| File name: | zenmap-7.97.msi |
| Full analysis: | https://app.any.run/tasks/6abd1bec-1ad5-45eb-bb64-012b064af096 |
| Verdict: | Malicious activity |
| Analysis date: | May 29, 2025, 00:36:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: nmap, Author: nmap, Keywords: Installer, Comments: This installer database contains the logic and data required to install nmap., Template: x64;1033, Revision Number: {68BF0968-ADE4-47B2-97F8-76D977F31566}, Create Time/Date: Wed May 28 11:56:10 2025, Last Saved Time/Date: Wed May 28 11:56:10 2025, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 93730D57460C98988AC0F6931F87DE19 |
| SHA1: | 9ADC9C86A6A6F17FA49EB0ED91EBB9F22E8A55CF |
| SHA256: | 9514B84ABED58AD7C02E39020C8847B80975E5D49CEA5D33F22C75AF3C3DB583 |
| SSDEEP: | 393216:PG2+t/xkMo7cpC6eivNfm4mFrMVWluYPpoa7AJrbk5jKFrzdf:O3tyMC6eiA5yWluYPp77cAJKFR |
MALICIOUS
Executing a file with an untrusted certificate
- dwm.exe (PID: 5936)
Connects to the CnC server
- dwm.exe (PID: 5936)
Run PowerShell with an invisible window
- powershell.exe (PID: 4424)
- powershell.exe (PID: 4400)
- powershell.exe (PID: 5864)
- powershell.exe (PID: 6048)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 1912)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 1616)
- msiexec.exe (PID: 1812)
Executes as Windows Service
- VSSVC.exe (PID: 5772)
Executable content was dropped or overwritten
- nmap-7.95-setup.exe (PID: 300)
- npcap-1.79.exe (PID: 4112)
- drvinst.exe (PID: 904)
- NPFInstall.exe (PID: 5172)
Contacting a server suspected of hosting an CnC
- dwm.exe (PID: 5936)
Starts a Microsoft application from unusual location
- dwm.exe (PID: 5936)
Malware-specific behavior (creating "System.dll" in Temp)
- npcap-1.79.exe (PID: 4112)
Drops a system driver (possible attempt to evade defenses)
- npcap-1.79.exe (PID: 4112)
- drvinst.exe (PID: 904)
- NPFInstall.exe (PID: 5172)
The process hide an interactive prompt from the user
- npcap-1.79.exe (PID: 4112)
