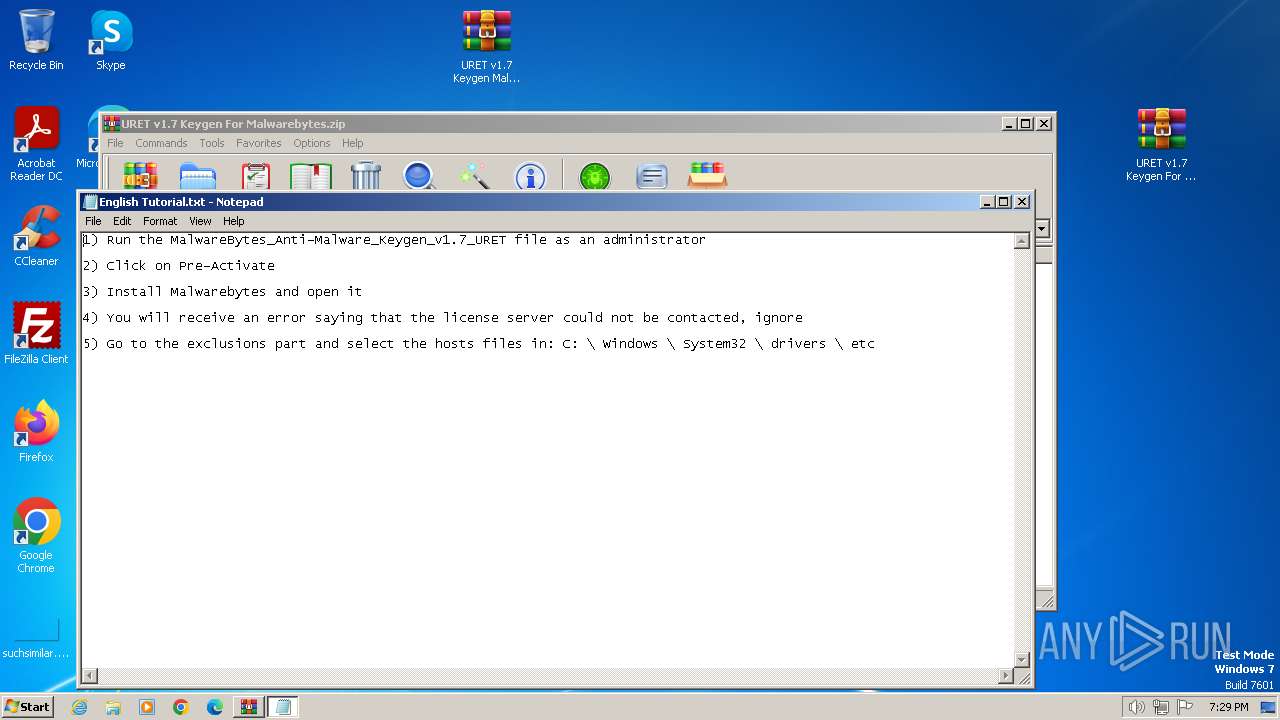
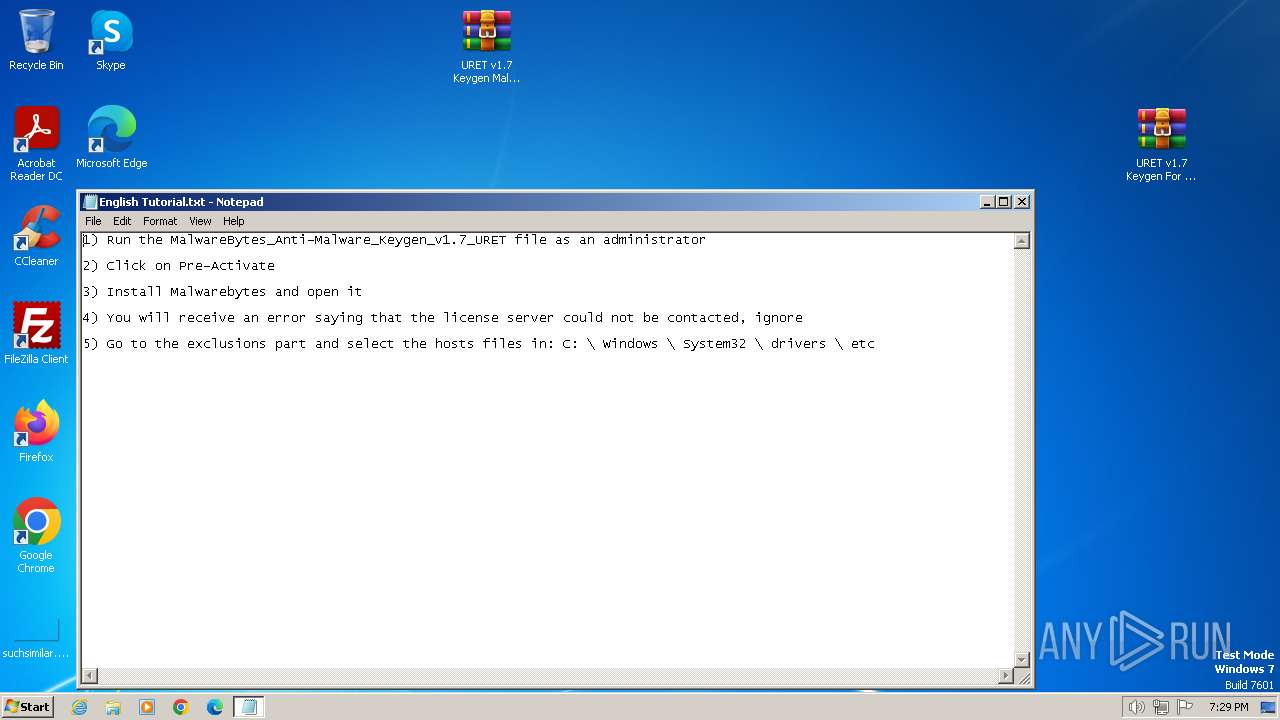
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3368)
SUSPICIOUS
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3172)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1044)
Reads the Windows owner or organization settings
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Searches for installed software
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Creates a software uninstall entry
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3172)
- WinRAR.exe (PID: 1044)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1044)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1044)
- WinRAR.exe (PID: 3172)
Checks supported languages
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Reads the computer name
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Creates files or folders in the user directory
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Reads the machine GUID from the registry