The process bypasses the loading of PowerShell profile settings
- npcap-1.79.exe (PID: 4112)
Removes files via Powershell
- powershell.exe (PID: 5864)
- powershell.exe (PID: 6048)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 5864)
- powershell.exe (PID: 6048)
- powershell.exe (PID: 4400)
- powershell.exe (PID: 4424)
Starts POWERSHELL.EXE for commands execution
- npcap-1.79.exe (PID: 4112)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 1616)
- msiexec.exe (PID: 1812)
- npcap-1.79.exe (PID: 4112)
- nmap-7.95-setup.exe (PID: 300)
Reads the software policy settings
- msiexec.exe (PID: 1616)
Checks proxy server information
- msiexec.exe (PID: 1616)
Checks supported languages
- msiexec.exe (PID: 1812)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1616)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1812)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 6640)
- conhost.exe (PID: 1600)
- conhost.exe (PID: 4844)
- conhost.exe (PID: 4056)
- conhost.exe (PID: 2084)
- conhost.exe (PID: 4628)
- conhost.exe (PID: 3396)
- conhost.exe (PID: 6828)
- conhost.exe (PID: 1452)
- conhost.exe (PID: 7036)
- conhost.exe (PID: 6264)
- conhost.exe (PID: 3896)
- conhost.exe (PID: 2040)
- powershell.exe (PID: 3032)
- conhost.exe (PID: 3268)
- conhost.exe (PID: 5548)
Creates files or folders in the user directory
- msiexec.exe (PID: 1616)
Manages system restore points
- SrTasks.exe (PID: 736)
Reads the computer name
- msiexec.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | nmap |
| Author: | nmap |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install nmap. |
| Template: | x64;1033 |
| RevisionNumber: | {68BF0968-ADE4-47B2-97F8-76D977F31566} |
| CreateDate: | 2025:05:28 11:56:10 |
| ModifyDate: | 2025:05:28 11:56:10 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
183
Monitored processes
44
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
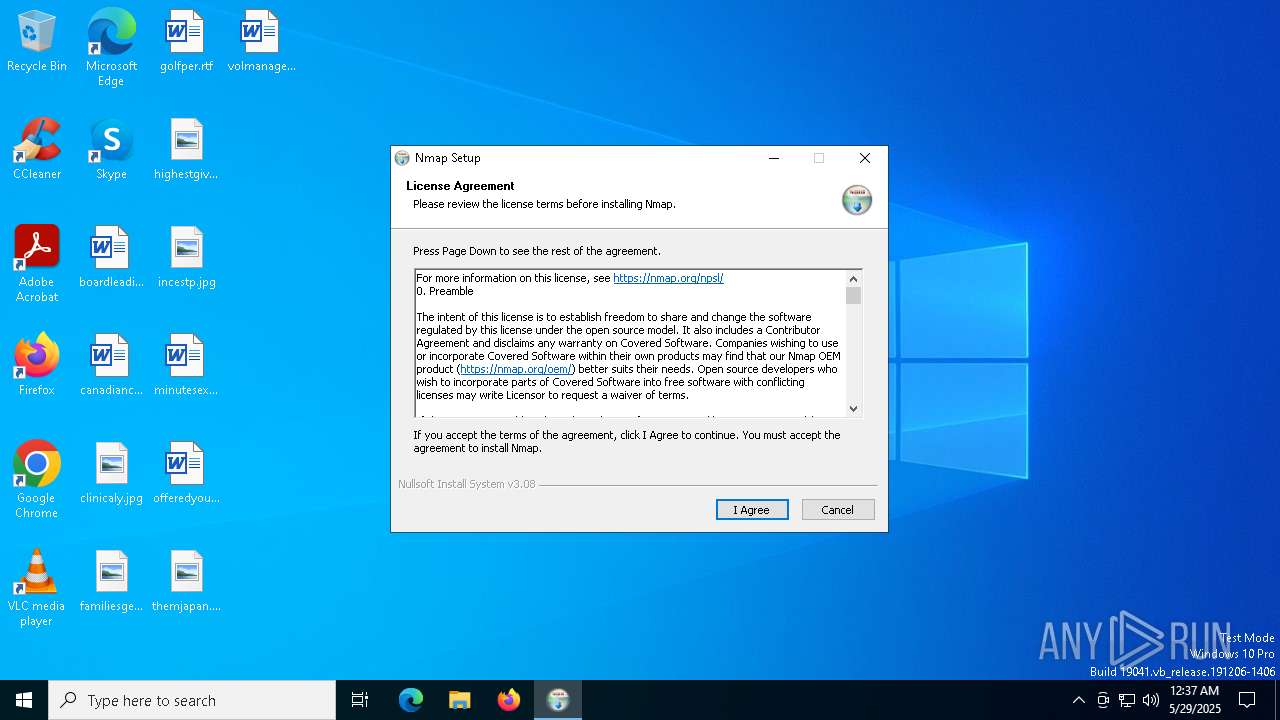
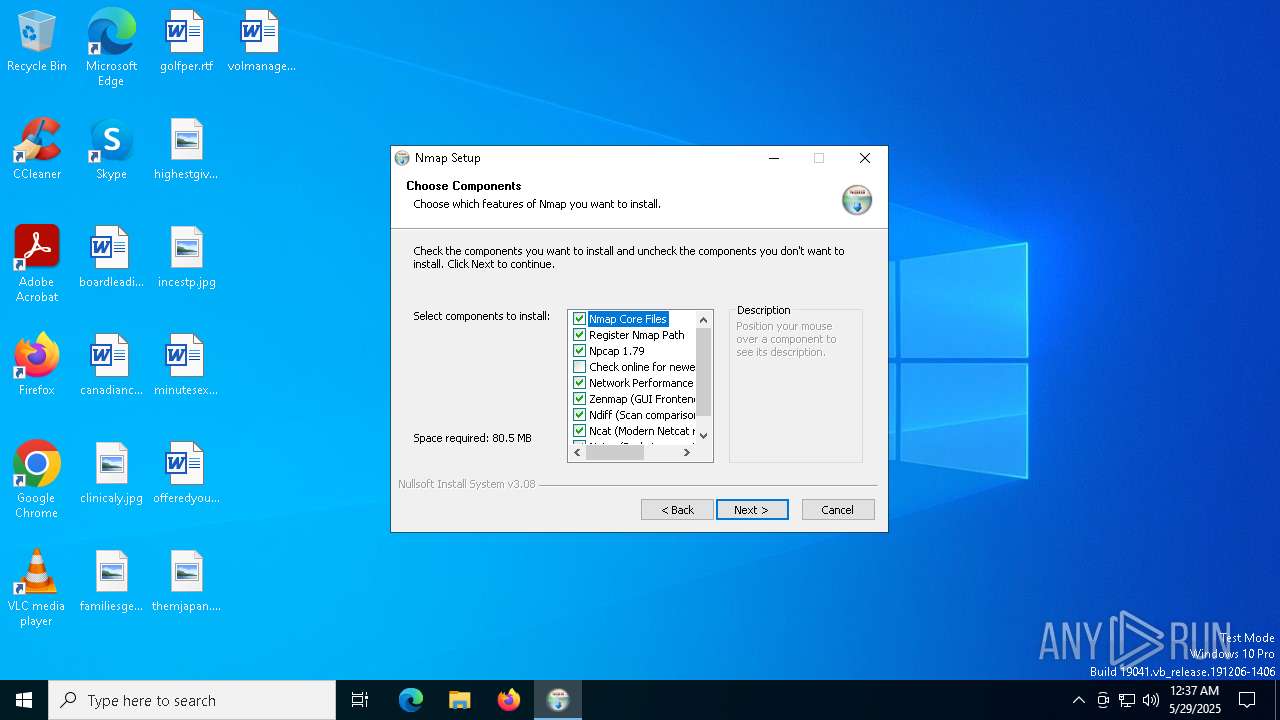
| 300 | "C:\Users\admin\AppData\Local\Temp\ApplicationInstallationFolder_11\nmap-7.95-setup.exe" | C:\Users\admin\AppData\Local\Temp\ApplicationInstallationFolder_11\nmap-7.95-setup.exe | msiexec.exe | ||||||||||||
User: admin Company: Insecure.org Integrity Level: MEDIUM Description: Nmap installer Version: 7.95 Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | certutil.exe -verifystore "Root" "0563b8630d62d75abbc8ab1e4bdfb5a899b24d43" | C:\Windows\SysWOW64\certutil.exe | — | npcap-1.79.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: CertUtil.exe Exit code: 2148073489 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | pnputil.exe -e | C:\Windows\System32\pnputil.exe | — | NPFInstall.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft PnP Utility - Tool to add, delete, export, and enumerate driver packages. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | DrvInst.exe "4" "1" "C:\Program Files\Npcap\NPCAP.inf" "9" "405306be3" "00000000000001E0" "WinSta0\Default" "00000000000001F0" "208" "C:\Program Files\Npcap" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
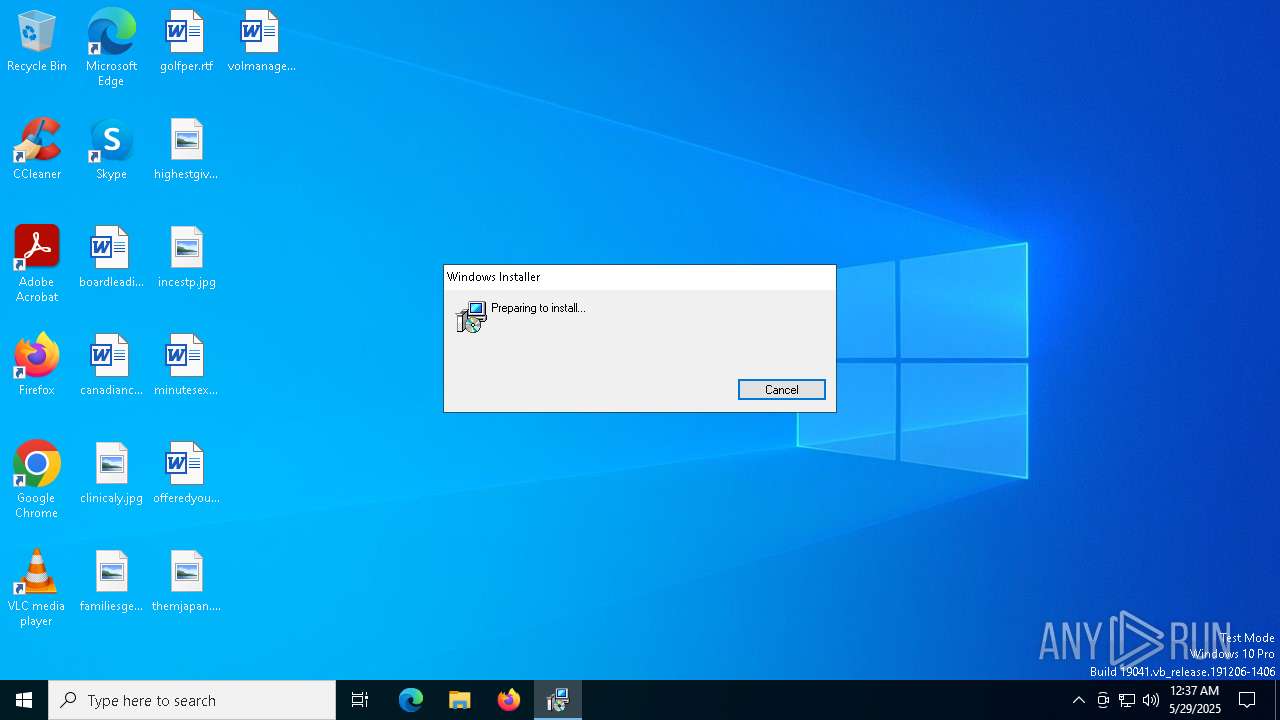
| 1616 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\zenmap-7.97.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
53 916
Read events
53 569
Write events
320
Delete events
27
Modification events
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000887ECFD131D0DB018C1600009C040000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000887ECFD131D0DB018C160000BC080000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000887ECFD131D0DB018C16000054140000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000887ECFD131D0DB018C160000CC040000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5772) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
31
Suspicious files
66
Text files
825