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Creates files in the program directory
- MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe (PID: 3556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:07:05 18:28:50 |
| ZipCRC: | 0xedb1297d |
| ZipCompressedSize: | 442398 |
| ZipUncompressedSize: | 442289 |
| ZipFileName: | URET v1.7 Keygen For Malwarebytes.zip |
Total processes
48
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\URET v1.7 Keygen Malwarebytes.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
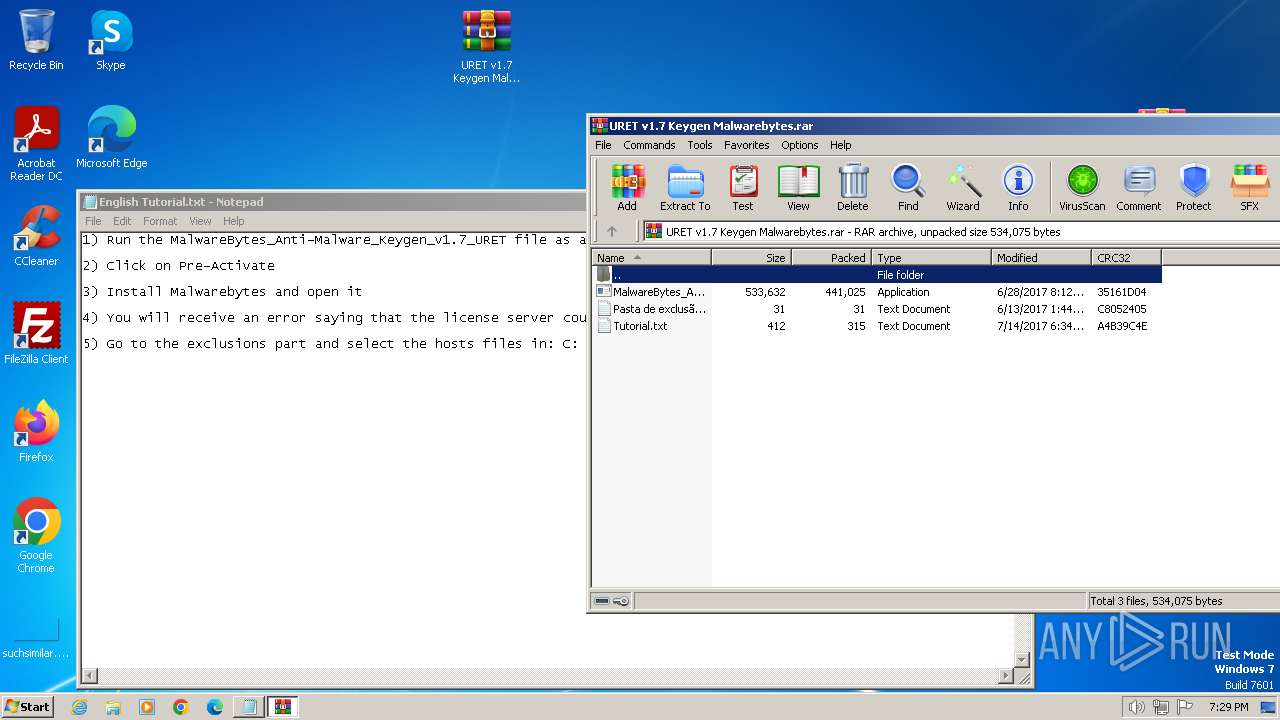
| 3124 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3172.49725\English Tutorial.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
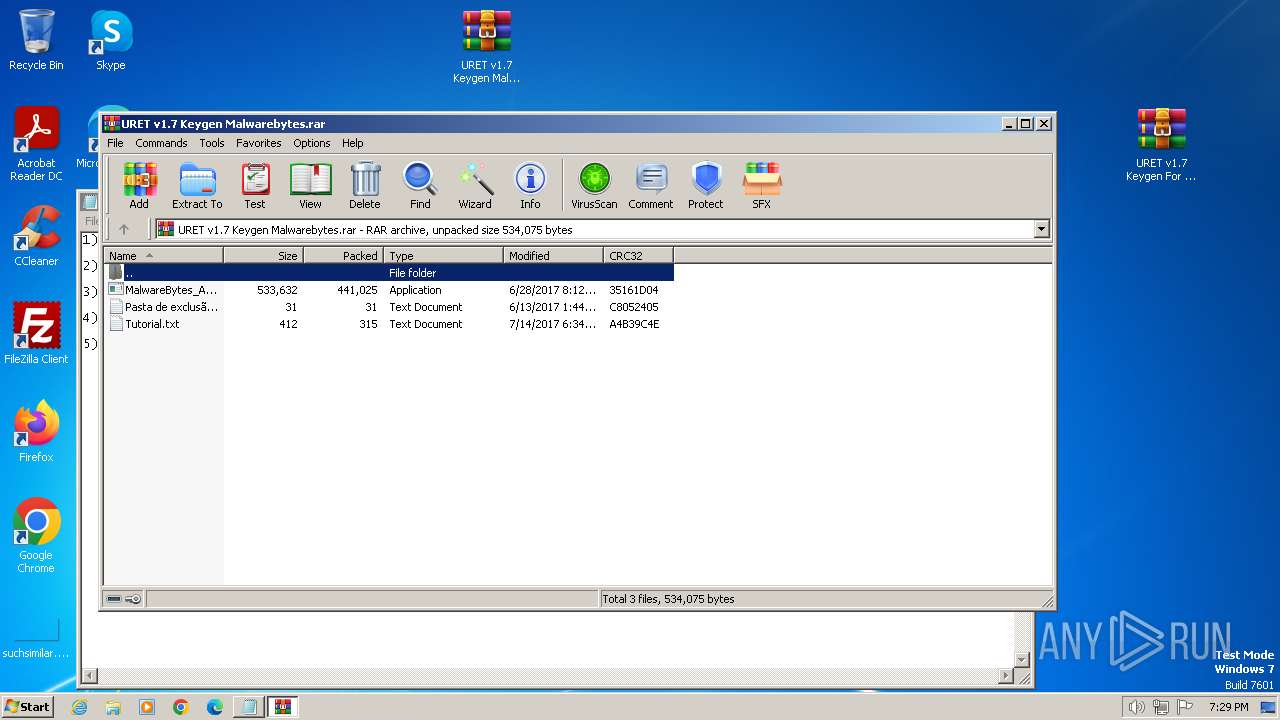
| 3172 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\URET v1.7 Keygen For Malwarebytes.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3368 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\URET v1.7 Keygen For Malwarebytes.zip.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
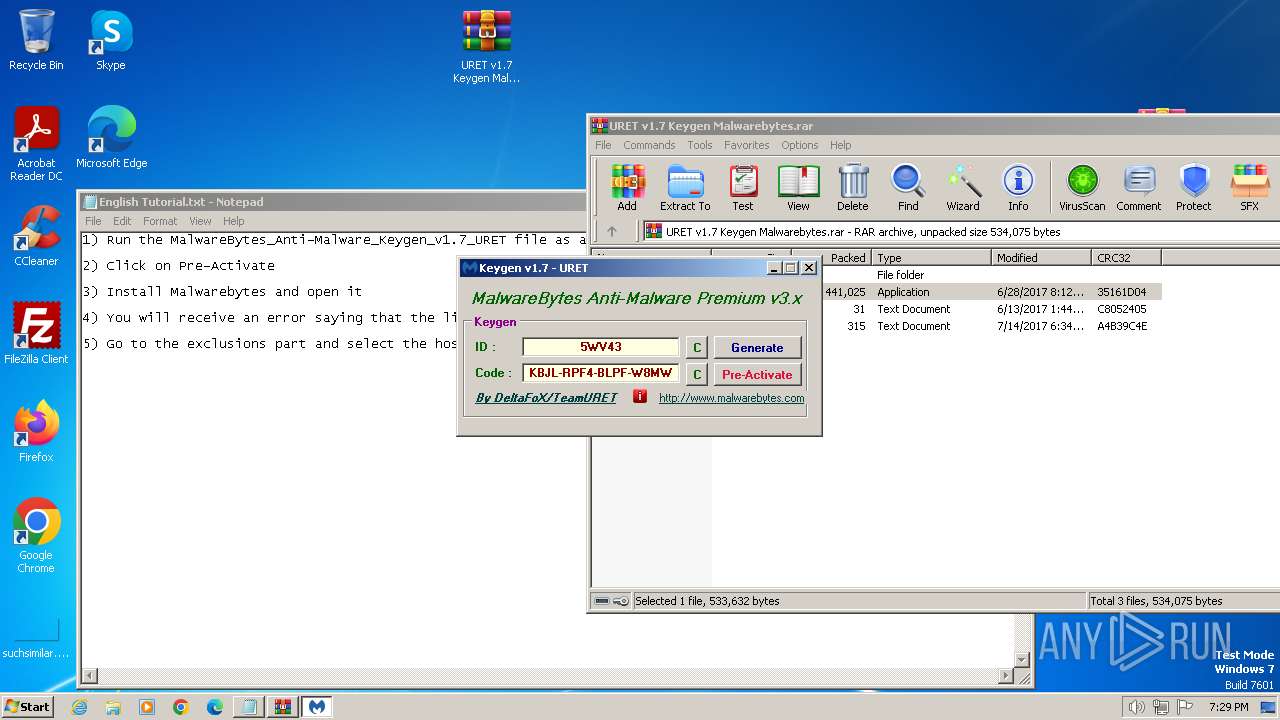
| 3484 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe | — | WinRAR.exe | |||||||||||
User: admin Company: URET Integrity Level: MEDIUM Description: MalwareBytes_Anti-Malware_DFoX Exit code: 3221226540 Version: 1.7.0.0 Modules
| |||||||||||||||
| 3556 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe | WinRAR.exe | ||||||||||||
User: admin Company: URET Integrity Level: HIGH Description: MalwareBytes_Anti-Malware_DFoX Exit code: 0 Version: 1.7.0.0 Modules
| |||||||||||||||
Total events
10 038
Read events
9 953
Write events
85
Delete events
0
Modification events
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\URET v1.7 Keygen For Malwarebytes.zip.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3368.48372\URET v1.7 Keygen For Malwarebytes.zip | compressed | |
MD5:735F77B30670F266B0F7433CCE61E6C2 | SHA256:E06C77B1CF1440E494009A769A3A837D3B1E14E736466B746771604CCDE817B9 | |||