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1812 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1812 | msiexec.exe | C:\Windows\Installer\111e43.msi | — | |
MD5:— | SHA256:— | |||
| 1812 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\ApplicationInstallationFolder_11\nmap-7.95-setup.exe | — | |
MD5:— | SHA256:— | |||
| 1812 | msiexec.exe | C:\Windows\Installer\111e45.msi | — | |
MD5:— | SHA256:— | |||
| 1616 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:431C428AC31F380234121D6E7C91C7B5 | SHA256:6953EA30844D0D828221111589B39EAC4F6529E6A856D978418E666AC69767F9 | |||
| 1812 | msiexec.exe | C:\Windows\Temp\~DF2DF8AC5383737C19.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 1616 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:81CA39BA0B512299991EC171143A3DB5 | SHA256:5265FA2E83340CFFE7E08206CA3E3AEDDD92212FF8A03B3F0523B8C3C7F371C7 | |||
| 1812 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:6184DCD8658BDEFC3E186A093A4FF795 | SHA256:17D9B5E251A1F3F0EC7DE73B7118D1DE4C2CD77CC68163AD1E8FF77268865BD3 | |||
| 1812 | msiexec.exe | C:\Windows\Temp\~DFF767C96A4EC11B07.TMP | binary | |
MD5:6184DCD8658BDEFC3E186A093A4FF795 | SHA256:17D9B5E251A1F3F0EC7DE73B7118D1DE4C2CD77CC68163AD1E8FF77268865BD3 | |||
| 1812 | msiexec.exe | C:\Windows\Temp\~DFF997D9F2B7409FAC.TMP | binary | |
MD5:A973AD7E7937597491A1558500CBF74B | SHA256:996D7C4DC65868F79683C684EC41D0EEF86DFAB12BDCC6BDD1EE64DC3EA3A619 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
43
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1616 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDCHLZjLc8G1PAc6kMA%3D%3D | unknown | — | — | whitelisted |
1616 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
6424 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6424 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1616 | msiexec.exe | 151.101.130.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5936 | dwm.exe | Malware Command and Control Activity Detected | ET MALWARE BumbleBee Loader CnC Checkin |