| 1044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe | executable | |
MD5:31CEA736B899295526B0F750BFC5362B | SHA256:6AB07188EF43720F78D19FBCBDF31A65768C27FCAE0899E9DC96106A5589C574 | |||
| 1044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\Pasta de exclusão.txt | text | |
MD5:65A0201F8283C2F3C1960146EF063A83 | SHA256:73A27AF4300C85E32A5060BBCE2F6B9B41240FEE05D4FA8D331B5F7B21AC7132 | |||
| 3556 | MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe | C:\Windows\system32\drivers\etc\hosts | text | |
MD5:5A0236338F3A342F99894C1C2392CC4B | SHA256:4418E91234485F9A0E9AF6580761B072B6E5631CF05D02361D49AEF85950DD59 | |||
| 3556 | MalwareBytes_Anti-Malware_Keygen_v1.7_URET.exe | C:\ProgramData\Malwarebytes\Malwarebytes Anti-Malware\Configuration\license.conf | binary | |
MD5:88A1F7F17383A9D7C1152ECF2E4E3134 | SHA256:C624D20E4F6BA44C6D91473C4E951FBF14B271F209CBB0A6094CA4C8023FF0EE | |||
| 1044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1044.744\Tutorial.txt | text | |
MD5:819F090666638D7AADA0A5F448FAB510 | SHA256:3933A2F4F693A38DF61D80221A09089AB031B62F8260A9DF4D525386640EB342 | |||
| 3172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3172.49725\English Tutorial.txt | text | |
MD5:EB0CDB47EF9C36A8F859A1D5F5FA6864 | SHA256:3F6F94CEFE37D4B94074EC879851A763394B3B7678669F1FF33FF3643C1E8375 | |||
| 3172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3172.49565\URET v1.7 Keygen Malwarebytes.rar | compressed | |
MD5:DE7E46FE549A6B1866FA95823B2251B0 | SHA256:9EA7FB86A816A5126CC81235B6CDF885DF5921BEA436582C79C410845E2EE0BD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 41.63.96.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 41.63.96.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 41.63.96.0:80 | ctldl.windowsupdate.com | LLNW | ZA | unknown |
1372 | svchost.exe | 23.48.23.146:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1060 | svchost.exe | 41.63.96.0:80 | ctldl.windowsupdate.com | LLNW | ZA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |